N63050 第八周运维作业
就业需掌握的进度:
十五、加密安全2
1、实现私有CA和证书申请(56分钟)
2、证书管理和ssh服务工作原理(62分钟)
3、ssh客户端使用(44分钟)
4、ssh基于key验证(52分钟)
5、ssh高级用法及自动运维工具(49分钟)
6、sudo进行权限委派(55分钟)
7、cobbler实现系统自动化部署(67分钟)
十六、时间同步及自动化部署
1、pam实现资源限制和google的MFA验证(55分钟)
2、时间同步服务和SELinux安全管理(78分钟)
3、自动化运维和光盘启动文件(27分钟)
4、系统的自动化安装应答文件制作(49分钟)
5、dhcp和tftp服务管理(62分钟)
6、基于PXE实现自动化的系统安装(42分钟)
7、cobbler实现系统自动化部署(67分钟)
第八周就业应完成的作业:
1、创建私有CA并进行证书申请。
1.1创建CA相关目录和文件
[root@centos8 ~]#mkdir /etc/pki/CA/{certs,crl,newcerts,private} -p
[root@centos8 ~]#tree /etc/pki/CA
/etc/pki/CA
├── certs
├── crl
├── newcerts
└── private
4 directories, 0 files
[root@centos8 ~]#cd /etc/pki/CA
[root@centos8 CA]#touch /etc/pki/CA/index.txt
[root@centos8 CA]#ls
certs crl index.txt newcerts private
[root@centos8 CA]#echo 01 > /etc/pki/CA/serial
[root@centos8 CA]#ls
certs crl index.txt newcerts private serial
1.2生成私钥并给CA颁发自签名证书
#生成私钥
[root@centos8 CA]#openssl genrsa -out private/cakey.pem 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
...........+++++
...........................................+++++
e is 65537 (0x010001)
[root@centos8 CA]#ls
certs crl index.txt newcerts private serial
[root@centos8 CA]#ll ./private/cakey.pem
-rw------- 1 root root 1675 Aug 8 17:04 ./private/cakey.pem
[root@centos8 CA]#openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:sichuan
Locality Name (eg, city) [Default City]:chengdu
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:it
Common Name (eg, your name or your server's hostname) []:www.magedu.com
Email Address []:admin@mage.com
[root@centos8 CA]#openssl x509 -in cacert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
15:c1:49:fc:fe:85:45:24:0d:55:fe:7e:8b:b6:f1:d7:6c:18:e1:a4
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = sichuan, L = chengdu, O = magedu, OU = it, CN = www.magedu.com, emailAddress = admin@mage.com
Validity
Not Before: Aug 8 09:11:42 2022 GMT
Not After : Aug 5 09:11:42 2032 GMT
Subject: C = CN, ST = sichuan, L = chengdu, O = magedu, OU = it, CN = www.magedu.com, emailAddress = admin@mage.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:c0:46:2b:1f:4a:3b:cc:bc:00:47:22:45:42:03:
f5:f3:47:17:b4:ff:63:02:77:6a:6e:65:97:12:51:
ce:0b:2f:03:c8:5a:ad:02:0f:f4:87:fb:bc:69:e7:
03:2d:ea:5c:6f:d1:5e:a7:b0:e9:9c:e4:24:c5:81:
af:0d:eb:bf:b7:74:ac:e2:0d:86:ac:e1:c8:3f:7c:
ef:77:cc:49:73:5e:c7:db:d0:95:1f:b4:e6:d3:d1:
ac:ed:24:a8:86:c2:3a:ab:d5:2d:78:33:f5:80:bc:
ec:9c:b8:53:8e:89:3a:86:ca:06:97:3d:9b:d1:9c:
a9:f9:c6:d4:36:ea:07:46:98:b1:67:67:19:20:2c:
00:0b:84:89:fc:75:21:79:78:20:a3:85:dd:68:e3:
65:f6:22:22:22:90:c6:80:d0:2d:40:ea:90:22:47:
76:2c:b9:93:5e:e4:00:3a:92:de:5d:31:4e:17:19:
0d:9f:f0:c2:b4:1f:f9:30:48:9c:3d:eb:38:83:64:
cd:40:cf:34:87:25:8a:87:7b:b0:59:44:b4:9a:56:
24:0b:71:57:d9:48:45:b3:d8:58:67:ab:ff:93:0b:
60:09:27:af:18:37:09:25:54:d8:86:d3:7c:24:16:
c3:9f:53:a7:c0:e7:80:2d:cf:3c:a0:67:23:7b:ba:
ec:f9
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
AA:50:FF:1B:B1:63:0F:75:D4:30:EB:AC:E6:E6:70:50:F0:A7:B2:FF
X509v3 Authority Key Identifier:
keyid:AA:50:FF:1B:B1:63:0F:75:D4:30:EB:AC:E6:E6:70:50:F0:A7:B2:FF
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
1.3用户生成私钥和证书申请
[root@centos8 CA]#midir /data/app1
bash: midir: command not found...
