kerberos&ssh 原理、免密登录搭建
原理
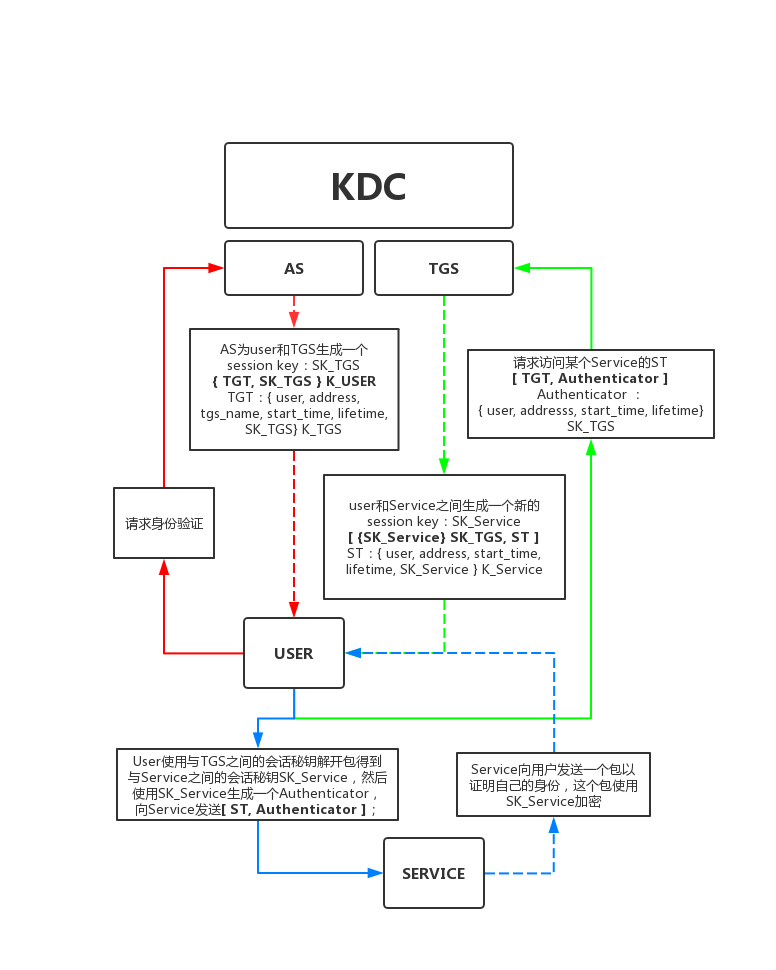
详细介绍
参考oracle文档:Kerberos 服务
安装过程
1.安装krb5
yum install -y krb5-server
yum install krb5-workstation pam_krb5 -y
用hosts代替dns
[root@localhost ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.130.98.196 example.com
10.130.98.196 kerberos.example.com
10.130.98.155 test1.example.com
10.130.98.156 test2.example.com
2.修改krb5配置
vim /etc/krb5.conf
# Configuration snippets may be placed in this directory as well
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
pkinit_anchors = /etc/pki/tls/certs/ca-bundle.crt
default_realm = EXAMPLE.COM
default_ccache_name = KEYRING:persistent:%{uid}
[realms]
EXAMPLE.COM = {
kdc = kerberos.example.com
admin_server = kerberos.example.com
}
[domain_realm]
.example.com = EXAMPLE.COM
example.com = EXAMPLE.COM
3.修改ssh配置
修改后需systemctl restart sshd
3.1 vim /etc/ssh/ssh_config
GSSAPIAuthentication yes
GSSAPIDelegateCredentials yes
3.2 vim /etc/ssh/sshd_config
KerberosAuthentication yes
GSSAPIAuthentication yes
GSSAPICleanupCredentials yes
GSSAPIStrictAcceptorCheck no
GSSAPIKeyExchange yes
4.创建数据库
kdb5_util create -r EXAMPLE.COM -s //建立keberbos鉴权数据库
kadmin.local -q "addprinc root/admin@EXAMPLE.COM" //创建库管理员
5.启动krb5
systemctl start kadmin
systemctl start krb5kdc
systemctl enable krb5kdc
systemctl enable kadmin
6.创建用户
kadmin中
addprinc cjb
用listprincs查看用户
要进kadmin,kdc上可
kadmin.local,通用kadmin -p root/admin
7.创建服务主机
相当于在kdc注册该服务
kadmin中
addprinc -randkey host/test1.example.com
addprinc -randkey host/test2.example.com
8.服务主机保存密钥
在,test1上,kadmin
ktadd -k /etc/krb5.keytab host/test1.example.com
本地查看/etc/krb5.keytab
验证klist -t -e -k /etc/krb5.keytab
可选,此步骤为在本地保存服务key,配置好即可实现免密钥直接登录
9.本地用户获取凭据
kinit cjb
查看获取凭据信息klist
删除凭据kdestroy
10.测试
ssh cjb@test1.example.com
已下载keytab则无需输密码,反之输入kdc中cjb的密码
安装过程问题汇总
1 kadmin、kinit显示无法连接
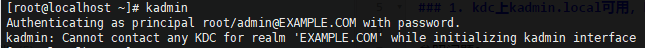
1.1 kdc上kadmin.local可用,kadmin不可用
参照方法2
1.2 检查域名是否可访问
可通过配置/etc/hosts解决

1.3 iptables
通过iptables -F关闭(生产环境不建议这么做)
2 ssh无法验证通过
确保你要登录的那台机子有当前身份账号,无需设置密码(如有设置密码,验证过程先是kdc在验证本地密码)
3 可以通过域名登录,但无法使用ip
例 ssh cjb@10.130.98.156
解决方法:在kdc上注册ip
参考链接
https://www.jianshu.com/p/78564a5ef983?tdsourcetag=s_pctim_aiomsg
https://www.cnblogs.com/gongxin12/articles/9851868.html
https://www.cnblogs.com/xiaodf/p/5968178.html
https://www.cnblogs.com/lsdb/p/11309245.html?tdsourcetag=s_pctim_aiomsg


 浙公网安备 33010602011771号
浙公网安备 33010602011771号