linux tomcat【9.0.12】 使用 ssl证书 配置 https 的具体操作 【使用 域名 】
1.前言
根据上一个随笔,已经可以正式在 阿里云服务器发布 工程了 ,但是用的协议默认是 http ,端口80
但是 http不安全 ,容易被拦截抓包 ,于是出来了个 https
tomcat发布 对https 的配置根据版本会有所变化 ,但是其实变化不大
版本9.x版本的tomcat 强制要求证书 别名是tomcat,否则报错
引用官网的解释:

下面的演示是在上一随笔的基础上做的,不清楚 Linux使用公网ip配置tomcat ,请去看完上一随笔【 https://www.cnblogs.com/c2g5201314/p/13058413.html 】
2.操作
(1)进入阿里云后台 ,下载ssl证书和密钥
地址 https://yundun.console.aliyun.com/?spm=5176.10173289.products-recent.dcas.116e2e77ITJsCC&p=cas#/overview/cn-hangzhou
【需要登录才可以访问】
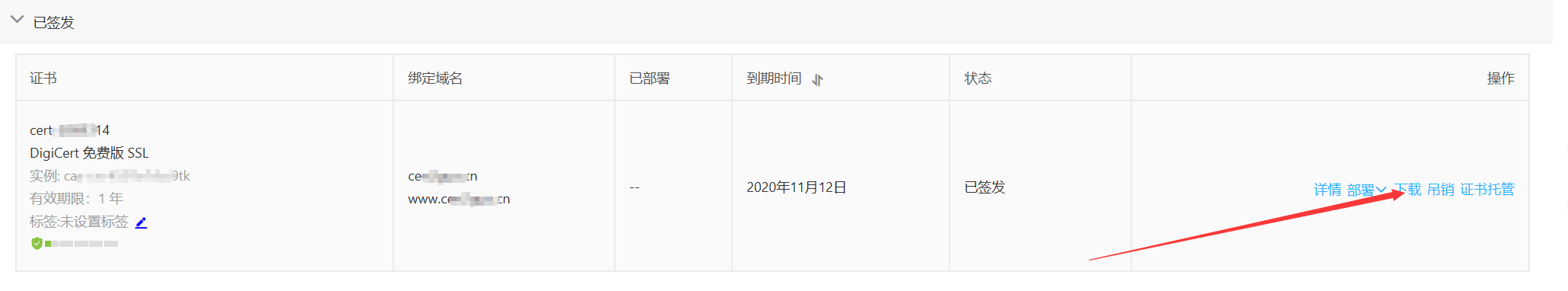
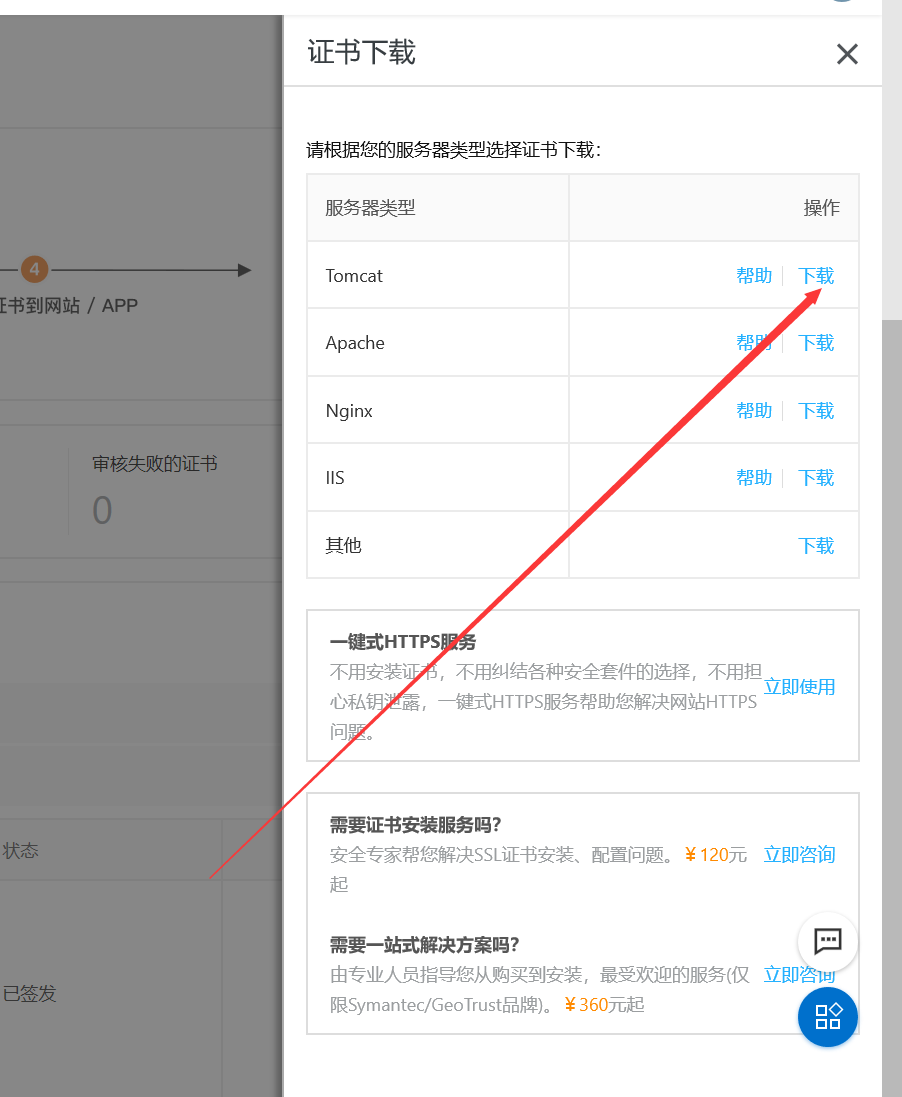
加载的两个文件
在 tomcat根路径新建一个叫cerf的文件夹,将加载的文件拷贝到里面【我是使用xftp传输的】

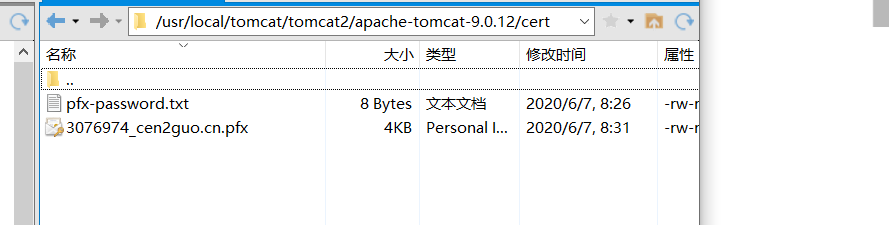
后缀 .pfx 的文件就是安全证书 ,另一个是密钥
(2)我的是tomcat 9.0.12,因此需要修改证书别名 ,不是9.x版本客户省略这一步
需要找到jdk的安装目录,然后找到keytool 的路径

我的是 /usr/local/java/jdk1.8.0_251/bin/keytool
因为 我 的 安全证书 的路径是 /usr/local/tomcat/tomcat2/apache-tomcat-9.0.12/cert/3076974_cen2guo.cn.pfx
因此修改别名的指令
/usr/local/java/jdk1.8.0_251/bin/keytool -changealias -keystore /usr/local/tomcat/tomcat2/apache-tomcat-9.0.12/cert/3076974_cen2guo.cn.pfx -alias alias -destalias tomcat
然后会提示输入密码 ,即密钥文件里的内,回车即可执行【建议直接复制粘贴,手写容易写错,无明文】
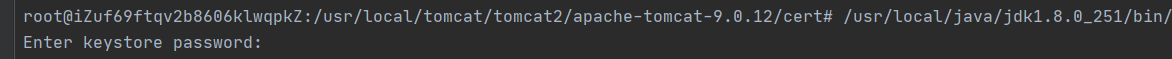
(3)配置server.xml文件
服务节点的 的端口 可以不变 ,如果需要使用域名 ,则直接将 写有 公网ip 的 字符串换成 域名字符串即可【就两个地方,多简单,哈哈哈】


好了回归正题 ,配置 安全证书
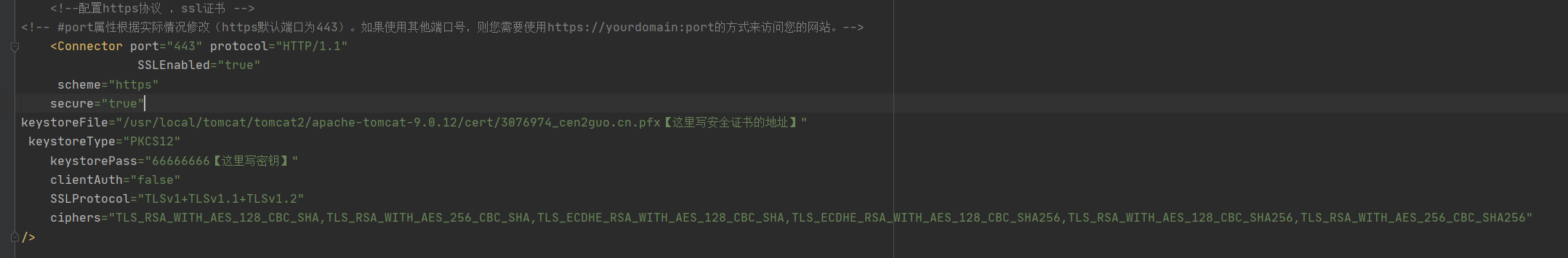
源码

<?xml version="1.0" encoding="UTF-8"?> <!-- Licensed to the Apache Software Foundation (ASF) under one or more contributor license agreements. See the NOTICE file distributed with this work for additional information regarding copyright ownership. The ASF licenses this file to You under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. --> <!