安全基线检查脚本
分享一个满足等保要求的基线核查shell脚本~
 关注上方浩道Linux,回复资料,即可获取海量Linux、Python、网络通信、网络安全等学习资料!
关注上方浩道Linux,回复资料,即可获取海量Linux、Python、网络通信、网络安全等学习资料!
前言
大家好,这里是浩道Linux,主要给大家分享Linux、Python、网络通信、网络安全等相关的IT知识平台。
浩道Linux
浩道,专注工作与实践的一名IT民工。本号主要分享linux,python,网络通信、安全等相关IT干货。相聚在此,通过分享知识与经验,一起成长。
公众号
昨天群里看到小伙伴分享了一个满足等保要求的基线核查脚本,包括Linux环境下的shell脚本和windows系统下的powershell脚本,这两个脚本都是可以复制粘贴可执行的,本人已经亲自实验,可谓真香序列!今天分享给大家,让大家都能够做安全小达人!
文章来源:脚本综合来源网络
一、Linux环境下的shell脚本test.sh内容如下:
echo "+++++++++++++++++++++++++++++"echo " "echo "linux基线检"echo " "echo "++++++++++++++++++++++++++++"echo "--------------------------------------------------"a=$(ifconfig -a | grep -w inet | grep -v 127.0.0.1 | awk 'NR==1{print $2}')b=$(uname -s)c=$(hostname)e=$(date)echo "=====================系统基础信息=========================="echo "本机ip:$a"echo "操作系统:$b"echo "主机名称:$c"echo "系统时间:$e"echo ""echo "==================高危端口开放检测========================="echo " "tcpport=`netstat -anlpt | awk '{print $4}' | awk -F: '{print $NF}' | sort | uniq | grep '[0-9].*'`udpport=`netstat -anlpu | awk '{print $4}' | awk -F: '{print $NF}' | sort | uniq | grep '[0-9].*'`echo "开放高危tcp端口有:$tcpport"echo "开放高危udp端口有:$udpport"echo "僵尸进程:"ps -ef | grep zombie | grep -v grepif [ $? == 1 ];thenecho "无僵尸进程"elseecho "有僵尸进程------[需调整]"fiecho " "echo "=================路由表=============="route -necho " "echo "================监听端口查看========="netstat -tunlpecho " "echo "==============查看已建立连接========="netstat -ano | grep "ES"echo "==========查看占用CPU前十============"ps aux|head -1ps aux|grep -v PID|sort -rn -k +3|headecho " "echo "==============内存占用前十========="ps aux|head -1ps aux|grep -v PID|sort -rn -k +4|headecho " "echo "============免密登录检查============"if [ -f "/root/.ssh" ];thenecho "root下无.ssh文件"elseecho "root下存在.ssh文件"fiecho " "echo "===========查看系统活动账户==="w | tail -n +2echo " "echo "========当前用户的计划任务====="crontab -lecho " "echo "=======================身份鉴别安全================================"grep -i "^password.*requisite.*pam_cracklib.so" /etc/pam.d/system-auth > /dev/nullif [ $? == 0 ];thenecho "密码复杂度:已设置"elsegrep -i "pam_pwquality\.so" /etc/pam.d/system-auth > /dev/nullif [ $? == 0 ];thenecho ">>>密码复杂度:已设置"elseecho ">>>密码复杂度:未设置]"fifiecho "=============================dividing line================================"awk -F":" '{if($2!~/^!|^*/){print ">>>("$1")" " 是一个未被锁定的账户,请管理员检查是否是可疑账户--------[需调整]"}}' /etc/shadowecho "=============================dividing line================================"more /etc/login.defs | grep -E "PASS_MAX_DAYS" | grep -v "#" |awk -F' ' '{if($2!=90){print ">>>密码过期天数是"$2"天,请管理员改成90天------[需调整]"}}'echo "=============================dividing line================================"grep -i "^auth.*required.*pam_tally2.so.*$" /etc/pam.d/sshd > /dev/nullif [ $? == 0 ];thenecho ">>>登入失败处理:已开启"elseecho ">>>登入失败处理:未开启,请加固登入失败锁定功能----------[需调整]"fiecho " "echo ">>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>访问控制安全<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<"echo "系统中存在以下非系统默认用户:"more /etc/passwd |awk -F ":" '{if($3>500){print ">>>/etc/passwd里面的"$1 "的UID为"$3",该账户非系统默认账户,请管理员确认是否为可疑账户--------[需调整]"}}'echo "=============================dividing line================================"echo "系统特权用户:"awk -F: '$3==0 {print $1}' /etc/passwdecho "=============================dividing line================================"echo "系统中空口令账户:"awk -F: '($2=="!!") {print $1"该账户为空口令账户,请管理员确认是否为新增账户,如果为新建账户,请配置密码-------[需调整]"}' /etc/shadowecho " "echo ">>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>安全审计<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<"echo "正常情况下登录到本机30天内的所有用户的历史记录:"last | head -n 30echo "=============================dividing line================================"echo "查看syslog日志审计服务是否开启:"if service rsyslog status | egrep " active \(running";thenecho ">>>经分析,syslog服务已开启"elseecho ">>>经分析,syslog服务未开启,建议通过service rsyslog start开启日志审计功能---------[需调整]"fiecho "=============================dividing line================================"echo "查看syslog日志是否开启外发:"if more /etc/rsyslog.conf | egrep "@...\.|@..\.|@.\.|\*.\* @...\.|\*\.\* @..\.|\*\.\* @.\.";thenecho ">>>经分析,客户端syslog日志已开启外发--------[需调整]"elseecho ">>>经分析,客户端syslog日志未开启外发---------[无需调整]"fiecho "=============================dividing line================================"echo "审计的要素和审计日志:"more /etc/rsyslog.conf | grep -v "^[$|#]" | grep -v "^$"echo "=============================dividing line================================"echo "系统中关键文件修改时间:"ls -ltr /bin/ls /bin/login /etc/passwd /bin/ps /etc/shadow|awk '{print ">>>文件名:"$9" ""最后修改时间:"$6" "$7" "$8}'echo "################################################################################################ ls文件:是存储ls命令的功能函数,被删除以后,就无法执行ls命令 ## login文件:login是控制用户登录的文件,一旦被篡改或删除,系统将无法切换用户或登陆用户 ## /etc/passwd是一个文件,主要是保存用户信息 ## /bin/ps 进程查看命令功能支持文件,文件损坏或被更改后,无法正常使用ps命令 ## /etc/shadow是/etc/passwd的影子文件,密码存放在该文件当中,并且只有root用户可读 ################################################################################################"echo "=============================dividing line================================"echo "检查重要日志文件是否存在:"log_secure=/var/log/securelog_messages=/var/log/messageslog_cron=/var/log/cronlog_boot=/var/log/boot.loglog_dmesg=/var/log/dmesgif [ -e "$log_secure" ]; thenecho ">>>/var/log/secure日志文件存在"elseecho ">>>/var/log/secure日志文件不存在------[需调整]"fiif [ -e "$log_messages" ]; thenecho ">>>/var/log/messages日志文件存在"elseecho ">>>/var/log/messages日志文件不存在------[需调整]"fiif [ -e "$log_cron" ]; thenecho ">>>/var/log/cron日志文件存在"elseecho ">>>/var/log/cron日志文件不存在--------[需调整]"fiif [ -e "$log_boot" ]; thenecho ">>>/var/log/boot.log日志文件存在"elseecho ">>>/var/log/boot.log日志文件不存在--------[需调整]"fiif [ -e "$log_dmesg" ]; thenecho ">>>/var/log/dmesg日志文件存在"elseecho ">>>/var/log/dmesg日志文件不存在--------[需调整]"fiecho " "echo ">>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>剩余信息保护<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<"echo "分区情况:"echo "如果磁盘空间利用率过高,请及时调整---------[需调整]"df -hecho "=============================dividing line================================"echo "可用块设备信息:"lsblkecho "=============================dividing line================================"echo "文件系统信息:"more /etc/fstab | grep -v "^#" | grep -v "^$"echo " "echo ">>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>入侵防范安全<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<"echo "系统入侵行为:"more /var/log/secure |grep refusedif [ $? == 0 ];thenecho "有入侵行为,请分析处理--------[需调整]"elseecho ">>>无入侵行为"fiecho "=============================dividing line================================"echo "用户错误登入列表:"lastb | head > /dev/nullif [ $? == 1 ];thenecho ">>>无用户错误登入列表"elseecho ">>>用户错误登入--------[需调整]"lastb | headfiecho "=============================dividing line================================"echo "ssh暴力登入信息:"more /var/log/secure | grep "Failed" > /dev/nullif [ $? == 1 ];thenecho ">>>无ssh暴力登入信息"elsemore /var/log/secure|awk '/Failed/{print $(NF-3)}'|sort|uniq -c|awk '{print ">>>登入失败的IP和尝试次数: "$2"="$1"次---------[需调整]";}'fiecho " "echo ">>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>恶意代码防范<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<"echo "检查是否安装病毒软件:"crontab -l | grep clamscan.sh > /dev/nullif [ $? == 0 ];thenecho ">>>已安装ClamAV杀毒软件"crontab -l | grep freshclam.sh > /dev/nullif [ $? == 0 ];thenecho ">>>已部署定时更新病毒库"fielseecho ">>>未安装ClamAV杀毒软件,请部署杀毒软件加固主机防护--------[无需调整]"fiecho " "echo ">>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>资源控制安全<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<"echo "查看是否开启了xinetd服务:"if ps -elf |grep xinet |grep -v "grep xinet";thenecho ">>>xinetd服务正在运行,请检查是否可以把xinetd服务关闭--------[无需调整]"elseecho ">>>xinetd服务未开启-------[无需调整]"fiecho "=============================dividing line================================"echo "查看是否开启了ssh服务:"if service sshd status | grep -E "listening on|active \(running\)"; thenecho ">>>SSH服务已开启"elseecho ">>>SSH服务未开启--------[需调整]"fiecho "=============================dividing line================================"echo "查看是否开启了Telnet-Server服务:"if more /etc/xinetd.d/telnetd 2>&1|grep -E "disable=no"; thenecho ">>>Telnet-Server服务已开启"elseecho ">>>Telnet-Server服务未开启--------[无需调整]"fiecho "=============================dividing line================================"ps axu | grep iptables | grep -v grep || ps axu | grep firewalld | grep -v grepif [ $? == 0 ];thenecho ">>>防火墙已启用"iptables -nvL --line-numberselseecho ">>>防火墙未启用--------[需调整]"fiecho "=============================dividing line================================"echo "查看系统SSH远程访问设置策略(host.deny拒绝列表):"if more /etc/hosts.deny | grep -E "sshd"; thenecho ">>>远程访问策略已设置--------[需调整]"elseecho ">>>远程访问策略未设置--------[无需调整]"fiecho "=============================dividing line================================"echo "查看系统SSH远程访问设置策略(hosts.allow允许列表):"if more /etc/hosts.allow | grep -E "sshd"; thenecho ">>>远程访问策略已设置--------[需调整]"elseecho ">>>远程访问策略未设置--------[无需调整]"fiecho "=============================dividing line================================"echo "当hosts.allow和host.deny相冲突时,以hosts.allow设置为准"echo "=============================dividing line================================"grep -i "TMOUT" /etc/profile /etc/bashrcif [ $? == 0 ];thenecho ">>>已设置登入超时限制"elseecho ">>>未设置登入超时限制,请设置,设置方法:在/etc/profile或者/etc/bashrc里面添加参数TMOUT=600 --------[需调整]"fiecho
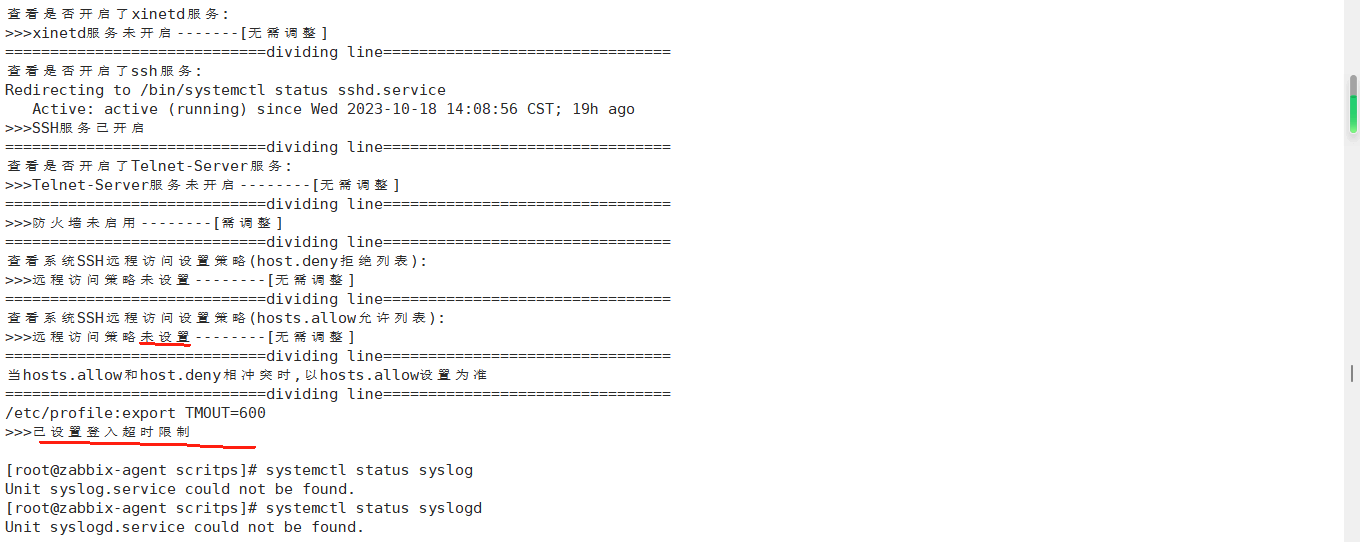
执行结果如下所示:
######################################################## @Description: Windows Server安全配置策略基线检测脚本# @Version: 1.0#######################################################<#.SYNOPSISWindows Server 安全配置策略基线检测脚本.DESCRIPTIONWindows Server 操作系统配置策略核查.EXAMPLEWindowsSecurityBaseLine.ps1 -Executor WeiyiGeek -MsrcUpdate False- Executor : 脚本执行者- MsrcUpdate : 是否在线拉取微软安全中心的服务器安全补丁列表信息(建议一台主机拉取好之后将WSUSList.json和WSUSListId.json拷贝到当前脚本同级目录下).NOTES注意:不同的版本操作系统以下某些关键项可能会不存在会有一些警告。#>#设置PowerShell执行脚本#Set-ExecutionPolicy# * 文件输出默认为UTF-8格式$PSDefaultParameterValues['Out-File:Encoding'] = 'utf8'$ip = (ipconfig|select-string "IPV4"|out-string).split(":")[1].split("I")[0].Trim(" ").Trim(".-`t`n`r")$houzhui = ".log"$file_name = $ip + $houzhuiecho "$file_name"################################################################################################################################# **********************## * 全局公用工具依赖函数 *# **********************#Function F_IsCurrentUserAdmin{<#.SYNOPSISF_IsCurrentUserAdmin 函数:全局公用工具依赖。.DESCRIPTION判断当前运行的powershell终端是否管理员执行,返回值 true 或者 false.EXAMPLEF_IsCurrentUserAdmin#>$user = [Security.Principal.WindowsIdentity]::GetCurrent();(New-Object Security.Principal.WindowsPrincipal $user).IsInRole([Security.Principal.WindowsBuiltinRole]::Administrator)}function F_Logging {<#.SYNOPSISF_Logging 日志输出函数.DESCRIPTION用于输出脚本执行结果并按照不同的日志等级输出显示到客户终端上。.EXAMPLEF_Logging -Level [Info|Warning|Error] -Msg "测试输出字符串"#>param ([Parameter(Mandatory=$true)]$Msg,[ValidateSet("Info","Warning","Error")]$Level)switch ($Level) {Info {Write-Host "[INFO] ${Msg}" -ForegroundColor Green;}Warning {Write-Host "[WARN] ${Msg}" -ForegroundColor Yellow;}Error {Write-Host "[ERROR] ${Msg}" -ForegroundColor Red;}Default {Write-Host "[*] F_Logging 日志 Level 等级错误`n Useage:F_Logging -Level [Info|Warning|Error] -Msg '测试输出字符串'" -ForegroundColor Red;}}}function F_Tools {<#.SYNOPSISF_Tools 检测对比函数.DESCRIPTION验证判断传入的字段是否与安全加固字段一致.EXAMPLEF_Tools -Key "ItemDemo" -Value "2" -Operator "eq" -DefaultValue "1" -Msg "对比ItemDemo字段值与预设值"#>param ([Parameter(Mandatory=$true)][String]$Key,[Parameter(Mandatory=$true)]$Value,[Parameter(Mandatory=$true)]$DefaultValue,[String]$Msg,[String]$Operator)if ( $Operator -eq "eq" ) {if ( $Value -eq $DefaultValue ) {$Result = @{"$($Key)"="[合格项]|$($Value)|$($DefaultValue)|$($Msg)-【符合】等级保护标准."}Write-Host "$($Key)"=" [合格项]|$($Value)|$($DefaultValue)|$($Msg)-【符合】等级保护标准." -ForegroundColor Whitereturn $Result} else {$Result = @{"$($Key)"="[异常项]|$($Value)|$($DefaultValue)|$($Msg)-【不符合】等级保护标准."