记一次尝试性的CCB积分页面登录(一)
1.打开CCB积分登录页
http://jf.ccb.com/exchangecenter/member/memberBegin.jhtml?redirectUrl=687474703a2f2f6a662e6363622e636f6d2f696e6465782e68746d6c
进行登录,发现点击登录后跳转的第一个链接为http://login.ccb.com/tran/WCCMainPlatV5?CCB_IBSVersion=V5&SERVLET_NAME=WCCMainPlatV5
格式如下
POST http://login.ccb.com/tran/WCCMainPlatV5?CCB_IBSVersion=V5&SERVLET_NAME=WCCMainPlatV5 HTTP/1.1 Host: login.ccb.com Connection: keep-alive Content-Length: 184 Pragma: no-cache Cache-Control: no-cache Upgrade-Insecure-Requests: 1 Origin: http://login.ccb.com Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://login.ccb.com/tran/WCCMainPlatV5?CCB_IBSVersion=V5&SERVLET_NAME=WCCMainPlatV5&TXCODE=D15001&persEnterprise=0&sid=60000&rid=667247183919492001&flagCenter=1&errcode=0060Z1109001&errInfo=%E8%BE%93%E5%85%A5%E4%BF%A1%E6%81%AF%E6%9C%89%E8%AF%AF%EF%BC%8C%E8%AF%B7%E9%87%8D%E8%AF%95.. Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: WCCTC=934727482_391736417_958468229; tranCCBIBS1=UuEFKzKzthz7iFGzTA1OiLZmrdTazL7m9tt%2CVLonv9irV8XtYu5jIjkm7txeLQWnpdayrT5ohdy6RQfmX9YmOLLmJdHyfZDgwu; ccbcustomid=8b4f5912372b6e96PrsA5zVwKuKl8d9s6Csh1646987082743wB86SiGpGkr7qlaNaCPUc44af89bdff0db8acdf941cc37f59ccb; ccbsessionid=thxfXzj5UxAJgeq04ab6bd94a9e-20220311162442; cityName=%E4%B8%B4%E6%B2%82%E5%B8%82; cityCode=371300; bankName=%E5%B1%B1%E4%B8%9C%E7%9C%81%E5%88%86%E8%A1%8C; bankCode