【系列】CentOS 7.3 离线安装(无网络环境)CI CD环境之sonarqube配置
目录
1.【系列】CentOS 7.3 离线安装(无网络环境)CI CD环境之docker+docker compose
2.【系列】CentOS 7.3 离线安装(无网络环境)CI CD环境之gitlab + gitlab runner(docker in docker)
3.【系列】CentOS 7.3 离线安装(无网络环境)CI CD环境之harbor
4.【系列】CentOS 7.3 离线安装(无网络环境)CI CD环境之gitlab runner 关于私有docker仓库配置
5.【系列】CentOS 7.3 离线安装(无网络环境)CI CD环境之sonarqube配置 (本篇在此)
接上文,配置完gitlab runner 之后,需要对代码质量进行管理,尽管gitlab已经内置的代码质量检查,但是对.net core 不友好,这里选择使用sonarqube平台进行管理,
sonarqube支持语言多样,质量阈配置灵活,并且可以方便的集成gitlab ci,这里仍然采用docker安装,方便快捷,不污染宿主环境
1.docker compose 运行sonarqube
镜像下载打包至服务器重新加载,此处省略不表,
docker compose :
version: '3' services: postgres: image: postgres:12 restart: unless-stopped ports: - 5432:5432 volumes: - /opt/postgres/postgresql/:/var/lib/postgresql - /opt/postgres/data/:/var/lib/postgresql/data environment: - TZ=Asia/Shanghai - POSTGRES_USER=sonar - POSTGRES_PASSWORD=sonar - POSTGRES_DB=sonarqube networks: - gitlab-network-overlay sonarqube: image: sonarqube:8.4-community ports: - 9000:9000 - 9092:9092 volumes: - /opt/sonarqube/conf:/opt/sonarqube/conf - /opt/sonarqube/extensions:/opt/sonarqube/extensions - /opt/sonarqube/logs:/opt/sonarqube/logs - /opt/sonarqube/bundled-plugins:/opt/sonarqube/lib/bundled-plugins # - /etc/sysctl.conf:/etc/sysctl.conf # - "/root/gitlab-ce/sonarqube/data:/opt/sonarqube/data" environment: sonar.jdbc.username: sonar #root管理员用户密码 sonar.jdbc.password: sonar #创建test用户 sonar.jdbc.url: "jdbc:postgresql://postgres:5432/sonarqube" restart: unless-stopped # depends_on: # - postgres networks: - gitlab-network-overlay # sysctls: # - net.core.somaxconn=1024 networks: gitlab-network-overlay: external: true