-- Note: A "Server" is not itself a "Container", so you may not define subcomponents such as "Valves" at this level. Documentation at /docs/config/server.html --> <Server port="83" shutdown="SHUTDOWN"> <Listener className="org.apache.catalina.startup.VersionLoggerListener" /> <!-- Security listener. Documentation at /docs/config/listeners.html <Listener className="org.apache.catalina.security.SecurityListener" /> --> <!--APR library loader. Documentation at /docs/apr.html --> <Listener className="org.apache.catalina.core.AprLifecycleListener" SSLEngine="on" /> <!-- Prevent memory leaks due to use of particular java/javax APIs--> <Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" /> <Listener className="org.apache.catalina.mbeans.GlobalResourcesLifecycleListener" /> <Listener className="org.apache.catalina.core.ThreadLocalLeakPreventionListener" /> <!-- Global JNDI resources Documentation at /docs/jndi-resources-howto.html --> <GlobalNamingResources> <!-- Editable user database that can also be used by UserDatabaseRealm to authenticate users --> <Resource name="UserDatabase" auth="Container" type="org.apache.catalina.UserDatabase" description="User database that can be updated and saved" factory="org.apache.catalina.users.MemoryUserDatabaseFactory" pathname="conf/tomcat-users.xml" /> </GlobalNamingResources> <!-- A "Service" is a collection of one or more "Connectors" that share a single "Container" Note: A "Service" is not itself a "Container", so you may not define subcomponents such as "Valves" at this level. Documentation at /docs/config/service.html --> <Service name="Catalina"> <!--The connectors can use a shared executor, you can define one or more named thread pools--> <!