=370000000; cityCodeFlag=2; lastLoginTime=; center123=2; zg_did=%7B%22did%22%3A%20%2217f78147cf059a-00f9472b8cda2f-977173c-1fa400-17f78147cf1750%22%7D; zg_002714230c264ddda7d94375a4d23e40=%7B%22sid%22%3A%201646987082996%2C%22updated%22%3A%201646987217164%2C%22info%22%3A%201646987082998%2C%22superProperty%22%3A%20%22%7B%7D%22%2C%22platform%22%3A%20%22%7B%7D%22%2C%22utm%22%3A%20%22%7B%7D%22%2C%22referrerDomain%22%3A%20%22login.ccb.com%22%7D; appUniCode=90FE302D66A0ACCA81CE2A506E35B45AC4C81ECE2E724E7EE02DE02FD3595DF057F7CE93E54C87C3; ticketCmp=; custNameCmp=; userTypeCmp=; lastLoginTimeCmp=; custIdCmp=; cloudDSInfo=5DB64935EEA2F8714A5E40AE2405D6803509C4192CB2F0BBE0A1FBDC4D8FDE392BE9F878AAE629819D5E2D9BB8FFCC39; m_user_bitmap=00000000003700000000; DsCustInfo=dong9993; dsloginTypeTips=1; ticket=; cs_cid=; custName=; userType=; ReturnUrl=687474703a2f2f6a662e6363622e636f6d2f696e6465782e68746d6c; null=!rynGbYuljJRoVbWgKYCvKuj9oaHnn+eUOOTEAuA9U4l+qWbFvgbO+uFiLHGnj1Ddpsuzt03vINBwmA==; JSESSIONID=Nyd4K_qLfVMyGAjI7M6KQFFJnuKLFBJjlkPlDQorttHVk7cT8jl6!-1613961330; INFO=nj9d|YisNU; tranFAVOR=Dw2B3es27QjgNXYr7vj0NSY%2C7tj7N0YU7YjYMzS4oafWcSMJotjIMPSipQ.V4vOypOfd4ONgqBfeoLVFoUv7APQYqCv9kjM4olfhh8Yn7bjzNdAC31SDVEDcqOvaA1VdoLTYMabD6Q8tzf
