#harbor使用自签名证书部署、为什么要用san模式签发呢?
原因:因为新版的containerd 使用go写的 harbor使用containerd就需要san模式签发的证书。
实验环境
安装harbor步骤
1.安装docker
2.配置docker-compose
3.下载安装包
-rw-r--r--. 1 root root 76724391 Feb 25 13:03 docker-20.10.17-binary-install.tar.gz
-rw-r--r--. 1 root root 25907200 Feb 25 13:04 docker-compose-linux-x86_64
-rw-r--r--. 1 root root 605477475 Feb 25 13:04 harbor-offline-installer-v2.3.2.tgz
实验环境:
1台CentOS7.6.1810
harbor.magedu.net
Docker:20.10.17
docker-compose:
harbor:v2.3.2
一、Docker安装部署、Harbor配置
#配置docker服务
#配置docker-compose
[root@harbor2 harbor]# chmod a+x docker-compose-linux-x86_64 && mv docker-compose-linux-x86_64 /usr/bin/docker-compose
mv: overwrite ‘/usr/bin/docker-compose’? y
[root@harbor2 harbor]# docker --version
Docker version 20.10.17, build 100c701
#下载安装harbor离线包
tar xvf harbor-offline-installer-v2.3.2.tgz
#修改配置文件
cd harbor
cp harbor.yml.tmpl harbor.yml
修改如下五项参数
hostname: harbor的名称可以使用IP或域名,推荐域名可以实现https
certificate: 添加公钥,需要按照官方方式进行签发证书
private_key: 添加私钥
data_volume: 定义存储路径(建议一个单独分区作为存储路径)
harbor_admin_password: 修改harbor登录密码
#示例
hostname: harbor.magedu.net
http:
port: 8080
https:
port: 443
certificate: /root/Docker-Harbor/harbor/certs/magedu.net.crt
private_key: /root/Docker-Harbor/harbor/certs/magedu.net.key
harbor_admin_password: Harbor12345
database:
password: root123
max_idle_conns: 100
max_open_conns: 900
data_volume: /data
![]()
二、配置证书
参考官方文档:https://goharbor.io/docs/2.4.0/install-config/configure-https/
默认情况下,Harbor不附带证书。可以在没有安全性的情况下部署Harbor,这样您就可以通过HTTP连接到它。然而,只有在没有连接到外部互联网的测试或开发环境中,使用HTTP才是可接受的。在没有空隙的环境中使用HTTP会使您面临中间人攻击。在生产环境中,请始终使用HTTPS。如果您启用公证内容信任来正确签署所有图像,您必须使用HTTPS
要配置HTTPS,您必须创建SSL证书。您可以使用由受信任的第三方CA签名的证书,也可以使用自签名证书。本节描述如何使用OpenSSL创建CA,以及如何使用CA签署服务器证书和客户端证书。您可以使用其他CA提供商,例如Let's Encrypt
生成证书颁发机构证书
在生产环境中,您应该从CA获得证书。在测试或开发环境中,您可以生成自己的CA。要生成CA证书,请运行以下命令。
1.生成CA证书私钥
openssl genrsa -out ca.key 4096
touch /root/.rnd #记录签发信息 提前进行创建
2.生成CA证书
#Template
#openssl req -x509 -new -nodes -sha512 -days 3650 \
# -subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=yourdomain.com" \
# -key ca.key \
# -out ca.crt
#实验
openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=magedu.com" \
-key ca.key \
-out ca.crt
![]()
生成服务器证书
证书通常包含一个. crt文件和一个. key文件,例如yourdomain.com.crt和yourdomain.com.key
1.生成私钥
#openssl genrsa -out yourdomain.com.key 4096
openssl genrsa -out magedu.net.key 4096
2.生成证书签名请求(CSR)
#openssl req -sha512 -new \
# -subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=yourdomain.com" \
# -key yourdomain.com.key \
# -out yourdomain.com.csr
openssl req -sha512 -new \
-subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=magedu.net" \
-key magedu.net.key \
-out magedu.net.csr
3.生成x509 v3扩展文件
无论您是使用FQDN还是IP地址连接到您的Harbor主机,您都必须创建此文件,以便您可以为您的Harbor主机生成符合主题备用名称(SAN)和x509 v3扩展要求的证书。替换DNS条目以反映您的域
