网络安全友商-Cisco -- Stealthwatch
思科的网络安全产品Stealthwatch(现改名为Cisco Secure Network Analytics)主要从网络层面解决安全问题。
其主要功能包括:
1. 威胁狩猎
- 调查网络内恶意软件的持久性
- 发现恶意软件横向移动
2. 网络运维
- 带宽使用增长
- 应用分析
3. 安全运维
- 通过代理检测用户
- 检测流氓系统/设备(Detecting Rogue systems/devices)
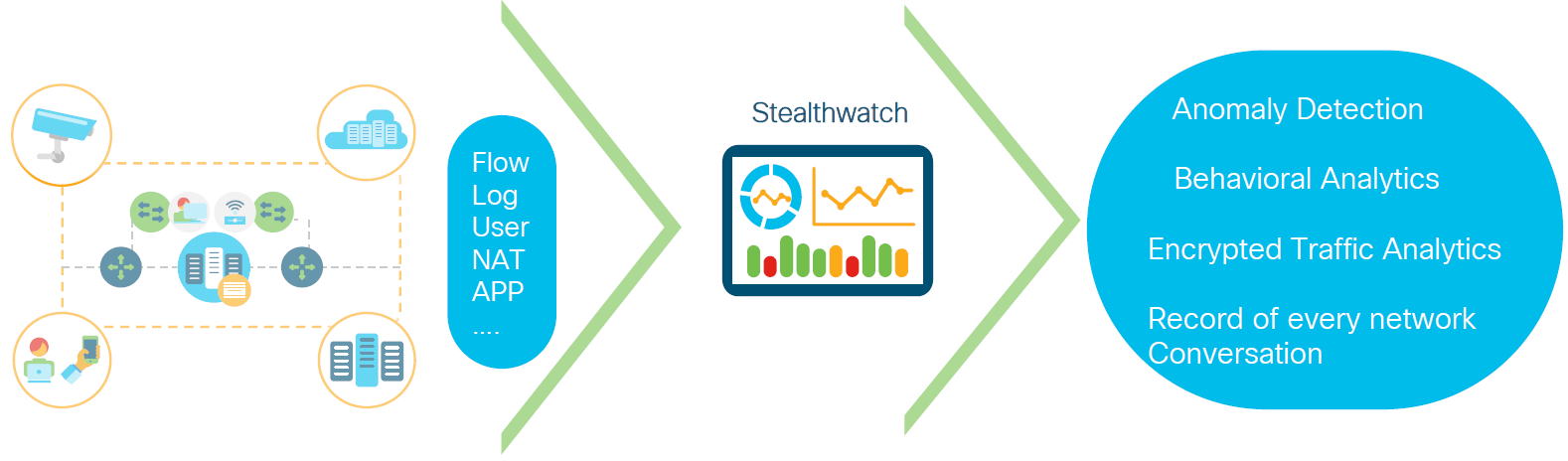
Stealthwatch工作场景
说明1)Stealthwatch 是遥测(telemetry)的收集器和聚合器,目的是安全分析和监控。
说明2)Stealthwatch分为Stealthwatch Enterprise和Stealthwatch cloud两种
Stealthwatch Enterprise包括:
- On-premises appliances(本地设备)
- On-premises telemetry collection, storage and analytics(现场遥测收集、存储和分析)
- (Optional) Cloud Analytics Engine(可选的云分析引擎)
- Cloud hosted (SaaS) telemetry(云托管的遥测收集、存储和分析)
- Public cloud (IaaS) monitoring(公有云监控)
- On-prem visibility and analytics(预置软件可见性和分析)

Stealthwatch Use Cases
思科Stealthwatch为加速事件响应提供全面的网络可见性和威胁检测。Stealthwatch使用案例包括:
- Compliance(合规)
- Verifying Change Control Management
- Using the Copyright Infringement Tool (SMC Web UI)
- Using the Visibility Assessment Application
- Using the Network Diagrams Application
- Using Stealthwatch for Network Segmentations and Policy Development
- Using the ETA Cryptographic Audit Application
- Using Maps to Monitor Host Groups
- Using Encryption Auditing
- Using Custom Security Events to Monitor Firewalls
- Using Bi-Directional Policies
- Reporting Traffic from Specific Geographies
- Monitoring Trusted Third Parties
- Monitoring Remote Access Users
- Monitoring Remote Access with Stealthwatch
- Monitoring Microsoft Update Traffic
- Monitoring Cloud Resources Using Stealthwatch Cloud
- Monitoring Branch Network Traffic
- Monitoring Backup Traffic
- Managing Stealthwatch Users
- Integrating Cisco Stealthwatch® and Identity Services Engine®
- Identifying Medical Asset Types on the Network
- Identifying Applications on the Network
- Identifying Active Endpoint Types
- Determining if a User Violated Access Policies
- Detecting Users Not Traversing the Web Proxy
- Detecting Torrent or File Sharing Traffic
- Detecting Shadow IT in Your Network
- Detecting Rogue and New Devices
- Detecting Obsolete Encryption Protocol
- Detecting Insecure Protocols
- Detecting Application Access Policy Violations
- Defining Business Applications
- Auditing Clients DNS Configurations Using Custom Security Events
- Alarm Category: Policy Violation
- *NEW* Using the ETA Cryptographic Audit Application
- Forensic Investigation(取证分析)
- Reporting Internet URL Access
- Using the Interface Status Report for Security Operations (SMC Web UI)
- Using the Security Event Workflow
- Using Top Reports (SMC Web UI)
- Obtaining Historical Conversations for Unauthorized Data Transfer (SMC Web UI)
- Incident Response(事件响应)
- Determining if a User Violated Access Policies
- Detecting Top Alarming Hosts on the Network
- Detecting Users NotTraversing the Web Proxy
- Detecting Unauthorized Hosts in a Bypass VLAN
