暑假集训6.29
Weird_List
一个没后缀的文件,用010打开,好多组数据,但加起来都是120,其中1特别多,把是1的地方画出来
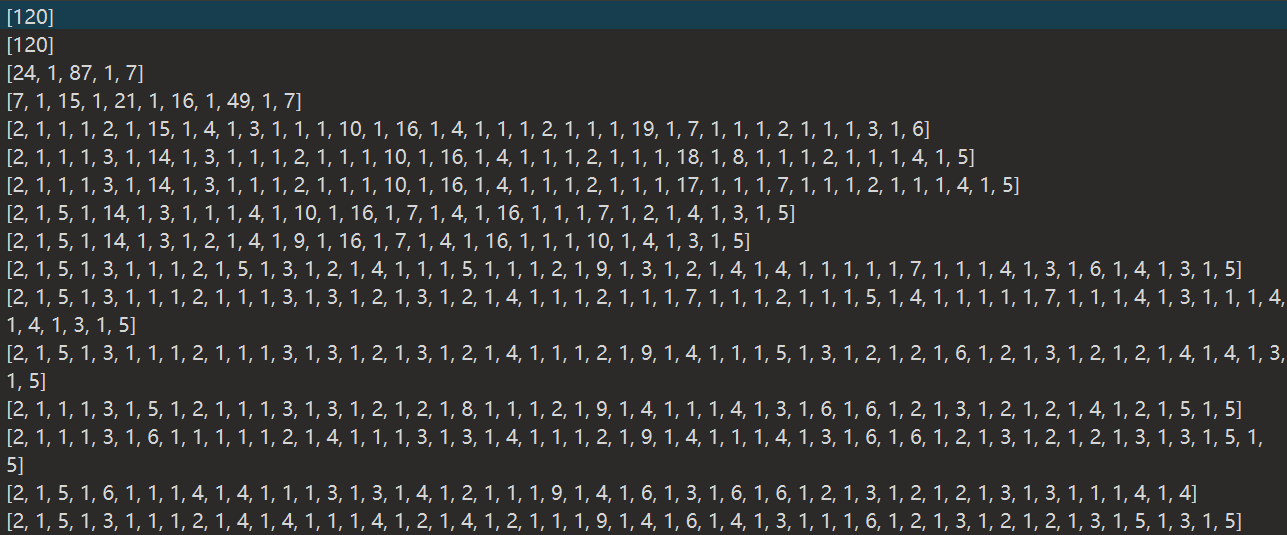
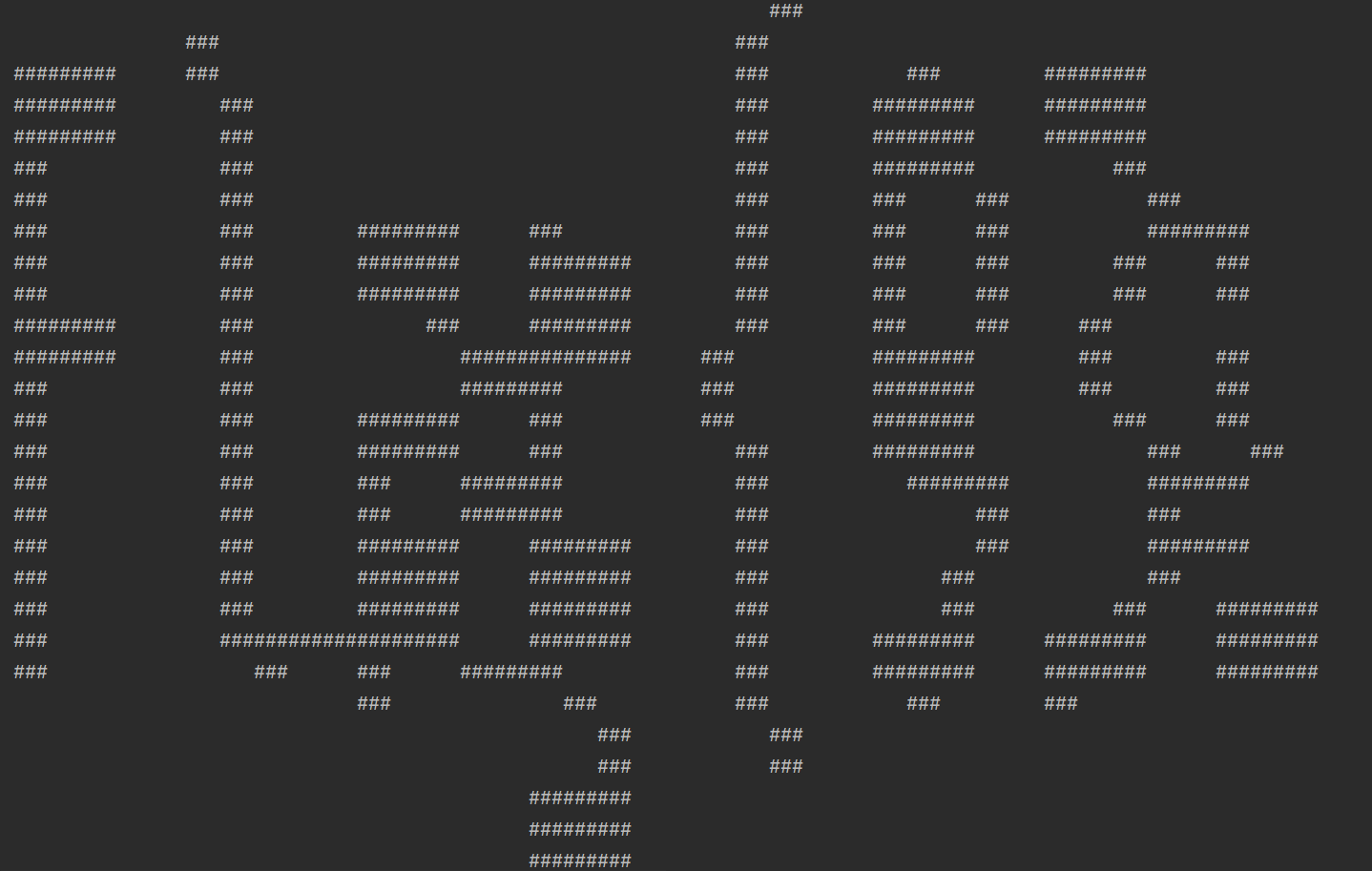
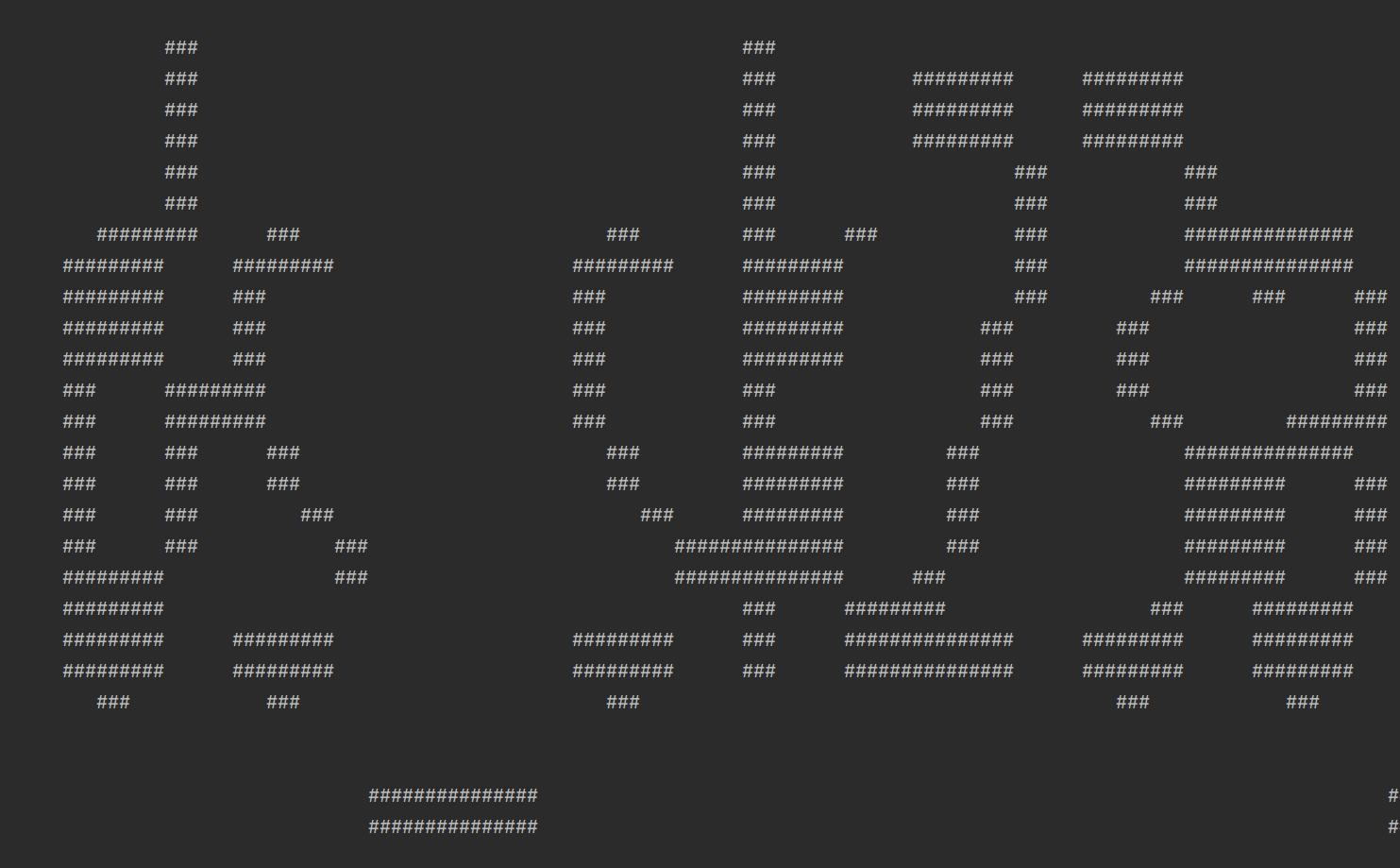
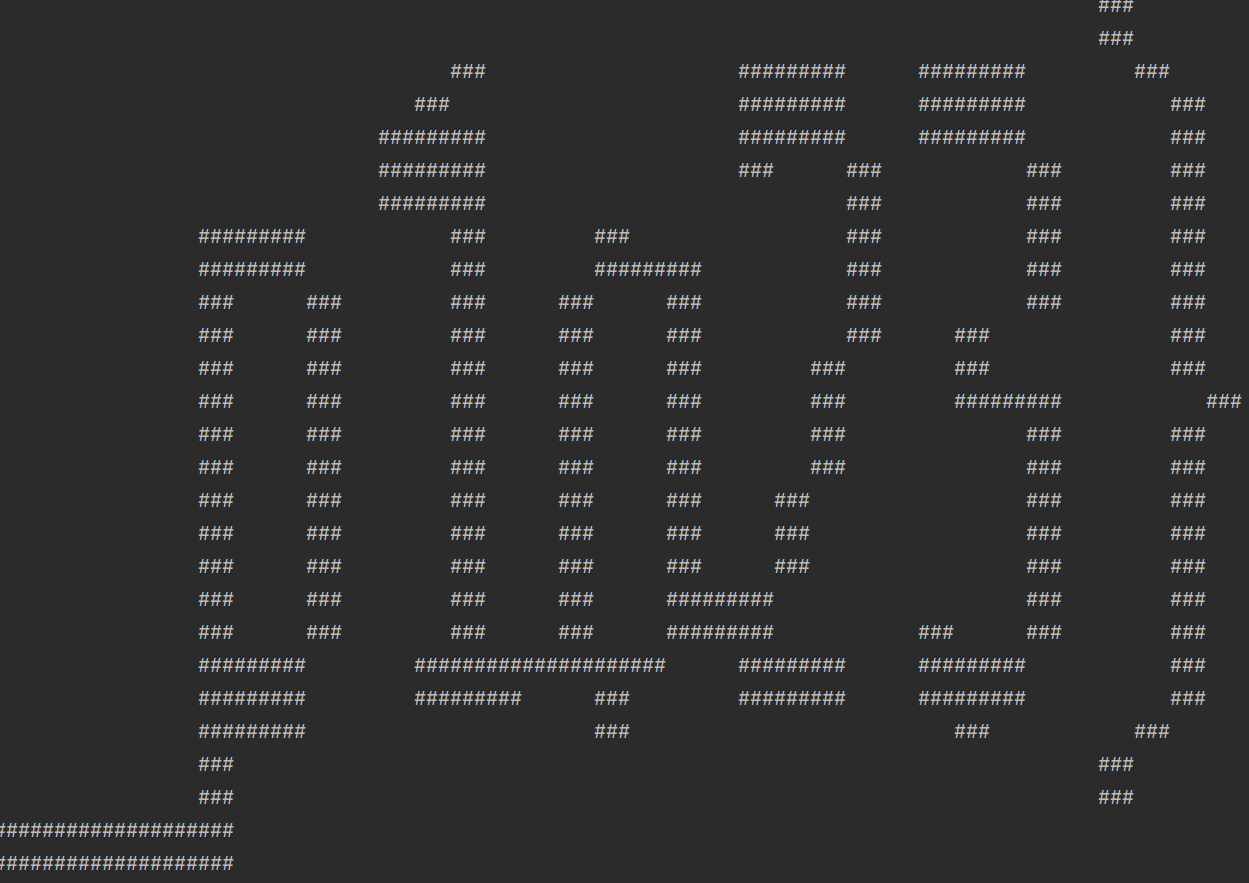
s =[ [120], [120], [24, 1, 87, 1, 7], [7, 1, 15, 1, 21, 1, 16, 1, 49, 1, 7], [2, 1, 1, 1, 2, 1, 15, 1, 4, 1, 3, 1, 1, 1, 10, 1, 16, 1, 4, 1, 1, 1, 2, 1, 1, 1, 19, 1, 7, 1, 1, 1, 2, 1, 1, 1, 3, 1, 6], [2, 1, 1, 1, 3, 1, 14, 1, 3, 1, 1, 1, 2, 1, 1, 1, 10, 1, 16, 1, 4, 1, 1, 1, 2, 1, 1, 1, 18, 1, 8, 1, 1, 1, 2, 1, 1, 1, 4, 1, 5], [2, 1, 1, 1, 3, 1, 14, 1, 3, 1, 1, 1, 2, 1, 1, 1, 10, 1, 16, 1, 4, 1, 1, 1, 2, 1, 1, 1, 17, 1, 1, 1, 7, 1, 1, 1, 2, 1, 1, 1, 4, 1, 5], [2, 1, 5, 1, 14, 1, 3, 1, 1, 1, 4, 1, 10, 1, 16, 1, 7, 1, 4, 1, 16, 1, 1, 1, 7, 1, 2, 1, 4, 1, 3, 1, 5], [2, 1, 5, 1, 14, 1, 3, 1, 2, 1, 4, 1, 9, 1, 16, 1, 7, 1, 4, 1, 16, 1, 1, 1, 10, 1, 4, 1, 3, 1, 5], [2, 1, 5, 1, 3, 1, 1, 1, 2, 1, 5, 1, 3, 1, 2, 1, 4, 1, 1, 1, 5, 1, 1, 1, 2, 1, 9, 1, 3, 1, 2, 1, 4, 1, 4, 1, 1, 1, 1, 1, 7, 1, 1, 1, 4, 1, 3, 1, 6, 1, 4, 1, 3, 1, 5], [2, 1, 5, 1, 3, 1, 1, 1, 2, 1, 1, 1, 3, 1, 3, 1, 2, 1, 3, 1, 2, 1, 4, 1, 1, 1, 2, 1, 1, 1, 7, 1, 1, 1, 2, 1, 1, 1, 5, 1, 4, 1, 1, 1, 1, 1, 7, 1, 1, 1, 4, 1, 3, 1, 1, 1, 4, 1, 4, 1, 3, 1, 5], [2, 1, 5, 1, 3, 1, 1, 1, 2, 1, 1, 1, 3, 1, 3, 1, 2, 1, 3, 1, 2, 1, 4, 1, 1, 1, 2, 1, 9, 1, 4, 1, 1, 1, 5, 1, 3, 1, 2, 1, 2, 1, 6, 1, 2, 1, 3, 1, 2, 1, 2, 1, 4, 1, 4, 1, 3, 1, 5], [2, 1, 1, 1, 3, 1, 5, 1, 2, 1, 1, 1, 3, 1, 3, 1, 2, 1, 2, 1, 8, 1, 1, 1, 2, 1, 9, 1, 4, 1, 1, 1, 4, 1, 3, 1, 6, 1, 6, 1, 2, 1, 3, 1, 2, 1, 2, 1, 4, 1, 2, 1, 5, 1, 5], [2, 1, 1, 1, 3, 1, 6, 1, 1, 1, 1, 1, 2, 