chm里的无文件攻击和检测思路
chm是Compiled HTML Help file的缩写,意为已编译的HTML帮助文件,当攻击者将恶意代码写入chm中,当用户点击就会执行预设的恶意命令。
chm命令执行示例
下载安装html help workshop,下载地址:https://www.helpandmanual.com/download/htmlhelp.exe
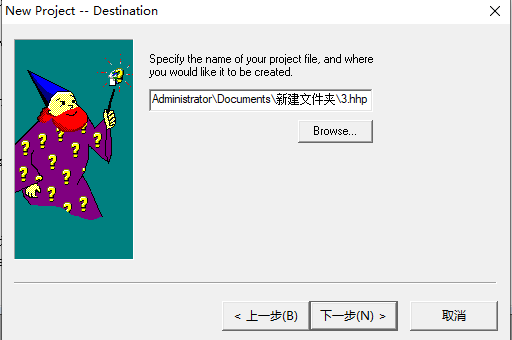
使用html help workshop创建新项目,选择一个.hhp文件为目标
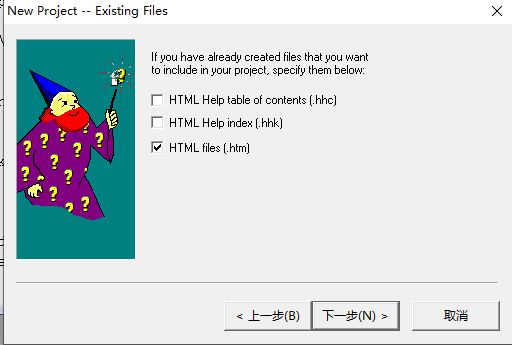
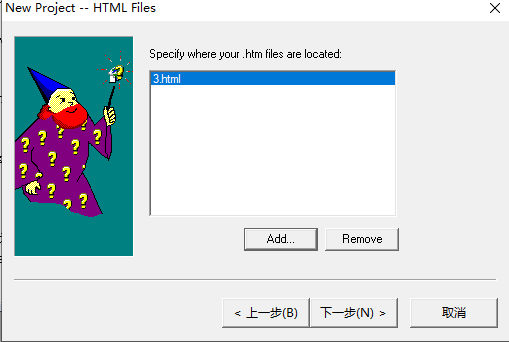
创建并添加恶意html文件(执行calc),内容如下
1
|
|
选择file-compile编译得到chm文件
运行chm文件,成功打开计算器(将calc换成木马即可运行恶意程序).
sysmon采集的数据如下:
Process Create:
RuleName: -
UtcTime: 2022-04-27 08:11:10.799
ProcessGuid: {d418462b-fa9e-6268-b00a-000000000a00}
ProcessId: 3648
Image: C:\Windows\hh.exe
FileVersion: 10.0.19041.1 (WinBuild.160101.0800)
Description: Microsoft® HTML Help Executable
Product: HTML Help
Company: Microsoft Corporation
OriginalFileName: HH.exe
CommandLine: "C:\Windows\hh.exe" C:\Users\bonel\Desktop\test3.chm
CurrentDirectory: C:\Users\bonel\Desktop\
User: DESKTOP-CIBNM6P\bonel
LogonGuid: {d418462b-b8ad-6268-818c-030000000000}
LogonId: 0x38C81
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=2C8FE78D53C8CA27523A71DFD2938241,SHA256=EB63FD45ED7EC773ECCAF0F20D44BC9B4ED0A3E01779D62321B1DA954A0F6EB8,IMPHASH=D3D9C3E81A404E7F5C5302429636F04C
ParentProcessGuid: {d418462b-b8b5-6268-3f00-000000000a00}
ParentProcessId: 1960
ParentImage: C:\Windows\explorer.exe
ParentCommandLine: C:\Windows\Explorer.EXE
ParentUser: DESKTOP-CIBNM6P\bonel
==》这个是双击打开上述chm文件的结果。
Process Create:
RuleName: -
UtcTime: 2022-04-27 08:11:11.597
ProcessGuid: {d418462b-fa9f-6268-b10a-000000000a00}
ProcessId: 6848
Image: C:\Windows\System32\calc.exe
FileVersion: 10.0.19041.1 (WinBuild.160101.0800)
Description: Windows Calculator
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: CALC.EXE
CommandLine: "C:\Windows\System32\calc.exe"
CurrentDirectory: C:\Users\bonel\Desktop\
User: DESKTOP-CIBNM6P\bonel
LogonGuid: {d418462b-b8ad-6268-818c-030000000000}
LogonId: 0x38C81
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=5DA8C98136D98DFEC4716EDD79C7145F,SHA256=58189CBD4E6DC0C7D8E66B6A6F75652FC9F4AFC7CE0EBA7D67D8C3FEB0D5381F,IMPHASH=8EEAA9499666119D13B3F44ECD77A729
ParentProcessGuid: {d418462b-fa9e-6268-b00a-000000000a00}
ParentProcessId: 3648
ParentImage: C:\Windows\hh.exe
ParentCommandLine: "C:\Windows\hh.exe" C:\Users\bonel\Desktop\test3.chm
ParentUser: DESKTOP-CIBNM6P\bonel
==》这个是打开chm后开启calc。exe的。可以看到其父进程是hh.exe说明在chm里启动了可疑进程!



 浙公网安备 33010602011771号
浙公网安备 33010602011771号