OtterCTF 2018(复现赛)
What the password?
you got a sample of rick's PC's memory. can you get his user password?
先查看内存镜像的基本信息
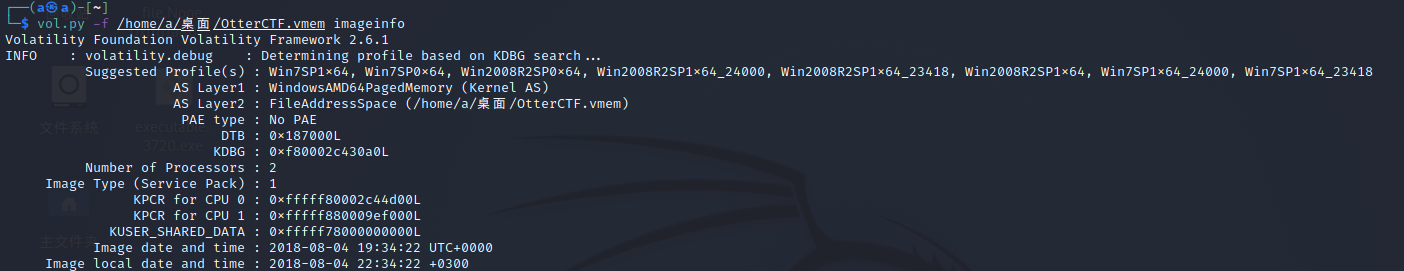
用mimikatz直接提取密码,也可以知道用户名为Rick,PC名为WIN-LO6FAF3DTFE
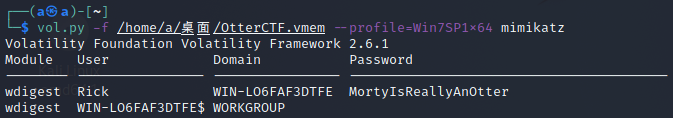
NSSCTF{MortyIsReallyAnOtter}
General Info
Let's start easy - whats the PC's name and IP address?
用netscan查看网络连接状况,来找到IP地址
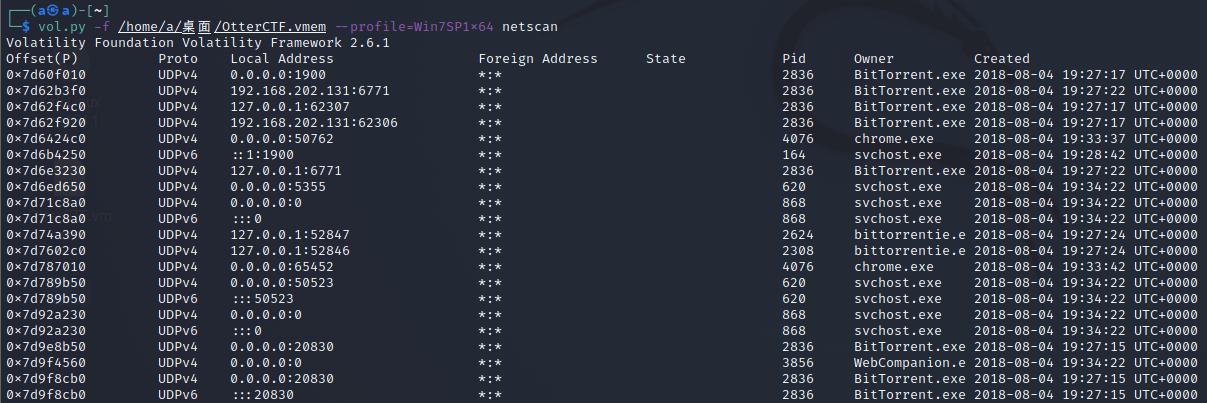
PC名在上面已经找到了
NSSCTF{WIN-LO6FAF3DTFE-192.168.202.131}
Play Time
Rick just loves to play some good old videogames. can you tell which game is he playing? whats the IP address of the server?