}Write-Host "$($Key)"=" [异常项]|$($Value)|$($DefaultValue)|$($Msg)-【不符合】等级保护标准." -ForegroundColor redreturn $Result}} elseif ($Operator -eq "ne" ) {if ( $Value -ne $DefaultValue ) {$Result = @{"$($Key)"="[合格项]|$($Value)|$($DefaultValue)|$($Msg)-【符合】等级保护标准."}Write-Host "$($Key)"=" [合格项]|$($Value)|$($DefaultValue)|$($Msg)-【符合】等级保护标准." -ForegroundColor Whitereturn $Result} else {$Result = @{"$($Key)"="[异常项]|$($Value)|$($DefaultValue)|$($Msg)-【不符合】等级保护标准."}Write-Host "$($Key)"=" [异常项]|$($Value)|$($DefaultValue)|$($Msg)-【不符合】等级保护标准." -ForegroundColor redreturn $Result}} elseif ($Operator -eq "le") {if ( $Value -le $DefaultValue ) {$Result = @{"$($Key)"="[合格项]|$($Value)|$($DefaultValue)|$($Msg)-【符合】等级保护标准."}Write-Host "$($Key)"=" [合格项]|$($Value)|$($DefaultValue)|$($Msg)-【符合】等级保护标准." -ForegroundColor Whitereturn $Result} else {$Result = @{"$($Key)"="[异常项]|$($Value)|$($DefaultValue)|$($Msg)-【不符合】等级保护标准."}Write-Host "$($Key)"=" [异常项]|$($Value)|$($DefaultValue)|$($Msg)-【不符合】等级保护标准." -ForegroundColor redreturn $Result}} elseif ($Operator -eq "ge") {if ( $Value -ge $DefaultValue ) {$Result = @{"$($Key)"="[合格项]|$($Value)|$($DefaultValue)|$($Msg)-【符合】等级保护标准."}Write-Host "$($Key)"=" [合格项]|$($Value)|$($DefaultValue)|$($Msg)-【符合】等级保护标准." -ForegroundColor Whitereturn $Result} else {$Result = @{"$($Key)"="[异常项]|$($Value)|$($DefaultValue)|$($Msg)-【不符合】等级保护标准."}Write-Host "$($Key)"=" [异常项]|$($Value)|$($DefaultValue)|$($Msg)-【不符合】等级保护标准." -ForegroundColor redreturn $Result}}}function F_GetRegPropertyValue {param ([Parameter(Mandatory=$true)][String]$Key,[Parameter(Mandatory=$true)][String]$Name,[Parameter(Mandatory=$true)][String]$Operator,[Parameter(Mandatory=$true)]$DefaultValue,[Parameter(Mandatory=$true)][String]$Msg)try {$Value = Get-ItemPropertyValue -Path "Registry::$Key" -ErrorAction Ignore -WarningAction Ignore -Name $Name$Result = F_Tools -Key "Registry::$($Name)" -Value $Value -Operator $Operator -DefaultValue $DefaultValue -Msg $Msgreturn $Result} catch {$Result = @{"Registry::$($Name)"="[异常项]|$($Key)中$($Name)不存在该项|$($DefaultValue)|$($Msg)"}Write-Host $Result.Values -ForegroundColor Redreturn $Result}}Function F_UrlRequest {param ([Parameter(Mandatory=$true)][String]$Msrc_api)Write-Host "[-] $($Msrc_api)" -ForegroundColor Gray$Response=Invoke-WebRequest -Uri "$($Msrc_api)"Return ConvertFrom-Json -InputObject $Response}################################################################################################################################## * 操作系统基础信息记录函数 * ### - 系统信息记录函数 - #$SysInfo = @{}# - Get-Computer 命令使用# Tips :在 Server 2019 以及 Windows 10 以下系统无该命令# $Item = 'WindowsProductName','WindowsEditionId','WindowsInstallationType','WindowsCurrentVersion','WindowsVersion','WindowsProductId','BiosManufacturer','BiosFirmwareType','BiosName','BiosVersion','BiosBIOSVersion','BiosSeralNumber','CsBootupState','OsBootDevice','BiosReleaseDate','CsName','CsAdminPasswordStatus','CsManufacturer','CsModel','OsName','OsType','OsProductType','OsServerLevel','OsArchitecture','CsSystemType','OsOperatingSystemSKU','OsVersion','OsBuildNumber','OsSerialNumber','OsInstallDate','OsSystemDevice','OsSystemDirectory','OsCountryCode','OsCodeSet','OsLocaleID','OsCurrentTimeZone','TimeZone','OsLanguage','OsLocalDateTime','OsLastBootUpTime','CsProcessors','OsBuildType','CsNumberOfProcessors','CsNumberOfLogicalProcessors','OsMaxNumberOfProcesses','OsTotalVisibleMemorySize','OsFreePhysicalMemory','OsTotalVirtualMemorySize','OsFreeVirtualMemory','OsInUseVirtualMemory','OsMaxProcessMemorySize','CsNetworkAdapters','OsHotFixes'# - Systeminfo 命令使用(通用-推荐)$Item = 'Hostname','OSName','OSVersion','OSManufacturer','OSConfiguration','OS Build Type','RegisteredOwner','RegisteredOrganization','Product ID','Original Install Date','System Boot Time','System Manufacturer','System Model','System Type','Processor(s)','BIOS Version','Windows Directory','System Directory','Boot Device','System Locale','Input Locale','Time Zone','Total Physical Memory','Available Physical Memory','Virtual Memory: Max Size','Virtual Memory: Available','Virtual Memory: In Use','Page File Location(s)','Domain','Logon Server','Hotfix(s)','Network Card(s)'Function F_SysInfo {# - 当前系统及计算机相关信息 (Primary)# Server 2019 以及 Windows 10 适用# $Computer = Get-ComputerInfo$Computer = systeminfo.exe /FO CSV /S $env:COMPUTERNAME |Select-Object -Skip 1 | ConvertFrom-CSV -Header $Itemforeach( $key in $Item) {$SysInfo += @{"$($key)"=$Computer.$key}}# - 通用设置针对采用`systeminfo.exe`命令方式$SysInfo += @{"WindowsProductName"="$($SysInfo.OSName)"}$SysInfo.OsVersion=($Sysinfo.OSVersion -split " ")[0]$SysInfo += @{"CsSystemType"=($Sysinfo."System Type" -split " ")[0]}# - 当前系统 PowerShell 版本信息以及是否为虚拟机$SysInfo += @{"PSVersion"=$PSVersionTable.PSEdition+"-"+$PSVersionTable.PSVersion}# - 验证当前计算机产品及其版本 (Primary)$Flag = $SysInfo.WindowsProductName -match "Windows 8.1|Windows 10|Server 2008|Server 2012|Server 2016|Server 2019"$ProductName = "$($Matches.Values)"if ( $ProductName.Contains("Windows")) {$SysInfo += @{"ProductType"="Client"}$SysInfo += @{"ProductName"=$ProductName}$SysInfo += @{"WindowsVersion"=Get-ItemPropertyValue -Path 'Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion' -Name ReleaseId}} else {$SysInfo += @{"ProductType"="Server"}$SysInfo += @{"ProductName"=$ProductName}}# - 验证当前计算机产品是是物理机还是虚拟机 (Primary)$ComputerType = get-wmiobject win32_computersystemif ($ComputerType.Manufacturer -match "VMware"){$SysInfo += @{"ComputerType"="虚拟机 - $($ComputerType.Model)"}} else {$SysInfo += @{"ComputerType"="物理机 - $($ComputerType.Model)"}}# # - 当前计算机温度值信息记录 (WINDOWSERVER2019支持)# Get-CimInstance -Namespace ROOT/WMI -Class MSAcpi_ThermalZoneTemperature | % {# $currentTempKelvin = $_.CurrentTemperature / 10# $currentTempCelsius = $currentTempKelvin - 273.15# $currentTempFahrenheit = (9/5) * $currentTempCelsius + 32# $Temperature += "InstanceName: " + $_.InstanceName+ " ==>> " + $currentTempCelsius.ToString() + " 摄氏度(C); " + $currentTempFahrenheit.ToString() + " 华氏度(F) ; " + $currentTempKelvin + "开氏度(K) `n"# }# $SysInfo += @{"Temperature"=$Temperature}return $SysInfo}## * - 计算机Mac及IP地址信息函数 * ### * 系统网络及适配器信息变量 * ##$SysNetAdapter = @{}#function F_SysNetAdapter {# - 计算机中已启用的网卡、Mac及IP地址信息# $Adapter = Get-NetAdapter | Where-Object {$_.Status -eq "Up"} | Sort-Object -Property LinkSpeed# foreach ( $Item in $Adapter) {# $IPAddress = (Get-NetIPAddress -AddressFamily IPv4 -InterfaceIndex $Item.ifIndex).IPAddress# $SysNetAdapter += @{"$($Item.MacAddress)"="$($Item.Status) | $($Item.Name) | $($IPAddress) | $($Item.LinkSpeed) | $($Item.InterfaceDescription)"}# }# return $SysNetAdapter#}## * - 计算机系统磁盘与空间剩余查询函数 * ### - 系统磁盘与空间剩余信息 - ##$SysDisk = @{}#function F_SysDisk {# - 计算机磁盘信息# $Disk = Get-Disk# foreach ( $Item in $Disk) {# $SysDisk += @{"$($Item.SerialNumber)"="$($Item.Number) | $($Item.FriendlyName) | $($Item.HealthStatus)| $($Item.Size / [math]::Pow(1024,3)) GB | $($Item.PartitionStyle) |$($Item.OperationalStatus)"}# }# $Drive = Get-PSDrive -PSProvider FileSystem | Sort-Object -Property Name# $Drive | % {# $Free = [Math]::Round( $_.Free / [math]::pow(1024,3),2 )# $Used = [Math]::Round( $_.Used / [math]::pow(1024,3),2 )# $Total = [Math]::Ceiling($Free + $Used)# $SysDisk += @{"FileSystem::$($_.Name)"="$($_.Name) | Free: $($Free) GB | Used: $($Used) GB | Total: $($Total) GB"}# }# return $SysDisk#}## * 系统账号检查函数 * ### - 系统账户信息变量 - #$SysAccount = @{}Function F_SysAccount {# - 账户检查$Account = Get-WmiObject -Class Win32_UserAccount | Select-Object Name,AccountType,Caption,SIDWrite-Host "* 当前系统存在的 $($Account.Length) 名账户 : $($Account.Name)" -ForegroundColor Greenif($Account.Length -ge 4 -and ($Account.sid | Select-String -Pattern "^((?!(-500|-501|-503|-504)).)*$")) {$Result = @{"SysAccount"="[异常项]-系统中存在其他账号请检查: $($Account.Name)"}$SysAccount += $Result}else{$Result = @{"SysAccount"="[合格项]-系统中无多余其他账号";}$SysAccount += $Result}return $SysAccount}## * 系统账号策略配置核查函数 * ### - 系统账号策略 - #$SysAccountPolicy = @{# + 密码最短留存期"MinimumPasswordAge" = @{operator="le";value=30;msg="密码最短留存期"}# + 密码最长留存期"MaximumPasswordAge" = @{operator="le";value=90;msg="密码最长留存期"}# + 密码长度最小值"MinimumPasswordLength" = @{operator="ge";value=14;msg="密码长度最小值"}# + 密码必须符合复杂性要求"PasswordComplexity" = @{operator="eq";value=1;msg="密码必须符合复杂性要求策略"}# + 强制密码历史 N个记住的密码"PasswordHistorySize" = @{operator="ge";value=3;msg="强制密码历史个记住的密码"}# + 账户登录失败锁定阈值N次数"LockoutBadCount" = @{operator="le";value=6;msg="账户登录失败锁定阈值次数"}# + 账户锁定时间(分钟)"ResetLockoutCount" = @{operator="ge";value=15;msg="账户锁定时间(分钟)"}# + 复位账户锁定计数器时间(分钟)"LockoutDuration" = @{operator="ge";value=15;msg="复位账户锁定计数器时间(分钟)"}# + 下次登录必须更改密码"RequireLogonToChangePassword" = @{operator="eq";value=0;msg="下次登录必须更改密码"}# + 强制过期"ForceLogoffWhenHourExpire" = @{operator="eq";value=0;msg="强制过期"}# + 当前管理账号登陆名称"NewAdministratorName" = @{operator="ne";value='"Administrator"';msg="当前系统默认管理账号登陆名称策略"}# + 当前来宾用户登陆名称"NewGuestName" = @{operator="ne";value='"Guest"';msg="当前系统默认来宾用户登陆名称策略"}# + 管理员是否被启用"EnableAdminAccount" = @{operator="eq";value=1;msg="管理员账户停用与启用策略"}# + 来宾用户是否启用"EnableGuestAccount" = @{operator="eq";value=0;msg="来宾账户停用与启用策略"}# + 指示是否使用可逆加密来存储密码一般禁用(除非应用程序要求超过保护密码信息的需要)"ClearTextPassword" = @{operator="eq";value=0;msg="指示是否使用可逆加密来存储密码 (除非应用程序要求超过保护密码信息的需要)"}# + 启用时此设置允许匿名用户查询本地LSA策略(0关闭)"LSAAnonymousNameLookup" = @{operator="eq";value=0;msg="启用时此设置允许匿名用户查询本地LSA策略 (0关闭)"}# + 检查结果存放的空数组"CheckResults" = @()}Function F_SysAccountPolicy {$Count = $Config.Countfor ($i=0;$i -lt $Count; $i++){$Line = $Config[$i] -split " = "if ($SysAccountPolicy.ContainsKey("$($Line[0])")) {$Result = F_Tools -Key "SysAccountPolicy::$($Line[0])" -Value $Line[1] -Operator $SysAccountPolicy["$($Line[0])"].Operator -DefaultValue $SysAccountPolicy["$($Line[0])"].Value -Msg "系统账号策略配置-$($SysAccountPolicy["$($Line[0])"].Msg)"$SysAccountPolicy['CheckResults'] += $Result}if ( $Line[0] -eq "[Event Audit]" ) { break;}}return $SysAccountPolicy['CheckResults']}## * 系统事件审核策略配置核查函数 * ### - 系统事件审核策略 - #$SysEventAuditPolicy = @{# + 审核系统事件(0) [成功(1)、失败(2)] (3)AuditSystemEvents = @{operator="eq";value=3;msg="审核系统事件"}# + 审核登录事件 成功、失败AuditLogonEvents = @{operator="eq";value=3;msg="审核登录事件"}# + 审核对象访问 成功、失败AuditObjectAccess = @{operator="eq";value=3;msg="审核对象访问"}# + 审核特权使用 失败AuditPrivilegeUse = @{operator="ge";value=3;msg="审核特权使用"}# + 审核策略更改 成功、失败AuditPolicyChange = @{operator="eq";value=3;msg="审核策略更改"}# + 审核账户管理 成功、失败AuditAccountManage = @{operator="eq";value=3;msg="审核账户管理"}# + 审核过程追踪 失败AuditProcessTracking = @{operator="ge";value=3;msg="审核过程追踪"}# + 审核目录服务访问 失败AuditDSAccess = @{operator="ge";value=3;msg="审核目录服务访问"}# + 审核账户登录事件 成功、失败AuditAccountLogon = @{operator="eq";value=3;msg="审核账户登录事件"}# + 检查结果存放的空数组CheckResults = @()}function F_SysEventAuditPolicy {$Count = $Config.Countfor ($i=0;$i -lt $Count; $i++){$Line = $Config[$i] -split " = "if ( $Line[0] -eq "[Registry Values]" ) { break;}if ($SysEventAuditPolicy.ContainsKey("$($Line[0])")) {$Result = F_Tools -Key "SysEventAuditPolicy::$($Line[0])" -Value $Line[1] -Operator $SysEventAuditPolicy["$($Line[0])"].Operator -DefaultValue $SysEventAuditPolicy["$($Line[0])"].Value -Msg "系统账号策略配置-$($SysEventAuditPolicy["$($Line[0])"].Msg)"$SysEventAuditPolicy['CheckResults'] += $Result}}return $SysEventAuditPolicy['CheckResults']}## * 操作系统用户权限管理策略检查 * ### - 组策略用户权限管理策略 - #$SysUserPrivilegePolicy = @{# + 操作系统本地关机策略安全SeShutdownPrivilege = @{operator="eq";value='*S-1-5-32-544';msg="操作系统本地关机策略"}# + 操作系统远程关机策略安全SeRemoteShutdownPrivilege = @{operator="eq";value='*S-1-5-32-544';msg="操作系统远程关机策略"}# + 取得文件或其他对象的所有权限策略SeProfileSingleProcessPrivilege = @{operator="eq";value='*S-1-5-32-544';msg="取得文件或其他对象的所有权限策略"}# + 从网络访问此计算机策略SeNetworkLogonRight = @{operator="eq";value='*S-1-5-32-544,*S-1-5-32-545,*S-1-5-32-551';msg="从网络访问此计算机策略"}CheckResults = @()}Function F_SysUserPrivilegePolicy {# - 策略组用户权限配置$Hash = $SysUserPrivilegePolicy.Clone() # 巨坑之处foreach ( $Name in $Hash.keys) {if ( $Name.Equals("CheckResults")){ continue; }$Line = ($Config | Select-String $Name.toString()) -split " = "$Result = F_Tools -Key "SysUserPrivilegePolicy::$($Line[0])" -Value $Line[1] -Operator $SysUserPrivilegePolicy["$($Line[0])"].Operator -DefaultValue $SysUserPrivilegePolicy["$($Line[0])"].Value -Msg "策略组用户权限配置-$($SysUserPrivilegePolicy["$($Line[0])"].Msg)"$SysUserPrivilegePolicy['CheckResults'] += $Result}return $SysUserPrivilegePolicy['CheckResults']}## * 操作系统策略组安全选项权限配置检查 * ### - 组策略安全选项策略 - #$SysSecurityOptionPolicy = @{# - 帐户:使用空密码的本地帐户只允许进行控制台登录(启用),注意此设置不影响使用域帐户的登录。