使用docker-compose up -d 运行起来,通过ip:9000可以进入sonarqube界面。
2.安装cicd所需sonarqube插件
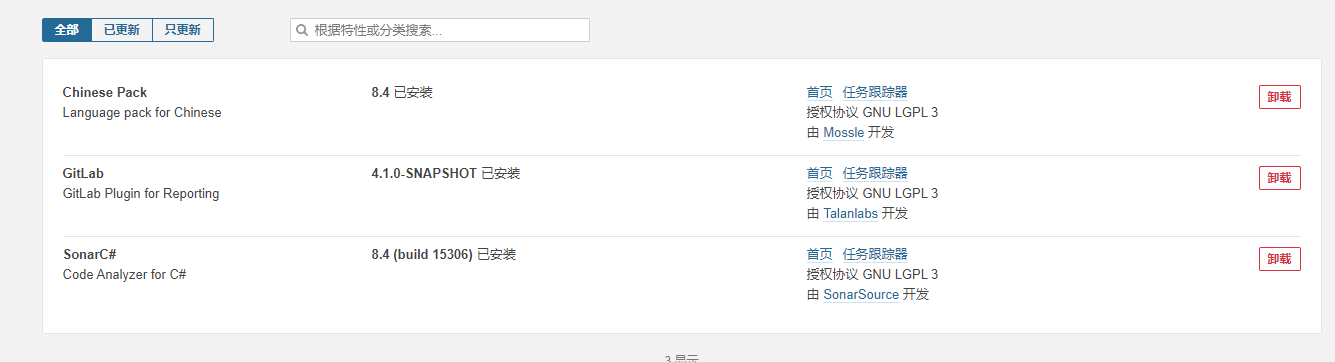
此次需要安装一下三个插件:
Chinese Pack 8.4
GitLab 4.1.0-SNAPSHOT
SonarC# 8.4 (build 15306)
下载地址:https://github.com/carlsonsoft/offline-install-gitlab-cicd/tree/master/sonarqube
下载完成后,将jar包放入sonarqube/extensions/plugins文件夹中,然后重启sonarqube服务,使插件生效
3.sonarqube的配置
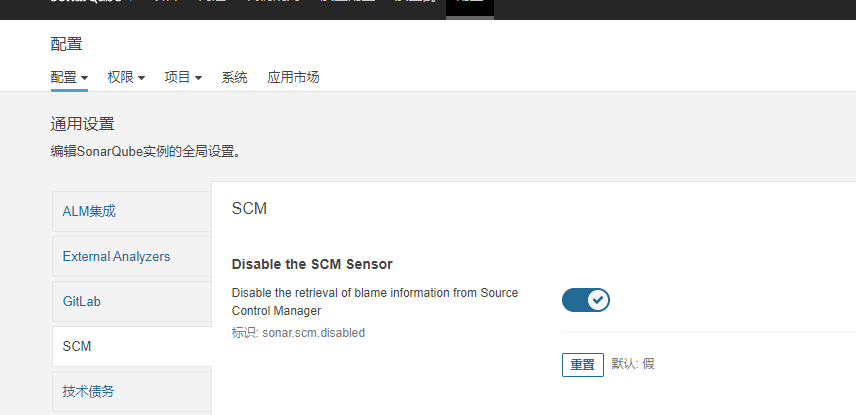
3.1进入配置菜单,选择SCM,将Disable the SCM Sensor设置为true
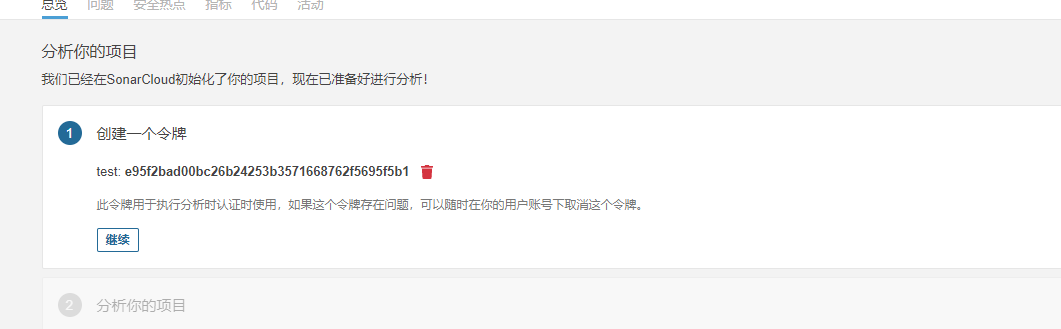
3.2 右上角选择增加项目,输入项目标识和项目显示名称,点击设置,然后设置一个令牌,此处令牌需要记住,后面配置cicd流程会用到
3.3构建ci需要的sonar scanner镜像
这里需要说明一下,使用sonar scaner cli 官方的docker镜像在分析完成后无法在sonarqube上显示,项目始终显示项目主分支为空,所以在这里我使用自己构建的jdk + .net core sdk + sonar scanner msbuild 的镜像
此镜像的dockerfile如下:
FROM openjdk:8u232-jre-stretch LABEL maintainer="Carlson" LABEL github="https://github.com/carlsonsoft/sonar-scanner-net" ENV SONAR_SCANNER_MSBUILD_VERSION=4.8.0.12008 \ DOTNET_3_SDK_VERSION=3.1 \ SONAR_SCANNER_MSBUILD_HOME=/opt/sonar-scanner-msbuild \ DOTNET_PROJECT_DIR=/project \ DOTNET_SKIP_FIRST_TIME_EXPERIENCE=true \ DOTNET_CLI_TELEMETRY_OPTOUT=true RUN mv /etc/apt/sources.list /etc/apt/sources.list.bak && \ echo "deb http://mirrors.163.com/debian/ buster main non-free contrib" >/etc/apt/sources.list && \ echo "deb