1, 4, 1, 1, 1, 3, 1, 3, 1, 4, 1, 1, 1, 2, 1, 9, 1, 4, 1, 1, 1, 4, 1, 3, 1, 6, 1, 6, 1, 2, 1, 3, 1, 2, 1, 2, 1, 3, 1, 3, 1, 5, 1, 5], [2, 1, 5, 1, 6, 1, 1, 1, 4, 1, 4, 1, 1, 1, 3, 1, 3, 1, 4, 1, 2, 1, 1, 1, 9, 1, 4, 1, 6, 1, 3, 1, 6, 1, 6, 1, 2, 1, 3, 1, 2, 1, 2, 1, 3, 1, 3, 1, 1, 1, 4, 1, 4], [2, 1, 5, 1, 3, 1, 1, 1, 2, 1, 4, 1, 4, 1, 1, 1, 4, 1, 2, 1, 4, 1, 2, 1, 1, 1, 9, 1, 4, 1, 6, 1, 4, 1, 3, 1, 1, 1, 6, 1, 2, 1, 3, 1, 2, 1, 2, 1, 3, 1, 5, 1, 3, 1, 5], [2, 1, 5, 1, 3, 1, 1, 1, 2, 1, 5, 1, 3, 1, 1, 1, 5, 1, 2, 1, 3, 1, 2, 1, 2, 1, 9, 1, 3, 1, 1, 1, 3, 1, 6, 1, 1, 1, 1, 1, 7, 1, 2, 1, 3, 1, 2, 1, 2, 1, 3, 1, 5, 1, 3, 1, 5], [2, 1, 5, 1, 3, 1, 2, 1, 1, 1, 5, 1, 4, 1, 1, 1, 4, 1, 1, 1, 4, 1, 2, 1, 2, 1, 9, 1, 3, 1, 1, 1, 3, 1, 6, 1, 1, 1, 2, 1, 6, 1, 2, 1, 3, 1, 2, 1, 2, 1, 2, 1, 6, 1, 3, 1, 5], [2, 1, 5, 1, 3, 1, 2, 1, 1, 1, 5, 1, 6, 1, 4, 1, 6, 1, 2, 1, 3, 1, 9, 1, 2, 1, 1, 1, 3, 1, 6, 1, 1, 1, 2, 1, 6, 1, 2, 1, 3, 1, 2, 1, 2, 1, 2, 1, 6, 1, 3, 1, 5], [2, 1, 5, 1, 3, 1, 1, 1, 2, 1, 1, 1, 3, 1, 6, 1, 4, 1, 1, 1, 4, 1, 2, 1, 4, 1, 9, 1, 1, 1, 1, 1, 3, 1, 6, 1, 1, 1, 2, 1, 6, 1, 2, 1, 3, 1, 2, 1, 2, 1, 2, 1, 6, 1, 3, 1, 5], [2, 1, 5, 1, 3, 1, 1, 1, 2, 1, 1, 1, 3, 1, 5, 1, 5, 1, 6, 1, 1, 1, 5, 1, 9, 1, 1, 1, 1, 1, 2, 1, 7, 1, 1, 1, 2, 1, 6, 1, 2, 1, 3, 1, 2, 1, 2, 1, 1, 1, 7, 1, 3, 1, 5], [2, 1, 5, 1, 3, 1, 1, 1, 2, 1, 1, 1, 3, 1, 5, 1, 4, 1, 2, 1, 1, 1, 2, 1, 1, 1, 17, 1, 2, 1, 1, 1, 6, 1, 2, 1, 1, 1, 7, 1, 2, 1, 3, 1, 2, 1, 2, 1, 1, 1, 4, 1, 2, 1, 3, 1, 5], [2, 1, 5, 1, 1, 1, 1, 1, 1, 1, 2, 1, 1, 1, 3, 1, 3, 1, 1, 1, 2, 1, 1, 1, 2, 1, 1, 1, 2, 1, 1, 1, 2, 1, 1, 1, 7, 1, 1, 1, 2, 1, 2, 1, 1, 1, 1, 1, 2, 1, 1, 1, 2, 1, 