-- <Executor name="tomcatThreadPool" namePrefix="catalina-exec-" maxThreads="150" minSpareThreads="4"/> --> <!-- A "Connector" represents an endpoint by which requests are received and responses are returned. Documentation at : Java HTTP Connector: /docs/config/http.html Java AJP Connector: /docs/config/ajp.html APR (HTTP/AJP) Connector: /docs/apr.html Define a non-SSL/TLS HTTP/1.1 Connector on port 8080 --> <Connector port="80" protocol="HTTP/1.1" connectionTimeout="20000" redirectPort="82" /> <!-- A "Connector" using the shared thread pool--> <!-- <Connector executor="tomcatThreadPool" port="8080" protocol="HTTP/1.1" connectionTimeout="20000" redirectPort="8443" /> --> <!-- Define a SSL/TLS HTTP/1.1 Connector on port 8443 This connector uses the NIO implementation. The default SSLImplementation will depend on the presence of the APR/native library and the useOpenSSL attribute of the AprLifecycleListener. Either JSSE or OpenSSL style configuration may be used regardless of the SSLImplementation selected. JSSE style configuration is used below. --> <!-- <Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="true"> <SSLHostConfig> <Certificate certificateKeystoreFile="conf/localhost-rsa.jks" type="RSA" /> </SSLHostConfig> </Connector> --> <!-- Define a SSL/TLS HTTP/1.1 Connector on port 8443 with HTTP/2 This connector uses the APR/native implementation which always uses OpenSSL for TLS. Either JSSE or OpenSSL style configuration may be used. OpenSSL style configuration is used below. --> <!--配置https协议 ,ssl证书 --> <!-- #port属性根据实际情况修改(https默认端口为443)。如果使用其他端口号,则您需要使用https://yourdomain:port的方式来访问您的网站。