K8S系列(二)——安装k8s-dashboard图形化集群管理界面
上篇文章我们已经安装好了K8S集群,但是只能通过kubectl控制操作集群,不是很方便,所以这次我们来研究下怎么安装k8s-dashboard图形化界面来管理集群
步骤大致如下:
1.部署dashboard
2.创建登陆用户
3.暴露dashboard服务
4.生成用户Token用于登陆
5.浏览器访问k8s-dashboard并验证
具体操作记录
一、部署dashboard
#下载yaml文件
wget https://raw.githubusercontent.com/cby-chen/Kubernetes/main/yaml/dashboard.yaml
#部署dashboard
kubectl apply -f dashboard.yaml存在问题:我的wget命令无法正常下载,只能先通过浏览器访问该链接并复制文本到dashboard.yaml文件。原文件直接部署会出现kubernetes-dashboard的状态为CrashLoopBackOff,看日志报10.96.0.1:443: i/o timeout错误
解决方法:修改dashboard.yaml文件,在191和277行前插入nodeName: k8s-master,这里的k8s-master是我master的主机名,用以指定dashboard只在master节点上运行。以下是我修改好的dashboard.yaml文件,可直接用。为什么是191和277行前,因为我们要修改的是Deployment的templates
dashboard.yaml文件内容,可点击查看
# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
apiVersion: v1
kind: Namespace
metadata:
name: kubernetes-dashboard
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kubernetes-dashboard
type: Opaque
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-csrf
namespace: kubernetes-dashboard
type: Opaque
data:
csrf: ""
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-key-holder
namespace: kubernetes-dashboard
type: Opaque
---
kind: ConfigMap
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-settings
namespace: kubernetes-dashboard
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
rules:
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster", "dashboard-metrics-scraper"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]
verbs: ["get"]
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
rules:
# Allow Metrics Scraper to get metrics from the Metrics server
- apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
securityContext:
seccompProfile:
type: RuntimeDefault
nodeName: k8s-master
containers:
- name: kubernetes-dashboard
image: registry.cn-hangzhou.aliyuncs.com/google_containers/dashboard:v2.6.1
imagePullPolicy: Always
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
ports:
- port: 8000
targetPort: 8000
selector:
k8s-app: dashboard-metrics-scraper
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: dashboard-metrics-scraper
template:
metadata:
labels:
k8s-app: dashboard-metrics-scraper
spec:
securityContext:
seccompProfile:
type: RuntimeDefault
nodeName: k8s-master
containers:
- name: dashboard-metrics-scraper
image: registry.cn-hangzhou.aliyuncs.com/google_containers/metrics-scraper:v1.0.8
ports:
- containerPort: 8000
protocol: TCP
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 8000
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:
- mountPath: /tmp
name: tmp-volume
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
volumes:
- name: tmp-volume
emptyDir: {}二、创建登陆用户
#下载yaml文件
wget https://raw.githubusercontent.com/cby-chen/Kubernetes/main/yaml/dashboard-user.yaml
#开始部署
kubectl apply -f dashboard-user.yaml为避免链接失效,这里附上yaml文件内容,可点击查看
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard三、暴露dashboard服务
目前部署好的dashboard服务只能内部访问,如果我们要在物理主机浏览器访问dashboard,则还需要暴露服务出来
#通过kubectl edit直接编辑kubernetes-dashboard服务
kubectl edit svc kubernetes-dashboard -n kubernetes-dashboard回车后会进入类似vim模式,在ports:后插入一行- nodePort: 32000(端口可自定义,用于外部访问),把port: 443前的-去掉,把type值改为NodePort,最后esc键:wq退出,pod会自动更新