- Monitoring Corporate Email
- Using the SMC Web UI for Threat Investigation
- Determining if Internet Hosts are Connecting to Internal Servers
- Network Visibility(网络可见性)
- Using the Interface Status Report for Security Operations (SMC Web UI)
- Investigating unidirectional Traffic
- Investigating NTP Reflection DDoS
- Using the Host Classifier Application
- Using the SMC Web UI for Network Usage Accounting
- Using Stealthwatch for Network Segmentation and Policy Development
- Identifying a Virutal Machine Generating Excessive Traffic
- Stealthwatch Cloud
- Determining if a User Violated Access Policies
- Detecting Top Alarming Hosts on the Network
- Detecting Users NotTraversing the Web Proxy
- Detecting Unauthorized Hosts in a Bypass VLAN
- Monitoring Corporate Email
- Using the SMC Web UI for Threat Investigation
- Determining if Internet Hosts are Connecting to Internal Servers
- Stealthwatch Cloud
- Investigating IP and Port Scans Using Stealthwatch Cloud
- Investigating Potential Threats Using Stealthwatch Cloud
- Investigating Potential Data Exfiltration Using Stealthwatch Cloud
- Detecting Endpoint Deviations Using Stealthwatch Cloud
- Monitoring Cloud Resources Using Stealthwatch Cloud
- System Integration
- Integrating Cisco Stealthwatch® and Identity Services Engine®
- Integrating Stealthwatch Alarms with a SIEM
- Integrating Stealthwatch Alarms with Splunk
- Threat Detection(威胁检测)
- Detecting Application Tunneling
- Detecting ATM Attacks (Jackpotting)
- Detecting Beaconing
- Detecting Bogon Traffic
- Detecting Browser-Based Attacks
- Detecting Command-and-Control Traffic Using the Threat Intelligence
- Detecting Cryptomining Attacks
- Detecting Data Loss
- Detecting DDoS Attacks
- Detecting Emotet Malware with Cognitive Intelligence
- Detecting Endpoint Deviations Using Stealthwatch Cloud
- Detecting Fake Applications
- Detecting Fileless Malware – PowerShell Attacks
- Detecting Fragmentation Attacks
- Detecting Hosts Using Peer-to-Peer Traffic
- Detecting Insecure Protocols
- Detecting Insider Threats (SMC Web UI)
- Detecting Internal Brute Force Attacks
- Detecting Lateral Movement
- Detecting Malware in Encrypted Traffic
- Detecting Malware Propagation
- Detecting Man in the Middle Attacks
- Detecting Password Spray Attacks
- Detecting Remote Access Trojan (RAT) Malware
- Detecting Rogue and New Devices
- Detecting Rogue DHCP Servers
- Detecting Rogue DNS Traffic (SMC Web UI)
- Detecting Shadow IT in Your Network
- Detecting Targeted Attacks
- Detecting Top Alarming Hosts on the Network
- Detecting Tor Traffic
- Detecting Unauthorized Hosts in a Bypass VLAN
- Detecting Unknown or Malicious Scanning on the Network
- Detecting Users Not Traversing the Web Proxy
- Detecting WannaCry Malware
- Determining if Internet Hosts are Connecting to Internal Servers
- Alarm Categories(告警分类)