在netscan里找连接外网的进程,找到LunarMS.exe,这是一个游戏
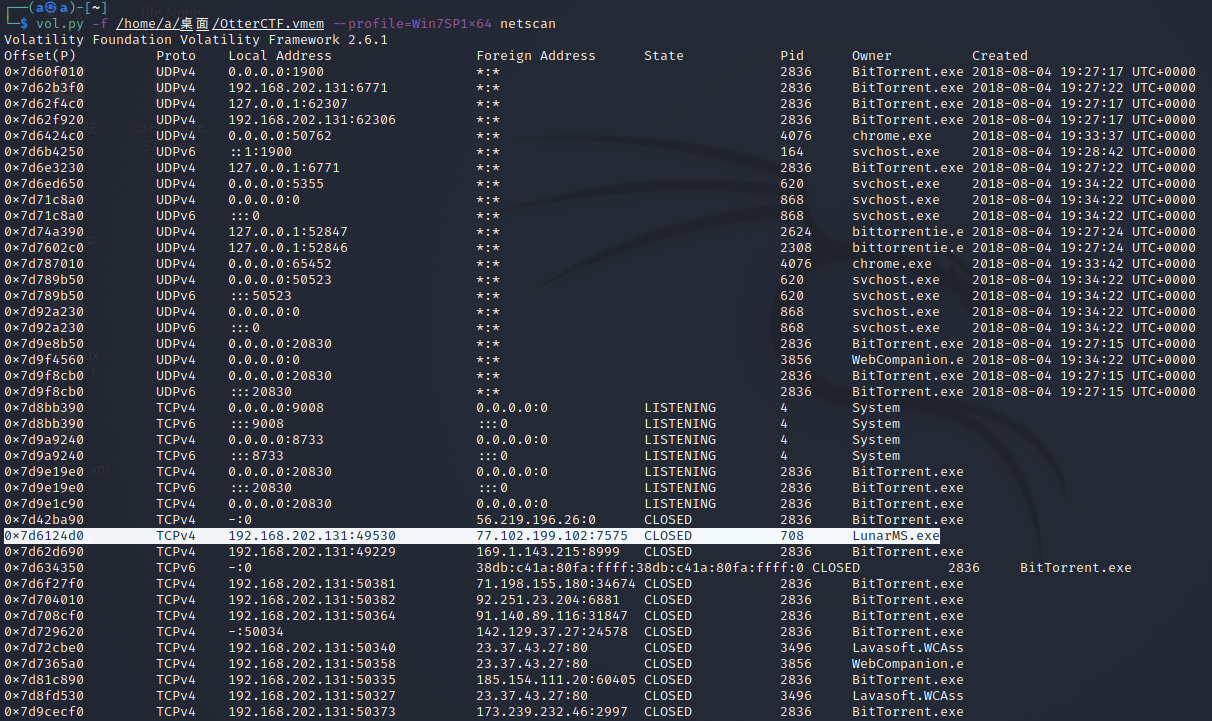
NSSCTF{LunarMS-77.102.199.102}
Name Game
We know that the account was logged in to a channel called Lunar-3. what is the account name?
用mendump把LunarMS.exe保存下来
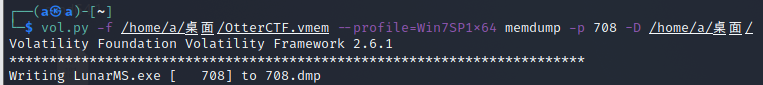
然后用strings搜索进程中Lunar-3前后五行的字符
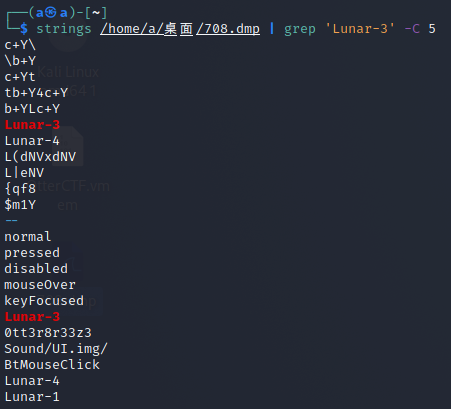
NSSCTF{0tt3r8r33z3}
Name Game 2
From a little research we found that the username of the logged on character is always after this signature: 0x64 0x??{6-8} 0x40 0x06 0x??{18} 0x5a 0x0c 0x00{2} What's rick's character's name?
