CVE-2020-0674 IE远程代码执行漏洞
0x00 漏洞描述
该漏洞影响组件为jscript.dll,该动态链接库是微软Internet Explorer浏览器的Javascript引擎之一,其中IE8及以下使用jscript.dll,IE9及以上默认使用jscript9.dll,但网页可以通过《script》标签指定在IE8兼容性模式下加载jscript.dll,因此IE9、IE10、IE11都受到此漏洞影响。
从操作系统范围来看,本漏洞影响范围横跨Windows 7至Windows 10中所有的个人操作系统和服务器操作系统。
该漏洞是一个Use-After-Free漏洞,攻击样本使用UAF达成类型混淆,进而获取全局内存读写能力并绕过ASLR等漏洞利用缓解技术,并从指定ip地址请求下一步攻击载荷,最终达到远程代码执行。
0x01 影响版本
| 产品 | 平台 |
|---|---|
| Internet Explorer 10 | Windows Server 2012 |
| Internet Explorer 11 | Windows 10 Version 1803 for 32-bit Systems |
| Internet Explorer 11 | Windows 10 Version 1803 for x64-based Systems |
| Internet Explorer 11 | Windows 10 Version 1803 for ARM64-based Systems |
| Internet Explorer 11 | Windows 10 Version 1809 for 32-bit Systems |
| Internet Explorer 11 | Windows 10 Version 1809 for x64-based Systems |
| Internet Explorer 11 | Windows 10 Version 1809 for ARM64-based Systems |
| Internet Explorer 11 | Windows Server 2019 |
| Internet Explorer 11 | Windows 10 Version 1909 for 32-bit Systems |
| Internet Explorer 11 | Windows 10 Version 1909 for x64-based Systems |
| Internet Explorer 11 | Windows 10 Version 1909 for ARM64-based Systems |
| Internet Explorer 11 | Windows 10 Version 1709 for 32-bit Systems |
| Internet Explorer 11 | Windows 10 Version 1709 for x64-based Systems |
| Internet Explorer 11 | Windows 10 Version 1709 for ARM64-based Systems |
| Internet Explorer 11 | Windows 10 Version 1903 for 32-bit Systems |
| Internet Explorer 11 | Windows 10 Version 1903 for x64-based Systems |
| Internet Explorer 11 | Windows 10 Version 1903 for ARM64-based Systems |
| Internet Explorer 11 | Windows 10 for 32-bit Systems |
| Internet Explorer 11 | Windows 10 for x64-based Systems |
| Internet Explorer 11 | Windows 10 Version 1607 for 32-bit Systems |
| Internet Explorer 11 | Windows 10 Version 1607 for x64-based Systems |
| Internet Explorer 11 | Windows Server 2016 |
| Internet Explorer 11 | Windows 7 for 32-bit Systems Service Pack 1 |
| Internet Explorer 11 | Windows 7 for x64-based Systems Service Pack 1 |
| Internet Explorer 11 | Windows 8.1 for 32-bit systems |
| Internet Explorer 11 | Windows 8.1 for x64-based systems |
| Internet Explorer 11 | Windows RT 8.1 |
| Internet Explorer 11 | Windows Server 2008 R2 for x64-based Systems Service Pack 1 |
| Internet Explorer 11 | Windows Server 2012 |
| Internet Explorer 11 | Windows Server 2012 R2 |
| Internet Explorer 9 | Windows Server 2008 for 32-bit Systems Service Pack 2 |
| Internet Explorer 9 | Windows Server 2008 for x64-based Systems Service Pack 2 |
0x02 漏洞复现
IE版本:11.900.18362.0
python:python 3.8
操作系统:windows 10 专业工作站版
0x03 编写脚本
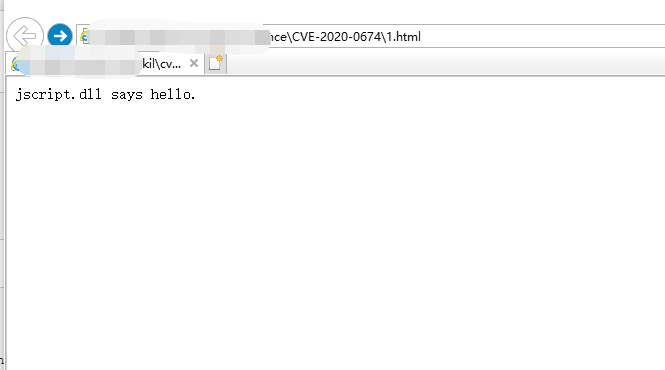
1.编写html CVE-2020-0674.html
<head>
<meta http-equiv="X-UA-Compatible" content="IE=11"></meta>
<script language="Jscript.Encode">
document.write("jscript.dll says hello.");</script>
2.编写py脚本 CVE-2020-0674.py
from selenium import webdriver
ieDriver = "C:\Program Files (x86)\Internet Explorer\IEDriverServer.exe"
browser = webdriver.Ie(ieDriver)
browser.get('file:///D:\My_hacker_tool kil\cve-jiance\CVE-2020-0674\cve-2020-0674.html') '''这里路径是存放html的路径'''
0x04 复现成功
0x05 修复意见
32位系统
takeown /f %windir%\system32\jscript.dll cacls %windir%\system32\jscript.dll /E /P everyone:N
64位系统
takeown /f %windir%\syswow64\jscript.dll cacls %windir%\syswow64\jscript.dll /E /P everyone:N takeown /f %windir%\system32\jscript.dll cacls %windir%\system32\jscript.dll /E /P everyone:N


 浙公网安备 33010602011771号
浙公网安备 33010602011771号