misc刷题记录
ctfshow单身杯
misc签到
一个加密的zip,直接爆破密码,得到一个png

用010打开图片,在末尾找到了base64密文,解码后发现是二维码
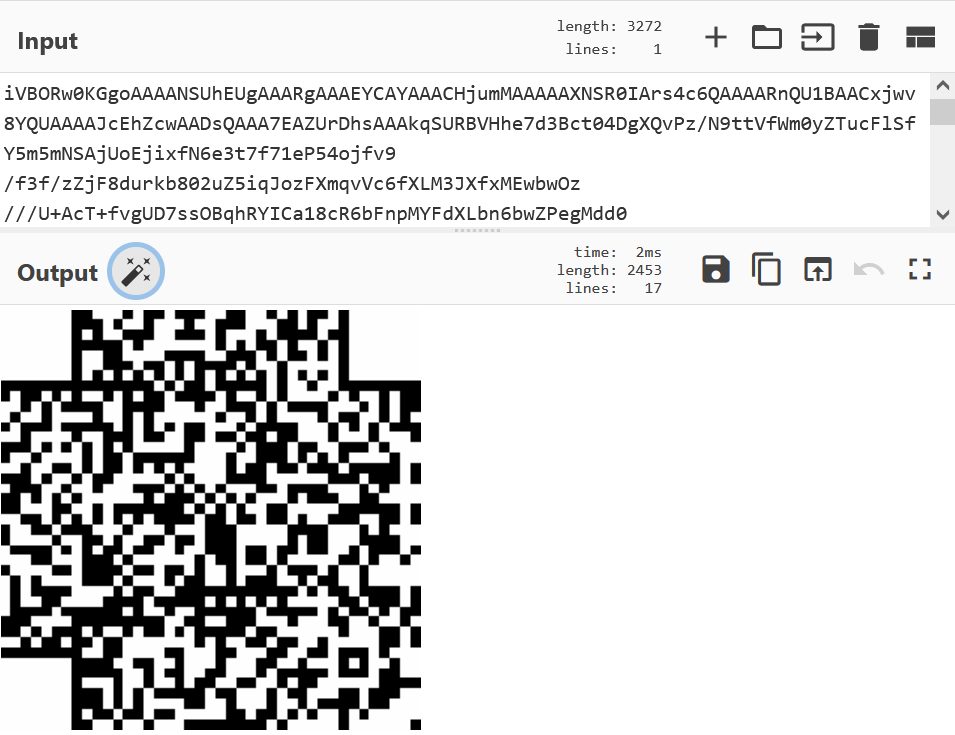
用stegsolve的red 0通道找到前一部分flag
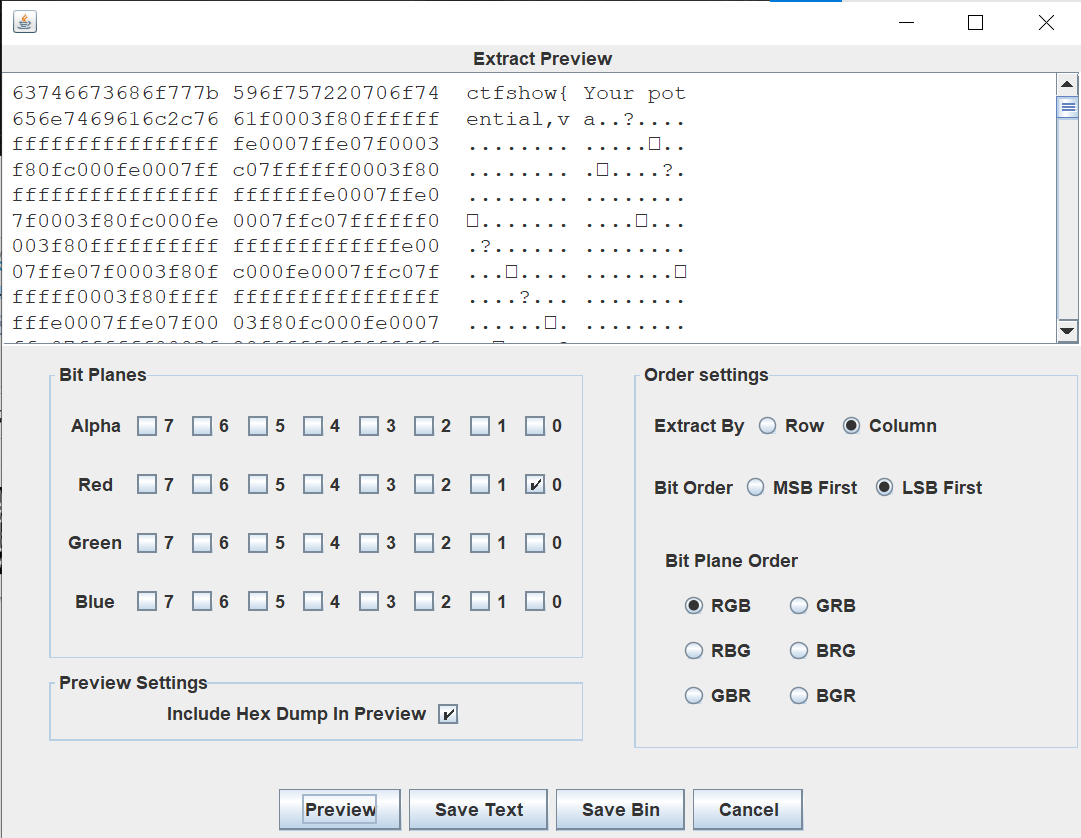
补全反色二维码,扫出十六进制密文