这是我修改后的文件内容,可点击查看
# Please edit the object below. Lines beginning with a '#' will be ignored,
# and an empty file will abort the edit. If an error occurs while saving this file will be
# reopened with the relevant failures.
#
apiVersion: v1
kind: Service
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"v1","kind":"Service","metadata":{"annotations":{},"labels":{"k8s-app":"kubernetes-dashboard"},"name":"kubernetes-dashboard","namespace":"kubernetes-dashboard"},"spec":{"ports":[{"port":443,"targetPort":8443}],"selector":{"k8s-app":"kubernetes-dashboard"}}}
creationTimestamp: "2022-09-22T08:09:28Z"
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
resourceVersion: "73886"
uid: 0d468fb5-0e48-42a7-9d48-008b6f3bec23
spec:
clusterIP: 10.98.115.155
clusterIPs:
- 10.98.115.155
externalTrafficPolicy: Cluster
internalTrafficPolicy: Cluster
ipFamilies:
- IPv4
ipFamilyPolicy: SingleStack
ports:
- nodePort: 32000
port: 443
protocol: TCP
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
sessionAffinity: None
type: NodePort
status:
loadBalancer: {}现在我们可以检查下服务是否暴露成功。type为NodePort,port也有暴露我们配置的32000端口,说明服务已经暴露出去了
[root@k8s-master ~]# kubectl get svc kubernetes-dashboard -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes-dashboard NodePort 10.98.115.155 <none> 443:32000/TCP 23m
[root@k8s-master ~]# netstat -tlnp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:2379 0.0.0.0:* LISTEN 1738/etcd
tcp 0 0 127.0.0.1:2381 0.0.0.0:* LISTEN 1738/etcd
tcp 0 0 127.0.0.1:39089 0.0.0.0:* LISTEN 1036/containerd
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1028/sshd
tcp 0 0 127.0.0.1:10257 0.0.0.0:* LISTEN 1677/kube-controlle
tcp 0 0 127.0.0.1:10259 0.0.0.0:* LISTEN 1718/kube-scheduler
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1116/master
tcp 0 0 127.0.0.1:10249 0.0.0.0:* LISTEN 1875/kube-proxy
tcp 0 0 127.0.0.1:10248 0.0.0.0:* LISTEN 1033/kubelet
tcp 0 0 192.168.179.133:2379 0.0.0.0:* LISTEN 1738/etcd
tcp 0 0 192.168.179.133:2380 0.0.0.0:* LISTEN 1738/etcd
tcp6 0 0 ::1:25 :::* LISTEN 1116/master
tcp6 0 0 :::6443 :::* LISTEN 1675/kube-apiserver
tcp6 0 0 :::10256 :::* LISTEN 1875/kube-proxy