--> <Connector port="443" protocol="HTTP/1.1" SSLEnabled="true" scheme="https" secure="true" keystoreFile="/usr/local/tomcat/tomcat2/apache-tomcat-9.0.12/cert/3076974_cen2guo.cn.pfx【这里写安全证书的地址】" keystoreType="PKCS12" keystorePass="66666666【这里写密钥】" clientAuth="false" SSLProtocol="TLSv1+TLSv1.1+TLSv1.2" ciphers="TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA256" /> <!-- <UpgradeProtocol className="org.apache.coyote.http2.Http2Protocol" /> <SSLHostConfig> <Certificate certificateKeyFile="conf/localhost-rsa-key.pem" certificateFile="conf/localhost-rsa-cert.pem" certificateChainFile="conf/localhost-rsa-chain.pem" type="RSA" /> </SSLHostConfig> </Connector> --> <!-- Define an AJP 1.3 Connector on port 8009 --> <Connector port="81" protocol="AJP/1.3" redirectPort="82" /> <!-- An Engine represents the entry point (within Catalina) that processes every request. The Engine implementation for Tomcat stand alone analyzes the HTTP headers included with the request, and passes them on to the appropriate Host (virtual host). Documentation at /docs/config/engine.html --> <!-- You should set jvmRoute to support load-balancing via AJP ie : <Engine name="Catalina" defaultHost="localhost" jvmRoute="jvm1"> --> <Engine name="Catalina" defaultHost="cen域名.cn"> <!--For clustering, please take a look at documentation at: /docs/cluster-howto.html (simple how to) /docs/config/cluster.html (reference documentation) --> <!-- <Cluster className="org.apache.catalina.ha.tcp.SimpleTcpCluster"/> --> <!-- Use the LockOutRealm to prevent attempts to guess user passwords via a brute-force attack --> <Realm className="org.apache.catalina.realm.LockOutRealm"> <!