1, 1, 7, 1, 1, 1, 3, 1, 1, 1, 1, 1, 1, 1, 2, 1, 1, 1, 2, 1, 1, 1, 4, 1, 5], [2, 1, 6, 1, 2, 1, 2, 1, 1, 1, 5, 1, 3, 1, 1, 1, 2, 1, 1, 1, 2, 1, 1, 1, 2, 1, 1, 1, 2, 1, 1, 1, 7, 1, 1, 1, 2, 1, 2, 1, 1, 1, 1, 1, 2, 1, 1, 1, 2, 1, 1, 1, 7, 1, 1, 1, 3, 1, 1, 1, 2, 1, 3, 1, 1, 1, 2, 1, 1, 1, 4, 1, 5], [12, 1, 5, 1, 4, 1, 4, 1, 3, 1, 10, 1, 4, 1, 9, 1, 14, 1, 4, 1, 8, 1, 1, 1, 8, 1, 9, 1, 4, 1, 6], [19, 1, 4, 1, 62, 1, 24, 1, 7], [19, 1, 4, 1, 62, 1, 24, 1, 7], [17, 1, 1, 1, 31, 1, 1, 1, 1, 1, 25, 1, 1, 1, 1, 1, 1, 1, 32], [17, 1, 1, 1, 31, 1, 1, 1, 1, 1, 25, 1, 1, 1, 1, 1, 1, 1, 32], [17, 1, 1, 1, 67, 1, 32], [120], [21, 1, 1, 1, 1, 1, 86, 1, 1, 1, 1, 1, 3], [120], [120], ] for i in s: for k in i: if k != 1: for i in range(k): print(' ', end='') else: print('###', end='') print('')
运行一下得到flag{93ids_sk23a_p1o23}
静静听这么好听的歌
给的txt文件是matlab脚本,是把一个bmp的位图写进wav文件里
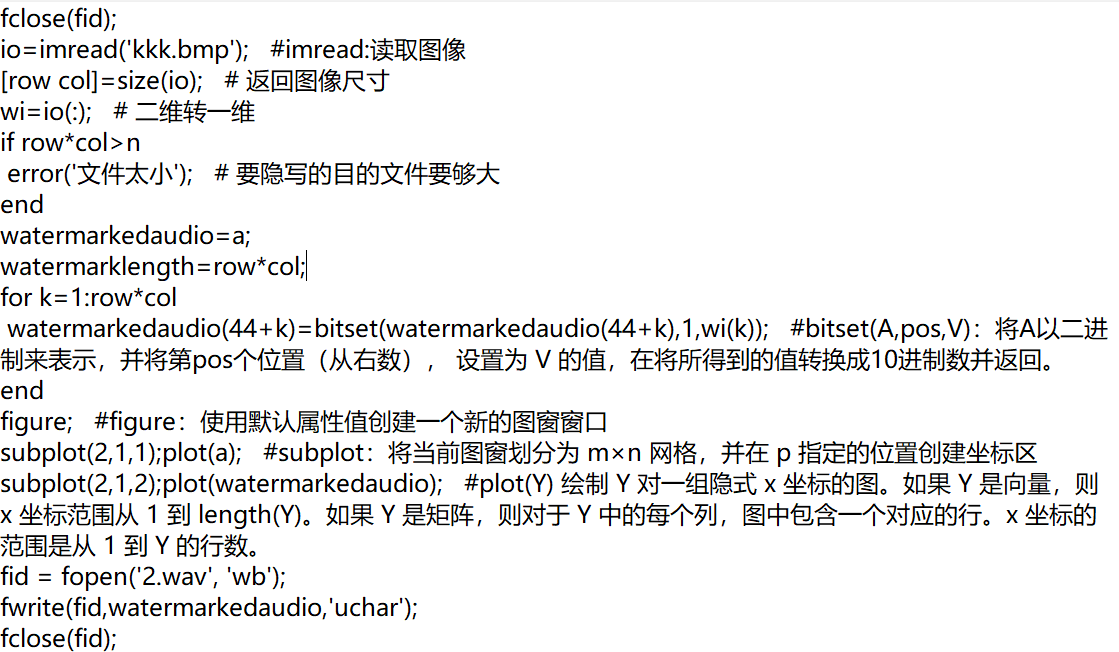
用脚本解出原图
# python脚本 import numpy as np from PIL import Image wav = open('a.wav','rb') content = wav.read() wav.close() bins = [] for i in range(45,45+388*100): bins.append(255 if int(bin(content[i])[-1:]) else 0)#为非0数据就添加255,否则添加0,bin:返回整数的二进制 flag = np.array(bins,np.uint8).reshape(388,100)#使bins以uint8的类型进行存储,设置宽为388,高为100 flag = np.flipud(flag)#将图片镜像翻转 imgg = Image.fromarray(flag).save('res.bmp')
得到flag

[RCTF2019]printer
usb流量分析,先拿脚本跑了一下,得到的数据没什么用
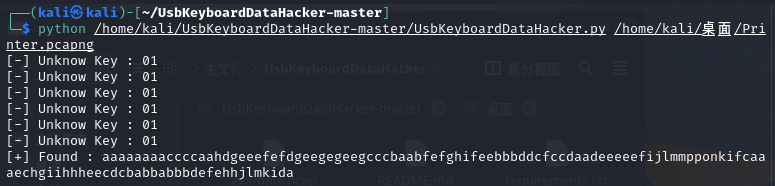
然后又在流量包里找到了两个特别的,其中一个有BAR数据和bitmap数据

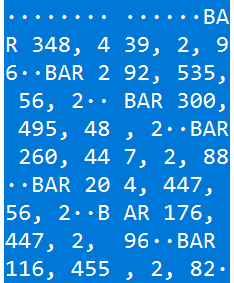
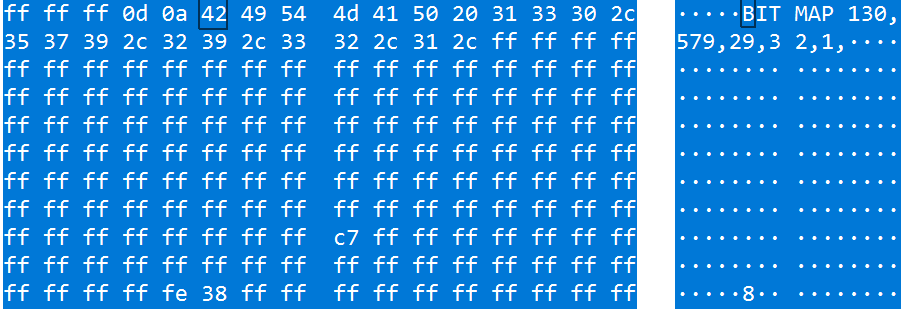
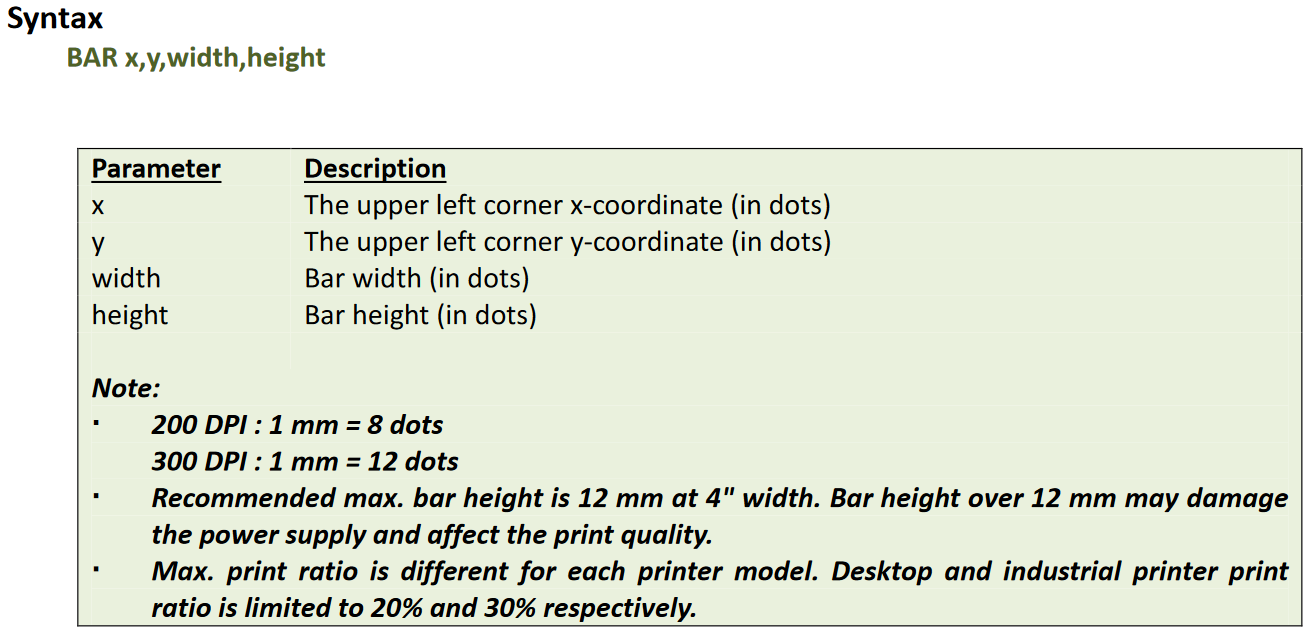
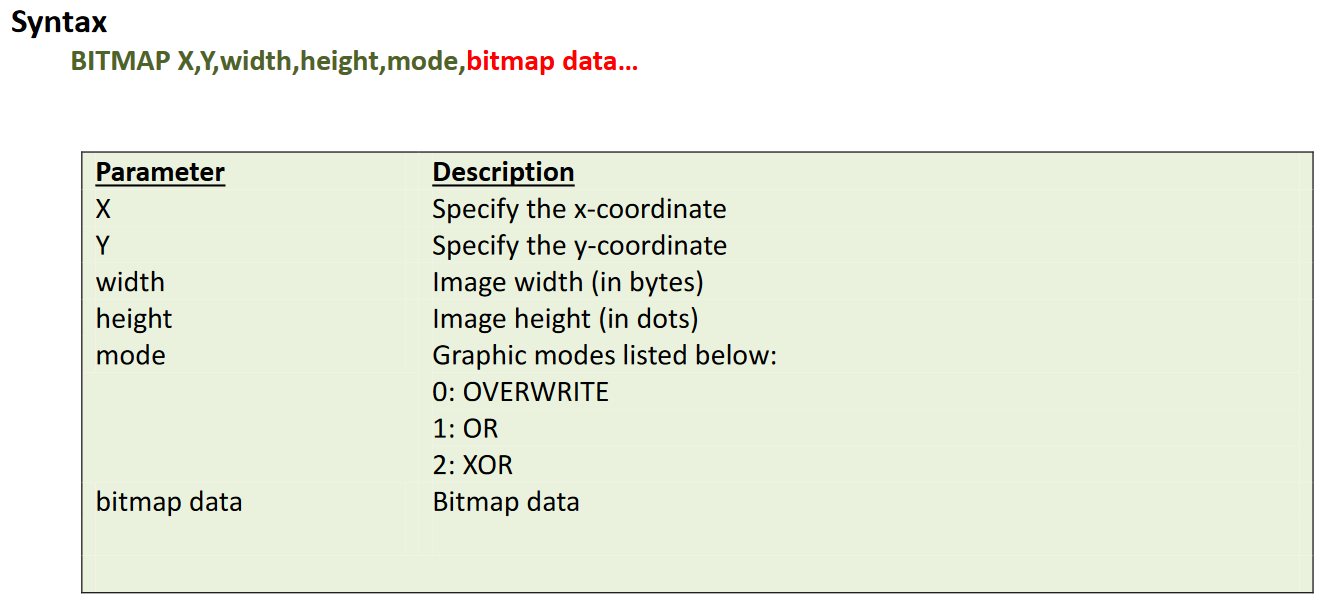
把BAR和bitmap提取出来,用相关脚本跑一下,得到flag
