恶意代码分析实战 windbg内核恶意代码分析 lab 10-1 10-2(通过rootkit隐藏文件) 有时windbg会卡死 一直busy GG EDR检测rootkit暂无思路
Lab 10-01
本实验包括一个驱动程序和一个可执行文件。你可以从任意位置运行可执行文件,但为了使程序能够正常运行,必须将驱动程序放到C:\Windows\System32目录下,这个目录在受害者计算机中已经存在。可执行文件是Lab10-01.exe,驱动程序是Lab 10-01.sys.
问题
1.这个程序是否直接修改了注册表?
修改了。
2.用户态的程序调用了ControlService函数,你是否能够使用WinDbg设置一个断点,以此来观察由于ControlService的调用导致内核执行了怎样的操作?
修改注册表,关闭防火墙。
3.这个程序做了些什么?
通过创建服务来加载驱动,驱动代码会创建并修改注册表键值来关闭防火墙。
先说下windbg的下载地址:https://pc.qq.com/detail/0/detail_2060.html 还是腾讯软件良心直接收录了,网上下载好用的太难找了。
使用ida对程序**lab 10-01.exe**进行分析。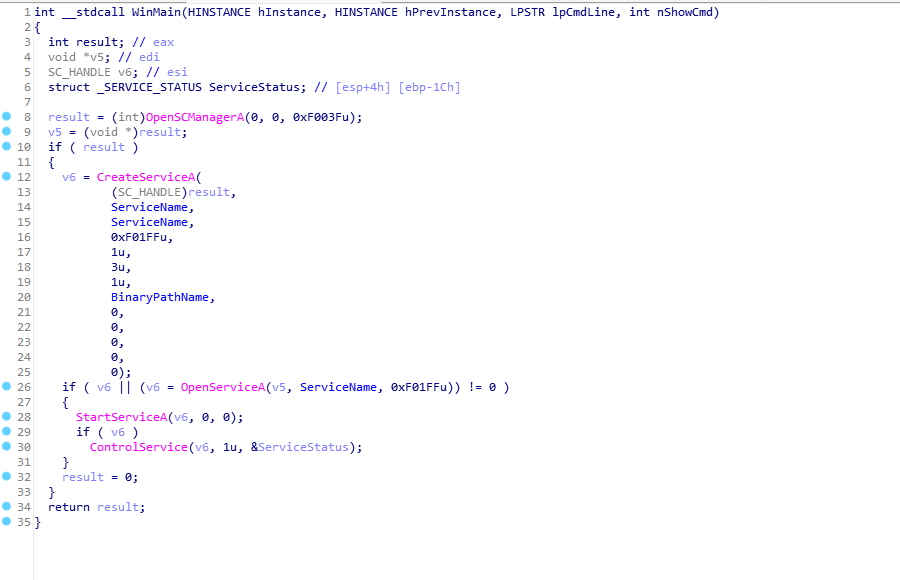
运行看看:
"时间","进程名","PID","操作","路径","结果","详细信息"
"21:31:32.7487660","Lab10-01.exe","2472","Process Start","","SUCCESS","Parent PID: 1796, Command line: ""C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe"" , Current directory: C:\Documents and Settings\Administrator\桌面\lab, Environment: ; =::=::\; ALLUSERSPROFILE=C:\Documents and Settings\All Users; APPDATA=C:\Documents and Settings\Administrator\Application Data; CLIENTNAME=Console; CommonProgramFiles=C:\Program Files\Common Files; COMPUTERNAME=BONELEE-B1632A4; ComSpec=C:\WINDOWS\system32\cmd.exe; FP_NO_HOST_CHECK=NO; HOMEDRIVE=C:; HOMEPATH=\Documents and Settings\Administrator; LOGONSERVER=\\BONELEE-B1632A4; NUMBER_OF_PROCESSORS=4; OS=Windows_NT; Path=C:\WINDOWS\system32;C:\WINDOWS;C:\WINDOWS\System32\Wbem; PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH; PROCESSOR_ARCHITECTURE=x86; PROCESSOR_IDENTIFIER=x86 Family 6 Model 167 Stepping 1, GenuineIntel; PROCESSOR_LEVEL=6; PROCESSOR_REVISION=a701; ProgramFiles=C:\Program Files; SESSIONNAME=Console; SystemDrive=C:; SystemRoot=C:\WINDOWS; TEMP=C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp; TMP=C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp; USERDOMAIN=BONELEE-B1632A4; USERNAME=Administrator; USERPROFILE=C:\Documents and Settings\Administrator; windir=C:\WINDOWS"
"21:31:32.7487673","Lab10-01.exe","2472","Thread Create","","SUCCESS","Thread ID: 2476"
"21:31:32.7489602","Lab10-01.exe","2472","QueryNameInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","Name: \Documents and Settings\Administrator\桌面\lab\Lab10-01.exe"
"21:31:32.7492284","Lab10-01.exe","2472","Load Image","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","Image Base: 0x400000, Image Size: 0x7000"
"21:31:32.7495446","Lab10-01.exe","2472","Load Image","C:\WINDOWS\system32\ntdll.dll","SUCCESS","Image Base: 0x7c920000, Image Size: 0x93000"
"21:31:32.7495621","Lab10-01.exe","2472","QueryNameInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","Name: \Documents and Settings\Administrator\桌面\lab\Lab10-01.exe"
"21:31:32.7497866","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\Prefetch\LAB10-01.EXE-1CC1417D.pf","SUCCESS","Desired Access: Generic Read, Disposition: Open, Options: Synchronous IO Non-Alert, Attributes: n/a, ShareMode: None, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7498790","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\Prefetch\LAB10-01.EXE-1CC1417D.pf","SUCCESS","AllocationSize: 8,192, EndOfFile: 5,154, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7499563","Lab10-01.exe","2472","ReadFile","C:\WINDOWS\Prefetch\LAB10-01.EXE-1CC1417D.pf","SUCCESS","Offset: 0, Length: 5,154"
"21:31:32.7500672","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\Prefetch\LAB10-01.EXE-1CC1417D.pf","SUCCESS",""
"21:31:32.7502083","Lab10-01.exe","2472","CreateFile","C:","SUCCESS","Desired Access: Read Attributes, Write Attributes, Synchronize, Disposition: Open, Options: Synchronous IO Non-Alert, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7503911","Lab10-01.exe","2472","QueryInformationVolume","C:","SUCCESS","VolumeCreationTime: 2022-10-2 3:29:03, VolumeSerialNumber: AC10-70A8, SupportsObjects: True, VolumeLabel: "
"21:31:32.7504064","Lab10-01.exe","2472","FileSystemControl","C:","SUCCESS","Control: FSCTL_FILE_PREFETCH"
"21:31:32.7504351","Lab10-01.exe","2472","CreateFile","C:\","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7504652","Lab10-01.exe","2472","QueryDirectory","C:\","SUCCESS","0: AUTOEXEC.BAT, 1: boot.ini, 2: bootfont.bin, 3: CONFIG.SYS, 4: DLL1.dll, 5: DLL2.dll, 6: Documents and Settings, 7: IO.SYS, 8: Lab09-01.exe, 9: MSDOS.SYS, 10: NTDETECT.COM, 11: ntldr, 12: ocl.exe, 13: pagefile.sys, 14: Program Files, 15: RECYCLER, 16: System Volume Information, 17: WINDOWS"
"21:31:32.7505056","Lab10-01.exe","2472","QueryDirectory","C:\","NO MORE FILES",""
"21:31:32.7505509","Lab10-01.exe","2472","CloseFile","C:\","SUCCESS",""
"21:31:32.7506592","Lab10-01.exe","2472","CreateFile","C:\DOCUMENTS AND SETTINGS","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7506830","Lab10-01.exe","2472","QueryDirectory","C:\Documents and Settings","SUCCESS","0: ., 1: .., 2: Administrator, 3: All Users, 4: Default User, 5: LocalService, 6: NetworkService"
"21:31:32.7507207","Lab10-01.exe","2472","QueryDirectory","C:\Documents and Settings","NO MORE FILES",""
"21:31:32.7507679","Lab10-01.exe","2472","CloseFile","C:\Documents and Settings","SUCCESS",""
"21:31:32.7508421","Lab10-01.exe","2472","CreateFile","C:\Documents and Settings\ADMINISTRATOR","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7509488","Lab10-01.exe","2472","QueryDirectory","C:\Documents and Settings\Administrator","SUCCESS","0: ., 1: .., 2: Application Data, 3: Cookies, 4: Favorites, 5: Local Settings, 6: log.txt, 7: My Documents, 8: NetHood, 9: NTUSER.DAT, 10: ntuser.dat.LOG, 11: ntuser.ini, 12: PrintHood, 13: Recent, 14: SendTo, 15: Templates, 16: UserData, 17: 「开始」菜单, 18: 桌面"
"21:31:32.7509947","Lab10-01.exe","2472","QueryDirectory","C:\Documents and Settings\Administrator","NO MORE FILES",""
"21:31:32.7510819","Lab10-01.exe","2472","CloseFile","C:\Documents and Settings\Administrator","SUCCESS",""
"21:31:32.7512018","Lab10-01.exe","2472","CreateFile","C:\Documents and Settings\Administrator\桌面","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7512682","Lab10-01.exe","2472","QueryDirectory","C:\Documents and Settings\Administrator\桌面","SUCCESS","0: ., 1: .., 2: DLL1.dll, 3: DLL2.dll, 4: Firefox-latest.exe, 5: lab, 6: Lab09-01.exe, 7: Lab09-02.exe, 8: Lab10-02.exe, 9: LieBaoBrowser.exe, 10: NetFx20SP1_x86.exe, 11: ocl.exe, 12: ProcessExplorer-20161118, 13: ProcessExplorer-20161118.zip, 14: ProcessMonitor_3.83, 15: ProcessMonitor_3.83.zip, 16: Procmon汉化版 v3.20.0.0.exe, 17: reg1-202210041846.hivu, 18: Regshot-1.9.0, 19: WinDbg.lnk, 20: Windbgx86-v6.12.2.633.msi, 21: WindowsXP-KB936929-SP3-x86-symbols-full-ENU.exe, 22: winsdk_web.exe, 23: ~res-x86.txt, 24: 快捷方式 到 procexp.lnk, 25: 猎豹安全浏览器.lnk"
"21:31:32.7513485","Lab10-01.exe","2472","QueryDirectory","C:\Documents and Settings\Administrator\桌面","NO MORE FILES",""
"21:31:32.7514376","Lab10-01.exe","2472","CloseFile","C:\Documents and Settings\Administrator\桌面","SUCCESS",""
"21:31:32.7515699","Lab10-01.exe","2472","CreateFile","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7517261","Lab10-01.exe","2472","QueryDirectory","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS","0: ., 1: .., 2: Lab10-01.exe, 3: Lab10-01.sys, 4: Lab10-02.exe, 5: Lab10-03.exe, 6: Lab10-03.sys"
"21:31:32.7518839","Lab10-01.exe","2472","QueryDirectory","C:\Documents and Settings\Administrator\桌面\lab","NO MORE FILES",""
"21:31:32.7519926","Lab10-01.exe","2472","CloseFile","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS",""
"21:31:32.7520911","Lab10-01.exe","2472","CreateFile","C:\WINDOWS","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7521455","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS","SUCCESS","0: ., 1: .., 2: 0.log, 3: addins, 4: AppPatch, 5: assembly, 6: Blue Lace 16.bmp, 7: bootstat.dat, 8: clock.avi, 9: cmsetacl.log, 10: Coffee Bean.bmp, 11: comsetup.log, 12: Config, 13: Connection Wizard, 14: control.ini, 15: Cursors, 16: Debug, 17: desktop.ini, 18: Downloaded Program Files, 19: Driver Cache, 20: DtcInstall.log, 21: ehome, 22: explorer.exe, 23: explorer.scf, 24: FaxSetup.log, 25: FeatherTexture.bmp, 26: Fonts, 27: Gone Fishing.bmp, 28: Greenstone.bmp, 29: Help, 30: hh.exe, 31: iis6.log, 32: ime, 33: imsins.BAK, 34: imsins.log, 35: inf, 36: Installer, 37: java, 38: L2Schemas, 39: MedCtrOC.log, 40: Media, 41: Microsoft.NET, 42: msagent, 43: msapps, 44: msdfmap.ini, 45: msgsocm.log, 46: msmqinst.log, 47: mui, 48: netfxocm.log, 49: Network Diagnostic, 50: NOTEPAD.EXE, 51: ntdtcsetup.log, 52: ocgen.log, 53: ocmsn.log, 54: ODBCINST.INI, 55: OEWABLog.txt, 56: Offline Web Pages, 57: oobeact.log, 58: pchealth, 59: PeerNet, 60: Prairie Wind.bmp, 61: Prefetch, 62: Provisioning, 63: regedit.exe, 64: Registration, 65: REGLOCS.OLD, 66: regopt.log, 67: repair, 68: Resources, 69: Rhododendron.bmp, 70: River Sumida.bmp, 71: Santa Fe Stucco.bmp, 72: SchedLgU.Txt, 73: security, 74: sessmgr.setup.log, 75: SET3.tmp, 76: SET4.tmp, 77: SET8.tmp, 78: setupact.log, 79: setupapi.log, 80: setuperr.log, 81: setuplog.txt, 82: Soap Bubbles.bmp, 83: SoftwareDistribution, 84: srchasst, 85: Sti_Trace.log, 86: Symbols, 87: system, 88: system.ini, 89: system32, 90: tabletoc.log, 91: TASKMAN.EXE, 92: Tasks, 93: Temp, 94: tsoc.log, 95: twain.dll, 96: twain_32, 97: twain_32.dll, 98: twunk_16.exe, 99: twunk_32.exe, 100: vb.ini, 101: vbaddin.ini, 102: vmmreg32.dll, 103: Web, 104: wiadebug.log, 105: wiaservc.log, 106: win.ini, 107: WindowsShell.Manifest, 108: WindowsUpdate.log, 109: winhelp.exe, 110: winhlp32.exe, 111: winnt.bmp, 112: winnt256.bmp, 113: WinSxS, 114: wmprfCHS.prx, 115: wmsetup.log, 116: WMSysPr9.prx, 117: Zapotec.bmp, 118: _default.pif"
"21:31:32.7522363","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS","NO MORE FILES",""
"21:31:32.7523703","Lab10-01.exe","2472","CloseFile","C:\WINDOWS","SUCCESS",""
"21:31:32.7525095","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\AppPatch","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7526004","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS\AppPatch","SUCCESS","0: ., 1: .., 2: AcAdProc.dll, 3: AcGenral.dll, 4: AcLayers.dll, 5: AcLua.dll, 6: AcSpecfc.dll, 7: AcXtrnal.dll, 8: apphelp.sdb, 9: apph_sp.sdb, 10: drvmain.sdb, 11: msimain.sdb, 12: sysmain.sdb"
"21:31:32.7527140","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS\AppPatch","NO MORE FILES",""
"21:31:32.7528747","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\AppPatch","SUCCESS",""
"21:31:32.7530275","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7531285","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: ., 1: .., 2: $winnt$.inf, 3: 1025, 4: 1028, 5: 1031, 6: 1033, 7: 1037, 8: 1041, 9: 1042, 10: 1054, 11: 12520437.cpx, 12: 12520850.cpx, 13: 2052, 14: 3076, 15: 3com_dmi, 16: 6to4svc.dll, 17: a15.tbl, 18: a234.tbl, 19: aaaamon.dll, 20: aaclient.dll, 21: access.cpl, 22: acctres.dll, 23: accwiz.exe, 24: acelpdec.ax, 25: acledit.dll, 26: aclui.dll, 27: acode.tbl, 28: activeds.dll, 29: activeds.tlb, 30: actmovie.exe, 31: actxprxy.dll, 32: admparse.dll, 33: adptif.dll, 34: adsldp.dll, 35: adsldpc.dll, 36: adsmsext.dll, 37: adsnds.dll, 38: adsnt.dll, 39: adsnw.dll, 40: advapi32.dll, 41: advpack.dll, 42: ahui.exe, 43: alg.exe, 44: alrsvc.dll, 45: amcompat.tlb, 46: amstream.dll, 47: ansi.sys, 48: apcups.dll, 49: append.exe, 50: apphelp.dll, 51: appmgmt, 52: appmgmts.dll, 53: appmgr.dll, 54: appwiz.cpl, 55: arp.exe, 56: arphr.tbl, 57: arptr.tbl, 58: array30.tab, 59: arrayhw.tab, 60: asctrls.ocx, 61: asferror.dll, 62: asr_fmt.exe, 63: asr_ldm.exe, 64: asr_pfu.exe, 65: asycfilt.dll, 66: at.exe, 67: atkctrs.dll, 68: atl.dll, 69: atmadm.exe, 70: atmfd.dll, 71: atmlib.dll, 72: atmpvcno.dll, 73: atrace.dll, 74: attrib.exe, 75: audiosrv.dll, 76: auditusr.exe, 77: authz.dll, 78: autochk.exe, 79: autoconv.exe, 80: autodisc.dll, 81: AUTOEXEC.NT, 82: autofmt.exe, 83: autolfn.exe, 84: avicap.dll, 85: avicap32.dll, 86: avifil32.dll, 87: avifile.dll, 88: avmeter.dll, 89: avtapi.dll, 90: avwav.dll, 91: azroles.dll, 92: basesrv.dll, 93: batmeter.dll, 94: batt.dll, 95: bidispl.dll, 96: big5.nls, 97: bios1.rom, 98: bios4.rom, 99: bitsprx2.dll, 100: bitsprx3.dll, 101: bitsprx4.dll, 102: blackbox.dll, 103: blastcln.exe, 104: bootcfg.exe, 105: bootok.exe, 106: bootvid.dll, 107: bootvrfy.exe, 108: bopomofo.nls, 109: bopomofo.uce, 110: browselc.dll, 111: browser.dll, 112: browseui.dll, 113: browsewm.dll, 114: bthci.dll, 115: bthprops.cpl, 116: bthserv.dll, 117: btpanui.dll, 118: cabinet.dll, 119: cabview.dll, 120: cacls.exe, 121: calc.exe, 122: camocx.dll, 123: capesnpn.dll, 124: cards.dll, 125: CatRoot, 126: CatRoot2, 127: catsrv.dll, 128: catsrvps.dll, 129: catsrvut.dll, 130: ccfgnt.dll, 131: cdfview.dll, 132: cdm.dll, 133: cdmodem.dll, 134: cdosys.dll, 135: cdplayer.exe.manifest, 136: certcli.dll, 137: certmgr.dll, 138: certmgr.msc, 139: cewmdm.dll, 140: cfgbkend.dll, 141: cfgmgr32.dll, 142: chajei.ime, 143: charmap.exe, 144: chcp.com, 145: chkdsk.exe, 146: chkntfs.exe, 147: ChsBrKr.dll, 148: chtbrkr.dll, 149: ciadmin.dll, 150: ciadv.msc, 151: cic.dll, 152: cidaemon.exe, 153: CINTLGNT.IME, 154: ciodm.dll, 155: cipher.exe, 156: cisvc.exe, 157: ckcnv.exe, 158: clb.dll, 159: clbcatex.dll, 160: clbcatq.dll, 161: cleanmgr.exe, 162: cliconf.chm, 163: cliconfg.dll, 164: cliconfg.exe, 165: cliconfg.rll, 166: clipbrd.exe, 167: clipsrv.exe, 168: clusapi.dll, 169: cmcfg32.dll, 170: cmd.exe, 171: cmdial32.dll, 172: cmdl32.exe, 173: cmdlib.wsc, 174: cmmgr32.hlp, 175: cmmon32.exe, 176: cmos.ram, 177: cmpbk32.dll, 178: cmprops.dll, 179: cmsetACL.dll, 180: cmstp.exe, 181: cmutil.dll, 182: cnbjmon.dll, 183: cnetcfg.dll, 184: cnvfat.dll, 185: colbact.dll, 186: Com, 187: comaddin.dll, 188: comcat.dll, 189: comctl32.dll, 190: comdlg32.dll, 191: comm.drv, 192: command.com, 193: commdlg.dll, 194: comp.exe, 195: compact.exe, 196: compatUI.dll, 197: compmgmt.msc, 198: compobj.dll, 199: compstui.dll, 200: comrepl.dll, 201: comres.dll, 202: comsnap.dll, 203: comsvcs.dll, 204: comuid.dll, 205: config, 206: CONFIG.NT, 207: CONFIG.TMP, 208: confmsp.dll, 209: conime.exe, 210: console.dll, 211: control.exe, 212: convert.exe, 213: corpol.dll, 214: country.sys, 215: credssp.dll, 216: credui.dll, 217: crtdll.dll, 218: crypt32.dll, 219: cryptdlg.dll, 220: cryptdll.dll, 221: cryptext.dll, 222: cryptnet.dll, 223: cryptsvc.dll, 224: cryptui.dll, 225: cscdll.dll, 226: cscript.exe, 227: cscui.dll, 228: csrsrv.dll, 229: csrss.exe, 230: csseqchk.dll, 231: ctfmon.exe, 232: ctl3d32.dll, 233: ctl3dv2.dll, 234: ctype.nls, 235: c_037.nls, 236: c_10000.nls, 237: c_10001.nls, 238: c_10002.nls, 239: c_10003.nls, 240: c_10006.nls, 241: c_10007.nls, 242: c_10008.nls, 243: c_10010.nls, 244: c_10017."
"21:31:32.7533208","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: dssec.dat, 1: dssec.dll, 2: dssenh.dll, 3: dsuiext.dll, 4: dswave.dll, 5: dumprep.exe, 6: duser.dll, 7: dvdplay.exe, 8: dvdupgrd.exe, 9: dwwin.exe, 10: dx7vb.dll, 11: dx8vb.dll, 12: dxdiag.exe, 13: dxdiagn.dll, 14: dxmasf.dll, 15: dxtmsft.dll, 16: dxtrans.dll, 17: eapolqec.dll, 18: eapp3hst.dll, 19: eappcfg.dll, 20: eappgnui.dll, 21: eapphost.dll, 22: eappprxy.dll, 23: eapqec.dll, 24: eapsvc.dll, 25: edit.com, 26: edit.hlp, 27: edlin.exe, 28: efsadu.dll, 29: ega.cpi, 30: els.dll, 31: emptyregdb.dat, 32: encapi.dll, 33: encdec.dll, 34: EqnClass.Dll, 35: ersvc.dll, 36: es.dll, 37: esent.dll, 38: esent97.dll, 39: esentprf.dll, 40: esentprf.hxx, 41: esentprf.ini, 42: esentutl.exe, 43: eudcedit.exe, 44: eula.txt, 45: eventcls.dll, 46: eventcreate.exe, 47: eventlog.dll, 48: eventquery.vbs, 49: eventtriggers.exe, 50: eventvwr.exe, 51: eventvwr.msc, 52: exe2bin.exe, 53: expand.exe, 54: export, 55: expsrv.dll, 56: extmgr.dll, 57: extrac32.exe, 58: exts.dll, 59: f3ahvoas.dll, 60: fastopen.exe, 61: faultrep.dll, 62: fc.exe, 63: fde.dll, 64: fdeploy.dll, 65: feclient.dll, 66: femgrate.exe, 67: filemgmt.dll, 68: find.exe, 69: findstr.exe, 70: finger.exe, 71: firewall.cpl, 72: fixmapi.exe, 73: fldrclnr.dll, 74: fltlib.dll, 75: fltMc.exe, 76: fmifs.dll, 77: FNTCACHE.DAT, 78: fontext.dll, 79: fontsub.dll, 80: fontview.exe, 81: forcedos.exe, 82: format.com, 83: framebuf.dll, 84: freecell.exe, 85: fsmgmt.msc, 86: fsquirt.exe, 87: fsusd.dll, 88: fsutil.exe, 89: ftp.exe, 90: ftsrch.dll, 91: fwcfg.dll, 92: g711codc.ax, 93: gb2312.uce, 94: gcdef.dll, 95: gdi.exe, 96: gdi32.dll, 97: geo.nls, 98: getmac.exe, 99: getuname.dll, 100: glmf32.dll, 101: glu32.dll, 102: gpedit.dll, 103: gpedit.msc, 104: gpkcsp.dll, 105: gpkrsrc.dll, 106: gpresult.exe, 107: gptext.dll, 108: gpupdate.exe, 109: graftabl.com, 110: graphics.com, 111: graphics.pro, 112: grpconv.exe, 113: h323.tsp, 114: h323log.txt, 115: h323msp.dll, 116: hal.dll, 117: hccoin.dll, 118: hdwwiz.cpl, 119: help.exe, 120: hhctrl.ocx, 121: hhsetup.dll, 122: hid.dll, 123: hidphone.tsp, 124: himem.sys, 125: hlink.dll, 126: hnetcfg.dll, 127: hnetmon.dll, 128: hnetwiz.dll, 129: homepage.inf, 130: hostname.exe, 131: hotplug.dll, 132: hticons.dll, 133: html.iec, 134: httpapi.dll, 135: htui.dll, 136: hypertrm.dll, 137: iac25_32.ax, 138: ias, 139: iasacct.dll, 140: iasads.dll, 141: iashlpr.dll, 142: iasnap.dll, 143: iaspolcy.dll, 144: iasrad.dll, 145: iasrecst.dll, 146: iassam.dll, 147: iassdo.dll, 148: iassvcs.dll, 149: icaapi.dll, 150: iccvid.dll, 151: icfgnt5.dll, 152: icm32.dll, 153: icmp.dll, 154: icmui.dll, 155: icsxml, 156: icwdial.dll, 157: icwphbk.dll, 158: ideograf.uce, 159: idq.dll, 160: ie4uinit.exe, 161: ieakeng.dll, 162: ieaksie.dll, 163: ieakui.dll, 164: iedkcs32.dll, 165: ieencode.dll, 166: iepeers.dll, 167: iernonce.dll, 168: iesetup.dll, 169: ieuinit.inf, 170: iexpress.exe, 171: ifmon.dll, 172: ifsutil.dll, 173: igmpagnt.dll, 174: iissuba.dll, 175: ils.dll, 176: imaadp32.acm, 177: imagehlp.dll, 178: imapi.exe, 179: IME, 180: imegen.tpl, 181: imekr61.ime, 182: imeshare.dll, 183: imgutil.dll, 184: imjp81.ime, 185: imjp81k.dll, 186: imm32.dll, 187: inetcfg.dll, 188: inetcomm.dll, 189: inetcpl.cpl, 190: inetcplc.dll, 191: inetmib1.dll, 192: inetpp.dll, 193: inetppui.dll, 194: inetres.dll, 195: inetsrv, 196: infosoft.dll, 197: initpki.dll, 198: input.dll, 199: inseng.dll, 200: instcat.sql, 201: intl.cpl, 202: iologmsg.dll, 203: ipconf.tsp, 204: ipconfig.exe, 205: iphlpapi.dll, 206: ipmontr.dll, 207: ipnathlp.dll, 208: ippromon.dll, 209: iprop.dll, 210: iprtprio.dll, 211: iprtrmgr.dll, 212: ipsec6.exe, 213: ipsecsnp.dll, 214: ipsecsvc.dll, 215: ipsmsnap.dll, 216: ipv6.exe, 217: ipv6mon.dll, 218: ipxmontr.dll, 219: ipxpromn.dll, 220: ipxrip.dll, 221: ipxroute.exe, 222: ipxrtmgr.dll, 223: ipxsap.dll, 224: ipxwan.dll, 225: ir32_32.dll, 226: ir41_32.ax, 227: ir41_qc.dll, 228: ir41_qcx.dll, 229: ir50_32.dll, 230: ir50_qc.dll, 231: ir50_qcx.dll, 232: irclass.dll, 233: irftp.exe, 234: irmon.dll, 235: irprops.cpl, 236: isign32.dll, 237: isrdbg32.dll, 238: itircl.dll, 239: itss.dll, 240: iuengine.d"
"21:31:32.7535113","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: mfc42.dll, 1: mfc42loc.dll, 2: mfc42u.dll, 3: mfc71.dll, 4: mfc71u.dll, 5: mfcsubs.dll, 6: mgmtapi.dll, 7: mib.bin, 8: Microsoft, 9: microsoft.managementconsole.dll, 10: midimap.dll, 11: miglibnt.dll, 12: migpwd.exe, 13: mimefilt.dll, 14: miniime.tpl, 15: mlang.dat, 16: mlang.dll, 17: mll_hp.dll, 18: mll_mtf.dll, 19: mll_qic.dll, 20: Mlwx486.sys, 21: mmc.exe, 22: mmcbase.dll, 23: mmcex.dll, 24: mmcfxcommon.dll, 25: mmcndmgr.dll, 26: mmcperf.exe, 27: mmcshext.dll, 28: mmdriver.inf, 29: mmdrv.dll, 30: mmfutil.dll, 31: mmsys.cpl, 32: mmsystem.dll, 33: mmtask.tsk, 34: mmutilse.dll, 35: mnmdd.dll, 36: mnmsrvc.exe, 37: mobsync.dll, 38: mobsync.exe, 39: mode.com, 40: modemui.dll, 41: modex.dll, 42: more.com, 43: moricons.dll, 44: mountvol.exe, 45: mouse.drv, 46: mp43dmod.dll, 47: mp4sdmod.dll, 48: mpeg2data.ax, 49: mpg2splt.ax, 50: mpg4dmod.dll, 51: mpg4ds32.ax, 52: mplay32.exe, 53: mpnotify.exe, 54: mpr.dll, 55: mprapi.dll, 56: mprddm.dll, 57: mprdim.dll, 58: mprmsg.dll, 59: mprui.dll, 60: mqad.dll, 61: mqbkup.exe, 62: mqcertui.dll, 63: mqdscli.dll, 64: mqgentr.dll, 65: mqise.dll, 66: mqlogmgr.dll, 67: mqoa.dll, 68: mqoa.tlb, 69: mqoa10.tlb, 70: mqoa20.tlb, 71: mqperf.dll, 72: mqperf.ini, 73: mqprfsym.h, 74: mqqm.dll, 75: mqrt.dll, 76: mqrtdep.dll, 77: mqsec.dll, 78: mqsnap.dll, 79: mqsvc.exe, 80: mqtgsvc.exe, 81: mqtrig.dll, 82: mqupgrd.dll, 83: mqutil.dll, 84: mrinfo.exe, 85: msaatext.dll, 86: msacm.dll, 87: msacm32.dll, 88: msacm32.drv, 89: msadds32.ax, 90: msadp32.acm, 91: msafd.dll, 92: msapsspc.dll, 93: msasn1.dll, 94: msaud32.acm, 95: msaudite.dll, 96: mscat32.dll, 97: mscdexnt.exe, 98: mscms.dll, 99: msconf.dll, 100: mscoree.dll, 101: mscorier.dll, 102: mscories.dll, 103: mscpx32r.dLL, 104: mscpxl32.dLL, 105: MSCTF.dll, 106: MSCTFIME.IME, 107: MSCTFP.dll, 108: msdadiag.dll, 109: msdart.dll, 110: msdatsrc.tlb, 111: msdayi.tbl, 112: msdmo.dll, 113: MsDtc, 114: msdtc.exe, 115: msdtclog.dll, 116: msdtcprf.h, 117: msdtcprf.ini, 118: msdtcprx.dll, 119: msdtctm.dll, 120: msdtcuiu.dll, 121: msdxm.ocx, 122: msdxmlc.dll, 123: msencode.dll, 124: msexch40.dll, 125: msexcl40.dll, 126: msftedit.dll, 127: msg.exe, 128: msg711.acm, 129: msg723.acm, 130: msgina.dll, 131: msgsm32.acm, 132: msgsvc.dll, 133: msh261.drv, 134: msh263.drv, 135: mshearts.exe, 136: mshta.exe, 137: mshtml.dll, 138: mshtml.tlb, 139: mshtmled.dll, 140: mshtmler.dll, 141: msi.dll, 142: msident.dll, 143: msidle.dll, 144: msidntld.dll, 145: msieftp.dll, 146: msiexec.exe, 147: msihnd.dll, 148: msimg32.dll, 149: msimsg.dll, 150: MSIMTF.dll, 151: msir3jp.dll, 152: msir3jp.lex, 153: msisip.dll, 154: msjet40.dll, 155: msjetoledb40.dll, 156: msjint40.dll, 157: msjter40.dll, 158: msjtes40.dll, 159: mslbui.dll, 160: msls31.dll, 161: msltus40.dll, 162: msnetobj.dll, 163: msnsspc.dll, 164: msobjs.dll, 165: msoeacct.dll, 166: msoert2.dll, 167: msorc32r.dll, 168: msorcl32.dll, 169: mspaint.exe, 170: mspatcha.dll, 171: mspbde40.dll, 172: mspmsnsv.dll, 173: mspmsp.dll, 174: msports.dll, 175: msprivs.dll, 176: msr2c.dll, 177: msr2cenu.dll, 178: msratelc.dll, 179: msrating.dll, 180: msrclr40.dll, 181: msrd2x40.dll, 182: msrd3x40.dll, 183: msrecr40.dll, 184: msrepl40.dll, 185: msrle32.dll, 186: mssap.dll, 187: msscds32.ax, 188: msscp.dll, 189: msscript.ocx, 190: mssha.dll, 191: msshavmsg.dll, 192: mssign32.dll, 193: mssip32.dll, 194: msswch.dll, 195: msswchx.exe, 196: mstask.dll, 197: mstext40.dll, 198: mstime.dll, 199: mstinit.exe, 200: mstlsapi.dll, 201: mstsc.exe, 202: mstscax.dll, 203: msutb.dll, 204: msv1_0.dll, 205: msvbvm50.dll, 206: msvbvm60.dll, 207: msvcirt.dll, 208: msvcp50.dll, 209: msvcp60.dll, 210: msvcr71.dll, 211: msvcrt.dll, 212: msvcrt20.dll, 213: msvcrt40.dll, 214: msvfw32.dll, 215: msvidc32.dll, 216: msvidctl.dll, 217: msvideo.dll, 218: msw3prt.dll, 219: mswdat10.dll, 220: mswebdvd.dll, 221: mswmdm.dll, 222: mswsock.dll, 223: mswstr10.dll, 224: msxbde40.dll, 225: msxml.dll, 226: msxml2.dll, 227: msxml2r.dll, 228: msxml3.dll, 229: msxml3r.dll, 230: msxml6.dll, 231: msxml6r.dll, 232: msxmlr.dll, 233: msyuv.dll, 234: mtxclu.dll, 235: mtxdm.dll, 236: mtxex.dll, 2"
"21:31:32.7536684","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: phoncode.tbl, 1: phonptr.tbl, 2: photometadatahandler.dll, 3: photowiz.dll, 4: pid.dll, 5: pid.inf, 6: pid.PNF, 7: pidgen.dll, 8: pifmgr.dll, 9: ping.exe, 10: ping6.exe, 11: PINTLGNT.IME, 12: PINTLPAD.HLP, 13: PINTLPAE.HLP, 14: pjlmon.dll, 15: plustab.dll, 16: pmspl.dll, 17: pngfilt.dll, 18: pnrpnsp.dll, 19: polstore.dll, 20: powercfg.cpl, 21: powercfg.exe, 22: powrprof.dll, 23: prc.nls, 24: prcp.nls, 25: prfc0804.dat, 26: prfd0804.dat, 27: prfh0804.dat, 28: prfi0804.dat, 29: prflbmsg.dll, 30: print.exe, 31: printui.dll, 32: prncnfg.vbs, 33: prndrvr.vbs, 34: prnjobs.vbs, 35: prnmngr.vbs, 36: prnport.vbs, 37: prnqctl.vbs, 38: proctexe.ocx, 39: prodspec.ini, 40: profmap.dll, 41: progman.exe, 42: proquota.exe, 43: proxycfg.exe, 44: psapi.dll, 45: psbase.dll, 46: pschdcnt.h, 47: pschdprf.dll, 48: pschdprf.ini, 49: pscript.sep, 50: psnppagn.dll, 51: pstorec.dll, 52: pstorsvc.dll, 53: pubprn.vbs, 54: qagent.dll, 55: qagentrt.dll, 56: qappsrv.exe, 57: qasf.dll, 58: qcap.dll, 59: qcliprov.dll, 60: qdv.dll, 61: qdvd.dll, 62: qedit.dll, 63: qedwipes.dll, 64: qmgr.dll, 65: qmgrprxy.dll, 66: qosname.dll, 67: qprocess.exe, 68: quartz.dll, 69: query.dll, 70: quick.ime, 71: qutil.dll, 72: qwinsta.exe, 73: racpldlg.dll, 74: ras, 75: rasadhlp.dll, 76: rasapi32.dll, 77: rasauto.dll, 78: rasautou.exe, 79: raschap.dll, 80: rasctrnm.h, 81: rasctrs.dll, 82: rasctrs.ini, 83: rasdial.exe, 84: rasdlg.dll, 85: rasman.dll, 86: rasmans.dll, 87: rasmontr.dll, 88: rasmxs.dll, 89: rasphone.exe, 90: rasppp.dll, 91: rasqec.dll, 92: rasrad.dll, 93: rassapi.dll, 94: rasser.dll, 95: rastapi.dll, 96: rastls.dll, 97: rcbdyctl.dll, 98: rcimlby.exe, 99: rcp.exe, 100: rdchost.dll, 101: rdpcfgex.dll, 102: rdpclip.exe, 103: rdpdd.dll, 104: rdpsnd.dll, 105: rdpwsx.dll, 106: rdsaddin.exe, 107: rdshost.exe, 108: recover.exe, 109: redir.exe, 110: reg.exe, 111: regapi.dll, 112: regedt32.exe, 113: regini.exe, 114: regsvc.dll, 115: regsvr32.exe, 116: regwiz.exe, 117: regwizc.dll, 118: ReinstallBackups, 119: relog.exe, 120: remotepg.dll, 121: remotesp.tsp, 122: rend.dll, 123: replace.exe, 124: reset.exe, 125: Restore, 126: resutils.dll, 127: rexec.exe, 128: rhttpaa.dll, 129: riched20.dll, 130: riched32.dll, 131: rnr20.dll, 132: romanime.ime, 133: route.exe, 134: routemon.exe, 135: routetab.dll, 136: rpcns4.dll, 137: rpcrt4.dll, 138: rpcss.dll, 139: rsaci.rat, 140: rsaenh.dll, 141: rsfsaps.dll, 142: rsh.exe, 143: rshx32.dll, 144: rsm.exe, 145: rsmps.dll, 146: rsmsink.exe, 147: rsmui.exe, 148: rsnotify.exe, 149: rsop.msc, 150: rsopprov.exe, 151: rsvp.exe, 152: rsvp.ini, 153: rsvpcnts.h, 154: rsvpmsg.dll, 155: rsvpperf.dll, 156: rsvpsp.dll, 157: rtcshare.exe, 158: rtipxmib.dll, 159: rtm.dll, 160: rtutils.dll, 161: runas.exe, 162: rundll32.exe, 163: runonce.exe, 164: rwinsta.exe, 165: safrcdlg.dll, 166: safrdm.dll, 167: safrslv.dll, 168: samlib.dll, 169: samsrv.dll, 170: sapi.cpl.manifest, 171: savedump.exe, 172: sbe.dll, 173: sbeio.dll, 174: sc.exe, 175: scarddlg.dll, 176: scardssp.dll, 177: scardsvr.exe, 178: sccbase.dll, 179: sccsccp.dll, 180: scecli.dll, 181: scesrv.dll, 182: schannel.dll, 183: schedsvc.dll, 184: schtasks.exe, 185: sclgntfy.dll, 186: scochs.dll, 187: scredir.dll, 188: scriptpw.dll, 189: scrnsave.scr, 190: scrobj.dll, 191: scrrnchs.dll, 192: scrrun.dll, 193: sdbinst.exe, 194: sdhcinst.dll, 195: sdpblb.dll, 196: secedit.exe, 197: seclogon.dll, 198: secpol.msc, 199: secupd.dat, 200: secupd.sig, 201: secur32.dll, 202: security.dll, 203: sendcmsg.dll, 204: sendmail.dll, 205: sens.dll, 206: sensapi.dll, 207: senscfg.dll, 208: serialui.dll, 209: servdeps.dll, 210: services.exe, 211: services.msc, 212: serwvdrv.dll, 213: sessmgr.exe, 214: sethc.exe, 215: Setup, 216: setup.bmp, 217: setup.exe, 218: setupapi.dll, 219: setupdll.dll, 220: setupn.exe, 221: setver.exe, 222: sfc.dll, 223: sfc.exe, 224: sfcfiles.dll, 225: sfc_os.dll, 226: sfmapi.dll, 227: shadow.exe, 228: share.exe, 229: shdoclc.dll, 230: shdocvw.dll, 231: shell.dll, 232: shell32.dll, 233: ShellExt, 234: shellstyle.dll, 235: shfolder.dll, 236: shgina.dll, 237: shiftjis.uce, 238: shimeng.dll, 239: sh"
"21:31:32.7538273","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: usrrtosa.dll, 1: usrsdpia.dll, 2: usrshuta.exe, 3: usrsvpia.dll, 4: usrv42a.dll, 5: usrv80a.dll, 6: usrvoica.dll, 7: usrvpa.dll, 8: utildll.dll, 9: utilman.exe, 10: uxtheme.dll, 11: v7vga.rom, 12: vbajet32.dll, 13: vbicodec.ax, 14: vbisurf.ax, 15: vbschs.dll, 16: vbscript.dll, 17: vcdex.dll, 18: vdmdbg.dll, 19: vdmredir.dll, 20: ver.dll, 21: verclsid.exe, 22: verifier.dll, 23: verifier.exe, 24: version.dll, 25: vfpodbc.dll, 26: vga.dll, 27: vga.drv, 28: vga256.dll, 29: vga64k.dll, 30: vjoy.dll, 31: vmGuestLib.dll, 32: vmGuestLibJava.dll, 33: vmhgfs.dll, 34: VMUpgradeAtShutdownWXP.dll, 35: vmwogl32.dll, 36: VMWSU_V1_0.DLL, 37: vmx_fb.dll, 38: vmx_mode.dll, 39: vsocklib.dll, 40: vssadmin.exe, 41: vssapi.dll, 42: vssvc.exe, 43: vss_ps.dll, 44: vwipxspx.dll, 45: vwipxspx.exe, 46: w32time.dll, 47: w32tm.exe, 48: w32topl.dll, 49: w3ssl.dll, 50: watchdog.sys, 51: wavemsp.dll, 52: wbcache.deu, 53: wbcache.enu, 54: wbcache.esn, 55: wbcache.fra, 56: wbcache.ita, 57: wbcache.nld, 58: wbcache.sve, 59: wbdbase.deu, 60: wbdbase.enu, 61: wbdbase.esn, 62: wbdbase.fra, 63: wbdbase.ita, 64: wbdbase.nld, 65: wbdbase.sve, 66: wbem, 67: wdigest.dll, 68: wdl.trm, 69: wdmaud.drv, 70: webcheck.dll, 71: webclnt.dll, 72: webfldrs.msi, 73: webhits.dll, 74: webvw.dll, 75: wextract.exe, 76: wfwnet.drv, 77: wiaacmgr.exe, 78: wiadefui.dll, 79: wiadss.dll, 80: wiascr.dll, 81: wiaservc.dll, 82: wiasf.ax, 83: wiashext.dll, 84: wiavideo.dll, 85: wiavusd.dll, 86: wifeman.dll, 87: win.com, 88: win32k.sys, 89: win32spl.dll, 90: win87em.dll, 91: WINABC.CNT, 92: WINABC.CWD, 93: WINABC.HLP, 94: WINABC.IME, 95: WINABC.OVL, 96: winar30.ime, 97: winbrand.dll, 98: winchat.exe, 99: windowscodecs.dll, 100: windowscodecsext.dll, 101: WindowsLogon.manifest, 102: winfax.dll, 103: WINGB.IME, 104: winhelp.hlp, 105: winhlp32.exe, 106: winhttp.dll, 107: winime.ime, 108: wininet.dll, 109: winipsec.dll, 110: winlogon.exe, 111: winmine.exe, 112: winmm.dll, 113: winmsd.exe, 114: winnls.dll, 115: winntbbu.dll, 116: winoldap.mod, 117: WINPY.IME, 118: WINPY.MB, 119: winrnr.dll, 120: wins, 121: winscard.dll, 122: winshfhc.dll, 123: winsock.dll, 124: WINSP.IME, 125: WINSP.MB, 126: winspool.drv, 127: winspool.exe, 128: winsrv.dll, 129: winsta.dll, 130: winstrm.dll, 131: wintrust.dll, 132: winver.exe, 133: WINZM.IME, 134: WINZM.MB, 135: wkssvc.dll, 136: wlanapi.dll, 137: wldap32.dll, 138: wlnotify.dll, 139: wmadmod.dll, 140: wmadmoe.dll, 141: wmasf.dll, 142: wmdmlog.dll, 143: wmdmps.dll, 144: wmerrCHS.dll, 145: wmerror.dll, 146: wmi.dll, 147: wmidx.dll, 148: wmimgmt.msc, 149: wmiprop.dll, 150: wmiscmgr.dll, 151: wmnetmgr.dll, 152: wmp.dll, 153: wmp.ocx, 154: wmpasf.dll, 155: wmpcd.dll, 156: wmpcore.dll, 157: wmpdxm.dll, 158: wmphoto.dll, 159: wmploc.dll, 160: wmpshell.dll, 161: wmpui.dll, 162: wmsdmod.dll, 163: wmsdmoe.dll, 164: wmsdmoe2.dll, 165: wmspdmod.dll, 166: wmspdmoe.dll, 167: wmstream.dll, 168: wmv8ds32.ax, 169: wmvcore.dll, 170: wmvdmod.dll, 171: wmvdmoe2.dll, 172: wmvds32.ax, 173: wow32.dll, 174: wowdeb.exe, 175: wowexec.exe, 176: wowfax.dll, 177: wowfaxui.dll, 178: wpa.dbl, 179: wpabaln.exe, 180: wpnpinst.exe, 181: write.exe, 182: ws2help.dll, 183: ws2_32.dll, 184: wscntfy.exe, 185: wscript.exe, 186: wscsvc.dll, 187: wscui.cpl, 188: wsecedit.dll, 189: wshatm.dll, 190: wshbth.dll, 191: wshchs.dll, 192: wshcon.dll, 193: wshext.dll, 194: wship6.dll, 195: wshirda.dll, 196: wshisn.dll, 197: wshnetbs.dll, 198: wshom.ocx, 199: WshRm.dll, 200: wshtcpip.dll, 201: wsnmp32.dll, 202: wsock32.dll, 203: wstdecod.dll, 204: wstpager.ax, 205: wstrenderer.ax, 206: wtsapi32.dll, 207: wuapi.dll, 208: wuauclt.exe, 209: wuauclt1.exe, 210: wuaucpl.cpl, 211: wuaucpl.cpl.manifest, 212: wuaueng.dll, 213: wuaueng1.dll, 214: wuauserv.dll, 215: wucltui.dll, 216: wupdmgr.exe, 217: wups.dll, 218: wuweb.dll, 219: wzcdlg.dll, 220: wzcsapi.dll, 221: wzcsvc.dll, 222: xactsrv.dll, 223: xcopy.exe, 224: xenroll.dll, 225: xircom, 226: xjis.nls, 227: xmllite.dll, 228: xmlprov.dll, 229: xmlprovi.dll, 230: xolehlp.dll, 231: xpob2res.dll, 232: xpsp1res.dll, 233: xpsp2res.dll, 234: xpsp3res.dll, 235: zh-CHS, 236"
