nc这个工具用于伪造c2服务器 做c2初始连接的抓包分析实在是太tm好用了!必要时候配合APATEDNS
DNS Spoofing with APATEDNS
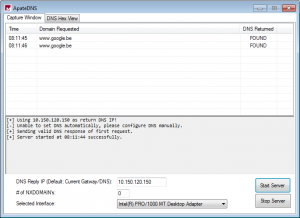
If you quickly want to find out what the malware in your sandbox is resolving, you can use ApateDNS. This free tool will listen for outgoing DNS requests and is able to spoof the answer.
 In my example I started the ApateDNS tool in my sandbox and set the DNS reply IP to my secondary machine -10.150.120.150.
In my example I started the ApateDNS tool in my sandbox and set the DNS reply IP to my secondary machine -10.150.120.150.
I captured a DNS request to “www.google.be” and its DNS response address
was spoofed to 10.150.120.150. This way the malware will start its
connection pointed to this IP address -10.150.120.150.
 Next I’ll set up the “TCP/IP Swiss army knife” – netcat.
Next I’ll set up the “TCP/IP Swiss army knife” – netcat.
On my secondary machine, the one with IP 10.150.120.150, I started a netcat listener on port 80. ==》场景:你发现某个恶意软件在链接c2服务器的80端口,则你使用如下方式伪造一个c2!
~ $ sudo nc -l 80If the malware then opens an HTTP connection to “www.google.be”, I will receive its HTTP requests.
example:
GET / HTTP/1.1
Accept: */*
Accept-Language: nl-be
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Accept-Encoding: gzip, deflate
Host: www.google.be
Connection: Keep-Alive
Cookie: PREF=ID=815......:
This might be fast way to find out what connections your malware is trying to make.
(netcat is also available for windows)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号