from PIL import Image from pwn import * img = Image.new( '1', (1000,1000),color=1) pixels = img.load() data1 = 'FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF 00FFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFC3FF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF E7FFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFE7FF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF E7FFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFE7FF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF E7FFE3FF FE1FFFFF FFFFF807 C03C603F C07C07E0 007F7FF0 1F8067FF 007FF803 FC07C03F FF1FF1F0 4F8FF1FF 1FFF1FFF 3FFCFF1F 27FC7F1F F3E1FF1F F9FFFF1F F1FC1FCF F8FF1FFF 1FFF3FFE FE3F87F8 FF9FEFF8 FF1FF9FF FF8FF1FC 3FC7FCFF 1FFF1FFF 1FFEFC7F C7F9FF8F DFFC7F1F F9FFFF8F F1FC7FE3 FC7F1FFF 1FFF1FFE FCFFE7F1 FF8F9FFC 3F1FF9FF FFC7F1FC 7FE3FE3F 1FFF1FFF 0FFEF8FF E7F1FF0F BFFE3F1F F9FFFFC7 F1FC7FE3 FE3F1FFF 1FFF0FFE F8FFE7E1 FF8F3FFE 3F1FF9FF FFE3F1FC 7FE3FF1F 1FFF1FFF 47FEF8FF E7E3FF9F 7FFE1F1F F9FFFFE3 F1FC7FF3 FF8E1FFF 1FFF47FE F9FFE7E3 FFFFFFFF 1F1FF9FF FFF1F1FC 7FF3FF8C 1FFF1FFF 63FEF9FF E7F1FFFF FFFF1F1F F9FFFFF1 F1FC7FF3 FFC11FFF 1FFF63FE F9FFE7F1 FFFFFFFF 1F1FF9FF FFF1F1FC 7FE3FFE3 1FFF1FFF 71FEF9FF E7F1FFFF FFFF1F1F F9FFFFF8 F1FC7FE3 FFE71FFF 1FFF71FE F8FFE7F8 FFFFFFFF 0F1FF9FF FFF8F1FC 7FE3FFCF 1FFF1FFF 78FEF8FF E7FCFFFF FFFF0F1F F9FFFFFC 61FC7FE7 FF9F1FFF 1FFF78FE F8FFC7FE 3FFFFFFF 0F1FF9FF FFFC41FC 7FC7FF3F 1FFF1FFF 7C7EFCFF C7FF83FF FFFF0F9F F1FFFFFE 11FC3F8F FF7F1FFF 1FFF7C7E FC7FA7FF 87FFFFFF 0F9FE9FF FFFE31FC 1F1FFE7F 1FFF1FFF 7E3EFE3E 67FE3FFF FFFF1F8F 99FFFFFF 31FC403F E01F1FFF 1FFF7E3E FF80E0FC 7FFFFFFF 1FC039FF FFFE71FC 