解码得到后半部分flag
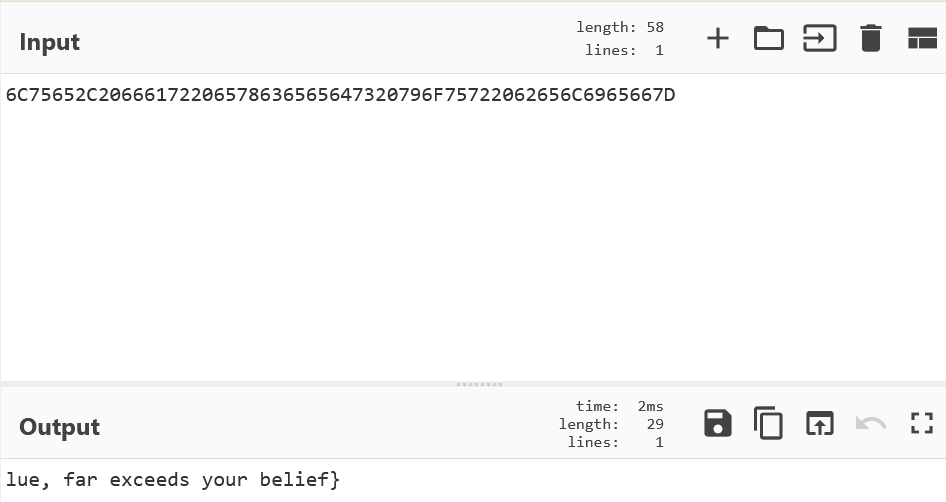
得到ctfshow{Your_potential_value_far_exceeds_your_belief}
没大没小的串串
打乱了大小写的flag是 y0U_RE4lLy_kn0W_TH1S_ConGr4tUlAT10Ns
其中正确的flag的md5是 7513209051f455fa44d0fa5cd0f3e051
得到最终的flag需要包上ctfshow{}
就是要求出字符串MD5值为7513209051f455fa44d0fa5cd0f3e051的大小写组合,写脚本跑出flag
import hashlib def alls(text):#获取字符串所有的大小写组合 res=[""] for i in text: if not i.isalpha(): for j in range(len(res)): res[j] += i else: for k in range(len(res)): tmp = res[k] res[k] += i.lower() res.append(tmp + i.upper()) return res s = r'y0U_RE4lLy_kn0W_TH1S_ConGr4tUlAT10Ns' res = alls(s) for i in res: m = hashlib.md5() #获取一个md5加密算法对象 m.update(i.encode()) #对字符串进行加密#update需要一个bytes格式参数 if(m.hexdigest() == '7513209051f455fa44d0fa5cd0f3e051'): #获取加密后的16进制字符串 print(i) break
y0U_Re4llY_kN0w_TH1s_coNgr4TULat10nS
得到ctfshow{y0U_Re4llY_kN0w_TH1s_coNgr4TULat10nS}
有眼睛就能做
提示:左右互搏
一个wav文件,直接查看频谱图,没有什么信息
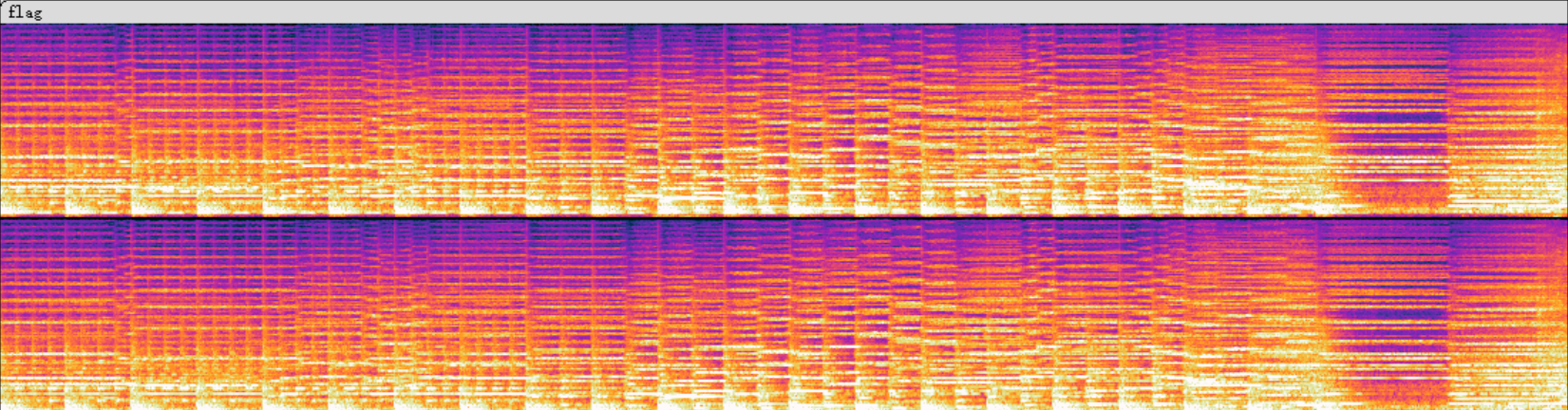
根据提示尝试着用左右声道频谱做减法
import torch ,torchaudio as ta import matplotlib.pyplot as plt,math wavf = ta.load('flag.wav')[0] specgram = ta.transforms.Spectrogram()(wavf) img = (specgram.log2()[0,:,:] - specgram.log2()[1,:,:]) plt.figure(figsize=(20,3)) plt.imshow(torch.tanh(img).numpy()) plt.show()
得到flag