http://mirrors.163.com/debian/ buster-updates main non-free contrib" >>/etc/apt/sources.list && \ echo "deb http://mirrors.163.com/debian/ buster-backports main non-free contrib" >>/etc/apt/sources.list && \ echo "deb-src http://mirrors.163.com/debian/ buster main non-free contrib" >>/etc/apt/sources.list && \ echo "deb-src http://mirrors.163.com/debian/ buster-updates main non-free contrib" >>/etc/apt/sources.list && \ echo "deb-src http://mirrors.163.com/debian/ buster-backports main non-free contrib" >>/etc/apt/sources.list && \ echo "deb http://mirrors.163.com/debian-security/ buster/updates main non-free contrib" >>/etc/apt/sources.list && \ echo "deb-src http://mirrors.163.com/debian-security/ buster/updates main non-free contrib" >>/etc/apt/sources.list && \ cat /etc/apt/sources.list && \ apt-get clean RUN set -x \ && apt-get update \ && apt-get install \ apt-transport-https \ wget \ -y \ && wget -qO- https://packages.microsoft.com/keys/microsoft.asc | gpg --dearmor > microsoft.asc.gpg \ && mv microsoft.asc.gpg /etc/apt/trusted.gpg.d/ \ && sh -c 'echo "deb [arch=amd64] https://packages.microsoft.com/debian/9/prod stretch main" > /etc/apt/sources.list.d/microsoft-prod.list' \ && apt-get update \ && apt-get install dotnet-sdk-$DOTNET_3_SDK_VERSION -y \ && apt-get clean \ && rm -rf /var/lib/apt/lists/* RUN dotnet tool install dotnet-sonarscanner --tool-path $SONAR_SCANNER_MSBUILD_HOME RUN mkdir -p $DOTNET_PROJECT_DIR ENV PATH="$SONAR_SCANNER_MSBUILD_HOME:${PATH}"
