攻防世界-进阶-2-IgniteMe
main函数代码
int __cdecl main(int argc, const char **argv, const char **envp)
{
int result; // eax
size_t i; // [esp+4Ch] [ebp-8Ch]
char v5[4]; // [esp+50h] [ebp-88h]
char v6[28]; // [esp+58h] [ebp-80h]
char v7; // [esp+74h] [ebp-64h]
sub_402B30(&unk_446360, "Give me your flag:");
sub_4013F0(sub_403670);
sub_401440(v6, 127);
if ( strlen(v6) < 0x1E && strlen(v6) > 4 )
{
strcpy(v5, "EIS{");
for ( i = 0; i < strlen(v5); ++i )
{
if ( v6[i] != v5[i] )
{
sub_402B30(&unk_446360, "Sorry, keep trying! ");
sub_4013F0(sub_403670);
return 0;
}
}
if ( v7 == 125 )
{
if ( (unsigned __int8)sub_4011C0(v6) )
sub_402B30(&unk_446360, "Congratulations! ");
else
sub_402B30(&unk_446360, "Sorry, keep trying! ");
sub_4013F0(sub_403670);
result = 0;
}
else
{
sub_402B30(&unk_446360, "Sorry, keep trying! ");
sub_4013F0(sub_403670);
result = 0;
}
}
else
{
sub_402B30(&unk_446360, "Sorry, keep trying!");
sub_4013F0(sub_403670);
result = 0;
}
return result;
}
加密函数代码
bool __cdecl sub_4011C0(char *a1)
{
size_t v2; // eax
signed int v3; // [esp+50h] [ebp-B0h]
char v4[32]; // [esp+54h] [ebp-ACh]
int v5; // [esp+74h] [ebp-8Ch]
int v6; // [esp+78h] [ebp-88h]
size_t i; // [esp+7Ch] [ebp-84h]
char v8[128]; // [esp+80h] [ebp-80h]
if ( strlen(a1) <= 4 )
return 0;
i = 4;
v6 = 0;
while ( i < strlen(a1) - 1 )
v8[v6++] = a1[i++];
v8[v6] = 0;
v5 = 0;
v3 = 0;
memset(v4, 0, 0x20u);
for ( i = 0; ; ++i )
{
v2 = strlen(v8);
if ( i >= v2 )
break;
if ( v8[i] >= 97 && v8[i] <= 122 )
{
v8[i] -= 32;
v3 = 1;
}
if ( !v3 && v8[i] >= 65 && v8[i] <= 90 )
v8[i] += 32;
v4[i] = byte_4420B0[i] ^ sub_4013C0(v8[i]);
v3 = 0;
}
return strcmp("GONDPHyGjPEKruv{{pj]X@rF", v4) == 0;
}
代码分析
if ( v8[i] >= 97 && v8[i] <= 122 )
{
v8[i] -= 32;
v3 = 1;
}
if ( !v3 && v8[i] >= 65 && v8[i] <= 90 )
v8[i] += 32;
大写变成小写,小写变成大写。
return (a1 ^ 0x55) + 72;
v4[i] = byte_4420B0[i] ^ sub_4013C0(v8[i]);
//转变为
v4[i] = byte_4420B0[i] ^ {(v8[i] ^ 0x55) + 72}
//则
v8[i]=(v4[i]^byte_4420B0[i]-72)^0x55
//其中,需要将其转换为ASCII
v4="GONDPHyGjPEKruv{{pj]X@rF"
4420B0中的数据需要在进入十六进制视图中查看,提取出其中32位
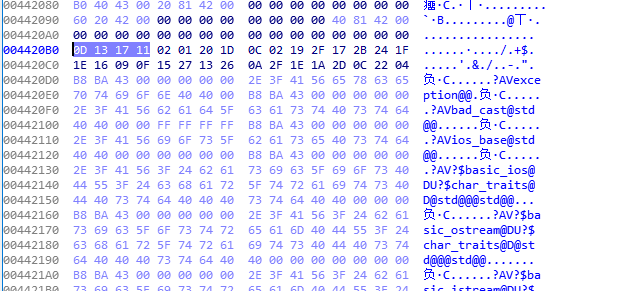
0D 13 17 11 02 01 20 1D 0C 02 19 2F 17 2B 24 1F
1E 16 09 0F 15 27 13 26 0A 2F 1E 1A 2D 0C 22 04
脚本
分两步走, 第一步求出v8:
for i in range(len(v4)):
v8 += chr(((ord(v4[i]) ^ byte_4420B0[i]) - 72) ^ 0x55)
第二部根据v8推出flag
直接大写变成小写就可以了