把708.dmp用010打开,然后去找十六进制的5A0C00
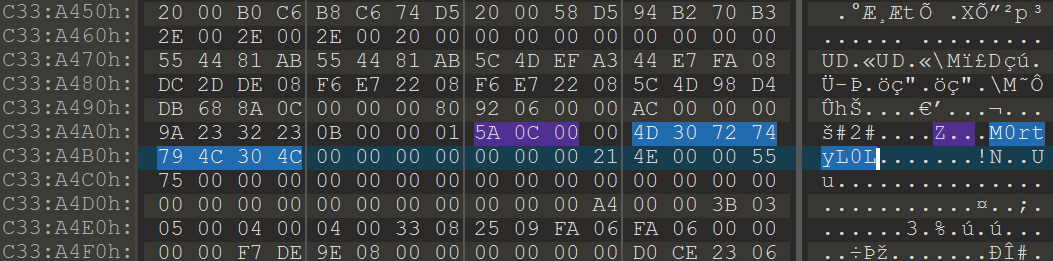
NSSCTF{M0rtyL0L}
Silly Rick
Silly rick always forgets his email's password, so he uses a Stored Password Services online to store his password. He always copy and paste the password so he will not get it wrong. whats rick's email password?
提示他经常复制粘贴,用clipboard查看剪贴板
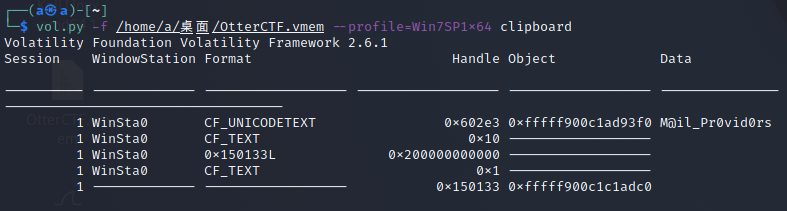
NSSCTF{M@il_Pr0vid0rs}
Hide And Seek
The reason that we took rick's PC memory dump is because there was a malware infection. Please find the malware process name (including the extension)
用pstree查看一下进程树,发现vmware-tray.exe居然是Rick And Morty的子进程(Rick And Morty是动画片,ware-tray.exe属于虚拟机关键进程)
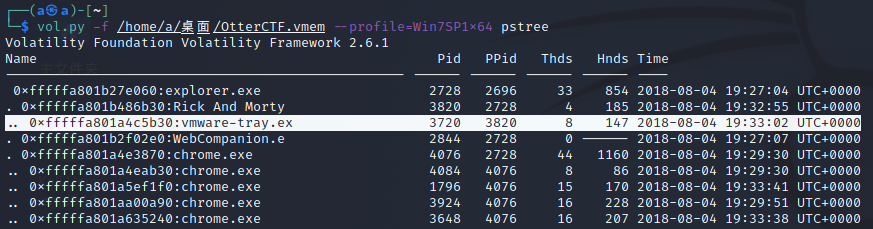
找一下vmware-tray.exe的文件,发现是在Temp文件夹下的,所以这是恶意软件进程
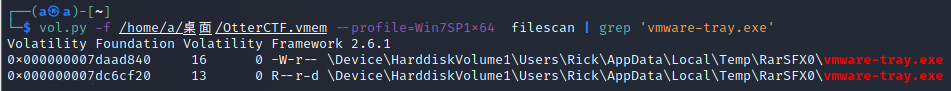
NSSCTF{vmware-tray.exe}
Path To Glory
How did the malware got to rick's PC? It must be one of rick old illegal habits...
恶意软件是在Rick And Morty进程后出现的,搜索Rick And Morty的相关文件
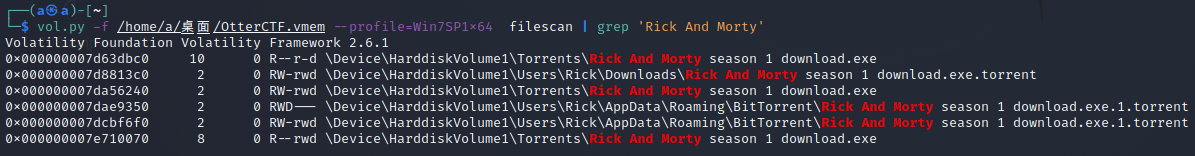
发现有三个BT种子,恶意软件应该就来自于这里,把它们保存下来查看其中的字符串信息,在其中一个找到了website信息

NSSCTF{M3an_T0rren7_4_R!ck}
Path To Glory 2
Continue the search after the way that malware got in.