3.4 gitlab增加sonarqube专属账号
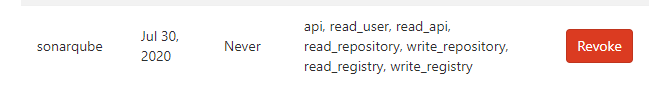
gitlab增加sonarqube账号,并赋予项目维护人员权限,同时配置一个access token,用于将sonarqube分析结果反馈回gitlab
3.5gitlab ci配置(将标红处替换成自己的配置):
3.2步骤中配置的token和gitlab sonarqube的access token在此处就用上了
sonar-analysis: variables: SONAR_PROJECT_BASE_DIR: "${CI_PROJECT_DIR}" GIT_DEPTH: 0 allow_failure: true stage: analysis image: $CI_REGISTRY_LIBRARY/sonarsource/sonar-scanner-net:3.1.0 script: - dotnet sonarscanner begin /k:"gisplatform" /n:"gisplatform" /v:$CI_BUILD_REF /d:sonar.host.url="{sonar url}" /d:sonar.login="{sonar project token}" /d:sonar.gitlab.user_token="{gitlab access token}" /d:sonar.gitlab.url="{gitlab url}" /d:sonar.exclusions="**/wwwroot/**, **/obj/**, **/bin/**" /d:sonar.gitlab.api_version="v4" /d:sonar.gitlab.commit_sha=$CI_BUILD_REF /d:sonar.gitlab.ref_name=$CI_BUILD_REF_NAME /d:sonar.gitlab.project_id=$CI_PROJECT_ID /d:sonar.cs.opencover.reportsPaths=**/coverage.opencover.xml - dotnet build --source {private nuget source} - dotnet test --no-restore /p:CollectCoverage=true /p:CoverletOutputFormat=opencover /p:CoverletOutput='./TestResults/' - dotnet sonarscanner end /d:sonar.login="{sonar project token}" cache: key: "sonar-${CI_PROJECT_ID}" paths: - ".scannerwork" - ".sonar"
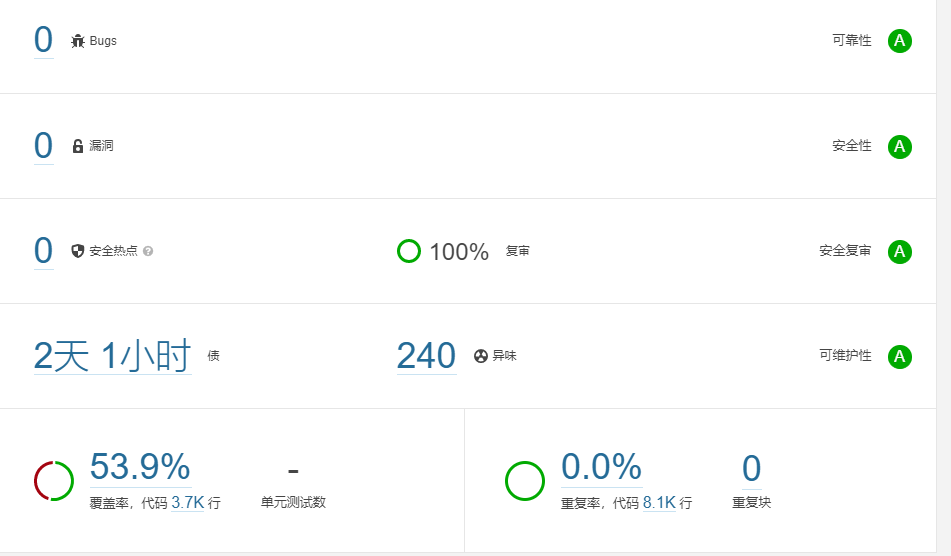
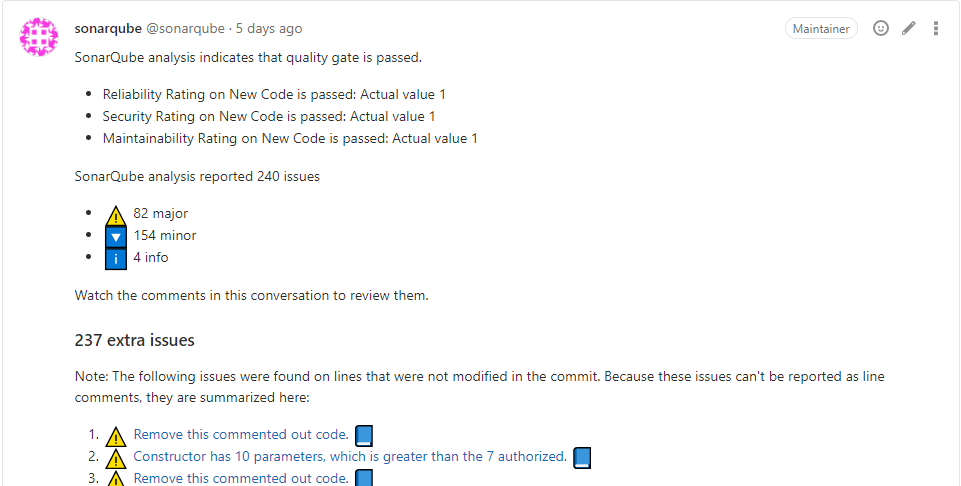
提交代码即可执行流水线并进行代码分析,并且分析结果会反馈到触发此次流水线的commit 的描述中


 浙公网安备 33010602011771号
浙公网安备 33010602011771号