79FFFFFF 1FFF1FFF 7F1EFFF3 EFF8FFFF FFFF1FF0 F9FFFFFE F1FC7FFF FFFF1FFF 1FFF7F0E FFFFFFF8 FFFFFFFF 1FFFF9FF FFFCF1FC 7FFFFFFF 1FFF1FFF 7F8EFFFF FFF8FFFF FFFE1FFF F9FFFFF9 F1FC7FFF FFFF1FFF 1FFF7F86 FFFFFFF8 FF9F7FFE 3FFFF9FF FFFBF1FC 7FFFFFFF 1FFF1FFF 7FC6FFFF FFF8FF0F 3FFE3FFF F9FFFFF7 F1FC7FFF FFFF1FFF 1FFF7FC2 FFFFFFF8 FF8FBFFC 7FFFF9FF FFE7F1FC 7FFFFFFF 1FFF1FFF 7FE2FFFF FFF8FF8F 9FFC7FFF F9FFFFCF F1FC7FFF FFFF1FFF 1FFF7FF0 FFFFFFFC FF9F9FF8 FFFFF9FF FF8FF1FC 7FFFFFFF 1FFF1FFF 7FF0FFFF FFFC7F9F 8FF1FFFF F9FFFF0F F0FC3FFF FFFF1FFF 0FFE7FF8 FFFFFFFE 1E7F83E3 FFFFF8FF FC03C03C 0FFFFFFF 03E00078 0FF83FFF FFFF80FF F80FFFFF F83FFFFF FFFDFFFF FFFF3FFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFBFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF' data1 = bits(int(data1.replace(' ', '').strip(), 16)) data2 = 'FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF C7FFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FE38FFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFDFF7F FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFF9FF 3FFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFF9 FF3FFFFF FFFFFFFF 9FFEFBFF C7FFFFFF E1FFF8FF FFFFFC3F FFFFFFFF F9FF3FF8 FFFFFFFF FF0FFEFB FF39FF00 7F9C7FE7 2FFFFFF3 C3FC07FF FFF87E78 463F803F F01F0FFE 7BFEFEFF F7FF3F3F 9F8FFFFF EFF3FFBF FFFFFC01 FA3F9FFB FFFE7F9F FE71FCFE 7FF7FF7F 9F9FCFFF FFEFFBFF BFFFFFFF C07E7F9F FBFFFE7F FFFC71F9 FF3FF7FE FF9F3FCF FFFFEFFB FFBFFFFF FFFE7E7F 8FFBFFFE 7FFFFD75 F9FF3FF7 FFFFCF3F CFFFFFE7 FFFFBFFF FFFFFE7E 7F9FFBFF FE7FFFFD 35F9FF3F F7FFFFCF 3FCFFFFF E3FFFFBF FFFFFF80 FE7F9FFB FFFE7FFF FD2CF9FF 3FF7FFFF CF3FCFFF FFF07FFF