[root@centos8 CA]#mkdir /data/app1
[root@centos8 CA]#ls
cacert.pem certs crl index.txt newcerts private serial
[root@centos8 CA]#tree
.
├── cacert.pem
├── certs
├── crl
├── index.txt
├── newcerts
├── private
│ └── cakey.pem
└── serial
4 directories, 4 files
#用户生成私钥
[root@centos8 CA]#(umask 066; openssl genrsa -out /data/app1/app1.key 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
............................................................+++++
............................+++++
e is 65537 (0x010001)
[root@centos8 CA]#cat /data/app1/app1.key
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA1Z3lSRMKyNr4BgrF6ZddYD9stVXAPVoaSaMD33objIJYBQSl
AUgezyaA2TdmR4LnU+MkIw1+WXyv+6KOJSyIZHjtZnv73J3N9Hrdjp/0e/Unk1yv
EdOvLTlyc+Rr4t280rL8AD+9HhX6f6b/ZdjCaBBb12ifziOjOogiDKH78VHuVGok
W3V0ji3zISc17keWQCpm2JVFUWvdDL0yF2u2b/Mdws5CauFWk4hyL1NdiFCoGoW/
gCjBq9Ta7WQPSncvSHW5dPeL5BoVex5SdN45M0IB75cPNjdjjwKIoKlQEoYCtizw
TSfdpNePHSlGgJ1nzp3+HLWdiuAsolZk4tjWGwIDAQABAoIBACRNBcbKPp3tYBKe
yA0vFMYjYRTbsqR6aFc1JZZXiNDy4YRQyr2SBPJM576CBJaIb0k5I031oBAS+VD4
ydEVZUQ1rJoq3Z0bEAHI01fGZOSfv47yRCnyYCV+Sq3ZFmBiMBFaKyrbqgav03bX
6TTkhfzrMsBDXkzIj5eFxMuCx261nyCZeo/w4BUJymLtFpvkIaTFYDbEl/GBZyFj
PH/b/SYnIYPZXWZZzTjz7lC0hbvSpWj5K3JPVJBl9S8pgCyAU5+cprcCn/okYB7p
shf1eIkf0/2QhVYsJ17ESda6oZfqXohvieJkuB3CH3CueHP+VZv1nmSLPH2gMu7B
WzIRtHkCgYEA6wroglpamrhr4yBotWR8ThBbHXntOIDTi+8VhoFGLf3YwwakavGa
ZsdoWn0lnpqG/FNjNMOCfxMDsRYfvgsjCdGg8Ekv/yJAR9j5g6HwNRELlms2HjIG
A2Wxh+kfiQbYxNElfMddL8QNtEXiMf1JqROueiefi1S9ovVLc46HEQUCgYEA6Knr
qmJ9BoXKiOUmRgnJ3hVl2R+nsFxvwRCLVKBpC0IfseZqUBz1e4mfP1U/jNtAgWwv
7vJft7gW79flDcg5dMqz0NVR1iiF63CuYbE3+aNdcsWUV2ewnbiNgx5eZQq2T6UI
gFPf0KVFZwRJg3saVYO3iQ5+qJ1rjYnprrRzdJ8CgYAGKVULBb9WSvtZCuJzztyL
V1ZsIWQclRP2mR/hVMY4Mm1aP3RT8V1w0E1mAd3YmIhtWOpC2dUz65WvMLtIShZz
DXHAmsqNT6KLv55a2wXm/jllig3zILCTqjjLLUtMVkeccTcgXEGPHP6W+TYCxXcG
3aM3RI6kImaOPQvrTZMw2QKBgQDdISKrPhA2MtLcaW6HAqaqPQwf4MYwCKruhBro
w80StjYJj0Vb/yoR0CtatltANOKKH5kvMY1nv7+NFVTOVI7HQiDFSvoM4Vbm/qG+
mADrcylN/BuRNyvVu6JEDIkK37OG3wPFc/I1C996mciE/mt4+0dlLDGVcIjYbUt8
kGVrYQKBgBvTCoIA1Bep6iYx+TSsr+DE1U333epFZfwlhslXecoXqdxSp+0b+sGG
NkpqpoKhm+4GNQTfCTfjJz1FFQlf5V0/vIfhIlvMjsIem8eZl5eIbfWzoFrtrXY4
drbMrp77nsOtUMmAyby9D1RgclGFOPJdtUtSdsj0qql3xnXyP38N
-----END RSA PRIVATE KEY-----
#用户证书申请
[root@centos8 CA]#openssl req -new -key /data/app1/app1.key -out /data/app1/app1.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:sichuan
Locality Name (eg, city) [Default City]:chengdu
