复现:NepCTF 2022
签到题
一个jpg

末尾有zip的数据,提取出来
里面是多层无密码加密,用脚本解
import zipfile def unZip(filename): fz = zipfile.ZipFile(filename, 'r') fz.extractall() fz.close() # 及时关闭文件,释放内存 for i in range(232,0,-1): unZip(str(i) + ".zip")
最后得到一个usb键盘流量包,用tshark指令提取数据
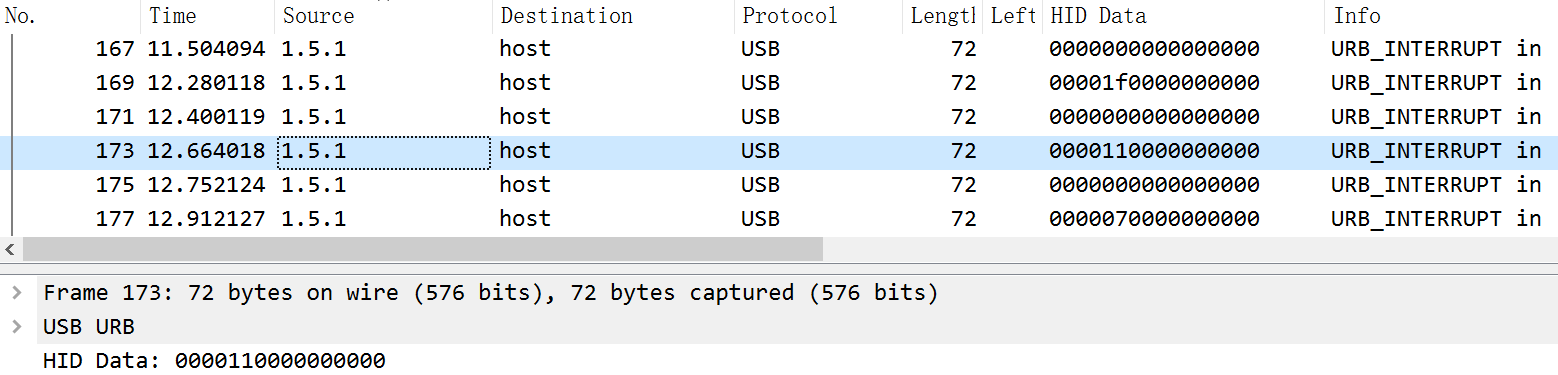