- Alarm Category: Anomaly
- Alarm Category: Recon
- Alarm Category: Command and Control
- Alarm Category: Data Exfiltration
- Alarm Category: Data Hoarding
- Alarm Category: DDoS
- Alarm Category: Exploitation
- Alarm Category: High Concern and High Target Index
- Alarm Category: Policy Violation
Stealthwatch与其他安全技术比较
Stealthwatch系统收集分析网络遥测(network telemetry)如flow数据(NetFlow, sFlow, JFlow, IPFIX,etc),这些flow数据可以来自于交换机、路由器及防火墙,以便监控网络和用户行为。系统对网络数据执行高级、专有的分析自动化检测标识攻击的异常行为。
Stealthwatch与其他监控解决方案如SIEM(Security Information and Event Management)或全包捕获(full packet capture)进行对比。SIEM技术通过网络资产跟踪syslog,并通过基于签名的工具发出警报和警报。源自失陷主机的syslog日志是不可靠的,并且基于签名的监控工具只能看到它们所访问的内容,而忽略了行为变化。而全包捕获由于其极高的成本和复杂性,只能部署在有限的网络区域。用普遍的、基于行为的监控来补充这些信息源对于填补危险的安全漏洞至关重要。此外,Stealthwatch可以与思科®安全包分析器(Cisco® Security Packet Analyzer)一起使用,以捕获和检查数据包相关的异常流量由Stealthwatch报警。
Stealthwatch超越其他竞争安全技术(包括其他基于flow的监控工具)的原因在于其扩展性(scalability)。消除重复和将单向流量记录拼接在一起的能力,即使是最大、最复杂的企业网络,也能实现成本效益高的流量监控和存储。
Stealthwatch架构和组件
Stealthwatch系统可以定制,但其所需的核心组件是流量许可证(the Flow Rate License),流量收集器(Flow Collector)和管理控制台(the Management Console)。
- 在管理控制台采集、管理和分析流量遥测和汇聚流量需要流量许可证。流量许可证还定义了可收集的流量,并以每秒流量(fps)为基础进行许可。
- 流量收集器利用NetFlow、IPFIX和来自现有基础设施(如路由器、交换机、防火墙、代理服务器、端点和其他网络基础设施设备)的其他类型的流量数据。数据被收集和分析,以提供一个完整的网络活动图。
- Stealthwatch管理控制台从多达25个流收集器、思科身份服务引擎(Cisco Identity Services Engine),和其他来源聚集,组织,并呈现分析。它使用网络流量、身份信息、定制总结报告(customized summary reports)和安全与网络智能一体化进行综合分析。
- 流量传感器用于网络中不支持流量遥测数据的地方。它结合使用深度包检测(DPI)和行为分析来识别网络中使用的应用程序和协议。
- UDP Director是一个高速、高性能的设备,从多个位置接收基本的网络和安全信息。它将单个数据流中的信息转发到一个或多个目的地(如流收集器)
- Stealthwatch云许可证是一个附加许可证,提供了对跨公有、私有和混合云网络基础设施的现有实现的活动和潜在威胁的更大的可视性和增强的意识。
- Stealthwatch终端许可证是一个附加许可证,对显示出可疑行为的终端用户设备提供更高效、上下文丰富的调查。该许可证允许由AnyConnect NVM收集的端点数据在管理控制台中导出和分析。
- Stealthwatch学习网络许可证使用思科集成服务路由器(Cisco Integrated Services Router,ISR)作为安全传感器,以获得对特定分支路由器的流量的深度可见性。它还将行为分析与机器学习、包捕获和分支级威胁的即时检测结合在一起。
- 威胁情报许可证(Threat Intelligence License)接进全球威胁情报源生成警报和事件关注指数(Concern Index),以标记可疑通信,以便迅速调查。
使用案例
| All industries |
● Continuously monitor the extended network |
| Retail |
● Remotely monitor hundreds of systems for security and performance issues ● Safeguard point-of-sale (POS) terminals ● Maintain PCI compliance |
| Healthcare |
● Protect patient records |
| Financial services |
● Detect both outsider and insider threats ● Protect customer data ● Uphold strict compliance requirements ● Maintain 24-hour access to critical financial information ● Find and fix threats and performance issues before they become crises |
| Government |
● Continuously monitor across networks for advanced attacks |
| Higher education |
● Safeguard mobile devices ● Detect Peer-to-Peer (P2P) file sharing ● Protect sensitive information ● Prevent network misuse and abuse ● Maintain high levels of availability and performance ● Streamline security workflows ● Meet regulatory compliance demands |