恶意软件肯定从浏览器下载的,把chrome.exe的进程保存下来
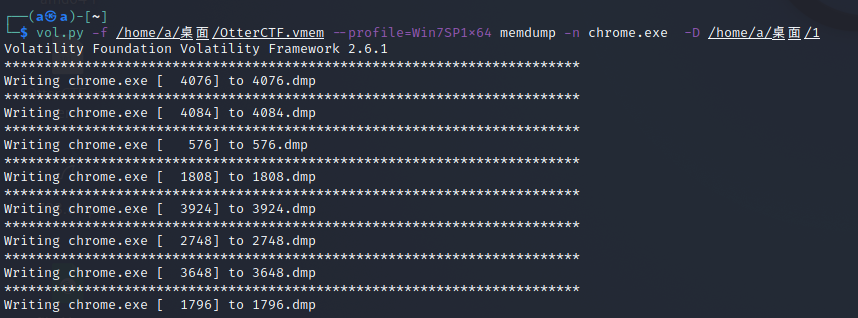
然后用strings和grep搜索Rick And Morty season 1 download.exe前后的字符串

最后在一个BT种子前面找到信息
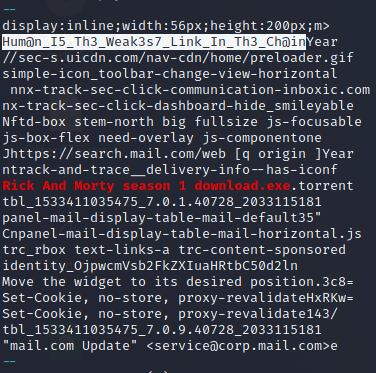
NSSCTF{Hum@n_I5_Th3_Weak3s7_Link_In_Th3_Ch@in}
Bit 4 Bit
We've found out that the malware is a ransomware. Find the attacker's bitcoin address.
把之前的恶意软件进程保存下来
用strings查找有关ransomware的信息
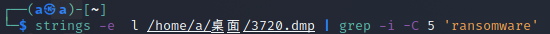
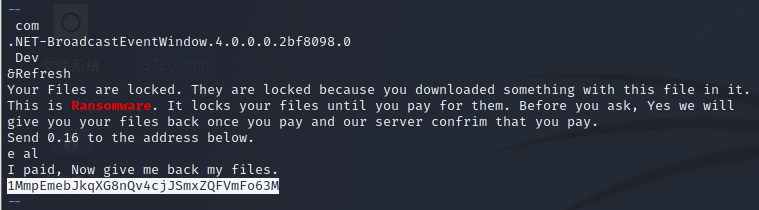
NSSCTF{1MmpEmebJkqXG8nQv4cjJSmxZQFVmFo63M}
Graphic's For The Weak
There's something fishy in the malware's graphics.
用foremost分离3720.dmp
在里面找图片

NSSCTF{S0_Just_M0v3_Socy}
Recovery
Rick got to have his files recovered! What is the random password used to encrypt the files?
把恶意软件进程保存成可执行文件
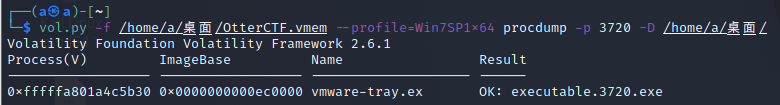
放进dnSpy进行反编译,在这里也能找到前两题的答案
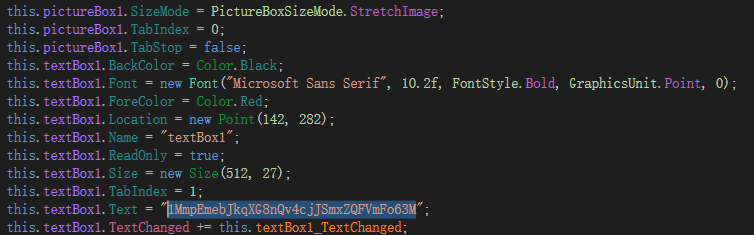

还找到了密码的生成和发送的函数,发送的信息即为WIN-LO6FAF3DTFE-Rick password(password就是我们找的密码)

去恶意软件进程里搜索
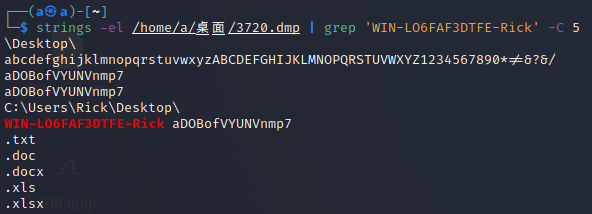
NSSCTF{aDOBofVYUNVnmp7}
Closure
Now that you extracted the password from the memory, could you decrypt rick's files?