ctfshow原谅杯
原谅1
一个png和一个加密的zip

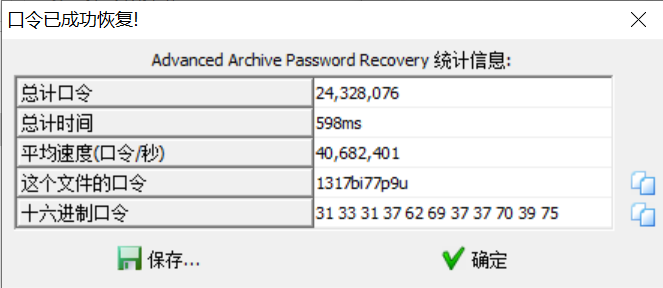
看图猜密码,前四位是1317,中间两个不知道,然后是7,🍺是p9,最后一位不知道,去试掩码爆破
得到一个jpg,一个txt,jpg用stegsolve打开在red 2通道找到flag

原谅2
zip加密了一个jpg,两txt,打开没有加密的hint.txt
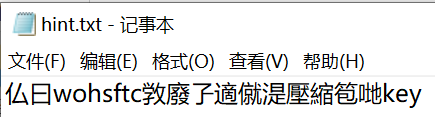
这是火星文
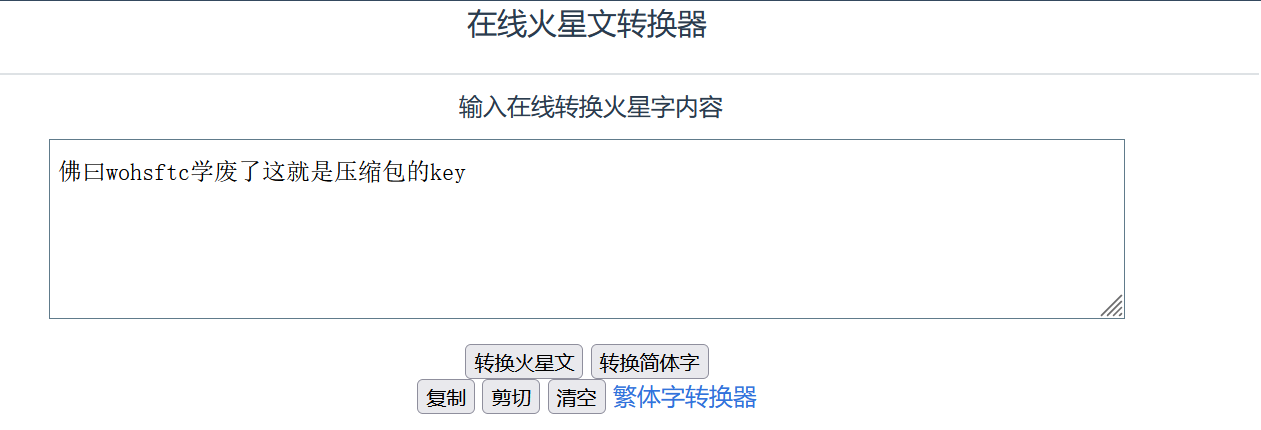
然后不用再进行佛曰解密了,这直接就是密码,打开flag.txt,得到flag
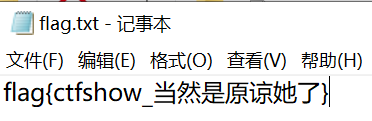
原谅3_来份色图
一个setu.png

用stegsolve打开,第一次遇到MSB,三个颜色的通道全选
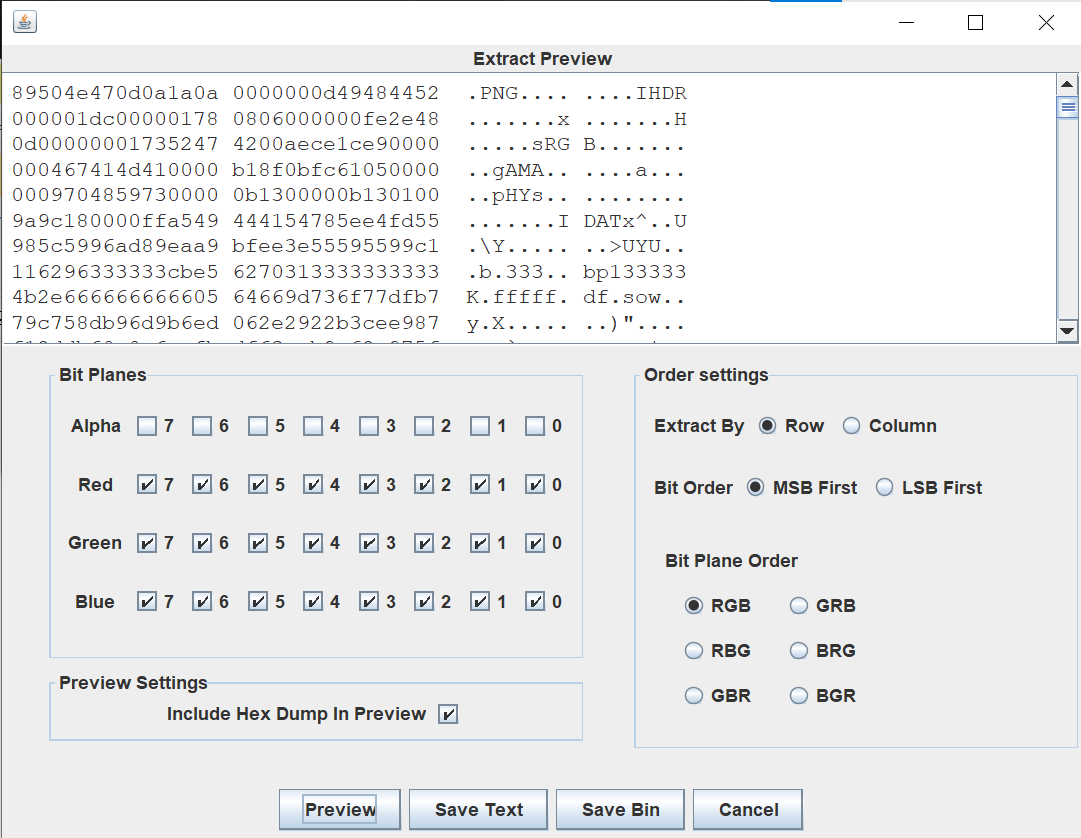
得到png,暂时不知道用处