#cat > v3.ext <<-EOF
#authorityKeyIdentifier=keyid,issuer
#basicConstraints=CA:FALSE
#keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
#extendedKeyUsage = serverAuth
#subjectAltName = @alt_names
#[alt_names]
#DNS.1=yourdomain.com
#DNS.2=yourdomain
#DNS.3=hostname
#EOF
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=magedu.com
DNS.2=harbor.magedu.net
DNS.3=harbor.magedu.local
DNS.4=harborsync.magedu.net
EOF
4.使用v3.ext文件为您的Harbor主机生成证书。 用harbor主机名替换CRS和CRT文件名中的yourdomain.com
#openssl x509 -req -sha512 -days 3650 \
# -extfile v3.ext \
# -CA ca.crt -CAkey ca.key -CAcreateserial \
# -in yourdomain.com.csr \
# -out yourdomain.com.cr
openssl x509 -req -sha512 -days 3650 \
-extfile v3.ext \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in magedu.net.csr \
-out magedu.net.crt
-CA ca.crt -CAkey ca.key表示CA直接签发,指定magedu.net.csr这个文件,
签发完后是magedu.net.crt文件;并会加载v3.ext这个文件,v3.ext文件的
信息会被签发到magedu.net.crt文件信息证书里
我们harbor用的就是这个magedu.net.crt和magedu.net.key文件
![]()
![]()
5.将crt文件转换为cert客户端证书文件
#docker程序认为"*.crt"文件是CA证书文件,"*.cert"客户端证书文件,于是上面第五步需要转换一下,其实使用cp一下也是可以的,内容并没有变化。
[root@harbornew certs]# openssl x509 -inform PEM -in magedu.net.crt -out magedu.net.cert
6.证书整理一下 方便后续维护
[root@harbornew certs]# ll
total 32
drwxr-xr-x 5 root root 44 Jul 12 14:59 all
-rw-r--r-- 1 root root 2025 Jul 12 14:33 ca.crt
-rw-r--r-- 1 root root 3243 Jul 12 14:33 ca.key
-rw-r--r-- 1 root root 17 Jul 12 14:34 ca.srl
-rw-r--r-- 1 root root 2143 Jul 12 14:55 magedu.net.cert
-rw-r--r-- 1 root root 2143 Jul 12 14:34 magedu.net.crt
-rw-r--r-- 1 root root 1704 Jul 12 14:34 magedu.net.csr
-rw-r--r-- 1 root root 3247 Jul 12 14:33 magedu.net.key
-rw-r--r-- 1 root root 307 Jul 12 14:34 v3.ext
[root@harbornew certs]# ll all/
total 0
drwxr-xr-x 2 root root 48 Jul 12 14:58 CA
drwxr-xr-x 2 root root 65 Jul 12 14:59 Client
drwxr-xr-x 2 root root 95 Jul 12 14:59 Server
[root@harbornew certs]# ll all/CA/
total 12
-rw-r--r-- 1 root root 2025 Jul 12 14:58 ca.crt
-rw-r--r-- 1 root root 3243 Jul 12 14:58 ca.key
-rw-r--r-- 1 root root 17 Jul 12 14:58 ca.srl
[root@harbornew certs]# ll all/Client/
total 12
-rw-r--r-- 1 root root 2025 Jul 12 14:59 ca.crt
-rw-r--r-- 1 root root 2143 Jul 12 14:59 magedu.net.cert
-rw-r--r-- 1 root root 3247 Jul 12 14:59 magedu.net.key
[root@harbornew certs]# ll all/Server/
total 16
-rw-r--r-- 1 root root 2143 Jul 12 14:59 magedu.net.cert
-rw-r--r-- 1 root root 2143 Jul 12 14:59 magedu.net.crt
-rw-r--r-- 1 root root 1704 Jul 12 14:59 magedu.net.csr
-rw-r--r-- 1 root root 3247 Jul 12 14:59 magedu.net.key
三、配置harbor.yml HTTPS 证书
# http related config
#http:
# port for http, default is 80. If https enabled, this port will redirect to https port
#port: 80