(0禁用|1启用)LimitBlankPasswordUse = @{operator="eq";value="MACHINE\System\CurrentControlSet\Control\Lsa\LimitBlankPasswordUse=4,1";msg="帐户-使用空密码的本地帐户只允许进行控制台登录(启用)"}# - 交互式登录: 不显示上次登录用户名值(启用)DontDisplayLastUserName = @{operator="eq";value="MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\DontDisplayLastUserName=4,1";msg="交互式登录-不显示上次登录用户名值(启用)"}# - 交互式登录: 登录时不显示用户名DontDisplayUserName = @{operator="eq";value="MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\DontDisplayUserName=4,1";msg="交互式登录: 登录时不显示用户名"}# - 交互式登录: 锁定会话时显示用户信息(不显示任何信息)DontDisplayLockedUserId = @{operator="eq";value="MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\DontDisplayLockedUserId=4,3";msg="交互式登录: 锁定会话时显示用户信息(不显示任何信息)"}# - 交互式登录: 无需按 CTRL+ALT+DEL(禁用)DisableCAD = @{operator="eq";value="MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\DisableCAD=4,0";msg="交互式登录-无需按CTRL+ALT+DEL值(禁用)"}# - 交互式登录:计算机不活动限制值为600秒或更少InactivityTimeoutSecs = @{operator="le";value="MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\InactivityTimeoutSecs=4,600";msg="交互式登录-计算机不活动限制值为600秒或更少"}# - 交互式登录: 计算机帐户阈值此策略设置确定可导致计算机重启的失败登录尝试次数MaxDevicePasswordFailedAttempts = @{operator="le";value="MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\MaxDevicePasswordFailedAttempts=4,10";msg="交互式登录: 此策略设置确定可导致计算机重启的失败登录尝试次数"}# - 交互式登录: 试图登录的用户的消息标题LegalNoticeCaption = @{operator="eq";value='MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\LegalNoticeCaption=1,"安全登陆"';msg="交互式登录: 试图登录的用户的消息标题"}# - 交互式登录: 试图登录的用户的消息文本LegalNoticeText = @{operator="eq";value='MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\LegalNoticeText=7,请谨慎的操作服务器中数据,您所有操作将被记录审计';msg="交互式登录: 试图登录的用户的消息文本"}# - Microsoft网络客户端: 将未加密的密码发送到第三方 SMB 服务器(禁用)EnablePlainTextPassword = @{operator="eq";value="MACHINE\System\CurrentControlSet\Services\LanmanWorkstation\Parameters\EnablePlainTextPassword=4,0";msg="Microsoft网络客户端-将未加密的密码发送到第三方 SMB 服务器(禁用)"}# - Microsoft网络服务器:暂停会话前所需的空闲时间数量值为15分钟或更少但不为0AutoDisconnect = @{operator="eq";value="MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters\AutoDisconnect=4,15";msg="Microsoft网络服务器-暂停会话前所需的空闲时间数量值为15分钟"}# - 网络安全: 再下一次改变密码时不存储LAN管理器哈希值(启用)NoLMHash = @{operator="eq";value="MACHINE\System\CurrentControlSet\Control\Lsa\NoLMHash=4,1";msg="网络安全-在下一次改变密码时不存储LAN管理器哈希值(启用)"}# - 网络访问: 不允许SAM账户的匿名枚举值为(启用)RestrictAnonymousSAM = @{operator="eq";value="MACHINE\System\CurrentControlSet\Control\Lsa\RestrictAnonymousSAM=4,1";msg="网络访问-不允许SAM账户的匿名枚举值为(启用)"}# - 网络访问:不允许SAM账户和共享的匿名枚举值为(启用)RestrictAnonymous = @{operator="eq";value="MACHINE\System\CurrentControlSet\Control\Lsa\RestrictAnonymous=4,1";msg="网络访问-不允许SAM账户和共享的匿名枚举值为(启用)"}# - 关机:设置确定是否可以在无需登录 Windows 的情况下关闭计算机(禁用)ClearPageFileAtShutdown = @{operator="eq";value="MACHINE\System\CurrentControlSet\Control\Session Manager\Memory Management\ClearPageFileAtShutdown=4,0";msg="关机-设置确定是否可以在无需登录 Windows 的情况下关闭计算机(禁用)"}"CheckResults" = @()}Function F_SysSecurityOptionPolicy {$Hash = $SysSecurityOptionPolicy.Clone() # 巨坑之处foreach ( $Name in $Hash.keys) {if ( $Name.Equals("CheckResults")){ continue; }$Flag = $Config | Select-String $Name.toString()$Value = $SysSecurityOptionPolicy["$($Name)"].Value -split ","if ( $Flag ) {$Line = $Flag -split ","$Result = F_Tools -Key "SysSecurityOptionPolicy::$($Name)" -Value $Line[1] -Operator $SysSecurityOptionPolicy["$($Name)"].Operator -DefaultValue $Value[1] -Msg "策略组安全选项配置-$($SysSecurityOptionPolicy["$($Name)"].Msg)"$SysSecurityOptionPolicy['CheckResults'] += $Result} else {$Result = @{"SysSecurityOptionPolicy::$($Name)"="[异常项]|未配置|$($Value[1])|策略组安全选项配置-$($SysSecurityOptionPolicy["$($Name)"].Msg)-【不符合】等级保护标准."}$SysSecurityOptionPolicy['CheckResults'] += $Result}}return $SysSecurityOptionPolicy['CheckResults']}## * 操作系统注册表相关配置检查函数 * ### - 注册表相关安全策略 -$SysRegistryPolicy = @{# + 屏幕自动保护程序ScreenSaveActive = @{regname="HKEY_CURRENT_USER\Control Panel\Desktop";name="ScreenSaveActive";operator="eq";value=1;msg="系统基配核查-屏幕自动保护程序策略"}# + 屏幕恢复时使用密码保护ScreenSaverIsSecure = @{regname="HKEY_CURRENT_USER\Control Panel\Desktop";name="ScreenSaverIsSecure";operator="eq";value=1;msg="系统基配核查-屏幕恢复时使用密码保护策略"}# + 屏幕保护程序启动时间ScreenSaveTimeOut = @{regname="HKEY_CURRENT_USER\Control Panel\Desktop";name="ScreenSaveTimeOut";operator="le";value=600;msg="系统基配核查-屏幕保护程序启动时间策略"}# + 禁止全部驱动器自动播放DisableAutoplay = @{regname="HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer";name="DisableAutoplay";regtype="DWord";operator="eq";value=1;msg="禁止全部驱动器自动播放"}NoDriveTypeAutoRun = @{regname="HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer";name="NoDriveTypeAutoRun";regtype="DWord";operator="eq";value=255;msg="禁止全部驱动器自动播放"}# - 检查关闭默认共享盘restrictanonymous = @{regname="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa";name="restrictanonymous";operator="eq";value=1;msg="系统网络基配核查-关闭默认共享盘策略"}restrictanonymoussam = @{regname="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa";name="restrictanonymoussam";regtype="DWord";operator="eq";value=1;msg="不允许SAM账户的匿名枚举值为(启用)"}# - 禁用磁盘共享(SMB)AutoShareWks = @{regname="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanserver\parameters";name="AutoShareWks";regtype="DWord";operator="eq";value=0;msg="关闭禁用默认共享策略-Server2012"}AutoShareServer = @{regname="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanserver\parameters";name="AutoShareServer";regtype="DWord";operator="eq";value=0;msg="关闭禁用默认共享策略-Server2012"}# - 系统、应用、安全、PS日志查看器大小设置(此处设置默认的两倍配置-建议一定通过日志采集平台采集系统日志比如ELK)EventlogSystemMaxSize = @{regname="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\System";name="MaxSize";operator="ge";value=41943040;msg="系统日志基配核查-系统日志查看器大小设置策略"}EventlogApplicationMaxSize = @{regname="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\Application";name="MaxSize";operator="ge";value=41943040;msg="系统日志基配核查-应用日志查看器大小设置策略"}EventlogSecurityMaxSize = @{regname="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\Security";name="MaxSize";operator="ge";value=41943040;msg="系统日志基配核查-安全日志查看器大小设置策略"}EventlogPSMaxSize = @{regname="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\Windows PowerShell";name="MaxSize";operator="ge";value=31457280;msg="系统日志基配核查-PS日志查看器大小设置策略"}# - 防火墙相关操作设置(开启、协议、服务)DomainEnableFirewall = @{regname='HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile';name='EnableFirewall';regtype="DWord";operator="eq";value=1;msg="开启域网络防火墙"}StandardEnableFirewall = @{regname='HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\SharedAccess\Parameters\FirewallPolicy\StandardProfile';name='EnableFirewall';regtype="DWord";operator="eq";value=1;msg="开启专用网络防火墙"}PPEnableFirewall = @{regname='HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\SharedAccess\Parameters\FirewallPolicy\PublicProfile';name='EnableFirewall';regtype="DWord";operator="eq";value=1;msg="开启公用网络防火墙"}# - 结果存储CheckResults=@()}Function F_SysRegistryPolicy {$Registry= $SysRegistryPolicy.Clone()foreach ( $item in $Registry.keys) {if ( $item -eq "CheckResults" ){ continue;}$Result = F_GetRegPropertyValue -Key $SysRegistryPolicy.$item.regname -Name $SysRegistryPolicy.$item.name -Operator $SysRegistryPolicy.$item.operator -DefaultValue $SysRegistryPolicy.$item.value -Msg $SysRegistryPolicy.$item.msg$SysRegistryPolicy['CheckResults'] += $Result}return $SysRegistryPolicy['CheckResults']}## * 操作系统服务及运行程序检查函数 * ##$SysProcessServicePolicy = @{"CheckResults"=@()}function F_SysProcessServicePolicy {# + 检测系统及用户开机启动项$SysAutoStart = Get-Item -Path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run'$SysAutoStart.GetValueNames() | % {$res += "$($_)#$($SysAutoStart.GetValue($_)) "}$Result = @{"SysProcessServicePolicy::SysAutoStart"=$res}$SysProcessServicePolicy['CheckResults'] += $Result$UserAutoStart = Get-Item -Path 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Run'$UserAutoStart.GetValueNames() | % {$res += "$($_)#$($SysAutoStart.GetValue($_)) "}$Result = @{"SysProcessServicePolicy::UserAutoStart"=$res}$SysProcessServicePolicy['CheckResults'] += $Result# + 否启用远程桌面服务$RDPStatus = (Get-Service -Name "TermService").Status# if ($RDP -eq "0" -and $RDPStatus -eq "Running" ) {# $Result = @{"SysProcessServicePolicy::RDPStatus"="当前系统【已启用】远程桌面服务."}# } else {# $Result = @{"SysProcessServicePolicy::RDPStatus"="当前系统【未启用】远程桌面服务."}# }if ($RDPStatus -eq "Running" ) {$Result = F_GetRegPropertyValue -Key 'HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server' -Name 'fDenyTSConnections' -Operator "eq" -DefaultValue 0 -Msg "是否将远程桌面服务禁用"} else {$Result = @{"SysProcessServicePolicy::RDPStatus"="当前系统【未启用】远程桌面服务."}}$SysProcessServicePolicy['CheckResults'] += $Result# - 否启用NTP服务来同步时钟# $NTP = F_GetReg -Key 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\NtpServer' -Name 'Enabled'# if ( $NTP -eq "1") {# $Result = @{"SysProcessServicePolicy::NtpServerEnabled"="[合格项]|$NTP|1|系统基础配置核查-启用NTP服务同步时钟策略-【符合】等级保护标准."}# } else {# $Result = @{"SysProcessServicePolicy::NtpServerEnabled"="[异常项]|$NTP|1|系统基础配置核查-启用NTP服务同步时钟策略-【不符合】等级保护标准."}# }$Result = F_GetRegPropertyValue -Key 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\NtpServer' -Name 'Enabled' -Operator "eq" -DefaultValue 1 -Msg "是否启用NTP服务同步时钟策略"$SysProcessServicePolicy['CheckResults'] += $Result# - 是否修改默认的远程桌面端口$RDP1 = Get-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\' | % {$_.GetValue("PortNumber")}$RDP2 = Get-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\Wds\rdpwd\Tds\tcp\' | % {$_.GetValue("PortNumber")}if ( $RDP1 -eq $RDP2 -and $RDP2 -ne "3389") {$Result = @{"SysProcessServicePolicy::RDPPort"="[合格项]|$RDP1|除3389以外的端口|系统基础配置核查-默认的远程桌面端口已修改-【符合】等级保护标准."}} else {$Result = @{"SysProcessServicePolicy::RDPPort"="[异常项]|$RDP1|除3389以外的端口|系统基础配置核查-默认的远程桌面端口未修改-【不符合】等级保护标准."}}$SysProcessServicePolicy['CheckResults'] += $Result}## * 操作系统安全检测函数 *## * 微软Windows服务器安全补丁列表信息 * #$Msrc_api = "https://api.msrc.microsoft.com/sug/v2.0/zh-CN/affectedProduct?%24orderBy=releaseDate+desc&%24filter=productFamilyId+in+%28%27100000010%27%29+and+severityId+in+%28%27100000000%27%2C%27100000001%27%29+and+%28releaseDate+gt+2020-01-14T00%3A00%3A00%2B08%3A00%29+and+%28releaseDate+lt+2021-05-22T23%3A59%3A59%2B08%3A00%29"$SysWSUSList = @{}$SysWSUSListId = @()$AvailableWSUSList = @{}function F_SysSecurityPolicy {# - 系统补丁验证if ( $MsrcUpdate -or ! (Test-Path -Path .\WSUSList.json) ) {$MSRC_JSON = F_UrlRequest -Msrc_api $Msrc_api$MSRC_JSON.value | % {$id = $_.id;$product = $_.product;$articleName = $_.kbArticles.articleName | Get-Unique;$fixedBuildNumber = $_.kbArticles.fixedBuildNumber | Get-Unique;$severity = $_.severity;$impact = $_.impact;$baseScore = $_.baseScore;$cveNumber = $_.cveNumber | Get-Unique;$releaseDate = $_.releaseDate$SysWSUSList += @{"$($id)"=@{"product"=$product;"articleName"=$articleName;"fixedBuildNumber"=$fixedBuildNumber;"severity"=$severity;"impact"=$impact;"baseScore"=$baseScore;"cveNumber"=$cveNumber;"releaseDate"=$releaseDate}}}while ($MSRC_JSON.'