用010打开setu.png,在末尾发现png数据,提取出来
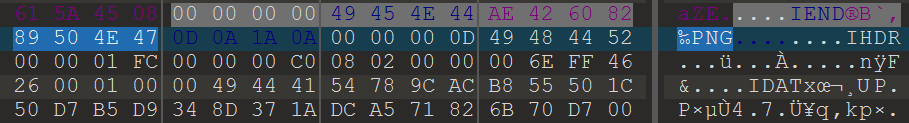
再进行一次MSB

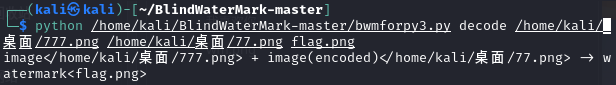
两张图片的深度不一样,可能是盲水印

进行盲水印,得到flag(这个盲水印我用python2的跑不出来,要用python3的)
ctfshow月饼杯
附加misc_问青天
提示:小姐姐声音是aiff格式
一个gif,用010打开可以分离出一个jpg(没有什么用)、一个加密的zip、一个aiff,aiff可以听得到:欢迎ctfshow的小哥哥来玩,用这个打开压缩包

发现都是八位的-和|,将-当作0,|当作1,手动提取出来,用脚本跑一下
s = '01100110 01101100 01100001 01100111 01111011 01100011 01110100 01100110 01011111 01110011 01101000 01101111 01110111 01011111 01101111 01100110 01011111 01100111 01101111 01101100 01100100 01011111 01110010 01100101 01100011 01101111 01110010 01100100 01111101' s_list = s.split(' ') flag = '' for i in range(len(s_list)): flag += chr(int(s_list[i],2)) print(flag)
得到flag{ctf_show_of_gold_record}
misc1_共婵娟
一个加密的压缩包,有提示