custname=(脱敏)&custpwd=O44%2B%7DGy&sub=&CCB_PWD_MAP_GIGEST=S000001083466567%7Ccustpwd&CCB_PWD_ENCKEY=&BRANCHID=*&TXCODE=D15002&KEY=&sid=60000&rid=667247183919492001&persEnterprise=0 HTTP/1.1 200 OK Date: Fri, 11 Mar 2022 08:51:14 GMT Server: Apache Content-Length: 3659 Set-Cookie: tranCCBIBS1=KbEmgSJc6cmplFXU%2CLmg5QkssyzC0fQOssjIoARFt5Dgx7Kl8i1B1kTa5Mj6kHW7tKjF4WZKuBjlAEWZtNTcwWZcsPjO0JfGI7oMeq;domain=.ccb.com;HttpOnly; Set-Cookie: tranFAVOR=CxbAdvDU6gikMvXZ6qiTM8XK6NikMb.a22RDU7CDpvu1.RUInoS8M2XD6qe2z1LJnSexbwLN6ke5zIRhoqOojoPzoLOHfmTVn7OY.QMmpWugrXUdnN%2C8bbLanTy4MFXX6ahRsoKi2JBW3iUDpNuH.0Op6pbrafaQ18x70d;domain=.ccb.com;path=/;HttpOnly; Set-Cookie: appUniCode=90FE302D66A0ACCA81CE2A506E35B45AC4C81ECE2E724E7EE02DE02FD3595DF057F7CE93E54C87C3; domain=ccb.com; expires=Sun, 10-Apr-2022 10:51:14 CEST; path=/ Set-Cookie: ticket=; domain=ccb.com; path=/ Set-Cookie: cs_cid=; domain=ccb.com; path=/ Set-Cookie: custName=; domain=ccb.com; path=/ Set-Cookie: userType=; domain=ccb.com; path=/ Set-Cookie: lastLoginTime=; domain=ccb.com; path=/ Set-Cookie: ticket=Nyd4K_qLfVMyGAjI7M6KQFFJnuKLFBJjlkPlDQorttHVk7cT8jl6!-1613961330!16469886224751646988674758; domain=ccb.com; path=/ Set-Cookie: cs_cid=1143622828; domain=ccb.com; path=/ Set-Cookie: custName=(脱敏); domain=ccb.com; path=/ Set-Cookie: userType=1000000000000000; domain=ccb.com; path=/ Set-Cookie: ticketCmp=; domain=ccb.com; path=/ Set-Cookie: custNameCmp=; domain=ccb.com; path=/ Set-Cookie: userTypeCmp=; domain=ccb.com; path=/ Set-Cookie: lastLoginTimeCmp=; domain=ccb.com; path=/ Set-Cookie: custIdCmp=; domain=ccb.com; path=/ Set-Cookie: cloudDSInfo=5DB64935EEA2F8714A5E40AE2405D6803509C4192CB2F0BBE0A1FBDC4D8FDE39AE186F831893F277B8AC91CCE6917B35; domain=ccb.com; path=/ Set-Cookie: m_user_bitmap=00000000003700000000; domain=ccb.com; expires=Sun, 10-Apr-2022 10:51:14 CEST; path=/ Set-Cookie: WCCTC=934727482_391736417_958468229; expires=Wed, 07-Sep-2022 10:51:14 CEST Set-Cookie: INFO=nj9d|YisNh; path=/ Cache-Control: max-age=0 Expires: Fri, 11 Mar 2022 08:51:14 GMT Vary: Accept-Encoding Keep-Alive: timeout=5, max=91 Connection: Keep-Alive Content-Type: text/html; charset=UTF-8
观察发现
Cookie
custpwd
CCB_PWD_MAP_GIGEST
TXCODE
sid
rid
这些字段我们需要去理解,我们首先要做的是找到这些字段是如何生成的。
2.搜索登录页
我们重新载入登录页,查看登录页的接口
发现有这样一条请求已经用到了这三个字段
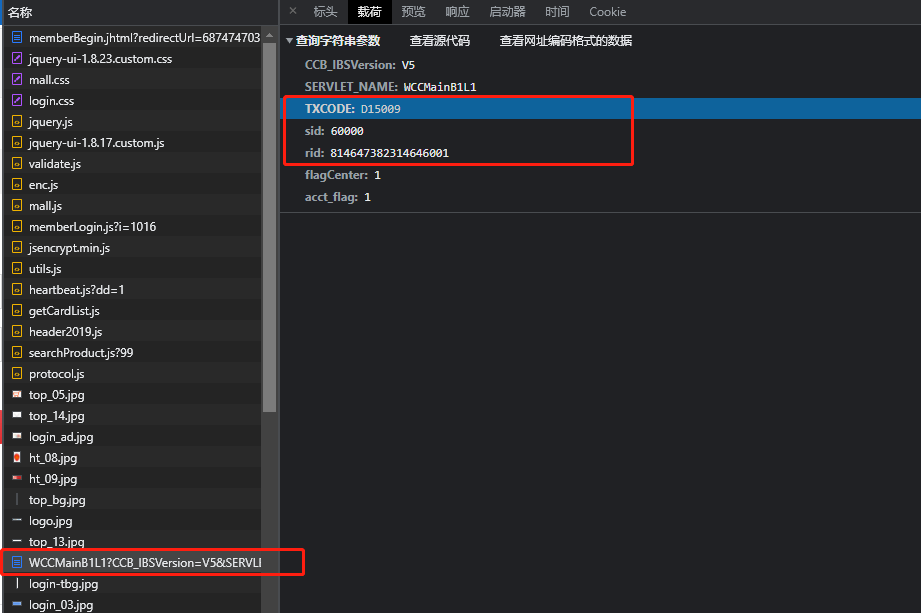
观察登录信息,发现这里的三个参数即是登录时的参数,。那么我们需要继续反向追溯,追溯此文件中的参数是如何生成的。
3.二次追溯
通过多次登录观察发现,TXCODE在本文件的回传中变为D15002,sid为定值60000,这里只分析rid。
在此链接之前的所有链接中查找,在第一个接口中找到了此字段的值
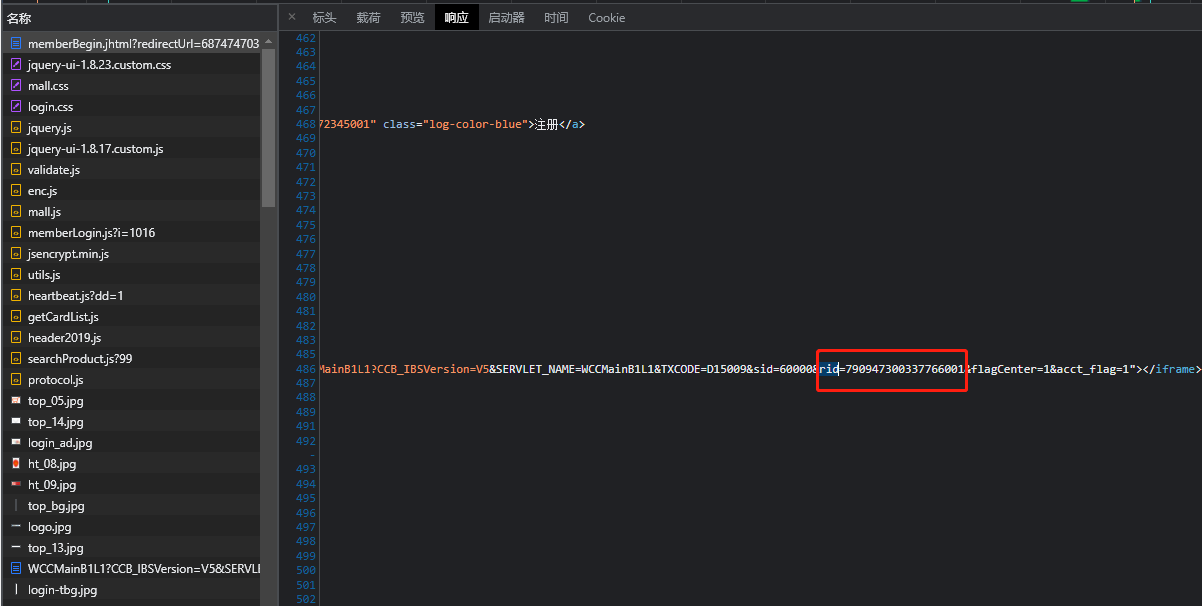
官方逻辑:请求登录网址,返回TXCODE、sid和rid,使用TXCODE、sid和rid请求新网址,返回登录时需要用到的TXCODE、sid和rid,但是我们经过分析得知TXCODE、sid为定值,因此只通过登陆网址获取rid即可。
4、密码加密方式
接下来寻找密码加密方式,即custpwd和CCB_PWD_MAP_GIGEST的生成方式。
因为CCB_PWD_MAP_GIGEST比较好寻找,我们先找他,在源码中搜索CCB_PWD_MAP_GIGEST并分析,找到了这样一段代码