再用脚本跑一下
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
nums = []
keys = open('out.txt')
for line in keys:
if len(line)!=17: #首先过滤掉鼠标等其他设备的USB流量
continue
if line[6:16] != "0000000000":
continue
nums.append(line[0:2]+line[4:6]) #取一、三字节
keys.close()
output = ""
for n in nums:
if n[2:4] == "00" :
continue
if n[2:4] in normalKeys:
if n[0:2]=="02" or n[0:2]=="20": #表示按下了shift
output += shiftKeys [n[2:4]]
else :
output += normalKeys [n[2:4]]
else:
output += '[unknown]'
print('output:' + output)
output:nepctf{welcome_to_nepctf_2nd}<RET>
花画画画花花
一个osz文件
要下载一个osu!来打开,打开后是一种音游,可以直接通过编辑可以看到flag
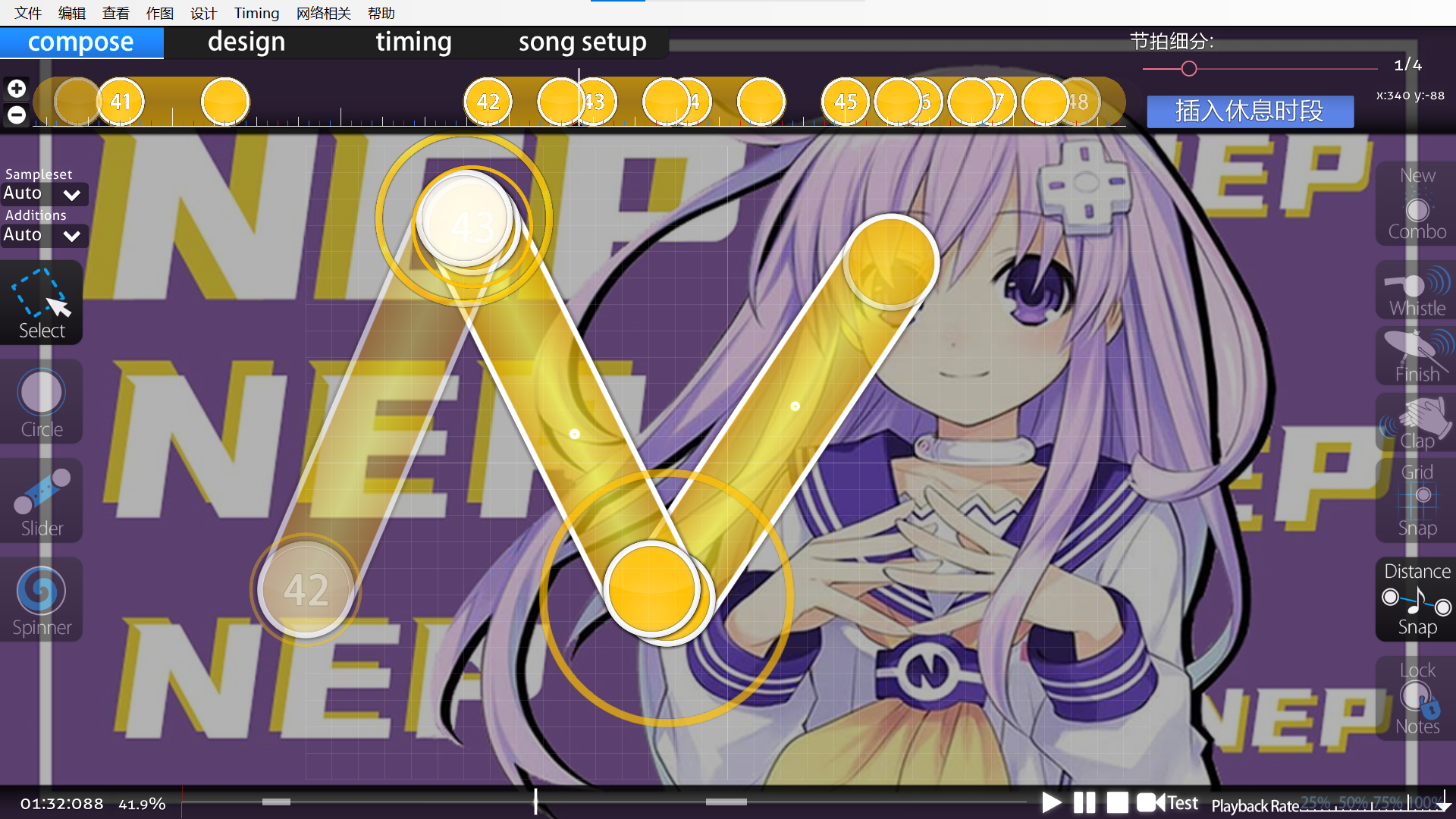
组合起来得到NepCTF{MASTER_OF_坏女人!}(最后的感叹号是中文的)
少见的bbbbase
一个jpg