密码就是第一行字母对应的序号(A=1,B=2......),密码为279121518192122

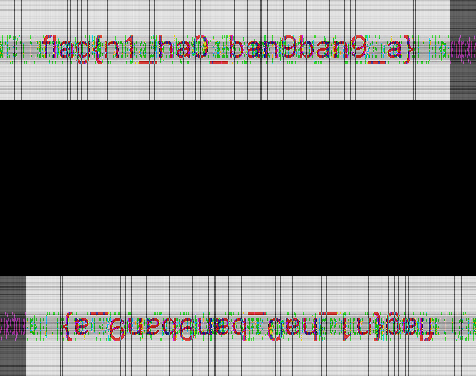
用010打开jpg,末尾有zip数据,提取出来,发现要密码,jpg高度感觉不对

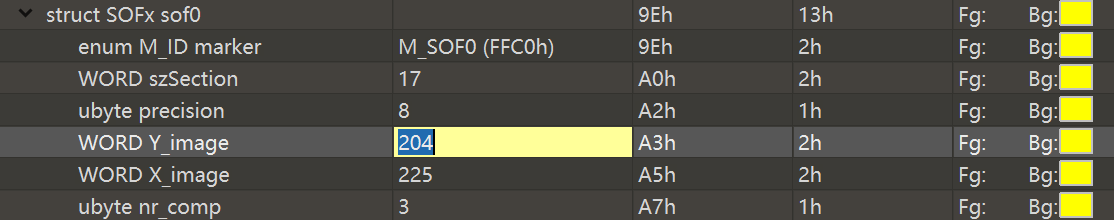
把高度改成225,得到密码

打开压缩包,里面是usb键盘流量,长度为35的是键盘流量,把他提取出来(直接跑usb键盘流量脚本跑不出)
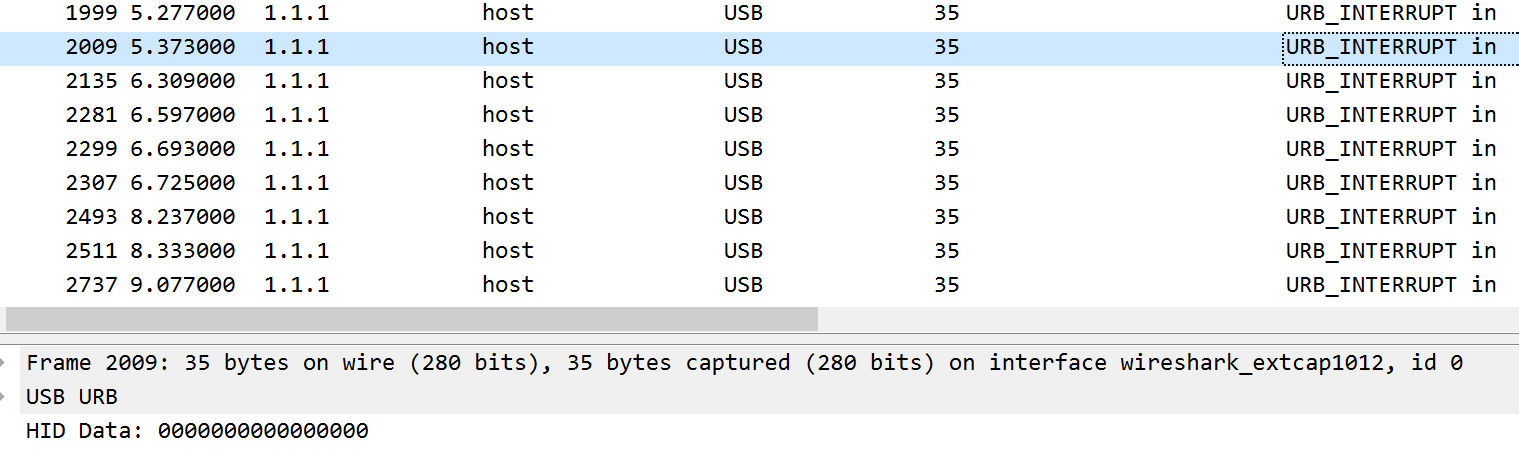
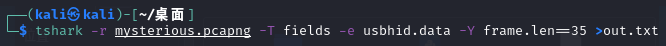
再用脚本提取信息
import os normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"} shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"} nums = [] keys = open('out.txt') for line in keys: if len(line)!=17: #首先过滤掉鼠标等其他设备的USB流量 continue nums.append(line[0:2]+line[4:6]) #取一、三字节 keys.close() output = "" for n in nums: if n[2:4] == "00" : continue if n[2:4] in normalKeys: if n[0:2]=="02": #表示按下了shift output += shiftKeys [n[2:4]] else : output += normalKeys [n[2:4]] else: output += '[unknown]' print('output :n' + output)