"21:31:32.7540021","Lab10-01.exe","2472","QueryDirectory","C:\WINDOWS\system32","NO MORE FILES",""
"21:31:32.7542029","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32","SUCCESS",""
"21:31:32.7544000","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7545279","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\ntdll.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7545379","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS","AllocationSize: 589,824, EndOfFile: 589,312, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7545575","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\ntdll.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7547306","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7548573","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\kernel32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7548672","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS","AllocationSize: 1,150,976, EndOfFile: 1,150,464, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7548877","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\kernel32.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7550784","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\unicode.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7552206","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\unicode.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7552321","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\unicode.nls","SUCCESS","AllocationSize: 90,112, EndOfFile: 89,588, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7552515","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\unicode.nls","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7555619","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\locale.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7556898","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\locale.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7556998","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\locale.nls","SUCCESS","AllocationSize: 266,240, EndOfFile: 265,948, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7557187","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\locale.nls","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7559399","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\sorttbls.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7560645","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\sorttbls.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7560739","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\sorttbls.nls","SUCCESS","AllocationSize: 24,576, EndOfFile: 23,044, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7560930","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\sorttbls.nls","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7562543","Lab10-01.exe","2472","CreateFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7563711","Lab10-01.exe","2472","CreateFileMapping","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7563806","Lab10-01.exe","2472","QueryStandardInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","AllocationSize: 28,672, EndOfFile: 28,672, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7564006","Lab10-01.exe","2472","CreateFileMapping","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7565629","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7566826","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\advapi32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7566920","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS","AllocationSize: 675,840, EndOfFile: 674,816, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7567113","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\advapi32.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7568836","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7570040","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7570135","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","AllocationSize: 585,728, EndOfFile: 584,704, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7570323","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7571882","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\secur32.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7573076","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\secur32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7573170","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\secur32.dll","SUCCESS","AllocationSize: 57,344, EndOfFile: 56,320, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7573359","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\secur32.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7574962","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\ctype.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7576157","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\ctype.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7576251","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\ctype.nls","SUCCESS","AllocationSize: 12,288, EndOfFile: 8,386, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7576443","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\ctype.nls","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7578001","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\sortkey.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7579439","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\sortkey.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7579585","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\sortkey.nls","SUCCESS","AllocationSize: 266,240, EndOfFile: 262,148, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7579777","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\sortkey.nls","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7581476","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7582765","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7582861","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS","AllocationSize: 4,096, EndOfFile: 3,712, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7583052","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7584991","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\AppPatch\drvmain.sdb","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7586180","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\AppPatch\drvmain.sdb","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE"
"21:31:32.7586274","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\AppPatch\drvmain.sdb","SUCCESS","AllocationSize: 12,288, EndOfFile: 9,424, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7586535","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\AppPatch\drvmain.sdb","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7588229","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS",""
"21:31:32.7589581","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS",""
"21:31:32.7590830","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\unicode.nls","SUCCESS",""
"21:31:32.7592067","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\locale.nls","SUCCESS",""
"21:31:32.7593475","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\sorttbls.nls","SUCCESS",""
"21:31:32.7594705","Lab10-01.exe","2472","CloseFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS",""
"21:31:32.7595953","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS",""
"21:31:32.7597197","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS",""
"21:31:32.7598442","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\secur32.dll","SUCCESS",""
"21:31:32.7599688","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\ctype.nls","SUCCESS",""
"21:31:32.7601041","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\sortkey.nls","SUCCESS",""
"21:31:32.7602289","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS",""
"21:31:32.7603633","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\AppPatch\drvmain.sdb","SUCCESS",""
"21:31:32.7605288","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7606477","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\ntdll.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE"
"21:31:32.7606852","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\ntdll.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7608498","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7609840","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\kernel32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE"
"21:31:32.7610219","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\kernel32.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7611850","Lab10-01.exe","2472","CreateFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7613013","Lab10-01.exe","2472","CreateFileMapping","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE"
"21:31:32.7613463","Lab10-01.exe","2472","CreateFileMapping","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7615154","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7616458","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\advapi32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE"
"21:31:32.7616838","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\advapi32.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7618557","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7619878","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE"
"21:31:32.7620259","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7621830","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\secur32.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7623041","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\secur32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE"
"21:31:32.7623407","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\secur32.dll","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7624985","Lab10-01.exe","2472","CreateFile","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7626218","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE"
"21:31:32.7626317","Lab10-01.exe","2472","QueryStandardInformationFile","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS","AllocationSize: 4,096, EndOfFile: 3,712, NumberOfLinks: 1, DeletePending: False, Directory: False"
"21:31:32.7626437","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7629434","Lab10-01.exe","2472","CreateFileMapping","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS","SyncType: SyncTypeOther"
"21:31:32.7630826","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS",""
"21:31:32.7632081","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS",""
"21:31:32.7633340","Lab10-01.exe","2472","CloseFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS",""
"21:31:32.7634587","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS",""
"21:31:32.7636003","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS",""
"21:31:32.7637489","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\secur32.dll","SUCCESS",""
"21:31:32.7639222","Lab10-01.exe","2472","CloseFile","C:\WINDOWS\system32\Lab10-01.sys","SUCCESS",""
"21:31:32.7639377","Lab10-01.exe","2472","CloseFile","C:","SUCCESS",""
"21:31:32.7640805","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Lab10-01.exe","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7642941","Lab10-01.exe","2472","CreateFile","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS","Desired Access: Execute/Traverse, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Attributes: n/a, ShareMode: Read, Write, AllocationSize: n/a, OpenResult: Opened"
"21:31:32.7643837","Lab10-01.exe","2472","FileSystemControl","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS","Control: FSCTL_IS_VOLUME_MOUNTED"
"21:31:32.7645091","Lab10-01.exe","2472","QueryOpen","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe.Local","NAME NOT FOUND",""
"21:31:32.7647745","Lab10-01.exe","2472","Load Image","C:\WINDOWS\system32\kernel32.dll","SUCCESS","Image Base: 0x7c800000, Image Size: 0x11e000"
"21:31:32.7652751","Lab10-01.exe","2472","RegOpenKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS","Desired Access: Read"
"21:31:32.7653141","Lab10-01.exe","2472","RegQueryValue","HKLM\System\CurrentControlSet\Control\Terminal Server\TSAppCompat","SUCCESS","Type: REG_DWORD, Length: 4, Data: 0"
"21:31:32.7653349","Lab10-01.exe","2472","RegCloseKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS",""
"21:31:32.7659686","Lab10-01.exe","2472","Load Image","C:\WINDOWS\system32\advapi32.dll","SUCCESS","Image Base: 0x77da0000, Image Size: 0xa9000"
"21:31:32.7662367","Lab10-01.exe","2472","Load Image","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","Image Base: 0x77e50000, Image Size: 0x92000"
"21:31:32.7664688","Lab10-01.exe","2472","Load Image","C:\WINDOWS\system32\secur32.dll","SUCCESS","Image Base: 0x77fc0000, Image Size: 0x11000"
"21:31:32.7665836","Lab10-01.exe","2472","RegOpenKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS","Desired Access: Read"
"21:31:32.7666157","Lab10-01.exe","2472","RegQueryValue","HKLM\System\CurrentControlSet\Control\Terminal Server\TSAppCompat","SUCCESS","Type: REG_DWORD, Length: 4, Data: 0"
"21:31:32.7666302","Lab10-01.exe","2472","RegCloseKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS",""
"21:31:32.7666689","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Secur32.dll","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7666934","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RPCRT4.dll","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7667077","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ADVAPI32.dll","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7667246","Lab10-01.exe","2472","RegOpenKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS","Desired Access: Read"
"21:31:32.7667439","Lab10-01.exe","2472","RegQueryValue","HKLM\System\CurrentControlSet\Control\Terminal Server\TSAppCompat","SUCCESS","Type: REG_DWORD, Length: 4, Data: 0"
"21:31:32.7667505","Lab10-01.exe","2472","RegQueryValue","HKLM\System\CurrentControlSet\Control\Terminal Server\TSUserEnabled","SUCCESS","Type: REG_DWORD, Length: 4, Data: 0"
"21:31:32.7667613","Lab10-01.exe","2472","RegCloseKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS",""
"21:31:32.7667705","Lab10-01.exe","2472","RegOpenKey","HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon","SUCCESS","Desired Access: Read"
"21:31:32.7667872","Lab10-01.exe","2472","RegQueryValue","HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\LeakTrack","NAME NOT FOUND","Length: 144"
"21:31:32.7668003","Lab10-01.exe","2472","RegCloseKey","HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon","SUCCESS",""
"21:31:32.7668072","Lab10-01.exe","2472","RegOpenKey","HKLM","SUCCESS","Desired Access: Maximum Allowed"
"21:31:32.7668216","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Diagnostics","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7668393","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ntdll.dll","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7668471","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kernel32.dll","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7670465","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Rpc\PagedBuffers","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7670569","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Rpc","SUCCESS","Desired Access: Read"
"21:31:32.7670805","Lab10-01.exe","2472","RegQueryValue","HKLM\SOFTWARE\Microsoft\Rpc\MaxRpcSize","NAME NOT FOUND","Length: 144"
"21:31:32.7670918","Lab10-01.exe","2472","RegCloseKey","HKLM\SOFTWARE\Microsoft\Rpc","SUCCESS",""
"21:31:32.7671009","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Lab10-01.exe\RpcThreadPoolThrottle","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7671313","Lab10-01.exe","2472","RegOpenKey","HKLM\Software\Policies\Microsoft\Windows NT\Rpc","NAME NOT FOUND","Desired Access: Read"
"21:31:32.7671470","Lab10-01.exe","2472","RegOpenKey","HKLM\System\CurrentControlSet\Control\Session Manager","SUCCESS","Desired Access: Query Value"
"21:31:32.7671786","Lab10-01.exe","2472","RegQueryValue","HKLM\System\CurrentControlSet\Control\Session Manager\SafeDllSearchMode","NAME NOT FOUND","Length: 16"
"21:31:32.7671901","Lab10-01.exe","2472","RegCloseKey","HKLM\System\CurrentControlSet\Control\Session Manager","SUCCESS",""
"21:31:32.7673393","Lab10-01.exe","2472","QueryNameInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","BUFFER OVERFLOW","Name: \D"
"21:31:32.7673574","Lab10-01.exe","2472","QueryNameInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-01.exe","SUCCESS","Name: \Documents and Settings\Administrator\桌面\lab\Lab10-01.exe"
"21:31:32.7673995","Lab10-01.exe","2472","RegSetValue","HKLM\SOFTWARE\Microsoft\Cryptography\RNG\Seed","SUCCESS","Type: REG_BINARY, Length: 80, Data: E8 1E 52 4B EC 59 29 40 5F 3C D5 51 1B 00 0D 5E"
"21:31:32.7676262","Lab10-01.exe","2472","SetEndOfFileInformationFile","C:\WINDOWS\system32\config\software.LOG","SUCCESS","EndOfFile: 8,192"
"21:31:32.7678656","Lab10-01.exe","2472","SetEndOfFileInformationFile","C:\WINDOWS\system32\config\software.LOG","SUCCESS","EndOfFile: 8,192"
"21:31:32.7680713","Lab10-01.exe","2472","SetEndOfFileInformationFile","C:\WINDOWS\system32\config\software.LOG","SUCCESS","EndOfFile: 16,384"
"21:31:32.7689014","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7689368","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\PlugPlayServiceType","NAME NOT FOUND","Length: 144"
"21:31:32.7689552","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS","Desired Access: Read"
"21:31:32.7689725","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum\Count","SUCCESS","Type: REG_DWORD, Length: 4, Data: 1"
"21:31:32.7689813","services.exe","736","RegQueryKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS","Query: Cached, SubKeys: 0, Values: 3"
"21:31:32.7689940","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS",""
"21:31:32.7690099","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7690189","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7690434","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\PlugPlayServiceType","NAME NOT FOUND","Length: 144"
"21:31:32.7690496","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS","Desired Access: Read"
"21:31:32.7690630","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum\Count","SUCCESS","Type: REG_DWORD, Length: 4, Data: 1"
"21:31:32.7690818","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum\0","SUCCESS","Type: REG_SZ, Length: 52, Data: Root\LEGACY_LAB10-01\0000"
"21:31:32.7690941","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS",""
"21:31:32.7691192","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7691292","services.exe","736","RegOpenKey","HKCC\System\CurrentControlSet\Enum","SUCCESS","Desired Access: Query Value"
"21:31:32.7691882","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Hardware Profiles\0001\System\CurrentControlSet\Enum\Root\LEGACY_LAB10-01\0000","NAME NOT FOUND","Desired Access: Query Value"
"21:31:32.7692065","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Hardware Profiles\0001\System\CurrentControlSet\Enum","SUCCESS",""
"21:31:32.7692142","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services","SUCCESS","Desired Access: Read"
"21:31:32.7692337","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7692509","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services","SUCCESS",""
"21:31:32.7692596","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\ObjectName","NAME NOT FOUND","Length: 12"
"21:31:32.7692700","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7694681","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7694920","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\PlugPlayServiceType","NAME NOT FOUND","Length: 144"
"21:31:32.7694985","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS","Desired Access: Read"
"21:31:32.7695132","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum\Count","SUCCESS","Type: REG_DWORD, Length: 4, Data: 1"
"21:31:32.7695202","services.exe","736","RegQueryKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS","Query: Cached, SubKeys: 0, Values: 3"
"21:31:32.7695299","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS",""
"21:31:32.7695558","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7695643","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7695795","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\PlugPlayServiceType","NAME NOT FOUND","Length: 144"
"21:31:32.7695856","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS","Desired Access: Read"
"21:31:32.7697634","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum\Count","SUCCESS","Type: REG_DWORD, Length: 4, Data: 1"
"21:31:32.7697722","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum\0","SUCCESS","Type: REG_SZ, Length: 52, Data: Root\LEGACY_LAB10-01\0000"
"21:31:32.7697994","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS",""
"21:31:32.7698133","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7698232","services.exe","736","RegOpenKey","HKCC\System\CurrentControlSet\Enum","SUCCESS","Desired Access: Query Value"
"21:31:32.7698679","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Hardware Profiles\0001\System\CurrentControlSet\Enum\Root\LEGACY_LAB10-01\0000","NAME NOT FOUND","Desired Access: Query Value"
"21:31:32.7698826","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Hardware Profiles\0001\System\CurrentControlSet\Enum","SUCCESS",""
"21:31:32.7699056","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services","SUCCESS","Desired Access: Read"
"21:31:32.7699285","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7699483","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services","SUCCESS",""
"21:31:32.7699580","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\ObjectName","NAME NOT FOUND","Length: 12"
"21:31:32.7699688","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7701067","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services","SUCCESS","Desired Access: Read"
"21:31:32.7701281","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7701464","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services","SUCCESS",""
"21:31:32.7701615","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\ObjectName","NAME NOT FOUND","Length: 12"
"21:31:32.7701719","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7702379","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services","SUCCESS","Desired Access: Read"
"21:31:32.7702610","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7702783","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services","SUCCESS",""
"21:31:32.7702868","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\ObjectName","NAME NOT FOUND","Length: 12"
"21:31:32.7702975","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7726573","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7726741","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\PlugPlayServiceType","NAME NOT FOUND","Length: 144"
"21:31:32.7726805","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS","Desired Access: Read"
"21:31:32.7726947","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum\Count","SUCCESS","Type: REG_DWORD, Length: 4, Data: 1"
"21:31:32.7727010","services.exe","736","RegQueryKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS","Query: Cached, SubKeys: 0, Values: 3"
"21:31:32.7727111","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS",""
"21:31:32.7727235","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7727320","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7727450","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\PlugPlayServiceType","NAME NOT FOUND","Length: 144"
"21:31:32.7727508","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS","Desired Access: Read"
"21:31:32.7727634","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum\Count","SUCCESS","Type: REG_DWORD, Length: 4, Data: 1"
"21:31:32.7727706","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum\0","SUCCESS","Type: REG_SZ, Length: 52, Data: Root\LEGACY_LAB10-01\0000"
"21:31:32.7727812","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01\Enum","SUCCESS",""
"21:31:32.7727933","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS",""
"21:31:32.7728021","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Enum\Root\LEGACY_LAB10-01\0000","SUCCESS","Desired Access: Read"
"21:31:32.7728252","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Enum\Root\LEGACY_LAB10-01\0000\ClassGUID","SUCCESS","Type: REG_SZ, Length: 78, Data: {8ECC055D-047F-11D1-A537-0000F8753ED1}"
"21:31:32.7728366","services.exe","736","RegCloseKey","HKLM\System\CurrentControlSet\Enum\Root\LEGACY_LAB10-01\0000","SUCCESS",""
"21:31:32.7729525","services.exe","736","RegOpenKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Desired Access: Read"
"21:31:32.7729748","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\ObjectName","NAME NOT FOUND","Length: 48"
"21:31:32.7729811","services.exe","736","RegQueryValue","HKLM\System\CurrentControlSet\Services\Lab10-01\Type","SUCCESS","Type: REG_DWORD, Length: 4, Data: 1"
"21:31:32.7729873","services.exe","736","RegQueryKey","HKLM\System\CurrentControlSet\Services\Lab10-01","BUFFER TOO SMALL","Query: Basic, Length: 0"
"21:31:32.7729924","services.exe","736","RegQueryKey","HKLM\System\CurrentControlSet\Services\Lab10-01","SUCCESS","Query: Basic, Name: Lab10-01"
"21:31:32.7737162","Lab10-01.exe","2472","Thread Exit","","SUCCESS","Thread ID: 2476, User Time: 0.0000000, Kernel Time: 0.0156250"
"21:31:32.7740933","Lab10-01.exe","2472","Process Exit","","SUCCESS","Exit Status: 0, User Time: 0.0156250 seconds, Kernel Time: 0.0000000 seconds, Private Bytes: 241,664, Peak Private Bytes: 245,760, Working Set: 962,560, Peak Working Set: 966,656"
"21:31:32.7742097","Lab10-01.exe","2472","CloseFile","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS",""
"21:31:32.8858636","services.exe","736","WriteFile","C:\WINDOWS\system32\config\SysEvent.Evt","SUCCESS","Offset: 73,988, Length: 196"
"21:31:32.8860102","services.exe","736","WriteFile","C:\WINDOWS\system32\config\SysEvent.Evt","SUCCESS","Offset: 74,184, Length: 40"
"21:32:27.1410284","csrss.exe","612","RegQueryValue","HKLM\SYSTEM\Setup\SystemSetupInProgress","SUCCESS","Type: REG_DWORD, Length: 4, Data: 0"
服务的交互,是由services.exe完成的!services.exe是微软Windows操作系统的一部分。用于管理启动和停止服务。该进程也会处理在计算机启动和关机时运行的服务。这个程序对你系统的正常运行是非常重要的。终止进程后会重启。
这尼玛EDR后面咋关联检测啊。、。。。。todo。。。
先反汇编看下,可以知道是在创建服务并启动!然后再看strings,基本判断是通过驱动方式来加载恶意代码。
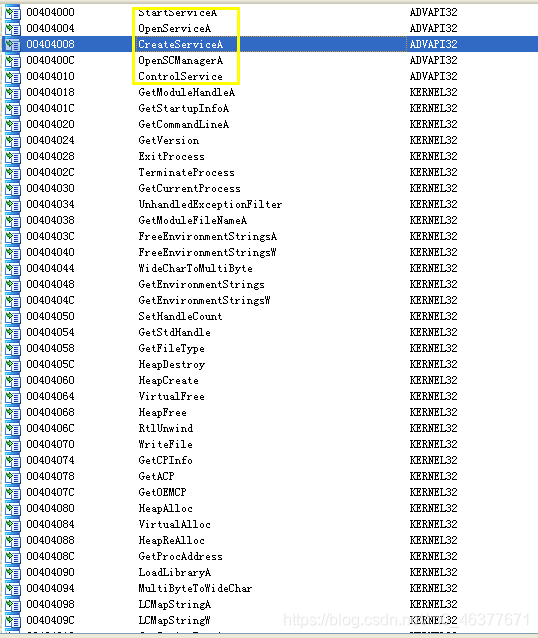
可以看到有与服务相关的敏感操作。通过ida的strings进行分析。
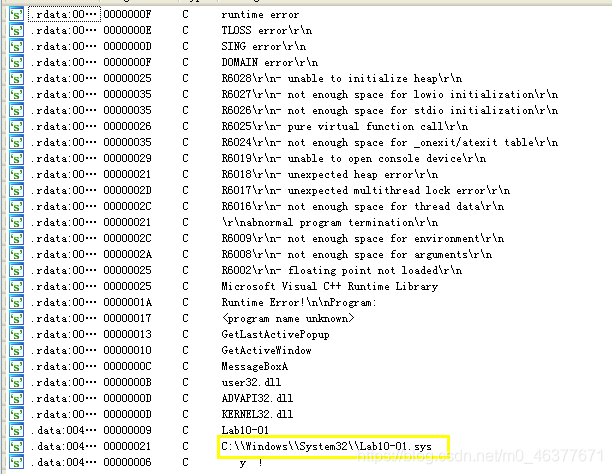
可以看到出现了敏感文件路径。
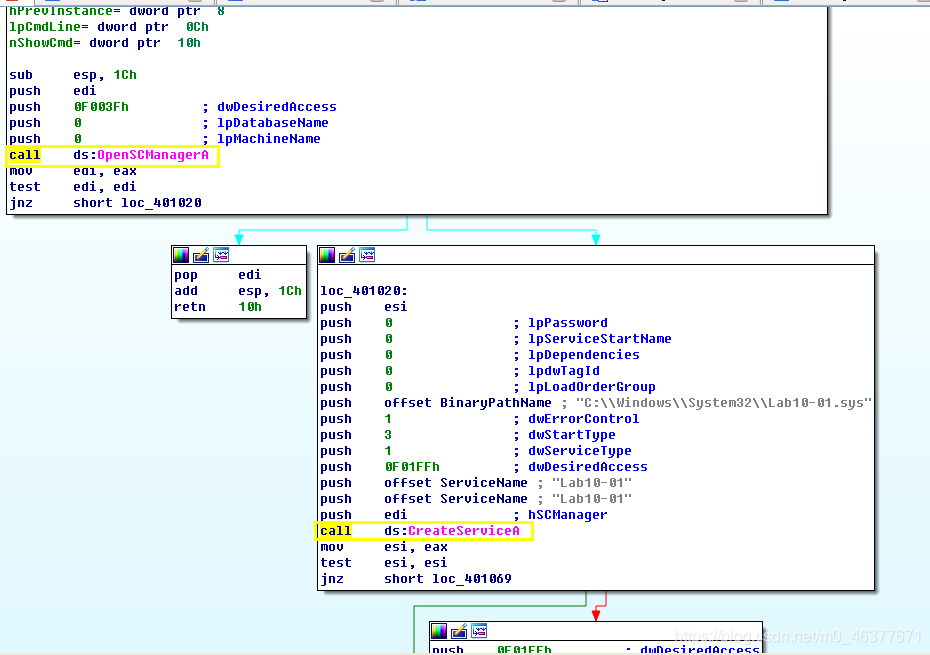
OpenSCManger:在指定及其上创建与服务控制管理程序的联系,并打开指定的数据库,返回的是一个服务管理器的句柄。
CreateService:创建一个服务对象,并将它添加到指定的服务控制管理程序的数据库中。Service为创建的服务名称,此处为lab10-01。
dwServiceType为服务类型,1表示此服务为驱动服务(此文件会加载到内核中去).dwStartType为服务启动类型,3表示此服务会自动启动 。
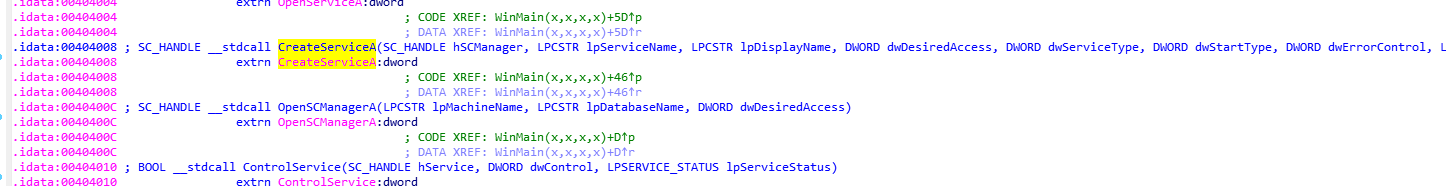
dwErrorControl表示严重性错误,以及采取的行动,如果这项服务无法启动,1表示启动程序在事件日志中记录,但继续启动操作。BinaryPathName表示服务二进制文件的完全限定路径,dwDesiredAccess为访问权限,0xF01FF表示除此表中的所有访问权限外,还包括STANDARD_RIGHTS_REQUIRED 。
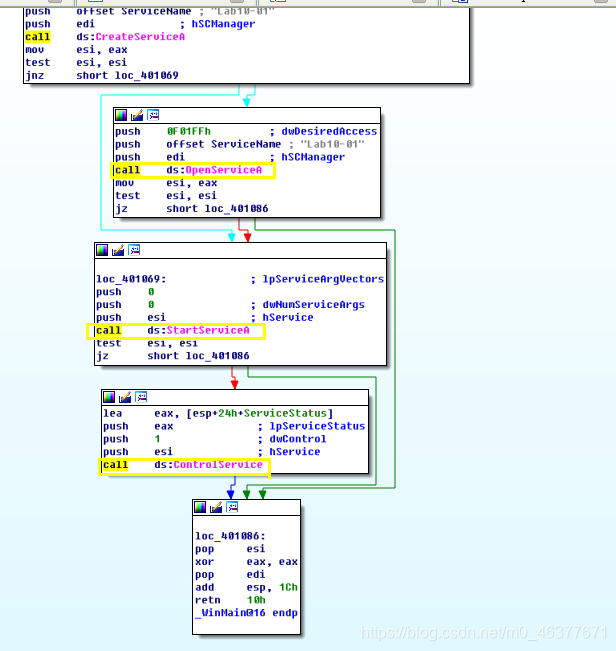
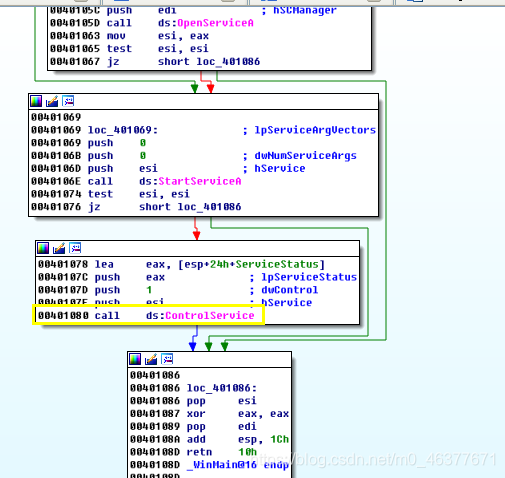
如果服务存在导致服务创建失败,则使用OpenService打开同名服务。如果打开成功,使用StartService开启服务。
ControlService: hservice,OpenService或CreateService 返回的服务句柄。
dwControl,要发送的控制码,此处为1,表示CONTROL _SERVICE_STOP,将会卸载驱动并调用驱动卸载的函数。==》此次实验就是要在运行过程中,打断点,看看这个程序究竟安装了什么驱动!因为它会自删除驱动。。。
IpServiceStatus,返回值,指向存储服务最新状态的结构体Service,返回信息来自SCM中最近的服务状态报告。
使用ida对Lab 10-01.sys进行分析,首先查看导入函数。
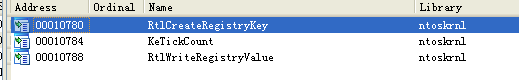
能够看到有与注册表相关的敏感操作。其中KeTickCount几乎所有驱动程序都会包括这个函数,可以忽略。
通过strings工具对其进行分析。
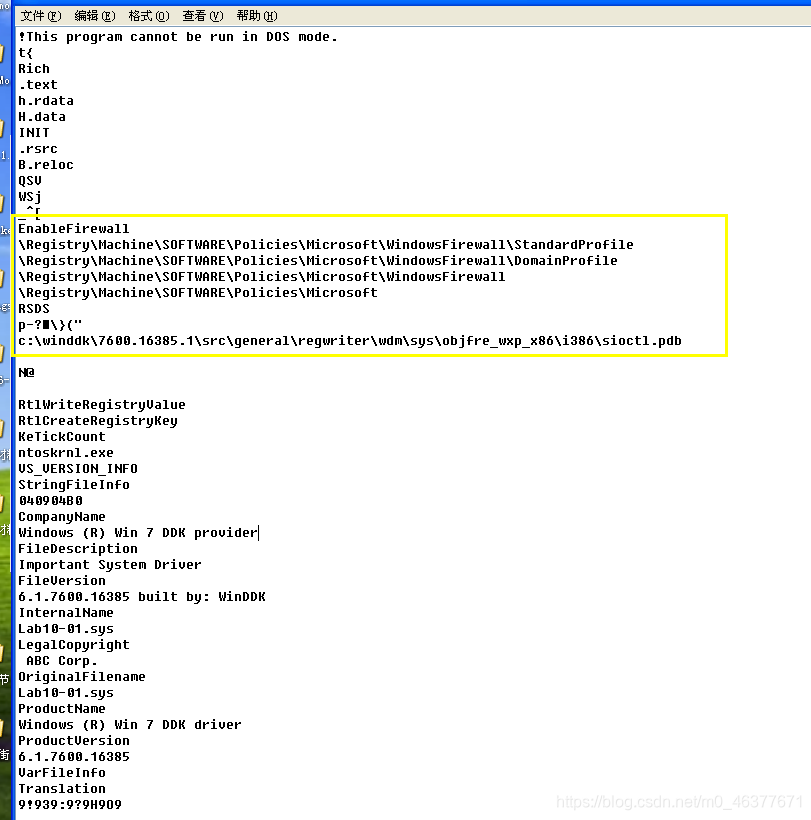
有与防火墙有关注册表相关。
反汇编看下:

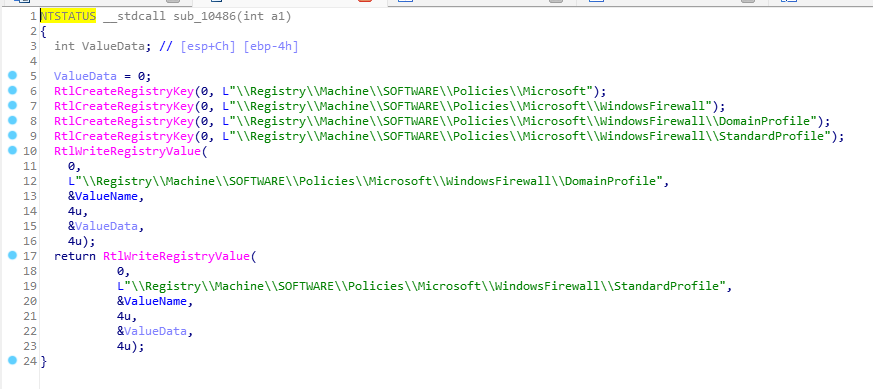
的确是在修改注册表。
使用process monitor进行分析。
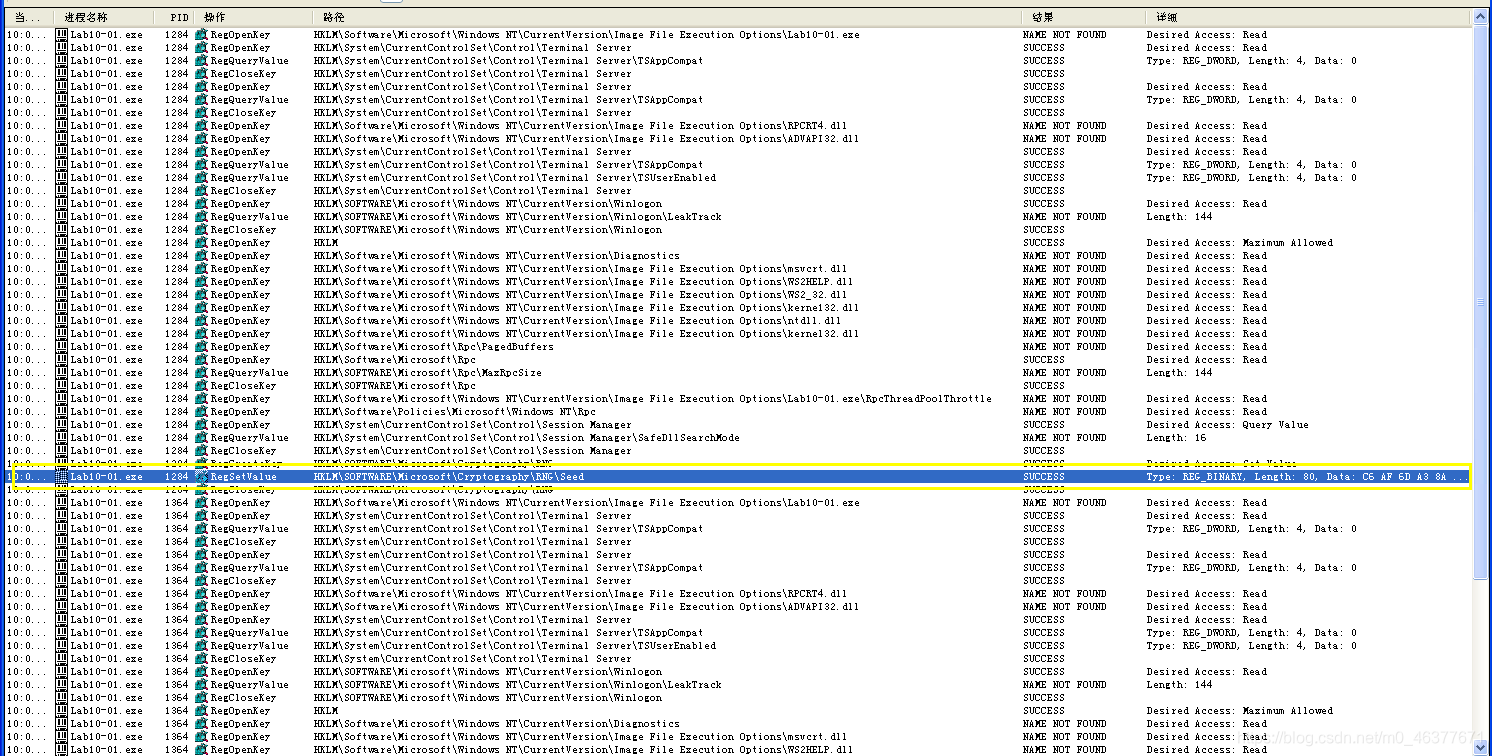
可以看到有关注册表的更改子键,设置了seed(随机的更改)。==》上述代码里为啥没有看到???
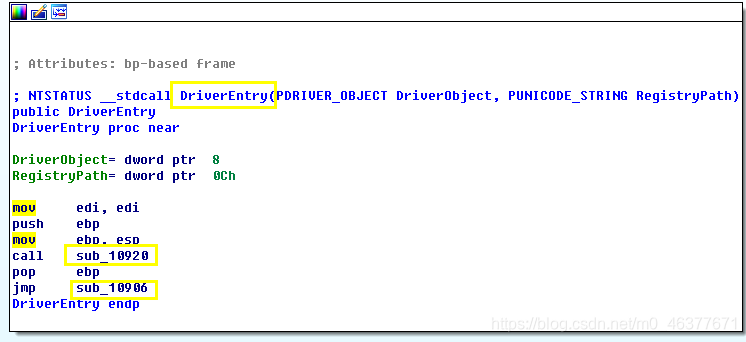
此处的DriverEntry为sub_10906,进入查看。
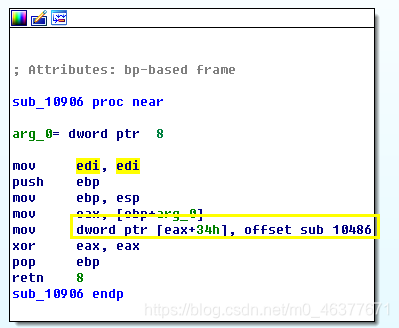
查看sub_10486
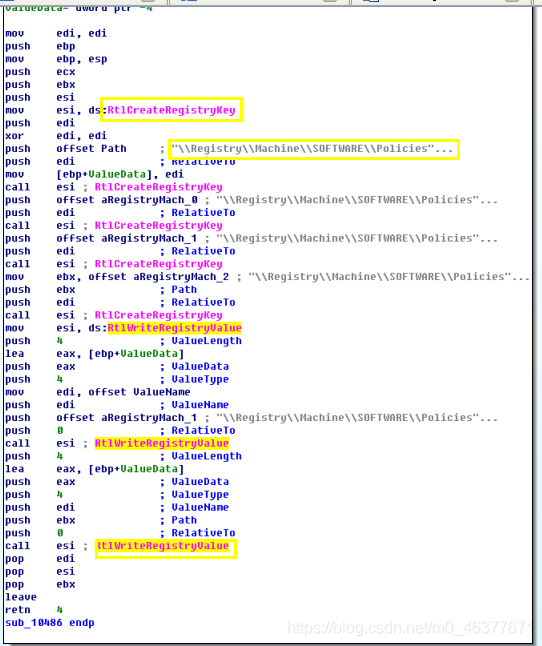
能够看到大量对注册表的操作。
RtlCreaterRegistrykey:通过一个给定的注册表相对路径和值创建指定的键。
RtlWriteRegistryValue:将提供的数据以指定的值名称写入指定的相对路径。参数实际的意义,还需要学习了解。
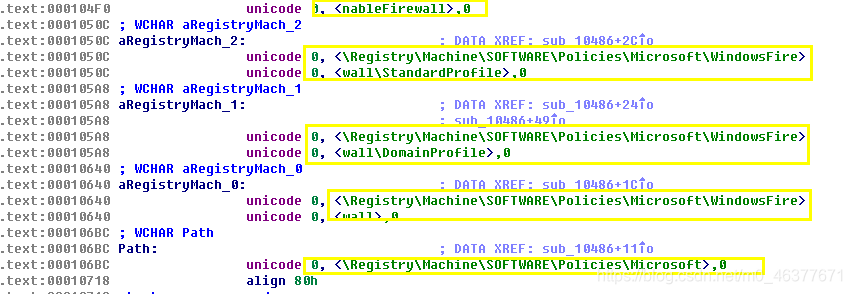
可以得知通修改注册表键值关闭了防火墙。
使用windbg调试内核。
我使用的是win7+win xp sp3,符号表使用了win xp3的下载器,因为之前使用的是win xp sp2加上微软的符号表链接,symbols文件只有十几兆,一直报错,于是使用下载器下载,共六百多兆,能够运行了。
在虚拟机中使用windbg加载lob 10-01.exe
在之前使用ida得到的controlservice地址进行断点,bp 00401080