tcp6 0 0 :::22 :::* LISTEN 1028/sshd
tcp6 0 0 :::10250 :::* LISTEN 1033/kubelet
[root@k8s-master ~]#四、生成用户Token用于登陆
#生成用户Token。返回内容可直接复制到浏览器进行登录
kubectl -n kubernetes-dashboard create token admin-user输出内容如下,可点击查看
[root@k8s-master ~]# kubectl -n kubernetes-dashboard create token admin-user
eyJhbGciOiJSUzI1NiIsImtpZCI6IlZtRmJhdFV2QUZsTE5zbmt5SHo0bTQtOW9tSVprSzMzZzd2dVUyTWRQRncifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiXSwiZXhwIjoxNjYzODM5MjI2LCJpYXQiOjE2NjM4MzU2MjYsImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsInNlcnZpY2VhY2NvdW50Ijp7Im5hbWUiOiJhZG1pbi11c2VyIiwidWlkIjoiNmJiMmRmMDEtMDcxMy00YTZmLWI2OTQtYmUzNjUxYzA5ZWEzIn19LCJuYmYiOjE2NjM4MzU2MjYsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDphZG1pbi11c2VyIn0.XOsM-oT8wFhHpzPqi31oJZ-Gfcw_OijBZEdiDhoJyPFV5Br0mU12x6u3ANE38HtDt-W6Ak-tYf_bSfzxdbsmc3y1sppzuTHQBu3MsfXdTRcFFzlhb6xc2sCqW4eDtbZ9yfM_UfWrbufCPoF7FurQSoJEJu0grAY4eMIl-xA1D5LdYkNKTxBugPxxwM1ZfNCXRNdS0hg0FzZhkj9HBZxQDVNr4Ov4sIn8NMpyUXstlnDdB8r_84Uynd3QtJmr4iLx4bTxD4uzsUauQBjRgMj7xuLqsguuboZ2qL24ZJQWQYr0B80K_eOr9kE3XotmYybgaG66XD6Ss8FdVrp2QSJiGA
[root@k8s-master ~]#五、浏览器访问k8s-dashboard并验证
现在我们可以从物理主机上访问dashboard服务
访问链接为https://192.168.179.133:32000/ 其中133使我master节点ip,32000是我定义的暴露端口,注意需要协议是https
下面是访问界面,选择Token登陆方式,同时把Token复制进去进行登录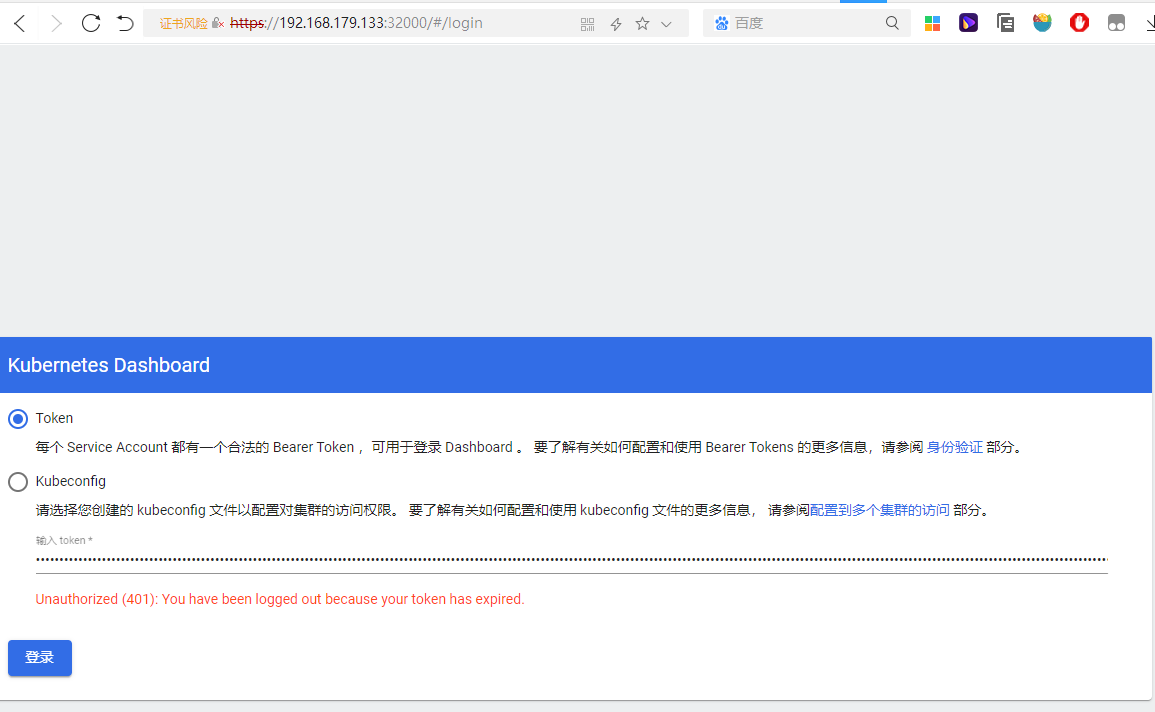
登录后界面
关于Token过期问题
默认Token过15分钟后就会过期,需要重新生成。我们可以配置更长的过期时间,或者直接配置永不过期。配置步骤如下。
#获取配置信息并重定向至文件
kubectl get deploy kubernetes-dashboard -o yaml -n kubernetes-dashboard > 88.yaml
#编辑vi 88.yaml,在- --auto-generate-certificates和- --namespace=kubernetes-dashboard后面新增一行- --token-ttl=0
vi 88.yaml
#更新pod
kubectl apply -f 88.yaml还可以通过dashboard里去做修改,具体可参考https://blog.csdn.net/weixin_37665711/article/details/119254622
如果Token已经过期,则需要重新执行以下命令重新生成
kubectl -n kubernetes-dashboard create token admin-user
参考链接:
https://zhuanlan.zhihu.com/p/515652838
https://computingforgeeks.com/how-to-install-kubernetes-dashboard-with-nodeport/
https://www.icode9.com/content-4-1337294.html





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· AI 智能体引爆开源社区「GitHub 热点速览」
· C#/.NET/.NET Core技术前沿周刊 | 第 29 期(2025年3.1-3.9)
· 从HTTP原因短语缺失研究HTTP/2和HTTP/3的设计差异