BFFFFFFF 7CFE7F3F FBFFFE7F FFFB2CF9 FF3FF7FE 000F3FCF FFFFFC1F FFBFFFFF FE7E7E7C 7FFBFFFE 7FFFFBAC F9FF3FF7 FE7FCF3F CFFFFFFF 87FFBFFF FFFE7E7E 03FFFBFF FE7FFFFB 9EF9FF3F F7FE7FCF 3FCFFFFF FFE7FFBF FFFFFEFE 7E7FFFFB FFFE7FFF FB9E79FF 3FF7FE7F 9F3FCFFF FFEFF3FF BFFFFFFE FE7E7F9F FBFFFE7F FFF79E7C FE7FF7FF 3F9F9F8F FFFFEFF3 FFBFFFFF FE7E7F7F 1FFBFFFE 7F1FF79E 7EFCFFF7 FF3F3F9F 0FFFFFE7 F7FFBFFF FFF27EFF 3F3FFBFF FE7F0FE3 8E3F39FF F7FFCE7F C04FFFFF E1CFFF9F FFFFF019 FF9E7FFB FFFE7F1F FFFFFFC7 FFF7FFF1 FFFBCFFF FFEE3FFF 87FFFFFB E7FFE1FF FBFFE00F FFFFFFFF FFFFF7FF FFFFFFCF FFFFFFFF FFFFFFFF FFFFFFFF FFFBFFFE 7FFFFFFF FFFFFFF7 FFFFFFFF CFFFFFFF FFFFFFFF FFFFFFFF FFFFFBFF FE7FFFFF FFFFFFFF F7FFFFFF FFCFFFFF FFFFFFFF FFFFFFFF FFFFFFFB FFFE7FFF FFFFFFFF FFF7FFFF FFFFCFFF FFFFFFFF FFFFFFFF FFFFFFFF FBFE7E7F FFFFFFFF FFFFF7FF FFFFFFCF FFFFFFFF FF3FFFFF FFFFFFFF FFFBFE7E FFFFFFFF FFFFFFF7 FFFFFFFF CFFFFFFF FFFF1FFF FFFFFFFF FFFFFBFE 7CFFFFFF FFFFFFFF F03FFFFF FFC3FFFF FFFFFF1F FFFFFFFF FFFFFFF8 1F03FFFF FFFFFFFF FFF3FFFF FFFFCFFF FFFFFFFF BFFFFFFF FFFFFFFF F9FFFFFF' data2 = bits(int(data2.replace(' ', '').strip(), 16)) cmds = ''' BAR 348, 439, 2, 96 BAR 292, 535, 56, 2 BAR 300, 495, 48, 2 BAR 260, 447, 2, 88 BAR 204, 447, 56, 2 BAR 176, 447, 2, 96 BAR 116, 455, 2, 82 BAR 120, 479, 56, 2 BAR 44, 535, 48, 2 BAR 92, 455, 2, 80 BAR 20, 455, 72, 2 BAR 21, 455, 2, 40 BAR 21, 495, 24, 2 BAR 45, 479, 2, 16 BAR 36, 479, 16, 2 BAR 284, 391, 40, 2 BAR 324, 343, 2, 48 BAR 324, 287, 2, 32 BAR 276, 287, 48, 2 BAR 52, 311, 48, 2 BAR 284, 239, 48, 2 BAR 308, 183, 2, 56 BAR 148, 239, 48, 2 BAR 196, 191, 2, 48 BAR 148, 191, 48, 2 BAR 68, 191, 48, 