使用win7宿主机的winbg进行调试,以查看此时内核中的驱动加载情况!
vmvare设置:
虚拟机配置
1,打开相应的虚拟机,选择“编辑虚拟机设置”,打开虚拟机设置对话框,如下

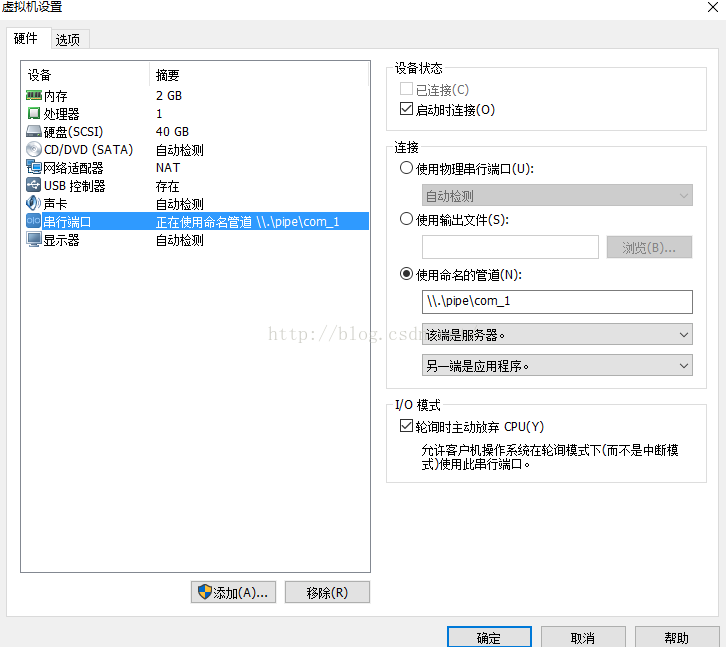
2,观察“虚拟机设置”这个对话框的“硬件”->“设备栏”,看看是否有“打印机”或“Printer”,如果有,则删除该设备。==》关键!!!否则链接不成功!
3,选择“添加”,然后选择“串行端口”,然后选择“使用命名管道”,并按如下设置
原文链接:https://blog.csdn.net/qq_25867649/article/details/54944675
winxp做一些准备工作,修改boot.ini文件:
我们在桌面上找到“我的电脑”然后右键单击,选择“属性”,进入系统属性页面之后,我们在第一行选择“高级”然后在下方选择“设置”

2、第二步,我们在"启动和故障恢复"页面中点击“编辑”就能对Boot.ini文件进行编辑了

[boot loader] timeout=30 default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS [operating systems] multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional" /noexecute=optin /fastdetect multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional with kernel debug" /noexecute=optin /fastdetect /debug /debugport=COM1 /baudrate=115200

修改好了以后重启!
然后windbg 点击kernel debug:
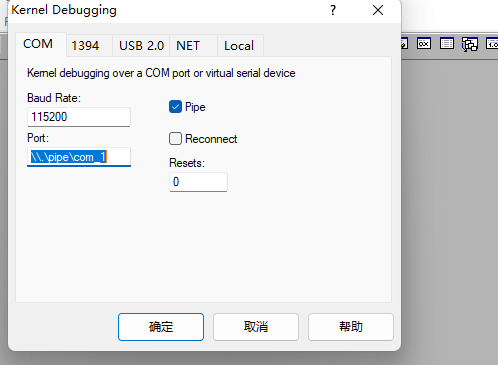
看到下面消息:
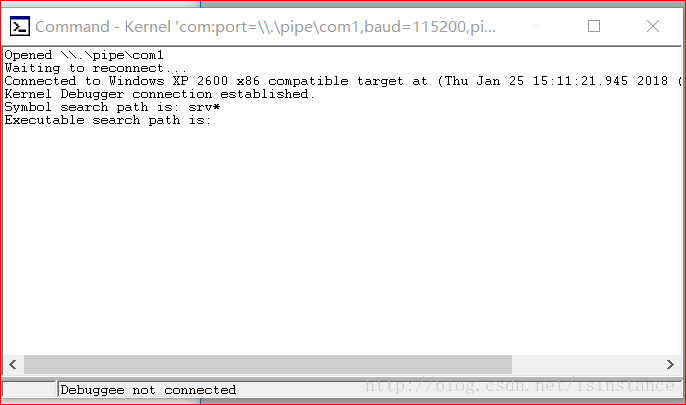
但是没有连接成功!
我的做法是这样的,其他做法也可以,只要你可以调试就行了,我找到Windbg的文件夹,然后把这个程序创建一个桌面快捷方式,目标修改下:
"C:\Program Files (x86)\Debugging Tools for Windows (x86)\windbg.exe" -b -k com:port=\\.\pipe\com_1,baud=115200,pipe -y C:\Windows\Symbols
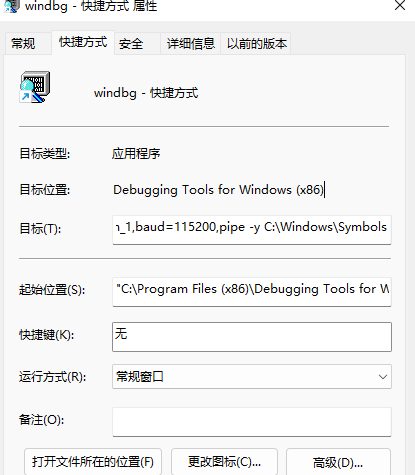
其中,C:\Windows\Symbols ,去资源文件:Windbg+Symbols 安装包(提取码:fvva)里下载安装,默认是安装在C:\Windows\Symbols!
成功后,然后我们双击windbg快捷方式,从下图看,就说明已经处于调试状态了!
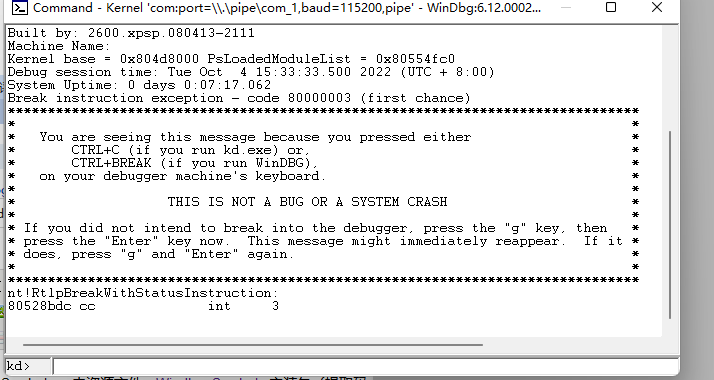
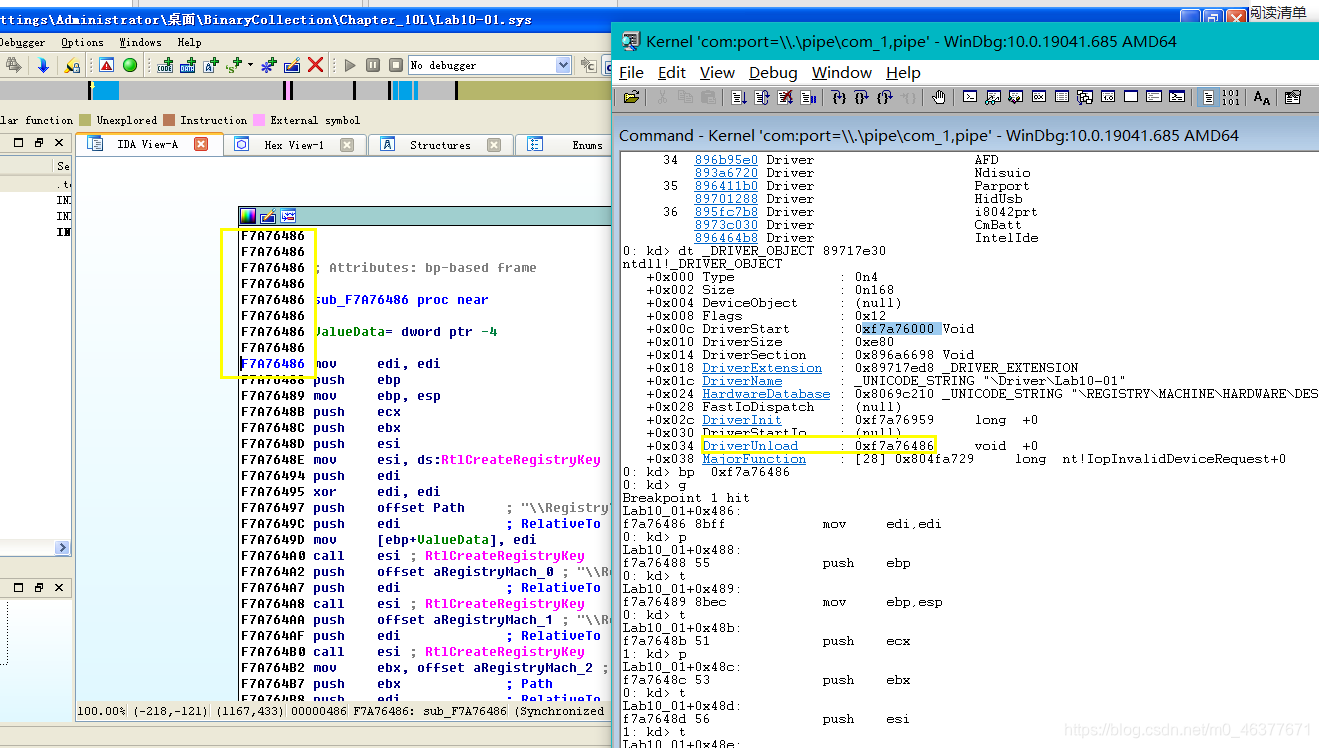
使用!drvobj查看Lab 10-01.exe创造的服务lab 10-01
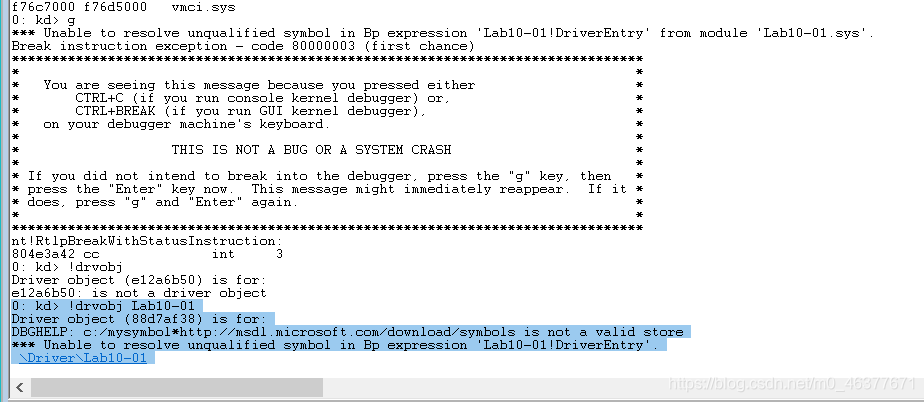
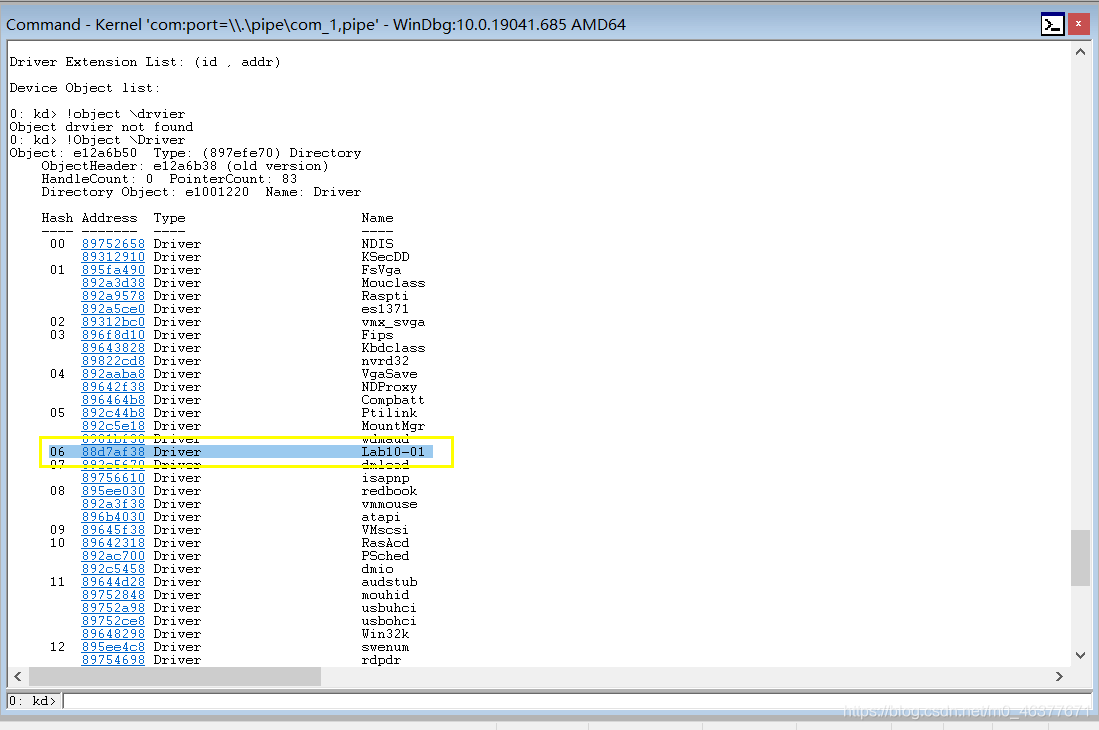
在这里设备列表为空,这个驱动没有供应用程序访问的设备,也可以使用命令!Object \Driver获得所有的驱动列表
使用dt _DRIVER_OBJECT 地址 来解析地址的数据结构 --》下面为啥是39而不是38???
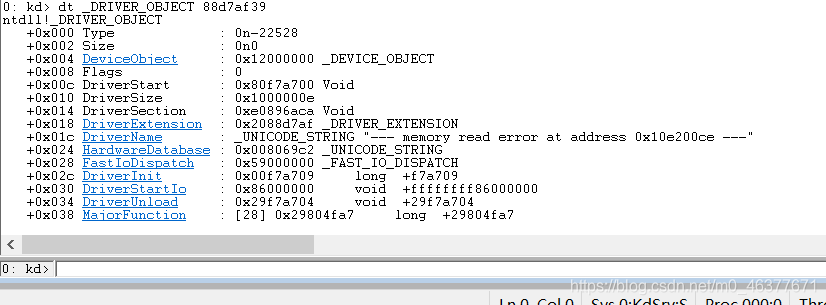
重点观察DriverUnload函数,地址为0x29f7a704,使用bp指令在此加断点,并使用g指令恢复内核的执行。

在虚拟机中继续运行
在win7并运行到断点处
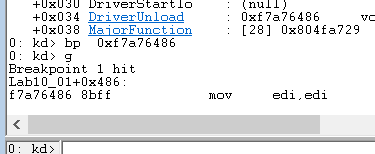
通过按t单步执行下一条指令
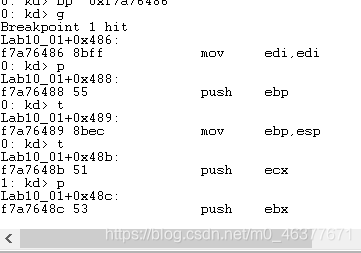
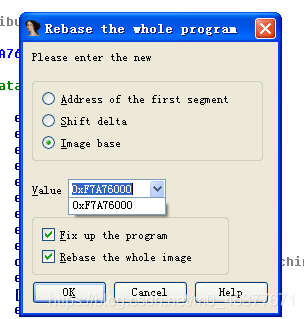
可以使用ida进行分析。从前面得知DriverStart的地址和DriverUpload的地址,从而得到偏移量0x486。
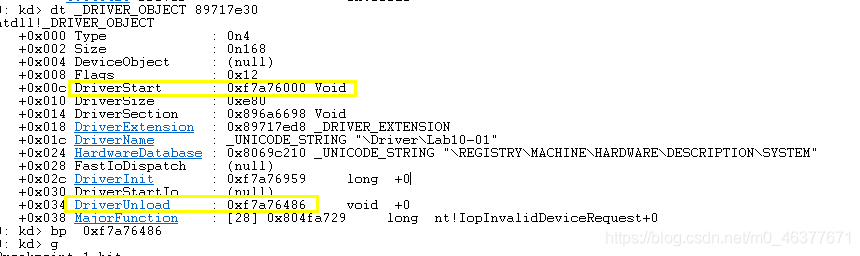
在ida中driver的默认地址的sys文件是从0x00010000开始的,所以函数卸载代码对应的地址为0x00010468。另外一个方法则是重新设置ida默认的基地址

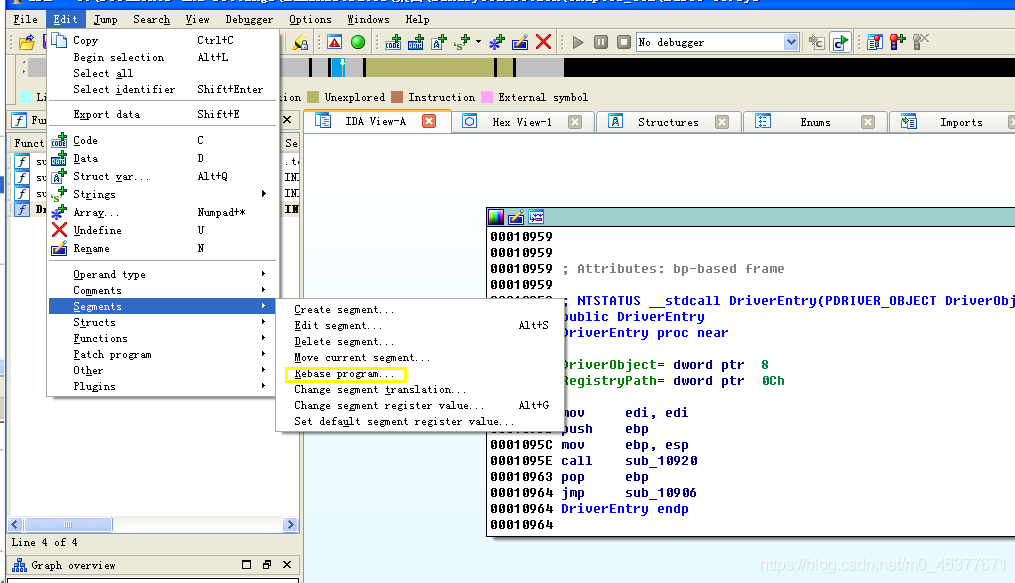
将基地址修改为driverstart的地址。
恶意代码分析实战 Lab 10-2 习题笔记
Lab 10-2
问题
1.这个程序创建文件了吗?它创建了什么文件?
解答: 我们依旧先从静态分析开始,这里我们在第一个导入DLL里面注意到的有趣的函数是这个WriteFile,说明这个代码会改变这个文件
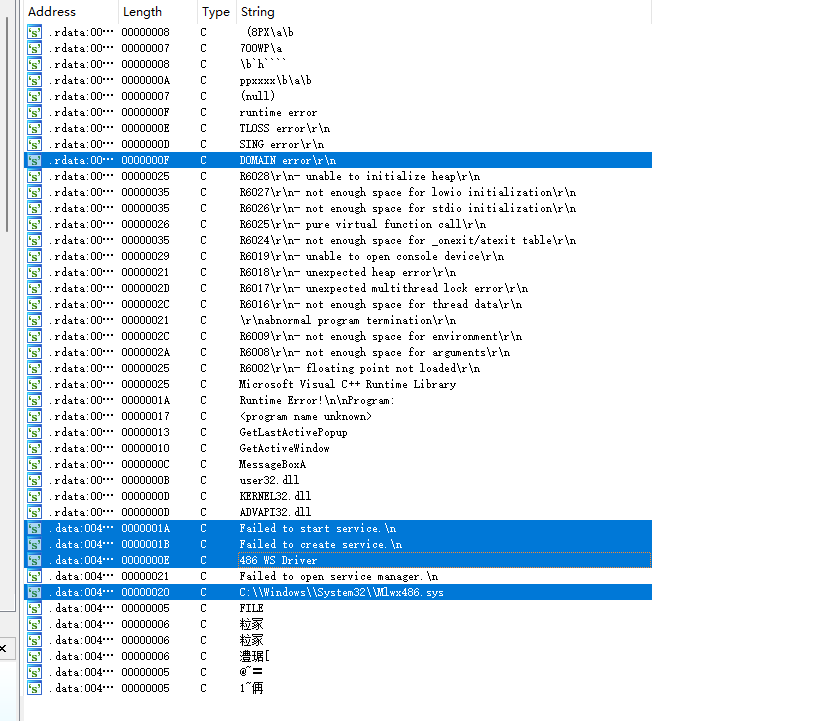
然后反汇编看下:

其中pathname就是sys这个。
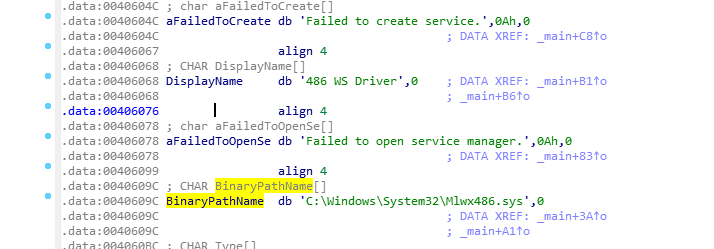
基本上可以确定是在利用资源文件创建服务,服务是一个sys驱动。
实际运行看看,procmon采集下数据:
"时间","进程名","PID","操作","路径","结果","详细信息" "21:42:46.0860193","Lab10-02.exe","3560","Process Start","","SUCCESS","Parent PID: 1796, Command line: ""C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe"" , Current directory: C:\Documents and Settings\Administrator\桌面\lab, Environment: ; =::=::\; ALLUSERSPROFILE=C:\Documents and Settings\All Users; APPDATA=C:\Documents and Settings\Administrator\Application Data; CLIENTNAME=Console; CommonProgramFiles=C:\Program Files\Common Files; COMPUTERNAME=BONELEE-B1632A4; ComSpec=C:\WINDOWS\system32\cmd.exe; FP_NO_HOST_CHECK=NO; HOMEDRIVE=C:; HOMEPATH=\Documents and Settings\Administrator; LOGONSERVER=\\BONELEE-B1632A4; NUMBER_OF_PROCESSORS=4; OS=Windows_NT; Path=C:\WINDOWS\system32;C:\WINDOWS;C:\WINDOWS\System32\Wbem; PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH; PROCESSOR_ARCHITECTURE=x86; PROCESSOR_IDENTIFIER=x86 Family 6 Model 167 Stepping 1, GenuineIntel; PROCESSOR_LEVEL=6; PROCESSOR_REVISION=a701; ProgramFiles=C:\Program Files; SESSIONNAME=Console; SystemDrive=C:; SystemRoot=C:\WINDOWS; TEMP=C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp; TMP=C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp; USERDOMAIN=BONELEE-B1632A4; USERNAME=Administrator; USERPROFILE=C:\Documents and Settings\Administrator; windir=C:\WINDOWS" "21:42:46.0860205","Lab10-02.exe","3560","Thread Create","","SUCCESS","Thread ID: 3512" "21:42:46.0862275","Lab10-02.exe","3560","QueryNameInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","Name: \Documents and Settings\Administrator\桌面\lab\Lab10-02.exe" "21:42:46.0864543","Lab10-02.exe","3560","Load Image","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","Image Base: 0x400000, Image Size: 0x9000" "21:42:46.0866099","Lab10-02.exe","3560","Load Image","C:\WINDOWS\system32\ntdll.dll","SUCCESS","Image Base: 0x7c920000, Image Size: 0x93000" "21:42:46.0866242","Lab10-02.exe","3560","QueryNameInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","Name: \Documents and Settings\Administrator\桌面\lab\Lab10-02.exe" "21:42:46.0867716","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\Prefetch\LAB10-02.EXE-323D9C35.pf","SUCCESS","Desired Access: Generic Read, Disposition: Open, Options: Synchronous IO Non-Alert, Attributes: n/a, ShareMode: None, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0868760","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\Prefetch\LAB10-02.EXE-323D9C35.pf","SUCCESS","AllocationSize: 8,192, EndOfFile: 4,804, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0869591","Lab10-02.exe","3560","ReadFile","C:\WINDOWS\Prefetch\LAB10-02.EXE-323D9C35.pf","SUCCESS","Offset: 0, Length: 4,804" "21:42:46.0871003","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\Prefetch\LAB10-02.EXE-323D9C35.pf","SUCCESS","" "21:42:46.0871324","Lab10-02.exe","3560","CreateFile","C:","SUCCESS","Desired Access: Read Attributes, Write Attributes, Synchronize, Disposition: Open, Options: Synchronous IO Non-Alert, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0871634","Lab10-02.exe","3560","QueryInformationVolume","C:","SUCCESS","VolumeCreationTime: 2022-10-2 3:29:03, VolumeSerialNumber: AC10-70A8, SupportsObjects: True, VolumeLabel: " "21:42:46.0871772","Lab10-02.exe","3560","FileSystemControl","C:","SUCCESS","Control: FSCTL_FILE_PREFETCH" "21:42:46.0872062","Lab10-02.exe","3560","CreateFile","C:\","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0872307","Lab10-02.exe","3560","QueryDirectory","C:\","SUCCESS","0: AUTOEXEC.BAT, 1: boot.ini, 2: bootfont.bin, 3: CONFIG.SYS, 4: DLL1.dll, 5: DLL2.dll, 6: Documents and Settings, 7: IO.SYS, 8: Lab09-01.exe, 9: MSDOS.SYS, 10: NTDETECT.COM, 11: ntldr, 12: ocl.exe, 13: pagefile.sys, 14: Program Files, 15: RECYCLER, 16: System Volume Information, 17: WINDOWS" "21:42:46.0872688","Lab10-02.exe","3560","QueryDirectory","C:\","NO MORE FILES","" "21:42:46.0873112","Lab10-02.exe","3560","CloseFile","C:\","SUCCESS","" "21:42:46.0873866","Lab10-02.exe","3560","CreateFile","C:\DOCUMENTS AND SETTINGS","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0874144","Lab10-02.exe","3560","QueryDirectory","C:\Documents and Settings","SUCCESS","0: ., 1: .., 2: Administrator, 3: All Users, 4: Default User, 5: LocalService, 6: NetworkService" "21:42:46.0874594","Lab10-02.exe","3560","QueryDirectory","C:\Documents and Settings","NO MORE FILES","" "21:42:46.0875079","Lab10-02.exe","3560","CloseFile","C:\Documents and Settings","SUCCESS","" "21:42:46.0875818","Lab10-02.exe","3560","CreateFile","C:\Documents and Settings\ADMINISTRATOR","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0876091","Lab10-02.exe","3560","QueryDirectory","C:\Documents and Settings\Administrator","SUCCESS","0: ., 1: .., 2: Application Data, 3: Cookies, 4: Favorites, 5: Local Settings, 6: log.txt, 7: My Documents, 8: NetHood, 9: NTUSER.DAT, 10: ntuser.dat.LOG, 11: ntuser.ini, 12: PrintHood, 13: Recent, 14: SendTo, 15: Templates, 16: UserData, 17: 「开始」菜单, 18: 桌面" "21:42:46.0876451","Lab10-02.exe","3560","QueryDirectory","C:\Documents and Settings\Administrator","NO MORE FILES","" "21:42:46.0877545","Lab10-02.exe","3560","CloseFile","C:\Documents and Settings\Administrator","SUCCESS","" "21:42:46.0878990","Lab10-02.exe","3560","CreateFile","C:\Documents and Settings\Administrator\桌面","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0879966","Lab10-02.exe","3560","QueryDirectory","C:\Documents and Settings\Administrator\桌面","SUCCESS","0: ., 1: .., 2: DLL1.dll, 3: DLL2.dll, 4: Firefox-latest.exe, 5: lab, 6: Lab09-01.exe, 7: Lab09-02.exe, 8: Lab10-02.exe, 9: LieBaoBrowser.exe, 10: Logfile.CSV, 11: Logfile2.CSV, 12: NetFx20SP1_x86.exe, 13: ocl.exe, 14: ProcessExplorer-20161118, 15: ProcessExplorer-20161118.zip, 16: ProcessMonitor_3.83, 17: ProcessMonitor_3.83.zip, 18: Procmon汉化版 v3.20.0.0.exe, 19: reg1-202210041846.hivu, 20: Regshot-1.9.0, 21: WinDbg.lnk, 22: Windbgx86-v6.12.2.633.msi, 23: WindowsXP-KB936929-SP3-x86-symbols-full-ENU.exe, 24: winsdk_web.exe, 25: ~res-x86.txt, 26: 快捷方式 到 procexp.lnk, 27: 猎豹安全浏览器.lnk" "21:42:46.0880896","Lab10-02.exe","3560","QueryDirectory","C:\Documents and Settings\Administrator\桌面","NO MORE FILES","" "21:42:46.0881978","Lab10-02.exe","3560","CloseFile","C:\Documents and Settings\Administrator\桌面","SUCCESS","" "21:42:46.0883479","Lab10-02.exe","3560","CreateFile","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0884575","Lab10-02.exe","3560","QueryDirectory","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS","0: ., 1: .., 2: Lab10-01.exe, 3: Lab10-01.sys, 4: Lab10-02.exe, 5: Lab10-03.exe, 6: Lab10-03.sys" "21:42:46.0885975","Lab10-02.exe","3560","QueryDirectory","C:\Documents and Settings\Administrator\桌面\lab","NO MORE FILES","" "21:42:46.0888475","Lab10-02.exe","3560","CloseFile","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS","" "21:42:46.0889764","Lab10-02.exe","3560","CreateFile","C:\WINDOWS","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0890507","Lab10-02.exe","3560","QueryDirectory","C:\WINDOWS","SUCCESS","0: ., 1: .., 2: 0.log, 3: addins, 4: AppPatch, 5: assembly, 6: Blue Lace 16.bmp, 7: bootstat.dat, 8: clock.avi, 9: cmsetacl.log, 10: Coffee Bean.bmp, 11: comsetup.log, 12: Config, 13: Connection Wizard, 14: control.ini, 15: Cursors, 16: Debug, 17: desktop.ini, 18: Downloaded Program Files, 19: Driver Cache, 20: DtcInstall.log, 21: ehome, 22: explorer.exe, 23: explorer.scf, 24: FaxSetup.log, 25: FeatherTexture.bmp, 26: Fonts, 27: Gone Fishing.bmp, 28: Greenstone.bmp, 29: Help, 30: hh.exe, 31: iis6.log, 32: ime, 33: imsins.BAK, 34: imsins.log, 35: inf, 36: Installer, 37: java, 38: L2Schemas, 39: MedCtrOC.log, 40: Media, 41: Microsoft.NET, 42: msagent, 43: msapps, 44: msdfmap.ini, 45: msgsocm.log, 46: msmqinst.log, 47: mui, 48: netfxocm.log, 49: Network Diagnostic, 50: NOTEPAD.EXE, 51: ntdtcsetup.log, 52: ocgen.log, 53: ocmsn.log, 54: ODBCINST.INI, 55: OEWABLog.txt, 56: Offline Web Pages, 57: oobeact.log, 58: pchealth, 59: PeerNet, 60: Prairie Wind.bmp, 61: Prefetch, 62: Provisioning, 63: regedit.exe, 64: Registration, 65: REGLOCS.OLD, 66: regopt.log, 67: repair, 68: Resources, 69: Rhododendron.bmp, 70: River Sumida.bmp, 71: Santa Fe Stucco.bmp, 72: SchedLgU.Txt, 73: security, 74: sessmgr.setup.log, 75: SET3.tmp, 76: SET4.tmp, 77: SET8.tmp, 78: setupact.log, 79: setupapi.log, 80: setuperr.log, 81: setuplog.txt, 82: Soap Bubbles.bmp, 83: SoftwareDistribution, 84: srchasst, 85: Sti_Trace.log, 86: Symbols, 87: system, 88: system.ini, 89: system32, 90: tabletoc.log, 91: TASKMAN.EXE, 92: Tasks, 93: Temp, 94: tsoc.log, 95: twain.dll, 96: twain_32, 97: twain_32.dll, 98: twunk_16.exe, 99: twunk_32.exe, 100: vb.ini, 101: vbaddin.ini, 102: vmmreg32.dll, 103: Web, 104: wiadebug.log, 105: wiaservc.log, 106: win.ini, 107: WindowsShell.Manifest, 108: WindowsUpdate.log, 109: winhelp.exe, 110: winhlp32.exe, 111: winnt.bmp, 112: winnt256.bmp, 113: WinSxS, 114: wmprfCHS.prx, 115: wmsetup.log, 116: WMSysPr9.prx, 117: Zapotec.bmp, 118: _default.pif" "21:42:46.0891914","Lab10-02.exe","3560","QueryDirectory","C:\WINDOWS","NO MORE FILES","" "21:42:46.0892817","Lab10-02.exe","3560","CloseFile","C:\WINDOWS","SUCCESS","" "21:42:46.0894543","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32","SUCCESS","Desired Access: Read Data/List Directory, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: n/a, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0895528","Lab10-02.exe","3560","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: ., 1: .., 2: $winnt$.inf, 3: 1025, 4: 1028, 5: 1031, 6: 1033, 7: 1037, 8: 1041, 9: 1042, 10: 1054, 11: 12520437.cpx, 12: 12520850.cpx, 13: 2052, 14: 3076, 15: 3com_dmi, 16: 6to4svc.dll, 17: a15.tbl, 18: a234.tbl, 19: aaaamon.dll, 20: aaclient.dll, 21: access.cpl, 22: acctres.dll, 23: accwiz.exe, 24: acelpdec.ax, 25: acledit.dll, 26: aclui.dll, 27: acode.tbl, 28: activeds.dll, 29: activeds.tlb, 30: actmovie.exe, 31: actxprxy.dll, 32: admparse.dll, 33: adptif.dll, 34: adsldp.dll, 35: adsldpc.dll, 36: adsmsext.dll, 37: adsnds.dll, 38: adsnt.dll, 39: adsnw.dll, 40: advapi32.dll, 41: advpack.dll, 42: ahui.exe, 43: alg.exe, 44: alrsvc.dll, 45: amcompat.tlb, 46: amstream.dll, 47: ansi.sys, 48: apcups.dll, 49: append.exe, 50: apphelp.dll, 51: appmgmt, 52: appmgmts.dll, 53: appmgr.dll, 54: appwiz.cpl, 55: arp.exe, 56: arphr.tbl, 57: arptr.tbl, 58: array30.tab, 59: arrayhw.tab, 60: asctrls.ocx, 61: asferror.dll, 62: asr_fmt.exe, 63: asr_ldm.exe, 64: asr_pfu.exe, 65: asycfilt.dll, 66: at.exe, 67: atkctrs.dll, 68: atl.dll, 69: atmadm.exe, 70: atmfd.dll, 71: atmlib.dll, 72: atmpvcno.dll, 73: atrace.dll, 74: attrib.exe, 75: audiosrv.dll, 76: auditusr.exe, 77: authz.dll, 78: autochk.exe, 79: autoconv.exe, 80: autodisc.dll, 81: AUTOEXEC.NT, 82: autofmt.exe, 83: autolfn.exe, 84: avicap.dll, 85: avicap32.dll, 86: avifil32.dll, 87: avifile.dll, 88: avmeter.dll, 89: avtapi.dll, 90: avwav.dll, 91: azroles.dll, 92: basesrv.dll, 93: batmeter.dll, 94: batt.dll, 95: bidispl.dll, 96: big5.nls, 97: bios1.rom, 98: bios4.rom, 99: bitsprx2.dll, 100: bitsprx3.dll, 101: bitsprx4.dll, 102: blackbox.dll, 103: blastcln.exe, 104: bootcfg.exe, 105: bootok.exe, 106: bootvid.dll, 107: bootvrfy.exe, 108: bopomofo.nls, 109: bopomofo.uce, 110: browselc.dll, 111: browser.dll, 112: browseui.dll, 113: browsewm.dll, 114: bthci.dll, 115: bthprops.cpl, 116: bthserv.dll, 117: btpanui.dll, 118: cabinet.dll, 119: cabview.dll, 120: cacls.exe, 121: calc.exe, 122: camocx.dll, 123: capesnpn.dll, 124: cards.dll, 125: CatRoot, 126: CatRoot2, 127: catsrv.dll, 128: catsrvps.dll, 129: catsrvut.dll, 130: ccfgnt.dll, 131: cdfview.dll, 132: cdm.dll, 133: cdmodem.dll, 134: cdosys.dll, 135: cdplayer.exe.manifest, 136: certcli.dll, 137: certmgr.dll, 138: certmgr.msc, 139: cewmdm.dll, 140: cfgbkend.dll, 141: cfgmgr32.dll, 142: chajei.ime, 143: charmap.exe, 144: chcp.com, 145: chkdsk.exe, 146: chkntfs.exe, 147: ChsBrKr.dll, 148: chtbrkr.dll, 149: ciadmin.dll, 150: ciadv.msc, 151: cic.dll, 152: cidaemon.exe, 153: CINTLGNT.IME, 154: ciodm.dll, 155: cipher.exe, 156: cisvc.exe, 157: ckcnv.exe, 158: clb.dll, 159: clbcatex.dll, 160: clbcatq.dll, 161: cleanmgr.exe, 162: cliconf.chm, 163: cliconfg.dll, 164: cliconfg.exe, 165: cliconfg.rll, 166: clipbrd.exe, 167: clipsrv.exe, 168: clusapi.dll, 169: cmcfg32.dll, 170: cmd.exe, 171: cmdial32.dll, 172: cmdl32.exe, 173: cmdlib.wsc, 174: cmmgr32.hlp, 175: cmmon32.exe, 176: cmos.ram, 177: cmpbk32.dll, 178: cmprops.dll, 179: cmsetACL.dll, 180: cmstp.exe, 181: cmutil.dll, 182: cnbjmon.dll, 183: cnetcfg.dll, 184: cnvfat.dll, 185: colbact.dll, 186: Com, 187: comaddin.dll, 188: comcat.dll, 189: comctl32.dll, 190: comdlg32.dll, 191: comm.drv, 192: command.com, 193: commdlg.dll, 194: comp.exe, 195: compact.exe, 196: compatUI.dll, 197: compmgmt.msc, 198: compobj.dll, 199: compstui.dll, 200: comrepl.dll, 201: comres.dll, 202: comsnap.dll, 203: comsvcs.dll, 204: comuid.dll, 205: config, 206: CONFIG.NT, 207: CONFIG.TMP, 208: confmsp.dll, 209: conime.exe, 210: console.dll, 211: control.exe, 212: convert.exe, 213: corpol.dll, 214: country.sys, 215: credssp.dll, 216: credui.dll, 217: crtdll.dll, 218: crypt32.dll, 219: cryptdlg.dll, 220: cryptdll.dll, 221: cryptext.dll, 222: cryptnet.dll, 223: cryptsvc.dll, 224: cryptui.dll, 225: cscdll.dll, 226: cscript.exe, 227: cscui.dll, 228: csrsrv.dll, 229: csrss.exe, 230: csseqchk.dll, 231: ctfmon.exe, 232: ctl3d32.dll, 233: ctl3dv2.dll, 234: ctype.nls, 235: c_037.nls, 236: c_10000.nls, 237: c_10001.nls, 238: c_10002.nls, 239: c_10003.nls, 240: c_10006.nls, 241: c_10007.nls, 242: c_10008.nls, 243: c_10010.nls, 244: c_10017." "21:42:46.0897328","Lab10-02.exe","3560","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: dssec.dat, 1: dssec.dll, 2: dssenh.dll, 3: dsuiext.dll, 4: dswave.dll, 5: dumprep.exe, 6: duser.dll, 7: dvdplay.exe, 8: dvdupgrd.exe, 9: dwwin.exe, 10: dx7vb.dll, 11: dx8vb.dll, 12: dxdiag.exe, 13: dxdiagn.dll, 14: dxmasf.dll, 15: dxtmsft.dll, 16: dxtrans.dll, 17: eapolqec.dll, 18: eapp3hst.dll, 19: eappcfg.dll, 20: eappgnui.dll, 21: eapphost.dll, 22: eappprxy.dll, 23: eapqec.dll, 24: eapsvc.dll, 25: edit.com, 26: edit.hlp, 27: edlin.exe, 28: efsadu.dll, 29: ega.cpi, 30: els.dll, 31: emptyregdb.dat, 32: encapi.dll, 33: encdec.dll, 34: EqnClass.Dll, 35: ersvc.dll, 36: es.dll, 37: esent.dll, 38: esent97.dll, 39: esentprf.dll, 40: esentprf.hxx, 41: esentprf.ini, 42: esentutl.exe, 43: eudcedit.exe, 44: eula.txt, 45: eventcls.dll, 46: eventcreate.exe, 47: eventlog.dll, 48: eventquery.vbs, 49: eventtriggers.exe, 50: eventvwr.exe, 51: eventvwr.msc, 52: exe2bin.exe, 53: expand.exe, 54: export, 55: expsrv.dll, 56: extmgr.dll, 57: extrac32.exe, 58: exts.dll, 59: f3ahvoas.dll, 60: fastopen.exe, 61: faultrep.dll, 62: fc.exe, 63: fde.dll, 64: fdeploy.dll, 65: feclient.dll, 66: femgrate.exe, 67: filemgmt.dll, 68: find.exe, 69: findstr.exe, 70: finger.exe, 71: firewall.cpl, 72: fixmapi.exe, 73: fldrclnr.dll, 74: fltlib.dll, 75: fltMc.exe, 76: fmifs.dll, 77: FNTCACHE.DAT, 78: fontext.dll, 79: fontsub.dll, 80: fontview.exe, 81: forcedos.exe, 82: format.com, 83: framebuf.dll, 84: freecell.exe, 85: fsmgmt.msc, 86: fsquirt.exe, 87: fsusd.dll, 88: fsutil.exe, 89: ftp.exe, 90: ftsrch.dll, 91: fwcfg.dll, 92: g711codc.ax, 93: gb2312.uce, 94: gcdef.dll, 95: gdi.exe, 96: gdi32.dll, 97: geo.nls, 98: getmac.exe, 99: getuname.dll, 100: glmf32.dll, 101: glu32.dll, 102: gpedit.dll, 103: gpedit.msc, 104: gpkcsp.dll, 105: gpkrsrc.dll, 106: gpresult.exe, 107: gptext.dll, 108: gpupdate.exe, 109: graftabl.com, 110: graphics.com, 111: graphics.pro, 112: grpconv.exe, 113: h323.tsp, 114: h323log.txt, 115: h323msp.dll, 116: hal.dll, 117: hccoin.dll, 118: hdwwiz.cpl, 119: help.exe, 120: hhctrl.ocx, 121: hhsetup.dll, 122: hid.dll, 123: hidphone.tsp, 124: himem.sys, 125: hlink.dll, 126: hnetcfg.dll, 127: hnetmon.dll, 128: hnetwiz.dll, 129: homepage.inf, 130: hostname.exe, 131: hotplug.dll, 132: hticons.dll, 133: html.iec, 134: httpapi.dll, 135: htui.dll, 136: hypertrm.dll, 137: iac25_32.ax, 138: ias, 139: iasacct.dll, 140: iasads.dll, 141: iashlpr.dll, 142: iasnap.dll, 143: iaspolcy.dll, 144: iasrad.dll, 145: iasrecst.dll, 146: iassam.dll, 147: iassdo.dll, 148: iassvcs.dll, 149: icaapi.dll, 150: iccvid.dll, 151: icfgnt5.dll, 152: icm32.dll, 153: icmp.dll, 154: icmui.dll, 155: icsxml, 156: icwdial.dll, 157: icwphbk.dll, 158: ideograf.uce, 159: idq.dll, 160: ie4uinit.exe, 161: ieakeng.dll, 162: ieaksie.dll, 163: ieakui.dll, 164: iedkcs32.dll, 165: ieencode.dll, 166: iepeers.dll, 167: iernonce.dll, 168: iesetup.dll, 169: ieuinit.inf, 170: iexpress.exe, 171: ifmon.dll, 172: ifsutil.dll, 173: igmpagnt.dll, 174: iissuba.dll, 175: ils.dll, 176: imaadp32.acm, 177: imagehlp.dll, 178: imapi.exe, 179: IME, 180: imegen.tpl, 181: imekr61.ime, 182: imeshare.dll, 183: imgutil.dll, 184: imjp81.ime, 185: imjp81k.dll, 186: imm32.dll, 187: inetcfg.dll, 188: inetcomm.dll, 189: inetcpl.cpl, 190: inetcplc.dll, 191: inetmib1.dll, 192: inetpp.dll, 193: inetppui.dll, 194: inetres.dll, 195: inetsrv, 196: infosoft.dll, 197: initpki.dll, 198: input.dll, 199: inseng.dll, 200: instcat.sql, 201: intl.cpl, 202: iologmsg.dll, 203: ipconf.tsp, 204: ipconfig.exe, 205: iphlpapi.dll, 206: ipmontr.dll, 207: ipnathlp.dll, 208: ippromon.dll, 209: iprop.dll, 210: iprtprio.dll, 211: iprtrmgr.dll, 212: ipsec6.exe, 213: ipsecsnp.dll, 214: ipsecsvc.dll, 215: ipsmsnap.dll, 216: ipv6.exe, 217: ipv6mon.dll, 218: ipxmontr.dll, 219: ipxpromn.dll, 220: ipxrip.dll, 221: ipxroute.exe, 222: ipxrtmgr.dll, 223: ipxsap.dll, 224: ipxwan.dll, 225: ir32_32.dll, 226: ir41_32.ax, 227: ir41_qc.dll, 228: ir41_qcx.dll, 229: ir50_32.dll, 230: ir50_qc.dll, 231: ir50_qcx.dll, 232: irclass.dll, 233: irftp.exe, 234: irmon.dll, 235: irprops.cpl, 236: isign32.dll, 237: isrdbg32.dll, 238: itircl.dll, 239: itss.dll, 240: iuengine.d" "21:42:46.0898942","Lab10-02.exe","3560","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: mfc42.dll, 1: mfc42loc.dll, 2: mfc42u.dll, 3: mfc71.dll, 4: mfc71u.dll, 5: mfcsubs.dll, 6: mgmtapi.dll, 7: mib.bin, 8: Microsoft, 9: microsoft.managementconsole.dll, 10: midimap.dll, 11: miglibnt.dll, 12: migpwd.exe, 13: mimefilt.dll, 14: miniime.tpl, 15: mlang.dat, 16: mlang.dll, 17: mll_hp.dll, 18: mll_mtf.dll, 19: mll_qic.dll, 20: Mlwx486.sys, 21: mmc.exe, 22: mmcbase.dll, 23: mmcex.dll, 24: mmcfxcommon.dll, 25: mmcndmgr.dll, 26: mmcperf.exe, 27: mmcshext.dll, 28: mmdriver.inf, 29: mmdrv.dll, 30: mmfutil.dll, 31: mmsys.cpl, 32: mmsystem.dll, 33: mmtask.tsk, 34: mmutilse.dll, 35: mnmdd.dll, 36: mnmsrvc.exe, 37: mobsync.dll, 38: mobsync.exe, 39: mode.com, 40: modemui.dll, 41: modex.dll, 42: more.com, 43: moricons.dll, 44: mountvol.exe, 45: mouse.drv, 46: mp43dmod.dll, 47: mp4sdmod.dll, 48: mpeg2data.ax, 49: mpg2splt.ax, 50: mpg4dmod.dll, 51: mpg4ds32.ax, 52: mplay32.exe, 53: mpnotify.exe, 54: mpr.dll, 55: mprapi.dll, 56: mprddm.dll, 57: mprdim.dll, 58: mprmsg.dll, 59: mprui.dll, 60: mqad.dll, 61: mqbkup.exe, 62: mqcertui.dll, 63: mqdscli.dll, 64: mqgentr.dll, 65: mqise.dll, 66: mqlogmgr.dll, 67: mqoa.dll, 68: mqoa.tlb, 69: mqoa10.tlb, 70: mqoa20.tlb, 71: mqperf.dll, 72: mqperf.ini, 73: mqprfsym.h, 74: mqqm.dll, 75: mqrt.dll, 76: mqrtdep.dll, 77: mqsec.dll, 78: mqsnap.dll, 79: mqsvc.exe, 80: mqtgsvc.exe, 81: mqtrig.dll, 82: mqupgrd.dll, 83: mqutil.dll, 84: mrinfo.exe, 85: msaatext.dll, 86: msacm.dll, 87: msacm32.dll, 88: msacm32.drv, 89: msadds32.ax, 90: msadp32.acm, 91: msafd.dll, 92: msapsspc.dll, 93: msasn1.dll, 94: msaud32.acm, 95: msaudite.dll, 96: mscat32.dll, 97: mscdexnt.exe, 98: mscms.dll, 99: msconf.dll, 100: mscoree.dll, 101: mscorier.dll, 102: mscories.dll, 103: mscpx32r.dLL, 104: mscpxl32.dLL, 105: MSCTF.dll, 106: MSCTFIME.IME, 107: MSCTFP.dll, 108: msdadiag.dll, 109: msdart.dll, 110: msdatsrc.tlb, 111: msdayi.tbl, 112: msdmo.dll, 113: MsDtc, 114: msdtc.exe, 115: msdtclog.dll, 116: msdtcprf.h, 117: msdtcprf.ini, 118: msdtcprx.dll, 119: msdtctm.dll, 120: msdtcuiu.dll, 121: msdxm.ocx, 122: msdxmlc.dll, 123: msencode.dll, 124: msexch40.dll, 125: msexcl40.dll, 126: msftedit.dll, 127: msg.exe, 128: msg711.acm, 129: msg723.acm, 130: msgina.dll, 131: msgsm32.acm, 132: msgsvc.dll, 133: msh261.drv, 134: msh263.drv, 135: mshearts.exe, 136: mshta.exe, 137: mshtml.dll, 138: mshtml.tlb, 139: mshtmled.dll, 140: mshtmler.dll, 141: msi.dll, 142: msident.dll, 143: msidle.dll, 144: msidntld.dll, 145: msieftp.dll, 146: msiexec.exe, 147: msihnd.dll, 148: msimg32.dll, 149: msimsg.dll, 150: MSIMTF.dll, 151: msir3jp.dll, 152: msir3jp.lex, 153: msisip.dll, 154: msjet40.dll, 155: msjetoledb40.dll, 156: msjint40.dll, 157: msjter40.dll, 158: msjtes40.dll, 159: mslbui.dll, 160: msls31.dll, 161: msltus40.dll, 162: msnetobj.dll, 163: msnsspc.dll, 164: msobjs.dll, 165: msoeacct.dll, 166: msoert2.dll, 167: msorc32r.dll, 168: msorcl32.dll, 169: mspaint.exe, 170: mspatcha.dll, 171: mspbde40.dll, 172: mspmsnsv.dll, 173: mspmsp.dll, 174: msports.dll, 175: msprivs.dll, 176: msr2c.dll, 177: msr2cenu.dll, 178: msratelc.dll, 179: msrating.dll, 180: msrclr40.dll, 181: msrd2x40.dll, 182: msrd3x40.dll, 183: msrecr40.dll, 184: msrepl40.dll, 185: msrle32.dll, 186: mssap.dll, 187: msscds32.ax, 188: msscp.dll, 189: msscript.ocx, 190: mssha.dll, 191: msshavmsg.dll, 192: mssign32.dll, 193: mssip32.dll, 194: msswch.dll, 195: msswchx.exe, 196: mstask.dll, 197: mstext40.dll, 198: mstime.dll, 199: mstinit.exe, 200: mstlsapi.dll, 201: mstsc.exe, 202: mstscax.dll, 203: msutb.dll, 204: msv1_0.dll, 205: msvbvm50.dll, 206: msvbvm60.dll, 207: msvcirt.dll, 208: msvcp50.dll, 209: msvcp60.dll, 210: msvcr71.dll, 211: msvcrt.dll, 212: msvcrt20.dll, 213: msvcrt40.dll, 214: msvfw32.dll, 215: msvidc32.dll, 216: msvidctl.dll, 217: msvideo.dll, 218: msw3prt.dll, 219: mswdat10.dll, 220: mswebdvd.dll, 221: mswmdm.dll, 222: mswsock.dll, 223: mswstr10.dll, 224: msxbde40.dll, 225: msxml.dll, 226: msxml2.dll, 227: msxml2r.dll, 228: msxml3.dll, 229: msxml3r.dll, 230: msxml6.dll, 231: msxml6r.dll, 232: msxmlr.dll, 233: msyuv.dll, 234: mtxclu.dll, 235: mtxdm.dll, 236: mtxex.dll, 2" "21:42:46.0900743","Lab10-02.exe","3560","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: phoncode.tbl, 1: phonptr.tbl, 2: photometadatahandler.dll, 3: photowiz.dll, 4: pid.dll, 5: pid.inf, 6: pid.PNF, 7: pidgen.dll, 8: pifmgr.dll, 9: ping.exe, 10: ping6.exe, 11: PINTLGNT.IME, 12: PINTLPAD.HLP, 13: PINTLPAE.HLP, 14: pjlmon.dll, 15: plustab.dll, 16: pmspl.dll, 17: pngfilt.dll, 18: pnrpnsp.dll, 19: polstore.dll, 20: powercfg.cpl, 21: powercfg.exe, 22: powrprof.dll, 23: prc.nls, 24: prcp.nls, 25: prfc0804.dat, 26: prfd0804.dat, 27: prfh0804.dat, 28: prfi0804.dat, 29: prflbmsg.dll, 30: print.exe, 31: printui.dll, 32: prncnfg.vbs, 33: prndrvr.vbs, 34: prnjobs.vbs, 35: prnmngr.vbs, 36: prnport.vbs, 37: prnqctl.vbs, 38: proctexe.ocx, 39: prodspec.ini, 40: profmap.dll, 41: progman.exe, 42: proquota.exe, 43: proxycfg.exe, 44: psapi.dll, 45: psbase.dll, 46: pschdcnt.h, 47: pschdprf.dll, 48: pschdprf.ini, 49: pscript.sep, 50: psnppagn.dll, 51: pstorec.dll, 52: pstorsvc.dll, 53: pubprn.vbs, 54: qagent.dll, 55: qagentrt.dll, 56: qappsrv.exe, 57: qasf.dll, 58: qcap.dll, 59: qcliprov.dll, 60: qdv.dll, 61: qdvd.dll, 62: qedit.dll, 63: qedwipes.dll, 64: qmgr.dll, 65: qmgrprxy.dll, 66: qosname.dll, 67: qprocess.exe, 68: quartz.dll, 69: query.dll, 70: quick.ime, 71: qutil.dll, 72: qwinsta.exe, 73: racpldlg.dll, 74: ras, 75: rasadhlp.dll, 76: rasapi32.dll, 77: rasauto.dll, 78: rasautou.exe, 79: raschap.dll, 80: rasctrnm.h, 81: rasctrs.dll, 82: rasctrs.ini, 83: rasdial.exe, 84: rasdlg.dll, 85: rasman.dll, 86: rasmans.dll, 87: rasmontr.dll, 88: rasmxs.dll, 89: rasphone.exe, 90: rasppp.dll, 91: rasqec.dll, 92: rasrad.dll, 93: rassapi.dll, 94: rasser.dll, 95: rastapi.dll, 96: rastls.dll, 97: rcbdyctl.dll, 98: rcimlby.exe, 99: rcp.exe, 100: rdchost.dll, 101: rdpcfgex.dll, 102: rdpclip.exe, 103: rdpdd.dll, 104: rdpsnd.dll, 105: rdpwsx.dll, 106: rdsaddin.exe, 107: rdshost.exe, 108: recover.exe, 109: redir.exe, 110: reg.exe, 111: regapi.dll, 112: regedt32.exe, 113: regini.exe, 114: regsvc.dll, 115: regsvr32.exe, 116: regwiz.exe, 117: regwizc.dll, 118: ReinstallBackups, 119: relog.exe, 120: remotepg.dll, 121: remotesp.tsp, 122: rend.dll, 123: replace.exe, 124: reset.exe, 125: Restore, 126: resutils.dll, 127: rexec.exe, 128: rhttpaa.dll, 129: riched20.dll, 130: riched32.dll, 131: rnr20.dll, 132: romanime.ime, 133: route.exe, 134: routemon.exe, 135: routetab.dll, 136: rpcns4.dll, 137: rpcrt4.dll, 138: rpcss.dll, 139: rsaci.rat, 140: rsaenh.dll, 141: rsfsaps.dll, 142: rsh.exe, 143: rshx32.dll, 144: rsm.exe, 145: rsmps.dll, 146: rsmsink.exe, 147: rsmui.exe, 148: rsnotify.exe, 149: rsop.msc, 150: rsopprov.exe, 151: rsvp.exe, 152: rsvp.ini, 153: rsvpcnts.h, 154: rsvpmsg.dll, 155: rsvpperf.dll, 156: rsvpsp.dll, 157: rtcshare.exe, 158: rtipxmib.dll, 159: rtm.dll, 160: rtutils.dll, 161: runas.exe, 162: rundll32.exe, 163: runonce.exe, 164: rwinsta.exe, 165: safrcdlg.dll, 166: safrdm.dll, 167: safrslv.dll, 168: samlib.dll, 169: samsrv.dll, 170: sapi.cpl.manifest, 171: savedump.exe, 172: sbe.dll, 173: sbeio.dll, 174: sc.exe, 175: scarddlg.dll, 176: scardssp.dll, 177: scardsvr.exe, 178: sccbase.dll, 179: sccsccp.dll, 180: scecli.dll, 181: scesrv.dll, 182: schannel.dll, 183: schedsvc.dll, 184: schtasks.exe, 185: sclgntfy.dll, 186: scochs.dll, 187: scredir.dll, 188: scriptpw.dll, 189: scrnsave.scr, 190: scrobj.dll, 191: scrrnchs.dll, 192: scrrun.dll, 193: sdbinst.exe, 194: sdhcinst.dll, 195: sdpblb.dll, 196: secedit.exe, 197: seclogon.dll, 198: secpol.msc, 199: secupd.dat, 200: secupd.sig, 201: secur32.dll, 202: security.dll, 203: sendcmsg.dll, 204: sendmail.dll, 205: sens.dll, 206: sensapi.dll, 207: senscfg.dll, 208: serialui.dll, 209: servdeps.dll, 210: services.exe, 211: services.msc, 212: serwvdrv.dll, 213: sessmgr.exe, 214: sethc.exe, 215: Setup, 216: setup.bmp, 217: setup.exe, 218: setupapi.dll, 219: setupdll.dll, 220: setupn.exe, 221: setver.exe, 222: sfc.dll, 223: sfc.exe, 224: sfcfiles.dll, 225: sfc_os.dll, 226: sfmapi.dll, 227: shadow.exe, 228: share.exe, 229: shdoclc.dll, 230: shdocvw.dll, 231: shell.dll, 232: shell32.dll, 233: ShellExt, 234: shellstyle.dll, 235: shfolder.dll, 236: shgina.dll, 237: shiftjis.uce, 238: shimeng.dll, 239: sh" "21:42:46.0902567","Lab10-02.exe","3560","QueryDirectory","C:\WINDOWS\system32","SUCCESS","0: usrrtosa.dll, 1: usrsdpia.dll, 2: usrshuta.exe, 3: usrsvpia.dll, 4: usrv42a.dll, 5: usrv80a.dll, 6: usrvoica.dll, 7: usrvpa.dll, 8: utildll.dll, 9: utilman.exe, 10: uxtheme.dll, 11: v7vga.rom, 12: vbajet32.dll, 13: vbicodec.ax, 14: vbisurf.ax, 15: vbschs.dll, 16: vbscript.dll, 17: vcdex.dll, 18: vdmdbg.dll, 19: vdmredir.dll, 20: ver.dll, 21: verclsid.exe, 22: verifier.dll, 23: verifier.exe, 24: version.dll, 25: vfpodbc.dll, 26: vga.dll, 27: vga.drv, 28: vga256.dll, 29: vga64k.dll, 30: vjoy.dll, 31: vmGuestLib.dll, 32: vmGuestLibJava.dll, 33: vmhgfs.dll, 34: VMUpgradeAtShutdownWXP.dll, 35: vmwogl32.dll, 36: VMWSU_V1_0.DLL, 37: vmx_fb.dll, 38: vmx_mode.dll, 39: vsocklib.dll, 40: vssadmin.exe, 41: vssapi.dll, 42: vssvc.exe, 43: vss_ps.dll, 44: vwipxspx.dll, 45: vwipxspx.exe, 46: w32time.dll, 47: w32tm.exe, 48: w32topl.dll, 49: w3ssl.dll, 50: watchdog.sys, 51: wavemsp.dll, 52: wbcache.deu, 53: wbcache.enu, 54: wbcache.esn, 55: wbcache.fra, 56: wbcache.ita, 57: wbcache.nld, 58: wbcache.sve, 59: wbdbase.deu, 60: wbdbase.enu, 61: wbdbase.esn, 62: wbdbase.fra, 63: wbdbase.ita, 64: wbdbase.nld, 65: wbdbase.sve, 66: wbem, 67: wdigest.dll, 68: wdl.trm, 69: wdmaud.drv, 70: webcheck.dll, 71: webclnt.dll, 72: webfldrs.msi, 73: webhits.dll, 74: webvw.dll, 75: wextract.exe, 76: wfwnet.drv, 77: wiaacmgr.exe, 78: wiadefui.dll, 79: wiadss.dll, 80: wiascr.dll, 81: wiaservc.dll, 82: wiasf.ax, 83: wiashext.dll, 84: wiavideo.dll, 85: wiavusd.dll, 86: wifeman.dll, 87: win.com, 88: win32k.sys, 89: win32spl.dll, 90: win87em.dll, 91: WINABC.CNT, 92: WINABC.CWD, 93: WINABC.HLP, 94: WINABC.IME, 95: WINABC.OVL, 96: winar30.ime, 97: winbrand.dll, 98: winchat.exe, 99: windowscodecs.dll, 100: windowscodecsext.dll, 101: WindowsLogon.manifest, 102: winfax.dll, 103: WINGB.IME, 104: winhelp.hlp, 105: winhlp32.exe, 106: winhttp.dll, 107: winime.ime, 108: wininet.dll, 109: winipsec.dll, 110: winlogon.exe, 111: winmine.exe, 112: winmm.dll, 113: winmsd.exe, 114: winnls.dll, 115: winntbbu.dll, 116: winoldap.mod, 117: WINPY.IME, 118: WINPY.MB, 119: winrnr.dll, 120: wins, 121: winscard.dll, 122: winshfhc.dll, 123: winsock.dll, 124: WINSP.IME, 125: WINSP.MB, 126: winspool.drv, 127: winspool.exe, 128: winsrv.dll, 129: winsta.dll, 130: winstrm.dll, 131: wintrust.dll, 132: winver.exe, 133: WINZM.IME, 134: WINZM.MB, 135: wkssvc.dll, 136: wlanapi.dll, 137: wldap32.dll, 138: wlnotify.dll, 139: wmadmod.dll, 140: wmadmoe.dll, 141: wmasf.dll, 142: wmdmlog.dll, 143: wmdmps.dll, 144: wmerrCHS.dll, 145: wmerror.dll, 146: wmi.dll, 147: wmidx.dll, 148: wmimgmt.msc, 149: wmiprop.dll, 150: wmiscmgr.dll, 151: wmnetmgr.dll, 152: wmp.dll, 153: wmp.ocx, 154: wmpasf.dll, 155: wmpcd.dll, 156: wmpcore.dll, 157: wmpdxm.dll, 158: wmphoto.dll, 159: wmploc.dll, 160: wmpshell.dll, 161: wmpui.dll, 162: wmsdmod.dll, 163: wmsdmoe.dll, 164: wmsdmoe2.dll, 165: wmspdmod.dll, 166: wmspdmoe.dll, 167: wmstream.dll, 168: wmv8ds32.ax, 169: wmvcore.dll, 170: wmvdmod.dll, 171: wmvdmoe2.dll, 172: wmvds32.ax, 173: wow32.dll, 174: wowdeb.exe, 175: wowexec.exe, 176: wowfax.dll, 177: wowfaxui.dll, 178: wpa.dbl, 179: wpabaln.exe, 180: wpnpinst.exe, 181: write.exe, 182: ws2help.dll, 183: ws2_32.dll, 184: wscntfy.exe, 185: wscript.exe, 186: wscsvc.dll, 187: wscui.cpl, 188: wsecedit.dll, 189: wshatm.dll, 190: wshbth.dll, 191: wshchs.dll, 192: wshcon.dll, 193: wshext.dll, 194: wship6.dll, 195: wshirda.dll, 196: wshisn.dll, 197: wshnetbs.dll, 198: wshom.ocx, 199: WshRm.dll, 200: wshtcpip.dll, 201: wsnmp32.dll, 202: wsock32.dll, 203: wstdecod.dll, 204: wstpager.ax, 205: wstrenderer.ax, 206: wtsapi32.dll, 207: wuapi.dll, 208: wuauclt.exe, 209: wuauclt1.exe, 210: wuaucpl.cpl, 211: wuaucpl.cpl.manifest, 212: wuaueng.dll, 213: wuaueng1.dll, 214: wuauserv.dll, 215: wucltui.dll, 216: wupdmgr.exe, 217: wups.dll, 218: wuweb.dll, 219: wzcdlg.dll, 220: wzcsapi.dll, 221: wzcsvc.dll, 222: xactsrv.dll, 223: xcopy.exe, 224: xenroll.dll, 225: xircom, 226: xjis.nls, 227: xmllite.dll, 228: xmlprov.dll, 229: xmlprovi.dll, 230: xolehlp.dll, 231: xpob2res.dll, 232: xpsp1res.dll, 233: xpsp2res.dll, 234: xpsp3res.dll, 235: zh-CHS, 236" "21:42:46.0904132","Lab10-02.exe","3560","QueryDirectory","C:\WINDOWS\system32","NO MORE FILES","" "21:42:46.0905182","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32","SUCCESS","" "21:42:46.0906878","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0908724","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\ntdll.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0908831","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS","AllocationSize: 589,824, EndOfFile: 589,312, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0909031","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\ntdll.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0910974","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0912333","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\kernel32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0912433","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS","AllocationSize: 1,150,976, EndOfFile: 1,150,464, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0912750","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\kernel32.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0914290","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\unicode.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0915864","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\unicode.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0915963","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\unicode.nls","SUCCESS","AllocationSize: 90,112, EndOfFile: 89,588, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0916152","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\unicode.nls","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0917800","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\locale.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0919066","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\locale.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0919161","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\locale.nls","SUCCESS","AllocationSize: 266,240, EndOfFile: 265,948, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0919349","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\locale.nls","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0920849","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\sorttbls.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0923734","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\sorttbls.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0923843","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\sorttbls.nls","SUCCESS","AllocationSize: 24,576, EndOfFile: 23,044, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0924050","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\sorttbls.nls","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0925602","Lab10-02.exe","3560","CreateFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0926859","Lab10-02.exe","3560","CreateFileMapping","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0926953","Lab10-02.exe","3560","QueryStandardInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","AllocationSize: 32,768, EndOfFile: 32,768, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0927147","Lab10-02.exe","3560","CreateFileMapping","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0930105","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0931303","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\advapi32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0931397","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS","AllocationSize: 675,840, EndOfFile: 674,816, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0931664","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\advapi32.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0933347","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0934547","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0934641","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","AllocationSize: 585,728, EndOfFile: 584,704, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0934835","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0936308","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\secur32.dll","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0937497","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\secur32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0937629","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\secur32.dll","SUCCESS","AllocationSize: 57,344, EndOfFile: 56,320, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0937821","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\secur32.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0939355","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\ctype.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0940494","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\ctype.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0940587","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\ctype.nls","SUCCESS","AllocationSize: 12,288, EndOfFile: 8,386, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0940819","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\ctype.nls","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0942488","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\sortkey.nls","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0943838","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\sortkey.nls","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0943934","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\sortkey.nls","SUCCESS","AllocationSize: 266,240, EndOfFile: 262,148, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0944127","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\sortkey.nls","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0945674","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\Mlwx486.sys","SUCCESS","Desired Access: Read Data/List Directory, Read Attributes, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0946913","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\Mlwx486.sys","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_READWRITE" "21:42:46.0947058","Lab10-02.exe","3560","QueryStandardInformationFile","C:\WINDOWS\system32\Mlwx486.sys","SUCCESS","AllocationSize: 4,096, EndOfFile: 3,456, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.0948449","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\Mlwx486.sys","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0949734","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS","" "21:42:46.0950960","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS","" "21:42:46.0952177","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\unicode.nls","SUCCESS","" "21:42:46.0953386","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\locale.nls","SUCCESS","" "21:42:46.0954587","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\sorttbls.nls","SUCCESS","" "21:42:46.0955772","Lab10-02.exe","3560","CloseFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","" "21:42:46.0957071","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS","" "21:42:46.0958440","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","" "21:42:46.0959653","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\secur32.dll","SUCCESS","" "21:42:46.0960855","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\ctype.nls","SUCCESS","" "21:42:46.0962050","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\sortkey.nls","SUCCESS","" "21:42:46.0963241","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\Mlwx486.sys","SUCCESS","" "21:42:46.0964816","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0965959","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\ntdll.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE" "21:42:46.0966336","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\ntdll.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0967903","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0969079","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\kernel32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE" "21:42:46.0969457","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\kernel32.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0970915","Lab10-02.exe","3560","CreateFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0972356","Lab10-02.exe","3560","CreateFileMapping","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE" "21:42:46.0972833","Lab10-02.exe","3560","CreateFileMapping","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0974363","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0975590","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\advapi32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE" "21:42:46.0975963","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\advapi32.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0977432","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0978570","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE" "21:42:46.0979024","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0980607","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\secur32.dll","SUCCESS","Desired Access: Execute/Traverse, Disposition: Open, Options: Non-Directory File, Attributes: N, ShareMode: Read, Write, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0981752","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\secur32.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE" "21:42:46.0982118","Lab10-02.exe","3560","CreateFileMapping","C:\WINDOWS\system32\secur32.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.0983385","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\ntdll.dll","SUCCESS","" "21:42:46.0984785","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\kernel32.dll","SUCCESS","" "21:42:46.0986044","Lab10-02.exe","3560","CloseFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","" "21:42:46.0987240","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\advapi32.dll","SUCCESS","" "21:42:46.0988442","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","" "21:42:46.0989739","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\secur32.dll","SUCCESS","" "21:42:46.0990084","Lab10-02.exe","3560","CloseFile","C:","SUCCESS","" "21:42:46.0991878","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Lab10-02.exe","NAME NOT FOUND","Desired Access: Read" "21:42:46.0993775","Lab10-02.exe","3560","CreateFile","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS","Desired Access: Execute/Traverse, Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Attributes: n/a, ShareMode: Read, Write, AllocationSize: n/a, OpenResult: Opened" "21:42:46.0994644","Lab10-02.exe","3560","FileSystemControl","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS","Control: FSCTL_IS_VOLUME_MOUNTED" "21:42:46.0995782","Lab10-02.exe","3560","QueryOpen","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe.Local","NAME NOT FOUND","" "21:42:46.0999411","Lab10-02.exe","3560","Load Image","C:\WINDOWS\system32\kernel32.dll","SUCCESS","Image Base: 0x7c800000, Image Size: 0x11e000" "21:42:46.1003262","Lab10-02.exe","3560","RegOpenKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS","Desired Access: Read" "21:42:46.1003536","Lab10-02.exe","3560","RegQueryValue","HKLM\System\CurrentControlSet\Control\Terminal Server\TSAppCompat","SUCCESS","Type: REG_DWORD, Length: 4, Data: 0" "21:42:46.1003680","Lab10-02.exe","3560","RegCloseKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS","" "21:42:46.1057409","conime.exe","560","QueryOpen","C:\WINDOWS\system32\MSIMTF.dll","SUCCESS","CreationTime: 2008-4-14 20:00:00, LastAccessTime: 2022-10-4 21:42:44, LastWriteTime: 2008-4-14 20:00:00, ChangeTime: 2022-10-1 19:31:26, AllocationSize: 159,744, EndOfFile: 159,232, FileAttributes: A" "21:42:46.1059036","conime.exe","560","CreateFile","C:\WINDOWS\system32\MSIMTF.dll","SUCCESS","Desired Access: Execute/Traverse, Synchronize, Disposition: Open, Options: Synchronous IO Non-Alert, Non-Directory File, Attributes: n/a, ShareMode: Read, Delete, AllocationSize: n/a, OpenResult: Opened" "21:42:46.1060176","conime.exe","560","CreateFileMapping","C:\WINDOWS\system32\MSIMTF.dll","SUCCESS","SyncType: SyncTypeCreateSection, PageProtection: PAGE_EXECUTE" "21:42:46.1060276","conime.exe","560","QueryStandardInformationFile","C:\WINDOWS\system32\MSIMTF.dll","SUCCESS","AllocationSize: 159,744, EndOfFile: 159,232, NumberOfLinks: 1, DeletePending: False, Directory: False" "21:42:46.1060471","conime.exe","560","CreateFileMapping","C:\WINDOWS\system32\MSIMTF.dll","SUCCESS","SyncType: SyncTypeOther" "21:42:46.1061626","conime.exe","560","CloseFile","C:\WINDOWS\system32\MSIMTF.dll","SUCCESS","" "21:42:46.1077331","Lab10-02.exe","3560","Load Image","C:\WINDOWS\system32\advapi32.dll","SUCCESS","Image Base: 0x77da0000, Image Size: 0xa9000" "21:42:46.1080494","Lab10-02.exe","3560","Load Image","C:\WINDOWS\system32\rpcrt4.dll","SUCCESS","Image Base: 0x77e50000, Image Size: 0x92000" "21:42:46.1082477","Lab10-02.exe","3560","Load Image","C:\WINDOWS\system32\secur32.dll","SUCCESS","Image Base: 0x77fc0000, Image Size: 0x11000" "21:42:46.1083130","Lab10-02.exe","3560","RegOpenKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS","Desired Access: Read" "21:42:46.1083362","Lab10-02.exe","3560","RegQueryValue","HKLM\System\CurrentControlSet\Control\Terminal Server\TSAppCompat","SUCCESS","Type: REG_DWORD, Length: 4, Data: 0" "21:42:46.1083490","Lab10-02.exe","3560","RegCloseKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS","" "21:42:46.1083774","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Secur32.dll","NAME NOT FOUND","Desired Access: Read" "21:42:46.1083998","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RPCRT4.dll","NAME NOT FOUND","Desired Access: Read" "21:42:46.1084658","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ADVAPI32.dll","NAME NOT FOUND","Desired Access: Read" "21:42:46.1084929","Lab10-02.exe","3560","RegOpenKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS","Desired Access: Read" "21:42:46.1085154","Lab10-02.exe","3560","RegQueryValue","HKLM\System\CurrentControlSet\Control\Terminal Server\TSAppCompat","SUCCESS","Type: REG_DWORD, Length: 4, Data: 0" "21:42:46.1085230","Lab10-02.exe","3560","RegQueryValue","HKLM\System\CurrentControlSet\Control\Terminal Server\TSUserEnabled","SUCCESS","Type: REG_DWORD, Length: 4, Data: 0" "21:42:46.1085419","Lab10-02.exe","3560","RegCloseKey","HKLM\System\CurrentControlSet\Control\Terminal Server","SUCCESS","" "21:42:46.1085512","Lab10-02.exe","3560","RegOpenKey","HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon","SUCCESS","Desired Access: Read" "21:42:46.1086020","Lab10-02.exe","3560","RegQueryValue","HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\LeakTrack","NAME NOT FOUND","Length: 144" "21:42:46.1086188","Lab10-02.exe","3560","RegCloseKey","HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon","SUCCESS","" "21:42:46.1086260","Lab10-02.exe","3560","RegOpenKey","HKLM","SUCCESS","Desired Access: Maximum Allowed" "21:42:46.1086410","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Diagnostics","NAME NOT FOUND","Desired Access: Read" "21:42:46.1086585","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ntdll.dll","NAME NOT FOUND","Desired Access: Read" "21:42:46.1087151","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kernel32.dll","NAME NOT FOUND","Desired Access: Read" "21:42:46.1090982","Lab10-02.exe","3560","RegOpenKey","HKCU","SUCCESS","Desired Access: Maximum Allowed" "21:42:46.1091166","Lab10-02.exe","3560","RegOpenKey","HKCU\Software\Policies\Microsoft\Control Panel\Desktop","NAME NOT FOUND","Desired Access: Read" "21:42:46.1091260","Lab10-02.exe","3560","RegOpenKey","HKCU\Control Panel\Desktop","SUCCESS","Desired Access: Read" "21:42:46.1091520","Lab10-02.exe","3560","RegQueryValue","HKCU\Control Panel\Desktop\MultiUILanguageId","NAME NOT FOUND","Length: 256" "21:42:46.1091629","Lab10-02.exe","3560","RegCloseKey","HKCU\Control Panel\Desktop","SUCCESS","" "21:42:46.1091749","Lab10-02.exe","3560","RegCloseKey","HKCU","SUCCESS","" "21:42:46.1093910","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32\Mlwx486.sys","SUCCESS","Desired Access: Generic Read/Write, Disposition: OverwriteIf, Options: Synchronous IO Non-Alert, Non-Directory File, Attributes: N, ShareMode: None, AllocationSize: 0, OpenResult: Overwritten" "21:42:46.1095674","Lab10-02.exe","3560","CreateFile","C:\WINDOWS\system32","SUCCESS","Desired Access: Synchronize, Disposition: Open, Options: Directory, Synchronous IO Non-Alert, Open For Backup, Attributes: N, ShareMode: Read, Write, AllocationSize: n/a, OpenResult: Opened" "21:42:46.1096675","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32","SUCCESS","" "21:42:46.1103389","Lab10-02.exe","3560","WriteFile","C:\WINDOWS\system32\Mlwx486.sys","SUCCESS","Offset: 0, Length: 3,456" "21:42:46.1105507","Lab10-02.exe","3560","CloseFile","C:\WINDOWS\system32\Mlwx486.sys","SUCCESS","" "21:42:46.1107331","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Rpc\PagedBuffers","NAME NOT FOUND","Desired Access: Read" "21:42:46.1107432","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Rpc","SUCCESS","Desired Access: Read" "21:42:46.1107580","Lab10-02.exe","3560","RegQueryValue","HKLM\SOFTWARE\Microsoft\Rpc\MaxRpcSize","NAME NOT FOUND","Length: 144" "21:42:46.1107781","Lab10-02.exe","3560","RegCloseKey","HKLM\SOFTWARE\Microsoft\Rpc","SUCCESS","" "21:42:46.1107885","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Lab10-02.exe\RpcThreadPoolThrottle","NAME NOT FOUND","Desired Access: Read" "21:42:46.1108200","Lab10-02.exe","3560","RegOpenKey","HKLM\Software\Policies\Microsoft\Windows NT\Rpc","NAME NOT FOUND","Desired Access: Read" "21:42:46.1108312","Lab10-02.exe","3560","RegOpenKey","HKLM\System\CurrentControlSet\Control\Session Manager","SUCCESS","Desired Access: Query Value" "21:42:46.1108518","Lab10-02.exe","3560","RegQueryValue","HKLM\System\CurrentControlSet\Control\Session Manager\SafeDllSearchMode","NAME NOT FOUND","Length: 16" "21:42:46.1108634","Lab10-02.exe","3560","RegCloseKey","HKLM\System\CurrentControlSet\Control\Session Manager","SUCCESS","" "21:42:46.1110067","Lab10-02.exe","3560","QueryNameInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","BUFFER OVERFLOW","Name: \D" "21:42:46.1110428","Lab10-02.exe","3560","QueryNameInformationFile","C:\Documents and Settings\Administrator\桌面\lab\Lab10-02.exe","SUCCESS","Name: \Documents and Settings\Administrator\桌面\lab\Lab10-02.exe" "21:42:46.1111282","Lab10-02.exe","3560","RegSetValue","HKLM\SOFTWARE\Microsoft\Cryptography\RNG\Seed","SUCCESS","Type: REG_BINARY, Length: 80, Data: 92 28 1C 2E A7 20 6E F9 C4 62 62 41 D8 BE 36 99" "21:42:46.1113430","Lab10-02.exe","3560","SetEndOfFileInformationFile","C:\WINDOWS\system32\config\software.LOG","SUCCESS","EndOfFile: 8,192" "21:42:46.1116926","Lab10-02.exe","3560","SetEndOfFileInformationFile","C:\WINDOWS\system32\config\software.LOG","SUCCESS","EndOfFile: 8,192" "21:42:46.1119784","Lab10-02.exe","3560","SetEndOfFileInformationFile","C:\WINDOWS\system32\config\software.LOG","SUCCESS","EndOfFile: 16,384" "21:42:46.1127924","Lab10-02.exe","3560","Thread Exit","","SUCCESS","Thread ID: 3512, User Time: 0.0000000, Kernel Time: 0.0000000" "21:42:46.1131951","Lab10-02.exe","3560","Process Exit","","SUCCESS","Exit Status: 0, User Time: 0.0156250 seconds, Kernel Time: 0.0000000 seconds, Private Bytes: 253,952, Peak Private Bytes: 258,048, Working Set: 1,015,808, Peak Working Set: 1,019,904" "21:42:46.1133121","Lab10-02.exe","3560","CloseFile","C:\Documents and Settings\Administrator\桌面\lab","SUCCESS",""
sys加载安装的过程基本上都看不到啊,gg,EDR检测咋做呢。。。todo
这里有几个我们已经见过好几次的函数,OpenSCManagerA是用来打开服务管理器的函数,StartServiceA是用来启动一个服务的函数,CreateServiceA是创建一个服务的,说明这个代码会在宿主计算机上创建一个服务来运行代码
书中还说了这两个函数LoadResource和SizeOfResource,说明这个代码对Lab10-02.exe的资源节做了一些操作,我们找找这两个函数
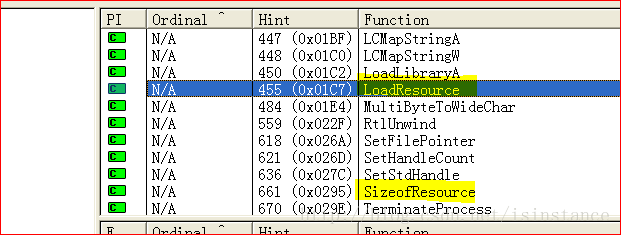
这两个函数是KERNEL32.DLL的导入函数,不注意看还是难发现的,然后我们知道了这个代码会操作自己的资源节,那我们就去检查一下这个程序的资源节
 ==》一看就是一个PE! dos mode。。。
==》一看就是一个PE! dos mode。。。
这里和书中的类似,发现了一个FILE,里面包含了一个PE头,正常程序的资源节长什么样,如下
这是ResourceHacker的资源节的样子,对比一下就知道区别在哪里了
接下来我们进行基础动态分析,对注册表做快照之后的结果 ==》我之前还嫌弃它,其实regshot这个工具还是可以的!避免了人工比较!
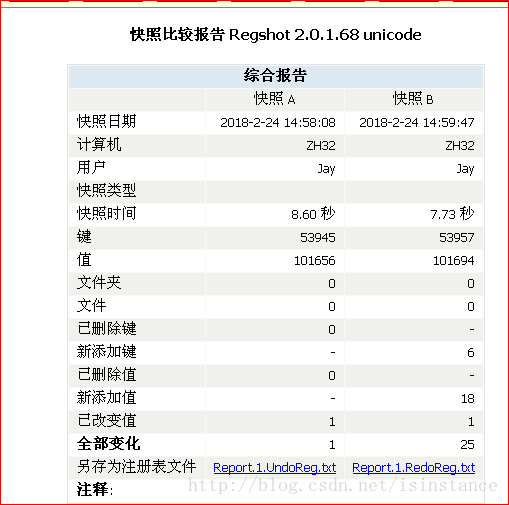
运行代码之后,增加了6个键,18个值,改变了1个值,增加的有以下
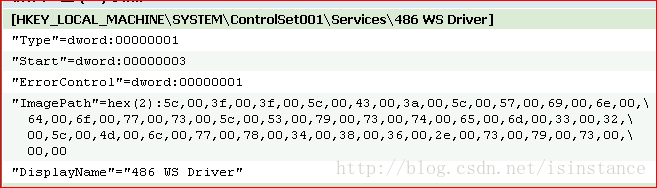
在服务这里增加了一个叫486 WS Driver的服务,然后下面就是对这个服务的集体细节进行配置

