watcher 告警邮件的body中添加相关告警字段值
-
目的
- 通过引用变量的方式,在watcher 邮件通知中添加触发警告的相关信息,以便收到邮件后能快速定位问题。
-
示例
-
环境:CentOS Linux release 7.7.1908 (Core)、[Elasticsearch Watcher 2.4]、[Elasticsearch Reference 7.6]、[Kibana Guide 7.6]
-
以auditbeat 登录审计为例,演示引用变量的方法
-
登录kibana,使用Dev Tools控制台搜索"login"审计记录
GET auditbeat-7.6.2-2020.06.16-000002/_search?pretty { "query": { "match": {"event.dataset": "login" } } }- 执行返回的结果如下:
{ "took" : 11, "timed_out" : false, "_shards" : { "total" : 1, "successful" : 1, "skipped" : 0, "failed" : 0 }, "hits" : { "total" : { "value" : 147, #=> 搜索到147条匹配记录 "relation" : "eq" }, "max_score" : 4.7221236, "hits" : [ #=> 此为hits.hits列表 { #=> 这里是hits.hits列表的第0位元素开始位置 "_index" : "auditbeat-7.6.2-2020.06.16-000002", "_type" : "_doc", "_id" : "35Dnv3IBAriavZt1-aOf", "_score" : 4.7221236, "_source" : { #=> "_source" 包含了匹配记录的源信息, #=> 其在hits.hits列表的0位元素里 "@timestamp" : "2020-06-17T01:32:24.965Z", "source" : { #=> _source里的字典类型字段,可通过.操作符获取 "ip" : "192.168.0.62" }, "service" : { #=> _source字段 "type" : "system" }, "user" : { #=> _source字段 "terminal" : "pts/0", "name" : "root", "id" : 0 }, "ecs" : { "version" : "1.4.0" }, "event" : { #=> _source字段 "action" : "user_login", "origin" : "/var/log/wtmp", "category" : "authentication", "outcome" : "success", "type" : "authentication_success", "module" : "system", "dataset" : "login", "kind" : "event" }, "message" : "Login by user root (UID: 0) on pts/0 (PID: 20728) from 192.168.0.62 (IP: 192.168.0.62)", #=> _source字段 "process" : { "pid" : 20728 }, "host" : { #=> _source字段 "os" : { "codename" : "Core", "platform" : "centos", "version" : "7 (Core)", "family" : "redhat", "name" : "CentOS Linux", "kernel" : "3.10.0-1062.18.1.el7.x86_64" }, "id" : "7623ac2580824c6c8d35ead472e38f61", "containerized" : false, "hostname" : "php-srv3", "architecture" : "x86_64", "name" : "php-srv3" }, "agent" : { #=> _source字段 "hostname" : "php-srv3", "id" : "539e4abc-52f3-494b-8bd7-aabd420fceb8", "version" : "7.6.2", "type" : "auditbeat", "ephemeral_id" : "95cb20b1-8bd9-4f97-810d-d81aa8da6d74" } } }, #=> ...[略]...-
在watcher action中,email body使用变量的方法
-
如果要调用所有匹配的信息,则使用:ctx.payload.hits
-
如果要获取自己想要的信息,可以通过对"_source"的相关字段进行过滤,并获取其值
-
由于
_source在hits.hits.0里,所以调用方式为:ctx.payload.hits.hits.0._source -
_source中的message:ctx.payload.hits.hits.0._source.message -
_source中agent的hostname:ctx.payload.hits.hits.0._source.agent.hostname -
_source中source的ip:ctx.payload.hits.hits.0._source.source.ip
-
-
-
watcher Json 的完整配置信息
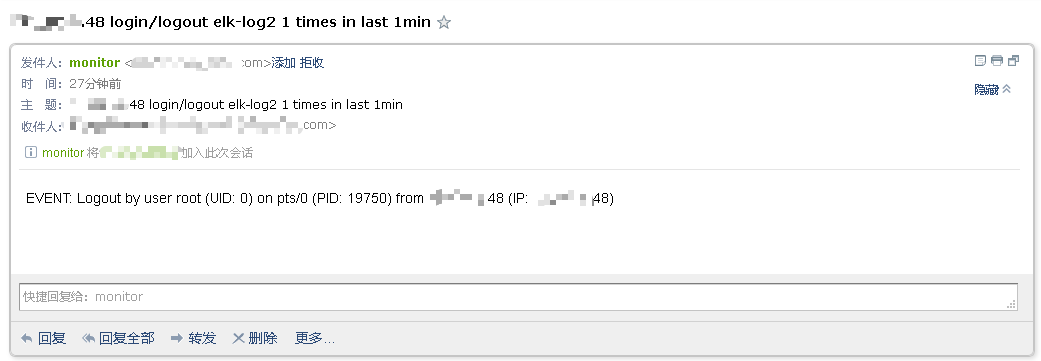
{ "trigger": { "schedule": { "interval": "1m" } # 触发检测频率,每分钟执行一次 }, "input": { # 输入文件 "search": { "request": { "search_type": "query_then_fetch", "indices": [ # 索引,支持通配符 "auditbeat-*" ], "rest_total_hits_as_int": true, "body": { "_source": { # 对body中的_source字段进行筛选 "includes": [ # 包含以下字段 "event", "message", "host", "user", "source" ] # , excludes [...] 排除某些字段 }, "query": { "bool": { "must": [ { "match": { "event.dataset": "login" # 搜索匹配值 } }, { "range": { "@timestamp": { # @当前时间2分钟内 "gte": "now-2m", "lte": "now" } } } ] } } } } } }, "condition": { "compare": { "ctx.payload.hits.total": { "gte": 1 # 有1次或1次以上匹配成功,则触发actions动作 } } }, "actions": { "send_email": { "email": { "profile": "standard", "to": [ "receiver@email.domain" ], # 邮件标题和body都使用变量获取相关信息 "subject": "{{ctx.payload.hits.hits.0._source.source.ip}} login/logout {{ctx.payload.hits.hits.0._source.host.name}} {{ctx.payload.hits.total}} times in last 1min", "body": { "text": "{{ctx.metadata.msg}}{{ctx.payload.hits.hits.0._source.message}}" } } } }, "metadata": { "msg": "EVENT: " } }- 收到的邮件效果(这只是简单的文本显示,如果需要更加酷炫的效果,可以把邮件模板设置html格式):
![]()
-
*** 你必须十分努力,才能看起来毫不费力 ***



 浙公网安备 33010602011771号
浙公网安备 33010602011771号