得到1j9dhfzlhcgu1cs<DEL>hdndg4c<DEL>vcw/f<DEL>dmdn<DEL>m,整理一下为1J9dhfZlHcgU1cHdnDG4VCw/dmdm,前面为百度网盘地址,后面为提取码,题目里给了百度网盘的前半段,但这百度网盘已经没了,所有后面就没做,看了一下后面大概是用到了零宽度、base64、base58、base62、emoji解码、仿射密码,真的太套娃了
misc2_洗寰瀛
一个加密的zip
提示: 1. 步骤1预计时间为50分钟 2. zip明文攻击 3. https://github.com/kimci86/bkcrack/blob/master/example/tutorial.md 4. flag[0:9]=='flag{TriG' 可能字体文件有问题
所以爆破zip要用bkcrack(至少已知明文的 12 个字节及偏移,其中至少 8 字节需要连续。 明文对应文件的加密算法需要是 ZipCrypto Store)
zip里面是png,png的前十六位是不变的,写成明文进行爆破
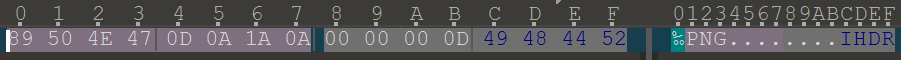
bkcrack的命令 -c 提取的密文部分 -p 提取的明文部分 -C 加密压缩包 -k 爆破出的密钥 -d 要还原出的文件名
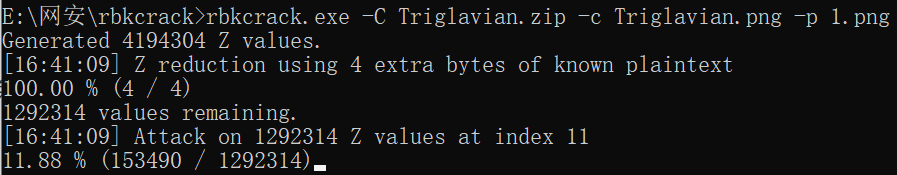
爆破时间要一个多小时吧,没去等,找了别人爆破的key:be056038 0a143c0c 1ea08ca5,再用key破解出文件
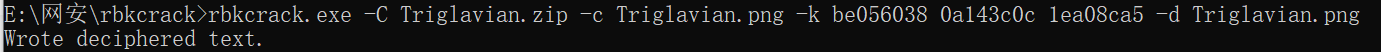