既然知道了这个代码已经改变了注册表,我们现在追着这个线索来搜索一下procmon ==》win xp的下载地址:http://www.downza.cn/soft/278272.html,之前一直没有找到合适的!

其他事件:

这里我们发现了一个叫services.exe的代码,执行了RegCreateKey,而且路径也和我们Regshot的结果相同
然后我们缩小搜索范围,搜索这个名叫services.exe的程序做了哪些其他事,记住此时这个程序的PID为656
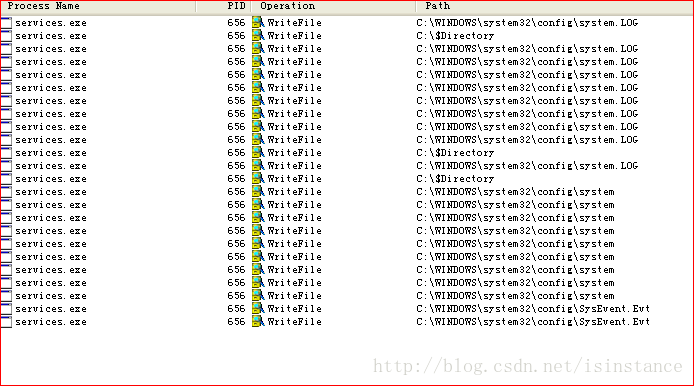
设置筛选条件为WriteFile之后,就会发现这个文件一共写了三个文件,一个是system.LOG,一个是system,还有一个是SysEvent.Evt,然后我们试试查找Lab10-02.exe这个进程名字,恶意行为分析本身就很繁琐
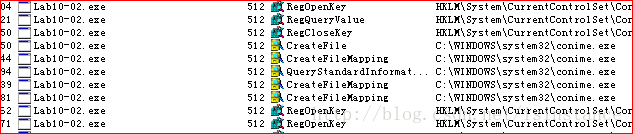
这里我们可以看到Lab10-02.exe这个文件创建了一个文件在C:\WINDOWS\system32\conime.exe,我们继续缩小搜索的范围

这里文件不仅创建了conime.exe,还有apphelp.dll,sysmain.sdb,systest.sdb,最后当然还有那个sys驱动Mlwx486.sys
然后我们搜搜这个conime.exe有没有做过其他操作
这里我们可以看到这个conime.exe的所有操作,包括这个进程的启动,这里我们注意到这个parents pid,放大一点
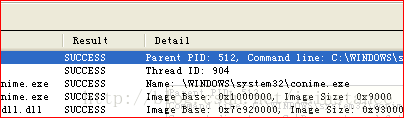
这个512就是Lab10-02.exe的PID
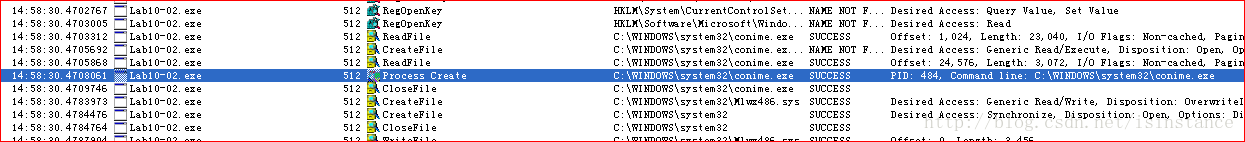
然后这个动态分析大概就只能分析出来这些东西了,书中说,如果你去找那个Mlwx486.sys,你是找不到的,但是我们可以找到这个 conime.exe文件 ==》这是本实验的核心,这个恶意软件的精髓就是隐藏这个Mlwx486.sys文件,如何做到的?就是利用内核的钩子,在系统使用NtQueryDirectoryFile遍历文件的时候,隐藏了Mlwx486.sys!
我们获取一下内核驱动的状态
sc query "486 WS Driver"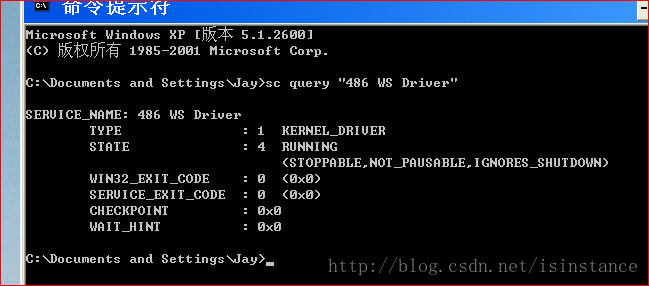
可以很明显的看出来这个是内核的驱动(KERNEL_DRIVER)
作者是如何知道这个内核驱动的名字是486 WS Driver呢?
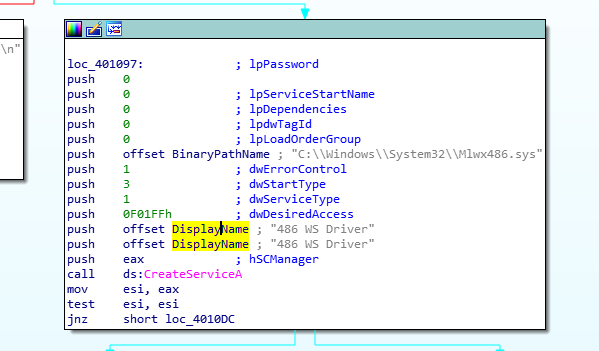
我们可以从注册表中可以找到这个字符串的位置,然后也可以从从CreateServiceA中看出(书中说),不过我无法找到这个CreateServiceA操作
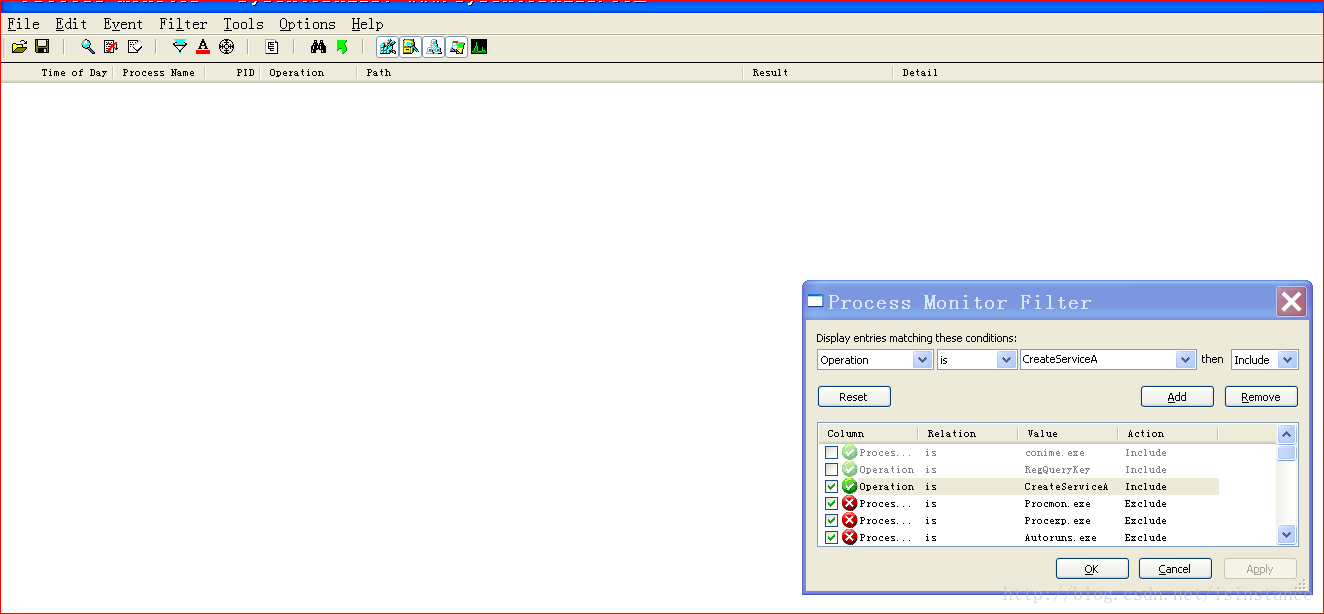

然后还发现这个conime.exe有很多注册表修改失败(BUFFER OVERFLOW)的操作,估计这就是为啥这个conime.exe没有从内核删除自己的原因吧
言归正传,这里我们就会发现这个486 WS Driver是个内核驱动,然后状态是还在运行(RUNNING)
所以这个问题的答案就是创建了conime.exe,还有apphelp.dll,sysmain.sdb,systest.sdb,最后当然还有那个sys驱动Mlwx486.sys
2.这个程序有内核组件吗?
解答: 现在我们就要连接内核调试器来操作了
WinDbg里面运行命令
lm然后仔细找就可以找到这个驱动,这里如果不事先告诉你这个驱动的名字叫Mlwx486还真是难找,不过如果你回想刚刚我们查看创建的文件里面,就有一个Mlwx486.sys
补充windbg分析,依照课本查看ssdt,发现蹊跷:
dd dwo(KeServiceDescriptorTable) L100在这里我们就可以看到这个跳转很多的内存地址b9887486,明显是和其他地址不是一路的!!!
然后书中下一步是要把虚拟机恢复成Rootkit安装之前的状态来查找这个位置上原来的函数是什么,我们在恢复之前可以看看这个地址b9887486上的是什么函数
这个是一个Mlwx486里面自带的函数,然后我们重启,并且恢复虚拟机成未运行病毒状态
然后我们运行
dd dwo(KeServiceDescriptorTable) L100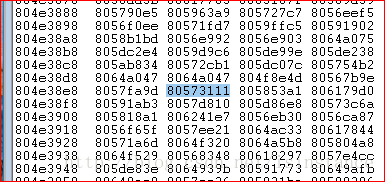
我们找到这个未被改变之前的值,为80573111这个值,我们下一步查查这个函数是什么

这个函数原来的位置是nt!NtQueryDirectoryFile,然后接下来我们运行这个病毒,开始继续分析这个病毒,现在我们已经运行了病毒,找到那个函数的位置!为了搞清楚这个函数在做啥,我们导出资源文件里面的PE,IDA反编译:
==》回头来看,如果我是恶意软件的作者,我会去看NtQueryDirectoryFile的使用,看了msdn,它返回的是链表,因此遍历的过程中,匹配自己的sys恶意文件,删掉我自己的sys文件。应该不难,但是要对windows编程很熟练才行。
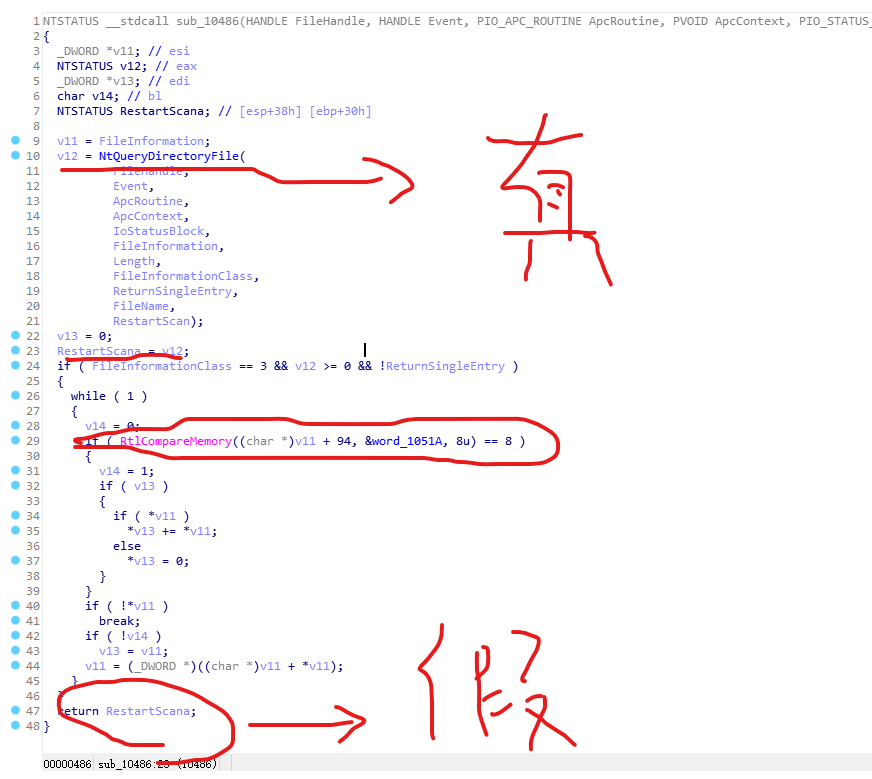
隐藏文件的部分,应该就是那个if部分的代码了。
word_1051A看看是啥?
就是Mlwx,看来是匹配文件是Mlws前缀!不就是 这个嘛!所以逻辑还是很清晰的!就是通过链表删除节点!
这个嘛!所以逻辑还是很清晰的!就是通过链表删除节点!