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:sale
Common Name (eg, your name or your server's hostname) []:www.mage.org
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:12345
An optional company name []:magedu
[root@centos8 CA]#ll /data/app1
total 8
-rw-r--r-- 1 root root 1066 Aug 8 17:31 app1.csr
-rw------- 1 root root 1675 Aug 8 17:27 app1.key
#CA证书颁发
[root@centos8 CA]#openssl ca -in /data/app1/app1.csr -out /etc/pki/CA/certs/app1.crt -days 1000
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Aug 8 09:33:22 2022 GMT
Not After : May 4 09:33:22 2025 GMT
Subject:
countryName = CN
stateOrProvinceName = sichuan
organizationName = magedu
organizationalUnitName = sale
commonName = www.mage.org
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
A1:43:BB:7A:84:8F:1D:C9:3F:BC:40:1F:65:B0:6B:86:FD:FE:7E:E1
X509v3 Authority Key Identifier:
keyid:AA:50:FF:1B:B1:63:0F:75:D4:30:EB:AC:E6:E6:70:50:F0:A7:B2:FF
Certificate is to be certified until May 4 09:33:22 2025 GMT (1000 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
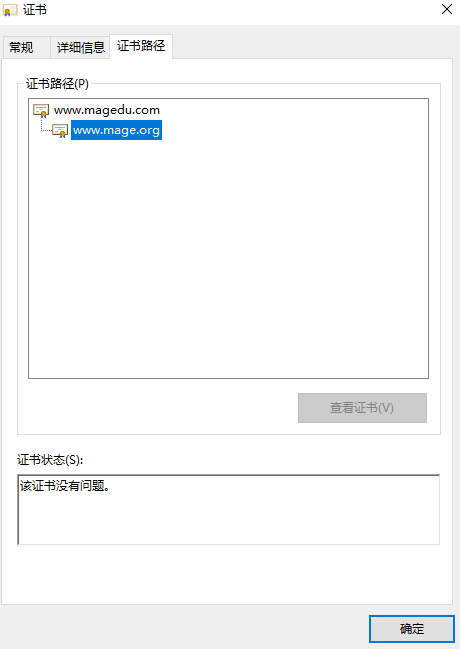
1.4证书的导入
把导出到win的文件名后缀改成cer或是crt,然后生成证书即可
1.5证书吊销
[root@centos8 CA]#openssl ca -revoke /etc/pki/CA/newcerts/02.pem
Using configuration from /etc/pki/tls/openssl.cnf
Revoking Certificate 02.
Data Base Updated
[root@centos8 CA]#openssl ca -status 02
Using configuration from /etc/pki/tls/openssl.cnf
02=Revoked (R)
[root@centos8 CA]#cat /etc/pki/CA/index.txt
V 250504093322Z 01 unknown /C=CN/ST=sichuan/O=magedu/OU=sale/CN=www.mage.org
R 250504102651Z 220808102900Z 02 unknown /C=CN/ST=sichuan/O=magedu/OU=salell/CN=www.mage.com.cn
2、总结ssh常用参数、用法
ssh命令是ssh客户端,允许实现对远程系统经验证地加密安全访问。
格式:
ssh [user@]host [COMMAND]
ssh [-l user] host [COMMAND]
常见选项:
-p port #远程服务器监听的端口
-b #指定连接的源IP
-v #调试模式
-C #压缩方式
-X #支持x11转发
-t #强制伪tty分配,如:ssh -t remoteserver1 ssh -t remoteserver2 ssh
remoteserver3
-o option 如:-o StrictHostKeyChecking=no
-i <file> #指定私钥文件路径,实现基于key验证,默认使用文件: ~/.ssh/id_dsa,
~/.ssh/id_ecdsa, ~/.ssh/id_ed25519,~/.ssh/id_rsa等
3、总结sshd服务常用参数。
服务器端:sshd
服务器端的配置文件: /etc/ssh/sshd_config
服务器端的配置文件帮助:man 5 sshd_config
常用参数:
Port #生产建议修改
ListenAddress ip
LoginGraceTime 2m
PermitRootLogin yes #默认ubuntu不允许root远程ssh登录
StrictModes yes #检查.ssh/文件的所有者,权限等
MaxAuthTries 6 #pecifies the maximum number of authentication
attempts permitted per connection. Once the number of failures reaches half this
value, additional failures are logged. The default is 6.