看一下桌面的文件,发现了READ_IT.txt和Flag.txt
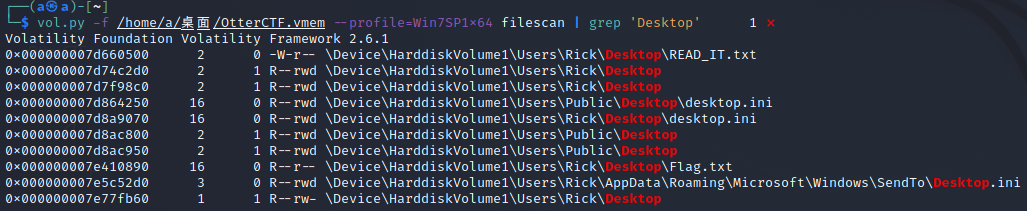
都保存下来查看一下,就是告诉我们Flag.txt文件是被加密了
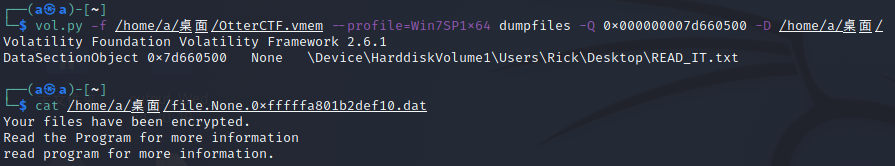
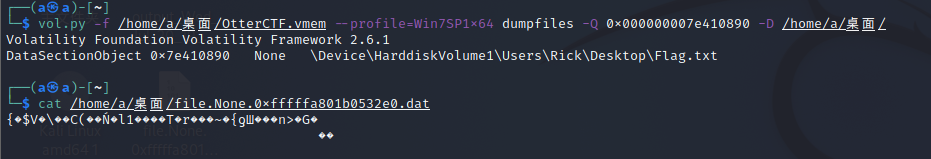
在之前找到的图片里可以看到$ucyLocker,这是勒索软件HiddenTear 的变种,把flag.txt文件末尾的0删掉,再加后缀.locked
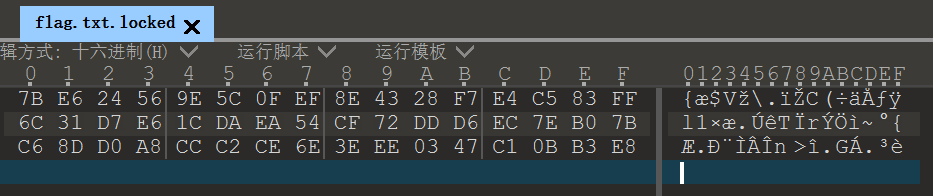
然后用HiddenTearDecrypter解密,解密的密码就是上面拿到的aDOBofVYUNVnmp7
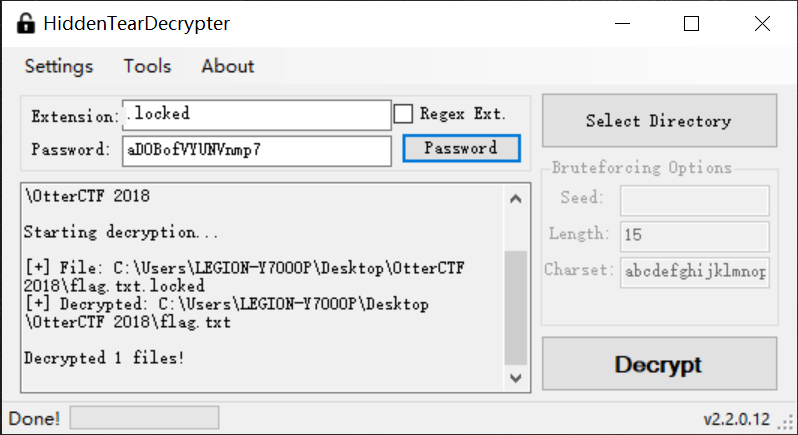
打开flag.txt,得到flag




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理