然后看了下网上的做法,这里面有介绍:本质上就是链表修改节点而已。
https://www.codeproject.com/articles/32744/driver-to-hide-processes-and-files#:~:text=To%20hide%20a%20file%2C%20we%20need%20to%20cut,someone%20calls%20NtQueryDirectoryFile%20%28%29%20function%20in%20the%20system.
这后面是在内核里去调试分析,如何做到。。。比较繁琐。。。汇编的调试太尼玛蛋疼了。。。主要是我的windbg经常卡死。感兴趣的可以看看下面。
我们先设置一个断点在f7a75486这里
bp f7a75486然后
g这时候断点不会马上名字,因为没涉及到查询文件夹的操作,我们回到虚拟机里面,点开我的电脑,断点马上就命中了

然后我就开始单步调试,来查明这个函数到底会做什么操作,函数开头的四句都栈初始化的
mov edi, edi
push ebp
mov ebp, esp
push esi下面继续
mov esi, dword ptr [ebp+1Ch]
push edi
push dword ptr [ebp+30h]
push dword ptr [ebp+2Ch]
push dword ptr [ebp+28h]
push dword ptr [ebp+24h]
push dword ptr [ebp+20h]
push esi
push dword ptr [ebp+18h]
push dword ptr [ebp+14h]
push dword ptr [ebp+10h]
push dword ptr [ebp+0Ch]
push dword ptr [ebp+8]
call Miwx486+0x514(f7a75514)到这里,函数开始调用函数Miwx486+0x514,为了搞清楚这个入参都是什么东西,我们一个一个的分析和调查这个入参,先计算地址的值,然后查看内存地址上的值是多少,比如[ebp=30h]我们可以查到它的值是0,然后可以得出下面的关系
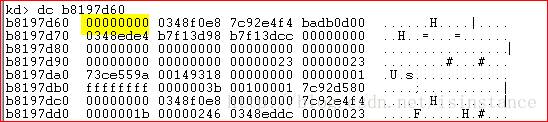
这里要注意的是数据结构的存储和识别,比如上面这图的第二段数据为0348f0e8,地址是b8197d64即(b8197d60 + 4),其实真实是数据在计算机上是这样的(倒着存放的)
b8197d64 e8
b8197d65 f0
b8197d66 48
b8197d67 03知道这点就好办了
mov esi, dword ptr [ebp+1Ch]
push edi = b95a5d64
/* Note: ebp = b95a5d30 */
push dword ptr [ebp+30h] = [b95a5d60] = 0
push dword ptr [ebp+2Ch] = [b95a5d5c] = 80 e1 70
push dword ptr [ebp+28h] = [b95a5d58] = 1
push dword ptr [ebp+24h] = [b95a5d54] = 3
push dword ptr [ebp+20h] = [b95a5d50] = 268
push esi = 0070e198
push dword ptr [ebp+18h] = [b95a5d48] = 68 e1 70
push dword ptr [ebp+14h] = [b95a5d44] = 0
push dword ptr [ebp+10h] = [b95a5d40] = 0
push dword ptr [ebp+0Ch] = [b95a5d3c] = 0
push dword ptr [ebp+8] = [b95a5d38] = 464
call Miwx486+0x514(f7ab7514)然后我们根据这个MSDN的文档,列出NtQueryDirectoryFile的定义
NTSTATUS ZwQueryDirectoryFile(
_In_ HANDLE FileHandle = 464,
_In_opt_ HANDLE Event = 0,
_In_opt_ PIO_APC_ROUTINE ApcRoutine = 0,
_In_opt_ PVOID ApcContext = 0,
_Out_ PIO_STATUS_BLOCK IoStatusBlock = 68 e1 70,
_Out_ PVOID FileInformation = 0070e198,
_In_ ULONG Length = 268,
_In_ FILE_INFORMATION_CLASS FileInformationClass = 3,
_In_ BOOLEAN ReturnSingleEntry = 1,
_In_opt_ PUNICODE_STRING FileName = 80 e1 70,
_In_ BOOLEAN RestartScan = 0
);这里我们注意这个第八个入参FileInformationClass的值为3,然后我们按t来进入这个函数中
t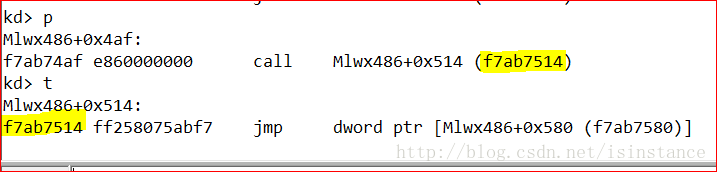
这里我调了一下字体,一进来这个函数的第一个代码就是一个jmp跳转来跳转到其他地方
jmp dword ptr[Mlwx486+0x580 (f7ab7580)]注意这里不是跳转到f7ab7580,而是跳转到保存在地址f7ab7580上那个地址(注意这里是地址,所以不需要倒过来看,如果这里存的是个字符串,就要倒过来看了)
所以下一个代码就会跳转来到这里
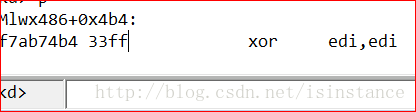
然后这里WinDbg已经将这个函数标注为nt!NtQueryDirectoryFile,就是那个被替换的函数的本身
函数调用完这个nt!NtQueryDirectoryFile之后,因为这个函数是Windows官方的函数,我们分析他没什么意义,我们等待这个函数调用完返回,之后就会跳到这里。。。。pass这些
然后运行到这里内核就退出恶意驱动函数的调用了,因为比较ReturnSIngleEntry这里时候,我们实际值是1,代码的期待值是0
总结一下这个函数,函数的全部代码如下
/* 栈初始化开始 */
mov edi, edi
push ebp
mov ebp, esp
push esi
/* 栈初始化结束 */
mov esi, dword ptr [ebp+1Ch]
push edi
push dword ptr [ebp+30h] // RestartScan
push dword ptr [ebp+2Ch] // FileName
push dword ptr [ebp+28h] // ReturnSingleEntry
push dword ptr [ebp+24h] // FileInformationClass
push dword ptr [ebp+20h] // Length
push esi // FileInformation
push dword ptr [ebp+18h] // IoStatusBlock
push dword ptr [ebp+14h] // ApcContext
push dword ptr [ebp+10h] // PacRoutine
push dword ptr [ebp+0Ch] // Event
push dword ptr [ebp+8] // FileHandle
call Mlwx486+0x514 //-> jmp dword ptr [Mlwx486+0x580 (f7ab2580)] -> nt!NtQueryDirectoryFile
xor edi, edi
cmp dword ptr [ebp+24h], 3 // FileInformationClass = 3
mov dword ptr [ebp+30h], eax // RestartScan, 0
jne Mlwx486+0x505 // if [ebp+24h] != 3 -> jmp and ret 2Ch
test eax, eax // eax is NtQueryDirectoryFile return value(success return 0)
jl Mlwx486+0x505 // if eax < 0 -> jmp and ret 2Ch
cmp byte ptr [ebp+28h], 0 // ReturnSingleEntry = 1
jne Mlwx486+0x505 // if [ebp+28h] != 0 -> jmp and ret 2Ch
push ebx //-> p(f7ab2486)
push 8 // function Mlwx486+0x4ca here
push offset Mlwx486+0x51a //-> 'Mlwx'
lea eax, [esi+5Eh]
push eax
xor bl, bl
call dword ptr [Mlwx486+0x590] // standard windows nt function RtlCompareMemory
cmp eax, 8 // eax = 0
jne Mlwx486+0x4f4
|_ mov eax , dword ptr [esi] // [esi] = 0
test eax, eax
je Mlwx486+0x504 // if eax == 0 -> jmp and ret 2Ch
test bl, bl // bl always equal 0
jne Mlwx486+0x500 // if bl != 0 -> jmp back to 'push 8'
mov edi, esi
add esi, eax
jmp Mlwx486+0x4ca // jmp back to 'push 8'
pop ebx
mov eax, dword ptr [ebp+30h]
pop edi
pop esi
pop ebp
ret 2Ch
inc bl
test edi, edi
je Mlwx486+0x4f4
mov eax, dword ptr [esi]
test eax, eax
jne Mlwx486+0x4f2
and dword ptr [edi], eax
jmp Mlwx486+0x4f4
add dword ptr [edi], eax
mov eax, dword ptr [esi]
test eax, eax
je Mlwx486+0x504
test bl, bl
jne Mlwx486+0x500
mov edi, esi
add esi, eax
jmp Mlwx486+0x4ca
pop ebx
mov eax dword ptr [ebp+30h]
pop edi
pop esi
pop ebp
ret 2Ch书上说,我们刚刚跳转结束那里吗可以设置一个条件断点,当returnSingleEntry为0时候,才会中断,然后我们看看这个断点怎么设置
书上是这样说:
bp f7ab2486 ".if dwo(esp+0x24)==0 {} .else {gc}"这里的f7ab2486为RootKit替换的那个SSDT地址,每次运行都不会相同
然后这里我们用dir命令去查看C:\WINDOWS\system32\,书中介绍了为什么不能用资源管理器的原因
不过这里我一直搞不明白,这里为什么是esp+0x24
这里为了在ReturnSingleEntry=0时候中断,而ReturnSingleEntry的值应该是[ebp+0x28],所以我们这里一般会觉得这个条件中断的语句应该这样写
bp f7ab2486 ".if dwo(ebp+0x28)==0 {} .else {gc}"但是,书上什么写的[esp+24h],为什么是esp+24h,这里我们着重分析一下
首先我们必须要明白,函数在被调用之后,第一步要做的操作就是保存调用着的堆栈信息,就是所谓的函数初始化堆栈,初始化的过程如下(代码截取于上面恶意驱动)
push ebp
mov ebp, esp
push esi如果我们画成栈图的话就是如下
(1). 函数执行到call语句时候的栈分布,原函数的栈分布
--------- <--- ESP(低地址) <- 地址值为esp1
|3| /|\|---------||
|2| | <-数据增长方向(地址递减)|---------||
|1| |--------- <---EBP(高地址) <-地址值为ebp1(2). 函数进入call,之后,开始执行初始化指令(就是上面那三条),初始化完之后的栈分布
--------- <---ESP(依旧指向栈顶)
| esi |
|---------| <---EBP(EBP移动到原来ESP-4的位置)//因为之前执行了pushebp的操作
| ebp1 |
|---------| <---未执行pushebp操作之前ESP指向的位置,执行完push之后esp往上一格
| 3 |
|---------|
| 2 |
|---------|
| 1 |
---------这就是函数调用之前的栈初始化过程,明白这点后面就好解释了
由于我们的断点是设置在外面的大循环,在中断的时候,并未执行栈初始化的过程,现在我们设准备调用函数的旧函数里面的ebp的值为ebp1,esp的值为esp1,执行初始化之后的调用函数l里的ebp值为ebp2,esp值为esp2
由此我们可得如下关系
ebp2 = esp1 - 0x4
esp2 = esp1 - 0x8已知我们在被调用函数里面的ReturnSingleEntry的值为[ebp+28h]
也就是ebp2+28h = esp1-4h+28h=esp1+24h
因为我们断点是在函数调用之前会被命中的,所以我们这里的断点要设置为esp+24h=0
讲了这么多,为什么是esp不是ebp就解释到这里
然后我们输入上面这个语句来设置条件中断,然后我们用dir命令来列出C:\WINDOWS\system32这个文件夹下面的所有文件和文件夹
dir C:\WINDOWS\system32然后就会发现,我们的条件断点被命中了,因为这里我们已经把这个恶意驱动的所有代码都列在了上面,所以这里我们就只列出必要的代码来进行分析
现在我们注意到以下这些代码,存在一个字符串
push offset Mlwa486+0x51a这里压栈的这个值,我们可以查到这个值是Mlwx

然后这段函数是这样的
push ebx // ebx is Mlwx486 function start address
push 8
push offset Mlwx486+0x51a // Mlwx
lea eax, [esi+5Eh]
push eax
xor bl, bl
call dword ptr [Mlwa486+0x590] // RtlCompareMemory然后引用MSDN的定义
SIZE_T RtlCompareMemory(
_In_ const VOID *Source1,
_In_ const VOID *Source2,
_In_ SIZE_T Length
);由图中可知道,eax要和Mlwx这个字符串进行比较,然后这个比较的最大长度为8,这里我在刚刚的调用Mlwx486+0x514时,就分别标注过各个参数在MSDN中的意义和名称,其中esi的值被标注为FileInformation,而且这个值是为3
这里我们就可以确定这个FileInformation的具体意义就是FileBothDirectoryInformation,然后这个值返回的是一个FILE_BOTH_DIR_INFORMATION的结构
关于这里如何知道值为3的意义就是FileBothDirectoryInformation,这个我也不是很清楚,因为MSDN里面并没有很明确的标注了这个值是多少,不过你可以通过bing FileBothDirectoryInformation就可以发现好多代码里面写的都等于3,这个问题已经反馈给了MSDN的维护组,希望能很快得到他们的回复,然后我们再说
(2018/3/5) MSDN的维护者给我发回了反馈,全文的MSDN原文链接如下MSDN原文,然后这是Github上的回复,总结来说就是文档的维护者现在暂时无法提供这个值的文档查询方式,但是他给了我们一个方法在
WinDbg里面查询的方法,这里后面他还说会将这个作为新的功能性在未来加入,原文如下
Hello isinstance
Thank you for the feedback. Unfortunately, at this time we are unable to provide enum values.
You can view the values in the debugger by using the dt command or view them in the header.
Apologize for the inconvenience. We'll definitely consider this as a feature request.
Please let us know if you have any other comments!
Page Writer这里的意思就是我们可以用dt命令来查询他的值,我们试试
kd> dt FileBothDirectoryInformation
*************************************************************************
*** ***
*** ***
*** Either you specified an unqualified symbol, or your debugger ***
*** doesn't have full symbol information. Unqualified symbol ***
*** resolution is turned off by default. Please either specify a ***
*** fully qualified symbol module!symbolname, or enable resolution ***
*** of unqualified symbols by typing ".symopt- 100". Note that ***
*** enabling unqualified symbol resolution with network symbol ***
*** server shares in the symbol path may cause the debugger to ***
*** appear to hang for long periods of time when an incorrect ***
*** symbol name is typed or the network symbol server is down. ***
*** ***
*** For some commands to work properly, your symbol path ***
*** must point to .pdb files that have full type information. ***
*** ***
*** Certain .pdb files (such as the public OS symbols) do not ***
*** contain the required information. Contact the group that ***
*** provided you with these symbols if you need this command to ***
*** work. ***
*** ***
*** Type referenced: FileBothDirectoryInformation ***
*** ***
*************************************************************************
Symbol FileBothDirectoryInformation not found.还是依旧无法查找到这个结构体,看来我们只能在header里面找寻这个变量了,但是不知道Windows这样的闭源操作系统会不会开放他的header出来,所以这里是根据书上和各种道听途说的搜索知道了这个对应的是FileBothDirectoryInformation,但是如果下次变成了2的话就不知道怎么对应。。。
我们可以观察一下这个结构的定义
typedef struct _FILE_BOTH_DIR_INFORMATION {
ULONG NextEntryOffset;
ULONG FileIndex;
LARGE_INTEGER CreationTime;
LARGE_INTEGER LastAccessTime;
LARGE_INTEGER LastWriteTime;
LARGE_INTEGER ChangeTime;
LARGE_INTEGER EndOfFile;
LARGE_INTEGER AllocationSize;
ULONG FileAttributes;
ULONG FileNameLength;
ULONG EaSize;
CCHAR ShortNameLength;
WCHAR ShortName[12];
WCHAR FileName[1];
} FILE_BOTH_DIR_INFORMATION, *PFILE_BOTH_DIR_INFORMATION;反正就是不论如何,现在我们确定了这个结构体是FILE_BOTH_DIR_INFORMATION,然后这个结构体的定义就是上面这个定义的
所以根据我们上面分析的,esi是FileInformation这个东西,然后这个东西是函数返回的一个结构体,这个结构体现在确定是FILE_BOTH_DIR_INFORMATION
所以在代码
lea eax,[esi+5Eh]此处,我们可以找到这个esi+5Eh这个地方为WCHAR FileName[1]这个地方,分析过程如下
首先我们确定各个数据类型所占的字节数,因为我们这个运行的虚拟机是32位的,所以可以得出如下结论
ULONG = 8 byte
LARGE_INTEGER = 8 byte
CCHAR = 1 byte
WCHAR = 2 byte这里我们要记住这个定理
原则1:数据成员对齐规则:结构(struct或联合union)的数据成员,第一个数据成员放在offset为0的地方,以后每个数据成员存储的起始位置要从该成员大小的整数倍开始(比如int在32位机为4字节,则要从4的整数倍地址开始存储)。
原则2:结构体作为成员:如果一个结构里有某些结构体成员,则结构体成员要从其内部最大元素大小的整数倍地址开始存储。(struct a里存有struct b,b里有char,int,double等元素,那b应该从8的整数倍开始存储。)
原则3:收尾工作:结构体的总大小,也就是sizeof的结果,必须是其内部最大成员的整数倍,不足的要补齐。
重点是第一点和第三点,结构会存在对齐的特性,具体原理就不解释了。
然后我们看,根据结构体定义,可以得出下面这样地址递增列表:
typedef struct _FILE_BOTH_DIR_INFORMATION { START - END
ULONG NextEntryOffset; 8 byte(32 bit) addr = esi+0x00 - esi+0x07
ULONG FileIndex; 8 byte(32 bit) esi+0x08 - esi+0x0f
LARGE_INTEGER CreationTime; 8 byte(64 bit) esi+0x10 - esi+0x17
LARGE_INTEGER LastAccessTime; 8 byte(64 bit) 0x18 - 0x1f
LARGE_INTEGER LastWriteTime; 8 byte(64 bit) 0x20 - 0x27
LARGE_INTEGER ChangeTime; 8 byte(64 bit) 0x28 - 0x2f
LARGE_INTEGER EndOfFile; 8 byte(64 bit) 0x30 - 0x37
LARGE_INTEGER AllocationSize; 8 byte(64 bit) 0x38 - 0x3f
ULONG FileAttributes; 8 byte(64 bit) 0x40 - 0x47
ULONG FileNameLength; 8 byte(64 bit) 0x48 - 0x4f
ULONG EaSize; 8 byte(64 bit) 0x50 - 0x57
CCHAR ShortNameLength; 1 byte(8 bit) (4 byte) 0x58 - 0x5b
WCHAR ShortName[12]; 2 byte(16 bit) 2*12=0x18 0x5c - 0x5d
WCHAR FileName[1]; 2 byte(16 bit) 0x5e - 0x5f
} FILE_BOTH_DIR_INFORMATION, *PFILE_BOTH_DIR_INFORMATION;然后我们再把5Eh比较一下,就可以得出这个esi+5eh就是FileName这个结构元素的起始地址,然后我们继续往下
push 8 // length
push offset Mlwx486+0x51a // Mlwx
lea eax, [esi+5Eh]
push eax // filename
xor bl, bl
call dword ptr [Mlwx486+0x590] // RtlCompareMemory到这时,就可以确定,这个函数的入参的具体值是什么
SIZE_T RtlCompareMemory(
_In_ const VOID *Source1,
_In_ const VOID *Source2,
_In_ SIZE_T Length
);再根据MSDN关于RtlCompareMemory的定义,我们可以知道,这个函数在比较Mlwx和dir列出来的各个filename,这个函数的意义在于,比较的是第一个入参和第二个入参,如果想的就返回了Length的值,如果不同就返回相同的字节数。
RtlCompareMemory returns the number of bytes in the two blocks that match. If all bytes match up to the specified Length value, the Length value is returned.
我们现在就去看看这个地址上的FileName具体是什么值了,使用db来查看
db esi+5eh这里可以看出,FileName参数是在C:\WINDOWS\system32下的各个文件的名字,这里我们抓到的是aaaamon.dll,结果可能会不同,但是不影响我们的继续分析
这里的操作是将C:\WINDOWS\system32下的各个文件名和Mlwx比较,比较完之后会执行下面的操作
cmp eax, 8
jne Mlwx486+0x4f4这里比较返回值和8的大小,一般来说,这个返回值是不会等于8的,除非你遇到Mlwx486.sys
如果返回值不等于8之后,程序就会跳到Mlwx486+0x4f4这个地方,这个地方的代码如下:
mov eax, dword ptr [esi]
test eax, eax
je Mlwx486+0x500 // if eax == 0 -> jump and return 2Ch
test bl, bl // bl always equal 0
jne Mlwx486+0x500 // if bl != 0 -> jump back to push '8'
mov edi, esi
add esi, eax
jmp Mlwx486+0x4ca // jump back to 'push 8'
pop ebx
pop esi
pop ebp
ret 2Ch上面的代码一般正常情况下,就会返回2Ch之后就退出函数了,逻辑上来说就是,如果每次传入的FileName和Mlwx不相等,函数直接就退出
然后我们继续往下
现在我们分析它是如何修改NtQueryDirectoryFile的返回值然后隐藏Mlwx486.sys文件的,我们可以查一下NtQueryDirectoryFile的文档,然后就可以知道,NtQueryDirectoryFile的返回值FILE_BOTH_DIR_INFORMATION结构是由一系列FILE_BOTH_DIR_INFORMATION结构串联而成的,如下图
---------------------------
| FILE_BOTH_DIR_INFORMATION | ---
--------------------------- |
--- | FILE_BOTH_DIR_INFORMATION | <--
| ---------------------------
--> | FILE_BOTH_DIR_INFORMATION |
---------------------------通常来说,第一个结构体是指向第二个结构体的,然后第二个结构体指向第三个结构体,这样依次下去
知道这些我们下面就可以来分析接下来的代码了,如果我们RtlCompareMemory返回值是8的话,就会执行以下这些代码
inc bl // bl now is equal 0 by [xor bl, bl]
test edi, edi
je Mlwx486+0x4f4 // if edi == 0, jump here -------------------
mov eax, dword ptr [esi] // esi -> FileInformation structure |
test eax, eax |
jne Mlwx486+0x4f2 // if eax !=0, jump here ----------------- |
and dword ptr [edi], eax // | |
jmp Mlwx486+0x4f4 // jump here -----------------------------|->|
add dword ptr [edi], eax // <-------------------------------------- |
mov eax, dword ptr [esi] // <-----------------------------------------
test eax, eax
je Mlwx486+0x504 // return 2Ch
test bl, bl
jne Mlwx486+0x500 // if bl != 0, jump here ------
mov edi, esi |
add esi, eax // <---------------------------
// esi now point to the next FILE_BOTH_DIR_INFORMATION structure
jmp Mlwx486+0x4ca // jump back to push'8'
pop ebx
mov eax dword ptr [ebp+30h]
pop edi
pop esi
pop ebp
ret 2Ch这个函数的大致操作就是如上所示,注意那出现了两次的那个指令你就明白它把指针往后移动了以为,抹除了Mlwx486.sys文件的FILE_BOTH_DIR_INFORMATION结构,之后就达到了隐藏文件的目的
mov eax, dword ptr[esi]如果你还是有点不理解他是怎么操作的,可以看如下的解释
加强版解释,执行第一次
mov eax, dword ptr[esi]的时候,eax成为了指向Mlwx486.sys的信息结构FILE_BOTH_DIR_INFORMATION的指针,这个结构体就是上面我推算内存地址时候那个结构体,现在eax指向了它
我们假设这个值不是空,然后就会跳到这里执行
add dword ptr [edi], eax假设在执行这句之前,edi=0015fbe0,而eax的值是00000078,一个add操作之后,就会对存储在0015fbe0地址上的数据加上00000078(其实这个0015fbe0存储的数据就是eax的值)
而根据我们推导的FILE_BOTH_DIR_INFORMATION结构的内存地址分布,可以看出esi这个值其实就是FILE_BOTH_DIR_INFORMATION结构内元素NextEntryOffset的起始地址,也就是修改[esi]这个值其实修改的是结构体FILE_BOTH_DIR_INFORMATION内的元素NextEntryOffset的值
而我们根据MSDN对NextEntryOffset的定义,NextEntryOffset指向的是下一个FILE_BOTH_DIR_INFORMATION的地址,也就是将指向第二个结构体的指针往后偏移了好几个结构体
NextEntryOffset
Byte offset of the next FILE_BOTH_DIR_INFORMATION entry, if multiple entries are present in a buffer. This member is zero if no other entries follow this one.
这个病毒对隐藏自生这里处理的比较充满,他是直接将NextEntryOffset的值乘以2(相同值相加等于这个值乘以2)
typedef struct _FILE_BOTH_DIR_INFORMATION { START - END
ULONG NextEntryOffset; 8 byte(32 bit) addr = esi+0x00 - esi+0x07
ULONG FileIndex; 8 byte(32 bit) esi+0x08 - esi+0x0f
LARGE_INTEGER CreationTime; 8 byte(64 bit) esi+0x10 - esi+0x17
LARGE_INTEGER LastAccessTime; 8 byte(64 bit) 0x18 - 0x1f
LARGE_INTEGER LastWriteTime; 8 byte(64 bit) 0x20 - 0x27
LARGE_INTEGER ChangeTime; 8 byte(64 bit) 0x28 - 0x2f
LARGE_INTEGER EndOfFile; 8 byte(64 bit) 0x30 - 0x37
LARGE_INTEGER AllocationSize; 8 byte(64 bit) 0x38 - 0x3f
ULONG FileAttributes; 8 byte(64 bit) 0x40 - 0x47
ULONG FileNameLength; 8 byte(64 bit) 0x48 - 0x4f
ULONG EaSize; 8 byte(64 bit) 0x50 - 0x57
CCHAR ShortNameLength; 1 byte(8 bit) (4 byte) 0x58 - 0x5b
WCHAR ShortName[12]; 2 byte(16 bit) 2*12=0x18 0x5c - 0x5d
WCHAR FileName[1]; 2 byte(16 bit) 0x5e - 0x5f
} FILE_BOTH_DIR_INFORMATION, *PFILE_BOTH_DIR_INFORMATION;这个操作就是如下所示这样,假设第一个结构体的偏移量为00000060,因为结构体长度为0x60
---------------------------
00000000 | FILE_BOTH_DIR_INFORMATION | - | NextEntryOffset = 00000000 |
---------------------------
00000060 | FILE_BOTH_DIR_INFORMATION | - | NextEntryOffset = 00000060 |
---------------------------
000000c0 | FILE_BOTH_DIR_INFORMATION | - | NextEntryOffset = 000000c0 |
---------------------------
00000120 | FILE_BOTH_DIR_INFORMATION | - | NextEntryOffset = 00000120 |
--------------------------- 我们假设恶意驱动在NtQueryDirectoryFile返回的第三个结构体里面发现了文件名字和Mlwx匹配,之后通过赋值语句
mov eax, dword ptr[esi]获得了Mlwx486.sys这个文件的FILE_BOTH_DIR_INFORMATION结构里面的NextEntryOffset的值,然后将这个这个偏移值乘以2
注:
这里的
NextEntryOffset不是地址,是地址的偏移值(offset),也就是基地址加上偏移值等于真实地址的那个偏移值真实地址 = 基地址 + 偏移地址
然后继续刚刚那个假设,程序在第三个结构体发现Mlwx之后,通过
add dword ptr [edi], eax偏移值NextEntryOffset的值变成了00000180(c0*2)
然后计算机通过上面那个公式计算真实地址
本来第三个结构体的地址是000000c0,但是经过这么一个通过改变offset之后,计算机计算之后,得出的地址就变成00000180(根据上面那个计算公式)
计算机通过计算之后,认为第三个结构体存在00000180这个地址上,就去00000180上取数据,从而跳过了第三个结构体,所以这个通过改变offset在不改变数据结构的前提之下,达到了隐藏文件的目的,也只会有天才才会想的出来了
然后分析基本就到这里
第二问的答案就是这个程序拥有一个内核模块,存储在程序的资源节上,执行的时候释放sys文件,然后这个sys文件就会加载到内核中执行
3.这个程序做了些什么?
解答:通过上面的分析,可以得出,这是用来隐藏文件的RootKit,它使用SSDT来挂钩覆盖NtQueryDirectoryFile函数,通过自定义一些操作,来隐藏文件
我们可以把被隐藏的sys文件导出来看看,书中给我们提供了三种方法来导出这个被隐藏的文件:
1. 禁用驱动的服务
2. 从安装的资源节提取出这个文件
3. 访问文件的目录,用cp命令将文件重命名后显示
我们这里先试试第一种,也是推荐的方法,这里需要重启
我们先用cmd来查询这个服务在运行了没有
然后我们输入命令
sc stop "486 WS Driver"服务无法被控制,那么没办法,再试试第二个
点这个然后保存到桌面上,用IDA来打开就行了
我们试试第三种方法
成功了,然后我们打开看看,这就是这个文件打开的样子
我们进入DriverEntry这个例程
这里就不详细分析这个代码了,书上说是RtlInitUnicodeString以参数KeServiceDescirptorTable和NtQueryDircetoryFile做入参,然后用MmGetSystemRoutineAddress这个函数来查找这个两个地址的偏移量,接下来他把地址做了一个替换



 浙公网安备 33010602011771号
浙公网安备 33010602011771号