centos上搭建dns解析服务器
使用的系统为centos6.5 64位
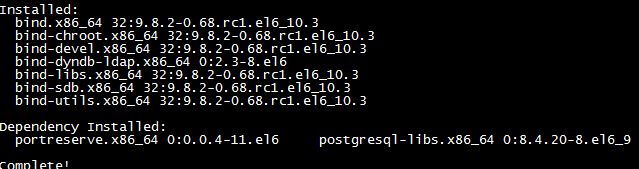
1.通过yum安装所需的BIND软件
yum -y install bind*
安装完成。
2.打开DNS服务的主配置文件:
vim /etc/named.conf
以下是主配置文件中的 “全局配置” ,更改标红部分
// // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // options { listen-on port 53 { 127.0.0.1; }; //监听地址和端口,此处改为any listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { localhost; }; //允许访问本dns服务器的网段,此处改为any recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";
配置区域文件,添加自己的域名,定义正向解析和反向解析信息
vi /etc/named.rfc1912.zones
此处我以添加test.com为例
test.com.zone为正向解析配置文件,存储路径为/var/named/
test.com.local为反向解析配置文件,存储路径为/var/named/
在末尾添加test.com.zone
1 // named.rfc1912.zones: 2 // 3 // Provided by Red Hat caching-nameserver package 4 // 5 // ISC BIND named zone configuration for zones recommended by 6 // RFC 1912 section 4.1 : localhost TLDs and address zones 7 // and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt 8 // (c)2007 R W Franks 9 // 10 // See /usr/share/doc/bind*/sample/ for example named configuration files. 11 // 12 13 zone "localhost.localdomain" IN { 14 type master; 15 file "named.localhost"; 16 allow-update { none; }; 17 }; 18 // 19 // See /usr/share/doc/bind*/sample/ for example named configuration files. 20 // 21 22 zone "localhost.localdomain" IN { 23 type master; 24 file "named.localhost"; 25 allow-update { none; }; 26 }; 27 // named.rfc1912.zones: 28 // 29 // Provided by Red Hat caching-nameserver package 30 // 31 // ISC BIND named zone configuration for zones recommended by 32 // RFC 1912 section 4.1 : localhost TLDs and address zones 33 // and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt 34 // (c)2007 R W Franks 35 // 36 // See /usr/share/doc/bind*/sample/ for example named configuration files. 37 // 38 39 zone "localhost.localdomain" IN { 40 type master; 41 file "named.localhost"; 42 allow-update { none; }; 43 }; 44 45 zone "localhost" IN { 46 type master; 47 file "named.localhost"; 48 allow-update { none; }; 49 }; 50 51 zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN { 52 type master; 53 file "named.loopback"; 54 allow-update { none; }; 55 }; 56 57 zone "1.0.0.127.in-addr.arpa" IN { 58 type master; 59 file "named.loopback"; 60 allow-update { none; }; 61 }; 62 63 zone "0.in-addr.arpa" IN { 64 type master; 65 file "named.empty"; 66 allow-update { none; }; 67 }; 68 69 zone "test.com" IN { 70 type master; 71 file "test.com.zone"; 72 allow-update { none; }; 73 };
进入/var/named/目录,创建正向解析配置文件和反向解析配置文件
cp -p named.localhost test.com.zone //正向解析文件 cp -p named.localhost test.com.local //反向解析文件
修改正向解析配置文件,添加解析记录。 #此处添加www和ftp两条A记录
$TTL 1D @ IN SOA @ rname.invalid. ( //rname.invalid. 此处改为test.com 0 ; serial //0改为1 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS @ //添加记录 A 127.0.0.1 AAAA ::1
$TTL 1D @ IN SOA test.com. mail.test.com ( //test.com为解析的主域名 mail为邮箱 1 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ IN NS ns.test.com. //域名服务器记录,和本机对应 ns IN A 192.168.2.32 //主机记录 www IN A 192.168.2.31 //主机记录 ftp IN A 192.168.2.31 //主机记录
vi /etc/hosts //添加主机名和上一步域名服务器记录对应
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 ns.test.com 192.168.2.32
设置服务器开机自动启动dns服务
service named start
chkconfig named on
更改防火墙允许53端口
# Firewall configuration written by system-config-firewall # Manual customization of this file is not recommended. *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A INPUT -m state --state NEW -m tcp -p tcp --dport 22 -j ACCEPT
-A INPUT -m state --state NEW -m udp -p udp --dport 53 -j ACCEPT -A INPUT -m state --state NEW -m tcp -p tcp --dport 53 -j ACCEPT -A INPUT -j REJECT --reject-with icmp-host-prohibited -A FORWARD -j REJECT --reject-with icmp-host-prohibited COMMIT
重启防火墙,查看信息
//重启防火墙
service iptables restart
//查看防火墙信息
[root@localhost named]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:53
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 state NEW udp dpt:53
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@localhost named]#
更改客户端dns服务器地址为192.168.2.32,解析域名成功
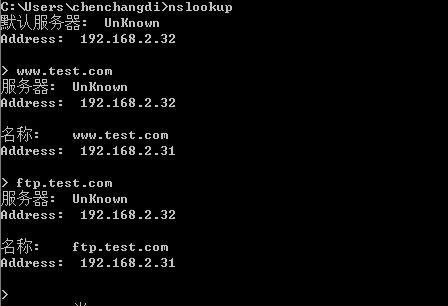
反向解析在test.com.local配置,此处只做正向解析。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号