MaxSessions 10 #同一个连接最大会话
PubkeyAuthentication yes #基于key验证
PermitEmptyPasswords no #空密码连接
PasswordAuthentication yes #基于用户名和密码连接
GatewayPorts no
ClientAliveInterval 10 #单位:秒
ClientAliveCountMax 3 #默认3
UseDNS yes #提高速度可改为no
GSSAPIAuthentication yes #提高速度可改为no
MaxStartups #未认证连接最大值,默认值10
Banner /path/file
#以下可以限制可登录用户的办法:
AllowUsers user1 user2 user3
DenyUsers user1 user2 user3
AllowGroups g1 g2
DenyGroups g1 g2
范例:设置 ssh 空闲60s 自动注销
Vim /etc/ssh/sshd_config
ClientAliveInterval 60
ClientAliveCountMax 0
Service sshd restart
#注意:新开一个连接才有效
范例:解决ssh登录缓慢的问题
vim /etc/ssh/sshd_config
UseDNS no
GSSAPIAuthentication no
systemctl restart sshd
ssh服务的最佳实践
- 建议使用非默认端口
- 禁止使用protocol version 1
- 限制可登录用户
- 设定空闲会话超时时长
- 利用防火墙设置ssh访问策略
- 仅监听特定的IP地址
- 基于口令认证时,使用强密码策略,比如:tr -dc A-Za-z0-9_ < /dev/urandom | head -c 12| xargs
- 使用基于密钥的认证
- 禁止使用空密码
- 禁止root用户直接登录
- 限制ssh的访问频度和并发在线数
- 经常分析日志
4、搭建dhcp服务,实现ip地址申请分发
#安装dhcp服务
[root@centos8 ~]# yum install -y dhcp-server
#查看包文件
[root@centos8 ~]# rpm -ql dhcp-server
/etc/NetworkManager
/etc/NetworkManager/dispatcher.d
/etc/NetworkManager/dispatcher.d/12-dhcpd
/etc/dhcp
/etc/dhcp/dhcpd.conf
/etc/dhcp/dhcpd6.conf
/etc/openldap/schema
/etc/openldap/schema/dhcp.schema
/etc/sysconfig/dhcpd
/usr/bin/omshell
/usr/lib/.build-id
/usr/lib/.build-id/6e
/usr/lib/.build-id/6e/cf67a6508de791165d10349bd963b97f2b89b3
/usr/lib/.build-id/ae
/usr/lib/.build-id/ae/2810922a9be73ff0b4843ab30fc5c3fc77ff86
/usr/lib/systemd/system/dhcpd.service
/usr/lib/systemd/system/dhcpd6.service
/usr/sbin/dhcpd
/usr/share/doc/dhcp-server
/usr/share/doc/dhcp-server/dhcp-lease-list.pl
/usr/share/doc/dhcp-server/dhcpd.conf.example
/usr/share/doc/dhcp-server/dhcpd6.conf.example
/usr/share/doc/dhcp-server/ldap
/usr/share/doc/dhcp-server/ldap/README.ldap
/usr/share/doc/dhcp-server/ldap/dhcp.schema
/usr/share/doc/dhcp-server/ldap/dhcpd-conf-to-ldap
/usr/share/man/man1/omshell.1.gz
/usr/share/man/man5/dhcpd.conf.5.gz
/usr/share/man/man5/dhcpd.leases.5.gz
/usr/share/man/man8/dhcpd.8.gz
/var/lib/dhcpd
/var/lib/dhcpd/dhcpd.leases
/var/lib/dhcpd/dhcpd6.leases
#默认dhcp服务启动文件无法启动,需要拷贝范例,并修改配置
#拷贝范例,覆盖原有配置文件
[root@centos8 ~]# cp /usr/share/doc/dhcp-server/dhcpd.conf.example /etc/dhcp/dhcpd.conf
cp: overwrite '/etc/dhcp/dhcpd.conf'? y
#修改配置文件子网
[root@centos8 ~]# vim /etc/dhcp/dhcpd.conf
#subnet 10.152.187.0 netmask 255.255.255.0 {
subnet 10.0.0.0 netmask 255.255.255.0 {
#已经启动了
[root@centos8 ~]# systemctl start dhcpd
#服务已启动
[root@centos8 ~]# systemctl status dhcpd
● dhcpd.service - DHCPv4 Server Daemon
Loaded: loaded (/usr/lib/systemd/system/dhcpd.service; enabled; vendor preset: disabled)
Active: active (running) since Tue 2022-02-22 12:35:59 CST; 55s ago
Docs: man:dhcpd(8)
man:dhcpd.conf(5)
Main PID: 5300 (dhcpd)
Status: "Dispatching packets..."