@odata.nextLink'.length) {$MSRC_JSON = F_UrlRequest -Msrc_api $MSRC_JSON.'@odata.nextLink'$MSRC_JSON.value | % {$id = $_.id;$product = $_.product;$articleName = $_.kbArticles.articleName | Get-Unique;$fixedBuildNumber = $_.kbArticles.fixedBuildNumber | Get-Unique;$severity = $_.severity;$impact = $_.impact;$baseScore = $_.baseScore;$cveNumber = $_.cveNumber | Get-Unique;$releaseDate = $_.releaseDate$SysWSUSList += @{"$($id)"=@{"product"=$product;"articleName"=$articleName;"fixedBuildNumber"=$fixedBuildNumber;"severity"=$severity;"impact"=$impact;"baseScore"=$baseScore;"cveNumber"=$cveNumber;"releaseDate"=$releaseDate }}}}Write-Host "[-] 已从 Microsoft 安全响应中心获取更新 $($MSRC_JSON.'@odata.count') 条补丁信息!" -ForegroundColor GreenWrite-Host "[-] 正在将获取的更新 $($MSRC_JSON.'@odata.count') 条补丁信息写入到本地 WSUSList.json 文件之中!" -ForegroundColor Green$SysWSUSList | ConvertTo-Json | Out-File WSUSList.json -Encoding utf8$SysWSUSListId = $SysWSUSList.keys$SysWSUSList.keys | ConvertTo-Json | Out-File WSUSListId.json -Encoding utf8} else {# 从本地读取JSON文件存储的补丁信息。if (Test-Path -Path .\WSUSList.json) {#$SysWSUSList = Get-Content -Raw -Encoding UTF8 .\WSUSList.json | ConvertFrom-Json$SysWSUSListId = Get-Content -Raw -Encoding UTF8 .\WSUSListId.json | ConvertFrom-JsonWrite-Host "[-] 已从本地 WSUSList.json 文件获得 $($SysWSUSListId.count) 条补丁信息!" -ForegroundColor Green} else {Write-Host "[-] 本地未能找到存放补丁信息的 WSUSList.json 文件! 请采用 -Update True 标记从Microsoft 安全响应中心获取更新" -ForegroundColor Redbreakexit}}# 获取当前系统版本可用的补丁列表$AvailableWSUSListId = @()if ($SysInfo.ProductType -eq "Client") {Write-Host "[-] Desktop Client" -ForegroundColor Grayforeach ($KeyName in $SysWSUSListId) {if(($SysWSUSList."$KeyName".product -match $SysInfo.ProductName) -and ($SysWSUSList."$KeyName".product -match $SysInfo.WindowsVersion) -and ($SysWSUSList."$KeyName".product -match ($SysInfo.CsSystemType -split " ")[0])) {if (($SysWSUSList."$KeyName".fixedBuildNumber -match $SysInfo.OsVersion) -or ($SysWSUSList."$KeyName".fixedBuildNumber.length -eq 0 )) {$AvailableWSUSList."$KeyName" = $SysWSUSList."$KeyName"$AvailableWSUSListId += "$KeyName"}}}} else {Write-Host "[-] Windows Server" -ForegroundColor Grayforeach ($KeyName in $SysWSUSListId) {if(($SysWSUSList."$KeyName".product -match $SysInfo.ProductName) -and ($SysWSUSList."$KeyName".product -match $SysInfo.ProductName)) {$AvailableWSUSList."$KeyName" = $SysWSUSList."$KeyName"$AvailableWSUSListId += "$KeyName"}}}Write-Host $SysInfo.ProductName $SysInfo.WindowsVersion ($SysInfo.CsSystemType -split " ")[0] $SysInfo.OsVersionWrite-Host "[-] 已从梳理出适用于当前 $($SysInfo.ProductType) 系统版本的 $($AvailableWSUSList.count) 条补丁信息!`n" -ForegroundColor Green# 已安装的补丁$InstallWSUSList = @{}$msg = @()foreach ($id in $AvailableWSUSListId) {if( $SysInfo.'Hotfix(s)' -match $AvailableWSUSList."$id".articleName ) {$InstallWSUSList."$id" = $SysWSUSList."$id"$msg += "[+]" + $SysWSUSList."$id".product + $SysWSUSList."$id".fixedBuildNumber + " " + $SysWSUSList."$id".articleName + "(" + $SysWSUSList."$id".cveNumber + ")" + $SysWSUSList."$id".severity + $SysWSUSList."$id".baseScore + "`n"}}Write-Host "[-] $($SysInfo.'Hotfix(s)') ,共 $($AvailableWSUSList.count) 条漏洞补丁信息!`n$($msg)" -ForegroundColor Green# 未安装的补丁$NotInstallWSUSList = @{}$msg = @()foreach ($id in $AvailableWSUSListId) {if(-not($InstallWSUSList."$id")) {$NotInstallWSUSList."$id" = $SysWSUSList."$id"$msg += "[+]" + $SysWSUSList."$id".product + $SysWSUSList."$id".fixedBuildNumber + " " + $SysWSUSList."$id".articleName + "(" + $SysWSUSList."$id".cveNumber + ")" + $SysWSUSList."$id".severity + $SysWSUSList."$id".baseScore + "`n"}}Write-Host "[-] 未安装 $($NotInstallWSUSList.count) 条漏洞补丁信息,共 $($AvailableWSUSList.count) 条漏洞补丁信息!`n$($msg)" -ForegroundColor red}function Get-BasicInfo{$scanTime=Get-date -Format 'yyyy-M-d H:m:s'$hostname = hostname$osVersion=Get-WmiObject -Class Win32_OperatingSystem | Select-Object -ExpandProperty Caption$ipList = ""$macaddr = ""foreach($line in ipconfig /all|Select-String -Pattern "^\s*IPv4"){$line=$line.ToString().split(":")[1].replace("(","\(").replace(")","\)")$context = (ipconfig /all |Select-String -Pattern $line -Context 10,0).Context[0]if ($context.Precontext|Select-String "VMware" -Quiet){continue}foreach ($lline in $context.Precontext.split("\n")){#Write-Host $llineif ($lline.ToString().contains("Physical")){#Write-Host $lline.ToString() dddd$macaddr = $macaddr + $lline.ToString().split(":")[1].Trim() + ";"break}}$ipList = $ipList + $line.ToString().split("\")[0].trim() + ";"}Write-Host scanTime:$scanTimeWrite-Host osVersion:$osVersionWrite-Host hostname:$hostnameWrite-Host macaddr: $macaddrWrite-Host ipList : $ipList$basic_info="{""scanTime"":""$scanTime"",""osVersion"":""$osVersion"",""hostname"":""$hostname"",""macaddr"":""$macaddr"",""ipList"":""$ipList""}"return $basic_info}#2022年9月12日新增功能区域#搜集所有的KB补丁function Get-CollectKB(){$KBArray = @()$KBArray = Get-HotFix|ForEach-Object {$_.HotFixId}$CollectKB = $KBArray|ConvertTo-Jsonreturn $CollectKB}#自动运行程序数量获取function Get-SystemSecureCheckRes{$key="HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer"$name="NoDriveTypeAutoRun"#$autoRunRes=(Get-ItemProperty hklm:\software\wow6432node\microsoft\windows\currentversion\uninstall\* | select-object DisplayName, InstallDate).$name$autoRunRes=(Get-ItemProperty -Path "Registry::$key" -ErrorAction:SilentlyContinue).$nameif(-not $autoRunRes){$autoRunRes="False"}$systemsecure_check_res="{""autoRunRes"":""$autoRunRes""}"return $systemsecure_check_res}#远程端口获取测试(虽然鸡肋,但我还是要写出来,就是玩儿!)function Get-PortSecureCheckRes{$key="HKLM\SYSTEM\CurrentControlSet\Control\Terminal server\WinStations\RDP-Tcp"$name="Portnumber"$rdpPort=(Get-ItemProperty -Path "Registry::$key" -ErrorAction:SilentlyContinue).