var ifUseYinshe = "1"; var jiami = 0; var keyjiami = 0; var keyjiamiName = "0"; function jiamiMimas(mimaName) { keyjiamiName = "," + keyjiamiName; var everyMimaName = mimaName.split(','); for (var j = 0; j < everyMimaName.length; j++) { if (keyjiamiName.indexOf("," + everyMimaName[j] + ",") != -1) { jiamiEveryMimas(everyMimaName[j]); } } if (ifUseYinshe == 1) { var ccbPwbMapGigest = document.getElementById("CCB_PWD_MAP_GIGEST"); var jimaPass = ''; for (var n = 0; n < everyMimaName.length; n++) { jimaPass = document.getElementById(everyMimaName[n]); if (n == 0) { ccbPwbMapGigest.value = a + "|" + jimaPass.name; } else { ccbPwbMapGigest.value = ccbPwbMapGigest.value + "," + jimaPass.name; } } } keyjiamiName = "0"; }
并且得知了mimaName为定值“custpwd”,a为本文件中的值
var a = 'S000001380001751';
经过组合就得到了 CCB_PWD_MAP_GIGEST=S000001380001751|custpwd
本文件是通过链接 http://login.ccb.com/tran/WCCMainPlatV5?CCB_IBSVersion=V5&SERVLET_NAME=WCCMainPlatV5&TXCODE=D15001&persEnterprise=&sid=60000&rid=638507107288313001&flagCenter=1&isDirect=2
获取的,此链接中的参数值我们都已经知道了。
通过观察,发现在输入密码后执行了keyjiami函数
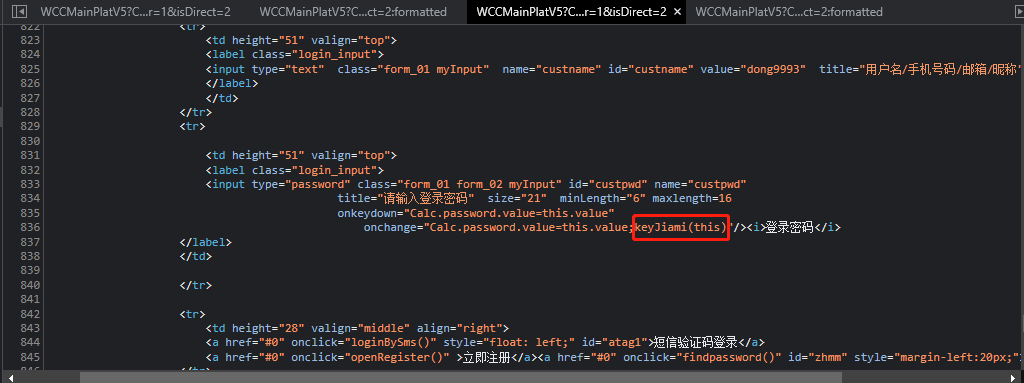
此函数生成了CCB_PWD_MAP_GIGEST和custpwd,CCB_PWD_MAP_GIGEST上步已经得到了,所以只看custpwd
在点击登陆后,此函数生成了加密密码
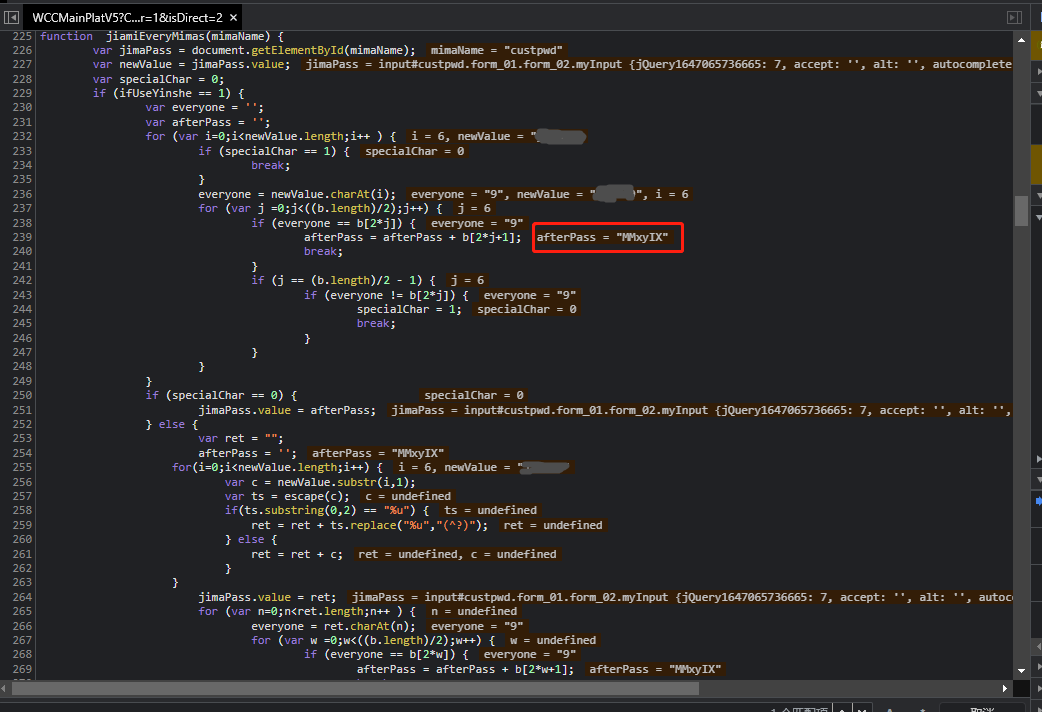
并且因为每次的b值不同,生成的加密密码也是不同的

所以,1、将函数提取出来保存为js文件;2、通过此接口获取所有的b值。然后重新运行生成加密密码
可以看到,结果是一致的。
Cookie
custpwd 完成
CCB_PWD_MAP_GIGEST 完成
TXCODE 完成
sid 完成
rid 完成


 浙公网安备 33010602011771号
浙公网安备 33010602011771号