2 BAR 76, 151, 40, 2 BAR 76, 119, 2, 32 BAR 76, 55, 2, 32 BAR 76, 55, 48, 2 BAR 112, 535, 64, 2 BAR 320, 343, 16, 2 BAR 320, 319, 16, 2 BAR 336, 319, 2, 24 BAR 56, 120, 24, 2 BAR 56, 87, 24, 2 BAR 56, 88, 2, 32 BAR 224, 247, 32, 2 BAR 256, 215, 2, 32 BAR 224, 215, 32, 2 BAR 224, 184, 2, 32 BAR 224, 191, 32, 2 BAR 272, 311, 2, 56 BAR 216, 367, 56, 2 BAR 216, 319, 2, 48 BAR 240, 318, 2, 49 BAR 184, 351, 2, 16 BAR 168, 351, 16, 2 BAR 168, 311, 2, 40 BAR 152, 351, 16, 2 BAR 152, 351, 2, 16 ''' cmds = cmds.strip().split('\n') def draw_bitmap(pixels, x, y, width, height, data): width *= 8 for w in range(width): for h in range(height): rw = w + x rh = h + y pixels[rw, rh] = data1[w+h*width] def draw_bar(pixels, x, y, width, height): for w in range(width): for h in range(height): rw = w + x rh = h + y pixels[rw, rh] = 0 draw_bitmap(pixels, 138, 75, 26, 48, data1) draw_bitmap(pixels, 130,579,29,32, data2) for each in cmds: params = each.replace('BAR ','').split(', ') params = map(int, params) x, y, width, height = params draw_bar(pixels, x, y, width, height) img = img.transpose(Image.ROTATE_180) img.save('test.png')
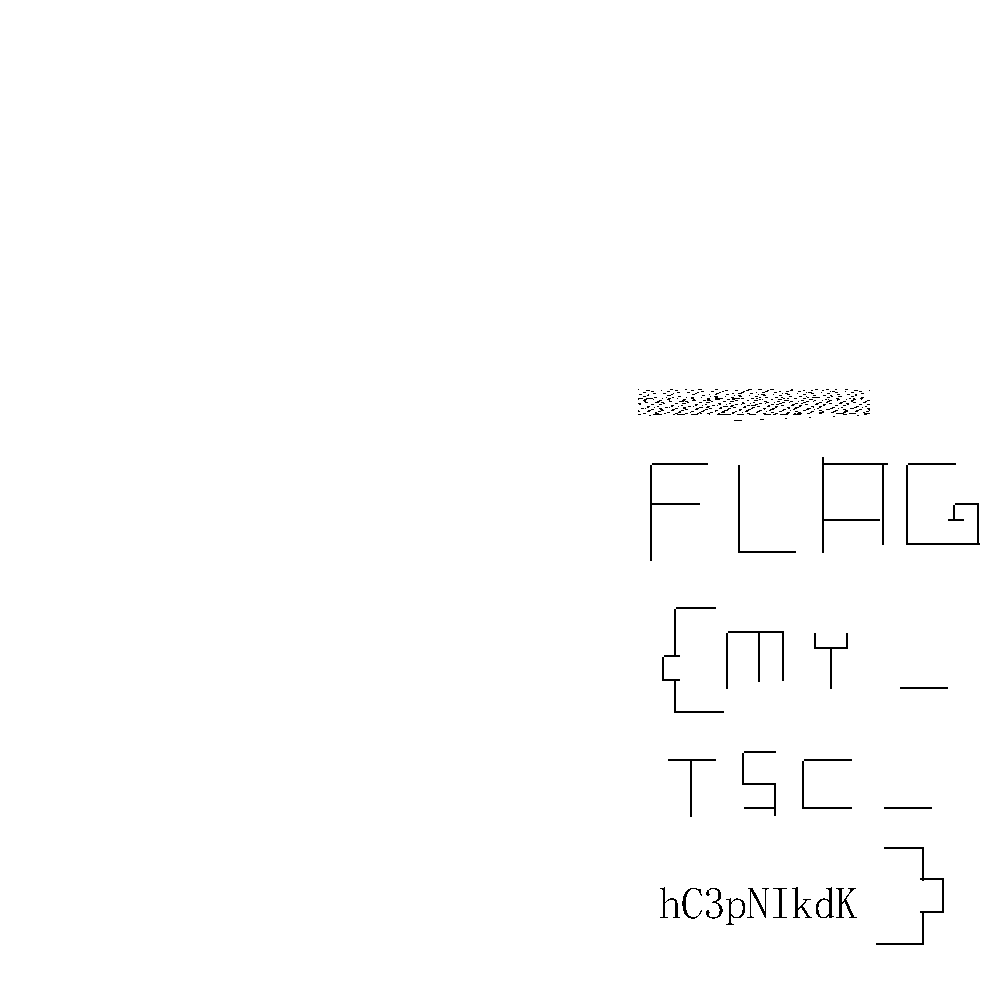
[SWPU2019]Android1
是安卓逆向,先把apk文件放进jadx,发现函数在判断是否登陆后就没有了,但之前调入了一个库文件
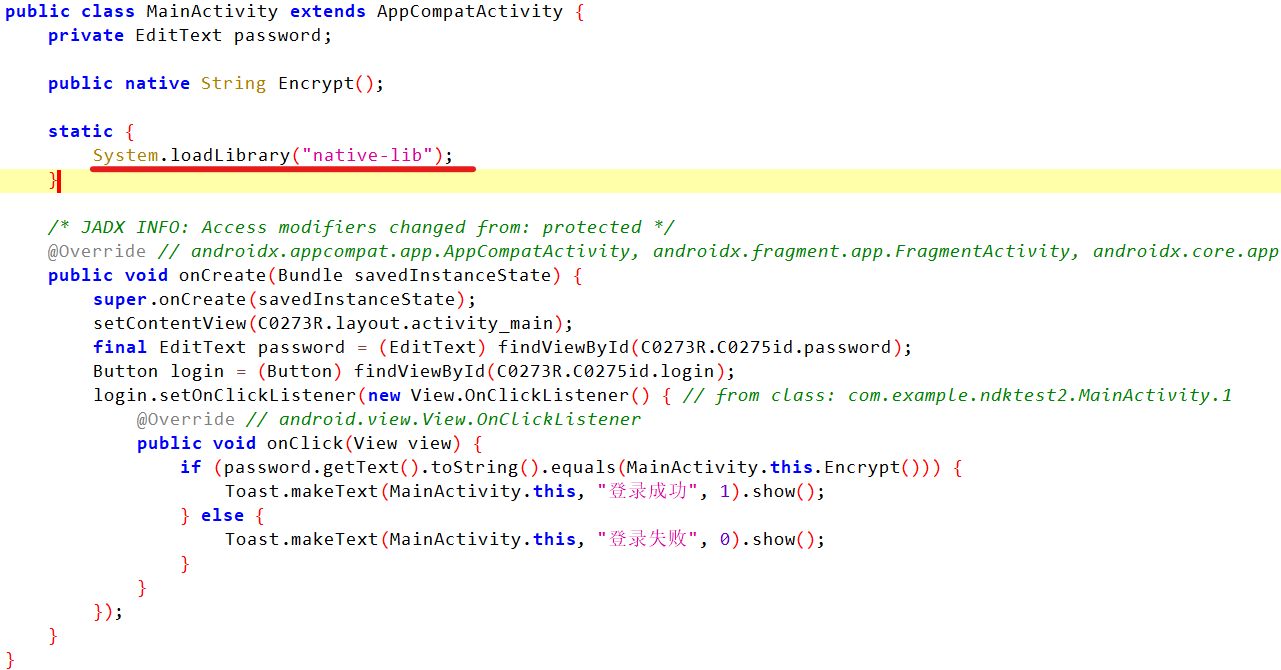
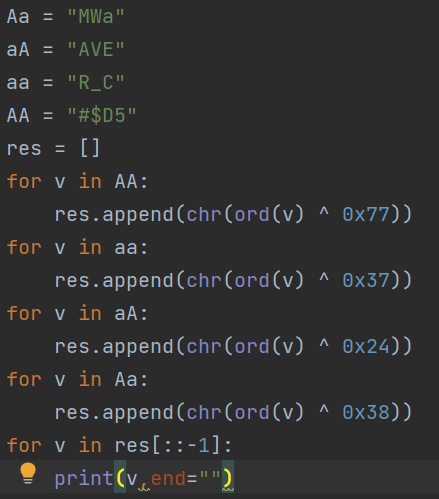
把文件后缀改成zip,在lib文件夹里面取出一个SO文件,放进IDA,发现了Aa,aA,aa,AA四个函数,F5查看伪代码
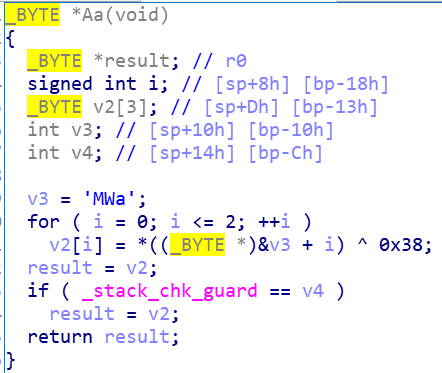
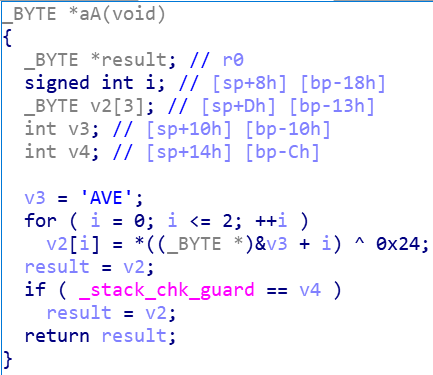
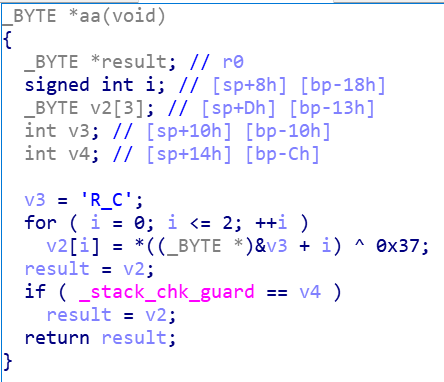
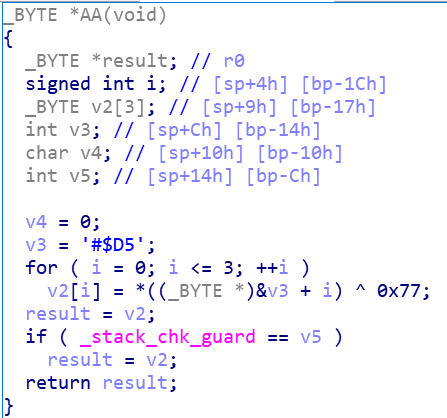
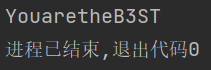
flag应该是每个函数的v3与对应的十六进制数异或得到的字符串,写脚本跑一下,得到flag{YouaretheB3ST}