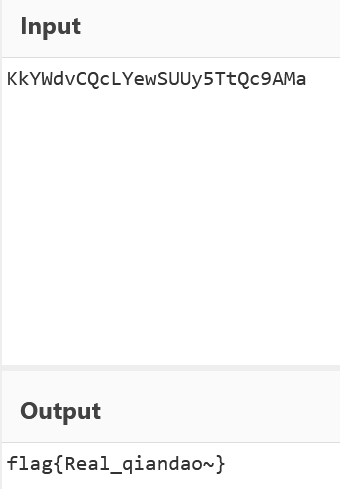
试了几个工具后,在jphide中seek出来一个密文
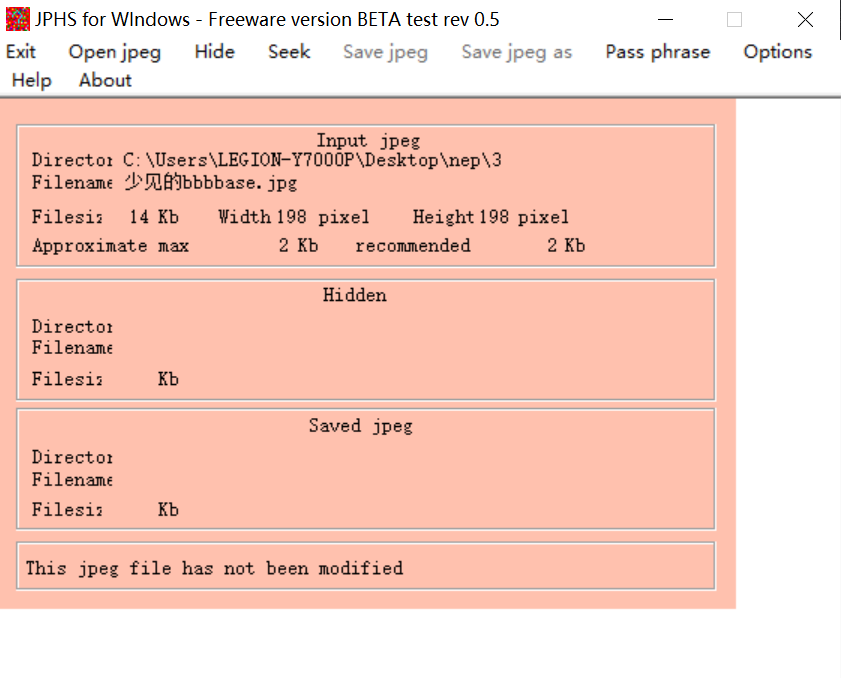

base58解码得到flag
馅饼?陷阱!
社工题,在图片里找到了琼,所以地点在海南省,然后找一下相关店面

最后发现题目给的图片就是在百度地图的实景图,flag即为NepCTF{www.cebbank.com}
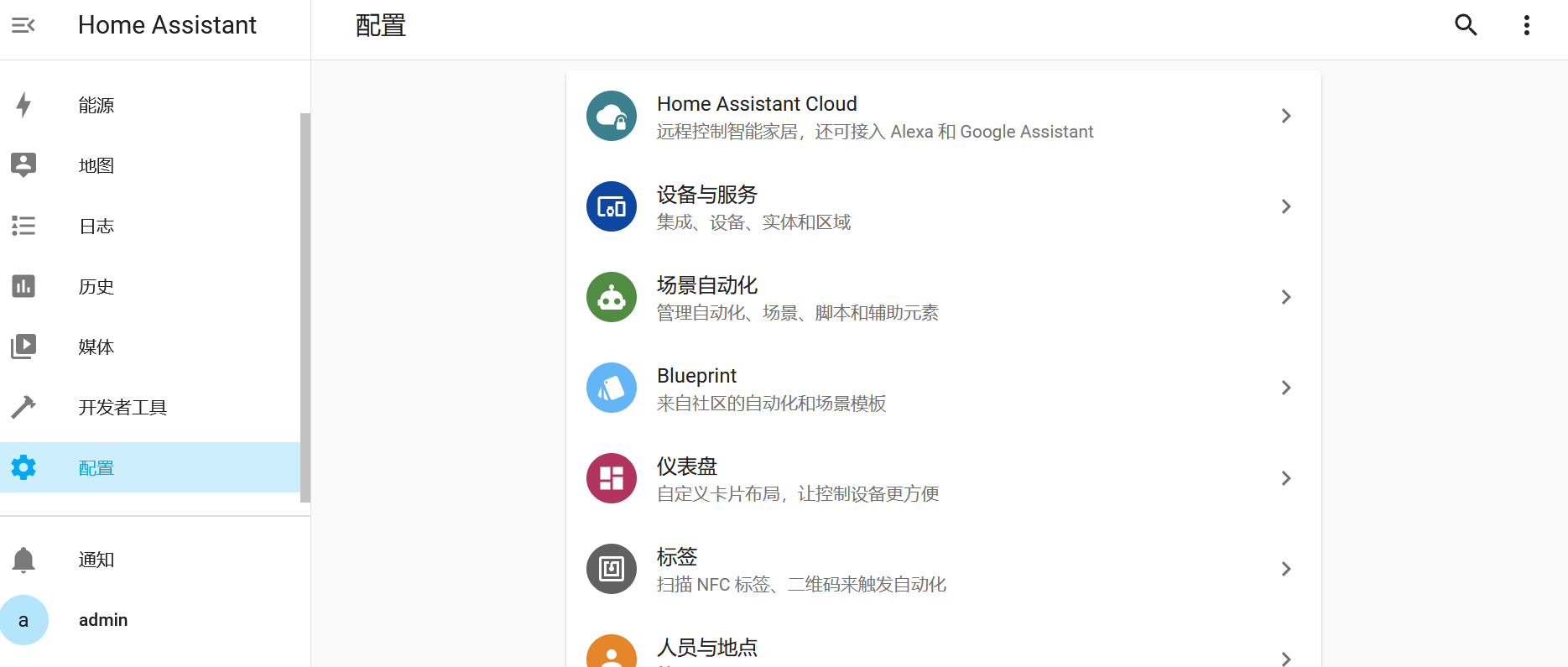
原来你也玩智能家居
关于Homeassistnt的题目,网址、账号、密码都给了,直接登上去,有一个显示器切换的开关