-- This Realm uses the UserDatabase configured in the global JNDI resources under the key "UserDatabase". Any edits that are performed against this UserDatabase are immediately available for use by the Realm. --> <Realm className="org.apache.catalina.realm.UserDatabaseRealm" resourceName="UserDatabase"/> </Realm> <Host name="cen域名.cn" appBase="" unpackWARs="true" autoDeploy="true"> <!-- path="" 是访问路径 , docBase是war包解压后的文件夹在tomcat里的相对位置 ,reloadable是当配置文件有修改时重启节点--> <Context path="" docBase="webapps/aliyun-html5" reloadable="true" /> <!-- SingleSignOn valve, share authentication between web applications Documentation at: /docs/config/valve.html --> <!-- <Valve className="org.apache.catalina.authenticator.SingleSignOn" /> --> <!-- Access log processes all example. Documentation at: /docs/config/valve.html Note: The pattern used is equivalent to using pattern="common" --> <Valve className="org.apache.catalina.valves.AccessLogValve" directory="logs" prefix="localhost_access_log" suffix=".txt" pattern="%h %l %u %t "%r" %s %b" /> </Host> </Engine> </Service> </Server>
3.测试
启动tomcat ,等几分钟,等<server>节点的关闭端口启动后即可使用浏览器访问
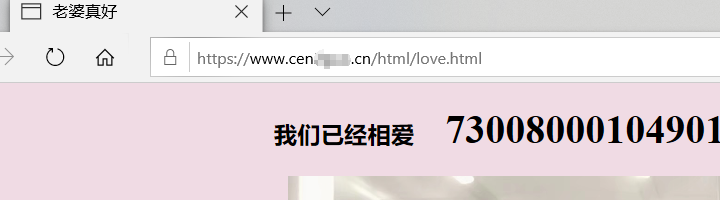
访问 网址 https://cen域名.cn/html/love.html 访问静态前端 ,不需要写端口号443 ,这是https的默认端口,类似于http的80
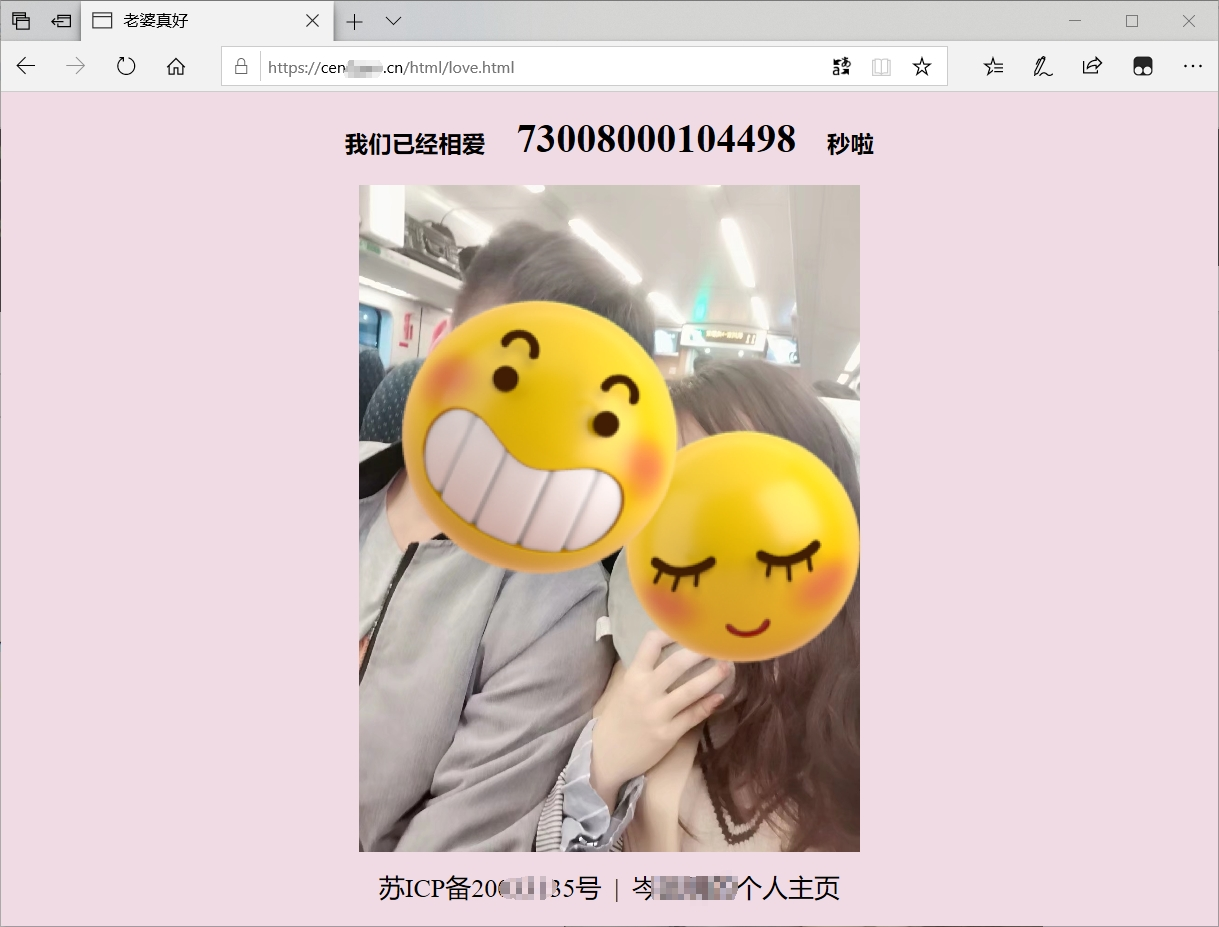
点开网址边上的锁,可以查看证书信息,认证成功
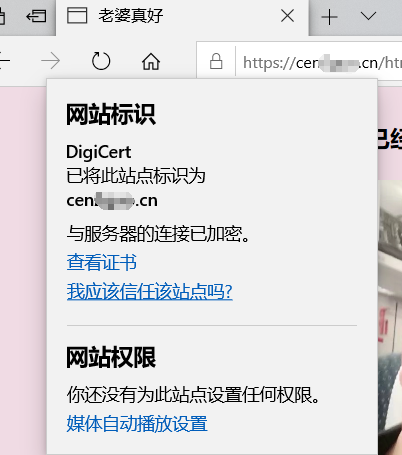
网址也可以添加 www.前缀,这是默认允许的,【一般用来向小白装逼,是我就懒得写】
当然,即便配置了https ,那http其实也是可以用的

本文来自博客园,作者:岑惜,转载请注明原文链接:https://www.cnblogs.com/c2g5201314/p/13063432.html
响应开源精神相互学习,内容良币驱除劣币







【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· go语言实现终端里的倒计时
· 如何编写易于单元测试的代码
· 10年+ .NET Coder 心语,封装的思维:从隐藏、稳定开始理解其本质意义
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· 分享一个免费、快速、无限量使用的满血 DeepSeek R1 模型,支持深度思考和联网搜索!
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· ollama系列01:轻松3步本地部署deepseek,普通电脑可用
· 按钮权限的设计及实现
· 25岁的心里话