搜索了一下Triglavian,得知是深渊三神裔字体(Triglavian fonts)
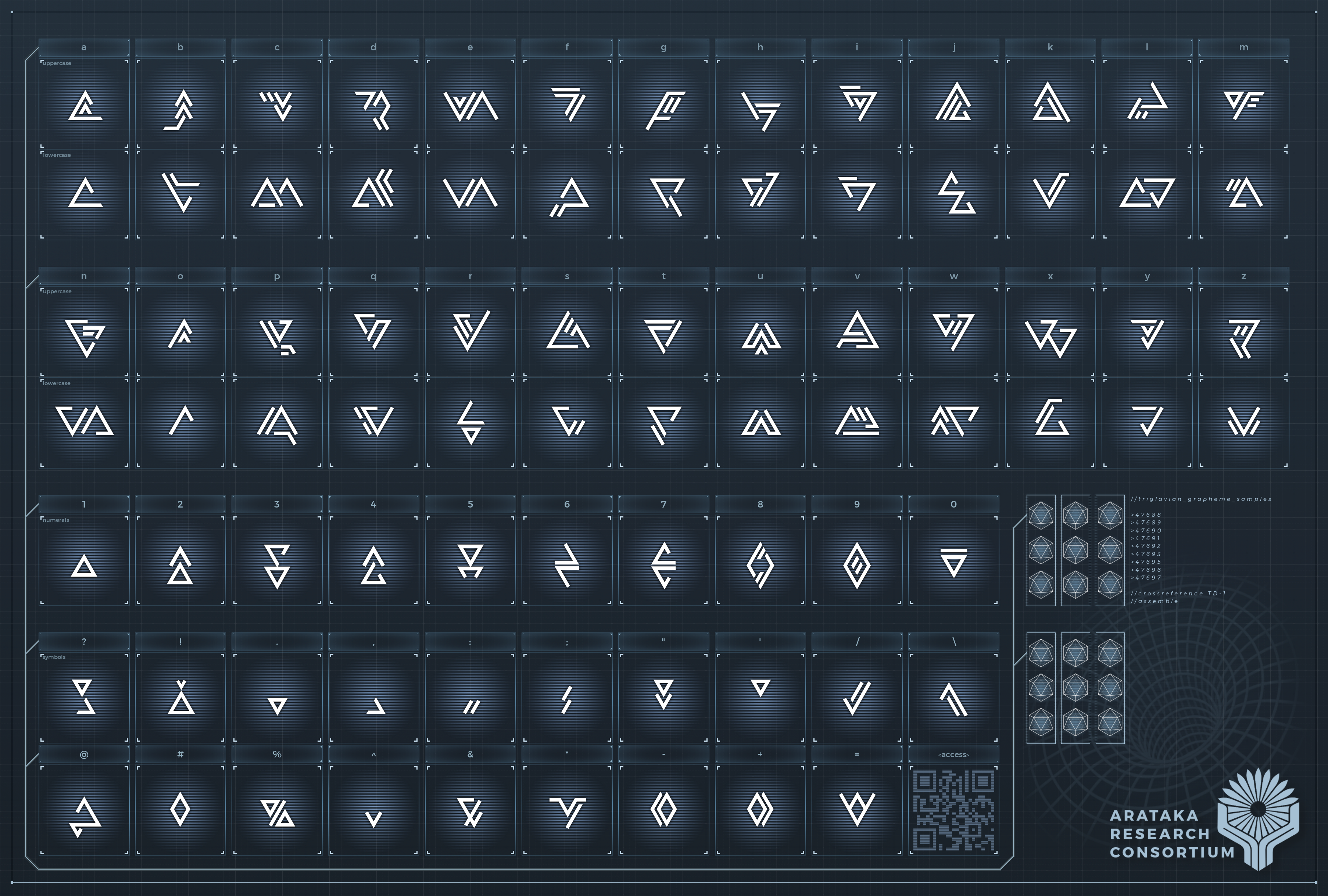
对照一下,得到flag{TriG1aviAn_Techn0lo9y}




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· 【自荐】一款简洁、开源的在线白板工具 Drawnix