X3ctf 比赛 Write Up
X3ctf Write Up
1. Misc
p11n-trophy(签到题):
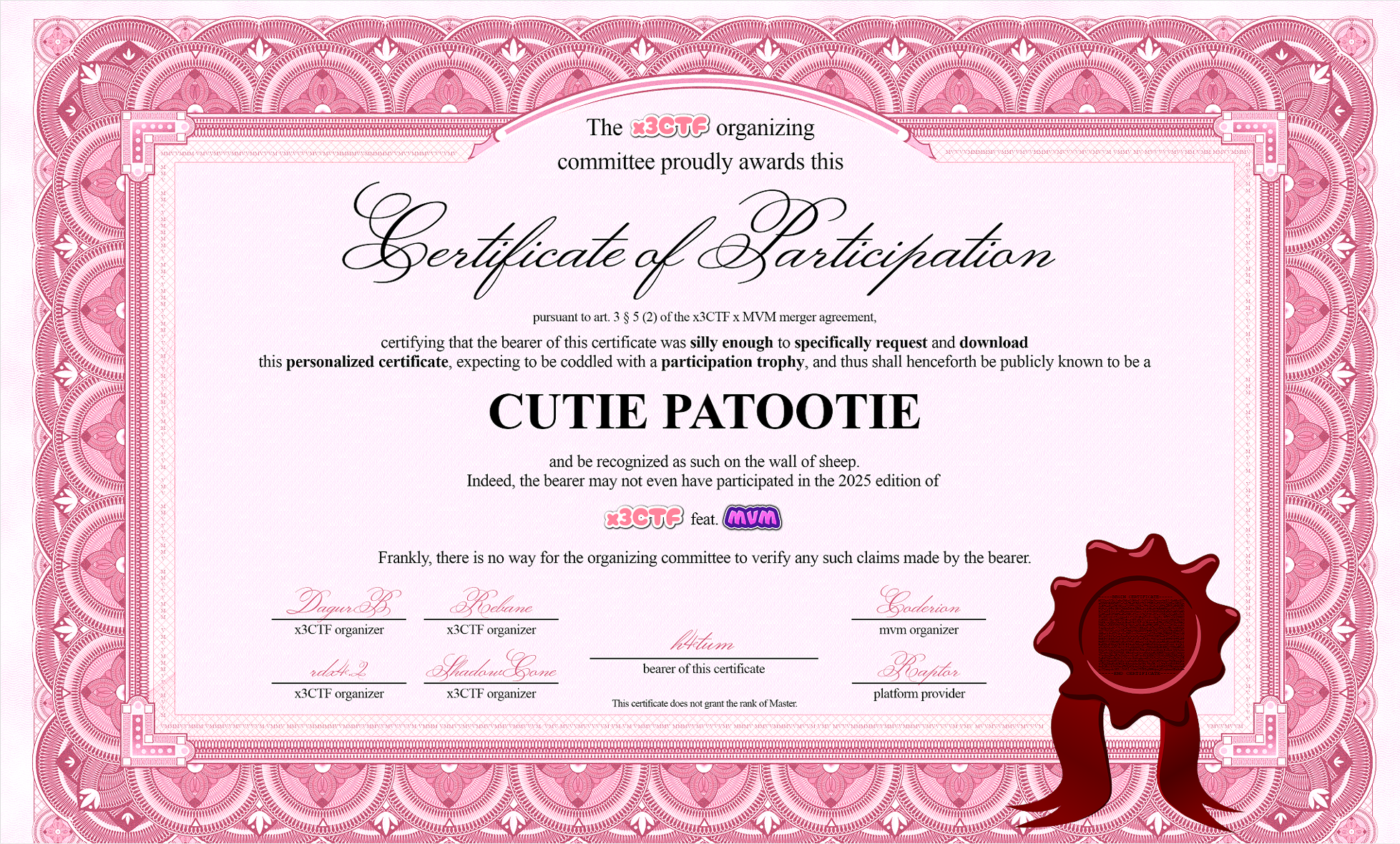
我们首先会得到这样一份证书:
第一题签到题的答案就是证书下面正中间的“This certificate does not grant the rank of Master"。
trophy-plus + trophy-plus64:
这两道目描述一模一样
其中一个flag是藏在certificate周围一圈的位置:
人工将这些内容识别,再翻译成二进制然后解码就会得到flag
另外一个flag则是藏在右下角的勋章里:

人工将这些内容识别出来然后用base64进行解码即可。
内容大概为:
会有一些误差,所以最后提交flag时需要多试几次。
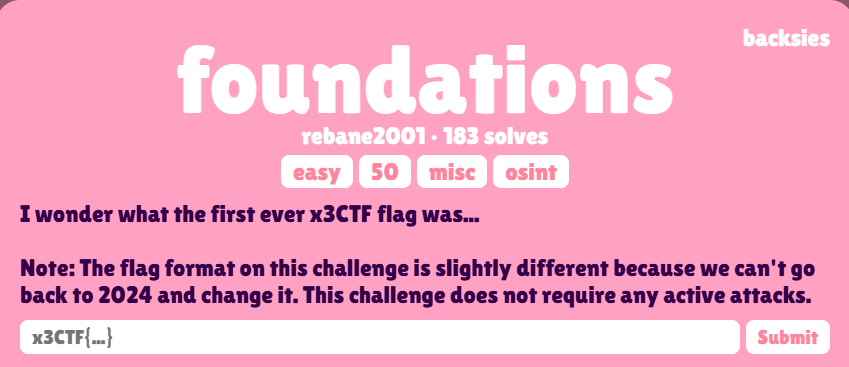
foundations (Osint):
题目描述:
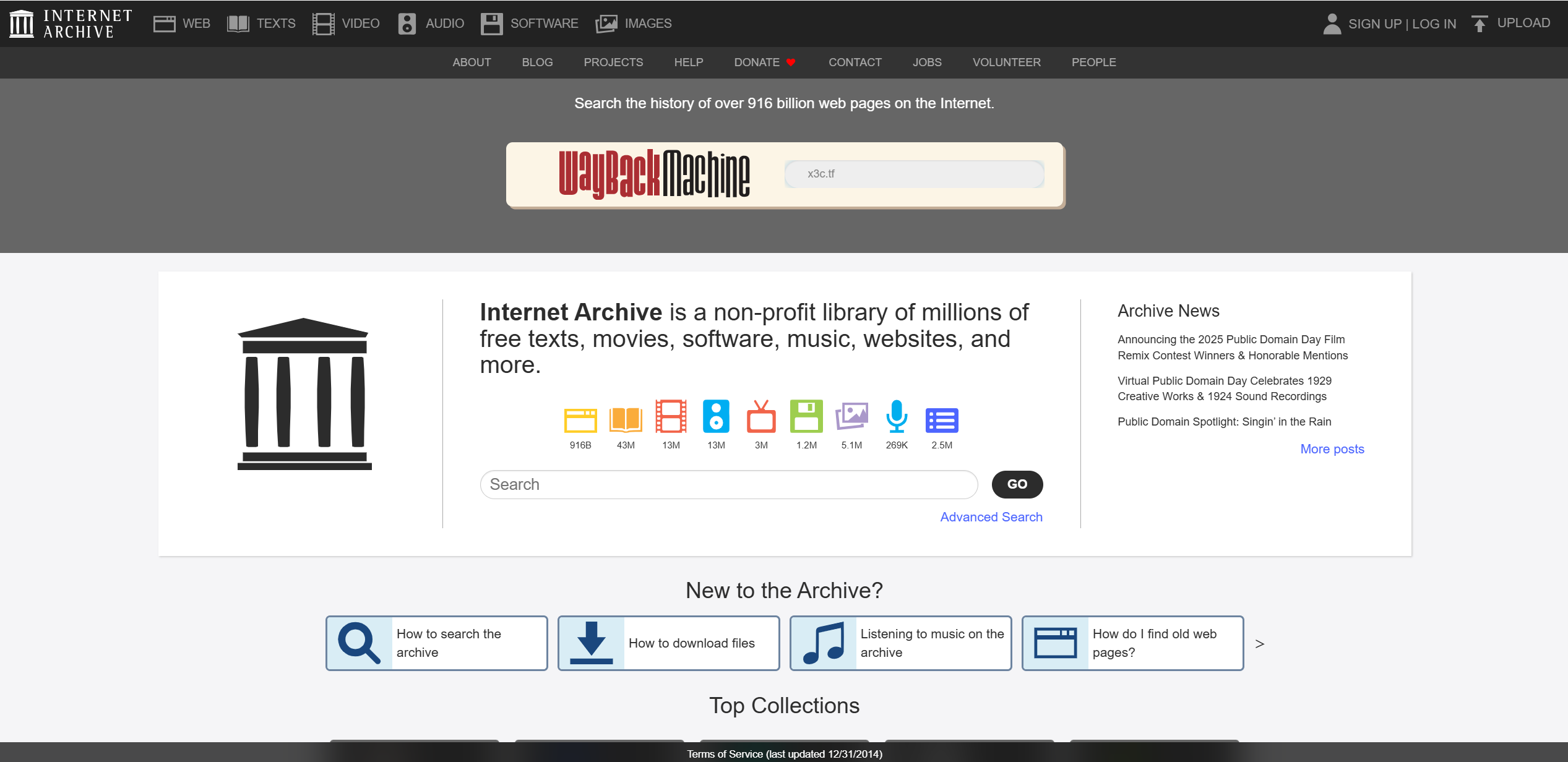
使用https://archive.org/来搜索这个比赛网站的历史纪录内容
可以在这里发现最早的纪录是在2024年7月14日:
x3CTF{m4yb3_w3ll_m4ke_4_ch4ll3nge_0u7_0f_7h1s}
mvm:
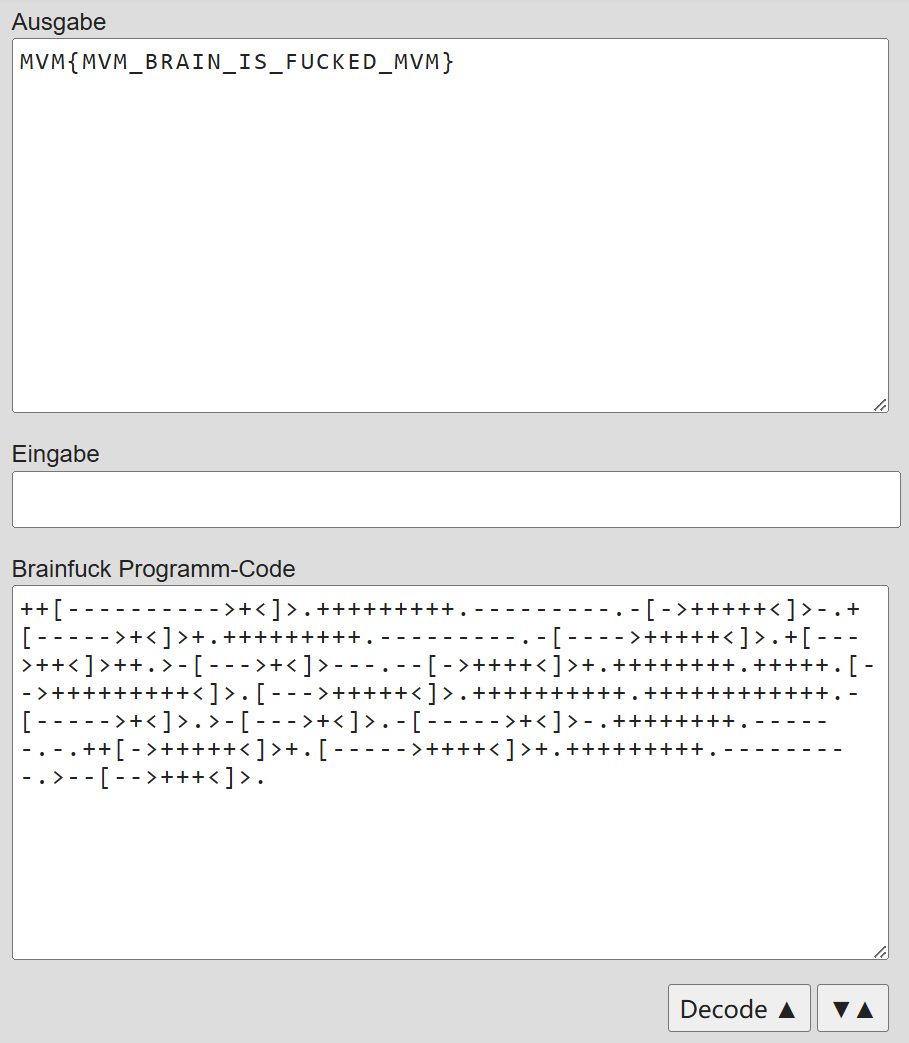
打开下载文件会得到
跟之前一样,将其转成二进制再解码会得到
很显然这是Brainfuck,所以找个在线的intepreter运行一下就可以得到flag:
MVM{MVM_BRAIN_IS_FUCKED_MVM}
2. Crypto
man-vs-matrix:
题目描述:
打开下载文件会看到:
是几个随机数的生成器(RNG),但生成逻辑非常简单。
每次会计算
(括号外的乘法是内积。在sage里,矩阵与矩阵/向量的乘法和向量与向量的内积都是用*)。并且有
这里的初始state是已知的,所以我们只需要建立一个9元1次线性方程组即可。
我们可以写一段sagemath的代码来通过解方程逆推出matrix以及flag内容:
__EOF__

本文链接:https://www.cnblogs.com/bimohuixinghe/p/18695017.html
关于博主:评论和私信会在第一时间回复。或者直接私信我。
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
声援博主:如果您觉得文章对您有帮助,可以点击文章右下角【推荐】一下。您的鼓励是博主的最大动力!










【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 单线程的Redis速度为什么快?
· 展开说说关于C#中ORM框架的用法!
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· Pantheons:用 TypeScript 打造主流大模型对话的一站式集成库
· SQL Server 2025 AI相关能力初探