Kubernetes-ConfigMap、Secret
ConfigMap
一般于管理配置文件、或者一些大量的环境变量信息
创建配置文件
[root@K8S-Master ~]# cat redis.properties
redis.host=127.0.0.1
redis.port=6379
redis.password=123456
创建ConfigMap
[root@K8S-Master ~]# kubectl create configmap redis-config --from-file=redis.properties
[root@K8S-Master ~]# kubectl get configmap
NAME DATA AGE
kube-root-ca.crt 1 118m
redis-config 1 7s
[root@k8s-master ~]# kubectl describe cm redis-config
Name: redis-config
Namespace: default
Labels: <none>
Annotations: <none>
Data
====
redis.properties:
----
redis.host=127.0.0.1
redis.port=6379
redis.password=123456
BinaryData
====
Events: <none>
Volume挂载
# my-config-volume.yaml
apiVersion: v1
kind: Pod
metadata:
name: mypod
spec:
containers:
- name: busybox
image: busybox
command: [ "/bin/sh", "-c","cat /etc/config/redis.properties" ]
volumeMounts:
- name: config-volume
mountPath: /etc/config
volumes:
- name: config-volume
configMap:
name: redis-config
restartPolicy: Never
subPath挂载
ConfigMap和Secret如果是以subPath的形式挂载的,Pod是不会感知到ConfigMap和Secret的更新
# my-config-subpath.yaml
apiVersion: v1
kind: Pod
metadata:
name: mypod
spec:
containers:
- name: busybox
image: busybox
command: [ "/bin/sh", "-c","cat /etc/config/redis.properties" ]
volumeMounts:
- name: config-volume
mountPath: /etc/config
subPath: etc/redis.conf
volumes:
- name: config-volume
configMap:
name: redis-config
items:
- key: redis.conf
path: etc/redis.conf
restartPolicy: Never
env挂载
# myconfig-env.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: myconfig
namespace: default
data:
special.level: info
special.typF: hello
##config-var.yaml
apiVersion: v1
kind: Pod
metadata:
name: mypod
spec:
containers:
- name: busybox
image: busybox
command: [ "/bin/sh", "-c" , "echo $(LEVEL) $(TYPE)" ]
env:
- name: LEVEL
valueFrom:
configMapKeyRef:
name: myconfig
key: special.level
- name: TYPE
valueFrom:
configMapKeyRef:
name: myconfig
key: special.type
restartPolicy: Never
Secret
用于存储敏感信息,如密码、令牌、key、redis密码、mysql密码。
加密:echo -n test|base64
解密:echo -n test|base64 --decodeImagePullSecret:Pod拉取私有镜像仓库时使用的账号密码,里面的账号信息会传递给kubelet,然后kublet就可以拉取有密码的仓库镜像
创建secret加密数据,需要先手动对字符串进行加密
#secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: mysecret
type: Opaque
data:
username: YWRtaW4=
password: MWYyZDFlMmU2N2Rm
指定stringData之后不需要手动进行加密
apiVersion: v1
kind: Secret
metadata:
name: mysecret2
type: Opaque
stringData:
username: admin
password: Password
创建了secret之后,自动将password和username的字符串进行了加密
[root@k8s-master ~]# kubectl get secret mysecret2 -o yaml
apiVersion: v1
data:
password: UGFzc3dvcmQ=
username: YWRtaW4=
kind: Secret
metadata:
name: mysecret2
namespace: default
type: Opaque
$ echo -n UGFzc3dvcmQ= | base64 --decode
Password
$ echo -n YWRtaW4= | base64 --decode
admin
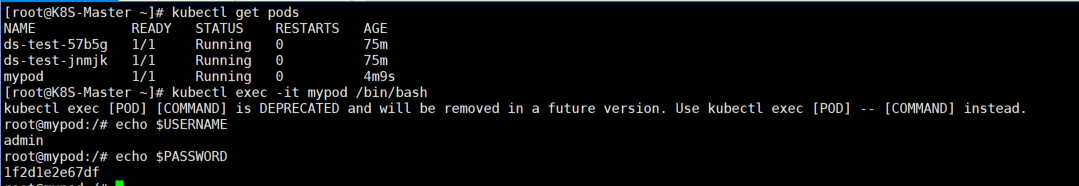
以变量的形式挂载到pod容器中
#secret-var.yaml
apiVersion: v1
kind: Pod
metadata:
name: mypod
spec:
containers:
- name: nginx
image: nginx
env:
- name: USERNAME
valueFrom:
secretKeyRef:
name: mysecret
key: username
- name: PASSWORD
valueFrom:
secretKeyRef:
name: mysecret
key: password


 浙公网安备 33010602011771号
浙公网安备 33010602011771号