Tasks: 1 (limit: 12241)
Memory: 5.4M
CGroup: /system.slice/dhcpd.service
└─5300 /usr/sbin/dhcpd -f -cf /etc/dhcp/dhcpd.conf -user dhcpd -group dhcpd --no-pid
Feb 22 12:35:59 centos8.magedu.org dhcpd[5300]: Source compiled to use binary-leases
Feb 22 12:35:59 centos8.magedu.org dhcpd[5300]: Wrote 0 class decls to leases file.
Feb 22 12:35:59 centos8.magedu.org dhcpd[5300]: Wrote 0 deleted host decls to leases file.
Feb 22 12:35:59 centos8.magedu.org dhcpd[5300]: Wrote 0 new dynamic host decls to leases file.
Feb 22 12:35:59 centos8.magedu.org dhcpd[5300]: Wrote 0 leases to leases file.
Feb 22 12:35:59 centos8.magedu.org dhcpd[5300]: Listening on LPF/eth0/00:0c:29:5e:b6:6f/10.0.0.0/24
Feb 22 12:35:59 centos8.magedu.org dhcpd[5300]: Sending on LPF/eth0/00:0c:29:5e:b6:6f/10.0.0.0/24
Feb 22 12:35:59 centos8.magedu.org dhcpd[5300]: Sending on Socket/fallback/fallback-net
Feb 22 12:35:59 centos8.magedu.org dhcpd[5300]: Server starting service.
Feb 22 12:35:59 centos8.magedu.org systemd[1]: Started DHCPv4 Server Daemon.
#监听udp 67端口
[root@centos8 ~]# ss -ntul
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 0.0.0.0:67 0.0.0.0:*
#修改IP地址获取范围或租期、网关等信息
[root@centos8 ~]# cat /etc/dhcp/dhcpd.conf
#option domain-name-servers ns1.example.org, ns2.example.org;
option domain-name-servers 180.76.76.76, 223.5.5.5; #修改DNS
default-lease-time 86400; #租期
max-lease-time 106400; #最大租期
#subnet 10.152.187.0 netmask 255.255.255.0 {
subnet 10.0.0.0 netmask 255.255.255.0 {
range 10.0.0.150 10.0.0.180; #dhcp范围
option routers 10.0.0.2; #dhcp网关
}
#重启服务
[root@centos8 ~]# systemctl restart dhcpd
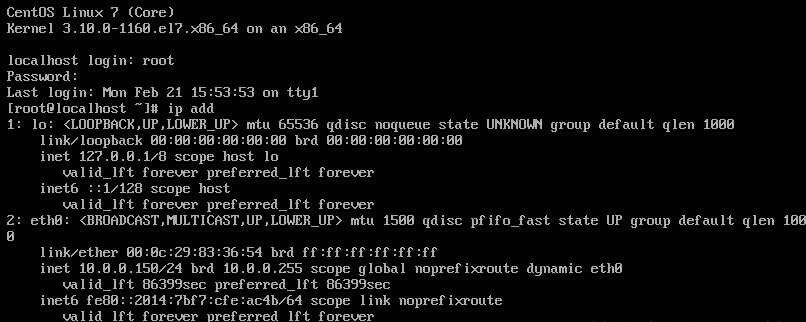
#使用centos7主机测试,需重启centos7主机,如下图,可看到租期时间为86399sec,不是静态获取显示为forever!