配置的设备与服务可以看到一个MQTT和一个Tasmota
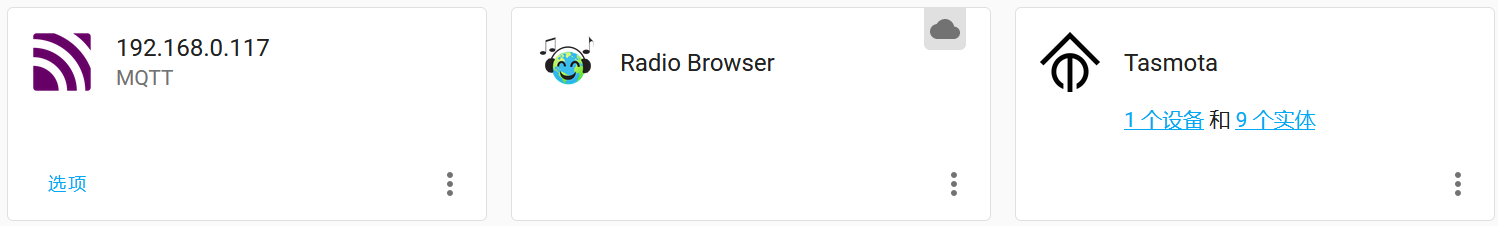
题目里说配置都是默认的,找到资料,Tasmota的默认主题是cmnd
用MQTT监听cmnd/#主题
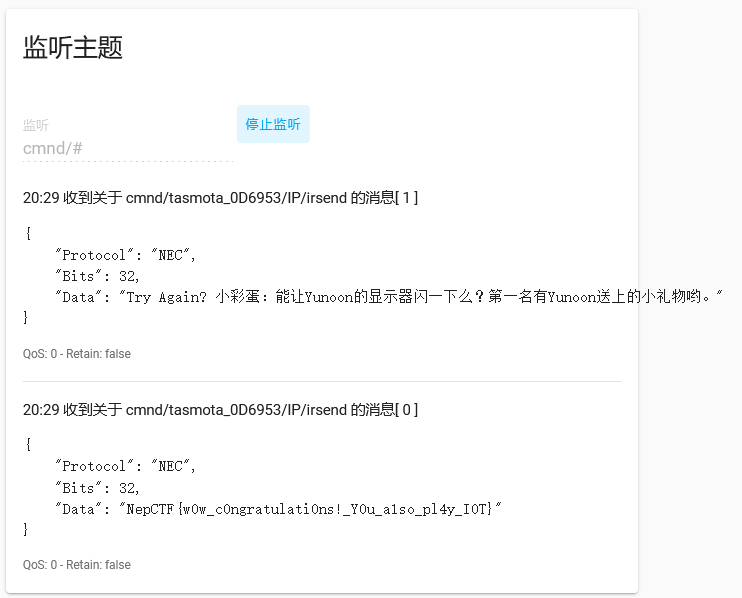
然后另开一个网站登进去,按显示器切换的开关,然后就能监听到flag




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理