[SWPU2019]Android2
把apk文件丢进jadx发现报错了,把后缀改成zip,发现真的apk藏在里面,把txt改成apk
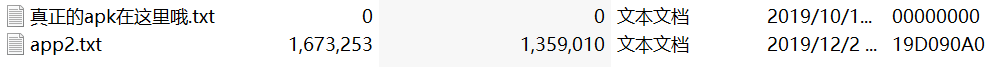
把真的apk文件丢进jadx,发现程序延迟很长且判断永远为假
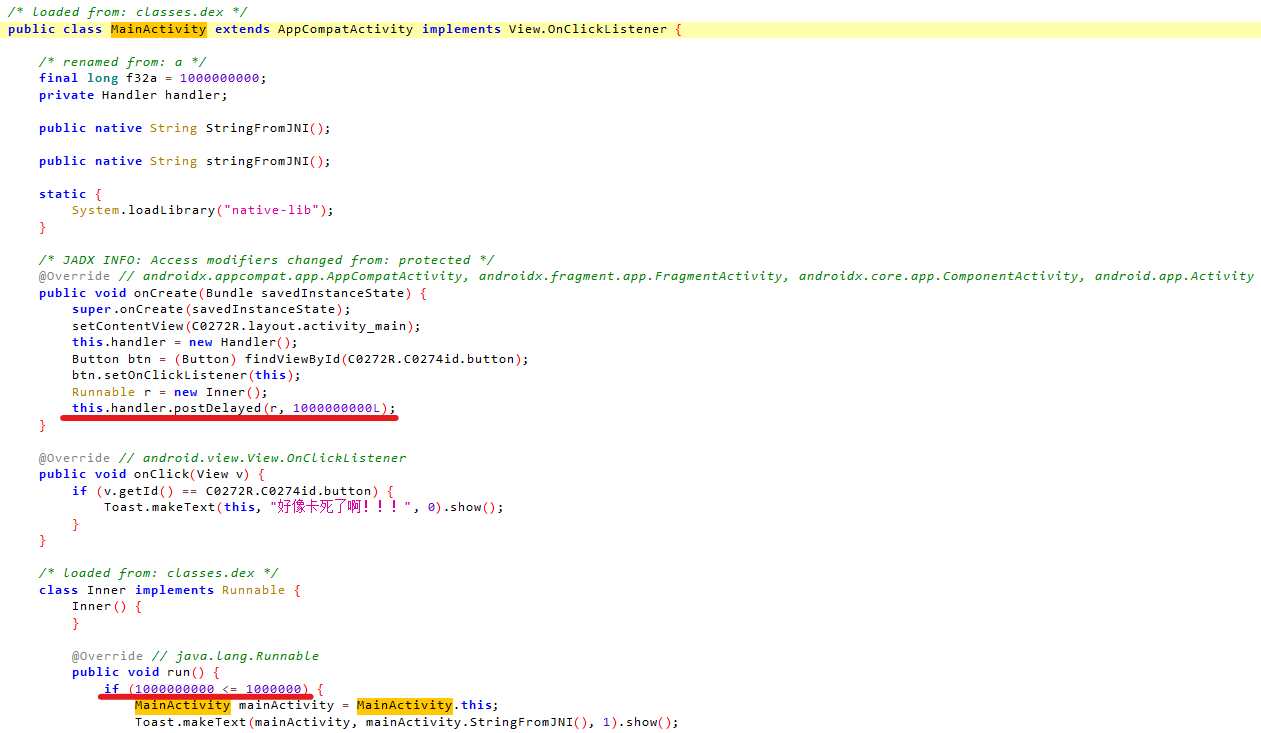
把apk改成zip,在lib里取出一个SO文件,放进IDA,shift+f12找了应该是加密后的flag
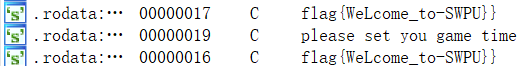
因为里面还有一个加密的函数
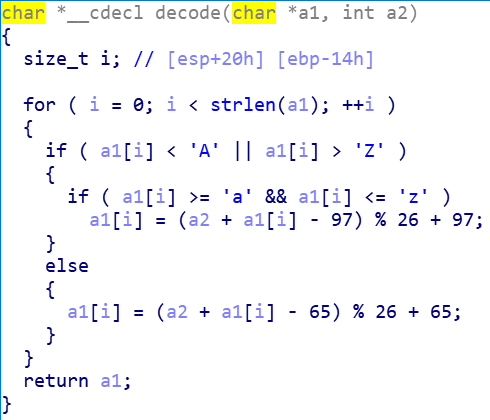
写脚本解密一下
s = "flag{WeLcome_to-SWPU}" for x in range(0,26): for v in s: if v >= "A" and v <= "Z": v = chr(((ord(v) - 65) - x)%26 + 65) if v >= "a" and v <= "z": v = chr(((ord(v) - 97) - x)%26 + 97) print(v,end="") print()
flag{WeLcome_to-SWPU}
ekzf{VdKbnld_sn-RVOT}
djye{UcJamkc_rm-QUNS}
cixd{TbIzljb_ql-PTMR}
bhwc{SaHykia_pk-OSLQ}
agvb{RzGxjhz_oj-NRKP}
zfua{QyFwigy_ni-MQJO}
yetz{PxEvhfx_mh-LPIN}
xdsy{OwDugew_lg-KOHM}
wcrx{NvCtfdv_kf-JNGL}
vbqw{MuBsecu_je-IMFK}
uapv{LtArdbt_id-HLEJ}
tzou{KsZqcas_hc-GKDI}
synt{JrYpbzr_gb-FJCH}
rxms{IqXoayq_fa-EIBG}
qwlr{HpWnzxp_ez-DHAF}
pvkq{GoVmywo_dy-CGZE}
oujp{FnUlxvn_cx-BFYD}
ntio{EmTkwum_bw-AEXC}
mshn{DlSjvtl_av-ZDWB}
lrgm{CkRiusk_zu-YCVA}
kqfl{BjQhtrj_yt-XBUZ}
jpek{AiPgsqi_xs-WATY}
iodj{ZhOfrph_wr-VZSX}
hnci{YgNeqog_vq-UYRW}
gmbh{XfMdpnf_up-TXQV}
最后发现flag是不用解密的,所以flag为flag{BjQhtrj_yt-XBUZ}
[SWPU2019]Android3
把apk文件放进jadx,发现调用了库文件的check
改成zip,把SO文件放进IDA
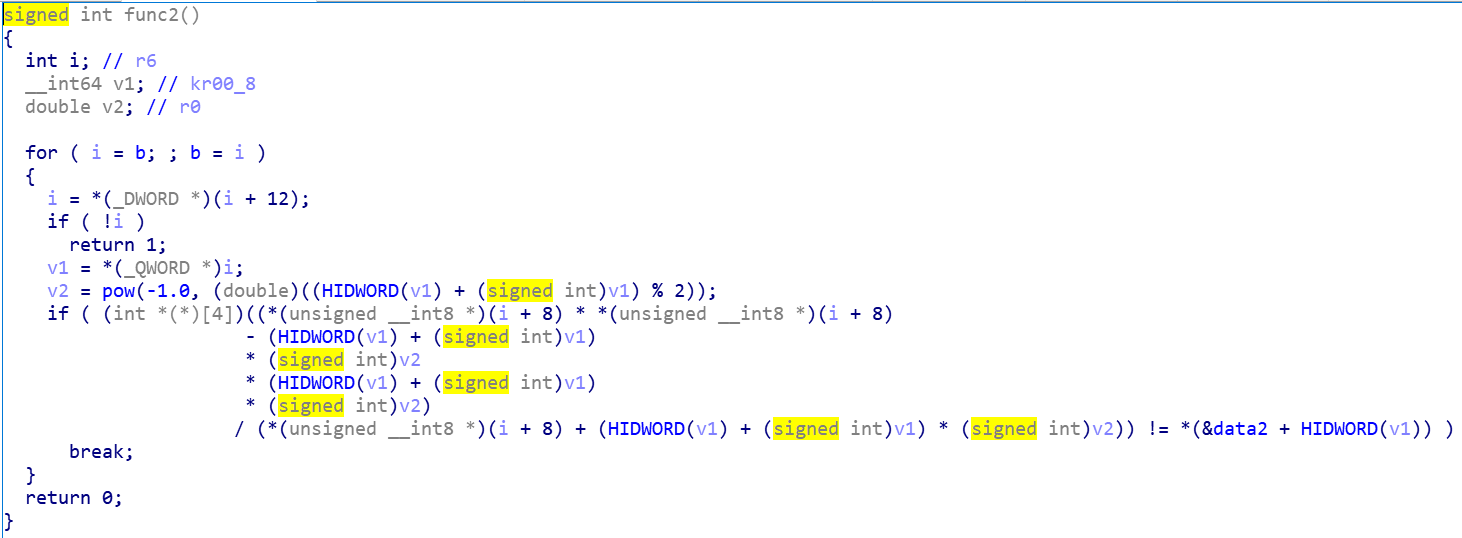
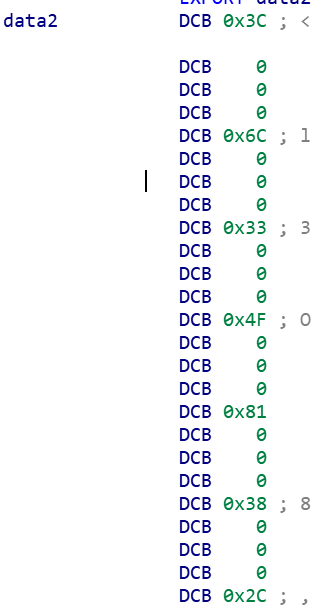
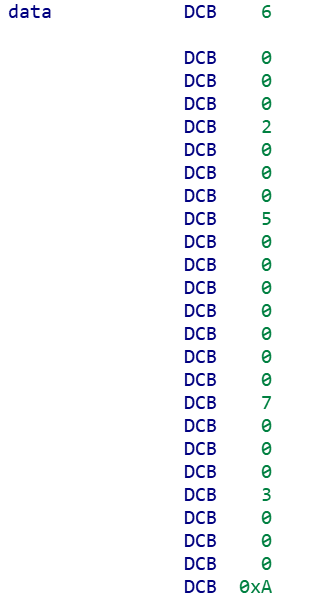
然后写代码跑出flag
a = [60,108,51,79,129,56,44,94,84,69,64] index = [6,2,5,0,7,3,10,9,1,4,8] res = [] for i in range(len(a)): y1 = pow(-1,(index.index(i)+i)%2) res.append(chr(a[i]+y1*(index.index(i)+i))) for v in index: print(res[v],end="")




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理