$nameif($rdpPort -eq "3389"){Write-Host "[-] RDPPort should not be 3389" -ForegroundColor Red}$portsecure_check_res="{""rdpPort"":""$rdpPort""}"return $portsecure_check_res}#2022年9月15号新增功能区域#查询系统中所有的用户信息$OtherUserCheck = @{}function F_OtherUserPolicy {$UserOther = Get-WmiObject -Class Win32_UserAccount -Filter "Name='$env:username' and Domain='$env:userdomain'" | Select-Object *$OtherUserCheck += @{"UserOther"="$($UserOther)"}return $OtherUserCheck}#获取系统时间function F_Date {$Date = Get-Date$DateCheck += @{"Date"="$($Date)"}return $DateCheck}#获取NTP时钟设备function F_NTP {$NTP = w32tm /query /status | Format-Table | Out-String$NTPCheck += @{"NTP"="$($NTP)"}return $NTPCheck}#获取系统服务function F-Service {$Service = Get-Service$ServiceCheck += @{"Service"="$($Service)"}return $ServiceCheck}## * 杂类检测函数 *#$OtherCheck = @{}function F_OtherCheckPolicy {# - 当前系统已安装的软件$Product = Get-WmiObject -Class Win32_Product | Select-Object -Property Name,Version,IdentifyingNumber | Sort-Object Name | Out-String$OtherCheck += @{"Product"="$($Product)"}# - 当前系统最近访问文件或者目录$Recent = (Get-ChildItem ~\AppData\Roaming\Microsoft\Windows\Recent).Name$OtherCheck += @{"Recent"="$($Recent)"}return $OtherCheck}function Main() {<#.SYNOPSISmain 函数程序执行入口.DESCRIPTION调用上述编写的相关检测脚本.EXAMPLEmain#>$ScanStartTime = Get-date -Format 'yyyy-M-d H:m:s'F_Logging -Level Info -Msg "[*] Windows Server 安全配置策略基线检测脚本已启动."F_Logging -Level Info -Msg "[*] 脚本执行: $($Executor), 是否在线拉取微软安全中心的服务器安全补丁列表信息: $($MsrcUpdate)`n"# 1.判断当前运行的powershell终端是否管理员执行F_Logging -Level Info -Msg "[-] 正在检测当前运行的PowerShell终端是否管理员权限...`n"$flag = F_IsCurrentUserAdminif (!($flag)) {F_Logging -Level Error -Msg "[*] 脚本执行发生错误,请使用管理员权限运行该脚本..例如: Start-Process powershell -Verb runAs...."F_Logging -Level Warning -Msg "[*] 正在退出执行该脚本......"return}F_Logging -Level Info -Msg "[*] PowerShell 管理员权限检查通过...`n"# 2.当前系统策略配置文件导出 (注意必须系统管理员权限运行)F_Logging -Level Info -Msg "[-] 正在导出当前系统策略配置文件 config.cfg......`n"secedit /export /cfg config.cfg /quietstart-sleep 3if ( -not(Test-Path -Path config.cfg)) {F_Logging -Level Error -Msg "[*] 当前系统策略配置文件 config.cfg 不存在,请检查......`n"F_Logging -Level Warning -Msg "[*] 正在退出执行该脚本......"return} else {Copy-Item -Path config.cfg -Destination config.cfg.bak -Force}$Config = Get-Content -path config.cfg# 3.系统相关信息以及系统安全组策略检测echo "————————————————————————" >> $file_nameecho "当前系统时间" >> $file_nameF_Logging -Level Info -Msg "[-] 当前系统时间"$DateCheck = F_Date$DateCheck >> $file_nameecho "————————————————————————" >> $file_nameecho "系统NTP时钟设置" >> $file_nameF_Logging -Level Info -Msg "[-] 系统NTP时钟设置"$NTPCheck = F_NTP$NTPCheck >> $file_nameecho "————————————————————————" >> $file_nameecho "IP地址查询" >> $file_nameF_Logging -Level Info -Msg "[-] IP地址查询"ipconfig >> $file_nameecho "————————————————————————" >> $file_nameecho "当前自动运行程序进程数量信息一览" >> $file_nameF_Logging -Level Info -Msg "[-] 当前自动运行程序进程数量信息一览"$systemsecure_check_res = Get-SystemSecureCheckRes$systemsecure_check_res >> $file_nameecho "————————————————————————" >> $file_nameecho "远程端口获取测试" >> $file_nameF_Logging -Level Info -Msg "[-] 当前远程端口获取信息一览"$portsecure_check_res = Get-PortSecureCheckRes$portsecure_check_res >> $file_nameecho "————————————————————————" >> $file_nameecho "IP地址查询" >> $file_nameF_Logging -Level Info -Msg "[-] IP地址查询"ipconfig >> $file_nameecho "————————————————————————" >> $file_nameecho "系统安装的修补程序一览" >> $file_nameF_Logging -Level Info -Msg "[-] 系统安装的修补程序一览"$CollectKB = Get-CollectKB$CollectKB >> $file_name#$SysNetAdapter#echo "————————————————————————" >> $file_name#echo "当前***信息一览" >> $file_name#F_Logging -Level Info -Msg "[-] 当前***信息一览"#$secInfoArray = Get-SecInfo#$secInfoArray >> $file_nameecho "————————————————————————" >> $file_nameecho "当前运行端口信息一览" >> $file_nameF_Logging -Level Info -Msg "[-] 当前运行端口信息一览"netstat -ano >> $file_nameecho "————————————————————————" >> $file_nameecho "系统服务运行一览" >> $file_nameF_Logging -Level Info -Msg "[-] 系统服务运行一览"$ServiceCheck = F-Service$ServiceCheck >> $file_name#echo "————————————————————————" >> $file_name#echo "当前默认共享信息一览" >> $file_name#F_Logging -Level Info -Msg "[-] 当前默认共享信息一览"#net share >> $file_nameecho "————————————————————————" >> $file_nameecho "当前系统账户信息一览" >> $file_nameF_Logging -Level Info -Msg "[-] 当前系统账户信息一览"$SysAccount = F_SysAccount$SysAccount >> $file_nameecho "————————————————————————" >> $file_nameecho "系统中所有的用户信息一览" >> $file_nameF_Logging -Level Info -Msg "[-] 系统中所有的用户信息一览"$OtherUserCheck = F_OtherUserPolicy$OtherUserCheck >> $file_nameecho "————————————————————————" >> $file_nameecho "当前系统安全策略信息一览" >> $file_nameF_Logging -Level Info -Msg "[-] 当前系统安全策略信息一览"$SysAccountPolicy.CheckResults = F_SysAccountPolicy >> $file_name$SysEventAuditPolicy.CheckResults = F_SysEventAuditPolicy >> $file_name$SysUserPrivilegePolicy.CheckResults = F_SysUserPrivilegePolicy >> $file_name$SysSecurityOptionPolicy.CheckResults = F_SysSecurityOptionPolicy >> $file_name$SysRegistryPolicy.CheckResults = F_SysRegistryPolicy >> $file_name$SysProcessServicePolicy.CheckResults = F_SysProcessServicePolicy >> $file_nameecho "————————————————————————" >> $file_nameecho "当前系统杂类信息一览" >> $file_nameF_Logging -Level Info -Msg "[-] 当前系统杂类信息一览"$OtherCheck = F_OtherCheckPolicy$OtherCheck.Values >> $file_name#F_Logging -Level Info -Msg "[-] 当前系统安全补丁情况信息一览"# 4.程序执行完毕$ScanEndTime = Get-date -Format 'yyyy-M-d H:m:s'F_Logging -Level Info -Msg "- Windows Server 安全配置策略基线检测脚本已执行完毕,详细见桌面$ip.txt文件`n开始时间:${ScanStartTime}`n完成时间: ${ScanEndTime}"}Main
执行结果如下所示(前后部分截图):
结语:如今各个公司对于等保安全越来越重视,一个方便快捷的自检方式就是通过脚本检测,大家可以自己复制粘贴代码到自己本地环境执行自检看看。
更多精彩
关注公众号「浩道Linux」
浩道Linux,专注于Linux系统的相关知识、网络通信、网络安全、Python相关知识以及涵盖IT行业相关技能的学习,理论与实战结合,真正让你在学习工作中真正去用到所学。同时也会分享一些面试经验,助你找到高薪offer,让我们一起去学习,一起去进步,一起去涨薪!期待您的加入~~~关注回复“资料”可免费获取学习资料(含有电子书籍、视频等)。
浩道Linux
浩道,专注工作与实践的一名IT民工。本号主要分享linux,python,网络通信、安全等相关IT干货。相聚在此,通过分享知识与经验,一起成长。
公众号
喜欢的话,记得点“赞”和“在看”哦
收录于合集 #linux学习
325个上一篇掌握这些Nginx常用配置与命令,关键时候不求人!
浩道Linux
写下你的留言
精选留言
-
朝花夕拾广东
已无更多数据




![[666]](https://res.wx.qq.com/mpres/zh_CN/htmledition/comm_htmledition/images/pic/common/pic_blank.gif)