#查看分配出去的IP地址
[root@centos8 ~]# cd /var/lib/dhcpd/
[root@centos8 dhcpd]# ll
total 8
-rw-r--r--. 1 dhcpd dhcpd 0 Jun 2 2020 dhcpd6.leases
-rw-r--r--. 1 dhcpd dhcpd 509 Feb 22 12:52 dhcpd.leases
-rw-r--r--. 1 dhcpd dhcpd 509 Feb 22 12:49 dhcpd.leases~
[root@centos8 dhcpd]# cat dhcpd.leases
# The format of this file is documented in the dhcpd.leases(5) manual page.
# This lease file was written by isc-dhcp-4.3.6
# authoring-byte-order entry is generated, DO NOT DELETE
authoring-byte-order little-endian;
server-duid "\000\001\000\001)\247$\257\000\014)^\266o";
lease 10.0.0.150 {
starts 2 2022/02/22 04:52:22; #UTC时间,需加8小时
ends 3 2022/02/23 04:52:22;
cltt 2 2022/02/22 04:52:22;
binding state active;
next binding state free;
rewind binding state free;
hardware ethernet 00:0c:29:83:36:54; #MAC地址
}
#前台执行,查看DHCP获取过程
[root@centos7 ~]# dhclient -d
Internet Systems Consortium DHCP Client 4.2.5
Copyright 2004-2013 Internet Systems Consortium.
All rights reserved.
For info, please visit https://www.isc.org/software/dhcp/
Listening on LPF/eth0/00:0c:29:c7:a5:e1
Sending on LPF/eth0/00:0c:29:c7:a5:e1
Sending on Socket/fallback
DHCPDISCOVER on eth0 to 255.255.255.255 port 67 interval 8 (xid=0x5df1045e) #四个过程
DHCPREQUEST on eth0 to 255.255.255.255 port 67 (xid=0x5df1045e)
DHCPOFFER from 10.0.0.8
DHCPACK from 10.0.0.8 (xid=0x5df1045e)
bound to 10.0.0.152 -- renewal in 36573 seconds. #获取到10.0.0.152 IP地址
#此时主机有一个静态IP和一个动态IP
[root@centos7 ~]# ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:c7:a5:e1 brd ff:ff:ff:ff:ff:ff
inet 10.0.0.7/24 brd 10.0.0.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet 10.0.0.152/24 brd 10.0.0.255 scope global secondary dynamic eth0
valid_lft 86211sec preferred_lft 86211sec
inet6 fe80::20c:29ff:fec7:a5e1/64 scope link
valid_lft forever preferred_lft forever
#编辑配置文件,分配固定IP地址
[root@centos8 ~]# vim /etc/dhcp/dhcpd.conf
host test {
hardware ethernet 00:0c:29:c7:a5:e1;
fixed-address 10.0.0.123;
}
host passacaglia {
hardware ethernet 0:0:c0:5d:bd:95;
filename "vmunix.passacaglia";
server-name "toccata.example.com";
}
#重启服务
[root@centos8 ~]# systemctl restart dhcpd
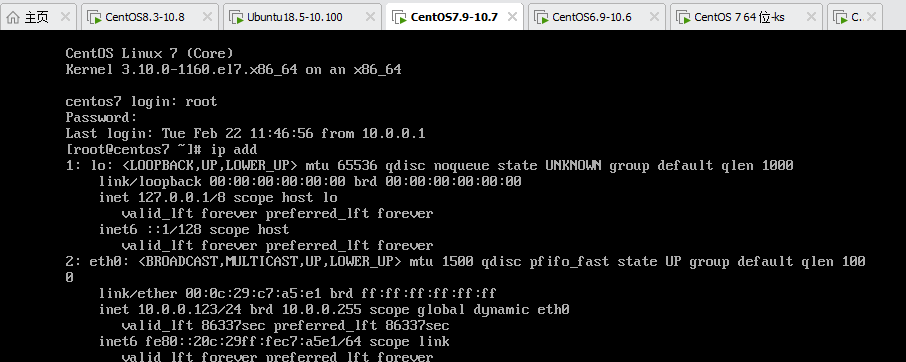
#重新获取IP地址,此时网络会中断
[root@centos7 ~]# dhclient -d
Internet Systems Consortium DHCP Client 4.2.5
Copyright 2004-2013 Internet Systems Consortium.
All rights reserved.
For info, please visit https://www.isc.org/software/dhcp/
Listening on LPF/eth0/00:0c:29:c7:a5:e1
Sending on LPF/eth0/00:0c:29:c7:a5:e1
Sending on Socket/fallback
DHCPREQUEST on eth0 to 255.255.255.255 port 67 (xid=0x15cf2d77)
DHCPNAK from 10.0.0.8 (xid=0x15cf2d77)
#进虚拟机查看获取到的IP地址




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义