# https related config
https:
# https port for harbor, default is 443
port: 443
# The path of cert and key files for nginx
certificate: /root/Docker-Harbor/harbor/certs/magedu.net.crt
private_key: /root/Docker-Harbor/harbor/certs/magedu.net.key
四、 运行harbor
./install.sh --with-trivy --with-chartmuseum
[root@harbornew harbor]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
2a6df79cb54b goharbor/harbor-jobservice:v2.3.2 "/harbor/entrypoint.…" About an hour ago Up About an hour (healthy) harbor-jobservice
d576de509508 goharbor/nginx-photon:v2.3.2 "nginx -g 'daemon of…" About an hour ago Up About an hour (healthy) 0.0.0.0:80->8080/tcp, 0.0.0.0:443->8443/tcp nginx
67ce130130fc goharbor/harbor-core:v2.3.2 "/harbor/entrypoint.…" About an hour ago Up About an hour (healthy) harbor-core
610264585f6e goharbor/trivy-adapter-photon:v2.3.2 "/home/scanner/entry…" About an hour ago Up About an hour (healthy) trivy-adapter
1cd26fcfcdae goharbor/harbor-registryctl:v2.3.2 "/home/harbor/start.…" About an hour ago Up About an hour (healthy) registryctl
c90e18c90602 goharbor/registry-photon:v2.3.2 "/home/harbor/entryp…" About an hour ago Up About an hour (healthy) registry
e8029f065c42 goharbor/chartmuseum-photon:v2.3.2 "./docker-entrypoint…" About an hour ago Up About an hour (healthy) chartmuseum
e07dde86f80a goharbor/harbor-portal:v2.3.2 "nginx -g 'daemon of…" About an hour ago Up About an hour (healthy) harbor-portal
10aa3de5d6a6 goharbor/redis-photon:v2.3.2 "redis-server /etc/r…" About an hour ago Up About an hour (healthy) redis
c340e69b0e15 goharbor/harbor-db:v2.3.2 "/docker-entrypoint.…" About an hour ago Up About an hour (healthy) harbor-db
67ea32b72fbd goharbor/harbor-log:v2.3.2 "/bin/sh -c /usr/loc…" About an hour ago Up About an hour (healthy) 127.0.0.1:1514->10514/tcp harbor-log
docker-compose up -d
docker-compose down -v
五、访问私有化镜像仓库
运行时为:docker
#Harbor 本地服务器 配置hosts
[root@harbornew harbor]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.40.148 harbor.magedu.net
#配置仓库
[root@harbornew harbor]# cat /etc/docker/daemon.json
{
"insecure-registries": ["harbor.magedu.net"]
}
#配置客户端证书才能登陆访问
#创建一个目录为 仓库域名并且把 Client证书复制进去
[root@harbornew all]# mkdir /etc/docker/certs.d/harbor.magedu.net -p
[root@harbornew all]# cd Client/
[root@harbornew Client]# ll
total 12
-rw-r--r-- 1 root root 2025 Jul 12 14:59 ca.crt
-rw-r--r-- 1 root root 2143 Jul 12 14:59 magedu.net.cert
-rw-r--r-- 1 root root 3247 Jul 12 14:59 magedu.net.key
[root@harbornew Client]# cp * /etc/docker/certs.d/harbor.magedu.net
#重启服务
[root@harbornew harbor]# systemctl damon-reload
[root@harbornew harbor]# systemctl restart docker
#login 输入账户密码
[root@harbornew harbor]# docker login harbor.magedu.net
Authenticating with existing credentials...
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
运行时为:containerd
#配置hosts文件
[root@xianchaonode1 harbor.magedu.net]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.40.180 xianchaomaster1
192.168.40.181 xianchaonode1
192.168.40.148 harbor.magedu.net
#创建 和 仓库域名一样的文件夹 存放证书
[root@xianchaonode1 harbor.magedu.net]# mkdir /etc/containerd/certs.d/harbor.magedu.net -p
#将Harbor服务上的 Client文件复制到远程客户端服务器上
[root@harbornew Client]# scp /root/Docker-Harbor/harbor/certs/all/Client/* 192.168.40.181:/etc/containerd/certs.d/harbor.magedu.net/
#containerd 服务器上 存放CLient证书
[root@xianchaonode1 harbor.magedu.net]# pwd
/etc/containerd/certs.d/harbor.magedu.net
[root@xianchaonode1 harbor.magedu.net]# ll
total 12
-rw-r--r-- 1 root root 2025 Jul 12 15:21 ca.crt
-rw-r--r-- 1 root root 2143 Jul 12 15:21 magedu.net.cert
-rw-r--r-- 1 root root 3247 Jul 12 15:21 magedu.net.key
#配置文件修改
#这里跳过认证 不用证书校验insecure_skip_verify = true
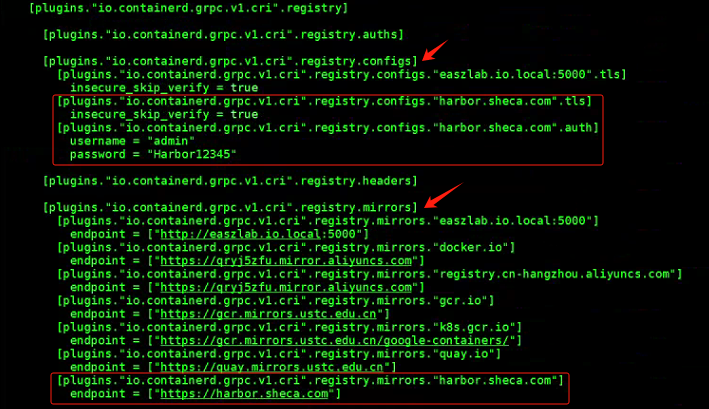
[root@xianchaonode1 harbor.magedu.net]# vim /etc/containerd/config.toml
[plugins."io.containerd.grpc.v1.cri".registry]
config_path = ""
[plugins."io.containerd.grpc.v1.cri".registry.mirrors]
[plugins."io.containerd.grpc.v1.cri".registry.mirrors."harbor.magedu.net"]
endpoint = ["https://harbor.magedu.net"]
[plugins."io.containerd.grpc.v1.cri".registry.configs]
[plugins."io.containerd.grpc.v1.cri".registry.configs."harbor.magedu.net".tls]
insecure_skip_verify = true
#ca_file = "/etc/containerd/certs.d/harbor.magedu.net/ca.crt"
#cert_file = "/etc/containerd/certs.d/harbor.magedu.net/magedu.net.cert"
#key_file = "/etc/containerd/certs.d/harbor.magedu.net/magedu.net.key"
[plugins."io.containerd.grpc.v1.cri".registry.configs."harbor.magedu.net".auth]
username = "admin"
password = "Harbor12345"
#重启服务
[root@xianchaonode1 harbor.magedu.net]# systemctl daemon-reload
[root@xianchaonode1 harbor.magedu.net]# systemctl restart containerd
#测试拉取镜像
#提前做好域名解析
[root@xianchaonode1 harbor.magedu.net]# crictl pull harbor.magedu.net/birkhoffxia/nginx:latest
W0712 16:51:43.784983 100760 util_unix.go:103] Using "/run/containerd/containerd.sock" as endpoint is deprecated, please consider using full url format "unix:///run/containerd/containerd.sock".
Image is up to date for sha256:3f8a00f137a0d2c8a2163a09901e28e2471999fde4efc2f9570b91f1c30acf94
#nerdctl push 镜像需要注意 如果不使用tls 先登录一下输入密码默认Harbor12345
nerdctl login -u admin --insecure-registry https://harbor.sheca.com
#添加--insecure-registry 才可以push镜像
nerdctl push --insecure-registry harbor.sheca.com/baseimages/logstash:v7.12.1-json-file-log-v1
![]()





 浙公网安备 33010602011771号
浙公网安备 33010602011771号